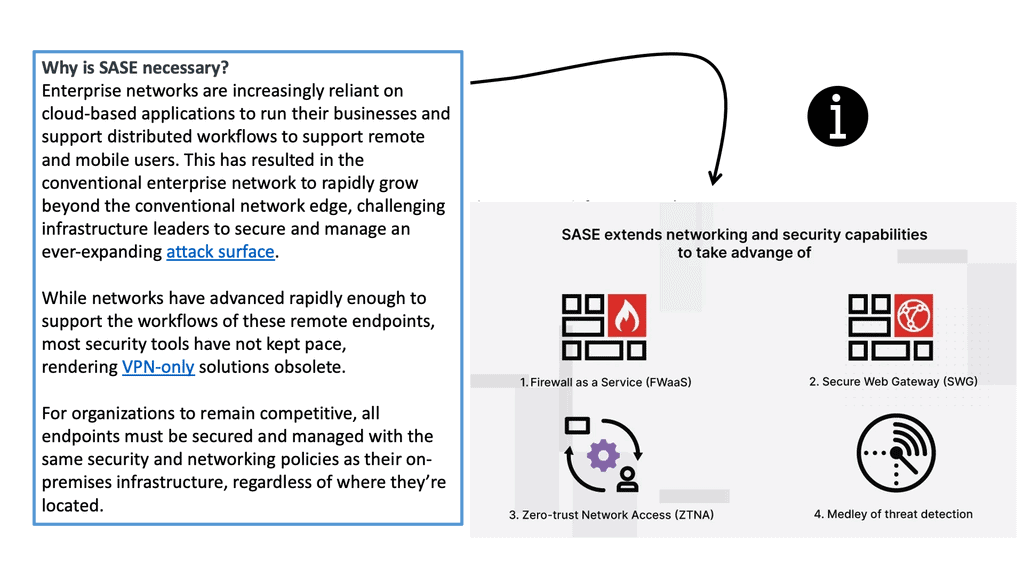
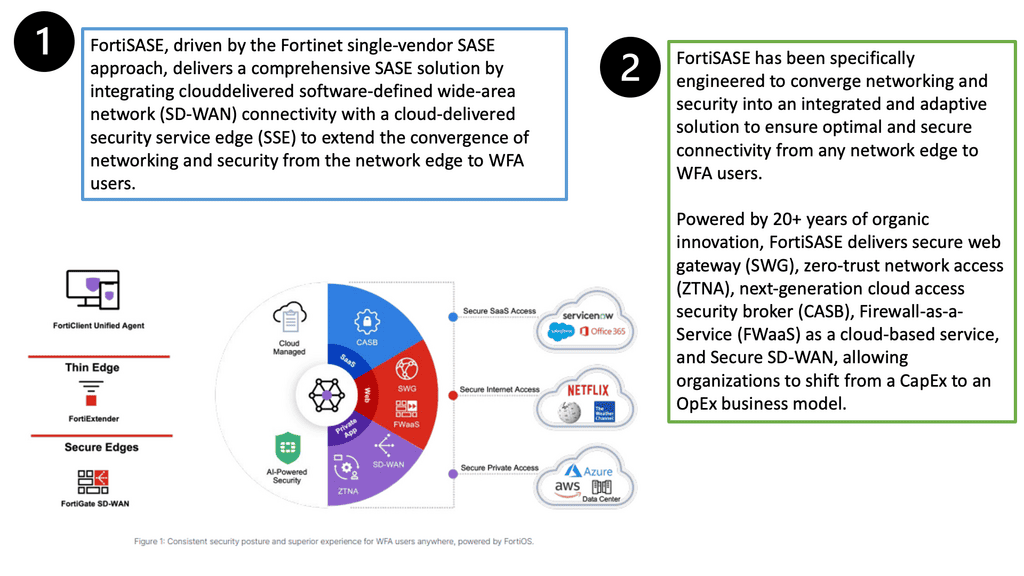
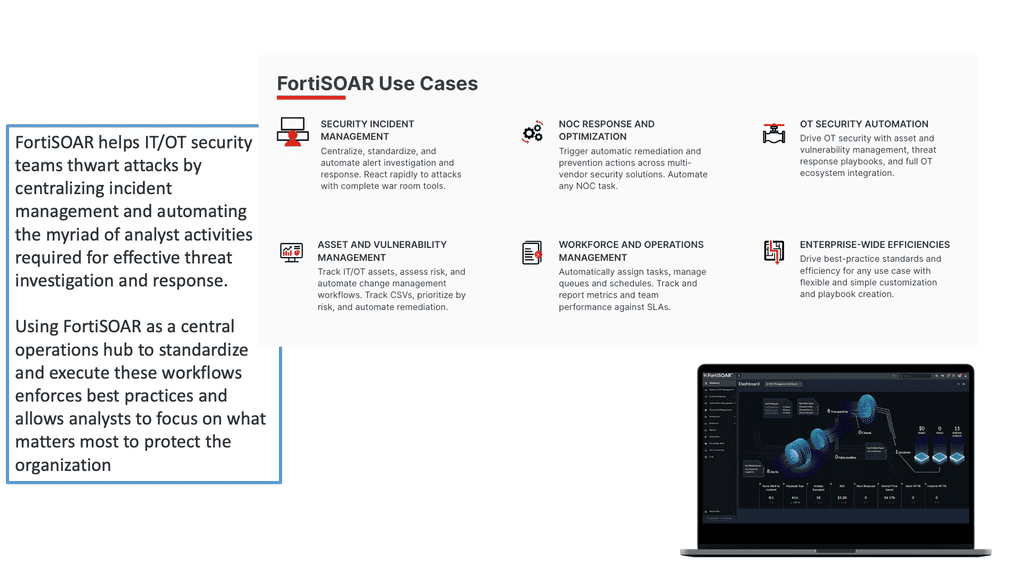
Ericom Cradlepoint
Ericsson ERIC subsidiary Cradlepoint acquired Ericom Software and its enterprise cloud security platform for an undisclosed amount. The acquisition will likely enhance Cradlepoint’s Secure Access Service Edge (SASE) framework and zero-trust offerings for hybrid 5G and wireline environments. By offering secure access service edge (SASE) capabilities for both users and devices via its agentless architecture, Ericom complements Cradlepoint NetCloud Exchange by providing zero trust-based access to both users and devices.
It is generally accepted that traditional security solutions rely on agents installed on the devices. However, this approach only works for IoT/IIoT devices or unmanaged devices connected to 5G/cellular networks. A SASE and zero trust policy are vital for IoT devices’ secure and reliable operation. Their number is rapidly increasing, becoming the favorite target of bad actors.
“Enterprise adoption of 5G requires an innovative network security approach that minimizes the attack surface caused by IoT and IIoT device proliferation. In addition, it provides agentless identity-based secure access from ever-growing IoT/IIoT devices and users to private and SaaS applications,” said Cradlepoint SVP Manish Tiwari.
A key point: Useful information for internal content:
- Ericom Browser Isolation
- Software Defined Internet Exchange
- SASE Model
- SD WAN SASE
- Zero Trust SASE
- SASE Definition
Cradlepoint Consultation
Having established many LTE networks worldwide, Ericsson is the world’s largest supplier of LTE technology. User demand for coverage speed and quality has grown manifold since the advent of the smartphone market and the subsequent use of mobile broadband. Additionally, network tuning and optimization are continuously needed to maintain superior performance as traffic grows. As a result, there is a high demand for Ericsson’s network coverage expansion and network upgrades for higher speeds and capacities among operators.
5G system development is the company’s main focus. Digitizing industries and broadband will be possible only with the standardization of 5G.In conjunction with 5G deployment, technologies such as network slicing are expected to gain traction in IoT devices. Currently, Ericsson has 145 5G networks active across 63 countries.
CradlePoint’s Netcloud Exchange
While Cradlepoint’s Netcloud Exchange platform focuses on private cellular networks and WAN security, the Ericom acquisition allows Cradlepoint to provide converged networking and security software.
With the Ericom acquisition, Cradlepoint will be able to offer cellular-focused enterprise customers a converged networking and security stack. As a result, users and devices can be mobile across cellular networks and WANs with a unified platform offering asset visibility and segmentation.
Through Cradlepoint NetCloud Exchange (NCX), organizations can combine 5G performance, SD-WAN efficiency, Zero Trust Network Access (ZTNA), and VPNs into one WWAN solution that combines 5G performance, SD-WAN efficiency, and Zero Trust Network Access (ZTNA).
Through integrating 5G, SD-WAN, and security, NetCloud Exchange on the Cradlepoint NetCloud platform facilitates growth and performance across the wide area network. What are the benefits of NetCloud Exchange for organizations?
- 5G comes first
The NCX platform is designed to help organizations transform their business into a 5G enterprise. By using this technology, vehicles, IoT devices, remote workers, fixed and temporary location users, and fixed and temporary locations can benefit from improved performance, latency, and network slicing capabilities.
- Optimized QoE
The SD-WAN services offered by NCX are designed to optimize the flow of cellular and wired traffic for the highest quality of experience (QoE). To achieve high quality of service, traffic is optimized over both dual cellular connections and hybrid WAN connections.
- A zero-trust foundation
It is through the use of identity- and context-based parameters that ZTNA restricts users from moving from one network to another. It is through the implementation of simple security policies and authentication requirements that the bad guys are kept out of the system, thereby reducing the attack surface.
- Built for scale
NCX architecture is designed for cellular scale thanks to the “pay as you grow” model that we offer. So no matter how many vehicles, sites, or things you have, whether you are onboarding a small fleet or expanding your fleet to tens of thousands, WAN growth can be accommodated easily.
- Simplified management
It is a powerful combination of name-based routing, adaptive traffic management, and built-in traffic orchestration that simplifies lean IT teams’ setup, monitoring, and troubleshooting process.
- Unified WAN architecture
In contrast to multi-vendor solutions, NCX combines 5G, SD-WAN, and security into one WAN architecture that shares standard components, policies, and streamlined processes across all its supported services to offer a complete solution.
By acquiring Ericom, Cradlepoint is further extending the Netcloud Exchange architecture, making it possible to offer a unified 5G enterprise security stack with a secure private cellular network, secure wide area network, and secure web application to protect both devices and users, providing consistent policies regardless of whether they are connected to a 5G WAN or a private cellular network.
With the ZTEdge security service edge (SSE) platform, Ericom will provide Cradlepoint customers with security capabilities such as remote browser isolation (RBI), secure web gateway (SWG), cloud access security broker (CASB), virtual meeting isolation (VMI), web app isolation (WAI), and zero trust network access (ZTNA).
Ericom Global Cloud platform
Ericom solutions are delivered via the Ericom Global Cloud platform. Ericom Global Cloud protects your users, data, and applications. As a result, your remote and home-based workers and globally distributed teams can easily access the resources they need without latency. A simple-as-a-service model allows Cradlepoint to deliver these security capabilities through Ericom Global Cloud. With Ericom Global Cloud, users have high availability elastic cloud infrastructure that scales to meet their needs.
In addition to being hosted by Tier 1 IaaS providers, it leverages multi-cloud infrastructure-as-code technologies. A geolocation service routes users to the closest cloud access point to minimize latency. As a result of auto-scaling and load balancing, high performance is ensured regardless of demand. New PoPs can be deployed in several days and are centrally managed and monitored.
Cradlepoint is now working on integrating Ericom capabilities with NetCloud Exchange to provide a 5G SASE stack as soon as possible.