SD WAN Security
In today's interconnected world, where businesses rely heavily on networks for their daily operations, ensuring the security of Wide Area Networks (WANs) has become paramount. WANs are at the heart of data transmission, connecting geographically dispersed locations and enabling seamless communication. However, with the rise of cyber threats and the increasing complexity of networks, it is crucial to understand and implement effective WAN security measures. In this blog post, we will explore the world of WAN security, its key components, and strategies to safeguard your network.
WAN security refers to the protection of data and network resources against unauthorized access, data breaches, and other malicious activities. It involves a combination of hardware, software, and protocols designed to ensure the confidentiality, integrity, and availability of data transmitted over wide area networks. By implementing robust security measures, organizations can mitigate the risks associated with WAN connectivity and maintain the privacy of their sensitive information.
Firewalls: Firewalls act as a barrier between internal networks and external threats, monitoring and controlling incoming and outgoing network traffic. They enforce security policies and filter data packets based on predetermined rules, preventing unauthorized access and potential attacks.
Virtual Private Networks (VPNs): VPNs create secure, encrypted tunnels over public networks, such as the internet. By establishing a VPN connection, organizations can ensure the confidentiality and integrity of data transmitted between remote locations, protecting it from eavesdropping and tampering.
Intrusion Detection and Prevention Systems (IDPS): IDPS solutions monitor network traffic in real-time, identifying and responding to potential threats. They analyze network packets, detect unusual or malicious activity, and take prompt action to prevent and mitigate attacks.
Key Services:
Strong Authentication: Implement multi-factor authentication methods to enhance access control and verify the identity of users connecting to the network. This includes the use of passwords, smart cards, biometrics, or other authentication factors.
Regular Patching and Updates: Keep network devices, software, and security solutions up to date with the latest patches and firmware releases. Regularly applying updates helps address known vulnerabilities and strengthens network security.
Encryption: Utilize strong encryption protocols, such as AES (Advanced Encryption Standard), to protect sensitive data in transit. Encryption ensures that even if intercepted, the data remains unreadable to unauthorized individuals.
In an age where cyber threats are ever-evolving, securing your WAN is crucial to maintain the integrity and confidentiality of your data. By understanding the key components of WAN security, implementing best practices, and maintaining proactive network monitoring, organizations can strengthen their defenses and safeguard their networksMatt Conran
Highlights: SD WAN Security
Understanding SD-WAN
SD-WAN is a technology that simplifies the management and operation of a Wide Area Network (WAN) by separating the network hardware from its control mechanism. It allows organizations to connect remote branches, data centers, and cloud networks efficiently. However, with this flexibility comes the need for robust security measures.
As businesses increasingly adopt SD-WAN to meet their networking needs, ensuring the security of these networks becomes paramount. Cyber threats such as data breaches, malware attacks, and unauthorized access pose significant risks. Organizations must understand the potential vulnerabilities and implement appropriate security measures to protect their SD-WAN infrastructure.
Deployment Best Practices:
When deploying SD-WAN, several crucial security considerations need to be addressed.Each of these factors plays a vital role in safeguarding the SD-WAN environment. These include:
- Authentication and access control,
- Encryption,
- Threat detection and prevention,
- Secure connectivity to cloud services, and
- Secure integration with existing security infrastructure.
Organizations should follow best practices to ensure optimal security in an SD-WAN environment. These include conducting regular security audits, implementing multi-factor authentication, utilizing encryption for data in transit, deploying intrusion detection and prevention systems, and establishing secure connectivity protocols. By adhering to these practices, businesses can mitigate potential risks and enhance their overall network security.
Key SD-WAN Security Point:
SD-WAN security is mainly based on the use of IP security (IPsec), VPN tunnels, next-generation firewalls (NGFWs), and the microsegmentation of application traffic.
Example Product: Cisco Meraki
**Section 1: Simplified Network Management**
One of the standout features of Cisco Meraki is its intuitive dashboard, which offers a centralized interface for managing your entire network. Gone are the days of juggling multiple consoles and interfaces. With Cisco Meraki, you can oversee network performance, security settings, and device management all in one place. This streamlined approach not only saves time but also reduces the likelihood of human error.
**Section 2: Advanced Security Features**
When it comes to network security, Cisco Meraki pulls out all the stops. The platform offers a variety of advanced security features, including:
– **Next-Gen Firewall:** Cisco Meraki’s firewall capabilities go beyond traditional firewalls by providing application visibility and control, intrusion prevention, and advanced malware protection.
– **Network Access Control (NAC):** Ensure that only authorized devices can connect to your network, minimizing the risk of unauthorized access.
– **Auto VPN:** Simplify the process of establishing secure connections between remote sites with automatic VPN configuration.
These features ensure that your network remains secure against a wide range of cyber threats, giving you peace of mind.
 **Section 3: Scalability and Flexibility**
**Section 3: Scalability and Flexibility**
Cisco Meraki is designed to grow with your business. Whether you’re adding new devices, expanding to new locations, or integrating third-party applications, the platform scales effortlessly. The cloud-based architecture allows for easy updates and seamless integration, ensuring that your network remains up-to-date with the latest security protocols and features.
**Section 4: Real-Time Analytics and Reporting**
Data is the new gold, and Cisco Meraki understands this well. The platform offers robust analytics and reporting tools that provide real-time insights into your network’s performance and security posture. From bandwidth usage to threat detection, the dashboard provides comprehensive metrics that help in making informed decisions. This level of visibility is crucial for identifying potential vulnerabilities and optimizing network performance.
A Layered Approach to Security
Decrease the Attack Surface
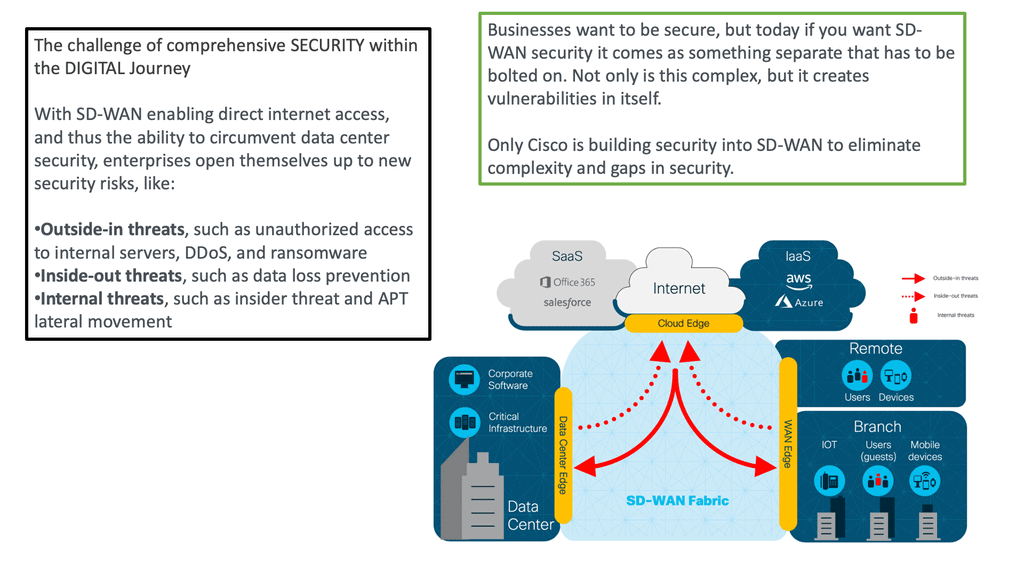
SD-WAN security allows end users to connect directly to cloud applications and resources without backhauling through a remote data center or hub. This will enable organizations to offload guest traffic to the Internet instead of using up WAN and data center resources. The DIA model, where Internet access is distributed across many branches, increases the network’s attack surface and makes security compliance a critical task for almost every organization.
The broad threat landscape includes cyber warfare, ransomware, and targeted attacks. Firewalling, intrusion prevention, URL filtering, and malware protection must be leveraged to prevent, detect, and protect the network from all threats. The branches can consume Cisco SD-WAN security through integrated security applications within powerful WAN Edge routers, cloud services, or regional hubs where VNF-based security chains may be leveraged or robust security stacks may already exist.
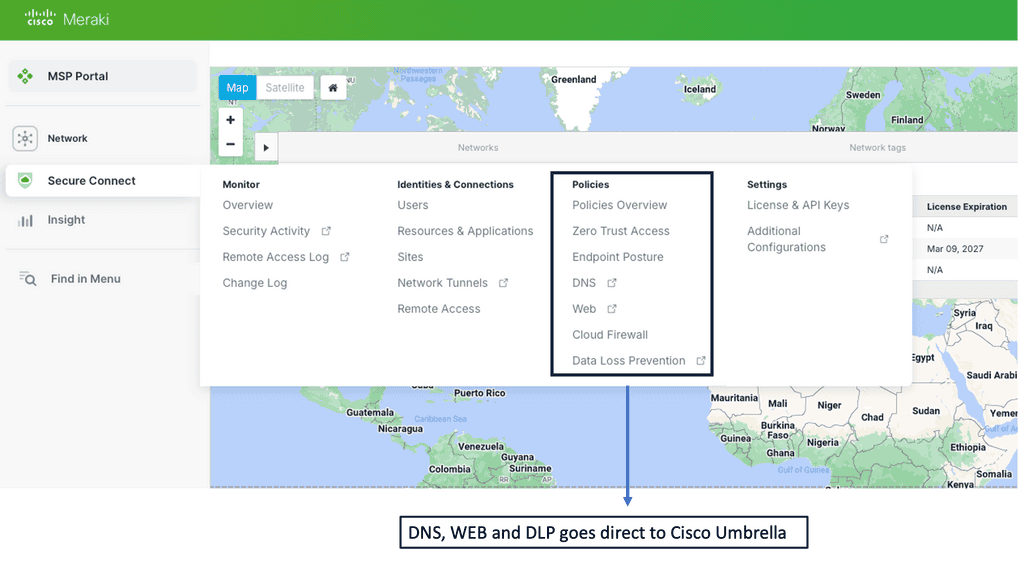
The Role of Cisco Umbrella
SD-WAN can be combined with Cisco Umbrella via a series of redundant IPsec tunnels for additional security measures, increasing the robustness of your WAN Security.
Cisco Umbrella is a cloud-based security platform that offers advanced threat protection and secure web gateways. By providing an additional layer of security, Umbrella helps organizations defend against malicious activities, prevent data breaches, and protect their network infrastructure. With its global threat intelligence and DNS-layer security, Umbrella offers real-time threat detection and protection, making it an ideal complement to SD-WAN deployments.
Integrating Umbrella with SD-WAN
By integrating Cisco Umbrella with SD-WAN, organizations can fortify their security posture. Umbrella’s DNS-layer security protects against threats, blocking malicious domains and preventing connections to command and control servers. This, combined with SD-WAN’s ability to encrypt traffic and segment networks, creates a robust security framework that safeguards against cyber threats and potential data breaches.
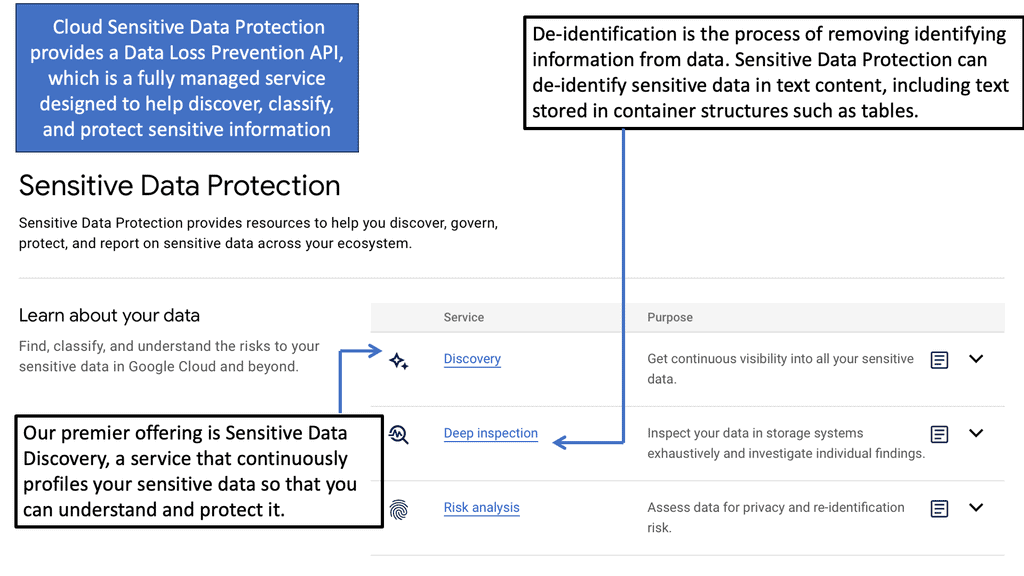
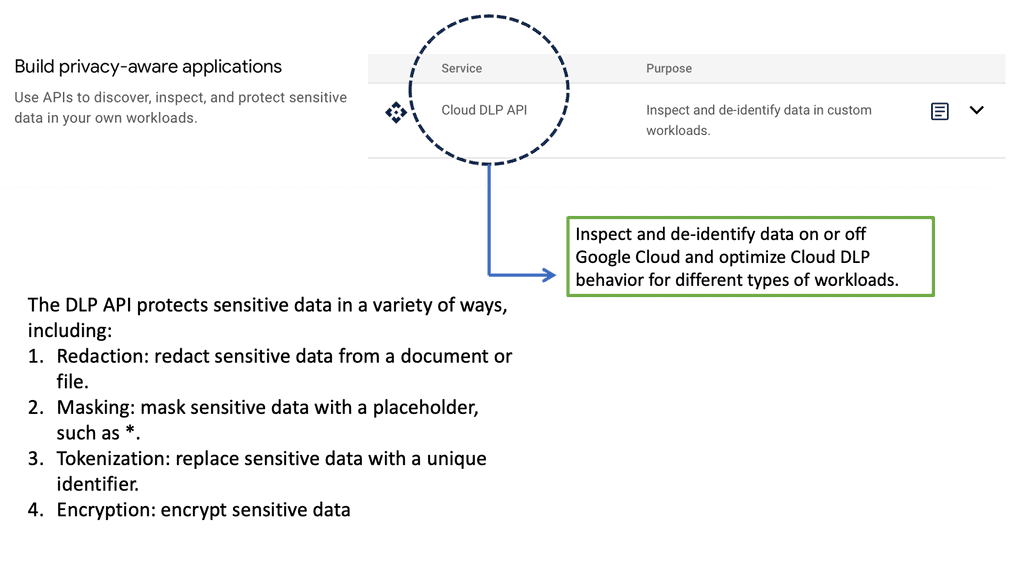
Example Technology: Sensitive Data Protection
SD-WAN Security Features
Encryption and Data Protection: One of SD-WAN’s fundamental security features is encryption. By encrypting data traffic, SD-WAN ensures that sensitive information remains protected from unauthorized access or interception. This feature is essential when transmitting data across public networks or between different branches of an organization.
Firewall Integration: Another key security feature of SD-WAN is its seamless firewall integration. SD-WAN solutions can provide advanced threat detection and prevention mechanisms by incorporating firewall capabilities. This helps businesses safeguard their networks against potential cyber-attacks, ensuring the confidentiality and integrity of their data.
Intrusion Detection and Prevention System (IDPS): SD-WAN solutions often have built-in Intrusion Detection and Prevention Systems (IDPS). These systems monitor network traffic for suspicious activity or potential threats, promptly alerting administrators and taking necessary actions to mitigate risks. The IDPS feature enhances the overall security posture of the network, proactively defending against possible attacks.
Secure Multi-tenancy: SD-WAN offers secure multi-tenancy capabilities for organizations operating in multi-tenant environments. This ensures that each tenant’s network traffic is isolated and protected, preventing unauthorized access between tenants. Secure multi-tenancy is essential for maintaining the confidentiality and preventing data breaches in shared network infrastructures.
Example Technology: IPS IDS
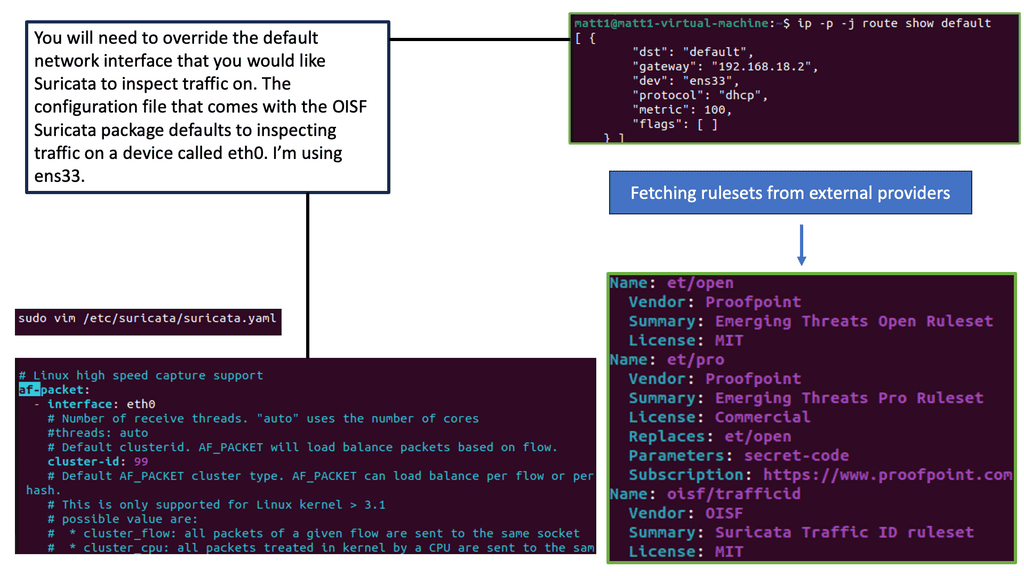
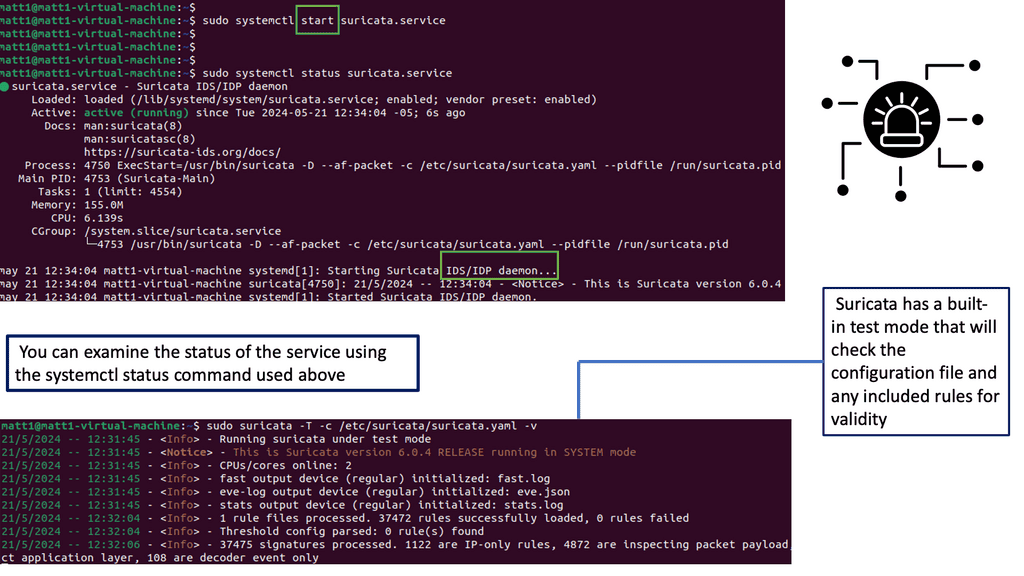
Understanding Suricata IPS/IDS
Suricata is an open-source intrusion detection and prevention system (IDS/IPS) that offers advanced threat detection and prevention capabilities. It combines the functionalities of a traditional IDS with the added benefits of an IPS, making it a powerful asset in network security.
Suricata boasts many features and capabilities, making it a formidable defense mechanism against cyber threats. It provides a multi-layered approach to identifying and mitigating security risks, from signature-based detection to protocol analysis and behavioral anomaly detection.
WAN Security
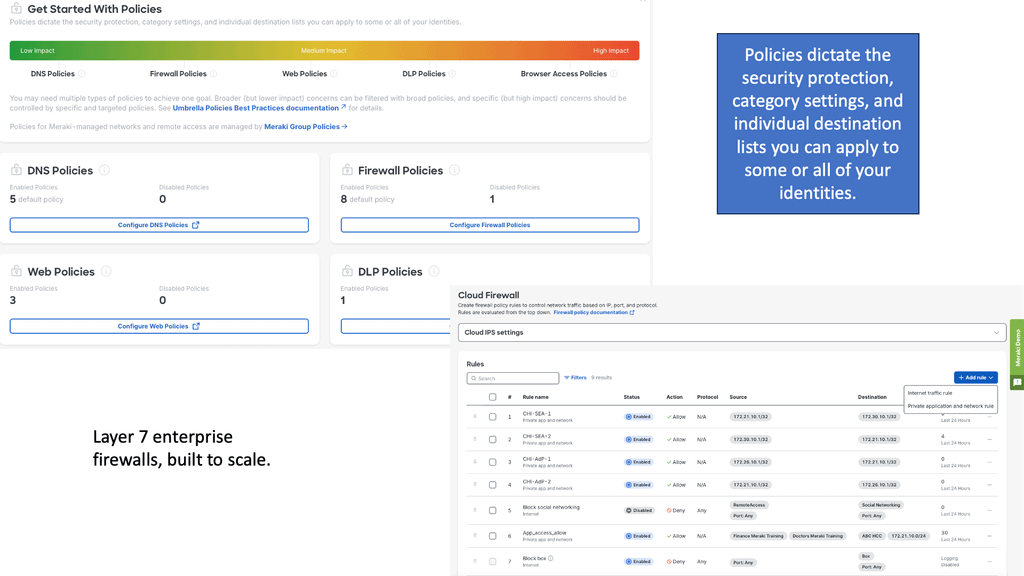
Enterprise Firewall:
Traditional branch firewall design involves deploying the appliance in either in-line Layer 3 mode or transparent Layer 2 mode behind or even ahead of the WAN Edge router. Now, for stateful inspection, we have to have another device. This adds complexity to the enterprise branch and creates unnecessary administrative overhead in managing the added firewalls.
**Application-aware Firewall**
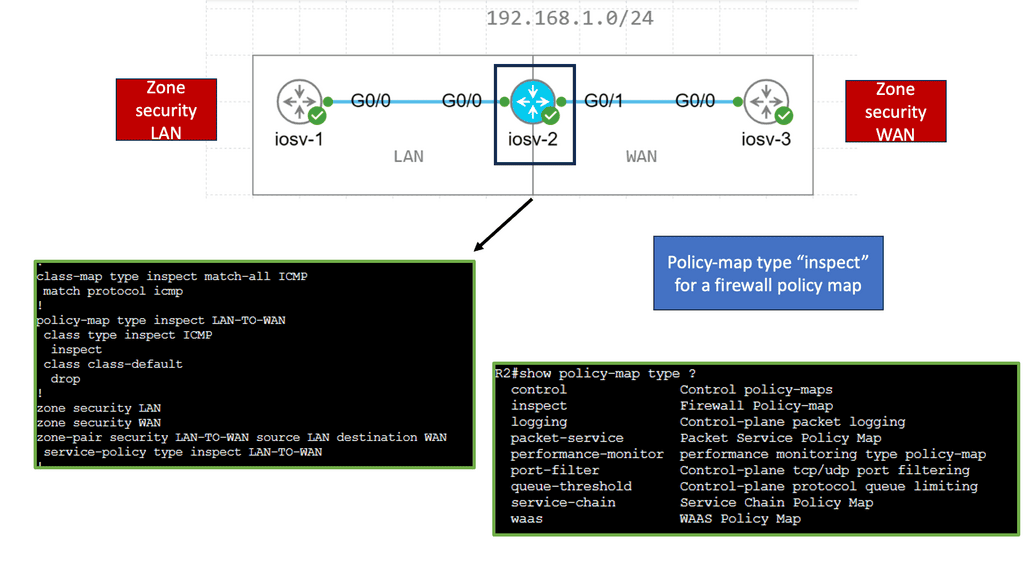
A proper firewall protects stateful TCP sessions, enables logging, and implements a zero-trust domain between network segments. Cisco SD-WAN takes an integrated approach and implements a robust Application-Aware Enterprise Firewall directly into the SD-WAN code.
Cisco SD-WAN takes an integrated approach. It has implemented an application-aware enterprise firewall directly into the SD-WAN code, so there is no need for another inspection device.
Cisco has integrated the stateful firewall with the NBAR 2 engine. Now, with these two, we have good application visibility and granularity. In addition, the enterprise firewall can detect applications with the very first packet. The Cisco SD-WAN firewall provides stateful inspection, zone-based policies, and segment awareness. It can also classify over 1,400 Layer 7 applications and apply granular policy control to them based on category or individual basis.
Example Firewalling: Cisco’s Zone-Based Firewall
Understanding Zone-Based Firewalls
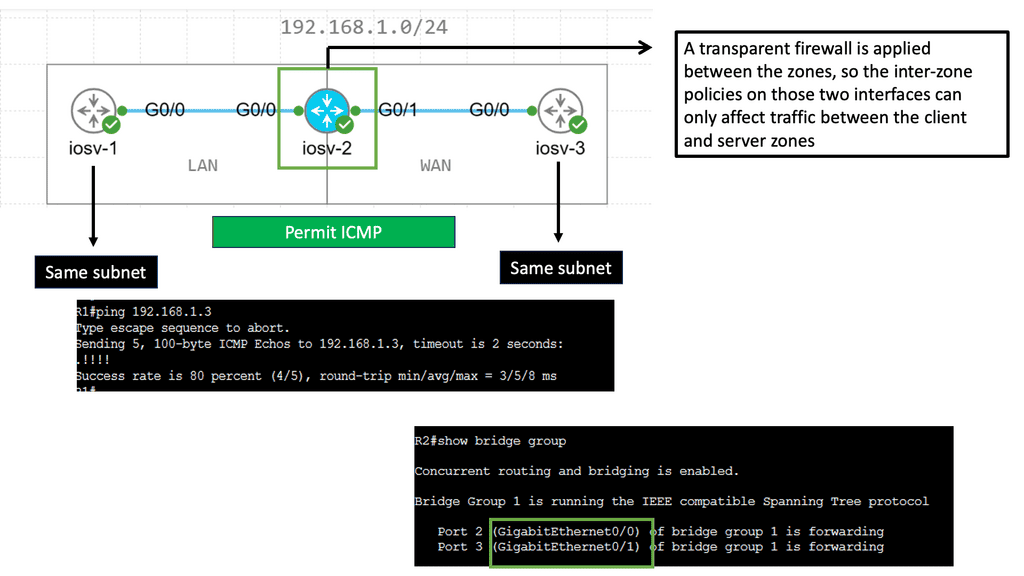
At its core, a zone-based firewall (ZBF) is a security feature that allows network administrators to define security zones and control the traffic flow between them. Unlike traditional firewalls, which operate based on interfaces, ZBF operates based on zones. Each zone represents a logical group of network devices, such as LAN, WAN, or DMZ, and traffic between these zones is regulated using policies defined by the administrator.
1. Enhanced Network Segmentation: By dividing the network into distinct security zones, ZBF enables granular control over the traffic flow, minimizing potential attackers’ risk of lateral movement. This segmentation helps contain breaches and limits the impact of security incidents.
2. Simplified Policy Management: ZBF simplifies firewall policy management by allowing administrators to define policies at the zone level rather than dealing with complex interface-based rules. This approach streamlines policy deployment and reduces the likelihood of misconfigurations.
3. Application Layer Inspection: ZBF supports deep packet inspection, enabling administrators to perform application-specific filtering and apply security policies based on the application layer attributes. This capability enhances network visibility and strengthens security posture.
 Intrusion Prevention:
Intrusion Prevention:
An IDS/IPS can inspect traffic in real time to detect and prevent attacks by comparing the application behavior against a known database of threat signatures. This is based on the Snort engine and runs as a container. So, Snort is the most widely deployed intrusion prevention system globally. The solution is combined with Cisco Talos, which puts out the signatures. The Cisco Talos Intelligence Group is one of the world’s largest commercial threat intelligence teams, which are comprised of researchers, analysts, and engineers.
**Connecting to Tales Signature Database**
Cisco vManage connects to the Talos signature database, downloads the signatures on a configurable periodic or on-demand basis, and pushes them down into the branch WAN Edge routers without user intervention. Signatures are rules that an IDS and an IPS uses to detect typical intrusive activity. Also, you can use the allowlist approach if you see many false positives. It is better to start this in detect mode so the engine can learn before you start blocking.
**Snort Based IPS/IDS**
Intrusion detection and prevention (IDS/IPS) can inspect traffic in real time to detect and prevent cyberattacks and notify the network operator through Syslog events and dashboard alerts. IDS/IPS is enabled through IOS-XE application service container technology. KVM and LxC containers are used, and they differ mainly in how tightly they are coupled to the Linux kernel used in most network operating systems, such as IOS XE.
The Cisco SD-WAN IDS/IPS runs Snort, the most widely deployed intrusion prevention engine globally, and leverages dynamic signature updates published by Cisco Talos. The signatures are updated via vManage or manually using CLI commands available on the WAN Edge device.
URL filtering:
URL filtering is another Cisco SD-WAN security function that leverages the Snort engine to inspect HTTP and HTTPS payloads to provide web security at the branch. In addition, the URL filtering engine enforces acceptable use controls to block or allow websites. It downloads the URL database and blocks websites based on over 80 categories. It can also make decisions based on a web application score. This information is gained from Webroot/Brightcloud.
**Comprehensive Security**
URL Filtering leverages the Snort engine to provide comprehensive web security at the branch. It can be configured to permit or deny websites based on 82 different categories, the site’s web reputation score, and a dynamically updated URL database when an end user requests access to a particular website through their web browser. The URL Filtering engine inspects the web traffic, queries any custom URL lists, compares the URL to the blocked or allowed categories policy, and finally consults the URL Filtering database.
Note: Advanced Malware Protection and Threat Grid:
Advanced Malware Protection (AMP) and Threat Grid are the newest additions to the SD-WAN security features. As with URL filtering, both AMP and Threat Grid leverage the Snort engine and Talos for the real-time inspection of file downloads and malware detection. AMP can block malware entering your network using antivirus detection engines, one-to-one signature matching, machine learning, and fuzzy fingerprinting.
DNS Web Layer Security:
Finally, we have DNS layer security. Some countries have a rule that you cannot inspect HTTP or HTTPS packets to filter content. So, how can you filter content if you can’t inspect HTTP or HTTPS packets?
We can do this with DNS packets. So before the page is loaded in the browser, the client sends a DNS request to the DNS server for the website, asking for a name to IP mapping. Once registered with Umbrella cloud, the WAN Edge router intercepts DNS requests from the LAN and redirects them to Umbrella resolvers.
If the requested page is a known malicious site or is not allowed (based on the policies configured in the Umbrella portal, the DNS response will contain the IP address for an Umbrella-hosted block page.
**DNSCrypt, EDNS, and TLS Decryption**
DNS web layer security also supports DNSCrypt, EDNS, and TLS decryption. In the same way that SSL turns HTTP web traffic into HTTPS encrypted web traffic, DNSCrypt turns regular DNS traffic into encrypted DNS traffic that is secure from eavesdropping and man-in-the-middle attacks. It does not require changes to domain names or how they work; it simply provides a method for securely encrypting communication between the end user and the DNS servers in the Umbrella cloud located around the globe.
In some scenarios, it may be essential to avoid intercepting DNS requests for internal resources and passing them on to an internal or alternate DNS resolver. To meet this requirement, the WAN Edge router can leverage local domain bypass functionality, where a list of internal domains is defined and referenced during the DNS request interception process.
Related: For additional pre-information, you may find the following posts helpful:
Starting WAN Security
Key Points on SD-WAN Security
A: Unveiling the Security Risks in SD-WAN Deployments:
While SD-WAN offers enhanced network performance and agility, it also expands the attack surface for potential security breaches. The decentralized nature of SD-WAN introduces complexities in securing data transmission and protecting network endpoints. Threat actors constantly evolve tactics, targeting vulnerabilities within SD-WAN architectures to gain unauthorized access, intercept sensitive information, or disrupt network operations. Organizations must be aware of these risks and implement robust security measures.
B: Implementing Strong Authentication and Access Controls:
Robust authentication mechanisms and access controls are essential to mitigate security risks in SD-WAN deployments. Multi-factor authentication (MFA) should be implemented to ensure that only authorized users can access the SD-WAN infrastructure. Additionally, granular access controls should be enforced to restrict privileges and limit potential attack vectors. By implementing these measures, organizations can significantly enhance the overall security posture of their SD-WAN deployments.
C: Ensuring Encryption and Data Privacy:
Protecting data privacy is critical to SD-WAN security. Encryption protocols should be employed to secure data in transit between SD-WAN nodes and across public networks. By leveraging robust encryption algorithms and key management practices, organizations can ensure the confidentiality and integrity of their data, even in the face of potential interception attempts. Data privacy regulations, such as GDPR, further emphasize the importance of encryption in safeguarding sensitive information.
D: Monitoring and Threat Detection:
Continuous monitoring and threat detection mechanisms are pivotal in maintaining SD-WAN security. Intrusion Detection Systems (IDS) and Security Information and Event Management (SIEM) tools can provide real-time insights into network activities, identifying potential anomalies or suspicious behavior. Through proactive monitoring and threat detection, organizations can swiftly respond to security incidents and mitigate potential risks before they escalate.
Example Technology: Scanning Networks
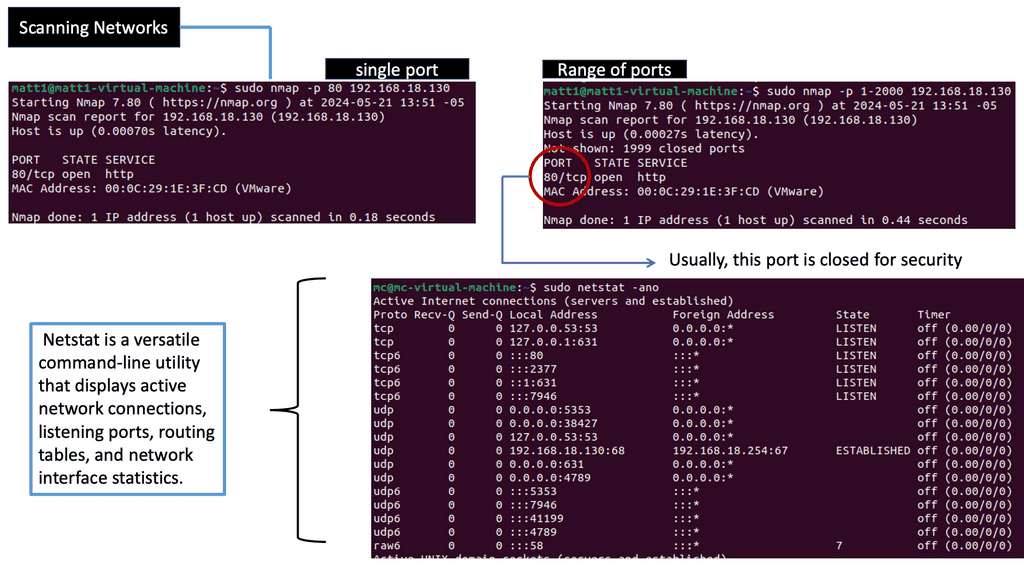
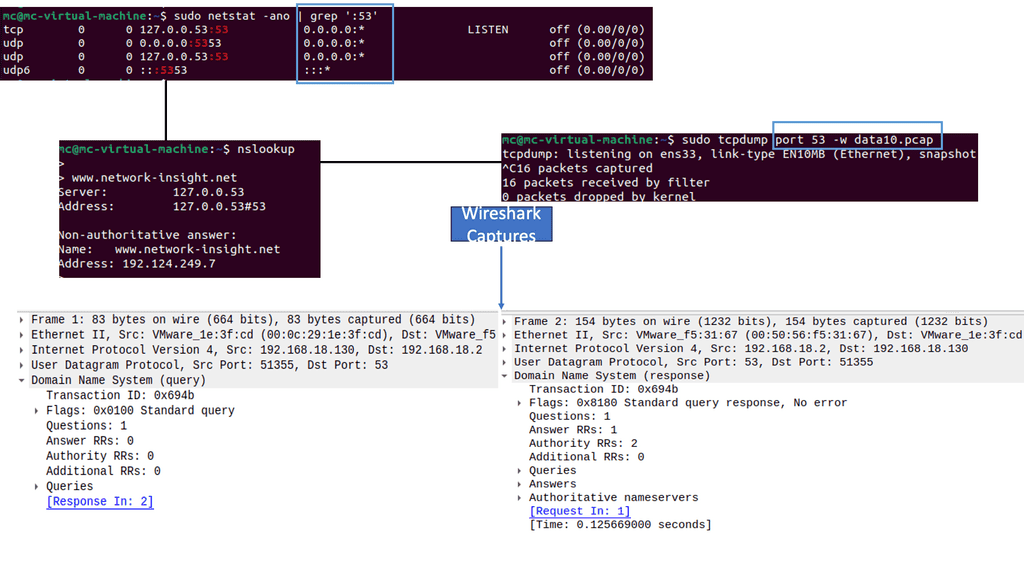
What is Network Scanning?
Network scanning examines a network to identify active hosts, open ports, and potential vulnerabilities. By systematically scanning a network, security experts gain valuable insights into its architecture and weaknesses, allowing them to strengthen defenses and prevent unauthorized access.
a. Ping Sweeps: Ping sweeps are simple yet effective techniques that involve sending ICMP Echo Request packets to multiple hosts to determine their availability and responsiveness.
b. Port Scans: Port scanning involves probing a host for open ports and determining which services or protocols are running. Tools like Nmap provide comprehensive port scanning capabilities.
c. Vulnerability Scans: Scanners search for weaknesses in network devices, operating systems, and applications. Tools such as OpenVAS and Nessus are widely used to identify potential vulnerabilities.
SD WAN’s Initial Focus
– The initial SD-WAN deployment model involved integrating corporate communications with the organizational fabric and corporate communications with the SD-WAN overlay. There was an immediate ROI, as cheap broadband links could be brought into the branch and connected to the organization’s network with the SD-WAN overlay.
– For some time now, we have been gaining benefits from SD-WAN’s base, such as site connection; we can now design and implement the application optimizations that SD-WAN offers, such as integrated security. This enables us to get additional benefits from SD-WAN.
– From a security perspective, end-to-end segmentation and policy are critical. The control, data, and management planes must be separated throughout the environment and secured appropriately. In addition, the environment should support native encryption that is robust and scalable and offers lightweight key management.
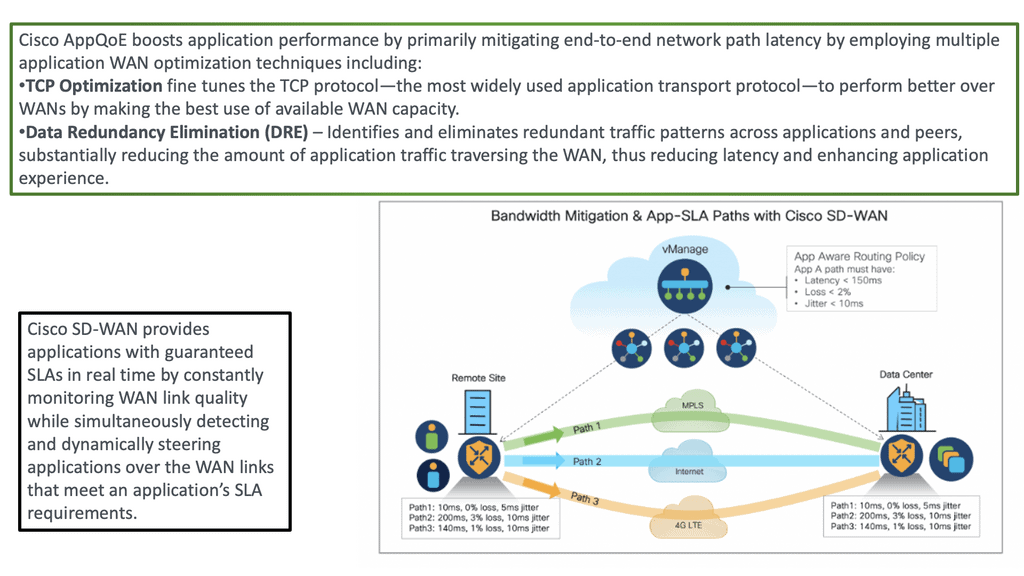
SD-WAN Key Security Feature: DIA
With SD-WAN, we can now instead go directly from the branch through DIA to the applications hosted in the Cloud by leveraging DNS and geo-location services for the best possible performance. This, however, presents different types of attack surfaces that we need to deal with.
We have different security implications for moving the Internet edge to the branch. In the DIA model, Internet access is distributed across many components; for example, unsecured guest users are allowed Internet access directly. They may be guests, but we are responsible for content filtering and ensuring compliance. So, we have internal and external attack vectors that need to be considered with this new approach to the WAN.
Threat Categories:
You could group these threats into three main categories. Outside-in threats could consist of denial of services or unauthorized access. Inside-out threats could be malware infection or phishing attacks. Then, we have internal threats where lateral movements are a real problem. With every attack vector, the bad actor must find high-value targets, which will likely not be the first host they land on.
Required: Integrated Security at the Branch:
To protect against these threats, we need a new security model with comprehensive, integrated security at the branch site. The branch leveraged the appropriate security mechanisms, such as application-aware firewalling, intrusion prevention, URL filtering, and malware protection, to prevent, detect, and protect the network and the various identities from all threats.
SD-WAN Deployment Models
SD-WAN can be designed in several ways. For example, you can have integrated security at the mentioned branch. We can also consume security through cloud services or regional hubs where VNF-based security chains may be leveraged. So, to enable or deploy SD-WAN security, you can choose from different types of security models.
**Thin Branch**
The first model would be cloud security, often considered a thin branch with security in the Cloud. For example, this design or deployment model might not suit healthcare. Then, we have integrated protection with a single platform for routing and security at the branch. This deployment model is widespread, and we will examine a use case soon.
**Regional Hub**
A final deployment model would be the regional hub design. We have a co-location or carrier-neutral facility (CNF) where the security functions are virtual network functions (VNFs) at the regional collection hub. I have seen similar architecture with a SASE deployment and segment routing between the regional hubs.
Recap: WAN Challenges
First, before we delve into these main areas, let me quickly recap the WAN challenges. We had many sites connected to the MPLS site without a single pane of glass. With many locations, you could not see or troubleshoot, and it could be the case that one application was taking up all the bandwidth.
A. Challenge: – **Visibility**
Visibility was a big problem; any gaps in visibility would affect your security. In addition, there needed to be more application awareness, which resulted in complex operations, and a DIY approach to application optimization and WAN virtualization resulted in fragmented security.
SD-WAN solves all the challenges by giving you an approach to centrally provisioning, managing, monitoring, and troubleshooting the WAN edges. So, SD-WAN is not a single VM; it is an array of technologies grouped under the umbrella of SD-WAN. As a result, it increases application performance over the WAN while offering security and data integrity.
B. Challenge: – **Identities & Identity Types**
So, we have users, devices, and things, and we no longer have one type of host to deal with. We have many identities and identity types. One person may have several devices that need an IP connection to communicate with applications hosted in the primary data center, IaaS, or SaaS.
C. Challenge: – **Useful Telemetry**
IP connectivity must be done securely and on a scale while gaining good telemetry. We know the network edges send a wealth of helpful information or telemetry. We can predict or know that you need to upgrade specific paths, which helps monitor traffic patterns and make predictions. Of course, all this needs to operate over a security infrastructure.
SD-WAN security is extensive and encompasses a variety of factors. However, it falls into two main categories. First, we have the security infrastructure category, which secures the control and data plane.
D. Challenge: – **DIA Security**
Then, we have the DIA side of things, where we need to deploy several security functions, such as intrusion prevention, URL filtering, and an application-aware firewall. SD-WAN can be integrated with SASE for DNS-layer filtering. The Cisco version of SASE is Cisco Umbrella.
Now, we need to have layers of security known as the defense-in-depth approach, and DNS-layer filtering is one of the most critical layers, if not the first layer of defense. Everything that wants IP connectivity has to perform a DNS request, so it’s an excellent place to start.
Cisco SD-WAN Security Features
**Secure the SD-WAN Infrastructure**
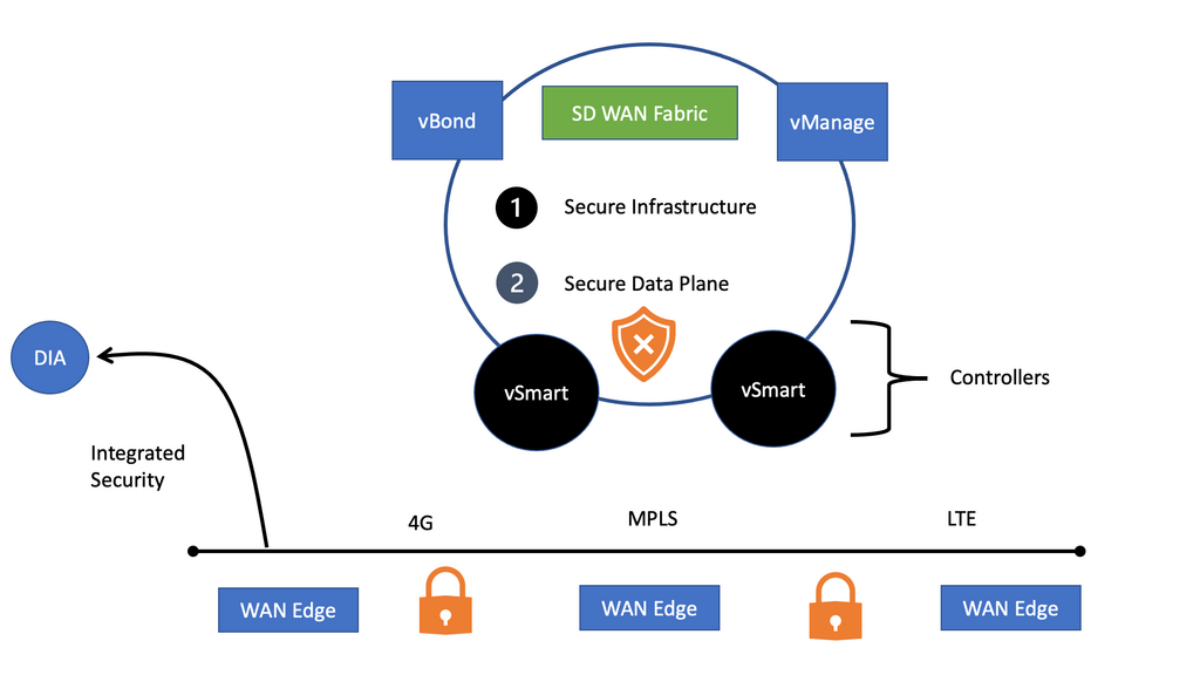
The SD-WAN infrastructure builds the SD-WAN fabric. Consider a material a mesh of connectivity that can take on different topologies. We have several SD-WAN components that can reside in the Cloud or on-premise. These components are the Cisco vBond, vAnalytics, vManage, and vSmart controllers. Of course, whether you are cloud-ready depends on whether you have these components on the Cloud or on-premises.
SD-WAN vBond
The Cisco vBond is the orchestration plane and orchestrates the control and management plane. The Cisco vBond is the entry into the network and is the first point of authentication. So if you pass authentication, the vBond will tell the WAN Edge device that is trying to come online in the fabric who they need to communicate in the Cloud or on-premises, depending on the design, to build a control plane and data plane and get into the fabric securely.
Essentially, the vBond distributes connectivity information of the vManage/vSmarts to all WAN edge routers.
The Cisco vBond also acts as a STUN server, allowing you to circumvent different types of Network Address Translation (NAT). There are different types of NAT, and we need a unit or device that can be aware of NAT and tell the WAN edge devices that this is your real IP and port. This way, when you build the control information, you ensure you have the correct address.
The Cisco vSmart
The Cisco vSmart is the brain of the solution and facilitates fabric discovery. It performs policy, routes, and key exchange. In addition, all the WAN edge devices, physical or virtual, will build connectivity to multiple vSmart controllers in different regions for redundancy.
So, the vSmart acts as a dissemination point that distributes data plane and application-aware routing policies to the WAN edge routers. It’s like an enhanced BGP route reflector (RR) but reflects much more than routes, such as policy, control, and security information. This drastically reduces complexity and offers a highly resilient architecture.
These devices connect to the control plane security with TLS or DTLS tunneling. You can choose this when you set up your SD-WAN. All of this is configured via vManage.
Data Plane Security
Then, we have the data plane—physical or virtual—known as your WAN edge, which is responsible for moving packets. It no longer has to deal with the complexity of a control pane on the WAN side, such as BGP configurations and maintaining peering relationships. Of course, it would help if you still had a control pane on the LAN site, such as route learning via OSPF. But on the WAN side, all the complex peerings have been pushed into the vSmart controllers.
The WAN edge device establishes DLTS or TLS tunnels to the SD-WAN control plane, which consists of the vSmart controllers. In addition to the DTLS and TLS tunnel, the WAN edge creates a secure control plane with the vSmarts and Cisco’s purpose-built Overlay Management Protocol (OMP).
OMP is the enhanced routing protocol for SD-WAN. You can add many extensions to OMP to enhance the SD-WAN fabric. It is much more intelligent than a standard routing protocol.
Cisco vManage
vManage is the UI you can use for Day 0, Day 1, and Day 2 operations. All policies, routing, and QoS security are configured in vManage. Then, vManage pushes this directly to the WAN edge or the vSmart. It depends on what you are looking for.
If you reconfigure a box, such as an IP address, this could be pushed down directly to the box with NETCONF; however, changing the policy to a remote site does not get pushed down via the vManage. So, in the case of advanced configurations, the vSmart will carry out some path calculation and push this down in a state mode to the WAN Edge.
Device Identity
We have started to secure the fabric, and everything is encrypted for the control plane. But before we get into the data plane security, we must look at physical security. So here, we need to address device and software authentication. How can you authenticate a Cisco device and make sure that Cisco OS runs on that device? Unfortunately, many counterfeit devices are produced, but those, when booted up, will not even load.
In the past, many vulnerabilities were found in the IOS classic routes. We had, for example, runtime infection and static infection. Someone could access the devices and modify them for all of these to be successful. With some vulnerabilities, it contacted C&C servers when the router came online. So, Malware in IOS is a real threat. There was a security breach that affected the line cards.
However, now Cisco authenticates Cisco hardware and software with Cisco Trust Anchor modules. We also need to secure the OS with Cisco Secure Boot.
Secure Control Plane
We have taken the burden from the WAN edge router. The traditional WAN had integrated control and data plane where we had high complexity, limited scale, and path selection. So, even if you use DMVPN, you still carry out the routing, such as EIGRP or OSPF. So you are not saved from this. We will have the IKE and routing components with DMVPN. IKE in large environments is hard to scale. .
With SD-WAN, we have a network-wide control pane that is different from that of DMVPN. Moreover, as the WAN edge has secure and authenticated connectivity to the vSmart controllers, we can use the vSmart controllers to remove the complexity, especially for central key rotation. So now, with SD-WAN, you can have IKE-less architecture.
So you only need a single peering to the vSmart, which allows you to scale horizontally. On top of this, we have OMP. It was designed from the ground up to be very extensive and to carry values that mean something to SD-WAN. It is not just used to replace a routing protocol; it can do much more than have IP prefixes. It can take the keys, policy information, service insertion, and multicast node information.
The TLOC
It is also distributed, allowing edge devices to provide their identity in the fabric. We have TLOC that will enable you to build a fabric. The TLOC allows you to make any network design you wish. The TLOC is a transport locator with a unique WAN fabric identity. The TLOC is on every box, composed of system IP, color, or label for the transport and the encapsulation ( IPsec and GRE ). Now, we can make a differential on every box, and you can have much more control. You can carry all the TLOC and sub information in the OMP peerings.
Once the TLOC is advertised to the vSmart controllers, the vSmart advertises it to the WAN edges. In this case, we have a full mesh, but you can limit who can learn the TLOC or block it to build a hub-and-spoke topology.
You can change the next hop of a TLOC to change where a route is advertised. In the past, changing BGP on a wide scale was challenging as it was box by box, but now, we can quickly build the topology with SD-WAN.
Secure Data Plane
So we have secure connectivity from their WAN edge to the vSmart. We have an OMP that runs inside secure DLTS/TLS tunnels. And this is all dynamic. The OMP session to the Smart to the WAN edge can get the required information, such as TLOC and security keys. Then, the WAN edge devices can build an IPsec tunnel to each other, and this is not just standard IPsec but UDP-based IPsec. The UDP-based IPsec tunnels between two boxes allow tunnels over multiple types of transport. The transport and fabric are now agnostic.
We still have route learning on the LAN side, and this route is placed into a VPN, just like a VRF. So this is new reachability information learned from the LAN and sent as an OMP update to the vSmart. The vSmart acts as a route reflector and reflects this information. The vSmart makes all the path decisions for the network.
If you want to manipulate the path information, you can do this in the vSmart controller. So you can choose your preferred transports or change the next hop from the controller without any box-by-box configuration.
Direct Internet Access
Next, let us examine direct internet access. So, for direct access, we need to meet several use cases. The primary use case is PCI compliance, so before the packet leaves the branch, it needs to be inspected with a stateful firewall and an IPS solution. The SD-WAN enterprise firewall is application-aware, and we have IPS integrated with SD-WAN that can solve this use case.
Then, we have a guest access use case, where guests work in a branch office. We need content filtering for these guests, too. SD-WAN can run URL filtering that can be used here, as well as a direct cloud access use case. So we want to provide optimal performance to employee traffic but select and choose applications and send them directly from the branch to the Cloud and other applications to the HQ. Again, the DNS web layer security would be helpful here.
So the main features, enterprise firewall, URL filtering, and IPS, are on the box, with the DNS layer filtering being a cloud feature with Cisco Umbrella. This provides complete edge security and does not need a two-box solution, except for the additional Cisco Umbrella, a cloud-native solution dispersed around the globe with security functions delivered from PoPs.
Example of a Cisco device or VNF
One way to consume Cisco SD-WAN security is by leveraging Cisco’s integrated security applications within a rich portfolio of powerful WAN Edge routers, such as the ISR4000 series. On top of the native application-aware stateful firewall, these WAN Edge routers can dedicate compute resources to application service containers running within IOS-XE to enable in-line IDS/IPS, URL filtering, and Advanced Malware Protection (AMP).
Remember, Cisco SD-WAN security can also be consumed through cloud services or regional hubs where VNF-based security chains may be leveraged, or robust security stacks may already exist.
Summary: SD WAN Security
In today’s digital landscape, organizations increasingly adopt Software-Defined Wide Area Network (SD-WAN) solutions to enhance their network connectivity and performance. However, with the growing reliance on SD-WAN, ensuring robust security measures becomes paramount. This blog post explored key considerations and best practices to ensure secure SD-WAN deployments.
Understanding the Basics of SD-WAN
SD-WAN brings flexibility and efficiency to network management by leveraging software-defined networking principles. It allows organizations to establish secure and scalable connections across multiple locations, optimizing traffic flow and reducing costs.
Recognizing the Security Challenges
While SD-WAN offers numerous benefits, it also introduces new security challenges. One key concern is the increased attack surface due to integrating public and private networks. Organizations must be aware of potential vulnerabilities and implement adequate security measures.
Implementing Layered Security Measures
To fortify SD-WAN deployments, a layered security approach is crucial. This includes implementing next-generation firewalls, intrusion detection and prevention systems, secure web gateways, and robust encryption protocols. It is also important to regularly update and patch security devices to mitigate emerging threats.
Strengthening Access Controls
Access control is a vital aspect of SD-WAN security. Organizations should enforce robust authentication mechanisms, such as multi-factor authentication, and implement granular access policies based on user roles and privileges. Additionally, implementing secure SD-WAN edge devices with built-in security features can enhance access control.
Monitoring and Incident Response
Continuous monitoring of SD-WAN traffic is essential for detecting and responding promptly to security incidents. Deploying security information and event management (SIEM) solutions can provide real-time visibility into network activities, enabling rapid threat identification and response.
Conclusion
In conclusion, securing SD-WAN deployments is a critical aspect of maintaining a resilient and protected network infrastructure. By understanding the basics of SD-WAN, recognizing security challenges, implementing layered security measures, strengthening access controls, and adopting proactive monitoring and incident response strategies, organizations can ensure a robust and secure SD-WAN environment.
- DMVPN - May 20, 2023
- Computer Networking: Building a Strong Foundation for Success - April 7, 2023
- eBOOK – SASE Capabilities - April 6, 2023