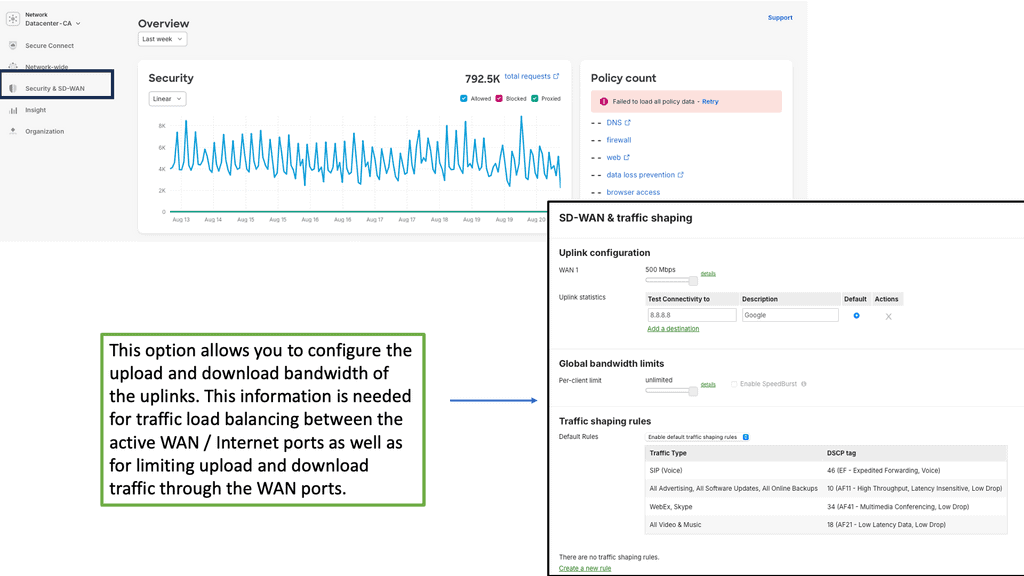
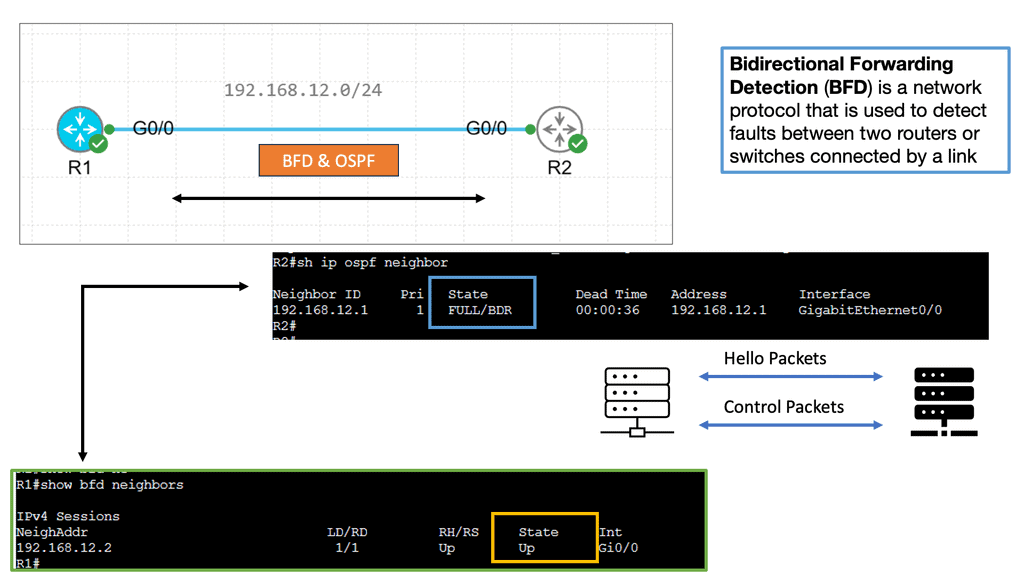
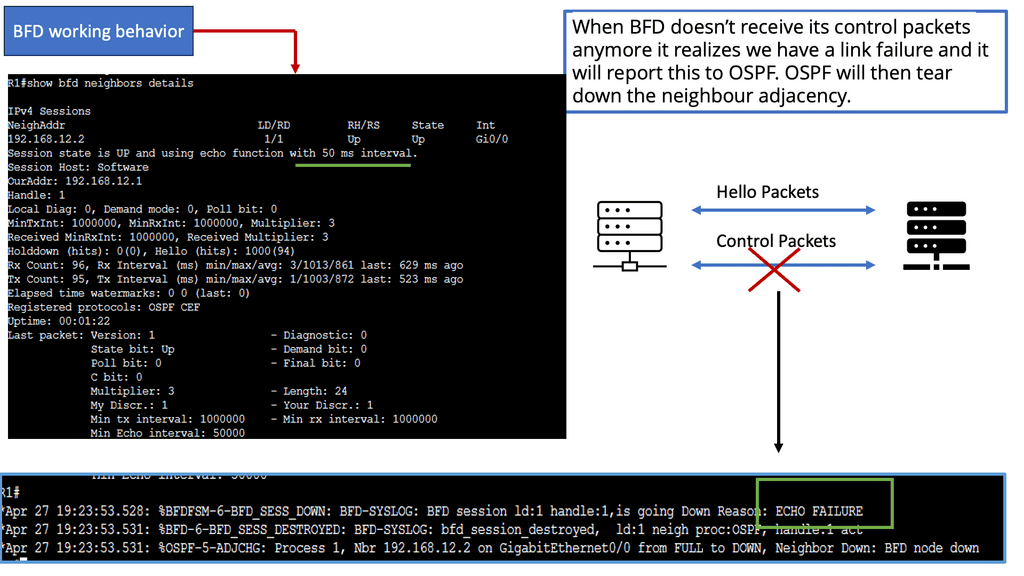
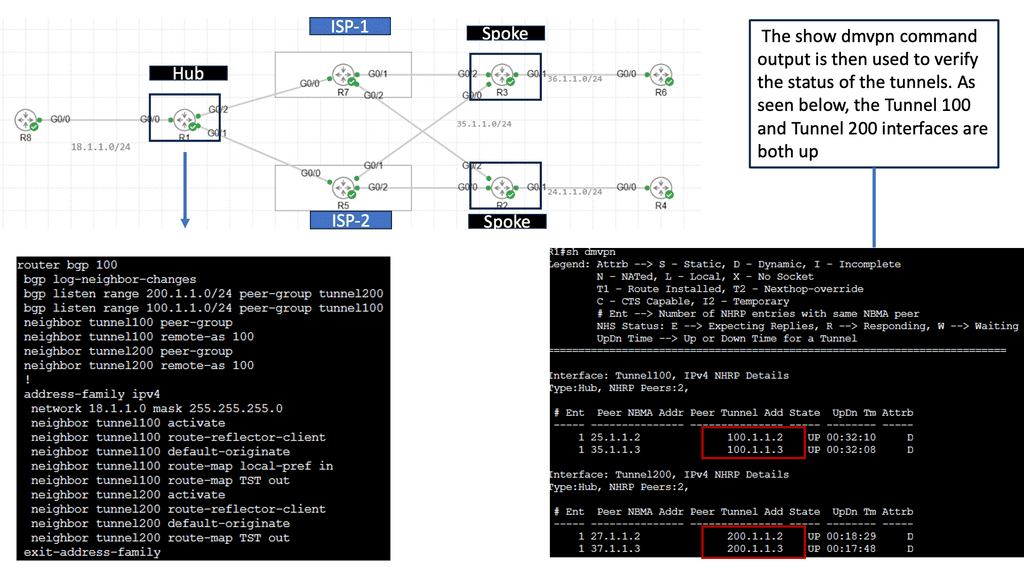
SD WAN Tutorial
In the ever-evolving landscape of networking technology, SD-WAN has emerged as a powerful solution that revolutionizes the way businesses connect and operate. This blog post delves into the world of SD-WAN, exploring its key features, benefits, and the impact it has on modern networks.
SD-WAN, which stands for Software-Defined Wide Area Networking, is a technology that simplifies the management and operation of a wide area network. By separating the network hardware from its control mechanism, SD-WAN enables businesses to have more flexibility and control over their network infrastructure. Unlike traditional WAN setups, SD-WAN utilizes software to intelligently route traffic across multiple connection types, optimizing performance and enhancing security.
One of the fundamental features of SD-WAN is its ability to provide centralized network management. This means that network administrators can easily configure and monitor the entire network from a single interface, streamlining operations and reducing complexity. Additionally, SD-WAN offers dynamic path selection, allowing traffic to be routed based on real-time conditions, such as latency, congestion, and link availability. This dynamic routing capability ensures optimal performance and resilience.
Another significant benefit of SD-WAN is its ability to support multiple connection types, including MPLS, broadband, and cellular networks. This enhances network reliability and scalability, as businesses can leverage multiple connections to avoid single points of failure and accommodate growing bandwidth demands. Moreover, SD-WAN solutions often incorporate advanced security features, such as encryption and segmentation, ensuring data integrity and protecting against cyber threats.?
SD-WAN has had a profound impact on modern networks, empowering businesses with greater agility and cost-efficiency. With the rise of cloud computing and the increasing adoption of SaaS applications, traditional network architectures were often unable to provide the necessary performance and reliability. SD-WAN addresses these challenges by enabling direct and secure access to cloud resources, eliminating the need for backhauling traffic to a central data center.
Furthermore, SD-WAN enhances network visibility and control, allowing businesses to prioritize critical applications, apply Quality of Service (QoS) policies, and optimize bandwidth utilization. This level of granular control ensures that essential business applications receive the required resources, enhancing user experience and productivity. Additionally, SD-WAN simplifies network deployments, making it easier for organizations to expand their networks, open new branches, and integrate acquisitions seamlessly.
SD-WAN represents a significant evolution in networking technology, offering businesses a comprehensive solution to modern connectivity challenges. With its centralized management, dynamic path selection, and support for multiple connection types, SD-WAN empowers organizations to build robust, secure, and agile networks. As businesses continue to embrace digital transformation, SD-WAN is poised to play a pivotal role in shaping the future of networking.Matt Conran
Highlights: SD WAN Tutorial
Network Abstraction
– In an era where digital transformation is no longer a luxury but a necessity, businesses are constantly looking for ways to optimize their network infrastructure.
Enter Software-Defined Wide Area Networking (SD-WAN), a revolutionary technology that is transforming how organizations approach WAN architecture.
– SD-WAN is not just a buzzword; it is a robust solution designed to simplify the management and operation of a WAN by decoupling the networking hardware from its control mechanism.
### The Basics of SD-WAN Technology
At its core, SD-WAN is a virtualized WAN architecture that allows enterprises to leverage any combination of transport services, including MPLS, LTE, and broadband internet services, to securely connect users to applications.
Unlike traditional WANs, which require proprietary hardware and complex configurations, SD-WAN uses a centralized control function to direct traffic across the WAN, increasing application performance and delivering a high-quality user experience. This separation of the data plane from the control plane is what makes SD-WAN a game-changer in the world of networking.
### WAN Virtualization: The Heart of SD-WAN
WAN virtualization is a critical component of SD-WAN. It abstracts the underlying network infrastructure, creating a virtual overlay that provides seamless connectivity across different network types. This virtualization enables businesses to manage network traffic more effectively, prioritize critical applications, and ensure reliable performance irrespective of the physical network.
With WAN virtualization, businesses can rapidly deploy new applications and services, respond to changes in network conditions, and optimize bandwidth usage without costly hardware upgrades.
### Benefits of Adopting SD-WAN
The benefits of adopting SD-WAN are manifold. Firstly, it offers cost savings by reducing the need for expensive MPLS circuits and allowing the use of more cost-effective broadband connections. Secondly, it provides enhanced security through integrated encryption and advanced threat protection. Additionally, SD-WAN simplifies network management by providing a centralized dashboard that offers visibility into network traffic and performance. This simplification leads to improved agility, allowing IT teams to deploy and manage applications with greater speed and efficiency.
### The Future of Networking with SD-WAN
As businesses continue to embrace cloud services and remote work becomes increasingly prevalent, the demand for flexible, scalable, and secure networking solutions will only grow. SD-WAN is well-positioned to meet these demands, offering a future-proof solution that can adapt to the ever-changing landscape of enterprise networking. With its ability to integrate with cloud platforms and support IoT deployments, SD-WAN is paving the way for the next generation of network connectivity.
Picture This: Personal Note –
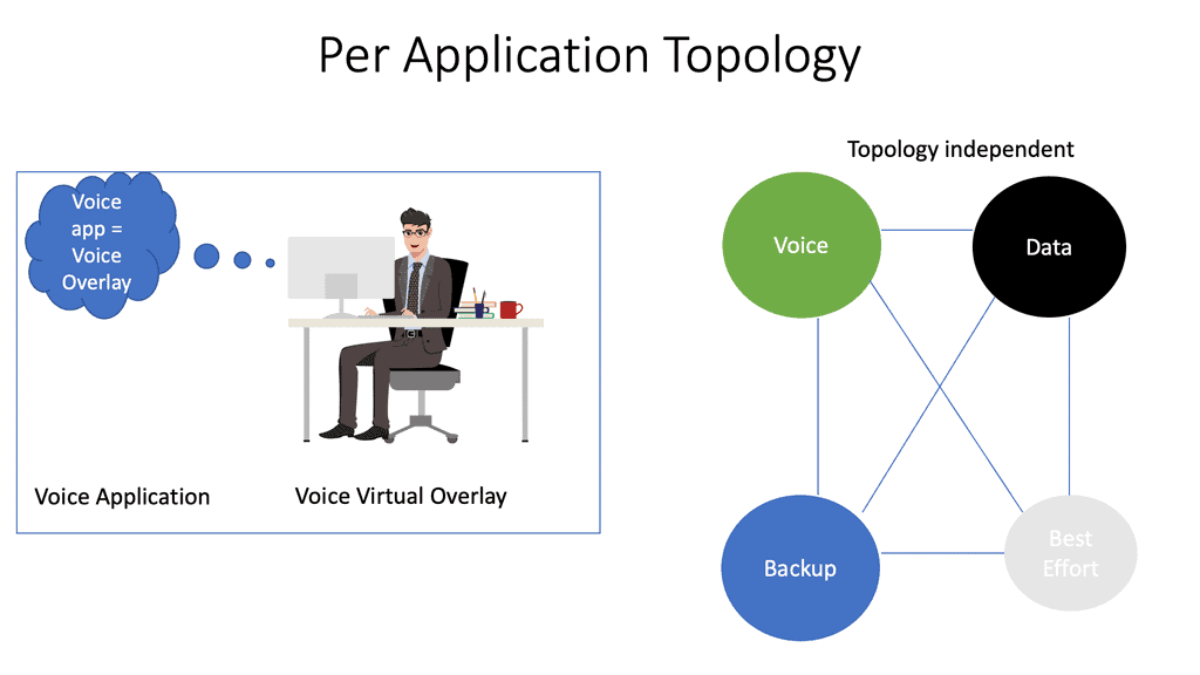
Now imagine these virtual WANs individually holding a single application running over the WAN, but consider them end-to-end instead of being in one location, i.e., on a server. The individual WAN runs to the cloud or enterprise location, having secure, isolated paths with different policies and topologies. Wide Area Network (WAN) virtualization is an emerging technology revolutionizing how networks are designed and managed.
Note: WAN virtualization allows for decoupling the physical network infrastructure from the logical network, enabling the same physical infrastructure for multiple logical networks. It allows organizations to utilize a single physical infrastructure to create multiple virtual networks, each with unique characteristics. WAN virtualization is a core requirement enabling SD-WAN.
SD WAN Overlay & Underlay Design
This SD-WAN tutorial will address the SD-WAN vendor’s approach to an underlay and an overlay, including the SD-WAN requirements. The underlay consists of the physical or virtual infrastructure and the overlay network, the SD WAN overlay to which the applications are mapped.
SD-WAN solutions are designed to provide secure, reliable, and high-performance connectivity across multiple locations and networks. Organizations can manage their network configurations, policies, and security infrastructure with SD-WAN.
In addition, SD-WAN solutions can be deployed over any type of existing WAN infrastructure, such as MPLS, Frame Relay, and more. SD-WAN offers enhanced security features like encryption, authentication, and access control. This ensures that data is secure and confidential and that only authorized users can access the network.
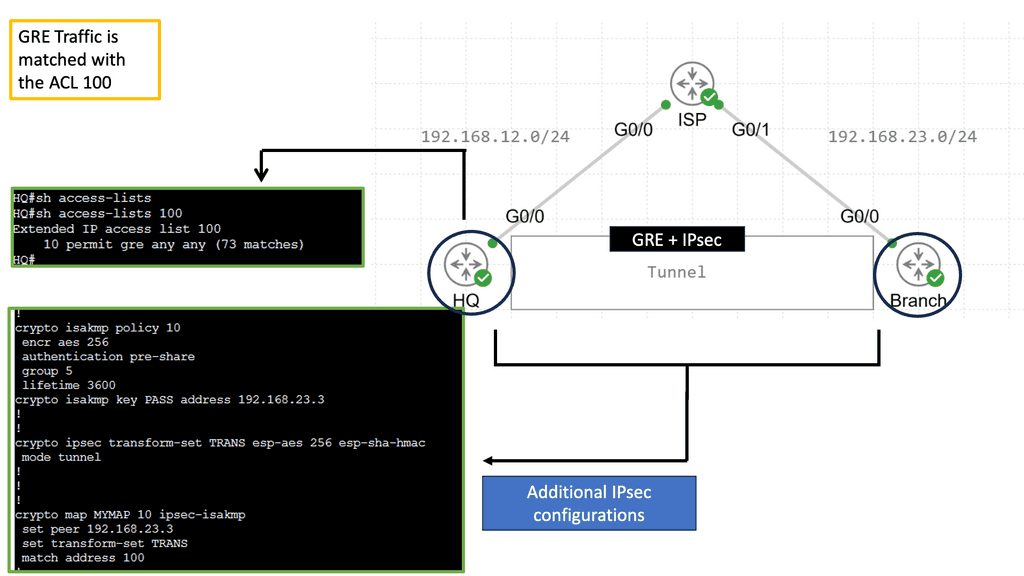
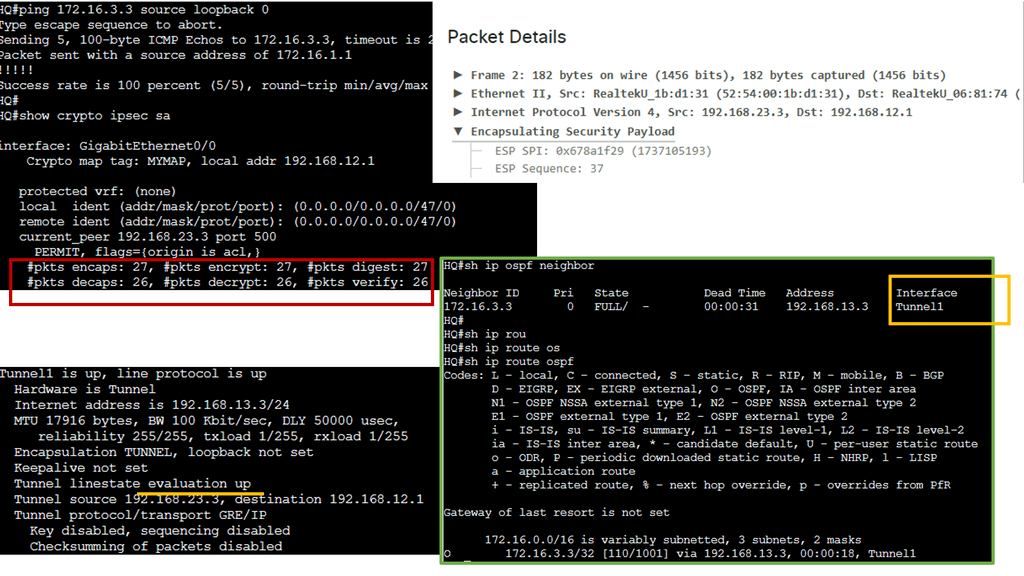
Example Technology: GRE Overlay with IPsec
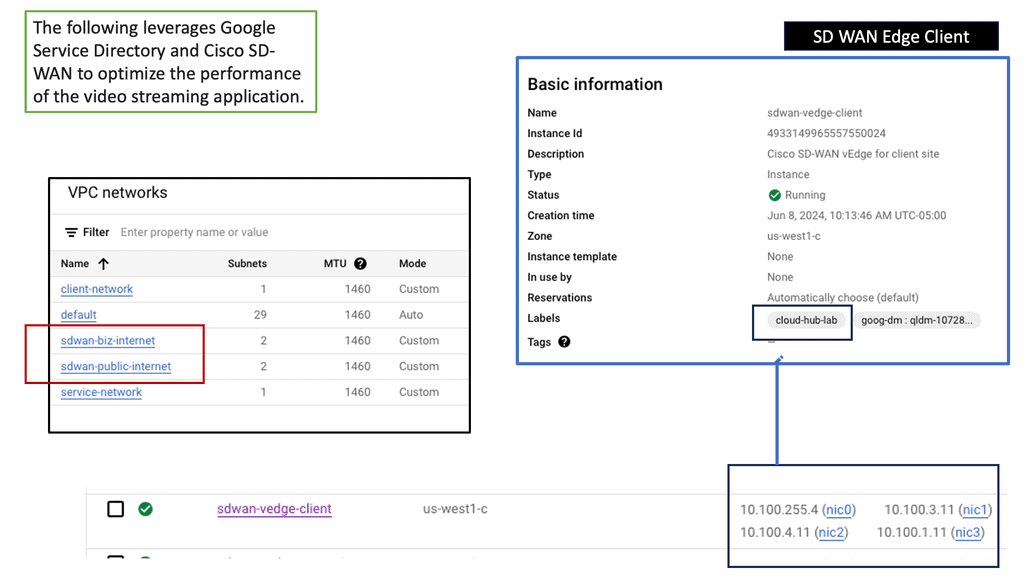
Google SD WAN Cloud Hub
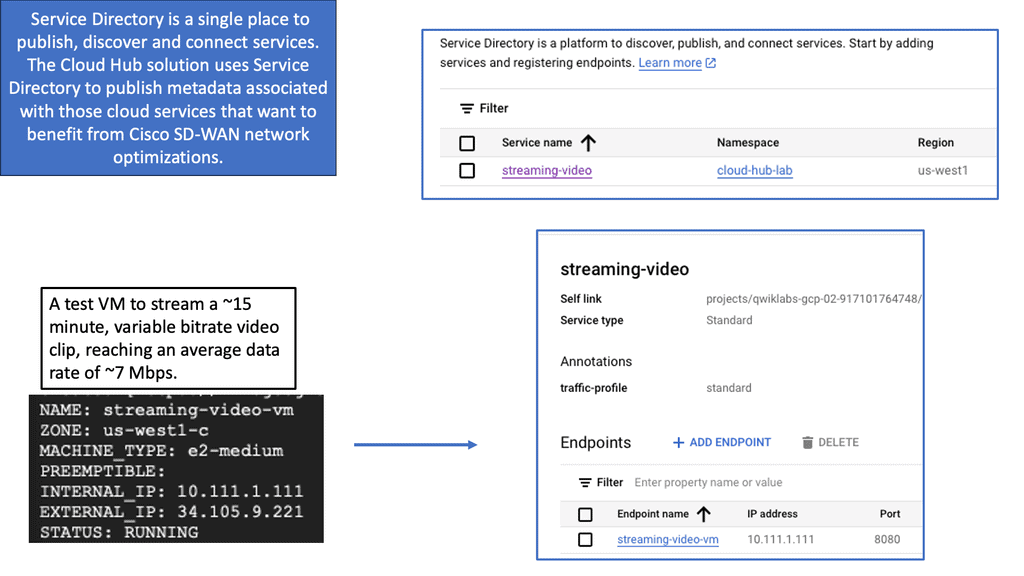
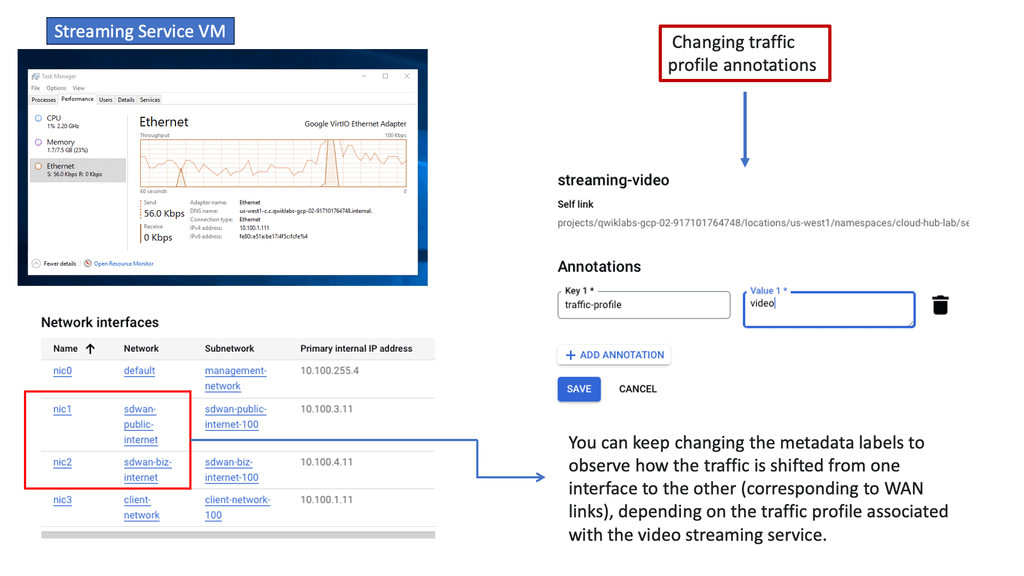
The integration of SD-WAN with Google Cloud takes connectivity to new heights. By deploying an SD-WAN Cloud Hub, businesses can seamlessly connect their branch networks to the cloud, leveraging the power of Google Cloud’s infrastructure.
This enables organizations to optimize network performance, reduce latency, and enhance overall user experience. The centralized management capabilities of SD-WAN further simplify network operations, allowing businesses to efficiently control traffic routing, prioritize critical applications, and ensure maximum uptime.
Seamless Integration
One of the standout aspects of SD-WAN Cloud Hub is its seamless integration with Google Cloud. Organizations can extend their on-premises network to Google Cloud, enabling them to leverage Google Cloud’s extensive services and resources. This integration empowers businesses to adopt a hybrid cloud strategy, seamlessly connecting their on-premises infrastructure with the scalability and flexibility of Google Cloud.
SD-WAN Enables
A) Performance-Based Routing
Performance-based routing is a dynamic routing technique that selects the best path for data transmission based on real-time performance metrics. Unlike traditional routing protocols that solely consider static factors like hop count, performance-based routing considers parameters such as latency, packet loss, and bandwidth availability.
-Enhanced Network Performance: Performance-based routing minimizes latency and packet loss by dynamically selecting the optimal path, improving overall network performance. This leads to faster data transfer speeds and better user experiences for applications and services.
-Efficient Bandwidth Utilization: Performance-based routing intelligently allocates network resources by diverting traffic to less congested routes. This ensures that available bandwidth is utilized optimally, preventing bottlenecks and congestion in the network.
-Redundancy and Failover: Another advantage of performance-based routing is its ability to provide built-in redundancy and failover mechanisms. By constantly monitoring performance metrics, it can automatically reroute traffic when a network link or node fails, ensuring uninterrupted connectivity.
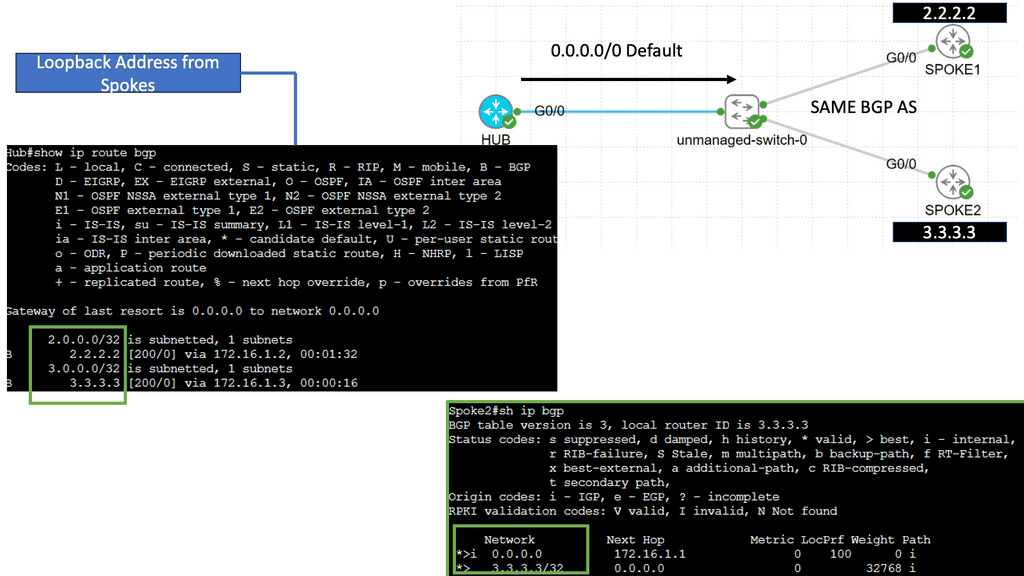
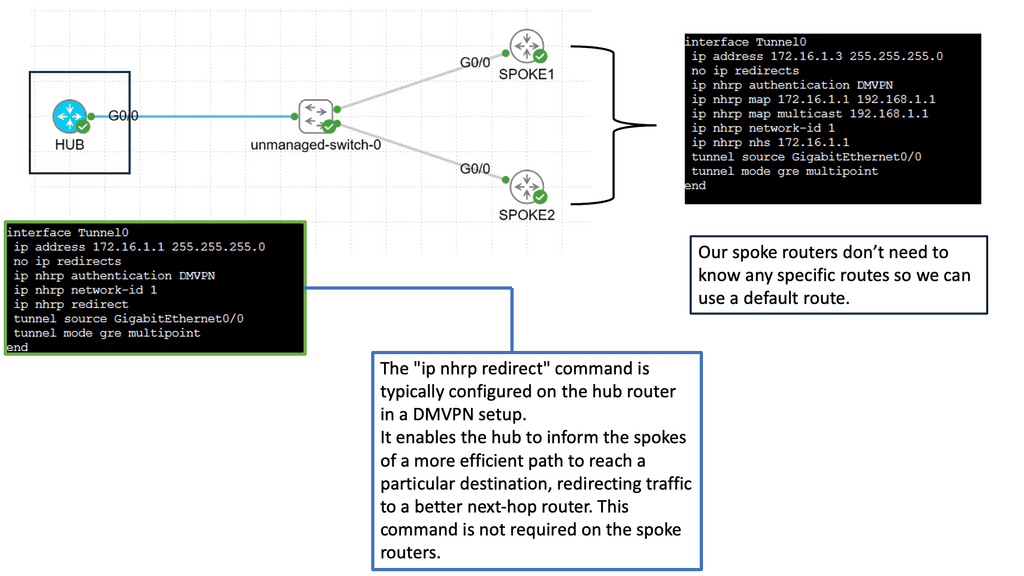
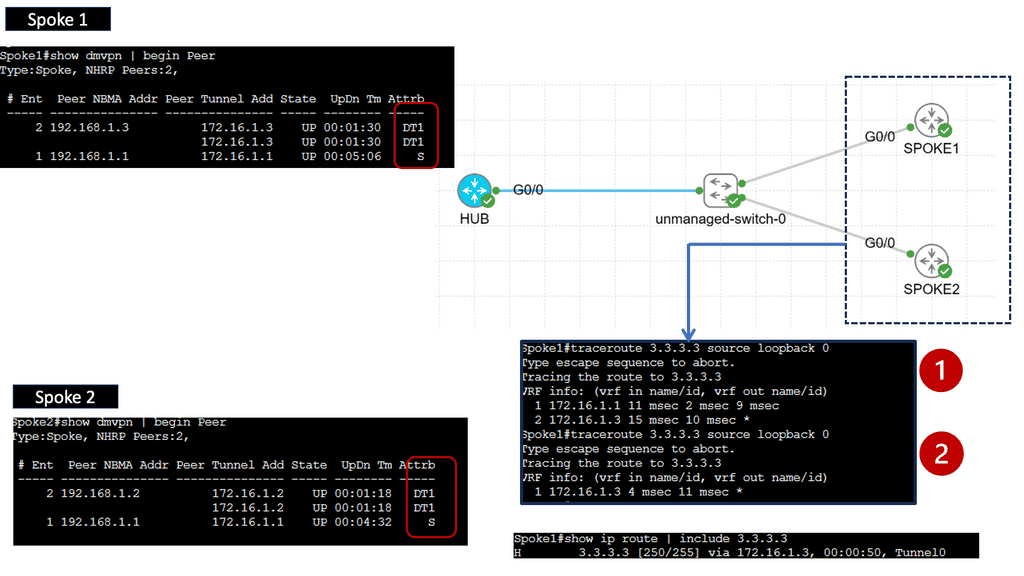
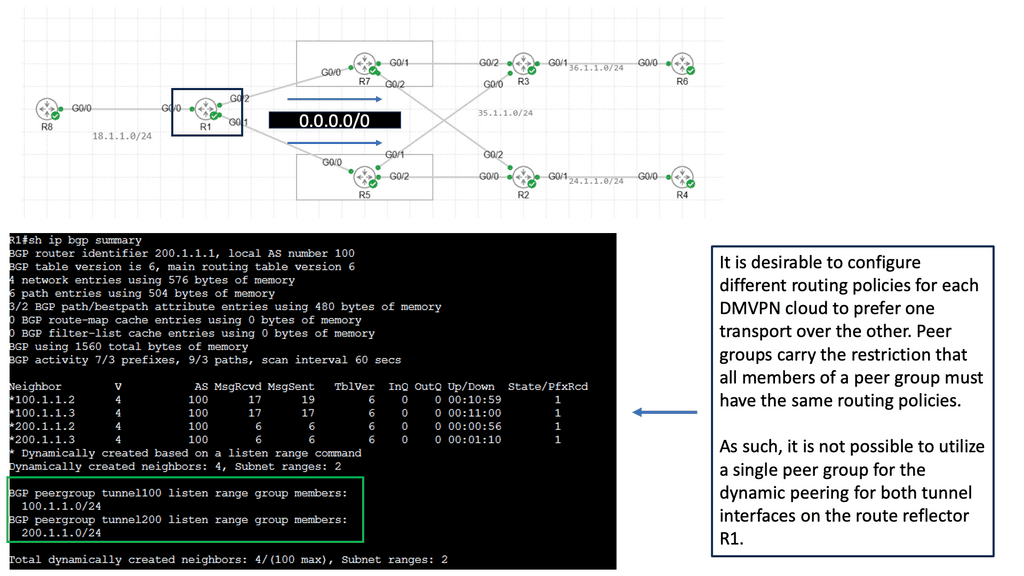
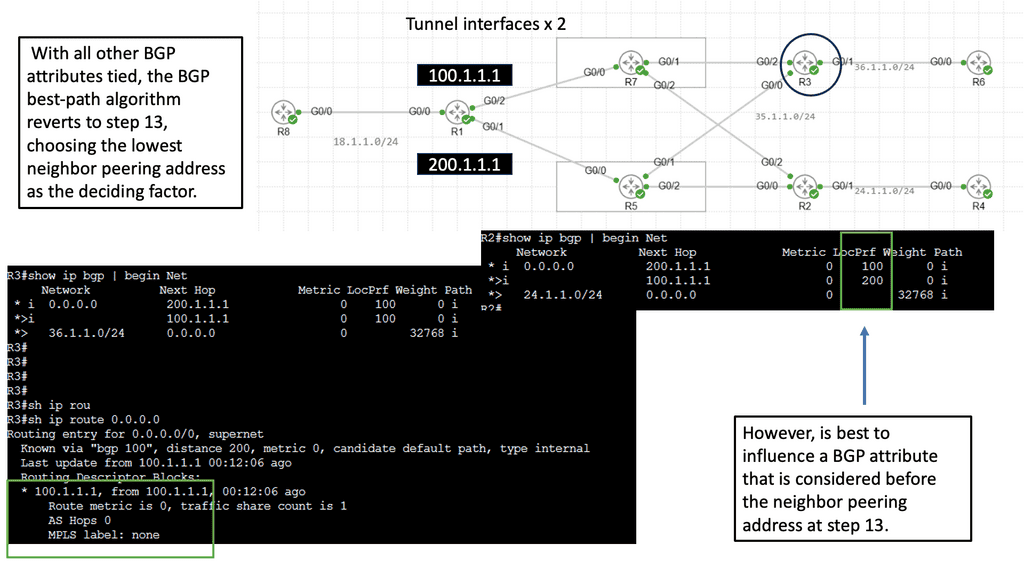
B) Understanding DMVPN Phase 3
DMVPN Phase 3 is an advanced networking solution that provides scalable and efficient connectivity for organizations with distributed networks. Unlike its predecessors, DMVPN Phase 3 introduces the concept of Spokes connecting directly with each other, eliminating the need for traffic to traverse through the Hub. This dynamic spoke-to-spoke tunneling architecture enhances network performance and reduces latency, making it an ideal choice for modern network infrastructures.
DMVPN Phase 3 offers many advantages for organizations seeking streamlined network connectivity. First, it provides enhanced scalability, allowing for easy addition or removal of spokes without impacting the overall network. Additionally, direct spoke-to-spoke communication reduces the dependency on the Hub, resulting in improved network resiliency and reduced bandwidth consumption. Moreover, DMVPN Phase 3 supports dynamic routing protocols, enabling efficient and automated network management.
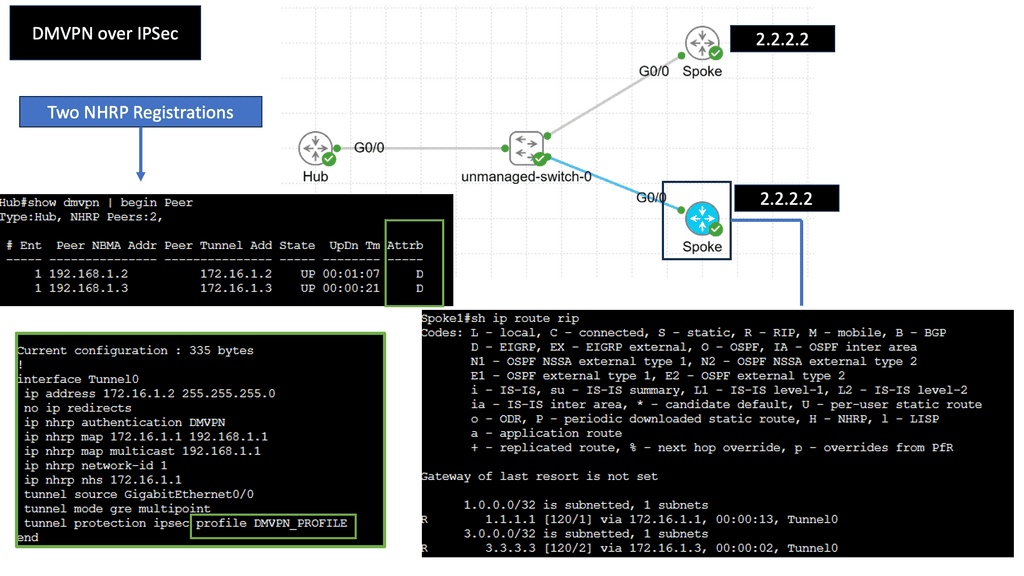
C) Securing DMVPN with IPSec
DMVPN is a Cisco proprietary solution that simplifies the deployment of VPN networks, offering scalability, flexibility, and ease of management. It utilizes multipoint GRE tunnels to establish secure connections between multiple sites, creating a virtual mesh network. This architecture eliminates the need for point-to-point tunnels between every site, reducing overhead and enhancing scalability.
IPsec, short for Internet Protocol Security, is a widely used protocol suite that provides secure communication over IP networks. With features like authentication, encryption, and data integrity, IPsec ensures confidentiality and integrity of data transmitted over the network. When combined with DMVPN, IPsec adds an additional layer of security to the virtual network, safeguarding sensitive information from unauthorized access.
DMVPN over IPsec offers numerous advantages for organizations. Firstly, it enables dynamic and on-demand connectivity, adding new sites seamlessly without manual configuration. This scalability reduces administrative overhead and streamlines network expansion. Secondly, DMVPN over IPsec provides enhanced security, ensuring that data remains confidential and protected from potential threats. Lastly, it improves network performance by leveraging multipoint connectivity, optimizing bandwidth usage, and reducing latency.
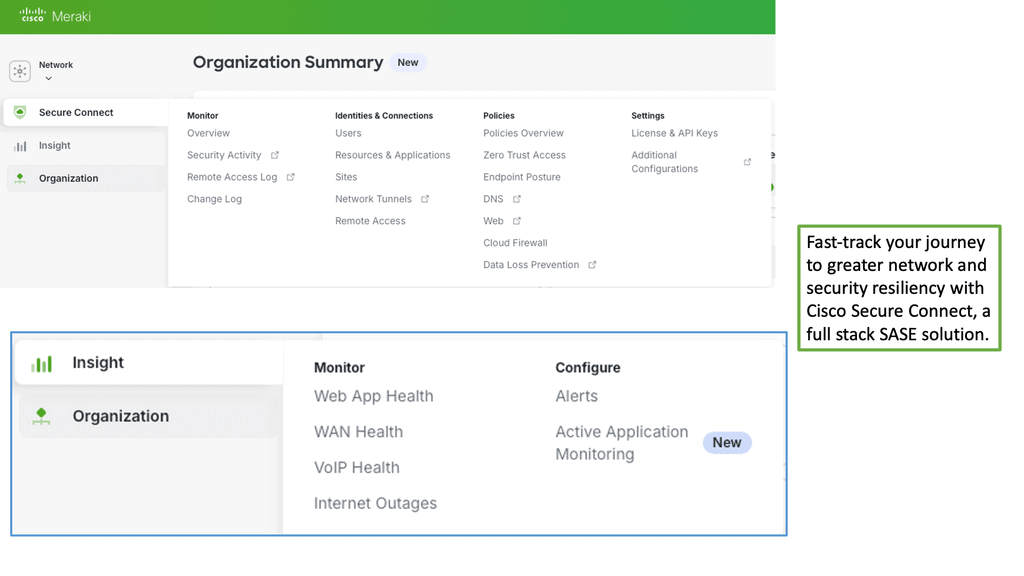
Example Product: Cisco Meraki
### Centralized Management
One of the standout features of the Cisco Meraki platform is its centralized management system. Gone are the days of configuring each device individually. With Meraki, all your network devices can be managed from a single, intuitive dashboard. This not only simplifies the administration process but also ensures that your network remains consistent and secure. The centralized dashboard provides real-time monitoring, configuration, and troubleshooting capabilities, allowing IT administrators to manage their entire network with ease and efficiency.
### Robust Security Features
Security is a top priority for any network, and Cisco Meraki excels in this area. The platform offers a comprehensive suite of security features designed to protect your network from a wide range of threats. Built-in firewall, intrusion detection, and prevention systems work seamlessly to safeguard your data. Additionally, Meraki’s advanced malware protection and content filtering ensure that harmful content is kept at bay. With automatic firmware updates, your network is always protected against the latest vulnerabilities, giving you peace of mind.
### Unparalleled Scalability
As your business grows, so does your network. Cisco Meraki is designed to scale effortlessly with your organization. Whether you are managing a small business or a large enterprise, Meraki’s cloud-based architecture allows you to add new devices and locations without the need for complex configurations or costly hardware investments. The platform supports a wide range of devices, including switches, routers, access points, and security cameras, all of which can be easily integrated into your existing network.
### Seamless Integration and Automation
Integration and automation are key to streamlining network management, and Cisco Meraki shines in these areas. The platform supports API integrations, allowing you to connect with third-party applications and services. This opens up a world of possibilities for automating routine tasks, such as device provisioning, network monitoring, and reporting. By leveraging these capabilities, businesses can reduce manual workload, minimize errors, and improve overall operational efficiency.
### Enhanced User Experience
User experience is at the heart of the Cisco Meraki platform. The user-friendly dashboard is designed with simplicity in mind, making it accessible even to those with limited technical expertise. Detailed analytics and reporting tools provide valuable insights into network performance, helping administrators make informed decisions. Additionally, the platform’s mobile app allows for on-the-go management, ensuring that your network is always within reach.
Related: Before you proceed, you may find the following posts helpful for pre-information:
SD WAN Tutorial
Transition: The era of client-server
The design for the WAN and branch sites was conceived in the client-server era. At that time, the WAN design satisfies the applications’ needs. Then, applications and data resided behind the central firewall in the on-premises data center. Today, we are in a different space with hybrid IT and multi-cloud designs, making applications and data distribution. Data is now omnipresent. The type of WAN and branch originating in the client-server era was not designed with cloud applications.
Hub and spoke designs:
The “hub and spoke” model was designed for client/server environments where almost all of an organization’s data and applications resided in the data center (i.e., the hub location) and were accessed by workers in branch locations (i.e., the spokes). Internet traffic would enter the enterprise through a single ingress/egress point, typically into the data center, which would then pass through the hub and to the users in branch offices.
Push to the Cloud:
The birth of the cloud resulted in a significant shift in how we consume applications, traffic types, and network topology. There was a big push to the cloud, and almost everything was offered as a SaaS. In addition, the cloud era changed traffic patterns, as traffic goes directly to the cloud from the branch site and doesn’t need to be backhauled to the on-premise data center.
**Challenge: Hub and spoke design**
The hub and spoke model needs to be updated. Because the model is centralized, day-to-day operations may be relatively inflexible, and changes at the hub, even in a single route, may have unexpected consequences throughout the network. It may be difficult or even impossible to handle occasional periods of high demand between two spokes.
The result of the cloud acceleration means that the best access point is only sometimes in the central location. Why would branch sites direct all internet-bound traffic to the central HQ, causing traffic tromboning and adding to latency when it can go directly to the cloud? The hub-and-spoke design could be an efficient topology for cloud-based applications.
**Active/Active and Active/Passive**
Historically, WANs are built on “active-passive,” where a branch can be connected using two or more links, but only the primary link is active and passing traffic. In this scenario, the backup connection only becomes active if the primary connection fails. While this might seem sensible, it could be more efficient.
Interest in active-active routing protocols has always existed, but it was challenging to configure and expensive to implement. In addition, active/active designs with traditional routing protocols are complex to design, inflexible, and a nightmare to troubleshoot.
Convergence & Application Performance:
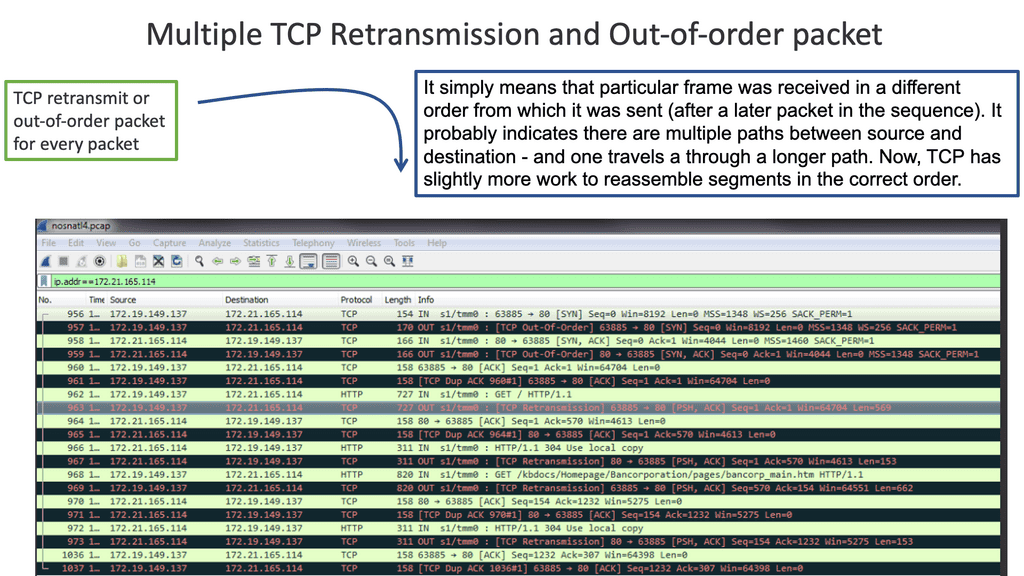
Convergence and application performance problems can arise from active-active WAN edge designs. For example, active-active packets that reach the other end could be out-of-order packets due to each link propagating at different speeds. Also, the remote end has to reassemble, resulting in additional jitter and delay. Both high jitter and delay are bad for network performance.
Packet reordering:
The issues arising from active-active are often known as spray and pray. It increases bandwidth but decreases good output. Spraying packets down both links can result in 20% drops or packet reordering. There will also be firewall issues as they may see asymmetric routes.
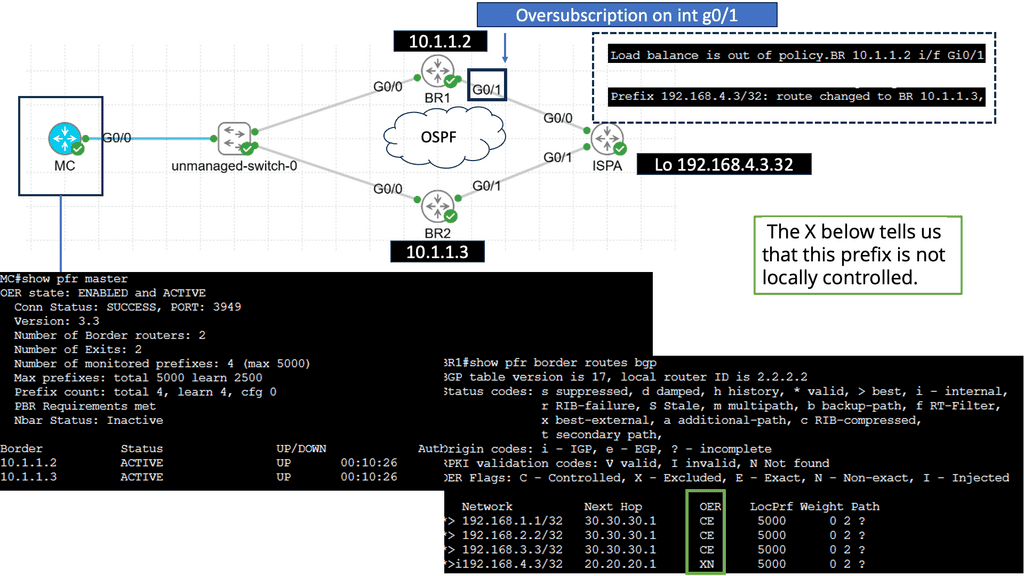
Key SD-WAN Requirements
1: SD-WAN requirement and active-active paths
For an active-active design, one must know the application session and design that eliminates asymmetric routing. In addition, it would help if you slice up the WAN so application flows can work efficiently over either link. SD-WAN does this. Also, WAN designs can be active–standby, which requires routing protocol convergence in the event of primary link failure.
Routing Protocol Convergence
Unfortunately, routing protocols are known to converge slowly. The emergence of SD-WAN technologies with multi-path capabilities combined with the ubiquity of broadband has made active-active highly attractive and something any business can deploy and manage quickly and easily.
SD-WAN solution enables the creation of virtual overlays that bond multiple underlay links. Virtual overlays would allow enterprises to classify and categorize applications based on their unique service level requirements and provide fast failover should an underlay link experience congestion, a brownout, or an outage.
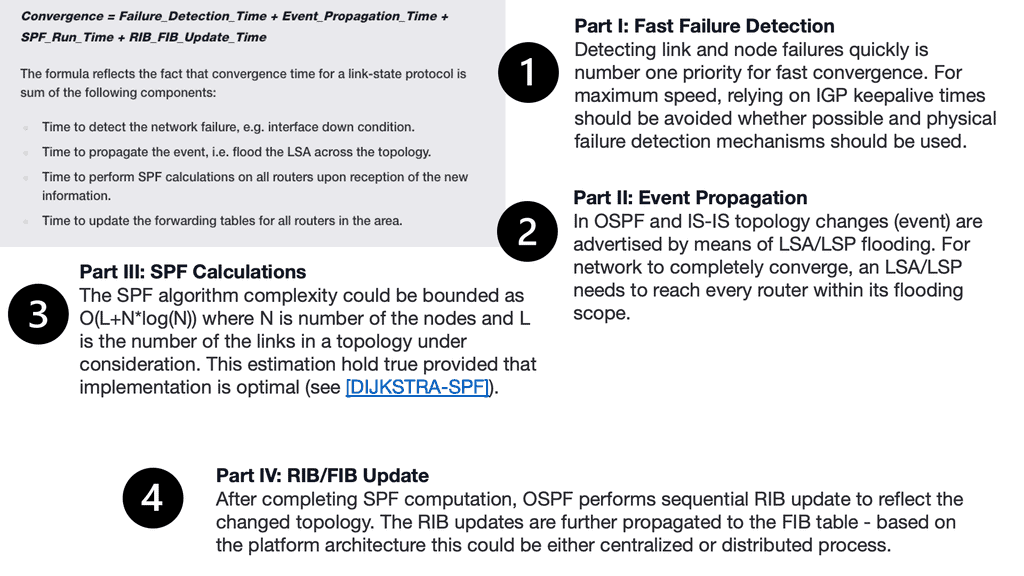
Example: BFD improving convergence
There is traditional routing regardless of the mechanism used to speed up convergence and failure detection. These several convergence steps need to be carried out:
a ) Detecting the topology change,
b ) Notifying the rest of the network about the change,
c ) Calculating the new best path, and
d) switching to the new best path.
Traditional WAN protocols route down one path and, by default, have no awareness of what’s happening at the application level. For this reason, there have been many attempts to enhance Wan’s behavior.

2: SD-WAN requirements: Flexible topologies
For example, using DPI, we can have Voice over IP traffic go over MPLS. Here, the SD-WAN will look at real-time protocol and session initiation protocol. We can also have less critical applications that can go to the Internet. MPLS can be used only for a specific app.
As a result, the best-effort traffic is pinned to the Internet, and only critical apps get an SLA and go on the MPLS path. Now, we better utilize the transports, and circuits never need to be dormant. With SD-WAN, we are using the B/W that you have available to ensure an optimized experience.
The SD-WAN’s value is that the solution tracks network and path conditions in real time, revealing performance issues as they occur. Then, it dynamically redirects data traffic to the following available path.
Then, when the network recovers to its normal state, the SD-WAN solution can redirect the data’s traffic path to its original location. Therefore, the effects of network degradation, such as brownouts and soft failure, can be minimized.
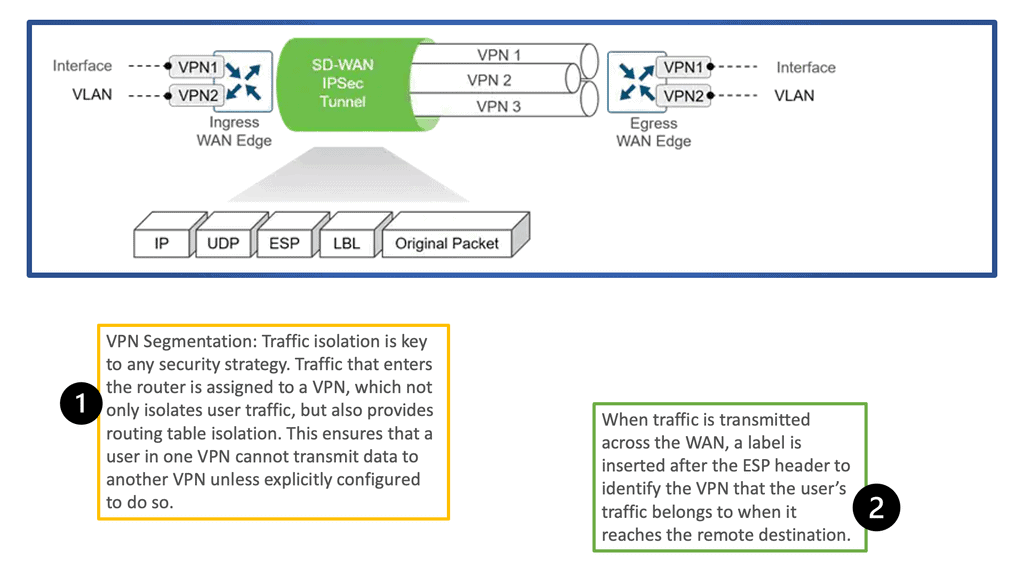
3: SD-WAN requirements: Encryption key rotation
Data security has never been a more important consideration than it is today. Therefore, businesses and other organizations must take robust measures to keep data and information safely under lock and key. Encryption keys must be rotated regularly (the standard interval is every 90 days) to reduce the risk of compromised data security.
However, regular VPN-based encryption key rotation can be complicated and disruptive, often requiring downtime. SD-WAN can offer automatic key rotation, allowing network administrators to pre-program rotations without manual intervention or system downtime.
4: SD-WAN requirements: Push to the cloud
Another critical feature of SD-WAN technology is cloud breakout. This lets you connect branch office users to cloud-hosted applications directly and securely, eliminating the inefficiencies of backhauling cloud-destined traffic through the data center. Given the ever-growing importance of SaaS and IaaS services, efficient and reliable access to the cloud is crucial for many businesses and other organizations. By simplifying how branch traffic is routed, SD-WAN makes setting up breakouts quicker and easier.
**The changing perimeter location**
Users are no longer positioned in one location with corporate-owned static devices. Instead, they are dispersed; additional latency degrades application performance when connecting to central areas. Applications and network devices can be optimized, but the only solution is to shorten the link by moving to cloud-based applications. There is a huge push and a rapid flux for cloud-based applications. Most are now moving away from on-premise in-house hosting to cloud-based management.
**SaaS-based Applications**
The ready-made global footprint enables the usage of SaaS-based platforms that negate the drawbacks of dispersed users tromboning to a central data center to access applications. Logically positioned cloud platforms are closer to the mobile user. In addition, hosting these applications on the cloud is far more efficient than making them available over the public Internet.
5: SD-WAN requirements: Decentralization of traffic
A lot of traffic is now decentralized from the central data center to remote branch sites. Many branches do not run high bandwidth-intensive applications. These types of branch sites are known as light edges. Despite the traffic change, the traditional branch sites rely on hub sites for most security and network services.
The branch sites should connect to the cloud applications directly over the Internet without tromboning traffic to data centers for Internet access or security services. An option should exist to extend the security perimeter into the branch sites without requiring expensive onsite firewalls and IPS/IDS. SD-WAN builds a dynamic security fabric without the appliance sprawl of multiple security devices and vendors.
**The ability to service chain traffic**
Also, service chaining. Service chaining through SD-WAN allows organizations to reroute their data traffic through one service or multiple services, including intrusion detection and prevention devices or cloud-based security services. It thereby enables firms to declutter their branch office networks.
After all, they can automate handling particular types of traffic flows and assemble connected network services into a single chain.
6: SD-WAN requirements: Bandwidth-intensive applications
Exponential growth in demand for high-bandwidth applications such as multimedia in cellular networks has triggered the need to develop new technologies capable of providing the required high-bandwidth, reliable links in wireless environments. Video streaming is the biggest user of internet bandwidth—more than half of total global traffic. The Cartesian study confirms historical trends reflecting consumer usage that remains highly asymmetric, as video streaming remains the most popular.
**Richer and hungry applications**
Richer applications, multimedia traffic, and growth in the cloud application consumption model drive the need for additional bandwidth. Unfortunately, the congestion leads to packet drops, ultimately degrading application performance and user experience.
SD-WAN offers flexible bandwidth allocation, so you don’t manually allocate bandwidth for specific applications. Instead, SD-WAN allows you to classify applications and specify a particular service level requirement. This way, you can ensure your set-up is better equipped to run smoothly, minimizing the risk of glitchy and delayed performance on an audio conference call.
7: SD-WAN requirements: Organic growth
We also have organic business growth, a big driver for additional bandwidth requirements. The challenge is that existing network infrastructures are static and need help to respond adequately to this growth in a reasonable period. The last mile of MPLS locks you in, destroying agility. Circuit lead times impede the organization’s productivity and create an overall lag.
A WAN solution should be simple. To serve the new era of applications, we need to increase the link capacity by buying more bandwidth. However, life is more complex. The WAN is an expensive part of the network, and employing link oversubscription to reduce the congestion is too costly.
Bandwidth is expensive to cater to new application requirements not met by the existing TDM-based MPLS architectures. At the same time, feature-rich MPLS is expensive for relatively low bandwidth. You will need more bandwidth to beat latency.
On the more traditional side, MPLS and private ethernet lines (EPLs) can range in cost from $700 to $10,000 per month, depending on bandwidth size and distance of the link itself. Some enterprises must also account for redundancies at each site as uptime for higher-priority sites comes into play. Cost becomes exponential when you have a large number of sites to deploy.
8: SD-WAN requirements: Limitations of protocols
We already mentioned some problems with routing protocols, but leaving IPsec to default raises challenges. IPSec architecture is point-to-point, not site-to-site. Therefore, it does not natively support redundant uplinks. Complex configurations and potentially additional protocols are required when sites have multiple uplinks to multiple providers.
Left to its defaults, IPsec is not abstracted, and one session cannot be sent over various uplinks. This will cause challenges with transport failover and path selection. Secure tunnels should be torn up and down immediately, and new sites should be incorporated into a secure overlay without much delay or manual intervention.
9: SD-WAN requirements: Internet of Things (IoT)
As millions of IoT devices come online, how do we further segment and secure this traffic without complicating the network design? Many dumb IoT devices will require communication with the IoT platform in a remote location. Therefore, will there be increased signaling traffic over the WAN?
Security and bandwidth consumption are vital issues concerning the introduction of IP-enabled objects. Although encryption is a great way to prevent hackers from accessing data, it is also one of the leading IoT security challenges.
These drives like the storage and processing capabilities found on a traditional computer. The result is increased attacks where hackers can easily manipulate the algorithms designed for protection. Also, Weak credentials and login details leave nearly all IoT devices vulnerable to password hacking and brute force. Any company that uses factory default credentials on its devices places its business, assets, customers, and valuable information at risk of being susceptible to a brute-force attack.
10: SD-WAN requirements: Visibility
Many service provider challenges include the need for more visibility into customer traffic. The lack of granular details of traffic profiles leads to expensive over-provision of bandwidth and link resilience. In addition, upgrades at both the packet and optical layers often need complete traffic visibility and justification.
In case of an unexpected traffic spike, many networks are left at half capacity. As a result, much money is spent on link underutilization, which should be spent on innovation. This link between underutilization and oversubscription is due to a need for more visibility.
**SD-WAN Use Case**
DMVPN: Exploring Single Hub Dual Cloud Architecture
Single Hub Dual Cloud architecture takes the traditional DMVPN setup to the next level. Instead of relying on a single cloud (service provider) for connectivity, this configuration utilizes two separate clouds, providing redundancy and improved performance. The hub device is the central point of contact for all remote sites, ensuring seamless communication between them.
1. Enhanced Redundancy: The Single Hub Dual Cloud configuration offers built-in redundancy with two separate clouds. If one cloud experiences downtime or connectivity issues, the network seamlessly switches to the alternate cloud, ensuring uninterrupted communication.
2. Improved Performance: By distributing the load across two clouds, Single Hub Dual Cloud architecture can handle higher traffic volumes efficiently. This leads to improved network performance and reduced latency for end-users.
3. Scalability: This architecture allows for easy scalability as new sites can be seamlessly added to the network without disrupting the existing infrastructure. The hub device manages the routing and connectivity, simplifying network management and reducing administrative overhead.
Summary: SD WAN Tutorial
SD-WAN, or Software-Defined Wide Area Networks, has emerged as a game-changing technology in the realm of networking. This tutorial delved into SD-WAN fundamentals, its benefits, and how it revolutionizes traditional WAN infrastructures.
Understanding SD-WAN
SD-WAN is an innovative approach to networking that simplifies the management and operation of a wide area network. It utilizes software-defined principles to abstract the underlying network infrastructure and provide centralized control, visibility, and policy-based management.
Key Features and Benefits
One of the critical features of SD-WAN is its ability to optimize network performance by intelligently routing traffic over multiple paths, including MPLS, broadband, and LTE. This enables organizations to leverage cost-effective internet connections without compromising performance or reliability. Additionally, SD-WAN offers enhanced security measures, such as encrypted tunneling and integrated firewall capabilities.
Deployment and Implementation
Implementing SD-WAN requires careful planning and consideration. This section will explore the different deployment models, including on-premises, cloud-based, and hybrid approaches. We will discuss the necessary steps in deploying SD-WAN, from initial assessment and design to configuration and ongoing management.
Use Cases and Real-World Examples
SD-WAN has gained traction across various industries due to its versatility and cost-saving potential. This section will showcase notable use cases, such as retail, healthcare, and remote office connectivity, highlighting the benefits and outcomes of SD-WAN implementation. Real-world examples will provide practical insights into the transformative capabilities of SD-WAN.
Future Trends and Considerations
As technology continues to evolve, staying updated on the latest trends and considerations in the SD-WAN landscape is crucial. This section will explore emerging concepts, such as AI-driven SD-WAN and integrating SD-WAN with edge computing and IoT technologies. Understanding these trends will help organizations stay ahead in the ever-evolving networking realm.
Conclusion:
In conclusion, SD-WAN represents a paradigm shift in how wide area networks are designed and managed. Its ability to optimize performance, ensure security, and reduce costs has made it an attractive solution for organizations of all sizes. By understanding the fundamentals, exploring deployment options, and staying informed about the latest trends, businesses can leverage SD-WAN to unlock new possibilities and drive digital transformation.
- Fortinet’s new FortiOS 7.4 enhances SASE - April 5, 2023
- Comcast SD-WAN Expansion to SMBs - April 4, 2023
- Cisco CloudLock - April 4, 2023