Blog
Network Insight.
- Premium Consultancy, Ebooks, Videos and Elearning
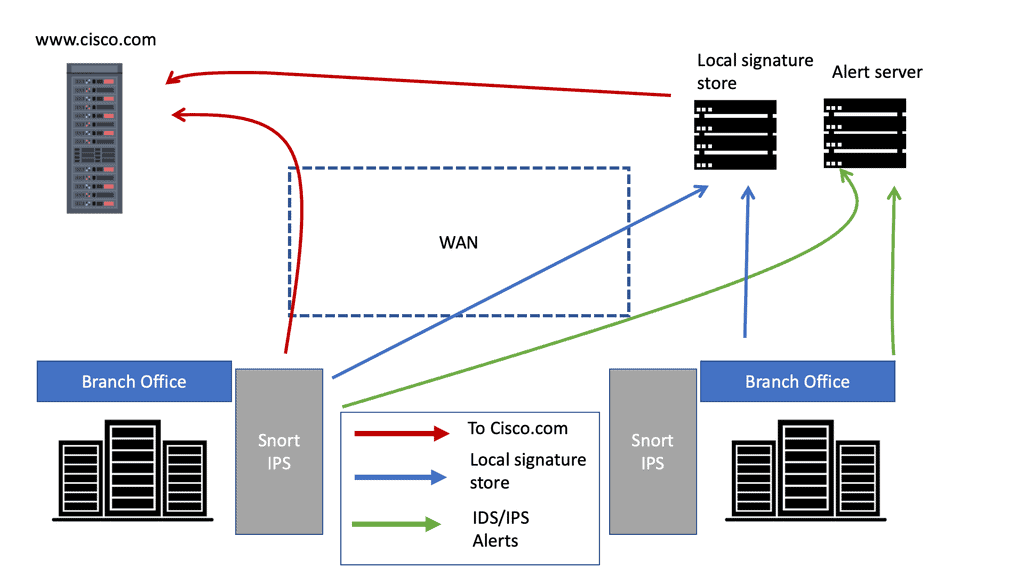
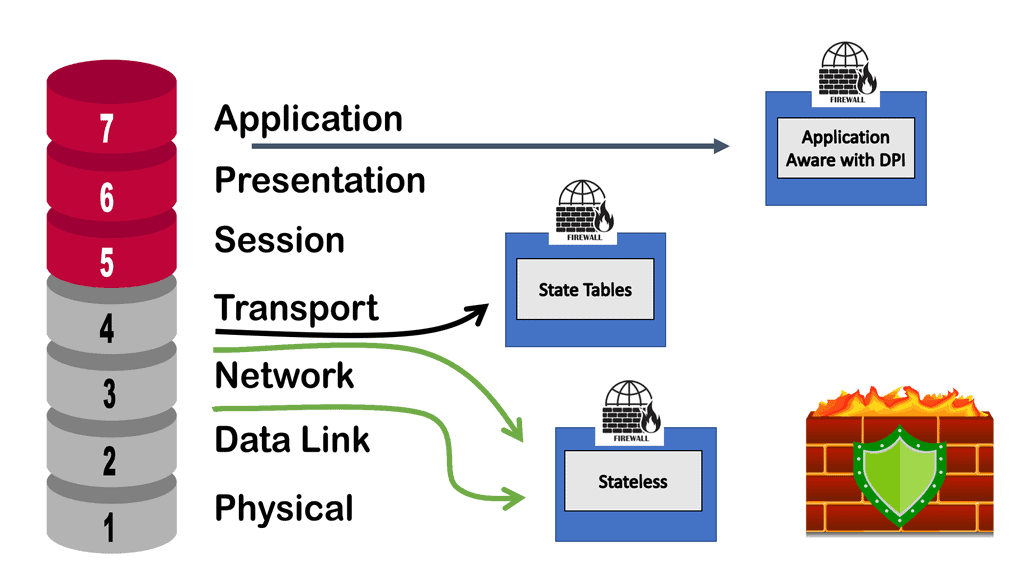
Cisco Firewall with Cisco IPS
Cisco Firewall with IPS In today’s digital landscape, the need for robust network security has never been more critical. With the increasing prevalence of cyber threats, businesses must invest in reliable firewall solutions to safeguard their sensitive data and systems. One such solution that stands out is the Cisco Firewall. …
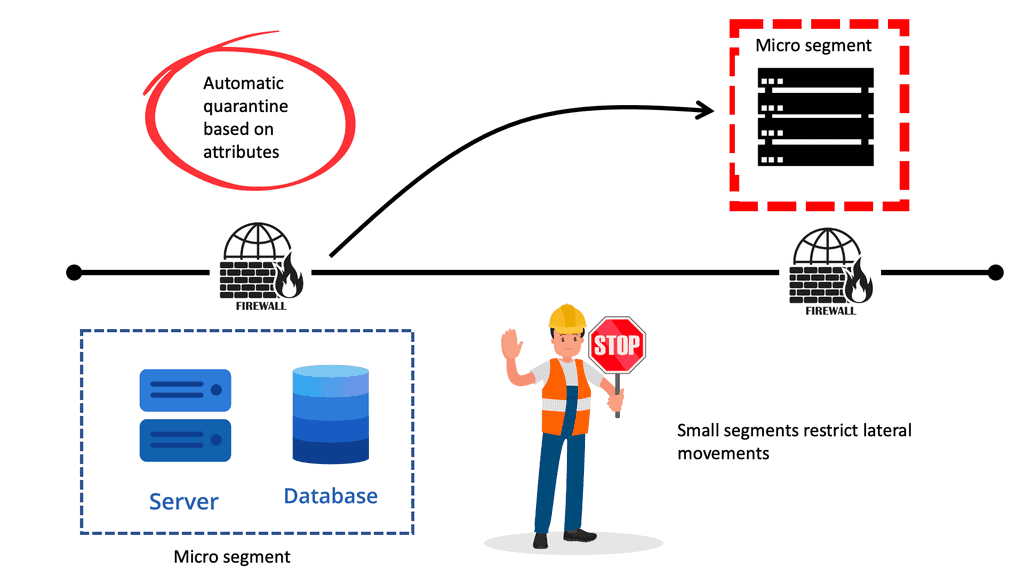
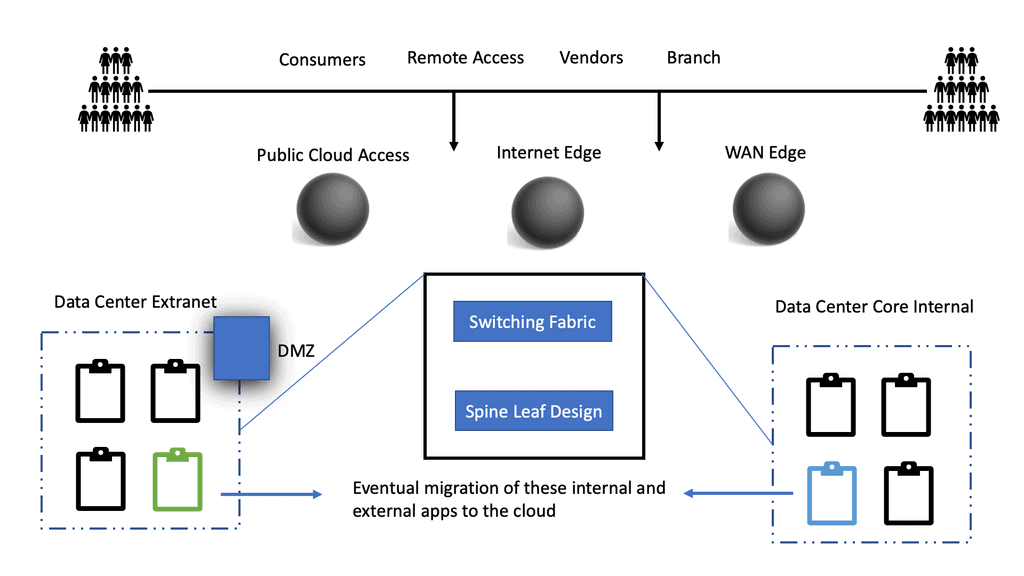
Data Center Security
Data Center Security Data centers are crucial in storing and managing vast information in today’s digital age. However, with increasing cyber threats, ensuring robust security measures within data centers has become more critical. This blog post will explore how Cisco Application Centric Infrastructure (ACI) can enhance data center security, providing …
Identity Security
Identity Security In today’s interconnected world, protecting our personal information has become more crucial than ever. With the rise of cybercrime and data breaches, ensuring identity security has become a paramount concern for individuals and organizations alike. In this blog post, we will explore the importance of identity security, common …
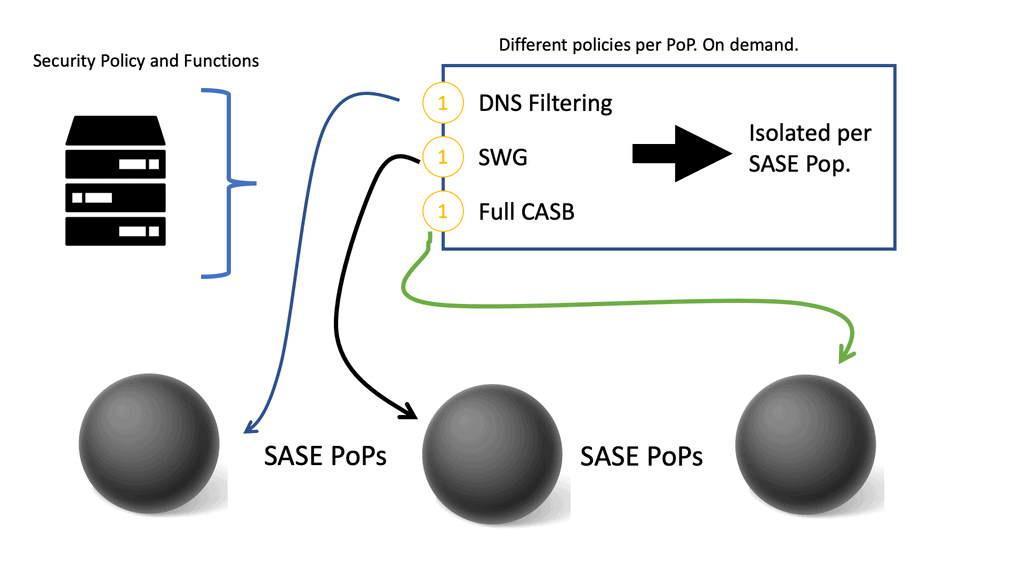
Cisco Secure Firewall with SASE Cloud
Cisco Secure Firewall with SASE Cloud In today’s digital era, network security is of paramount importance. With the rise of cloud-based services and remote work, businesses require a comprehensive security solution that not only protects their network but also ensures scalability and flexibility. Cisco Secure Firewall with SASE (Secure Access …
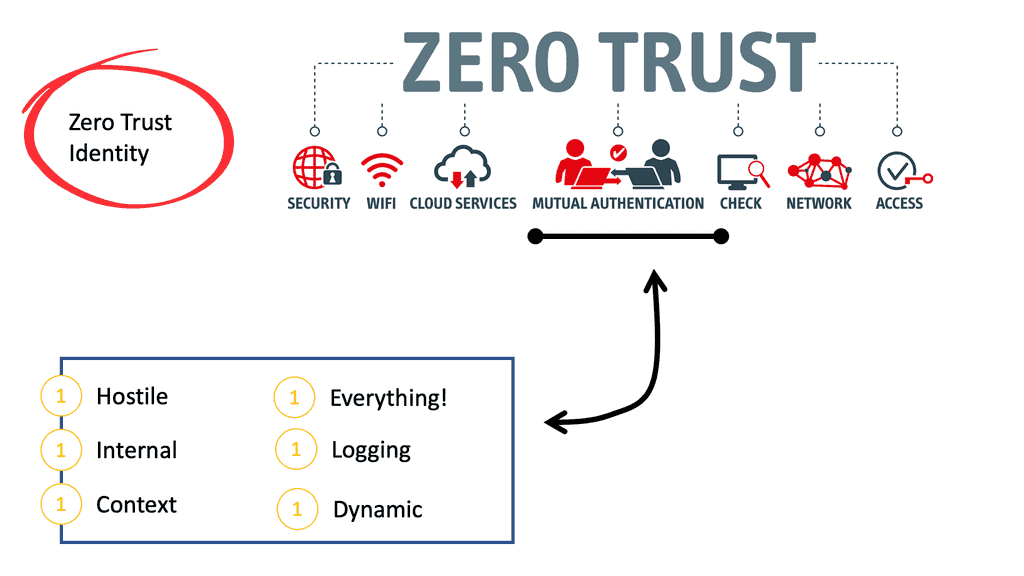
SASE Model | Zero Trust Identity
SASE Model | Zero Trust Identity In today’s ever-evolving digital landscape, the need for robust cybersecurity measures is more critical than ever. Traditional security models are being challenged by the growing complexity of threats and the increasing demand for remote work capabilities. This blog post delves into the SASE (Secure …
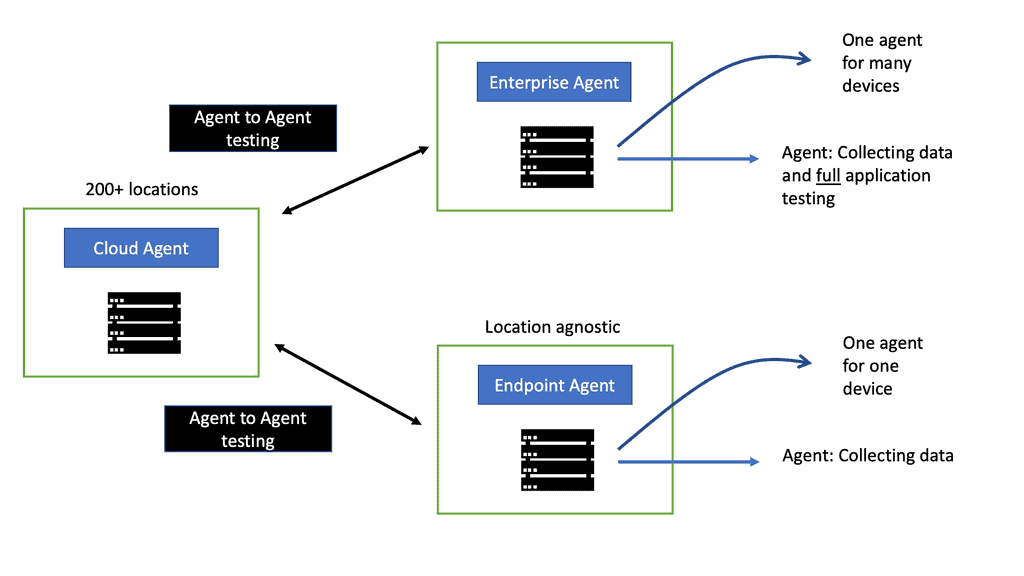
SASE Visibility with Cisco ThousandEyes
SASE Visibility with Cisco ThousandEyes In today’s interconnected digital landscape, enterprises are increasingly adopting Secure Access Service Edge (SASE) solutions to streamline their network and security infrastructure. One key aspect of SASE implementation is ensuring comprehensive visibility into the network performance and security posture. In this blog post, we will …
SD WAN Security
SD WAN Security In today’s interconnected world, where businesses rely heavily on networks for their daily operations, ensuring the security of Wide Area Networks (WANs) has become paramount. WANs are at the heart of data transmission, connecting geographically dispersed locations and enabling seamless communication. However, with the rise of cyber …
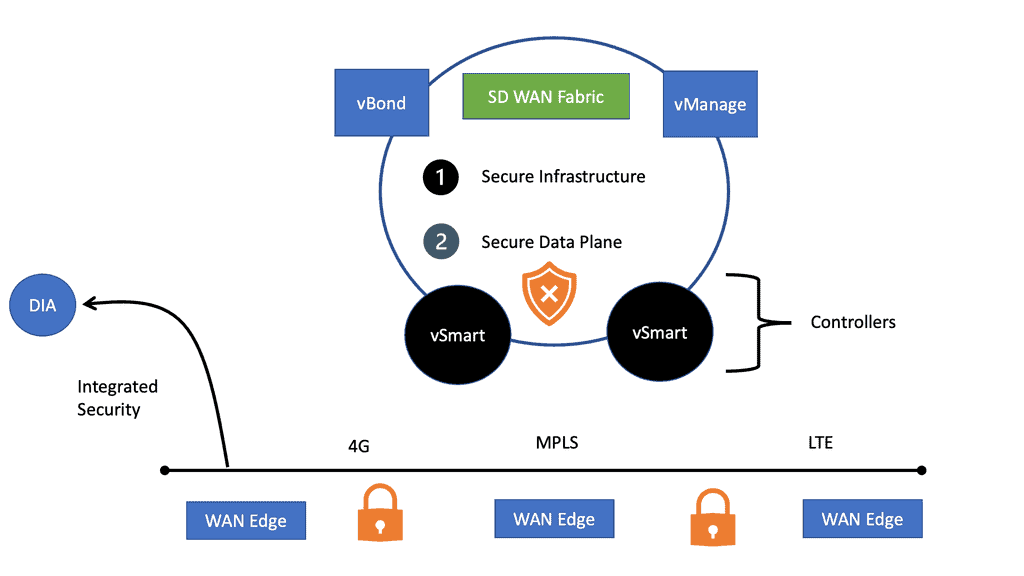
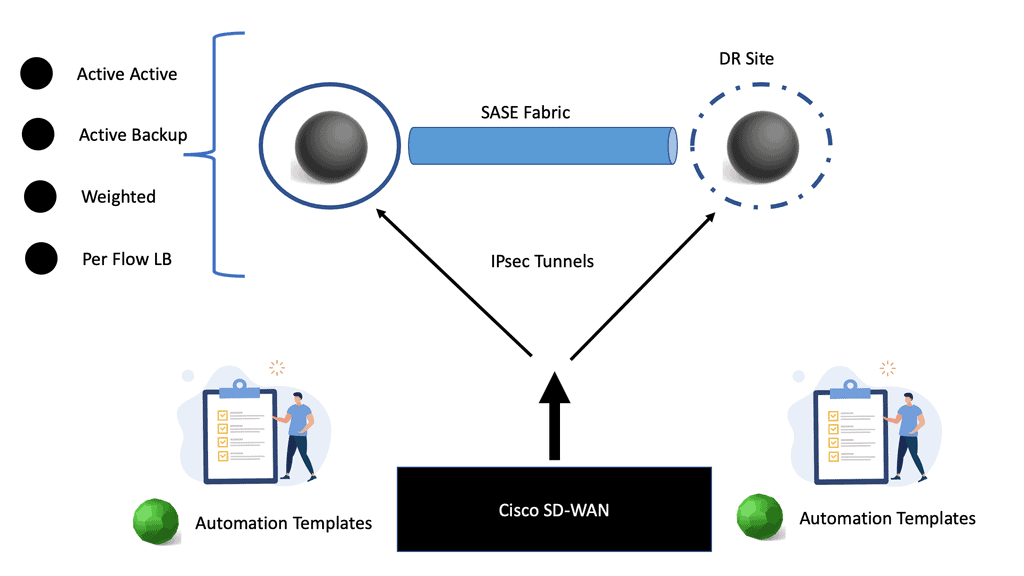
SD-WAN SASE
SD WAN SASE SD-WAN, or Software-Defined Wide Area Networking, is a transformative technology that enhances network connectivity for geographically dispersed businesses. By utilizing software-defined networking principles, SD-WAN empowers organizations to optimize their wide area network infrastructure, reduce costs, and improve application performance. The key features of SD-WAN include dynamic path …
SASE | SASE Solution
SASE Solution In the realm of network security, the rise of SASE (Secure Access Service Edge) solution has been nothing short of revolutionary. Combining the capabilities of networking and security into a single cloud-based service, SASE has transformed the way organizations manage and protect their digital infrastructure. In this blog …
Security Automation
Security Automation In today’s fast-paced digital landscape, ensuring the security of our online presence has become more critical than ever. With the ever-evolving threat landscape and increasing complexity of cyberattacks, manual security measures may no longer suffice. This is where security automation comes into play, revolutionizing the way we protect …
Splunk Security
Splunk Security In today’s rapidly evolving digital landscape, the need for robust security measures is more crucial than ever. With cyber threats becoming increasingly sophisticated, organizations must arm themselves with advanced tools and technologies to safeguard their valuable data. Enter Splunk Security, a powerful solution that revolutionizes the way businesses …
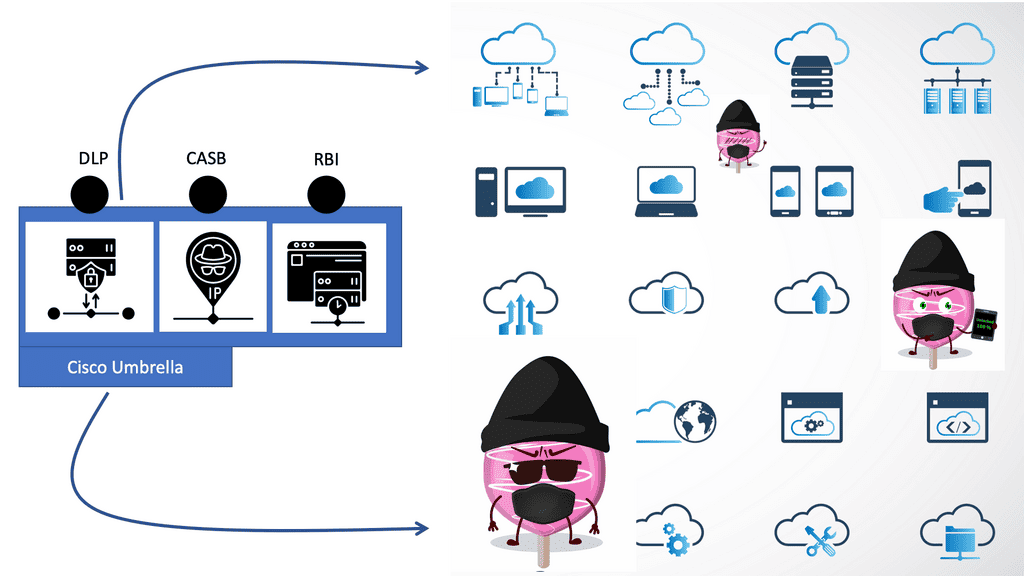
Cisco Umbrella CASB
Cisco Umbrella CASB In today’s digital landscape, businesses face numerous security challenges. Protecting sensitive data and ensuring compliance with regulations are top priorities. This is where Cisco Umbrella CASB (Cloud Access Security Broker) comes into play. In this blog post, we will explore the key features and benefits of Cisco …