Blog
Network Insight.
- Premium Consultancy, Ebooks, Videos and Elearning
SASE Definition
SASE Definition In today’s digital landscape, organizations constantly seek ways to enhance network security, simplify infrastructure, and optimize performance. One emerging concept that has gained significant attention is Secure Access Service Edge (SASE). In this blog post, we will delve into the definition of SASE, its key components, and how …
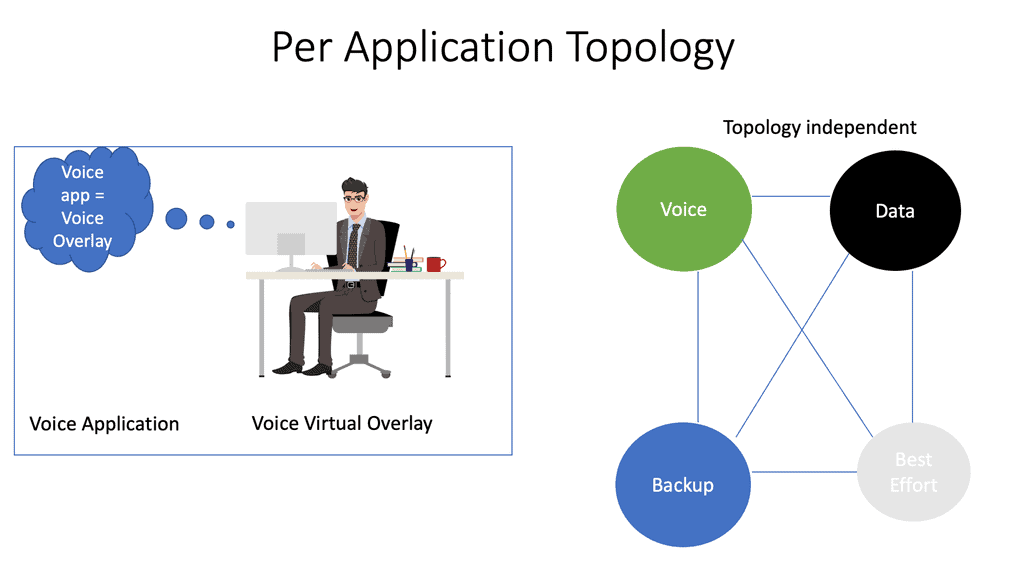
SD WAN Overlay
SD WAN Overlay In today’s digital age, businesses rely on seamless and secure network connectivity to support their operations. Traditional Wide Area Network (WAN) architectures often struggle to meet the demands of modern companies due to their limited bandwidth, high costs, and lack of flexibility. A revolutionary SD-WAN (Software-Defined Wide …
SD WAN | SD WAN Tutorial
In today’s digital age, businesses increasingly rely on technology for seamless communication and efficient operations. One technology that has gained significant traction is Software-Defined Wide Area Networking (SD-WAN). This blog post will provide a comprehensive tutorial on SD-WAN, explaining its key features, benefits, and implementation aspects. Matt Conran SD-WAN stands …
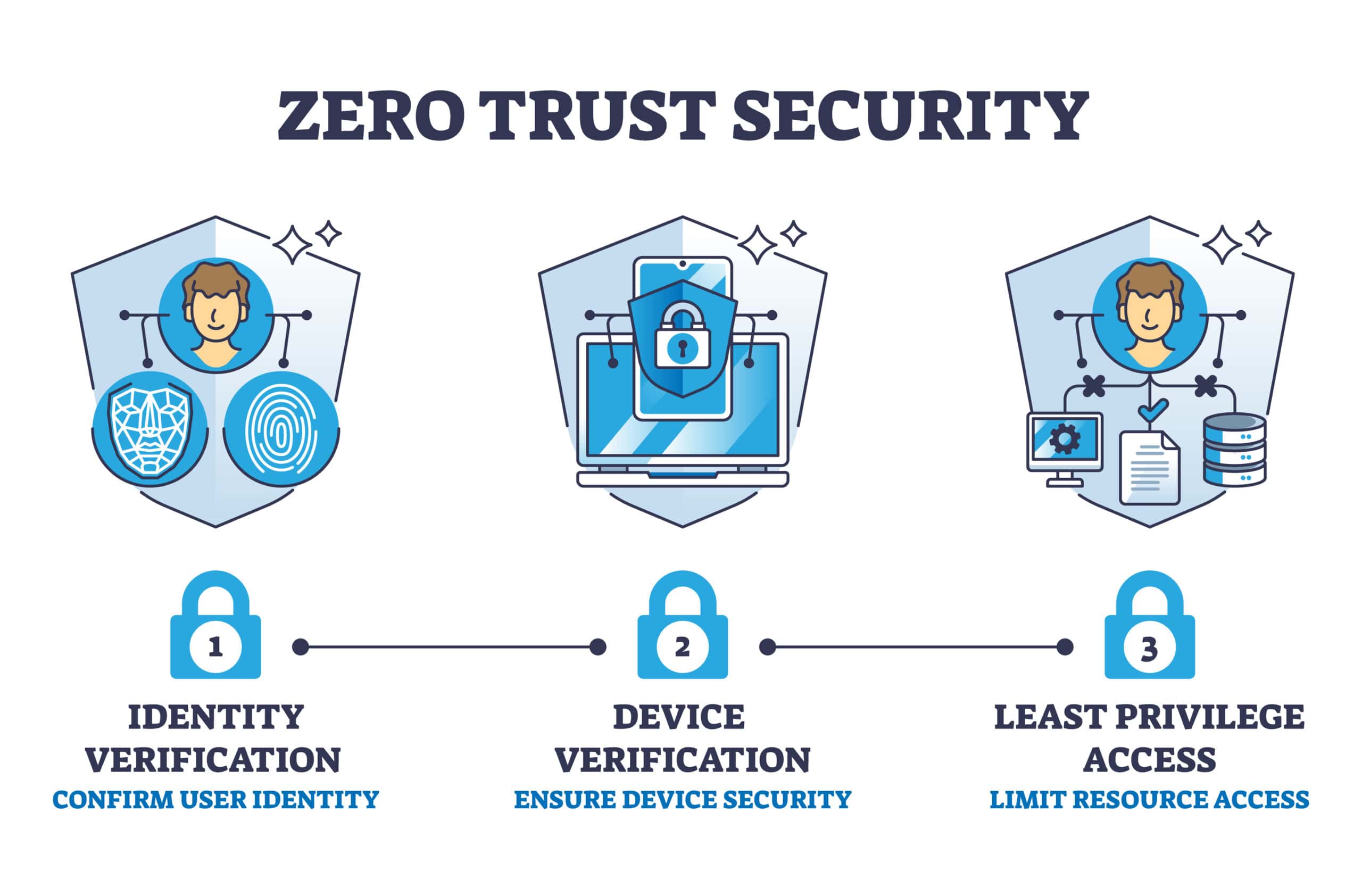
Zero Trust Network Design
Zero Trust Network Design In today’s interconnected world, where data breaches and cyber threats have become commonplace, traditional perimeter defenses are no longer enough to protect sensitive information. Enter Zero Trust Network Design is a security approach that prioritizes data protection by assuming that every user and device, inside or …
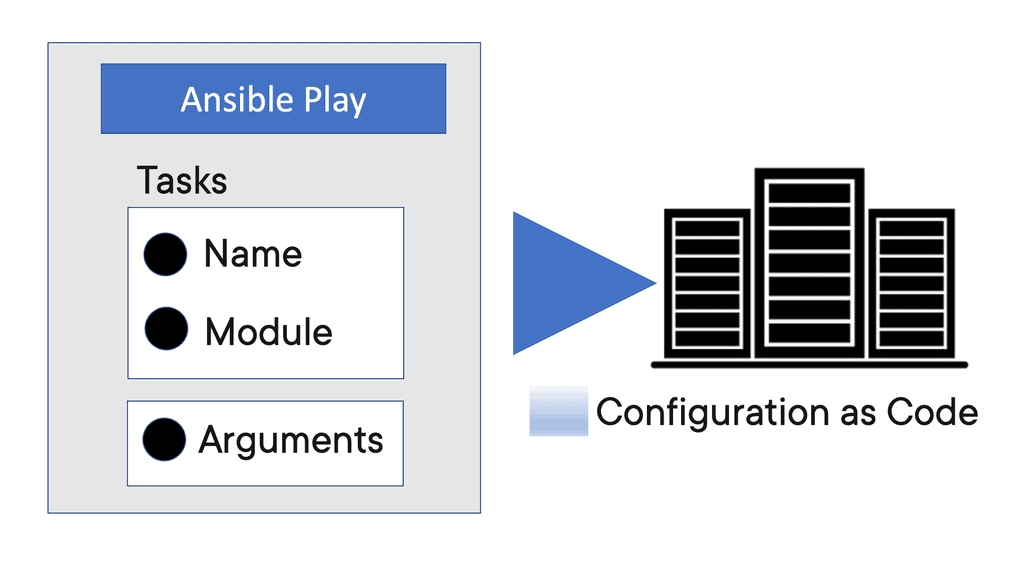
Ansible Variables | Ansible Automation
Ansible Variables In the world of automation, Ansible has emerged as a popular choice for managing and configuring systems. One of the key features that sets Ansible apart is its ability to work with variables. Variables in Ansible enable users to define and store values that can be …
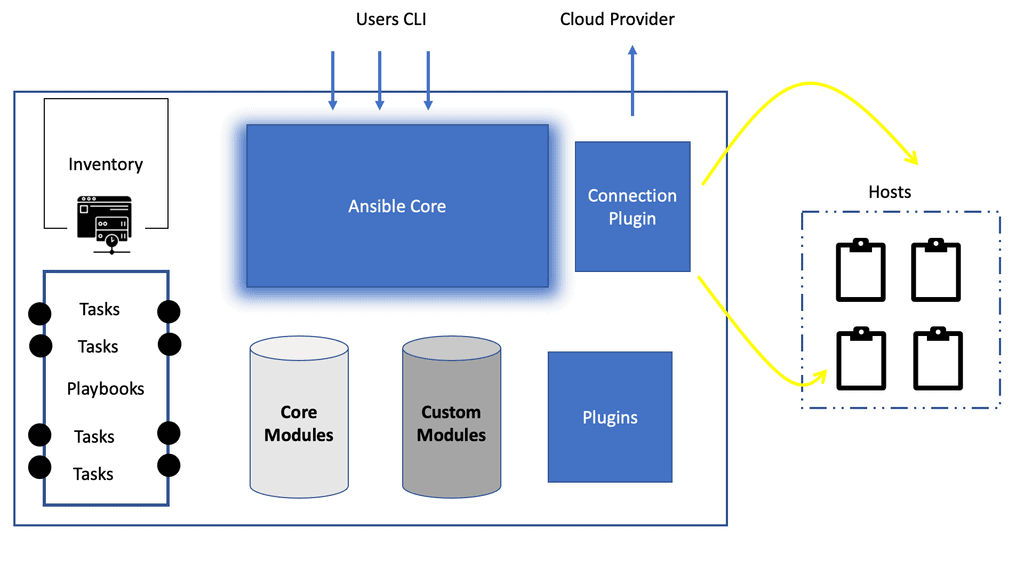
Ansible Architecture | Ansible Automation
Ansible Architecture Ansible has emerged as one of the most popular automation tools, revolutionizing how organizations manage and deploy their IT infrastructure. Ansible has gained widespread adoption across diverse industries with its simple yet robust architecture. In this blog post, we will delve into the intricacies of Ansible …
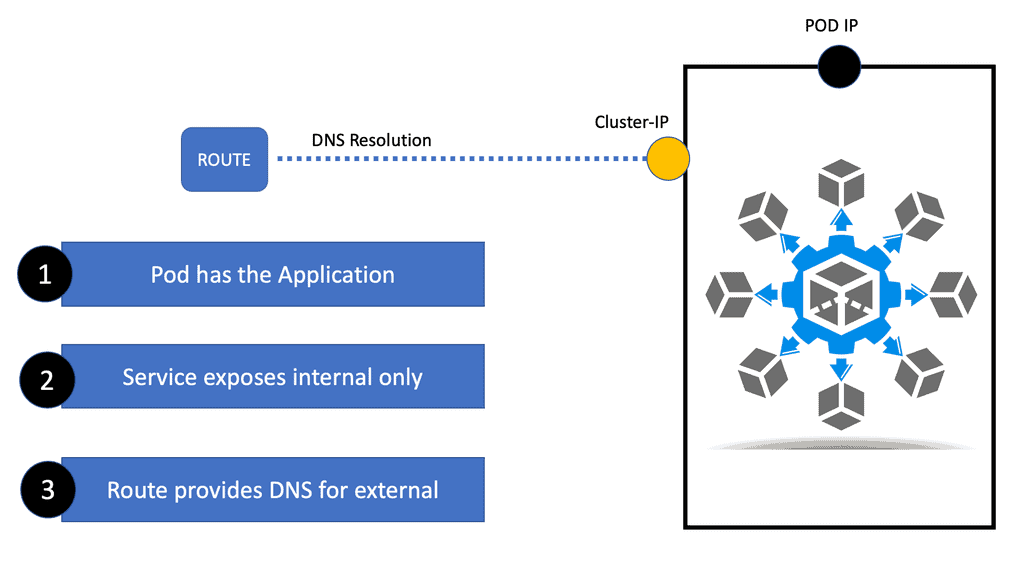
OpenShift SDN
OpenShift SDN In today’s fast-paced cloud computing and containerization world, efficient networking solutions are essential to ensure seamless communication between containers and applications. OpenShift SDN (Software-Defined Networking) has emerged as a powerful tool for simplifying container networking and managing the complexities of distributed systems. This blog post will explore what …
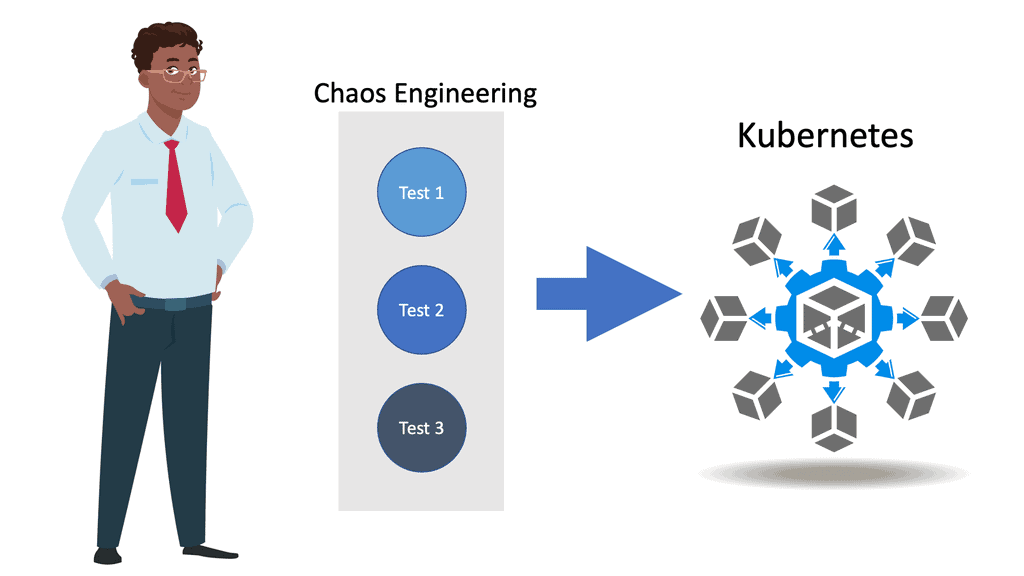
Chaos Engineering Kubernetes
Chaos Engineering Kubernetes In the world of cloud-native computing, Kubernetes has emerged as the de facto container orchestration platform. With its ability to manage and scale containerized applications, Kubernetes has revolutionized modern software development and deployment. However, as systems become more complex, ensuring their resilience and reliability has …
Docker Container Security: Building a Sandbox
Docker Container Security In recent years, Docker has revolutionized how software is developed and deployed. Its ability to create lightweight, isolated containers has made it a popular choice among developers. One of the most powerful features of Docker is the ability to create sandboxes, which are remote environments that mimic …
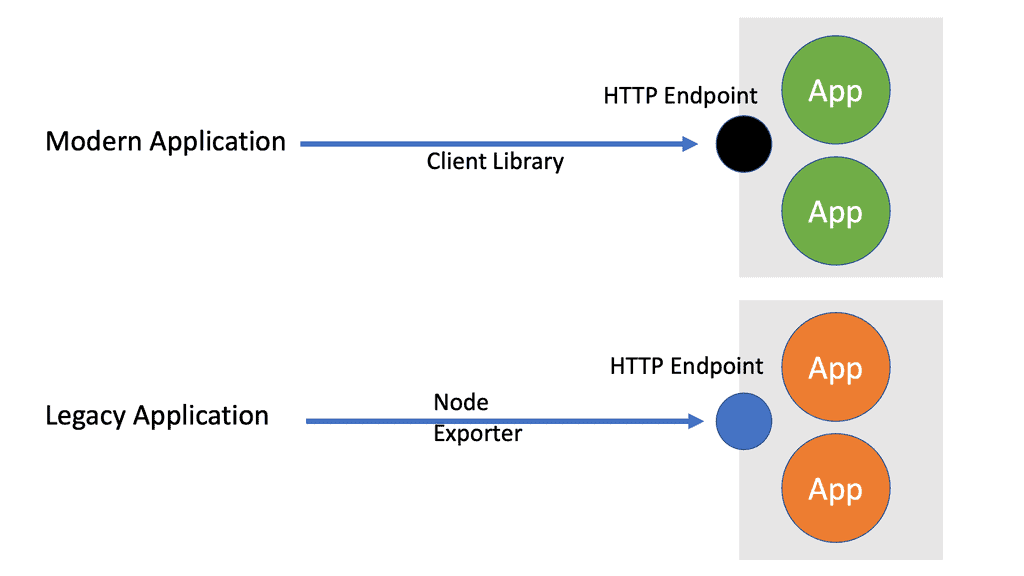
Prometheus Metric Types
Prometheus Metric Types Prometheus, an open-source monitoring and alerting toolkit, has gained immense popularity among DevOps engineers and system administrators. One of the key features that set Prometheus apart is its support for various metric types. This blog post will dive into Prometheus’s different metric types, explaining their significance and …
Prometheus Monitoring: The Pull Approach
Prometheus Monitoring: The Pull Approach In the world of monitoring and observability, Prometheus has emerged as a powerful tool for collecting and analyzing metrics. One of the key aspects of Prometheus is its unique approach to data collection, known as the pull approach. In this blog post, we will explore …
Starting Observability
Starting Observability In the ever-evolving landscape of technology, the complexity of modern systems continues to increase. As software developers, system administrators, and IT professionals, we are constantly faced with the challenge of ensuring the smooth operation of these intricate systems. This is where observability comes into play. In …