Splunk Security
In today's rapidly evolving digital landscape, the need for robust security measures is more crucial than ever. With cyber threats becoming increasingly sophisticated, organizations must arm themselves with advanced tools and technologies to safeguard their valuable data. Enter Splunk Security, a powerful solution that revolutionizes the way businesses approach data protection and threat detection.
At its core, Splunk Security is a comprehensive security information and event management (SIEM) platform that enables organizations to gain real-time insights into security events and incidents. By collecting, analyzing, and visualizing data from various sources, Splunk Security empowers businesses to proactively identify potential threats and mitigate risks effectively.
Splunk Security offers a wide array of features and capabilities that strengthen an organization's security posture. These include:
Log Management: Splunk Security allows for the centralization and indexing of logs from diverse sources, such as network devices, servers, and applications. This consolidated view enables efficient log analysis and correlation, making it easier to identify security anomalies.
Threat Intelligence: The platform integrates with external threat intelligence feeds, providing up-to-date information on emerging threats and vulnerabilities. By leveraging this intelligence, organizations can quickly detect and respond to potential attacks, minimizing the impact on their systems.
User Behavior Analytics: Splunk Security leverages machine learning algorithms to establish baselines of normal user behavior. This allows for the detection of anomalous activities that may indicate insider threats or compromised accounts, enhancing overall security posture.
One of the significant advantages of Splunk Security is its ability to seamlessly integrate with existing security tools and infrastructure. Whether it's firewalls, intrusion detection systems, or endpoint protection solutions, Splunk Security can ingest data from these sources and correlate it for a comprehensive security view. Furthermore, the platform is highly scalable, accommodating the growing data volumes and security needs of organizations of all sizes.
Splunk Security's real-time monitoring capabilities empower organizations to respond swiftly to potential threats. By continuously analyzing incoming data, the platform can trigger alerts and notifications based on predefined rules and thresholds. This proactive approach allows security teams to take immediate action, preventing security incidents from escalating into major breaches.
Splunk Security is a game-changer in the realm of data protection and threat detection. By leveraging its powerful features, seamless integration capabilities, and real-time monitoring, organizations can enhance their security posture and stay one step ahead of malicious actors. Embracing Splunk Security is not just a proactive measure; it's a strategic investment in safeguarding valuable data and ensuring business continuity.Matt Conran
Highlights: Splunk Security
Splunk Monitoring
Splunk is software for monitoring, searching, analyzing, and visualizing real-time machine-generated data. This tool can monitor and read several log files and store data as events in indexers. In addition, it uses dashboards to visualize data in various forms. Splunk is commonly thought of as “a Google for log files” because, like Google, it can be used to define the state of a network and the activities taking place within it. It is a centralized log management tool but works well with structured and unstructured data.
A. Real-time monitoring and Detection:
One of Splunk Security’s critical strengths is its ability to monitor and analyze massive volumes of data in real time. By aggregating data from various sources such as logs, network traffic, and security devices, Splunk Security provides a unified view of the entire IT environment. This enables the detection of anomalies, suspicious activities, and potential threats, empowering security teams to take immediate action and mitigate risks effectively.
B. Threat Intelligence Integration:
Splunk Security integrates seamlessly with external threat intelligence feeds, enriching the analysis and detection capabilities. By leveraging threat intelligence data from trusted sources, organizations can stay ahead of emerging threats and proactively defend their infrastructure. Splunk’s threat intelligence integration empowers security teams to identify patterns, correlate events, and make well-informed real-time decisions.
C. Incident Response and Forensics:
When a security incident occurs, time is of the essence—Splunk Security streamlines incident response by providing automated workflows, playbooks, and case management capabilities. Security teams can quickly investigate and triage alerts, gather evidence, and take necessary actions to contain and remediate the incident. Splunk’s forensics capabilities enable detailed analysis and post-incident investigations, helping organizations learn from past incidents and improve their security posture.
The Role of Visibility and Analytics
**Real time Visibility & Analytics**
Splunk Security is a powerful tool for monitoring an organization’s network security. It provides real-time visibility and analytics into network traffic, helping organizations promptly detect and respond to security threats. It can also identify malicious activity and vulnerabilities and help organizations protect their assets proactively.
Splunk Security is a comprehensive solution offering various security use cases, including threat detection, vulnerability management, incident response, and compliance reporting features. It is designed to be easy to use and secure, making it an ideal solution for any organization.
**Example: Splunk Enterprise Security**
The product set offering Splunk Security has several well-integrated products, such as Splunk Enterprise Security, also known as Splunk ES, which is the Splunk SIEM, Splunk SOAR, and User Behavior Analytics (UBA), and a variety of Observability tools at your disposal.
**Multiple Phases & Tasks**
In addition, SOAR Splunk brings a lot of power, especially when you push the boundaries of automation to fully detect and respond to scenarios with multiple phases and tasks. Finally, consider Splunk, the platform in the middle of your infrastructure that removes all the complexity.
One significant benefit of using Splunk security is that it can ingest data from every source and combine it into one platform that fully satisfies all security requirements.
Related: For pre-information, you may find the following helpful:
Common Security Challenges
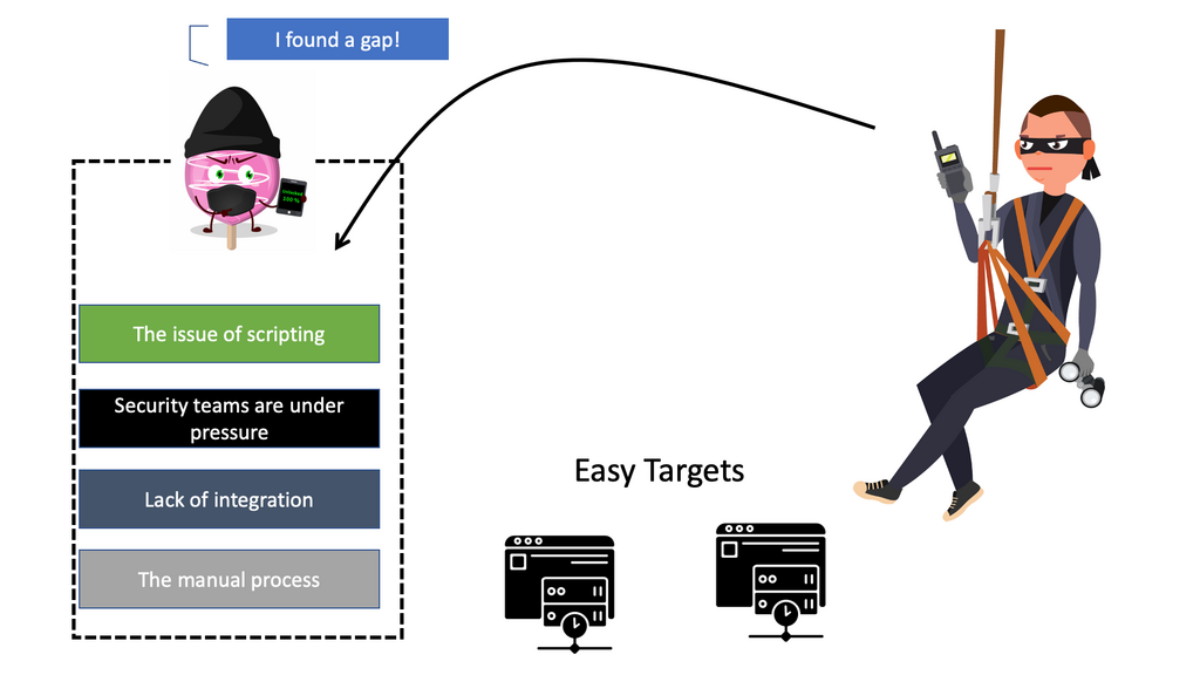
Security Teams are under pressure.
Security teams face diverse challenges, from repetitive tasks to cumbersome processes. They often need help with constant alerts, manual investigations, and the array of tools distributed throughout the organization. Hundreds of security alerts overpower analysts, making it impossible for them to investigate and resolve each day thoroughly. As a result, security operations work is rife with monotonous, routine, and repetitive tasks, with a complete lack of integration and process.
**Custom-made Logging**
Some security teams built their log analytics and incident response capabilities from the ground up. However, such a custom-made logging tool requires manually assembling correlated logs with too many custom-built and siloed point products. Teams are expected to manage disconnected security tools, which consist of static, independent controls with little or no integration.
In the current environment, many security teams must establish workflows and standard operating procedures for different security events. As a result, analysts can only act quickly and decisively when responding to an attack. However, the real problem is the manual process, especially with manual scripting.
**Issues of scripting**
Carrying out this capability across many security vendors will be challenging when using traditional scripting for automation. In addition, each vendor may change the API for its product. As a result, the automation scripts must change, leading to management and maintenance challenges. Most will only be able to integrate and create an automated workflow partially. The difficult-to-maintain processes lead to a need for more context.
Phishing, Ransomware, and Supply Chain
Security Concerns:
We have a rapidly changing threat landscape that includes everything from Phishing to the proliferation of Malware, Supply Chain, and Ransomware. In addition, there is a pervasive nature of Ransomware to when it started, and it has grown considerably since the early Ransomware strains such as Wanna Cry. So, we have a Ransomware wave with loads of Ransomware families that encrypt in different ways.
Remember that Ransomware applies Malware to many endpoints simultaneously, so if you have a network design with extensive macro segmentation and no intra-segment filtering, it can compromise all hosts with valuable assets.
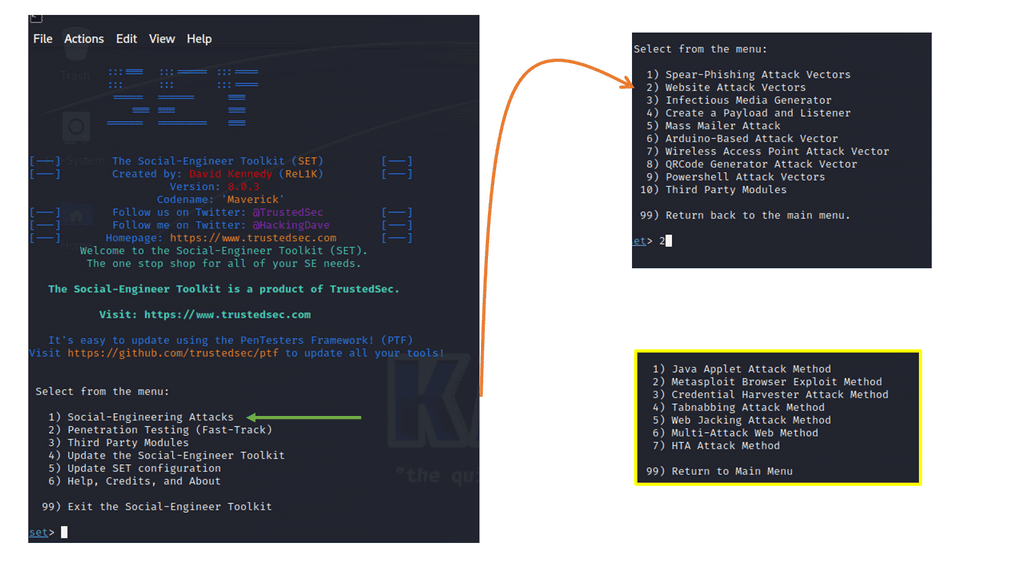
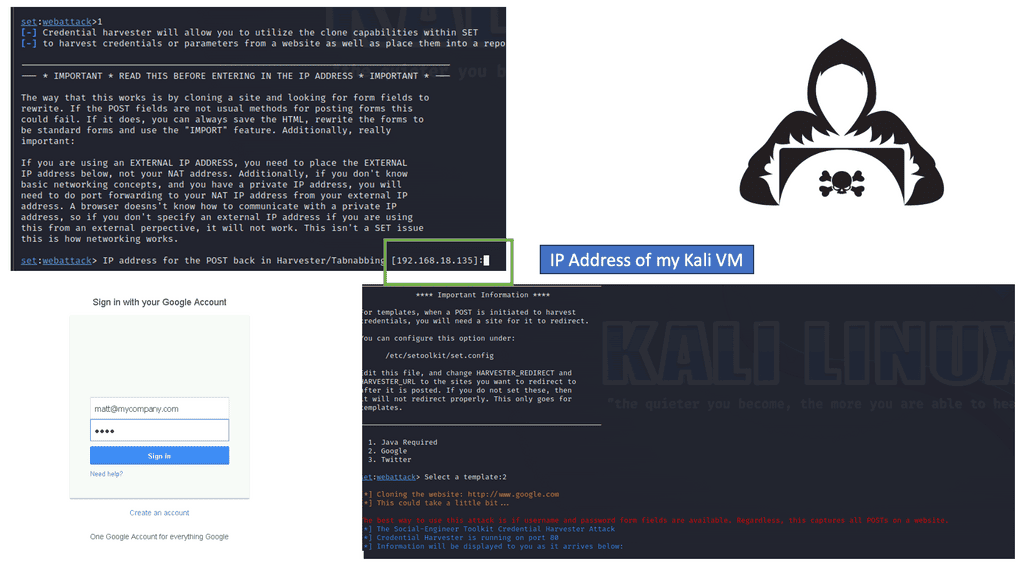
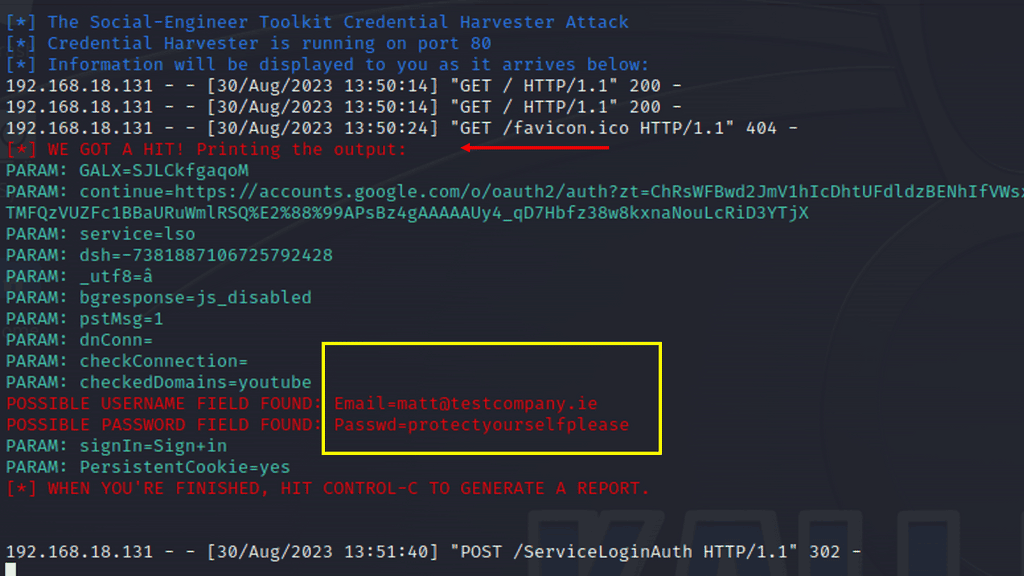
Example Phishing Attack
Below is an example of a phishing attack. I’m using the Credential Harvestor to sniff credentials on a Google Web Template. The credential harvester, a credential stealer, is malicious software designed to steal sensitive login information from unsuspecting victims. Its primary targets are online banking platforms, email accounts, and social media platforms. By infiltrating a victim’s device, it quietly captures keystrokes, takes screenshots, or even intercepts network traffic to gather valuable login credentials.
Safeguarding Against Credential Harvestors
Protecting oneself from the clutches of a credential harvester requires a proactive approach. Here are some essential tips to enhance your cybersecurity:
1. Strengthen Passwords: Use complex, unique passwords for each online account, incorporating a mix of uppercase and lowercase letters, numbers, and symbols.
2. Enable Two-Factor Authentication: Implement an additional layer of security by enabling two-factor authentication whenever available. This adds an extra step for authentication, making it harder for attackers to gain unauthorized access.
3. Exercise Caution with Emails and Links: Be vigilant when opening emails or clicking on links, especially from unknown senders. Avoid providing login credentials on suspicious websites or pop-up windows.
4. Keep Software Updated: Regularly update your operating system, antivirus software, and applications to ensure you have the latest security patches and protection against known vulnerabilities.
Protect Against Malware
Malware endeavors to destroy backups, perform data exfiltration, and corrupt the data. Once the Ransomware binaries have been executed, encryption starts over.
How might the adversary hop from one machine to another without exploiting vulnerabilities? Some long-established tactics are known: remotely creating WMI processes, scheduling tasks, and building services. However, they often go unseen. It would help if you focused on the detection. For Ransomware, we have about a 5-day window. You will not catch them using the manual process within such a short time.
Easy to evade; Malware is polymorphic.
Despite innovations like next-generation anti-malware solutions, threat intelligence feeds, and government collaboration initiatives and mandates such as zero trust, many of these attack techniques evade even the most innovative security tools today. For example, malware is polymorphic and programmed to avoid common signatures and rules, and we know that the perimeter-based defense mechanisms have not worked for a while now.
**Note: It is hard to do things quickly and thoroughly understanding**
– Fast detection and response to security events take a lot of work. A security analyst can spend hours on an alert. Multiply that by the hundreds of security alerts they deal with daily. For example, it’s common for an analyst to spend 90 minutes on average investigating and containing a single phishing alert.
– In addition, a SOC could receive hundreds of phishing emails in a given day. Security analysts are overwhelmed with phishing alerts to investigate and respond to. It takes too long to process each before the potential threat can cause damage manually. Phishing emails are a great starting point for Splunk SOAR to reply with low-code playbooks automatically.
**Note: Unknown accounts with Privilege access and controls**
– Not to mention that businesses frequently add contractors and others with privileged access to networks, it becomes challenging to understand whether everyone complies with the security policies and best practices or if there are any hidden risks in these activities. As a result, they face new challenges around secure configuration, software vulnerabilities, compliance, and maintaining an audit trail of access and training.
Splunk Security & Splunk ES: The Way, Forward
**Data Integration and Automated Response
So, you need to design security around data and build an approach to detect and respond to those risks. This requires a platform that can not collect the data but gain valuable insights. Of course, many platforms can collect data, but turning this data into useful insights for security is an entirely different challenge.
Therefore, data integration and an automated response will play a more significant role in security. This is where Splunk Enterprise Security ( Splunk ES), Splunk SIEM, and Splunk SOAR products can assist.
We can’t stop attacks
We can’t stop attacks, and you will be breached even by adopting the most robust zero-trust principles. All we can do is find ways to mitigate risk promptly. Splunk has a variety of security products that can help you do this.
One of the most critical ways to evolve and stay ahead is to examine data and derive helpful security insights. These insights can help you detect and respond to known, unknown, and advanced threats and fully use automation and orchestration to improve your security posture.
**Splunk Enterprise Security and Splunk SOAR
Automation is changing how teams traditionally use a Splunk SIEM. Splunk SOAR and Splunk Enterprise Security ( Splunk ES ) complement each other very well and allow us to improve security capabilities. So now we have a platform approach to security to fulfill diverse security use cases.
**Splunk SOAR: Orchestration and automation
The prime components of Splunk SOAR are automation and orchestration. With orchestration and automation, you will better support product-level workflows that allow security teams to automate complex processes across disparate products.
Introducing automation and orchestrating workflows and responses across your security stack will enable each previously siloed security product to participate more seamlessly in your defense strategy. So, we still have the unique tools, but Splunk SOAR is in the middle of orchestrating the events for each device with Playbooks.
A Splunk SOAR tool can easily thread the intelligence from multiple devices within the SOC, enriching alert data and surfacing it into a single interface. In addition, there is a playbook visualizer, so you can easily stick together security tasks.
**Integration with Existing Security Infrastructure
By automating the data collection and enrichment process from various sources, the analyst can see valuable details related to the alert as soon as it surfaces. This boosts your defenses by integrating existing security infrastructure, creating a mesh of more difficult-to-penetrate protection.
Splunk SOAR supports 350+ third-party tools and 2,400+ actions, allowing you to connect and coordinate workflows across teams and tools. This increases the speed of your investigation and response and unlocks value from previous investments. We will look at these playbooks in a moment.
Splunk Enterprise Security ( Splunk ES & Splunk SIEM )
Splunk Enterprise Security, the Splunk SIEM technology, is typically deployed to do the following security activities.
- Discover external and internal threats. This will help you detect compromised credentials and privileged attacks.
- Monitor users’ activities and specific types of users, such as those with privileged access and access to critical data assets. For example, this will help you see if users use the sysadmin tool Psexec or other means to move throughout the network laterally.
- Monitor server and database resource access and offer some data exfiltration monitoring capabilities. This can help you detect moments before Ransomware starts to encrypt your files.
- Support compliance requirements and provide compliance reporting.
- Provide analytics and workflow to support incident response. Orchestrate and automate actions and workflows by integrating with other tools, such as the SOAR.
A. Splunk ES & Splunk SIEM: The Value of Machine Data for Security
Splunk ES can complete these activities by gathering and turning unstructured data into valuable meaning. For example, we need to turn to machine data to understand the evidence of an attack and its movement in an organization.
Armed with that data, security teams can better remediate known threats and proactively respond to new threats in real-time to minimize potential damage to the organization.
B. Machine data and monitoring
Data can come in many forms, such as standard logs. So, by ingesting your application logs into Splunk SIEM, you can determine, for example, your application’s latency or your web server’s raw error rate. This can be carried out by using a simple SPL query against the.
Then, we have a security use case, our main concern. Machine data can tell you where a specific attack is coming from or how many login attempts result from invalid user names.
Machine data is everywhere and flows from all the devices we interact with, making up around 90% of today’s data. Harsing this data can give you powerful security insights. However, machine data can be in many formats, such as structured and unstructured. As a result, it can be challenging to predict and process.
C. Splunk SIEM. How Splunk Can Leverage Machine Data
This is where Splunk SIEM comes into play, and it can take any data and create an intelligent, searchable index—adding structure to previously unstructured data. This will allow you to extract all sorts of insights, which can be helpful for security and user behavior monitoring. In the case of Splunk Enterprise Security ( Splunk ES ), it helps you know your data very quickly. Splunk is a big data platform for machine data. It collects raw unstructured data and converts them into searchable events.
D. Splunk ES and Splunk SIEM Stage: Aggregates and Analyzes event data
SIEM technology aggregates and analyzes the event data produced by networks, devices, systems, and applications. The primary data source has been time-series-based log data, but SIEM technology is evolving to process and leverage other forms of data. SIEM technology aggregates event data produced by security devices, network infrastructure, systems, and applications.
**Any Source of Data**
The Index collects data from virtually any source. As data enters Splunk Enterprise Security, it examines it and understands how to process it. When it finds a match, it labels the data with source types. At the heart of Splunk is the Index, and data gets ingested. The Index contains machine data from servers, network devices, and web applications.
These events are then stored in the Splunk index. Once the events are in the Index, they can be searched. You can find events that contain values across multiple data sources so that you can run analysis and statistics on events using the Splunk search language.
E. Splunk ES and Splunk SIEM Stage: Searching and Analysis
Once data gets ingested into the Index, it is available for searching and analysis. Then, you can save search results into reports that can then be used to power dashboard panels. And that comes not just from tools that can sift through the volume of alerts and distractions. Analysts must find the cause, impact, and best resolution from all infrastructure elements. This will include the applications, networks, devices, and human users.
F. Splunk ES and Splunk SIEM Stage: Notable Events and Incident Review
Splunk Enterprise Security allows you to streamline the incident management process. Consolidating incident management will enable effective lifecycle management of security incidents, enabling rapid decision-making. Here, we automatically align all security contexts together for fast incident qualification.
G. Splunk ES and Splunk SIEM Stage: Event Correlation Rule Management
With Splunk Security, we have a framework for rule management, using which we can manage all correlation rules across the system.
Detailed Information on Splunk SOAR
- Low-code playbooks
With automated playbooks orchestrating and executing actions across different point products, Splunk SOAR can automate repetitive tasks, investigation, and response. We have several playbooks that are considered low-code to carry out the automation. Implementing low-code “playbooks” allows for the codification of processes where automation can be applied to improve consistency and time savings.
- Actions based on the Playbooks
Then, we could have a list of actions based on playbook results. This could include further investigation tasks or notifying users. Finally, when you want to push the boundaries of automation, we could have several steps to isolate or quarantine hosts depending on the results of the previous playbooks. These steps would be integrated with multi-factor authentication to ensure the action is appropriately authorized.
- Phases and Task
We have noted low-code playbooks and how they can be used to automate tasks and merge with security tools and other Spunk products. All of this is done with workbooks and phases. For example, we can have a single workbook with several tasks to complete, and after executing these tasks, we can quickly start a separate phase or even a different workbook.
- Splunk SOAR Integration with Other Products
You want to perform a containment action. The SOAR platform can, for example, use Carbon Black. Here, you can have manual, semi-automatic, or fully automatic containment. Or you can use Zscaler for containment. So, there are several additional products that SOAR can integrate with.
In this scenario, there will be one phase. And several playbooks in a single phase. First, some playbooks can be triggered automatically, and some are invoked manually. Then, some are being gathered manually but will have prompts for additional information.
These tasks will be semi-automatic because they can automatically import data for you and enrich events. Furthermore, they can import this data and enhance events from several platforms. So, this phase, which consists of a Risk Investigate workbook, is used as your initial triage.
Splunk SOAR Examples:
Splunk SOAR Example: Phishing Investigation and Response
A typical phishing email investigation begins with analyzing the initial data and searching for artifacts. Some artifacts to investigate include attachments within the email, phishing links disguised as legitimate URLs, email headers, the sender’s email address, and even the entire email content.
- Splunk SOAR Example: Phishing Investigate and Respond Playbook
In this use case, we will highlight the Phishing Investigate and Respond Playbook, which automatically investigates and contains incoming phishing emails. The Playbook has 15 actions available. Once Splunk SOAR receives a phishing email alert from a third-party source (e.g., fetching email directly from the mail server), it will automatically kick off the Playbook and begin analyzing the following artifacts: file reputation, URL reputation, and Domain Reputation.
Suppose a file, URL, IP address, or domain seems suspicious during the investigation phase. In that case, the Playbook will use the predetermined parameters to decide whether to contain the threat by deleting the email from the user’s inbox.
Splunk SOAR Example: Endpoint Malware Triage
Although endpoint detection and response (EDR) or endpoint protection platform (EPP) tools can help monitor any suspicious activity within endpoints in your organization’s systems, these tools can generate many alerts — some of which could be false positives, while others are legitimate threats.
Fortunately, a SOAR tool can orchestrate decisions and actions to investigate, triage quickly, and respond to this high volume of alerts, filtering out the false positives, determining the risk level, and reacting accordingly.
- Splunk SOAR Example: Crowdstrike Malware Triage Playbook
It enriches the alert detected by Crowdstrike and provides additional context for determining the severity. Once all the information is collected, the analyst will be prompted to review it. Based on the analyst’s choice, the file in question can be added to the custom indicators list in Crowdstrike with a detection policy of “detect” or “none.” The analyst can optionally quarantine the endpoint from the network.
Splunk SOAR Example: Command and Control with Investigation and Containment
- C2 Investigate and Contain Playbook
As soon as an alert for a command-and-control attack surfaces, Splunk SOAR will start the C2 Investigate and Contain Playbook. This Playbook is designed to perform the investigative and potential containment steps to handle a command-and-control attack scenario properly. It will extract file and connection information from a compromised virtual machine, enrich it, and then take containment actions depending on the significance of the data. Significant information includes files with threat scores greater than 50 and IP addresses with reputation status “MALICIOUS,” among other attributes.
Splunk SOAR Example: Alert Enrichment
- Indicators of Compromise
When investigating security alerts, you must first look at the indicators of compromise (IOCs), such as IP address, URL, user name, domain, hash, and other relevant criteria. This helps determine the severity of the alert. Many analysts manually dive into the data to search for additional context or hop between different threat intelligence platforms to gather more information.
- Recorded Future Indicator Enrichment Playbook
The Recorded Future Indicator Enrichment Playbook enriches ingested events that contain file hashes, IP addresses, domain names, or URLs. Contextualizing these details around relevant threat intelligence and IOC helps accelerate the investigation. Recorded Future is a security intelligence platform that provides additional context for analysts to respond to threats faster.
- Recorded Future Correlation Response Playbook
The Recorded Future Correlation Response Playbook gathers more context about the relevant network indicators in response to a Splunk correlation search. Once there’s enough context, the Playbook automatically blocks access upon an analyst’s approval. By comparing traffic monitoring data with Recorded Future bulk threat feeds, Splunk identifies high-risk network connections and forwards them to Splunk SOAR.
Splunk SOAR queries Recorded Future for details about why the network indicators are on the threat list and presents the analyst with a decision about whether the IP address and domain names should be blocked.
This example uses Layer 4 Traffic Monitoring by Cisco WSA as the network monitoring data source. Cisco Firepower NGFW and Cisco Umbrella can enforce blocking actions at the perimeter using DNS sinkholes. Once the analyst can secure the network access via the Recorded Future Correlation Response Playbook, Splunk SOAR can trigger a second playbook to investigate, hunt, and block a URL.
- Zscaler Hunt and Block URL Playbook
When a suspicious URL is detected, the Zscaler Hunt and Block URL Playbook can identify internal devices that have accessed that URL and triage their organizational importance.
Then, depending on the URL’s maliciousness and whether or not the affected device belongs to an executive in the organization, the URL will be blocked, and an appropriate ServiceNow ticket will be created. This Playbook is supported via VirusTotal, Zscaler, Microsoft Exchange, ServiceNow, Splunk, and Carbon Black. Use these pre-built playbooks to help your team save time by tracking down malicious indicators so they can spend more time addressing critical tasks.
Summary: Splunk Security
In today’s ever-evolving digital landscape, ensuring the security of your organization’s data and infrastructure has become paramount. One solution that has gained significant traction is Splunk Security. In this blog post, we will explore Splunk Security’s capabilities and benefits and how it can empower your defense strategy.
Understanding Splunk Security
Splunk Security is a comprehensive platform designed to help organizations monitor, detect, and respond to security threats effectively. Aggregating and analyzing data from various sources provides real-time insights into potential risks and vulnerabilities.
Splunk Security offers many features that enable proactive threat hunting, incident response, and security analytics. From its powerful search and correlation capabilities to its customizable dashboards and visualizations, Splunk Security provides security teams with a holistic view of their environment.
Threat Intelligence Integration
One of Splunk Security’s key strengths is its ability to integrate with external threat intelligence feeds. By leveraging up-to-date threat intelligence data, organizations can enhance their threat detection capabilities and stay ahead of emerging threats.
Automation and Orchestration
Splunk Security offers automation and orchestration capabilities to address the ever-increasing volume and complexity of security incidents. By automating repetitive tasks and orchestrating incident response workflows, security teams can streamline processes and respond to threats more efficiently.
Advanced Analytics and Machine Learning
Splunk Security leverages advanced analytics and machine learning algorithms to identify patterns, anomalies, and potential indicators of compromise. These capabilities enable early detection of threats and provide valuable insights for proactive mitigation strategies.
Conclusion: In conclusion, Splunk Security is a powerful and versatile solution that can significantly enhance your organization’s defense strategy. You can stay one step ahead of cyber threats by leveraging its comprehensive features, integrating threat intelligence, harnessing automation and orchestration, and utilizing advanced analytics. Embrace the power of Splunk Security and fortify your security posture today.
- Fortinet’s new FortiOS 7.4 enhances SASE - April 5, 2023
- Comcast SD-WAN Expansion to SMBs - April 4, 2023
- Cisco CloudLock - April 4, 2023