SASE Visibility with Cisco ThousandEyes
Introduction: In today's rapidly evolving digital landscape, the need for robust network visibility is paramount. As organizations embrace Secure Access Service Edge (SASE) frameworks, ensuring comprehensive visibility becomes even more crucial. In this blog post, we will explore how Cisco ThousandEyes empowers enterprises with enhanced SASE visibility, enabling them to optimize network performance, strengthen security, and elevate user experience.
Matt Conran
The traditional network perimeter has become increasingly obsolete with the rise of cloud applications, mobile workforces, and the proliferation of edge computing. Secure Access Service Edge (SASE) architecture emerges as a holistic approach that combines network security and wide-area networking capabilities. This convergence enables organizations to streamline their network infrastructure while ensuring robust security measures
Table of Contents
Highlights: SASE and Visibility
Proactive Approach
The following post discusses SASE visibility for the Cisco SASE solution, known as Cisco Umbrella SASE with Cisco ThousandEyes. Combining Cisco ThousandEyes with your SASE VPN gives you end-to-end visibility into the SASE security stacks and all network paths, including any nodes. All of these can be consumed from Cisco ThousandEyes, enabling a proactive approach to monitoring your SASE solution, a bundle of components.
Network Visibility
The following post aims to help you gain valuable insights and will guide you into deploying the correct network visibility and Observability into your Cisco SASE solution. Cisco ThousandEyes has several agent deployment models that you can use depending on whether you want visibility into remote workers or users at the branch site or even agent-to-agent testing.
Remember that ThousandEyes is not just for a Cisco SASE solution; it has multiple monitoring use cases, of which Cisco Umbrella SASE is just one. ThousandEyes also has good integrations with Cisco AppDynamics for full-stack end-to-end observability. First, let’s do a quick recap on the SASE definition.
Related: Before you proceed, you may find the following posts helpful:
Cisco Umbrella SASE Key SASE Visibility Discussion Points: |
|
Back to Basics: SASE Visibility
♦ Key Features of SASE Visibility
SASE visibility offers many features that empower organizations to gain deep insights into their network infrastructure. These features include:
1. Real-time Monitoring: SASE visibility solutions continuously monitor network traffic, providing instant visibility into application performance, bandwidth utilization, and network latency.
2. Advanced Analytics: By leveraging sophisticated analytics algorithms, SASE visibility solutions can identify trends, anomalies, and potential threats, enabling proactive network management and security.
3. User Behavior Analysis: SASE visibility allows organizations to understand user behavior patterns, such as application usage, location, and device preferences, enabling personalized experiences and targeted security measures.
SASE Visibility | SASE and Cisco ThousandEyes SASE Visibility
|
Integration with Cisco ThousandEyes
Cisco ThousandEyes, a leading network intelligence platform, seamlessly integrates with SASE visibility, amplifying its capabilities. With this integration, organizations can leverage ThousandEyes’ comprehensive network monitoring and troubleshooting capabilities, combined with SASE visibility’s holistic approach. This collaboration empowers organizations to identify network issues, optimize performance, and ensure a secure and seamless user experience.
The integration of SASE visibility and Cisco ThousandEyes brings forth numerous benefits for organizations, including:
1. Enhanced Network Performance: By combining real-time monitoring and advanced analytics, organizations can identify and resolve performance bottlenecks, ensuring optimal network performance and application delivery.
2. Improved Security: SASE visibility, along with Cisco ThousandEyes, enables organizations to detect and mitigate potential security threats, ensuring robust network security and data protection.
3. Simplified Network Management: The unified approach of SASE visibility and Cisco ThousandEyes simplifies network management, providing a single pane of glass for monitoring, troubleshooting, and security operations.
Example Vendor: Cisco Umbrella SASE
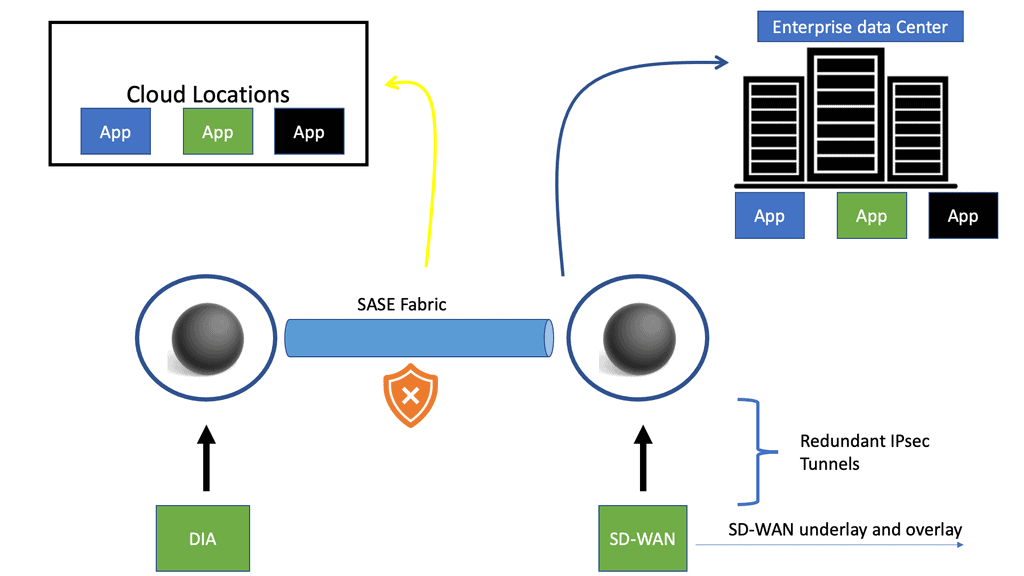
Cisco Umbrella SASE provides recursive DNS services and helps organizations securely embrace direct internet access (DIA). We don’t need to backhaul all traffic to the enterprise data center when applications are hosted in the cloud. There will still be applications hosted in the data center; we can use SD-WAN.
Cisco Umbrella started with DNS security solutions and then moved to include the following features, all delivered from a single cloud security service: So, we have DNS-layer security and interactive threat intelligence, a secure web gateway, firewall, cloud access security broker (CASB) functionality, and integration with Cisco SD-WAN.
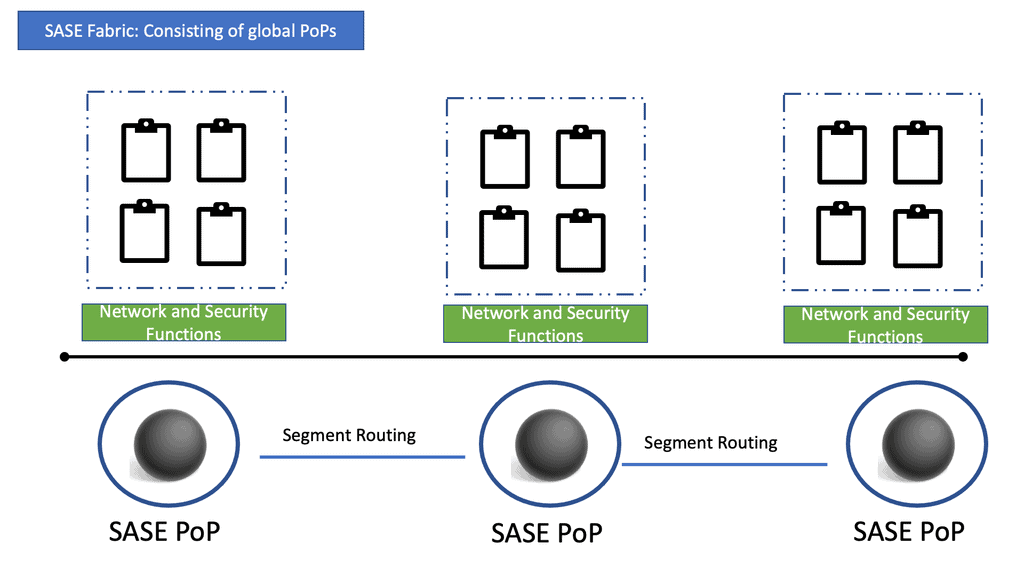
The following diagram shows several Cisco SASE solution PoPs connecting to form a SASE fabric. At each PoP location, we have network and security functions. A viable way to connect PoPs over large distances is with MPLS or Segment Routing.
Understanding MPLS
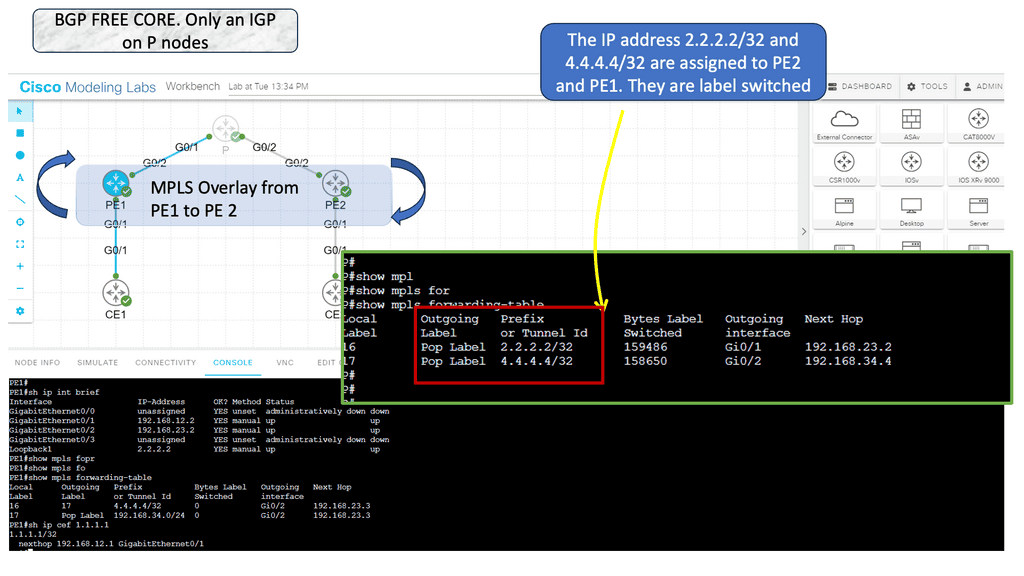
MPLS, short for Multiprotocol Label Switching, revolutionized how network data packets are forwarded. By assigning labels to packets, MPLS enables routers to make forwarding decisions based on these labels rather than examining the packet’s entire header. This label-switching technique improves network efficiency, reduces processing overhead, and enables traffic engineering capabilities.
MPLS forms an overlay, and in the core, everything is label-switched. The core, represented by the P node below, does not need customer routes to assist end-to-end reachability. Now, the core can focus on what is essential to the core: speed. All BGP prefixes are held on the PE nodes.
Exploring Segment Routing
Segment Routing takes a different approach to packet forwarding by leveraging the concept of source routing. Instead of relying on intermediate routers to make forwarding decisions, Segment Routing allows the source node to specify the path the packet should take through the network. This flexibility simplifies network design and enables enhanced traffic engineering, faster convergence, and greater scalability.
Enhanced Traffic Engineering
By leveraging MPLS and Segment Routing, network operators gain precise control over traffic paths, allowing for optimized utilization of network resources. This fine-grained traffic engineering capability enables better load balancing, improved Quality of Service (QoS), and efficient bandwidth allocation.
Scalability and Simplified Network Design
The label-switching nature of MPLS and the source-routing approach of Segment Routing contribute to simplified network architectures and improved scalability. These technologies provide the ability to efficiently handle increasing traffic demands while reducing complexity and operational costs.
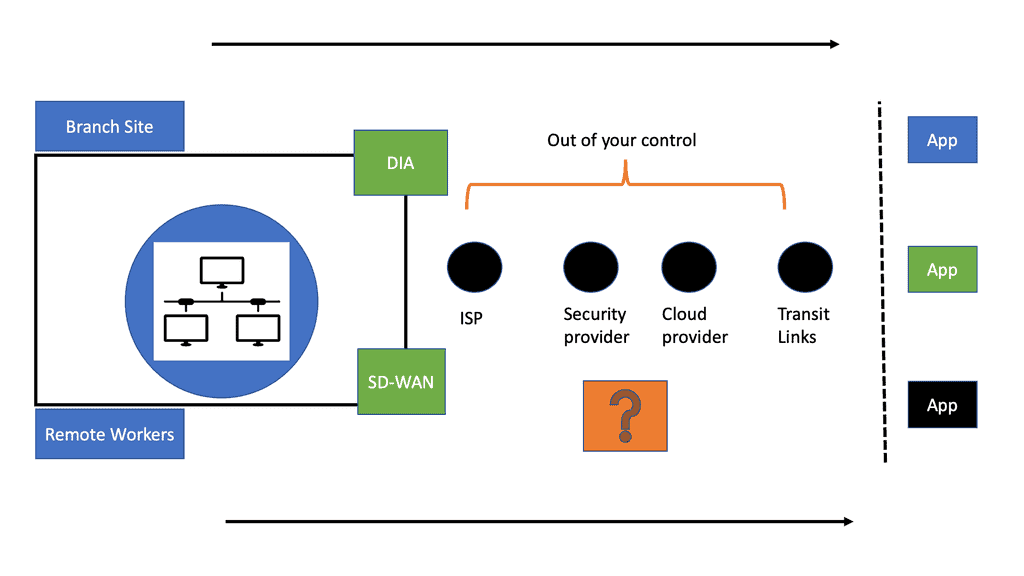
Challenging Landscape: Out of your control
Now that workers are everywhere with an abundance of cloud-based applications, the Internet is the new enterprise network. The perimeter is now moved to the edges, with most devices and components out of their control. And this has many consequences. So how do enterprises ensure digital experience when they no longer own the underlying transport, services, and applications their business relies on?
With these new complex and dynamic deployment models, we now have significant blind spots. Network paths are now much longer than they were in the past. Nothing is just one or two hops away. If you do a traceroute from your SASE VPN client, it may seem like one hop, but it’s much more.
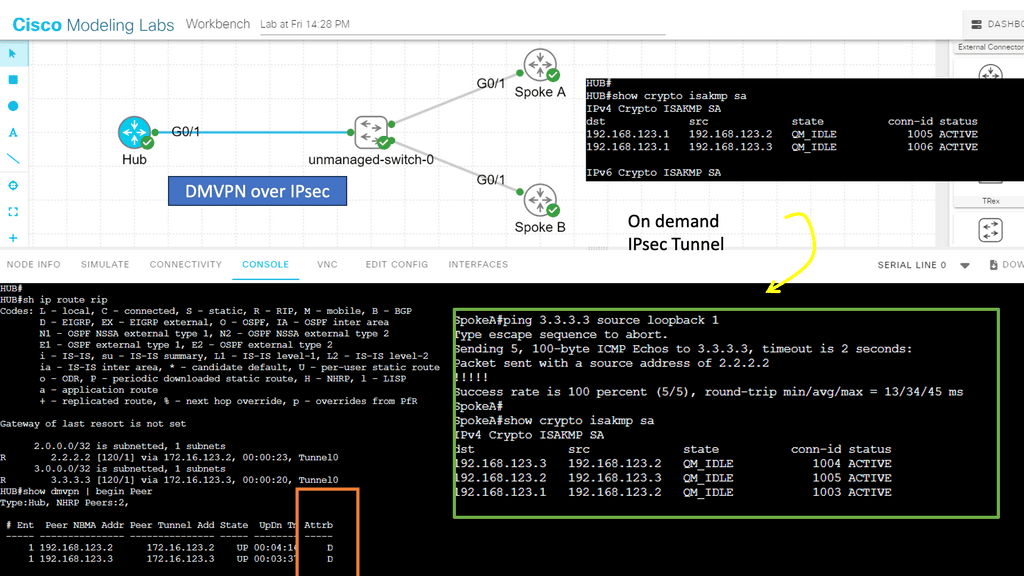
Outside of SASE, VPNs come in many shapes and sizes. In the screenshot below, we have DMVPN and IPsec. DMVPN is a routing technique classified as an overlay network. Does DMVPN have phases, or should we design phases? Below, we have DMVPN phase 3, which enabled spoke-to-spoke on-demand tunnels.
Multiple Segments & Multiple Components
And we have a lot of complexity with multiple segments and different types of components such as the Internet, security providers such as Zscaler, and cloud providers. All of this is out of your control. If I were to put my finger in the air, on average, 80% could be out of my control. So, it would help if you paid immediate attention to some things, such as visibility into the underlay, applications, and service dependencies.
The way forward: Understanding the SASE VPN end-to-end
Firstly, you need to gain visibility into the network underlay. If you do a traceroute, you may see only one hop. Still, it would help if you had insights into every Layer 3 hop across the network underlay, including Layer 2 or firewalling and load-balancing services in the path.
Secondly, you also need to monitor business-critical applications efficiently. And fully understand how users are experiencing an application with full-page loads, metrics that matter most to the users, and multistep transactions beyond an application’s front door. This will include login availability along with the entire application workflow.
It would help if you gained actionable visibility into service dependencies. This will enable you to detect, for example, any service disruptions in ISP networks and DNS providers. See how they impact application availability, response times, and page load performance.
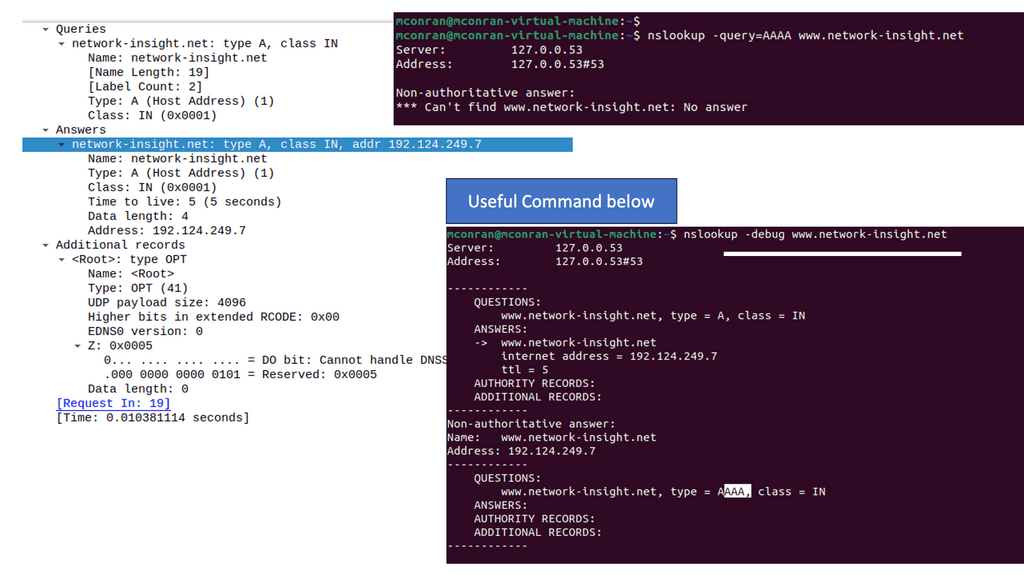
Testing DNS
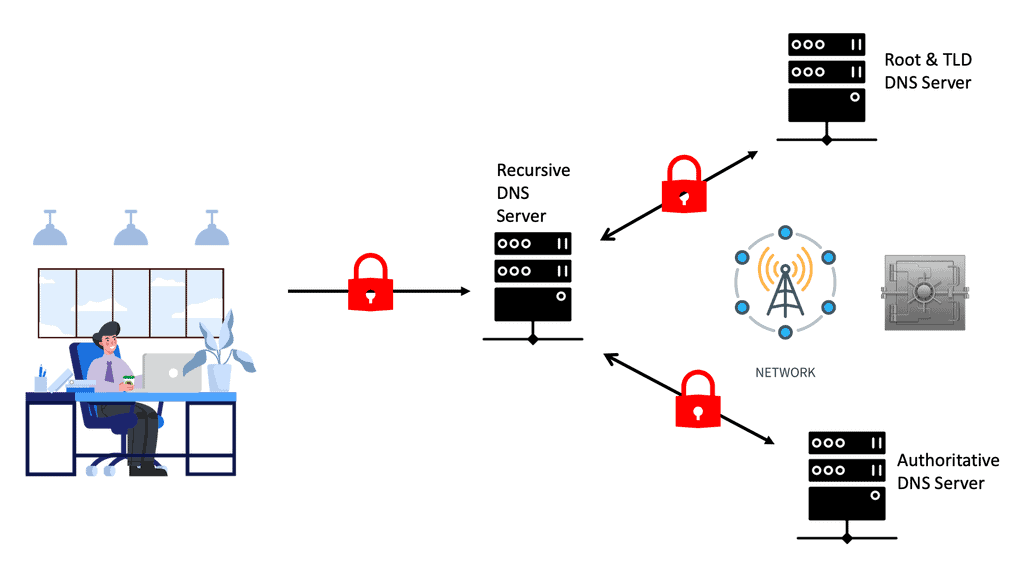
Always test the DNS servers, both internal and external; if this does not work, you will have problems with everything. So, you need to test internal and external domains for the DNS servers that your users are using. Once the transactions start, we will have a DNS process here. You will be familiar with DNS, and it’s something familiar; it developed in early 1980. It is used to manage the mapping between names and numbers.
However, we have a hierarchy of servers involved in the DNS process to support the number of steps in the DNS process. For example, some of these steps would include requesting website information, contacting the recursive DNS servers, querying the authoritative DNS servers, Accessing the DNS record, etc. We must consider the performance of your network’s DNS servers, resolvers, and records. And this can include various vendors across the DNS hierarchy.
The Internet is unstable.
The first issue we have is that the Internet is fragile. We have around 14,000 BGP routing incidents per year. This will include a range of outages and attacks on BGP protocol and peering relationships: Port 179. Border Gateway Protocol (BGP) is the glue of the Internet backbone, so when attacks and outages happen, it can have a rippling effect across different Autonomous Systems (AS). So, if BGP is not stable, which it is not.
Cloud connectivity based on the Internet will not be stable. Internet cloud providers need more stability regarding network performance on the Internet. These providers rely on the public Internet instead of using a private backbone to carry traffic.
BGP has neighbor relationships that operate over TCP port 179. While BGP is essential for internet routing, it is not immune to security vulnerabilities. Attackers can exploit weaknesses in BGP implementations or misuse BGP messages to carry out malicious activities. Unsecured BGP TCP Port 179 can be an entry point for various attacks, including route hijacking, route leaks, and distributed denial-of-service (DDoS) attacks.
Introducing Cisco ThousandEyes
You lose control and visibility when WAN connectivity and business-critical applications migrate to shared infrastructure, the Internet, and public cloud locations. One way to gain back visibility and control is with Cisco ThousandEyes.
Cisco ThousandEyes allows you to monitor your user’s digital experience against software as a service and on-prem applications, regardless of where your users are, through the essential elements of your SASE architecture. SASE is not just one virtual machine (VM) or virtual network function and consists of various technologies or VNFs such as SD-WAN, SWG, VPN, and ZTNA.
Introducing Cisco SASE Solution: Cisco Umbrella SASE
We know the SASE definition and the convergence of networking and security in cloud-native solutions with global PoP. Cisco SD-WAN is a great starting point for your Cisco SASE solution, especially SD-WAN security, which has been mainstream for a while now.
But what would you say about gaining the correct visibility into your SASE model? We have a lot of networking and security functionality now bundled into PoPs, along with different ways to connect to the PoP, whether you are at home or working from the branch office.
So, if you are at home, you will have a VPN client and go directly to Cisco Umbrella SASE. If you are in the Office, you will likely connect to the SASE PoP or on-premise application via Cisco SD-WAN. The SD-WAN merges with the SASE PoP with redundant IPsec tunnels. You can have up to 8 IPsec tunnels with four active tunnels. The automated policy can be set up between Cisco vManage and Cisco Umbrella, so it’s a good interaction.
Cisco Umbrella SASE is about providing secure connectivity to our users and employees. We need to know precisely what they are doing and not just blame the network all the time when there is an issue. Unfortunately, the network is easy to blame, even though it could be something else.
Scenario: Remote Worker: Creating a SASE VPN
Let’s say we have a secure remote worker. They need to access the business application that could be on-premises in the enterprise data center or served in the cloud. So, users will initiate their SASE VPN client to access a VPN gateway for on-premise applications and then land on the corporate LAN. Hopefully, the LAN is tied down with microsegmentation, and the SASE VPN users don’t get overly permissive broad access.
Suppose the applications are served over the Internet in a public cloud SaaS environment. In this case, the user must go through Cisco Umbrella, not to the enterprise data center but to the cloud. You know that Cisco Umbrella SASE will have a security stack such as DNS-layer filtering, CASB, and URL filtering. DNS-layer filtering is the first layer of defense.
SASE VPN: Identity Service
In both cases, working remotely or from the branch office, some Identity services may fall under the zero trust network access (ZTNA) category. Identity services are done with Cisco Duo. CyberArk also has complete identity services.
These identity providers offer identity services such as Single-Sign-On (SSO) and Multi-Factor Authentication (MFA) to ensure users are who they say they are—presenting them with multiple MFA challenges and a seamless experience with SSO via an identity portal.
Out of your control
In both use cases of creating a SASE VPN, we need visibility into several areas out of your control. For example, suppose the user works from home. In that case, we will need visibility into their WiFi network, the secure SASE VPN tunnel to the nearest Umbrella PoP, the transit ISP, and the SASE security functions.
We need visibility into numerous areas, and each region is different. But one thing that they share is that they are all out of our control. Therefore, we must question and gain complete visibility into something out of our control.
We will have similar problems with edge use cases where workers work from branch sites. If these users go to the Internet, they will still use the Cisco Umbrella SASE security stack, but it will go through SD-WAN first.
Monitoring SD-WAN
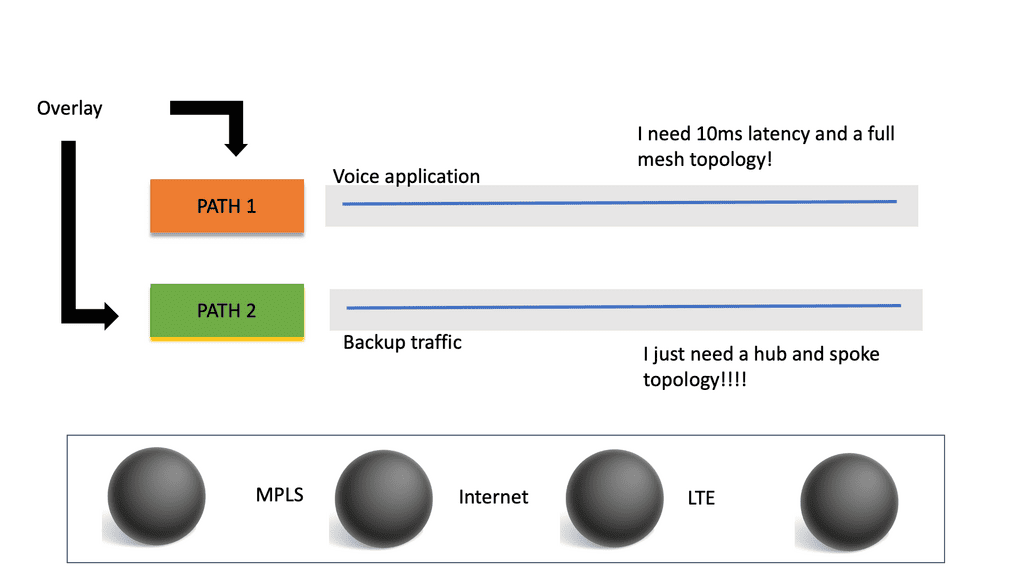
However, there will be another part to monitor, using SD-WAN. So, with SD-WAN, we add another layer of needed visibility into the SD-WAN overlay and underlay. There will be multiple ISPs with multiple components and decades-old equipment for the SD-WAN underlay.
We will have different applications mapped to other overlays for the overlay network—potentially changing on the fly based on performance metrics. The diagram below shows that some application types prefer different paths and network topologies based on performance metrics such as latency.
With SD-WAN, the network overlay is now entirely virtualized, allowing an adaptive, customized network infrastructure that responds to an organization’s changing needs. So when you move to a SASE environment, you are becoming more dependent on an increasing number of external networks and services that you do not own and that traditional tools can’t monitor, resulting in blind spots that will lead to gaps in security and many operational challenges to moving to SASE.
Challenges to the Cisco SASE Solution
When moving to a SASE environment, we face several challenges. Internet blindspots can be an Achilles’ heel to SASE deployments and performance. After all, network paths today consist of many more hops over longer and more complex segments (e.g., Internet, security, and cloud providers) that may be entirely out of the control of IT.
Legacy network monitoring tools are no longer suitable for this Internet-centric environment because they primarily collect passive data from on-premises infrastructure. We also have a lot of complexity and moving parts. Modern applications have become increasingly complex, involving modular architectures distributed across multi-cloud platforms. Not to mention a complex web of interconnected API calls and third-party services.
As a result, understanding the application experience for an increasingly remote and distributed workforce is challenging—and siloed monitoring tools fail to provide a complete picture of the end-to-end experience.
Cisco ThousandEyes: Different Vantage Points.
Cisco ThousandEyes provides visibility end-to-end across your SASE environment. It allows you to be proactive and see problems before they happen, reducing your time to resolution. Remember that today, we have a complex environment with many new and unpredictable failure modes. Having the correct visibility lets you control the known and unknown failure modes.
Cisco ThousandEyes can also give you actionable data. For example, when service degradation occurs, you can quickly identify where the problem is. So, your visibility will need to be actionable. To gain actionable visibility, you need to monitor different things from different levels. One way to do this is with different types of agents.
Using a global collective of cloud, enterprise, and end-user vantage points, ThousandEyes enables organizations to see any network, including those belonging to Internet and cloud providers, as if it were their own—and to correlate this visibility with application performance and employee experience.
From Thousand Eyes’ different vantage points, which are based on deploying agents, we can see the layer 3 hop-by-hop underlays from remote users and SD-WAN sites to secure edge and from secure edge to application servers SaaS application performance, including monitoring login availability and application workflows, service dependency monitoring, including secure edge PoP, and DNS servers.
Example of an Issue: HTTP Response Time
That’s quite a lot of areas to grasp. So, let’s say you are having performance issues with Office365, and the response time has increased. First, you would notice an increase in HTTP response time from a specific office. The next stage would be to examine the network layer and see an increase in latency. So, in this case, we have network problems.
Then, you can go deeper into the problem using the packet visualization Cisco ThousandEyes offers to pinpoint precisely where it is happening. The packet visualization shows you the exact path of the Office to the Internet via Umbrella. It provides all the legs of the Internet and can pinpoint the problem to the specific device. So now we have end-to-end visibility via this remote worker right to the application.
Cisco ThousandEyes agents
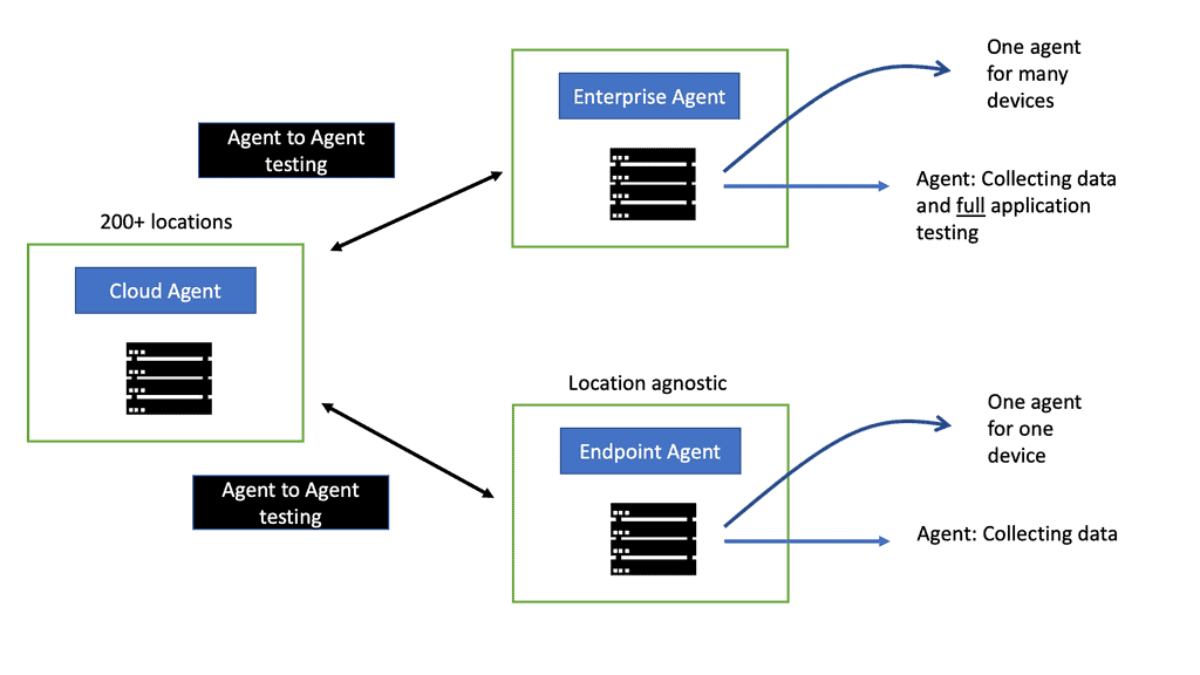
Endpoint Agent
The secure remote worker could be on the move and working from anywhere. In this case, you need the ThousandEyes Endpoint agent. The Endpoint agent performs active application and network performance tests and passively collects performance data, such as WiFi and device-level metrics like CPU and memory.
It also detects and monitors any SASE VPN, other VPN gateways, and proxies. The most crucial point to note about the Endpoint agent is that it follows the user regardless of where they work. The branch office or the remote locations. The endpoint agent is location agnostics. However, creating a baseline for users with this type of movement will be challenging.
The endpoint agent, by default, does some passive monitoring. WiFi performance is a metric that always sees the percentage of retransmitted packets that would indicate a problem occurring. If the user is working from home and saying this application is not working, you can tell if the WiFi is now working and ask them to carry out the necessary troubleshooting if the issue is at their end.
The endpoint agent also automatically performs default gateway networking testing. This is synthetic network testing using the default gateway. Remote working has an extensive internal network, so you can map it out and help them troubleshoot.
They can test the underlay network to the VPN termination points. So, if you are on a VPN, you have one hop! But if you need to determine any packet loss, etc., you must see the exact underlay. The underlay testing can tell you if there is a problem with the upstream ISP or the VPN termination points.
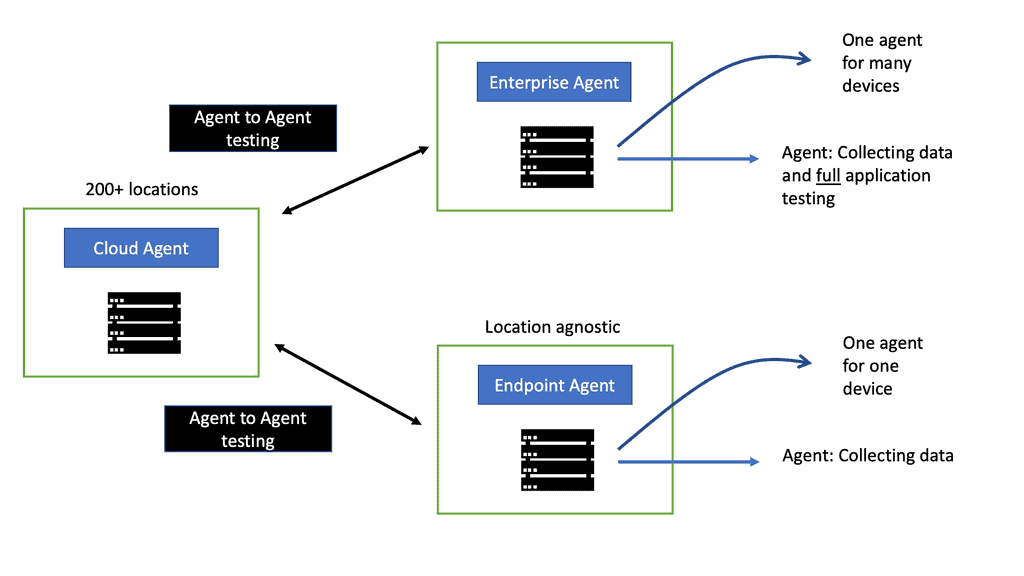
Enterprise Agent Testing
The Enterprise agent is set up from the Endpoint agent. The Enterprise agent has, on top of it, complete application testing. Unlike the endpoint agents, it can do page load testing. Using Webex, you can set up the RTP tests for the agent running in the various WebEx data centers.
Then, we have the secure edge design, where the users work from a branch office. This is where we have an Enterprise agent—one agent from all users working in the Office. So, one agent for all users and devices in the LAN can be installed on several device types—for example, Cisco Catalyst 8000 or ISR 4000 series. Or if you can’t install it on a Cisco device, you can install it as a Docker container or in a smaller office; you can deploy it on a Raspberry PI.
Network Performance Testing
It performs active application and network performance testing, similar to the Endpoint agent. But one main difference is that it can perform complex web application tests. The Enterprise agent has a fully-fledged browser on top of it, and it can open up a web application, download images needed to load the page load event, and log in to the application.
This is an essential test for the zero trust network access (ZTNA) category, as it supports complete web testing for applications beyond SSO. It can also test VPN and the SDN overlay and underlay. In addition, it provides a continuous baseline regardless of any active users. The baseline is 24/7, and you can immediately know if there are problems. This is compared to the Endpoint agent, which can’t provide a baseline due to choppy data.
Cisco ThousandEyes also has a Cloud agent that can augment the Enterprise agent. The Cloud agent is installed on over 200 worldwide locations and is also in WebEx data centers. Consider the cloud agent to increase the enterprise agent. It allows you to do two-way networking and bidirectional testing. Here, we can test agent to agent.
- SD-WAN Underlay Visibility
The enterprise agent can also test the SD-WAN underlay. In the underlay testing, you can configure some data policies and allow the network test to go into the underlay and even test the Umbrella IPsec Gateway or the SD-WAN router in the data center, which gives you hop-by-hop insights into the underlay.
- Device Layer Visibility
We also have device layer visibility. Here, we have visibility into the performance of the secure edge internal devices by gathering network device topology. This will show you all the Layer three nodes in your network, firewall, load balancer, and other Layer 2 devices.
AppDynamic and ThousandEye Integration
While most organizations cannot respond to 3rd party connectivity issues, ThousandEyes can give you the correct Observability into every application and service and track the network traffic hops inside and outside, including all your environments. If you want or need to go one step further, you can integrate Thousand Eye with AppDynamic and see your business transactions in detail.
Summary: SASE and Visibility
In today’s digital landscape, the demand for secure and efficient network connectivity is higher than ever. With the rise of remote work and cloud adoption, organizations are turning to Secure Access Service Edge (SASE) solutions to streamline their network infrastructure. Cisco Thousandeyes emerges as a powerful tool in this realm, offering enhanced visibility and control. In this blog post, we explored the key features and benefits of Cisco Thousandeyes, shedding light on how it can revolutionize SASE visibility.
Section 1: Understanding SASE Visibility
To grasp the importance of Cisco Thousandeyes, it’s crucial to comprehend the concept of SASE visibility. SASE visibility refers to monitoring and analyzing network traffic, performance, and security across an organization’s network infrastructure. It provides valuable insights into user experience, application performance, and potential security threats.
Section 2: The Power of Cisco Thousandeyes
Cisco Thousandeyes empowers organizations with comprehensive SASE visibility that extends across the entire network. By leveraging its advanced monitoring capabilities, businesses gain real-time insights into network performance, application behavior, and end-user experience. With Thousandeyes, IT teams can identify and troubleshoot issues faster, ensuring optimal network performance and security.
Section 3: Key Features and Functionalities
In this section, we will delve into the key features and functionalities offered by Cisco Thousandeyes. These include:
1. Network Monitoring: Thousandeyes provides end-to-end visibility, allowing organizations to monitor their network infrastructure from a single platform. It tracks network performance metrics, such as latency, packet loss, and jitter, enabling proactive issue resolution.
2. Application Performance Monitoring: With Thousandeyes, businesses can gain deep insights into application performance across their network. IT teams can identify bottlenecks, optimize routing, and ensure consistent application delivery to enhance user experience.
3. Security Monitoring: Cisco Thousandeyes offers robust security monitoring capabilities, enabling organizations to detect and mitigate potential threats. It provides visibility into network traffic, identifies anomalies, and facilitates rapid incident response.
Section 4: Integration and Scalability
One of the significant advantages of Cisco Thousandeyes is its seamless integration with existing network infrastructure. It can integrate with various networking devices, cloud platforms, and security tools, ensuring a cohesive and scalable solution. This flexibility allows businesses to leverage their current investments while enhancing SASE visibility.
Conclusion:
In conclusion, Cisco Thousandeyes proves to be a game-changer in SASE visibility. Its comprehensive monitoring capabilities empower organizations to optimize network performance, ensure application reliability, and enhance security posture. By embracing Cisco Thousandeyes, businesses can journey toward a more efficient and secure network infrastructure.
- DMVPN - May 20, 2023
- Computer Networking: Building a Strong Foundation for Success - April 7, 2023
- eBOOK – SASE Capabilities - April 6, 2023