Blog
Network Insight.
- Premium Consultancy, Ebooks, Videos and Elearning
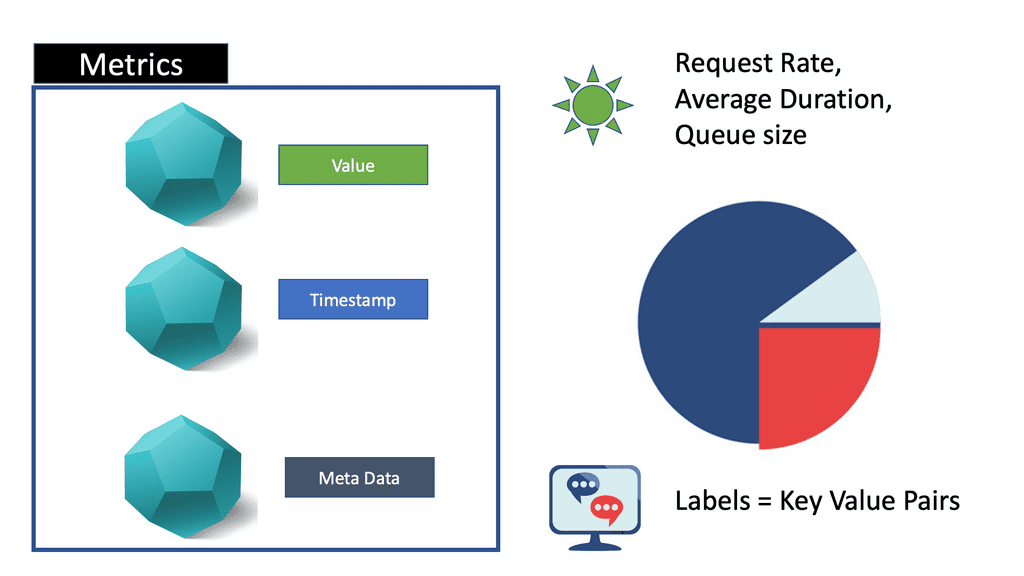
Auto Scaling Observability
Autoscaling Observability In today’s digital landscape, where applications and systems are becoming increasingly complex and dynamic, the need for efficient auto scaling observability has never been more critical. This blog post will delve into the fascinating world of auto scaling observability, exploring its importance, key components, and best practices. Let’s …
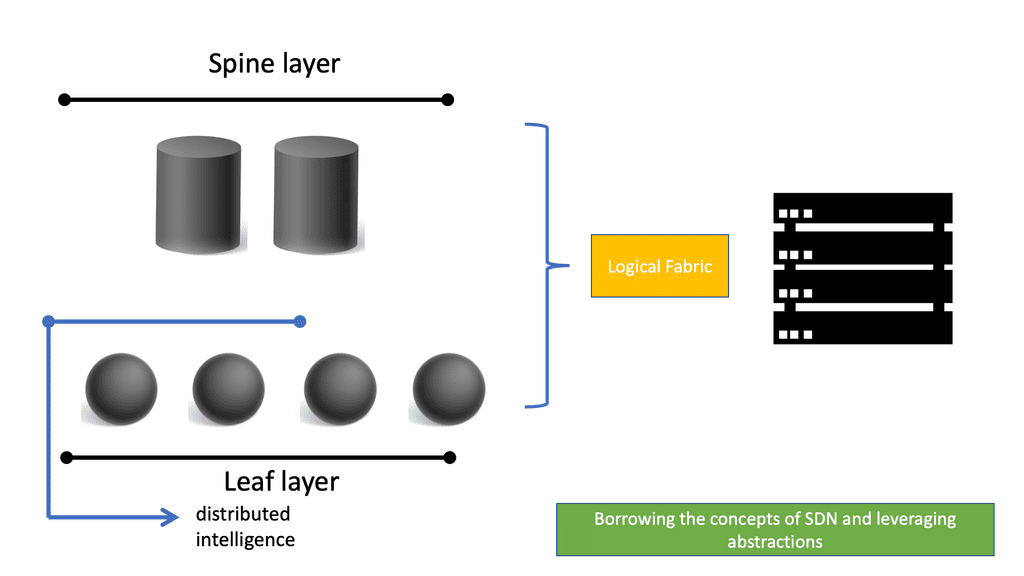
ACI Networks
ACI Networks ACI networks, short for Application Centric Infrastructure networks, have emerged as a game-changer in the realm of connectivity. With their innovative approach to networking architecture, ACI networks have opened up new possibilities for businesses and organizations of all sizes. In this blog post, we will explore the key …
Service Level Objectives (SLOs): Customer-centric view
Service Level Objectives (SLOs) In today’s rapidly evolving digital landscape, businesses are increasingly reliant on technology to deliver their products and services. To ensure a seamless user experience, organizations set specific performance targets known as Service Level Objectives (SLOs). This blog post will delve into the importance of SLOs, their …
Observability vs Monitoring
Observability vs Monitoring In today’s fast-paced digital landscape, where complex systems and applications drive businesses, it’s crucial to have a clear understanding of observability and monitoring. These two terms are often used interchangeably, but they represent distinct concepts in the realm of system management and troubleshooting. In this blog post, …
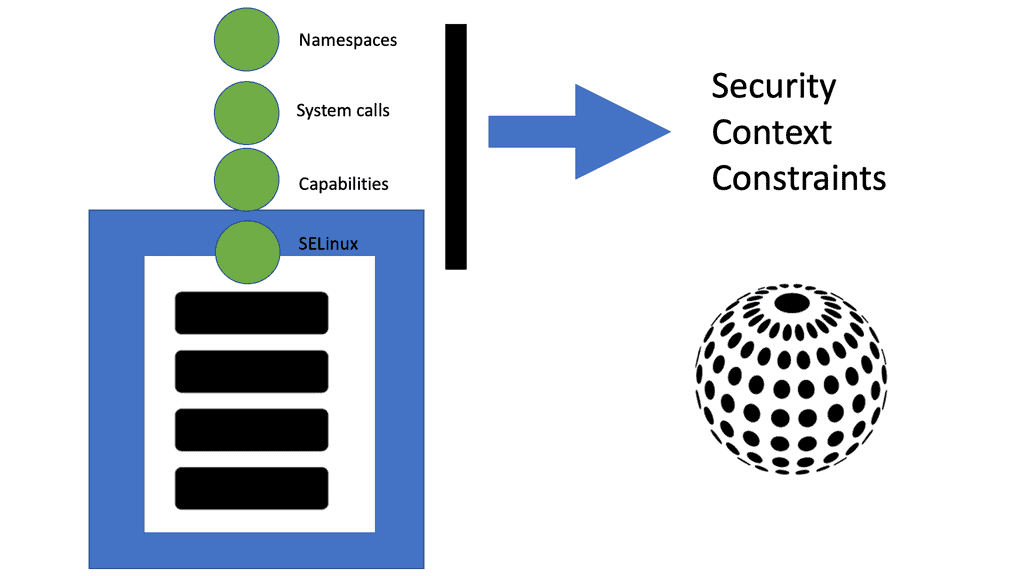
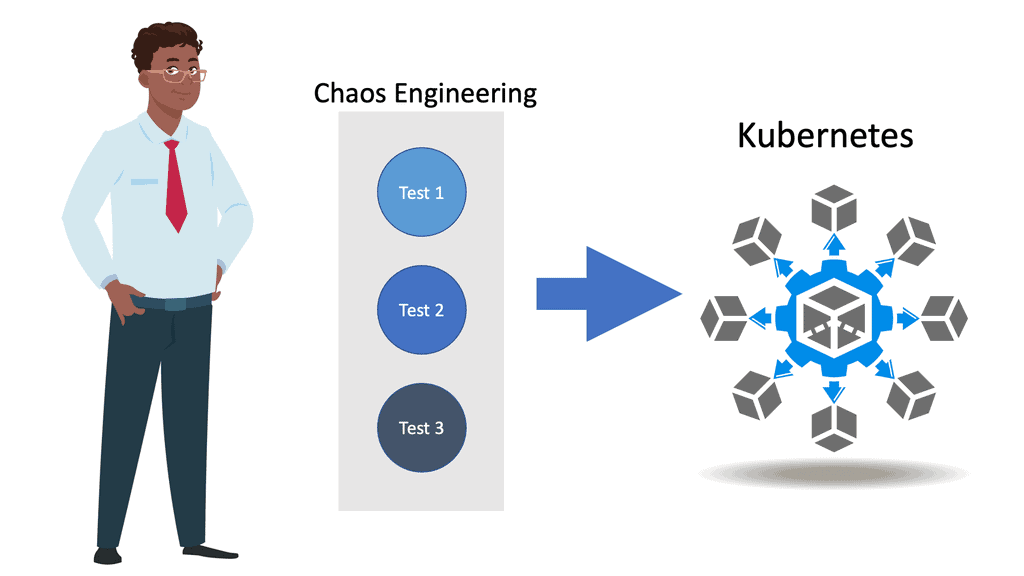
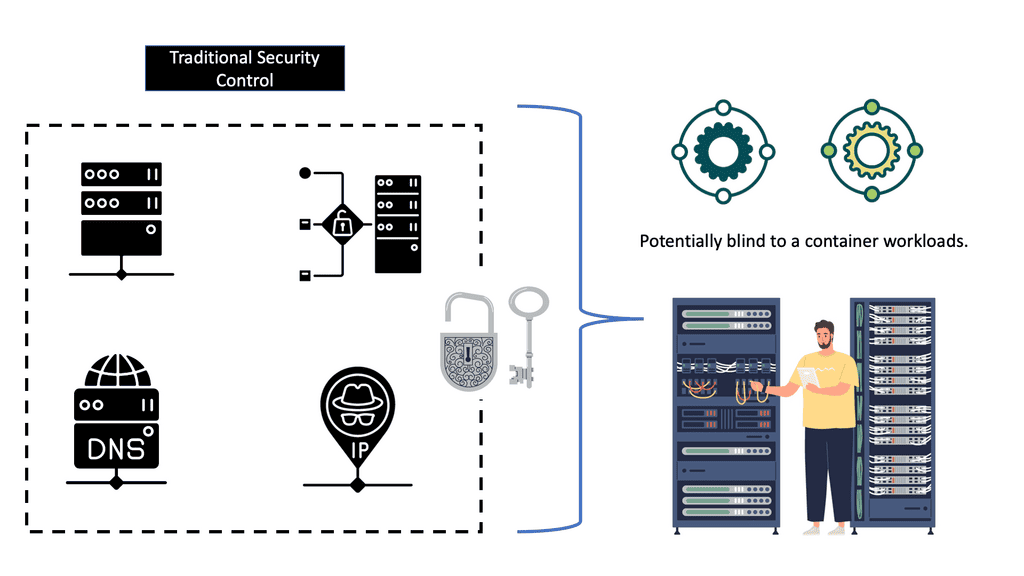
OpenShift Security Best Practices
OpenShift Security Best Practices In today’s digital landscape, security is of utmost importance. This is particularly true for organizations utilizing OpenShift, a powerful container platform. In this blog post, we will explore the best practices for OpenShift security, ensuring that your deployments are protected from potential threats. Container Security: Containerization …
Distributed Systems Observability
Distributed Systems Observability In the realm of modern technology, distributed systems have become the backbone of numerous applications and services. However, the increasing complexity of such systems poses significant challenges when it comes to monitoring and understanding their behavior. This is where observability steps in, offering a comprehensive solution to …
Reliability In Distributed System
Reliability In Distributed System Distributed systems have become an integral part of our modern technological landscape. Whether it’s cloud computing, internet banking, or online shopping, these systems play a crucial role in providing seamless services to users worldwide. However, as distributed systems grow in complexity, ensuring their reliability becomes increasingly …
Baseline Engineering
Baseline Engineering In today’s fast-paced digital landscape, network performance plays a vital role in ensuring seamless connectivity and efficient operations. Network baseline engineering is a powerful technique that allows organizations to establish a solid foundation for optimizing network performance, identifying anomalies, and planning for future scalability. In this blog post, …
Docker Security Options
Docker Security Options In the ever-evolving world of containerization, Docker has emerged as a leading platform for deploying and managing applications. As the popularity of Docker continues to grow, so does the importance of securing your containers and protecting your valuable data. In this blog post, we will delve into …
Safe-T SDP- Why Rip and Replace your VPN?
SDP VPN Although organizations realize the need to upgrade their approach to user access control, deploying existing technologies is holding back the introduction of Software Defined Perimeter (SDP). A recent Cloud Security Alliance (CSA) report on the “State of Software-Defined Perimeter” states that existing in-place security technologies are …
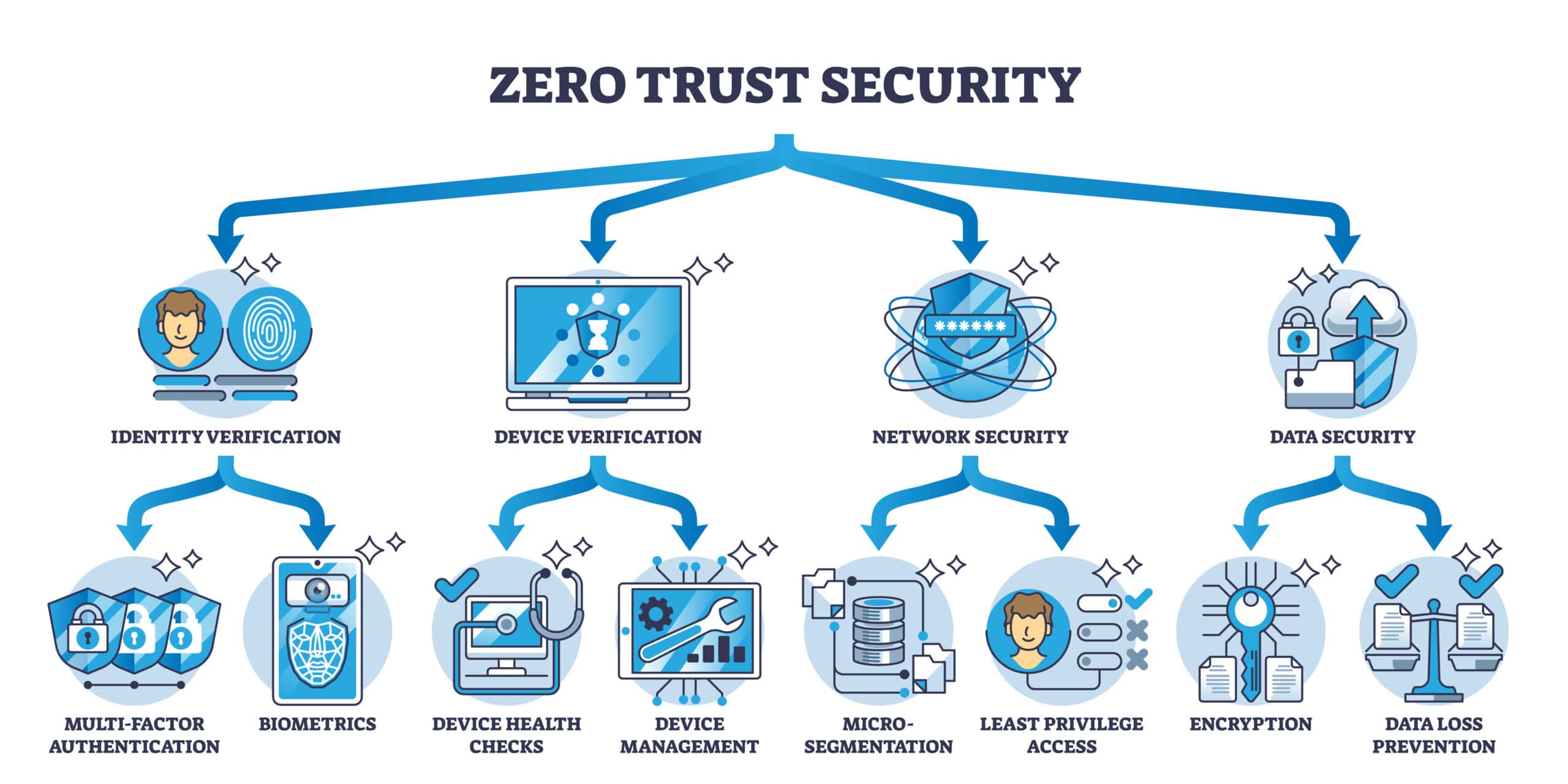
Safe-T; A Progressive Approach to Zero Trust Access
Zero Trust SDP The foundations that support our systems are built with connectivity, not security, as an essential feature. TCP connects before it authenticates. Security policy and user access based on IP lack context and allow architectures with overly permissive access. This will likely result in a brittle …
Remote Browser Isolation
Remote Browser Isolation In today’s digital landscape, where cyber threats continue to evolve at an alarming rate, businesses and individuals are constantly seeking innovative solutions to safeguard their sensitive information. One such solution that has gained significant attention is Remote Browser Isolation (RBI). In this blog post, we will explore …