Removing State From Network Functions
In recent years, the networking industry has witnessed a significant shift towards stateless network functions. This revolutionary approach has transformed the way networks are designed, managed, and operated. In this blog post, we will explore the concept of removing state from network functions and delve into the benefits it brings to the table.
State in network functions refers to the information that needs to be stored and maintained for each connection or flow passing through the network. Traditionally, network functions such as firewalls, load balancers, and intrusion detection systems heavily relied on maintaining state. This stateful approach introduced complexities and limitations in terms of scalability, performance, and fault tolerance.
Stateless network functions, on the other hand, operate without the need for maintaining connection-specific information. Instead, they process packets or flows independently, solely based on the information present in each packet. This paradigm shift eliminates the burden of state management, enabling networks to scale more efficiently, achieve higher performance, and exhibit enhanced resiliency.
Enhanced Scalability: By removing state from network functions, networks become inherently more scalable. Stateless functions allow for easier distribution and parallel processing, empowering networks to handle increasing traffic demands without being limited by state management overhead.
Improved Performance: Stateless network functions offer improved performance compared to their stateful counterparts. Without the need to constantly maintain state information, these functions can process packets or flows more quickly, resulting in reduced latency and improved overall network performance.
Enhanced Fault Tolerance: Stateless network functions facilitate fault tolerance by enabling easy redundancy and failover mechanisms. Since there is no state to be replicated or synchronized, redundant instances can seamlessly take over in case of failures, ensuring uninterrupted network services.
Conclusion: The removal of state from network functions has revolutionized the networking landscape. Stateless network functions bring enhanced scalability, improved performance, and enhanced fault tolerance to networks, enabling them to meet the ever-increasing demands of modern applications and services. Embracing this paradigm shift paves the way for more agile, efficient, and resilient networks that can keep up with the rapid pace of digital transformation.
Matt Conran
Highlights: Removing State From Network Functions
The Role of Non-Proprietary Hardware
We have seen a significant technological evolution where network functions can run in software on non-proprietary commodity hardware, whether a grey box or white box deployment model. Taking network functions from a physical appliance and putting them into a virtual appliance is only half the battle.
The move to software provides the on-demand elastically and scale of network security components and quick recovery from failures. However, we are still hindered by one major factor – the state that each network function needs to process.
The Tights Coupling of State
We still face challenges created by the tight coupling of the state and processing for each network function, be it virtual firewalls, load balancer scaling, intrusion protection system (IPS), or even distributed firewalls closer to the workloads for dynamic workload scaling use cases. Having the state tightly coupled with the network functions limits the network functions’ agility, scalability, and failure recovery.
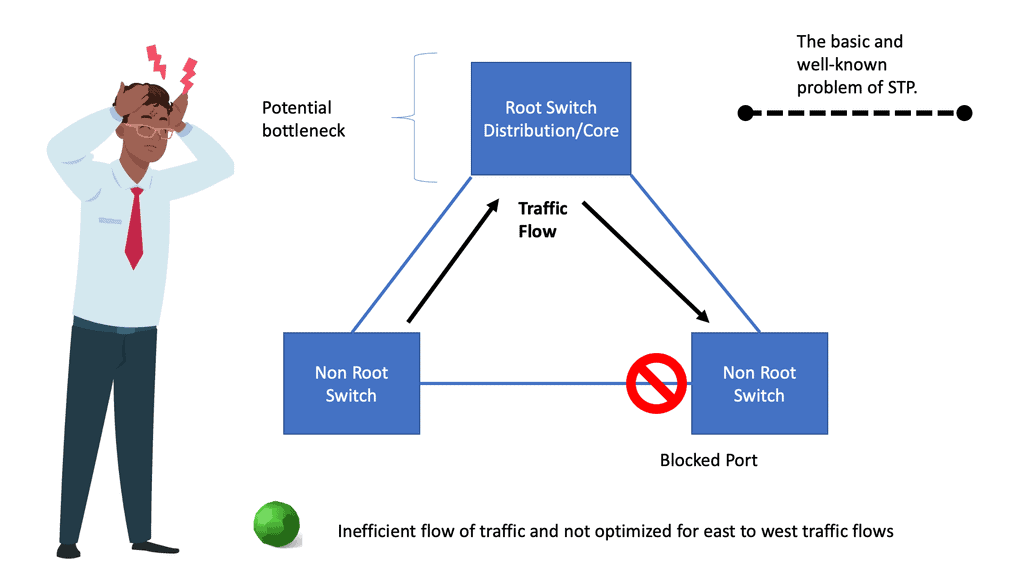
Compounded by this, we have seen an increase in network complexity. The rise of the public cloud and the emergence of hybrid and multi-cloud has made data center connectivity more complicated and critical than ever.
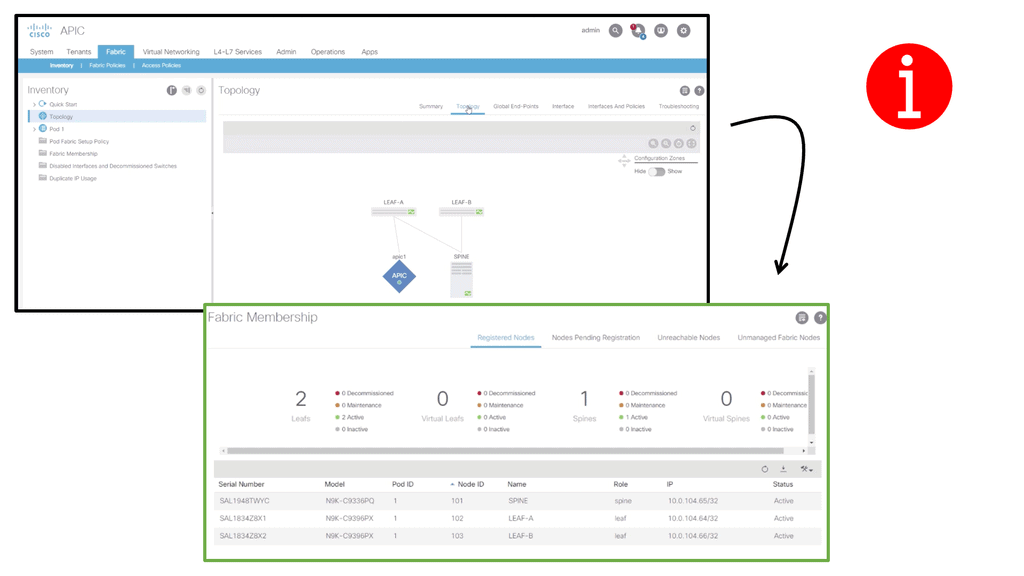
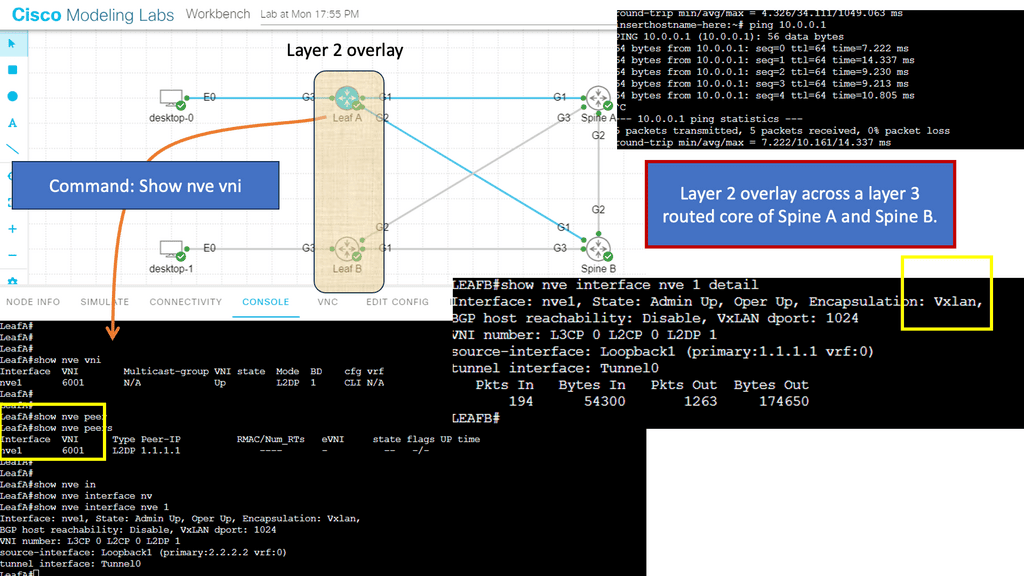
Network Functions. Key Network Functions Discussion points: |
|
For pre-information, you may find the following helpful:
A Key Point: Knowledge Check |
Back to basics with Network Functions
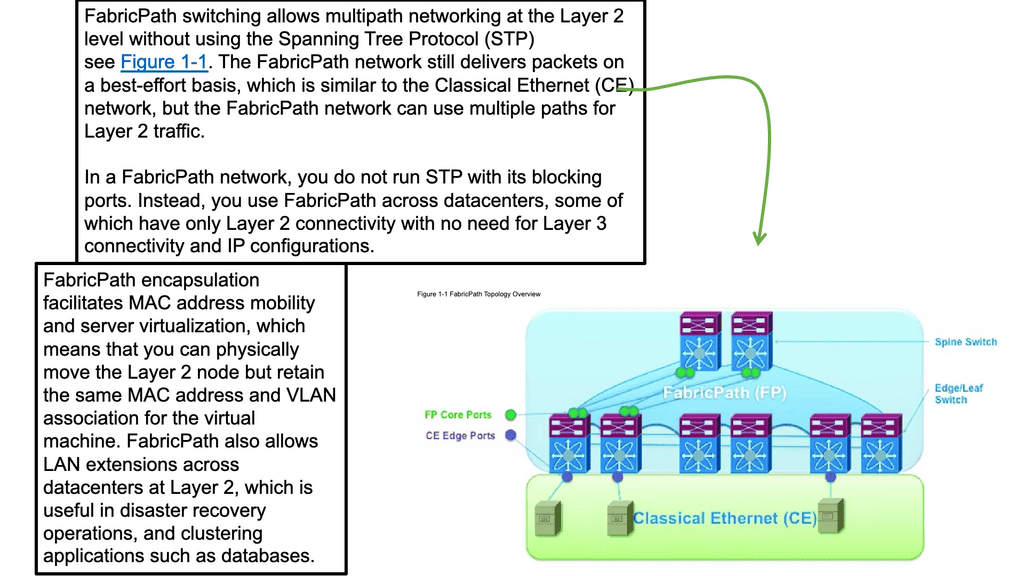
Virtualization
Virtualization (which generally indicates server virtualization when used as a standalone phrase) refers to the abstraction of the application and operating system from the hardware. Similarly, network virtualization is the abstraction of the network endpoints from the physical arrangement of the network. In other words, network virtualization permits you to group or arrange endpoints on a network independent from their physical location.
Network Virtualization refers to forming logical groupings of endpoints on a network. In this case, the endpoints are abstracted from their physical locations so that VMs (and other assets) can look, behave, and be managed as if they are all on the same physical segment of the network.
Importance of Network Functions:
Network functions are the backbone of modern communication systems, making them essential for businesses, organizations, and individuals. They provide the necessary infrastructure to connect devices, transmit data, and facilitate the exchange of information reliably and securely. Without network functions, our digital interactions, such as accessing websites, making online payments, or conducting video conferences, would be nearly impossible.
Types of Network Functions:
1. Routing: Routing functions enable forwarding data packets between different networks, ensuring that information reaches its intended destination. This process involves selecting the most efficient path for data transmission based on network congestion, bandwidth availability, and network topology.
2. Switching: Switching functions allow data packets to be forwarded within a local network, connecting devices within the same network segment. Switches efficiently direct packets to their intended destination, minimizing latency and optimizing network performance.
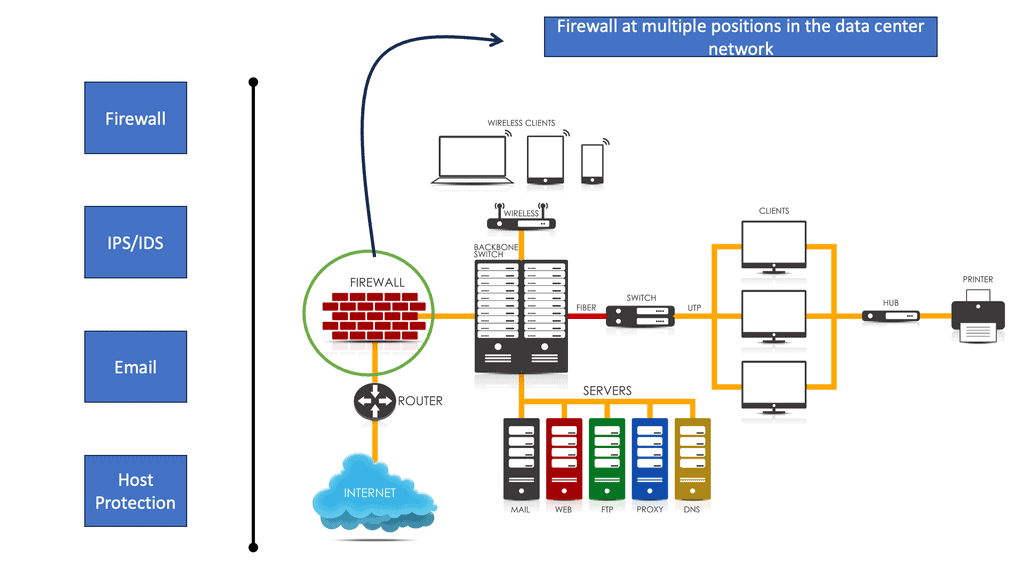
3. Firewalls: Firewalls act as barriers between internal and external networks, protecting against unauthorized access and potential security threats. They monitor incoming and outgoing traffic, filtering and blocking suspicious or malicious data packets.
4. Load Balancing: Load balancing distributes network traffic across multiple servers to prevent overloading and ensure optimal resource utilization. Load balancing enhances network performance, scalability, and reliability by evenly distributing workloads.
5. Network Address Translation (NAT): NAT allows multiple devices within a private network to share a single public IP address. It translates private IP addresses into public ones, enabling communication with external networks while maintaining the security and privacy of internal devices.
6. Intrusion Detection Systems (IDS): IDS monitors network traffic for any signs of intrusion or malicious activity. They analyze data packets, identify potential threats, and generate alerts or take preventive actions to safeguard the network from unauthorized access or attacks.
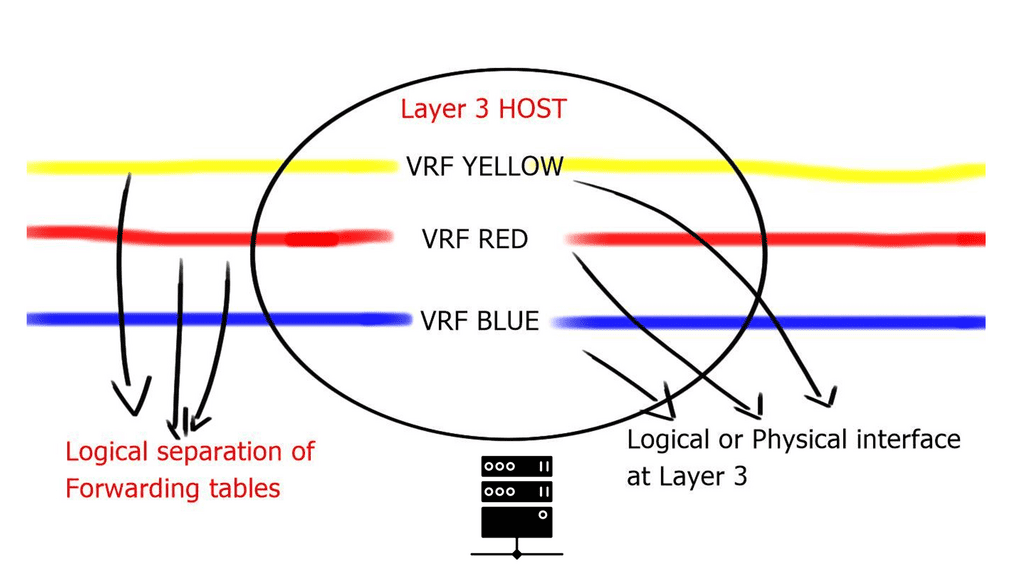
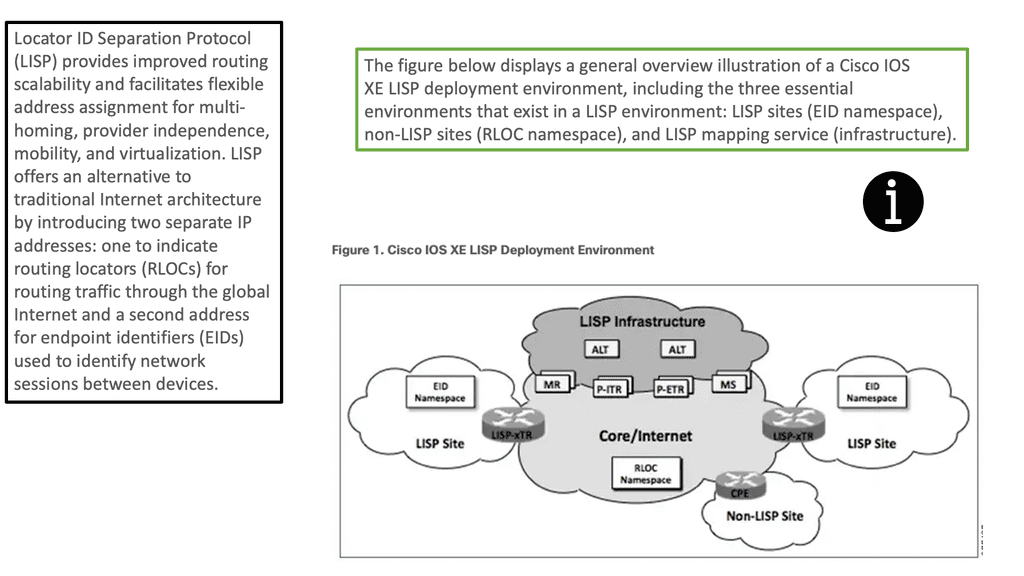
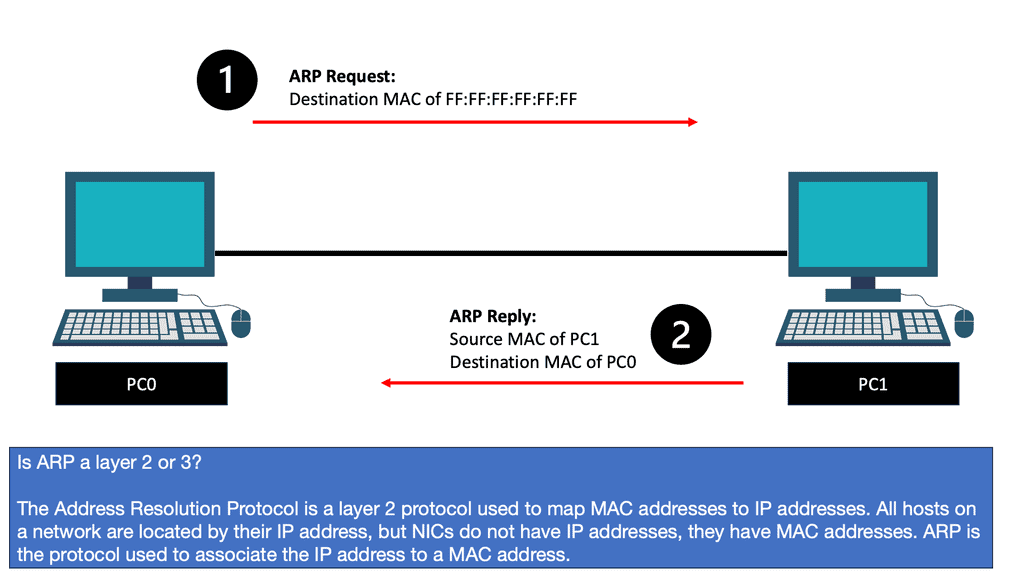
What is State
Before we delve into potential ways to solve this problem, mainly by introducing stateless network functions, let us first describe the different types of state. We have two: dynamic and static. The network function processes continuously update the dynamic state, which could be anything from a firewall’s connection information to the load balancer’s server mappings.
On the other hand, the static state could include something like pre-configured firewall rules or the IPS signature database. The dynamic state must persist across instance failures and be available to the network functions when scaling in or out. On the other hand, the static state is easy and can be replicated to a network instance upon boot time.
Stateless network functions
Stateless Network Functions are a new and disruptive technology that decouples the design of network functions into a stateless process component and a data store layer. An orchestration layer that can monitor the network function instances for load and failure and adjust the number of instances accordingly is also needed.
Taking or decoupling the state from a network function enables a more elastic and resilient infrastructure. So how does this work? From a 20,000 bird’s eye view, the network functions become stateless. The statefulness of the application, such as a stateful firewall, is maintained by storing the state in a separate data store. The data store provides the resilience of the state. No state is stored on the individual networking functions themselves.
Datastore example
The data store can be, for example, RAMCloud. RAMCloud is a distributed key-value storage system with high-speed storage for large-scale applications. It is designed for many servers needing low-latency access to a durable data store. RAMCloud is suitable for low-latency access as it’s based primarily on DRAM. RAMCloud keeps all data in DRAM. As a result, the network functions can read RAMCloud objects remotely over the network in as little as 5μs.
Stateless network functions advantages.
Stateless network functions may not be helpful for all but are valid for standard network functions that can be re-designed statelessly. Stateful network functions are useful for a stateful firewall, intrusion prevention system, network address translator, and load balancer. Removing the state and placing it on a database brings many advantages to network management.
As the state is accessed via a data store, a new instance can be launched, and traffic is immediately directed to it, offering elasticity. Secondly, resilience, a new instance, can be spawned instantaneously upon failure. Finally, as any instance can handle an individual packet, packets traversing different paths do not have asymmetric and multi-path routing issues.
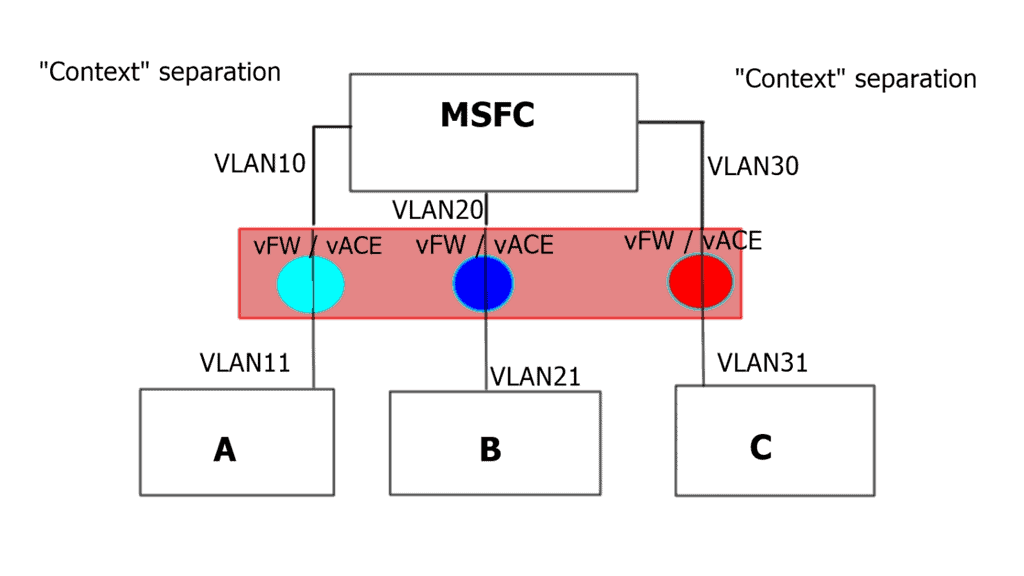
Problems with having state: Failure
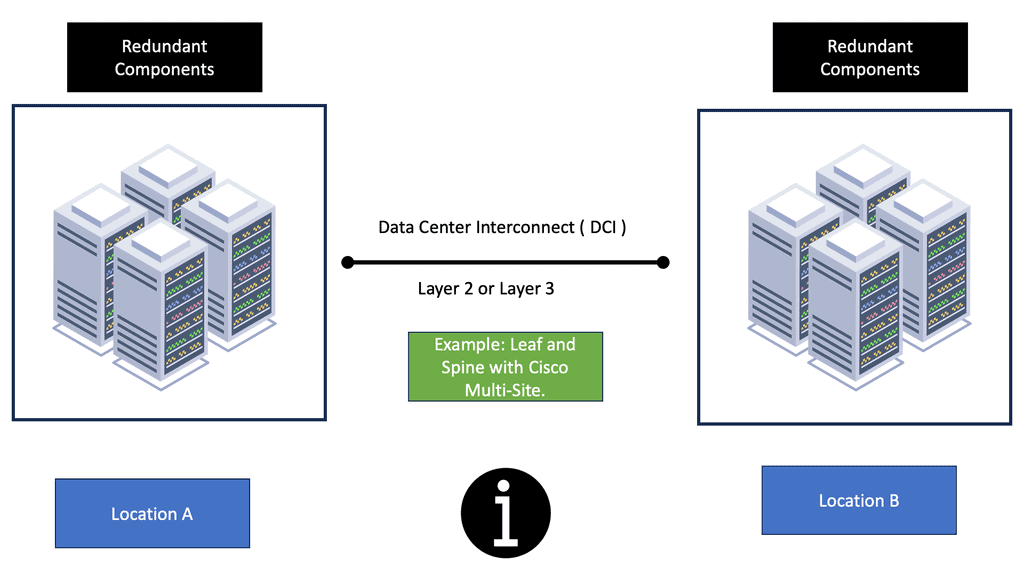
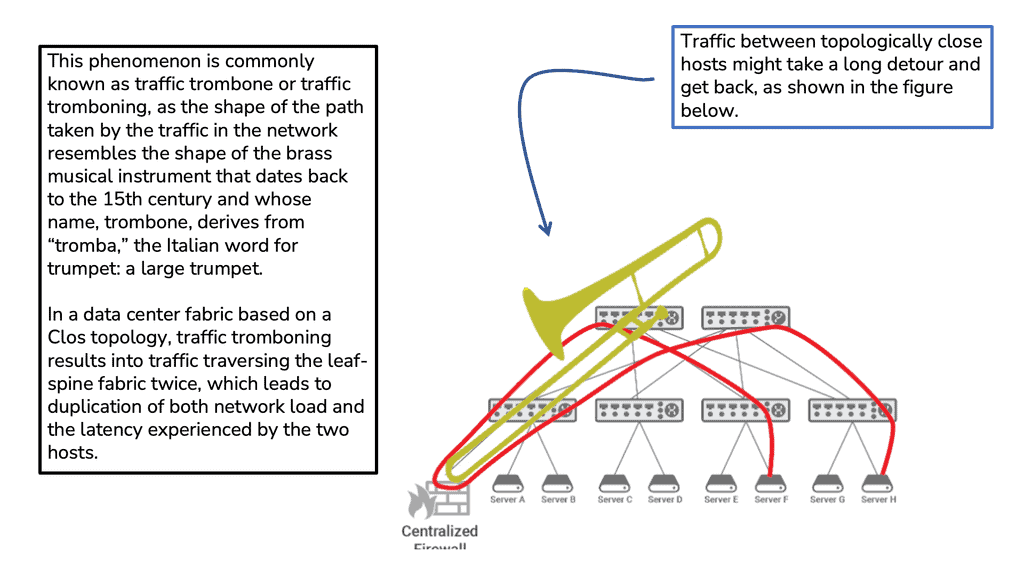
The majority of network designs have redundancy built-in. It sounds easy when one data center fails to let the secondary take over. When the data center interconnect (DCI) is configured correctly, everything should work upon failover, correct?
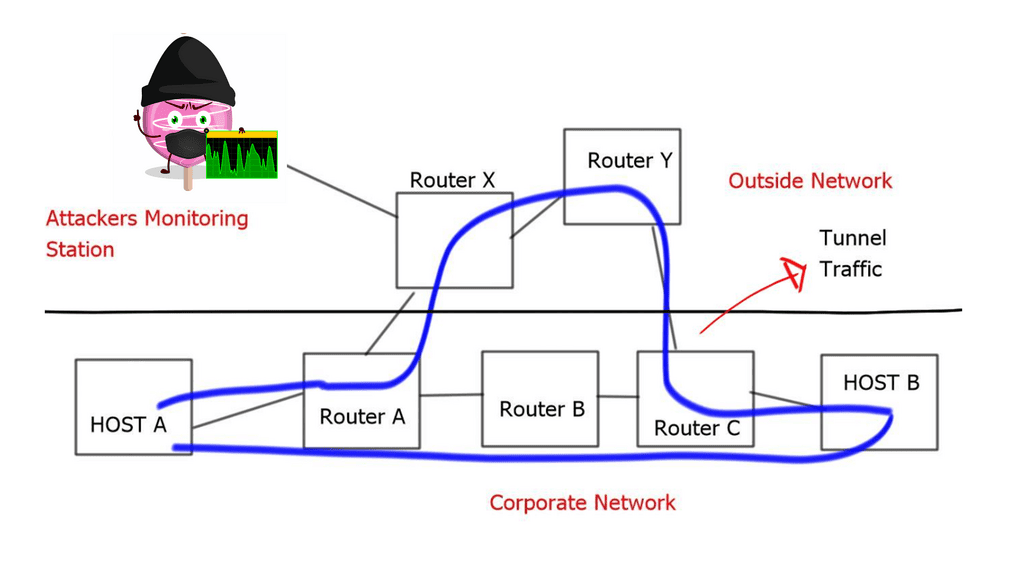
Let’s not forget about one little thing called state with a firewall in each data center design. The network address translation (NAT) in the primary data center stores the mapping for two flows, let’s call them F1 and F2. Upon failure, the second firewall in the other data center takes over, and traffic is directed to the new firewall. However, any packets from flows F1 and F2 will not enter the second firewall.
This will result in a failed lookup; existing connections will timeout, causing application failure. Asymmetric routing causes problems. If a firewall has an established state for a client-to-server connection (SYN packet), if the return SYN-ACK passes through a different firewall, the packet will result in a failed lookup and get dropped.
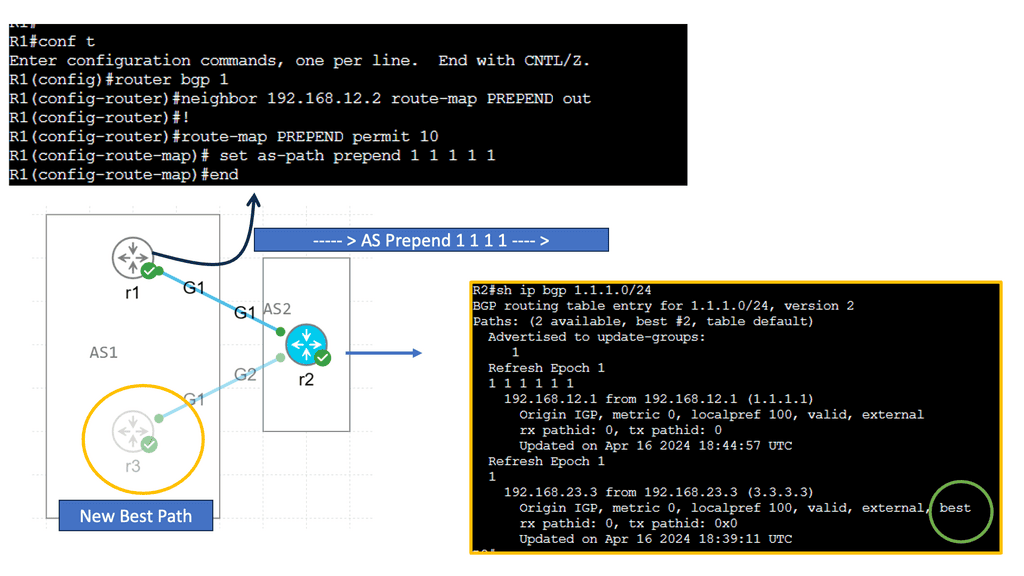
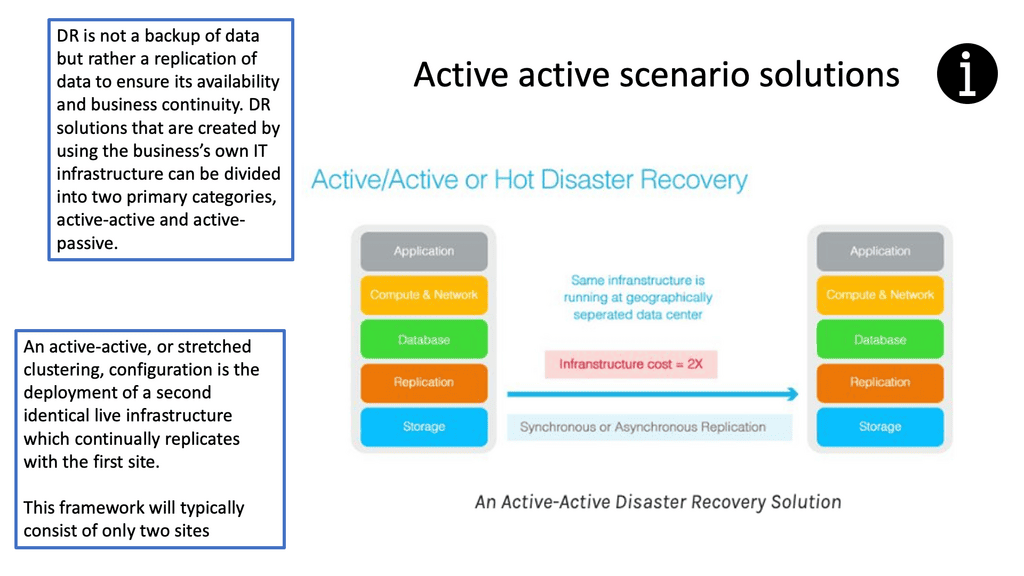
Some have tried to design distributed active-active firewalls to solve layer three issues and asymmetrical traffic flow over the stateful firewalls. The solution looks perfect. Configure both wide area network (WAN) routers to advertise the same IP prefix to the outside world.
This will attract inbound traffic and pass the traffic through the nearest firewall. Nice and easy. The active-active firewalls would exchange flow information, solving the asymmetrical flow problems.? Distributed active-active firewall state across each data center is better in PowerPoint than in real life.
Problems with having the state: Scaling
The tight coupling of the state can also cause problems with the scaling of network functions. Scaling out NAT functions will have the same effect as NAT box failure. Packets from flow originating from a different firewall directed to a new instance will result in a failed lookup.
Network functions form the foundation of modern communication systems, enabling us to connect, share, and collaborate in a digitized world. By performing vital tasks such as routing, switching, firewalls, load balancing, NAT, and IDS, network functions ensure smooth and secure data flow across networks. Understanding the significance of these functions is crucial for businesses and individuals to harness the full potential of the interconnected world we live in today.
Summary: Removing State From Network Functions
In networking, the concept of state plays a crucial role in determining the behavior and functionality of network functions. However, a paradigm shift is underway as experts explore the potential of removing the state from network functions. In this blog post, we delved into the significance of this approach and how it is revolutionizing the networking landscape.
Understanding State in Network Functions
In the context of networking, state refers to the stored information that network devices maintain about ongoing communications. It includes connection status, session data, and routing information. Stateful network functions have traditionally been widely used, allowing for complex operations and enhanced control. However, they also come with certain limitations.
The Limitations of Stateful Network Functions
While stateful network functions have played a crucial role in shaping modern networks, they also introduce challenges. One notable limitation is the increased complexity and overhead introduced by state management. The need to store and update state information for each communication session can lead to scalability and performance issues, especially in large-scale networks. Additionally, stateful functions are more susceptible to failures and require synchronization mechanisms, making them less resilient.
The Emergence of Stateless Network Functions
The concept of stateless network functions provides a promising alternative to overcome the limitations of their stateful counterparts. In stateless functions, the processing of network packets is decoupled from maintaining any session-specific information. This approach simplifies the design and implementation of network functions, offering benefits such as improved scalability, reduced resource consumption, and enhanced fault tolerance.
Benefits and Use Cases
Removing state from network functions brings a multitude of benefits. Stateless functions allow easier load balancing and horizontal scaling, as they don’t rely on session affinity. They enable better resource utilization, as there is no need to maintain per-session state information. Stateless functions also enhance network resilience, as they are not dependent on maintaining a synchronized state across multiple instances.
Stateless network functions have diverse and expanding use cases. They are well-suited for cloud-native applications, microservices architectures, and distributed systems. Organizations can build more flexible and scalable networks by leveraging stateless functions, supporting dynamic workloads and rapidly evolving infrastructure requirements.
Conclusion:
Removing the state from network functions marks a significant shift in the networking landscape. Stateless functions offer improved scalability, reduced complexity, and enhanced fault tolerance. As the demand for agility and scalability grows, embracing stateless network functions becomes paramount. By harnessing this approach, organizations can build resilient, efficient, and future-ready networks.