SASE Solution
In the realm of network security, the rise of SASE (Secure Access Service Edge) solution has been nothing short of revolutionary. Combining the capabilities of networking and security into a single cloud-based service, SASE has transformed the way organizations manage and protect their digital infrastructure. In this blog post, we will explore the key components and benefits of SASE, shedding light on how it is reshaping the landscape of network security.
SASE, an acronym for Secure Access Service Edge, is a comprehensive framework that converges network and security services into a unified cloud-native architecture. By merging wide area networking (WAN) and network security functions, SASE enables organizations to simplify their infrastructure while enhancing security and performance. This convergence is achieved through the integration of various technologies such as SD-WAN (Software-Defined Wide Area Networking), firewall-as-a-service, secure web gateways, and more.
SD-WAN: SD-WAN technology lies at the heart of SASE, providing agile and scalable connectivity across geographically dispersed locations. It offers centralized management, intelligent traffic routing, and dynamic path selection, optimizing network performance and reliability.
Cloud-native Security: SASE leverages cloud-native security services, including firewall-as-a-service (FWaaS), secure web gateways (SWG), data loss prevention (DLP), and zero-trust network access (ZTNA). These services are delivered from the cloud, ensuring consistent and robust security across the entire network infrastructure.
Identity-Centric Access: SASE incorporates an identity-centric approach to access control, focusing on user identity rather than network location. With zero-trust principles, SASE ensures that only authorized users and devices can access the network, regardless of their location or network connection.
Benefits of SASE
Simplified Infrastructure: SASE eliminates the need for multiple point solutions by consolidating networking and security into a single cloud-based service. This simplification reduces complexity, streamlines operations, and lowers costs associated with managing disparate security tools.
Enhanced Security: With its cloud-native security services, SASE provides advanced threat protection, real-time monitoring, and granular access control. This ensures that organizations can defend against emerging threats while maintaining compliance with industry regulations.
Improved Performance: SASE leverages SD-WAN technology to optimize network traffic, enabling faster and more reliable connectivity. By dynamically routing traffic based on application and network conditions, SASE minimizes latency and maximizes performance for end-users.
The emergence of SASE solution has revolutionized network security by converging networking and security services into a unified cloud-native architecture. With its key components such as SD-WAN, cloud-native security, and identity-centric access, SASE offers simplified infrastructure, enhanced security, and improved performance for organizations of all sizes.
As the digital landscape continues to evolve, embracing the power of SASE becomes imperative to stay resilient against ever-evolving cyber threats and ensure seamless connectivity across the network.Matt Conran
Highlights: SASE Solution
What is SASE?
SASE, which stands for Secure Access Service Edge, is an innovative networking architecture that combines network security and wide-area networking (WAN) capabilities into a unified cloud-based solution. It shifts networking and security functionalities to the cloud, eliminating the need for traditional hardware-centric approaches. By converging these services, SASE offers a holistic and scalable solution that adapts to the ever-evolving demands of modern businesses.
**The Core Components of SASE**
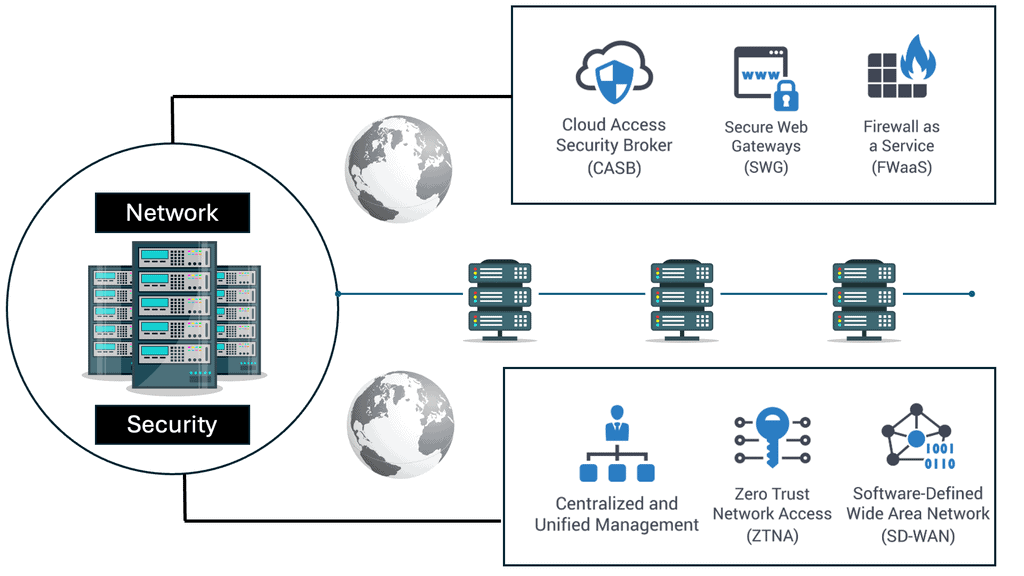
SASE integrates several key technologies to deliver its promise of seamless security and connectivity. At its core, SASE combines Software-Defined Wide Area Networking (SD-WAN) with robust security services such as Secure Web Gateways (SWG), Cloud Access Security Brokers (CASB), Firewall as a Service (FWaaS), and Zero Trust Network Access (ZTNA). This convergence allows organizations to simplify their IT infrastructure, reduce costs, and enhance security posture by delivering network and security functions from the cloud.
**Benefits of Adopting SASE**
Organizations that adopt SASE can experience a multitude of benefits. Firstly, SASE offers improved performance by leveraging the cloud’s scalability, ensuring users experience low latency and high-speed connections regardless of location. Secondly, the unified approach to security reduces complexity, enabling IT teams to manage policies across all users and devices from a single platform. Lastly, SASE enhances security by applying consistent and context-aware security policies, thus reducing vulnerabilities and potential breaches.
**Challenges and Considerations**
While SASE presents numerous advantages, organizations must also consider potential challenges. Transitioning to a SASE framework requires careful planning and execution, as it involves re-architecting existing network and security infrastructures. Additionally, choosing the right SASE provider is crucial, as the quality and range of services can vary significantly. Organizations must evaluate providers based on their ability to deliver comprehensive security features, global reach, and reliability.
SASE Key Points:
1. Enhanced Security: SASE provides robust security measures, such as integrated firewalling, data loss prevention, and secure web gateways, to safeguard networks and data from emerging threats. Organizations can streamline their security operations and reduce complexity with a unified security framework.
2. Improved Performance: SASE optimizes network performance and minimizes latency by leveraging cloud-native infrastructure. It enables efficient traffic routing, intelligent application steering, and dynamic bandwidth allocation, ensuring a seamless user experience even in geographically dispersed environments.
3. Simplified Network Management: Traditional networking architectures often involve managing multiple vendors and complex configurations. SASE simplifies network management through centralized policy-based controls and automation, reducing administrative overhead and enhancing operational efficiency.
Adopting a SASE Solution:
By adopting a SASE solution, businesses can unlock a plethora of benefits. Firstly, it provides secure access to applications and data from any location, enabling seamless remote work capabilities. Additionally, SASE eliminates the need for traditional hardware-based security appliances, reducing costs and complexity. The centralized management and policy enforcement offered by SASE ensures consistent security across the entire network, regardless of the user’s location or device.
**Adopt a Phased Approach**
While the benefits of SASE are enticing, organizations must approach its implementation strategically. Assessing the existing network infrastructure, defining security requirements, and selecting a reliable SASE provider is crucial. A phased approach to performance, starting with pilot projects and gradually scaling up, can help organizations ensure a smooth transition and maximize the potential of SASE.
**SASE Components**
Understanding its key components is essential to fully grasping the power of SASE. These include secure web gateways (SWG), cloud access security brokers (CASB), firewall-as-a-service (FWaaS), data loss prevention (DLP), and zero-trust network access (ZTNA). Each element is crucial in fortifying network security while enabling seamless user connectivity.
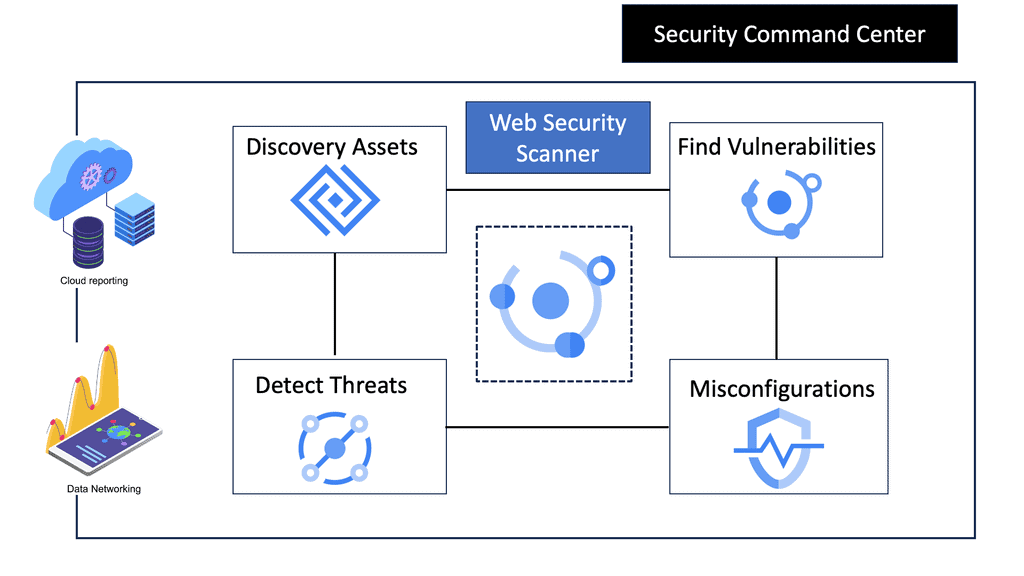
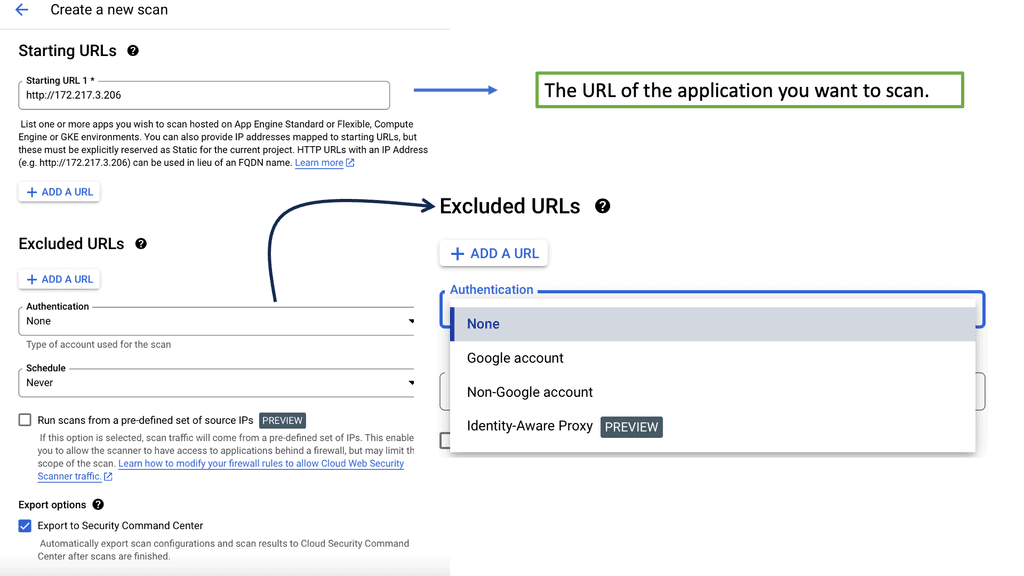
Example SASE Technology: Web Security Scanner
**What are Web Security Scanners?**
Web security scanners are automated tools designed to identify security vulnerabilities within web applications. They simulate cyber-attacks to detect weaknesses that malicious hackers might exploit. These tools scan for various vulnerabilities like SQL injection, cross-site scripting (XSS), and insecure server configurations. By identifying these weaknesses, web security scanners enable businesses to proactively address potential threats before they can be exploited.
**The Role of Google Cloud in Enhancing Web Security**
Google Cloud offers a comprehensive suite of security tools and services that complement web security scanners. By integrating these scanners with Google Cloud, businesses can leverage advanced analytics and machine learning capabilities to enhance their security posture. Google Cloud’s global infrastructure ensures high availability and scalability, allowing security scanners to operate efficiently across large-scale applications.
**Benefits of Using Web Security Scanners on Google Cloud**
1. **Automated Vulnerability Detection**: Web security scanners automate the process of identifying vulnerabilities, reducing the time and effort required for manual testing. This automation ensures that potential threats are detected quickly and efficiently.
2. **Scalability and Performance**: Google Cloud’s infrastructure supports the scalability of web security scanners, allowing them to handle large volumes of data without compromising performance. This scalability is crucial for businesses with extensive web applications.
3. **Integrated Security Solutions**: Google Cloud offers a range of integrated security solutions, including Identity and Access Management (IAM) and Security Command Center, which complement the capabilities of web security scanners. These solutions provide a holistic approach to securing web applications.
**Real-World Applications: Case Studies**
Several organizations have successfully implemented web security scanners on Google Cloud to enhance their security measures. For instance, a leading e-commerce company utilized these tools to identify and remediate vulnerabilities in their payment gateway, safeguarding customer transactions. Similarly, a healthcare provider leveraged Google Cloud’s security services to protect patient data, ensuring compliance with stringent regulations.

 Zero Trust & Identity
Zero Trust & Identity
The path to zero trust starts with identity. Network access is based on the identity of the user, the device, and the application, not on the device’s IP address or physical location. And this is for a good reason. There needs to be contextual information.
a) User & Device Identity
The user/device’s identity must reflect the business context instead of being associated with binary constructs utterly disjointed from the upper layers. This binds an identity to the networking world and is the best way forward for policy enforcement.
b) Lack of Good Identifiers
Therefore, the dependency on IP or applications as identifiers is removed. Now, the policy is applied consistently regardless of where the user/device is located, while the identity of the user/device/service can be factored into the policy. The SASE stack is dynamically applied based on originality and context while serving zero trust at strategic points in the cloud, enforcing an identity-centric perimeter.
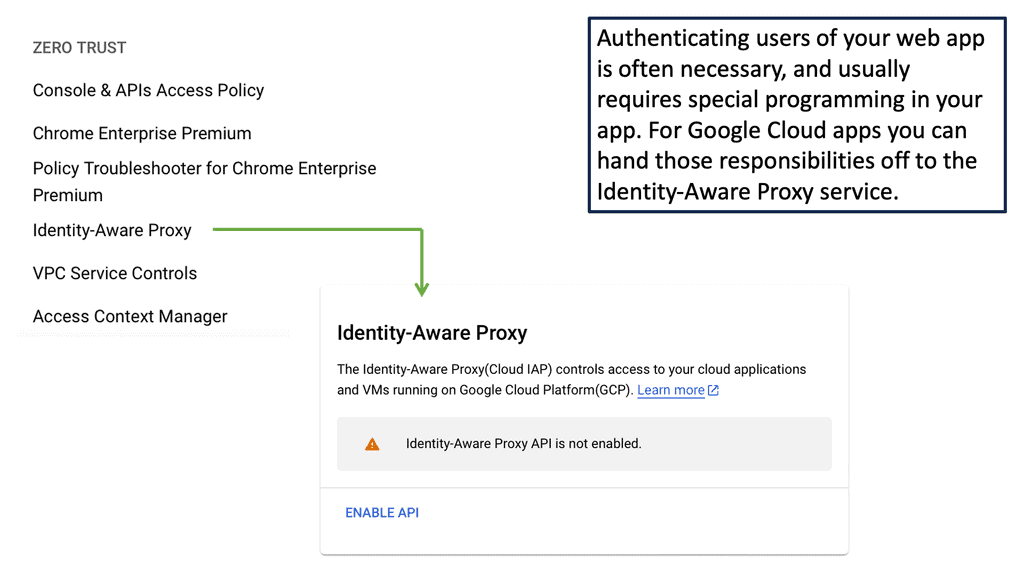
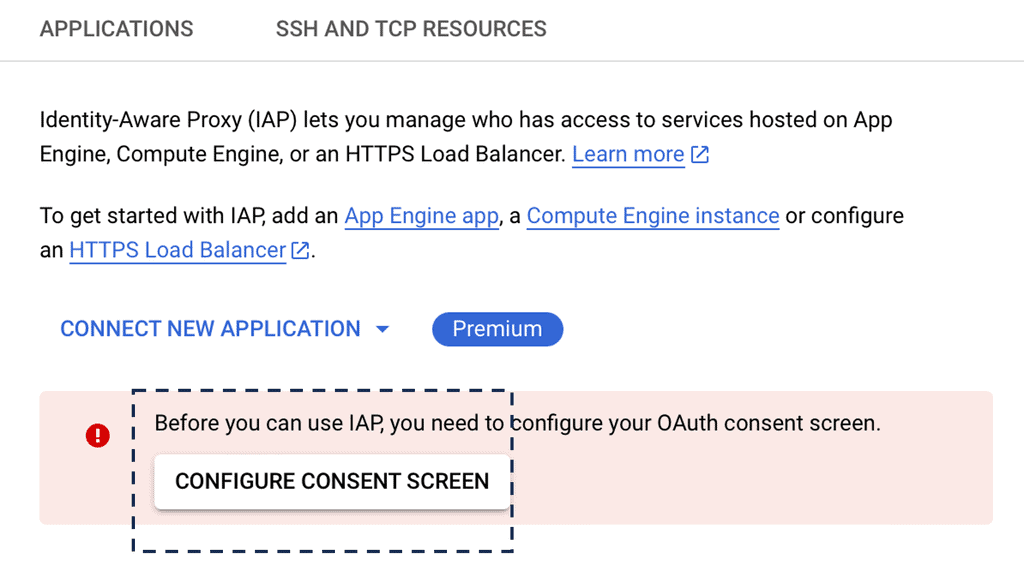
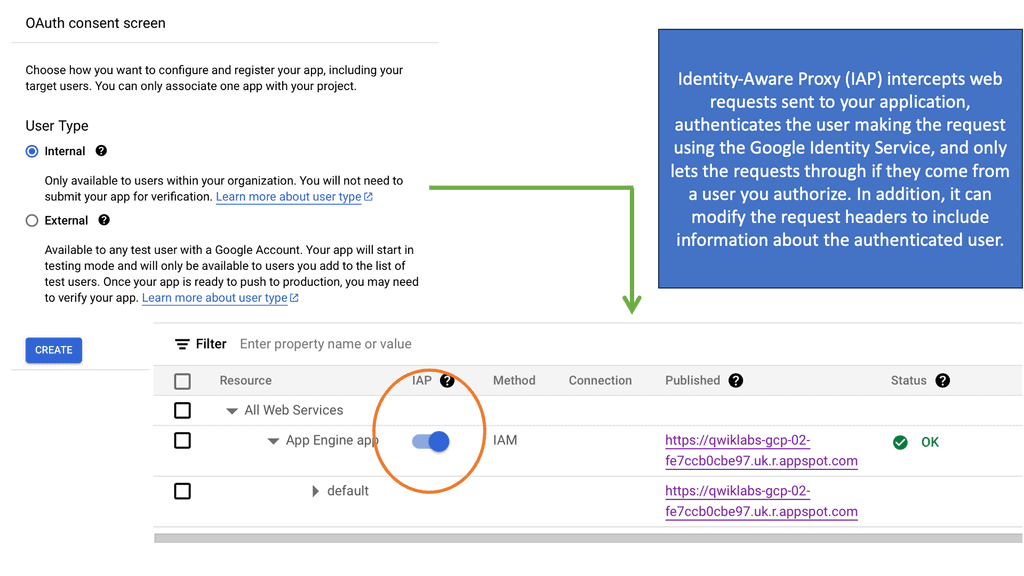
Example Identity Technology: Identity Aware Proxy
c) The Role of SASE Security
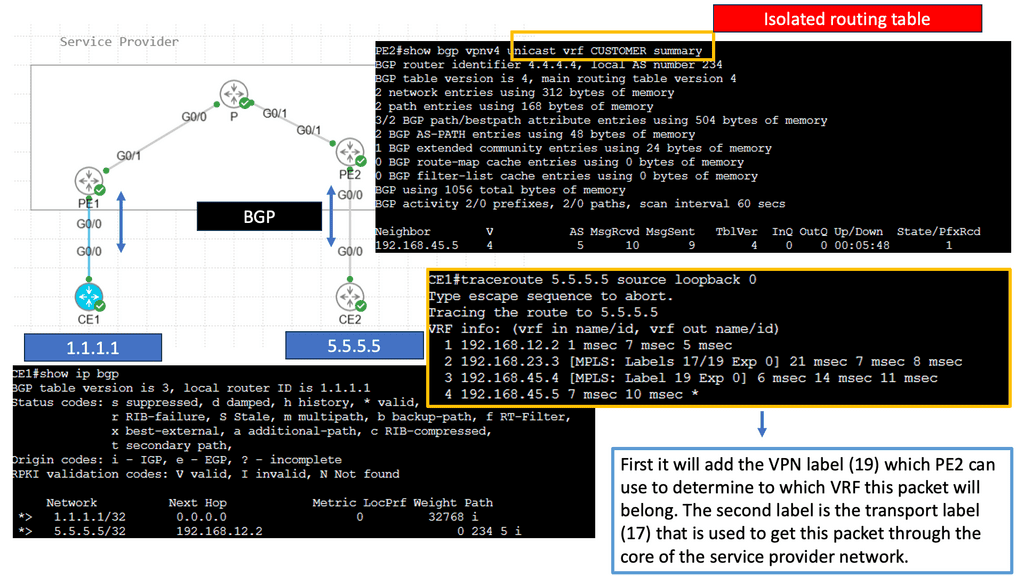
In this post, we will decompose the Zero Trust SASE, considering the SASE fabric and what a SASE solution entails. The SASE security consists of global PoPs. With network and security functions built into each PoP, they are operated with a single management plane. This post will examine the fabric components while discussing the generic networking and security challenges that SASE overcomes, focusing on Cisco SASE.
**Example SASE Solution – Cisco Approach: CSP 5000 & NFV**
The Cisco SASE definition is often deemed just Cisco Umbrella; however, that is just part of the solution. Cisco SASE includes the Umbrella but entails an entirely new architecture based on the CSP 5000 and Network Function Virtualization (NFV) and a series of Virtual Network Functions (VNFs) such as virtual firewalls. We will touch on Cisco SASE soon.
As the SASE solution has many dependencies, you, as an enterprise, know how far you are in your cloud adoption. Whether you are a public cloud first, hybrid, multi, or private cloud path affects the design of your DMZ. SASE security is all about optimizing the DMZ to enable secure methods.
Related: For pre-information, you may find the following posts helpful:
SASE Solution
SASE – Cloud-based
SASE directs to a concept incorporating cloud-based software-defined wide area networking (SD-WAN) with a range of security services and unified management functionality for delivering security and SD-WAN capabilities to any edge computing location. A prime use case for SASE is to address the performance bottleneck issues of traditional networks that rely on traffic backhauling. Further, by integrating identity, business context, and real-time risk assessment into every connection, SASE architectures pledge to control a variety of cyber-attacks.
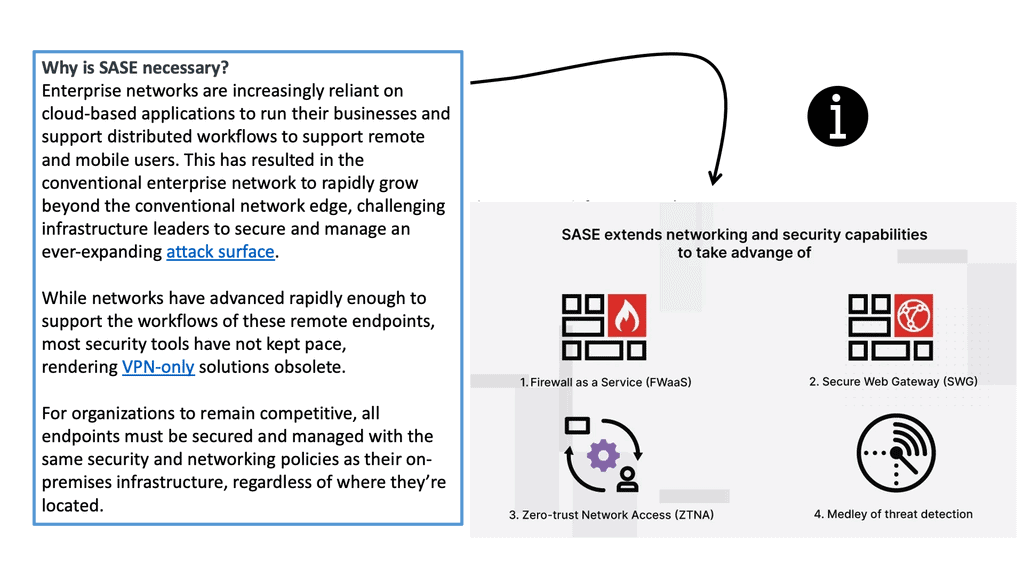
The DMZ: Calling a SASE Solution
**Updating the DMZ**
First, the SASE architecture updates the DMZ, which has remained unchanged since the mid-90s. The DMZ, often called the perimeter network, is a physical or logical subnetwork whose sole purpose is to expose an organization’s external-facing services to untrusted networks.
The DMZ adds a layer of security so that potentially insecure external networks can only access what is exposed in the DMZ. At the same time, the rest of the organization’s network is protected by a security stack.
**Extra Time But that’s about it**
As a result, the DMZ is considered a small, isolated network portion and, if configured correctly, will give you extra time to detect and address breaches, malware, and other types of attacks before they further penetrate the internal networks.
The critical factor here is that it’s a layer that, at best, gives you additional time before the breach to the internal network. The central pain point with the current DMZ architecture is that the bad actor knows it’s there unless you opt for zero trust single packet authentication or some other zero-trust technology.
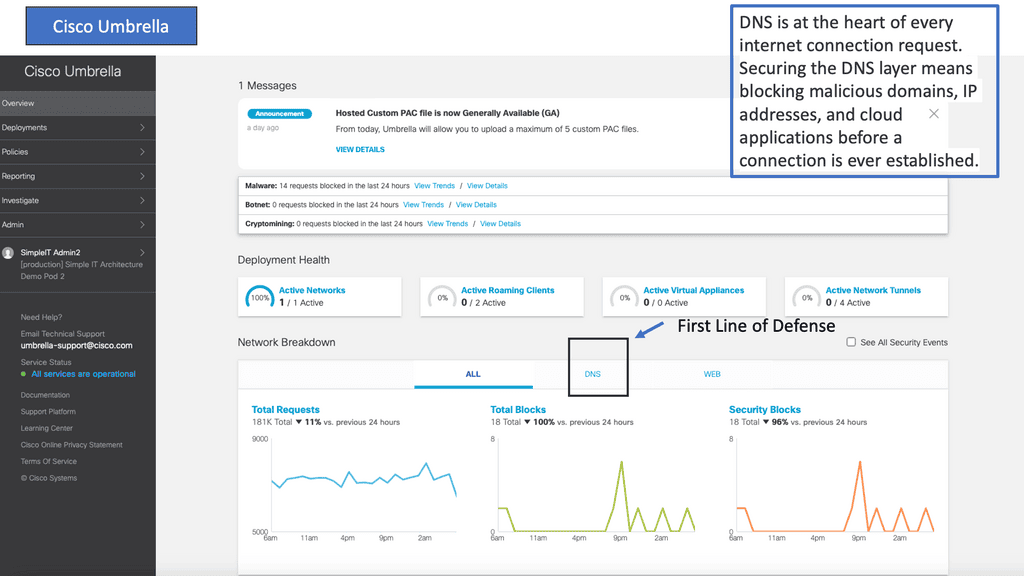
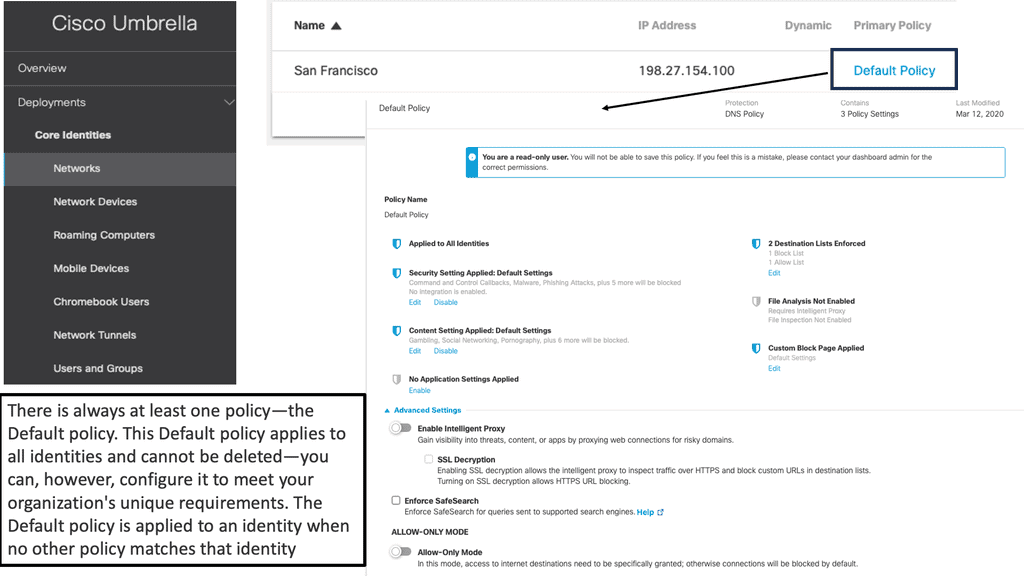
Example Product: Cisco Umbrella & DNS Layer Security
Key Note: SASE security and SD-WAN
This is similar to updating the WAN edge with SD-WAN to optimize performance per application with SDWAN overlays. Both SASE and SD-WAN are updating, let’s say, the last hardware bastions in your infrastructure: SD-WAN with the WAN edge and SASE with the DMZ.
The DMZ is a vital section, but it needs to be secure from a perimeter firewall with a port and our traffic flow. It also needs good visibility, the ability to detect and attack, and respond appropriately, and quick reaction time—speeds achievable only with secure automation.
A Perfect DMZ: SASE Solution
- Support API and Modeling Languages
These new DMZ designs need to be open. It must support API and open standard modeling languages like XML and YANG. This will allow you to support various network and security devices, physical, virtual, and hybrid, via secure API. Not only does it need to be open, but it also needs to be extensible and repeatable. So, we can allow new functionality to be added and removed as the architecture evolves and react to dynamic business objectives.
- Scalability with NFV
SASE also needs to scale up and down, out and in, with little or no disruption to existing services. It should be able to scale without adding physical appliances, as physical devices can only scale so far. The SASE solution needs Network Function Virtualization ( NFV ) with a series of Virtual Network Functions (VNFs) chained together. Cisco CSP 5000 can be used here, and we will discuss it briefly.
- Orchestration & Automation
You want to avoid dealing with the device’s CLI. The new SASE fabric needs to be well-programmable. All functional elements of the architecture are fully programmable via API.
The APIs cannot just read data but can change behavior, such as network device configurations. So you will need an orchestrator for this. For example, Ansible Tower could automate and manage configuration drift among the virtual network functions. Ansible Tower provides end-to-end team automation with features such as workflow templates and integration into the CI/CD pipelines.
SASE Security & SDN
Network segmentation is essential to segment the data and control plane traffic. So, the control plane configures the devices, and the data plane forwards the traffic. The segmentation aspect is sufficient for the scalability and performance of resolutions. To manage SASE security, you will need to employ software-defined networking principles. The SDN controller is not in the forward path. It just sets up the data plane. The data plane should operate even if the control plane fails. However, the control plane could have some clustering to avoid failure.
Example: Software Defined Perimeter (SDP)
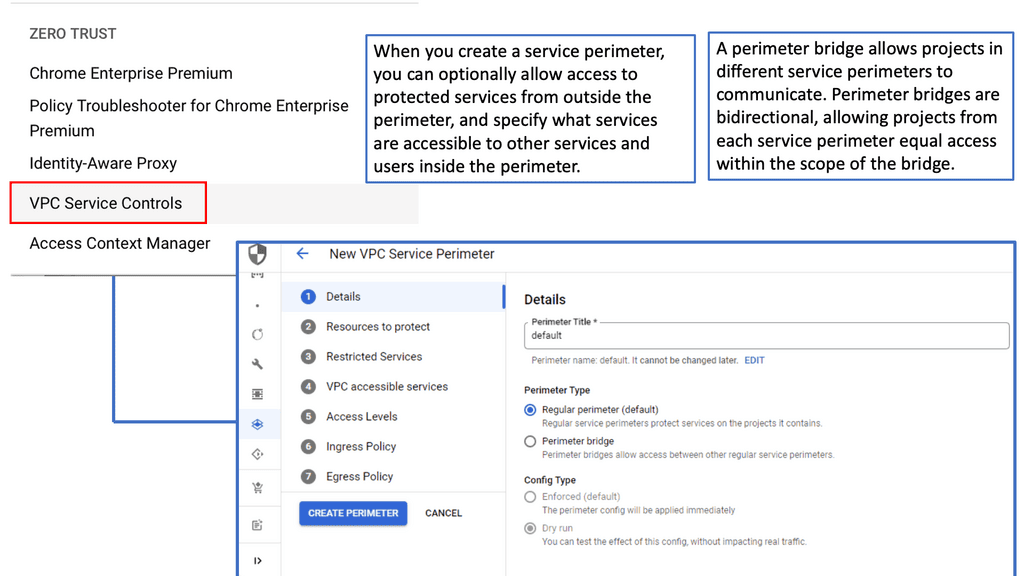
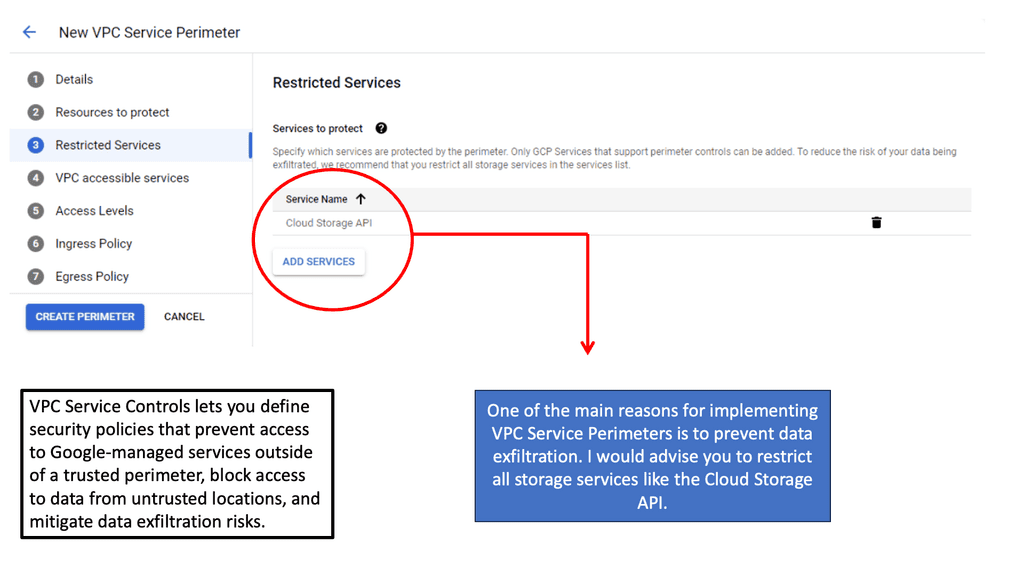
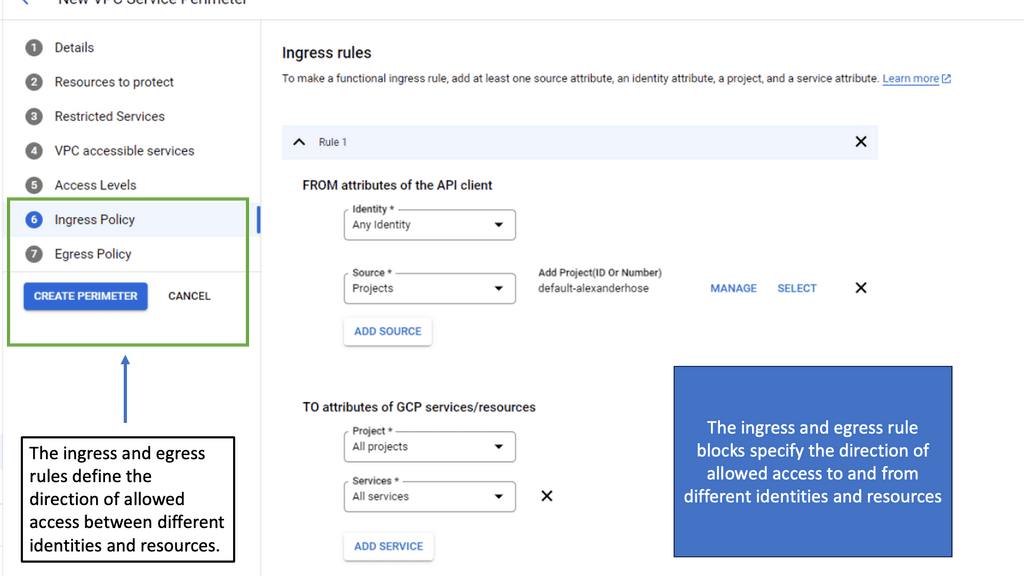
**Understanding the Basics of VPC Service Controls**
VPC Service Controls are designed to augment the security of Google Cloud services by establishing a security perimeter around your cloud resources. This means that even if a malicious actor gains access to your network, they won’t be able to exfiltrate data outside the defined boundaries. This section will delve into the fundamental components of VPC Service Controls, including service perimeters, access levels, and policy configurations. We’ll also touch on how these controls integrate with other Google Cloud security features to provide a comprehensive security framework.
**Implementing VPC Service Controls: Step-by-Step Guide**
Setting up VPC Service Controls can seem daunting, but with a structured approach, it becomes manageable. This section outlines a step-by-step guide to implementing VPC Service Controls on Google Cloud. From defining your service perimeter to configuring access levels and monitoring the setup, we’ll provide practical insights and best practices. Additionally, we’ll discuss common pitfalls and how to avoid them, ensuring a smooth and efficient configuration process.
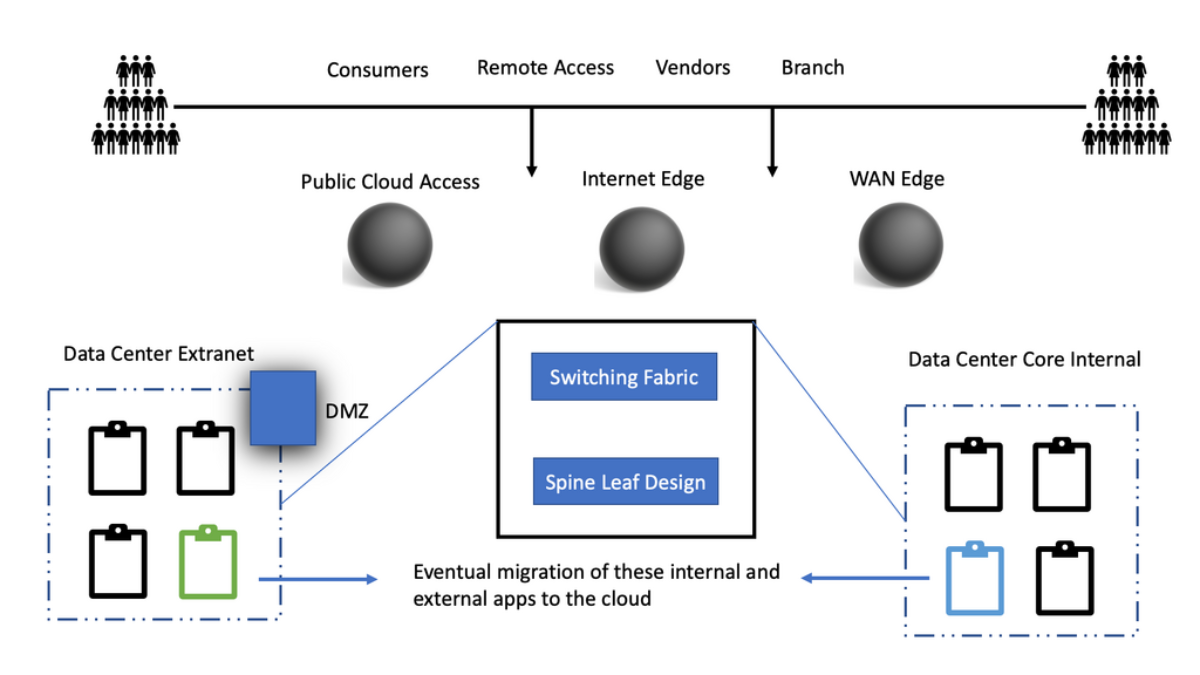
Standard Data Center Design
**Traffic Flows**
There will be the consumers of services. So, they can be customers, remote users, partners, and branch sites. These consumers will have to access applications which are hosted in the network or cloud domain. So, the consumers will typically have to connect to a WAN edge for applications hosted in the network.
On the other hand, if consumers want to connect to cloud-based applications, they can go directly to, let’s say, IaaS or the more common SaaS-based applications. Again, this is because access to cloud-based applications does not go via the WAN edge.
For consumers to access network applications not hosted in the cloud, as discussed, they are met with the WAN edge. Traffic will need to traverse the WAN edge to get to the application, which will have another layer of network and security functionality deeper in the network.
**WAN Edge Components**
At the network’s edge, we have many different types of network and security functionality. So, we will have standard routers, a WAN optimization controller, Firewalls, Email Gateways, Flow collectors, and other types of probes to collect traffic.
Then, a network will have to switch fabric. So, the old days of the 3-tier data Center architecture are gone. All primary switching fabrics or switching fabrics that you want IP forwarding to scale are based on the spine leaf architecture, for example, the Cisco ACI with ACI networks. The ACI Cisco has good Multi Pod and Multi-Site capabilities.
**Application Hosting**
Then, we go deeper into the applications and have app-tier access. So, we have application-hosted Internet for internal users. Each one will have its security, forwarding proxy devices, and load balancers. All these are physical wires tied to the fabric and will have limited capacity.
Example: MPLS Global WAN
For global data center design. These will commonly connect over MPLS, which provides the Global WAN. Each data center would connect to an MPLS network and will usually be grouped by regions such as EMEA or AMERICAS. So, we have distributed networks, such as the MPLS network label switches. You can also have Segment Routing to provide this global WAN, which improves traffic engineering.
So, some common trends have challenged parts of this design. Many of these trends have called for the introduction of a new network area called the SASE fabric, commonly held in a CNF or a collocation facility. This fabric already has all the physical connectivity and circuits for you.
Common Trends: SASE Architecture
In a cloud-centric world, users and devices require access to services everywhere. These services are now commonly migrated to SaaS and IaaS-based clouds. So we have an app migration from “dedicated” private to “shared” public cloud. These applications became easy to change based on a microservices design. The growth was rapid, and now you must secure workloads in a multi-tenant environment.
SASE – **Identity is the new perimeter**
As a result, the focal point has changed considerably. Now, it is the identity of the user and device, along with other entities around the connection group, as opposed to the traditional model focusing solely on the data center. Identity then becomes the new perimeter.
SASE – **Bandwidth Requirements**
Another major trend is that capacity requirements and bandwidth for public clouds doubled. Now that applications are hosted in the cloud, we also need to make changes on the fly to match the agility of the cloud.
When migrating these applications, we must rapidly upgrade internet-facing firewalling, for example, due to remote user access demands. Also, security teams demand IPS/AMP appliance insertions. In a cloud environment, it’s up to you to secure your workloads, and you need the same security levels in the cloud as you would on-premises.
SASE – **Constant Security Policy**
These apps are not in our data center, so we need to ensure that these migrated applications have the same security policy that would be housed in the AWS or Azure clouds. So we need more services in the current infrastructure.
Now we have more wiring and configuration, what is the impact on an extensive global network? You have a distributed application in several areas and want to open a port. These configurations need to be done and monitored in many places and with many teams.
Internal data applications are becoming less important than those that run in public clouds. More apps are in the cloud, and the data center is becoming less important as the prime focal point. The data center will always be retained, but the connectivity and design will change with the introduction of an SASE solution.
Security Solution Appliances
A. Different Technology Stacks:
Many common problems challenge the new landscape. Due to deployed appliances for different technology stacks for networking and security, not to mention the failover requirements between them, we are embedded with high complexity and overhead.
B. DMZ & Increased Latency:
The legacy network and security located in the DMZ designs increase latency. The latency is even with service chaining, but it will expand and become more challenging to troubleshoot. In addition, the world is encrypted. This needs to be inspected without degrading application performance.
C. Required: Global SASE Fabric
These challenges are compelling reasons to leverage a cloud-delivered SASE solution. The SASE architecture is a global fabric consisting of a tailored network for application types typically located in the cloud: SASE optimizes where it makes the most sense for the user, device, and application – at geographically dispersed PoPs. Many will connect directly to a colocation facility that can hold the SASE architecture.
D. Architectural Changes
The significant architecture changes you have seen in the past are that consumers, remote users, customers, branches, and partners will connect to the WAN edge, Internet, or IaaS via a colocation facility. Circuits migrated to selected “central hubs” connectivity and colocation sites from the data center.
The old DC will become another application provider connecting to the colocation. Before addressing what this collocation looks like, we will address the benefits of redefining the network and security architecture. Yes, adopting SASE reduces complexity and overhead, improves security, and increases application performance, but what does that mean practically?
Problems with complexity/overhead/processing/hardware-based solutions
E. Hardware Capacity Limits
Traditional mechanisms are limited by the hardware capacity of the physical appliances at the customer’s site and the lag created for hardware refresh rates needed to add new functionality. Hardware-based network and security solutions build the differentiator of the offering into the hardware. With different hardware, you can accelerate the services and add new features.
F. Feature Limits
Some features are available on specific hardware, not the hardware you already have on-site. In this case, the customer will need to do the heavy lifting. In addition, as the environment evolves, we should not depend on the new network and security features from the new appliance generation. This inefficient and complex model creates high operational overhead and management complexity.
G. Device Upgrades
Device upgrades for new features require significant management. From experience, changing out a line card would involve multiple teams. For example, if the line card ran out of ports or you need additional features from a new generation,
This would involve project planning, on-site engineers, design guides, and, hopefully, line card testing and out-of-hours work. For critical sites to ensure a successful refresh, team members may need to be backed up. Many touches need to be managed.
SASE architecture overcomes tight coupling/hardware-based solutions.
Cloud-based SASE
The cloud-based SASE enables updates for new features and functionality without requiring new deployments of physical appliances. A physical appliance will still need to be deployed, but it can host many virtual networks and security functions, which has an immediate effect on ease of management.
Network and security deployment can now occur without ever touching the enterprise network, allowing enterprises to adopt new capabilities quickly. Once the tight coupling between the features and the customer appliance is removed, we have increased agility and simplicity for deploying network and security services.
Cisco SASE: Virtualization of Network Functions
With a Cisco SASE platform, when we create an object, such as the virtualization of Network Functions. The policy in the networking domain is then available in other domains, such as security. Network function virtualization, where we de-couple software from hardware, is familiar.
This is often linked to automation and orchestration, where we focus on simplifying architecture, particularly on Layer 4 – Layer 7 services. Virtual machine hosting has enabled the evolution of a variety of virtualized workloads. The virtualization of network and security functions allows you to scale up, down, and in and out at speed and scale without embedding service.
Example: Virtual Appliances
Let’s say you have an ASAv5 as a virtual appliance. This virtual appliance has, for example, 1 Core. If you want more cores, you can scale up to support ASA v50, which supports eight cores. So we can scale up and down. However, what if you want to scale out?
Multipath load balancing
Here, we can add more cloud service providers and ASAv to scale out virtual firewalls with equal-cost multipath load balancing. You want to buy something other than a physical appliance that will only ever do one function. The days of multiple physical point solutions are ending as sase gains momentum. Instead, you want your data center to scale when capacity demands it without physical limitations.
Cisco SASE Architecture: NFV
NFV network services can be deployed and managed much more flexibly because they can be implemented in a virtualized environment using x86 computing resources instead of purpose-built dedicated hardware appliances. The CSP 5000 Series can help you make this technology transition.
In addition, with NFV, the Cisco SASE open approach allows other vendors to submit their Virtual Network Functions (VNF) for certifications to help ensure compatibility with Cisco NFV platforms.
Cloud Services Platform
This central location is a PoP that could be a Cloud Services Platform that could provide the virtualized host. For example, the Cloud Services Platform CSP-5000 could host CSR, FTD, F5, AVI networks, ASAv, or KVM-based services. These network and security functions represent the virtual network appliances that consist of virtual machines.
- Cisco SASE and the CSP 5000
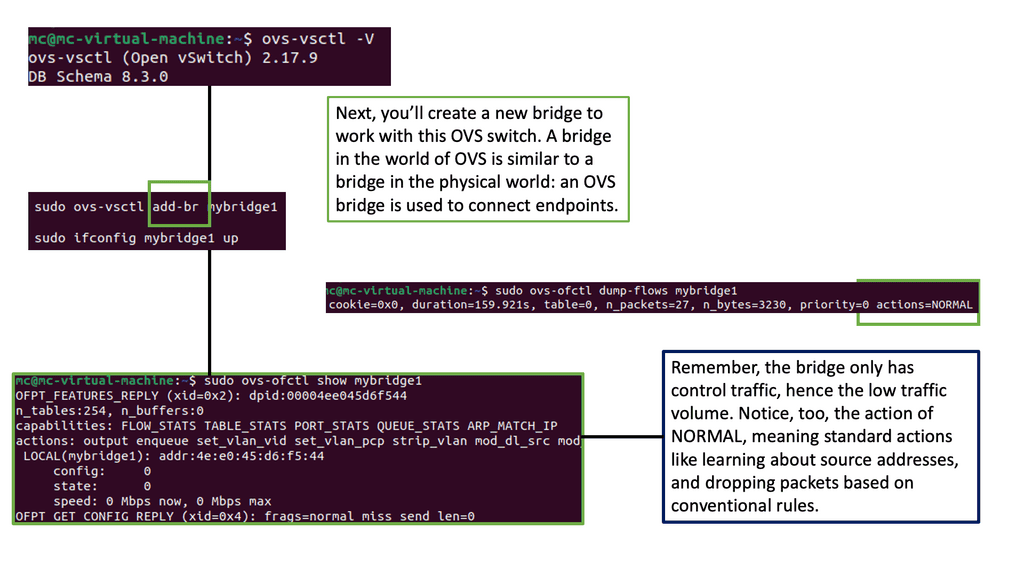
Within the Cisco SASE design, the CSP 5000 Series can be deployed within data centers, regional hubs, colocation centers, the WAN edge, the DMZ, and even at a service provider’sprovider’s Point of Presence (PoP), hosting various Cisco and third-party VNFs. We want to install the CSP at a PoP, specifically in a collocation facility. If you examine the CSP-5000 for a block diagram, you will see that Cisco SASE has taken a very open ecosystem approach to NFV, such as Open vSwitch.
- Key Technology: SR-IOV
It uses Single Root I/O Virtualization (SR-IOV) and an Open vSwitch Data Plane Development Kit (OVS-DPDK). The optimized data plane provides near-line rates for SR-IOV-enabled VNFs and high throughput with OVS DPDK interfaces.
- The Role of the OVS
The CSP has a few networking options. First, the Open vSwirch ( OVS) is the Software layer two switches for the CSP-500. So, the CSP internal software switches bridge the virtual firewall to the load balancer to the ToR switches. You can also use SR-IOV Virtual Ethernet Bridge Mode (VB), which performs better. As a third option, we have SR-IOV, virtual Ethernet Port Aggregators Mode (VEPA)
 **Cisco SASE Security Policies**
**Cisco SASE Security Policies**
With the flexible design Cisco SASE offers, any policies assigned to users are tied to that user regardless of network location. This removes the complexity of managing network and security policies across multiple locations, users, and devices. But, again, all of this can be done from one platform.
SASE architecture overcomes the complexity and heavy lifting/scale.
**A Personal Note: SASE**
I remember from a previous consultancy. We were planning next year’s security budget. The network was packed with numerous security solutions. All these point solutions are expensive, and there is never a fixed price, so how do you plan for this? Some new solutions we were considering charge on usage models, which we needed the quantity at that time. So the costs keep adding up and up.
SASE removes these types of headaches. In addition, consolidating services into a single provider will reduce the number of vendors and agents/clients on the end-user device. So we can still have different vendors operating a sase fabric, but they are now VNF on a single appliance.
**Complexity Reduction**
Overall, substantial complexity savings will be from consolidating vendors and technology stacks, pushing this to the cloud away from the on-premises enterprise network. The SASE fabric abstracts the complexity and reduces costs. In addition, from a hardware point of view, the cloud-based SASE can add more PoPs of the same instance for scale and additional capacity. This is known as vertical scaling, and also, in new locations, known as horizontal scaling.
**SASE Overcomes Intensive Processing**
Additionally, the SASE-based cloud takes care of intensive processing. For example, as much of internet traffic is now encrypted, malware can use encryption to evade and hide from detection. Here, each PoP can perform deep packet dynamics on TLS-encrypted traffic.
**Encryption/Decryption**
You may not need to decrypt to fully understand the payload. Still, partial decryption and examining payload patterns to understand the malicious activity seem enough. The SASE vendor needs to have some Deep Packet Dynamic technologies.
**Challenge: Traditional Firewalling**
Traditional firewalls are not capable of inspecting encrypted traffic. Therefore, performing DPI on TLS-encrypted traffic would require extra modules or a new appliance. A SASE solution ensures the decryption and inspection are done at the PoP, so no performance hits or new devices are needed on the customer sites. This can be done with Deep Packet Dynamic technologies.
Performance Problems – Packet drops/latency
Network congestion resulting in dropped and out-of-order packets could be better for applications. Latency-sensitivity applications such as collaboration, video, VoIP, and web conferencing are hit hardest by packet drops. Luckily, there are options to minimize latency and the effects of packet loss.
1. **WAN Optimization**
SD-WAN solutions have WAN optimization features that can be applied on an application-by-application or site-by-site basis. Along with WAN optimization features, there are protocol and application acceleration techniques.
2.**Privatize the WAN**
In addition to existing techniques to reduce packet loss and latency, we can privatize the WAN as much as possible. To control the adverse and varying effects the last mile and middle mile have on applications, we can privatize with a private global backbone consisting of a fabric of PoPs.
Once privatized, we have more control over traffic paths, packet loss, and latency. A private network fabric is a crucial benefit of SASE, as it drives application performance. So we can inspect east-west and north-south traffic.
3.** Traffic Engineering**
Traffic engineering and performance improvement are easy since we have a centralized fabric consisting of many hubs and spokes. When you centralize some of the architecture into a centralized fabric, it is easier to make traffic adjustments globally. The central hub will probably be a collocation facility and can be only one hop away, so the architecture will be simpler and easier to implement.
PoP optimization – Routing algorithms, and TCP proxy.
Each PoP in the SASE cloud-based solution optimizes where it makes the most sense, not just at the WAN edge. For example, within the SASE fabric, we have global route optimizations to determine which path is best and can be changed for all traffic or specific applications.
4.**PoP acting as TCP Proxy**
These routing algorithms factor in performance metrics such as latency, packet loss, and jitter. I am selecting the optimal route for every network packet. Unlike internet routing, which favors cost over performance, the WAN backbone constantly analyzes and tries to improve performance.
Example: Increasing The TCP Window Size
-As everything is privatized, we have all the information to create the largest packet size and use rate-based algorithms over traditional loss-based algorithms. As a result, you don’t need to learn anything, and throughput can be maintained end-to-end.
– As each PoP acts as a TCP proxy server, techniques are employed so that the TCP client and server think they are closer. Therefore, a larger TCP window is set, allowing more data to be passed before waiting for an acknowledgment.
Example Technology: TCP Performance Parameters
Summary: SASE Solution
In today’s rapidly evolving technological landscape, traditional networking approaches are struggling to keep up with the demands of modern connectivity. Enter SASE (Secure Access Service Edge) – a revolutionary solution that combines network and security capabilities into a unified cloud-based architecture. In this blog post, we explored the key features and benefits of SASE and delve into how it is shaping the future of networking.
Understanding SASE
SASE, pronounced “sassy,” represents a paradigm shift in networking. It converges wide-area networking (WAN) and network security services into a single, cloud-native solution. By integrating these traditionally disparate functions, organizations can simplify network management, improve security, and enhance overall performance. SASE embodies the principles of simplicity, scalability, and flexibility, all while delivering a superior user experience.
The Power of Cloud-native Architecture
At the core of SASE lies its cloud-native architecture. By leveraging the scalability and agility of the cloud, organizations can dynamically scale their network and security resources based on demand. This elasticity eliminates the need for costly infrastructure investments and allows businesses to adapt quickly to changing network requirements. With SASE, organizations can embrace the benefits of a cloud-first approach without compromising on security or performance.
Enhanced Security and Zero Trust
One of the key advantages of SASE is its inherent security capabilities. SASE leverages a Zero Trust model, which means that every user and device is treated as potentially untrusted, regardless of their location or network connection. By enforcing granular access controls, strong authentication mechanisms, and comprehensive threat detection, SASE ensures that only authorized users can access critical resources. This approach significantly reduces the attack surface, mitigates data breaches, and enhances overall security posture.
Simplified Network Management
Traditional networking architectures often involve complex configurations and multiple point solutions, leading to a fragmented and challenging management experience. SASE streamlines network management by centralizing control and policy enforcement through a unified console. This centralized approach simplifies troubleshooting, reduces administrative overhead, and enables organizations to maintain a consistent network experience across their distributed environments.
Conclusion
As the digital landscape continues to evolve, embracing innovative networking solutions like SASE becomes imperative for organizations seeking to stay ahead of the curve. By consolidating network and security functions into a unified cloud-native architecture, SASE provides simplicity, scalability, and enhanced security. As businesses continue to adopt cloud-based applications and remote work becomes the norm, SASE is poised to revolutionize the way we connect, collaborate, and secure our networks.
- Fortinet’s new FortiOS 7.4 enhances SASE - April 5, 2023
- Comcast SD-WAN Expansion to SMBs - April 4, 2023
- Cisco CloudLock - April 4, 2023