Intent Based Networking
In today's rapidly advancing technological landscape, the demand for efficient and intelligent networking solutions continues to rise. Intent-Based Networking (IBN) has emerged as a transformative approach that simplifies network management, enhances security, and enables businesses to align their network operations with their overall objectives.
Intent-Based Networking represents a paradigm shift in the way networks are designed, deployed, and managed. At its core, IBN leverages automation, artificial intelligence (AI), and machine learning (ML) to interpret high-level business policies and translate them into automated network configurations. By abstracting network complexity, IBN empowers organizations with greater control, visibility, and agility.
1. Policy Definition: IBN relies on a declarative approach, where network administrators define policies based on business intent rather than dealing with low-level configurations. This simplifies the process of managing networks and reduces human errors.
2. Real-Time Analytics: By continuously gathering and analyzing network data, IBN platforms provide actionable insights that enable proactive network optimization, troubleshooting, and security threat detection. This real-time visibility empowers IT teams to make informed decisions and respond swiftly to network events.
3. Automation and Orchestration: IBN leverages automation to dynamically adjust network configurations based on intent. It automates routine tasks, such as device provisioning, policy enforcement, and network provisioning, freeing up IT resources for more strategic initiatives.
1. Enhanced Network Security: IBN's ability to enforce policies consistently across the network enhances security by minimizing vulnerabilities and ensuring compliance. It enables organizations to swiftly identify and respond to security threats, reducing the risk of data breaches.
2. Improved Network Efficiency: IBN's automation capabilities streamline network operations, reducing manual errors and optimizing performance. Through dynamic network provisioning and configuration, organizations can adapt to changing business needs, ensuring efficient resource utilization.
3. Simplified Network Management: The abstraction of network complexity and the use of high-level policies simplify network management tasks. This reduces the learning curve for IT professionals and accelerates the deployment of new network services.
Intent-Based Networking represents a major leap forward in network management, offering organizations unprecedented levels of control, agility, and security. By embracing the power of automation, AI, and intent-driven policies, businesses can unlock the full potential of their networks and position themselves for future success
Matt Conran
Highlights: Intent Based Networking
Understanding Intent-Based Networking
– Intent-Based Networking is a paradigm shift in network management focusing on translating high-level business objectives into automated network configurations. By leveraging artificial intelligence and machine learning, IBN aims to streamline network operations, enhance security, and improve overall network performance. It truly empowers network administrators to align the network’s behavior with business intent.
– IBN offers many benefits that make it a game-changer in the networking realm. Firstly, it enables faster network provisioning and troubleshooting, reducing human error and minimizing downtime. Secondly, IBN enhances network security through real-time monitoring and automated threat response. Additionally, IBN provides valuable insights and analytics, enabling better decision-making and optimized resource allocation.
– Implementing IBN requires careful planning and execution. It integrates various components, such as a centralized controller, network devices with programmable interfaces, and AI-powered analytics engines. Furthermore, organizations must assess their network infrastructure and determine the automation and intelligence needed. Collaborating with experienced vendors and leveraging their expertise can facilitate implementation.
Defining: Intent-Baed Networking
Intent-Based Networking can only be understood if we understand what Intent is. Purpose makes the definition of intent easier to understand because it is a synonym. Intentions or purposes vary from person to person, department to department, and organization to organization. It is possible for an organization to provide the best in class software to schools or to provide the best phones available. The purpose of a business process can be to fulfill the described task as efficiently as possible. It is, of course, the potential for a person to have multiple intentions or purposes. Generally, intent or purpose describes a goal to be achieved.
Example: Cisco DNA
As a network infrastructure built on Cisco DNA, IBN describes how to manage, operate, and enable a digital business using the network. An intent within the industry is translated into a network configuration that fulfills that intent. This is accomplished by defining the intent utilizing a set of (repetitive) steps. Cisco DNA approaches networks using all aspects of IBN (design principles, concepts, etc.).
**Challenge: The Lack of Agility**
Intent-based networking is not just hype; we see many intent-driven networks already with many SD WAN overlay roll-outs. It is a necessary development; from a technology standpoint, it has arrived. However, cultural acceptance will take a little longer. Organizations are looking to modernize their business processes and their networks.
Yet, traditional vertically integrated monolithic networking solutions prohibit the network from achieving agility. This is why we need intent-based networking systems. So, what is intent-based networking? Intent-based networking is where an end-user describes what the network should do, and the system automatically configures the policy. It uses declarative statements instead of imperative statements.
**Converts the What into How**
You are telling the network what you want to accomplish, not precisely what to do and how to do it. For example, tell me what you want, not how to do it, all of which gets translated behind the scenes. Essentially, intent-based networking is a piece of open networking software that takes the “what” and converts it into the “how.” The system generates the resulting configuration for design and device implementation.
The system is provided with algorithms that translate business intent into network configurations. Humans can not match the speed of algorithms, and this is key. The system is aware of the network state and can ingest real-time network status from multiple sources in a transport and protocol-agnostic way.
**The Desired State**
It adds the final piece of the puzzle by validating in real time that the intent is being met. The system continuously compares the actual to the desired state of the running network. If the desired state is unmet, corrective actions such as modifying a QoS policy or applying an access control list (ACL) can occur. This allows for a closer alignment between the network infrastructure and business initiatives and maintains the network’s correctness.
Related: Before you proceed, you may find the following posts helpful.
Intent Based Networking
Learning more about intent-based networking is essential to understanding it. An intent is a brief description of the purpose and a concrete, predetermined set of steps that must be executed to (successfully) achieve the Intent. This principle can also be applied to the operation of a network infrastructure. The Intent and its steps precisely describe what needs to be done on the network to accomplish a specific task.
For example, the application is migrating to the cloud. In this case, the Intent or steps may include the following. First, take the existing access policy for that application from the data center policy, transform the policy into an application policy for Internet access, deploy the procedure on all perimeter firewalls, and change the routing for that application to the cloud.
Critical Principles of Intent-Based Networking:
1. Translation: Intent-based networking automatically translates high-level business objectives into network policies and configurations. By understanding the desired intent, the network infrastructure can autonomously make the necessary adjustments to align with the organization’s goals.
2. Automation: Automation is a fundamental aspect of IBN. By automating routine network tasks, such as provisioning, configuration, and troubleshooting, network administrators can focus on strategic activities that add value to the organization. Automation also reduces the risk of human error, leading to improved network reliability and security.
3. Assurance: IBN provides continuous monitoring and verification of network behavior against the intended state. By constantly comparing the network’s current state with the desired intent, IBN can promptly identify and mitigate any configuration drift or anomalies. This proactive approach enhances network visibility, performance, and compliance.
Benefits of Intent-Based Networking:
1. Simplified Network Management: With IBN, network administrators can easily manage complex networks. By abstracting the complexity of individual devices and focusing on business intent, IBN simplifies network operations, reducing the need for manual configuration and troubleshooting.
2. Enhanced Agility and Scalability: IBN enables organizations to respond quickly to changing business requirements and effortlessly scale their networks. By automating network provisioning and configuration, IBN supports rapid deployment and seamless integration of new services and devices.
3. Improved Network Security: Security is a top concern for modern networks. IBN offers enhanced security by continuously monitoring network behavior and enforcing security policies. This proactive approach reduces the risk of security breaches and enables faster threat detection and response.
4. Optimized Performance: IBN leverages real-time analytics and machine learning to optimize network performance. By dynamically adjusting network configurations based on traffic patterns and user behavior, IBN ensures optimal performance and user experience.
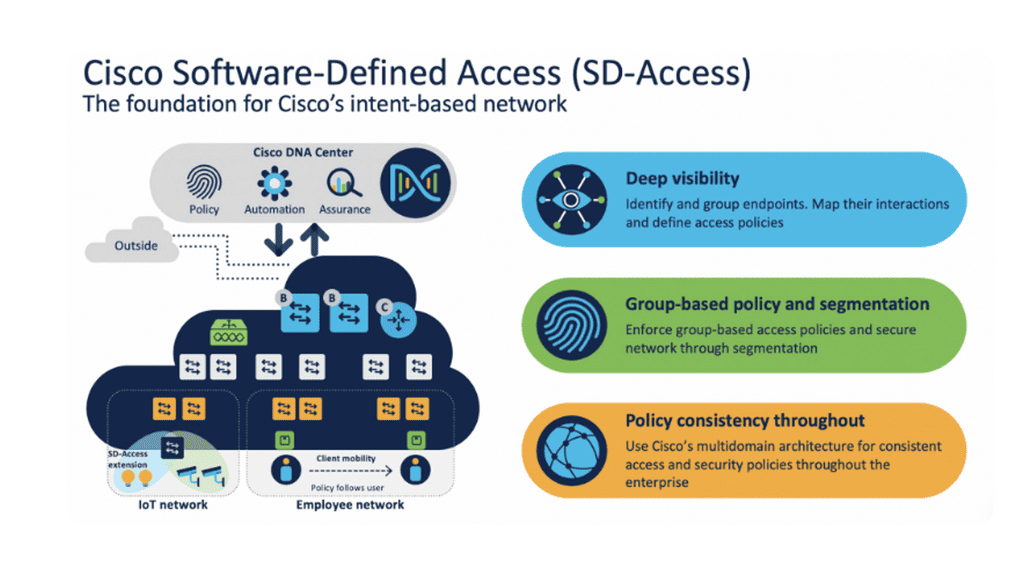
Intent-Based Networking Solution: Cisco SD-Access
The Cisco SD-Access digital network evolution transforms traditional campus LANs into intent-driven, programmable networks. Campus Fabric and DNA Center are Cisco SD-Access’s two main components. The Cisco DNA Center automates and assures the creation and monitoring of the Cisco Campus Fabric.
Cisco Campus Fabric Architecture: In Cisco SD-Access, fabric roles and terminology differ from those in traditional three-tier hierarchical networks. To create a logical topology, Cisco SD-Access implements fabric technology using overlay networks running on a physical (underlay) network.
Underlay networks are traditional physical networks that connect LAN devices such as routers and switches. Their primary function is to provide IP connectivity for traffic to travel from one point to another. Due to the IP-based underlay, any interior gateway protocol (IGP) can be utilized.
Overlay and Underlay Networking
Fabrics are overlay networks. In the IT world, Internet Protocol Security (IPsec), Generic Routing Encapsulation (GRE), Dynamic Multipoint Virtual Private Networks (DMVPN), Multiprotocol Label Switching (MPLS), Location Identifier Separation Protocol (LISP), and others are commonly used with overlay networks to connect devices virtually. An overlay network is a logical topology that connects devices over a topology-independent physical underlay network.
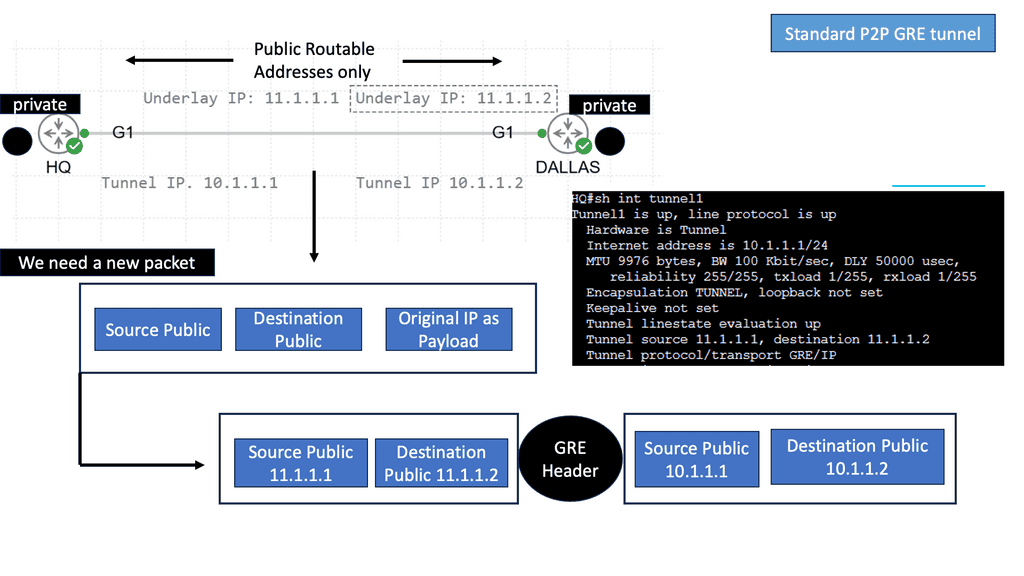
Example Overlay Technology: GRE Point to Point
Data & Control Plane
Forwarding and control planes are separated in overlay networks, resulting in a flexible, programmable, and scalable network. To simplify the underlay, the control plane and data plane are separated. As the control plane becomes the network’s brain, it allows faster forwarding and optimizes packets and network reliability. As an underlay for the centralized controller, Cisco SD-Access supports building a fabric using an existing network.
Underlay networks can be automated with Cisco DNA Center. As a result, it is helpful for new implementations or infrastructure growth since it eliminates the hassle of setting up the underlay. For differentiation, segmentation, and mobility, overlay networks often use alternate forwarding attributes in an additional header.
 Networking Complexity
Networking Complexity
Networks continue to get more complex as traffic demands increase. While software-defined networking (SDN) can abstract the underlying complexities, we must consider how we orchestrate the policy and intent across multi-vendor, multi-domain elements.
To overcome complexity, you have to abstract. We have been doing this with tunneling for decades. However, different abstractions are used at the business and infrastructure resource levels.
At a business level, you need to be flexible, as rules will change and must be approached differently from how the operating system models resources. We must make new architecture decisions for this, as it’s not just about configuration management and orchestrations. None of these can look at the network state, which we need to do.
For this, we need network intelligence. Networks are built and managed today using a manual approach without algorithmic validation. The manual process of networking will not be viable in the future. Let’s face it: humans make mistakes.
There are many reasons for network outages, ranging from software bugs and hardware/power failure to security breaches. All of these come from a lack of implementation of network security. However, human error is still the number one cause. Manual configuration inhibits us. Intent-based networking eliminates this inhibition.
The traditional approach to networking
In the traditional network model, there is a gap between the architect’s intent and what’s achieved. Not just for device configuration but also for achieved runtime behavior. Until now, there has not been a way to validate the original intent or to have a continuous verification mechanism.
Once you have achieved this level of assurance, you can focus on business needs and not be constrained by managing a legacy network. For example, Netflix moved its control plane to the cloud and now focuses all its time on its customer base.
We have gone halfway and spent billions of dollars on computing storage and applications, but the network still lags. The architecture and protocols have become more complex, but the management tools have not kept pace. Fortunately, now, this is beginning to change.
Software-defined networking; Slow Deployments
SDN shows great promise that could release networking, but deployments have been slow. Primarily down to large cloud-scale organizations with ample resources and dollars. But what can the rest of the industry do if we do not have that level of business maturity? Intent-based networking is a natural successor to SDN, as many intent-based vendors have borrowed the same principles and common architectures.
The systems are built on the divide between the application and the network infrastructure. However, SDN operates at the network architecture level, where the control plane instructs the data plane forwarding node. Intent-based systems work higher at the application level to offer true brownfield network automation.
SDN and SD-WAN have made considerable leaps in network programmability, but intent-based networking is a further leap to zero-touch self-healing networks. For additional information on SD-WAN, including the challenges with existing WANs, such as lack of agility with BGP ( what is BGP protocol in networking ) and the core features of SD-WAN, check out this SDWAN tutorial.
Intent-Based Networking Use Case
The wide-area network (WAN) edge consists of several network infrastructure devices, including Layer 3 routers, SD-WAN appliances such as Viptela SD-WAN, and WAN optimization controllers. These devices could send diagnostic information for the intent-based system to ingest. The system can ingest from multiple sources, including a monitoring system and network telemetry.
As a result, the system can track application performance over various links. Suppose there is a performance-related problem, the policies are unmet, and application performance degrades.
In that case, the system can take action, such as rerouting the traffic over a less congested link or notifying a network team member. The intent-based system does not have to take corrective action, similar to how IDS/IPS is deployed. These devices can take disciplinary action if necessary, but many use IDS/IPS to alert.
Looking deeper into intent-based networking systems
The intent-based architecture combines machine learning (ML), cognitive computing, and deep analytics, providing enhanced levels of automation and programmability through an easy-to-use GUI. Combining these technologies allows you to move from a reactive to a proactive system.
ML, a sub-application of artificial intelligence (AI), allows intent-based systems to analyze and learn from data automatically without explicit programming. Therefore, it enables systems to understand and predict the data for autonomous behavior. Intent-based networking represents a radical new approach to network architecture and takes networking to the next level in intelligence.
It is not a technology that will be accepted overnight. Its adoption will be slow as, to some, a fully automated network can sound daunting, placing faith in your business, which for many organizations is the network.
However, deploying intent-based networking systems offers a new way to build and operate networks, which increases agility, availability, and security compared to traditional networking.
Intent-based networking (IBN) is transforming the way networks are managed. By shifting the focus from device-centric configurations to intent-driven outcomes, IBN simplifies network management, enhances agility and scalability, improves security, and optimizes network performance. As organizations strive to meet the demands of the digital age, embracing this innovative approach can pave the way for a more efficient and intelligent network infrastructure.
Summary: Intent Based Networking
In today’s rapidly evolving digital landscape, traditional networking approaches often struggle to keep pace with the dynamic needs of modern organizations. This is where intent-based networking (IBN) steps in, revolutionizing how networks are designed, managed, and optimized. By leveraging automation, artificial intelligence, and machine learning, IBN empowers businesses to align their network infrastructure with their intent, enhancing efficiency, agility, and security.
Understanding Intent-Based Networking
Intent-based networking goes beyond traditional methods by enabling businesses to articulate their desired outcomes to the network rather than manually configuring every network device. This approach allows network administrators to focus on strategic decision-making and policy creation while the underlying network infrastructure dynamically adapts to fulfill the intent.
Key Components of Intent-Based Networking
1. Policy Definition: Intent-based networking relies on clear policies that define the network’s intended behavior. These policies can be based on business objectives, security requirements, or application-specific needs. By translating high-level business intent into actionable policies, IBN streamlines network management.
2. Automation and Orchestration: Automation lies at the heart of IBN. Network automation tools automate routine tasks like configuration, provisioning, and troubleshooting, freeing valuable time for IT teams to focus on critical initiatives. Orchestration ensures seamless coordination and integration between various network elements.
3. Artificial Intelligence and Machine Learning: IBN leverages AI and ML technologies to continuously monitor, analyze, and optimize network performance. These intelligent systems can detect anomalies, predict potential issues, and self-heal network problems in real-time, enhancing network reliability and uptime.
Benefits of Intent-Based Networking
1. Enhanced Network Agility: IBN enables organizations to quickly adapt to changing business requirements and market dynamics. By abstracting the complexity of network configurations, businesses can scale their networks, deploy new services, and implement changes with ease and speed.
2. Improved Security and Compliance: Intent-based networking incorporates security policies directly into network design and management. By automating security measures and continuously monitoring network behavior, IBN helps identify and respond to threats promptly, reducing the risk of data breaches and ensuring compliance with industry regulations.
3. Optimal Resource Utilization: IBN helps organizations optimize resource allocation across the network through AI-driven insights and analytics. By dynamically adjusting network resources based on real-time demands, businesses can ensure optimal performance, minimize latency, and reduce operational costs.
Conclusion:
Intent-based networking represents a paradigm shift in network management, offering a holistic approach to meet the ever-evolving demands of modern businesses. By aligning network behavior with business intent, automating configuration and management tasks, and leveraging AI-driven insights, IBN empowers organizations to unlock new levels of agility, security, and efficiency in their network infrastructure.