Zero Trust Network ZTN
In today’s rapidly evolving digital landscape, ensuring the security and integrity of sensitive data has become more crucial than ever. Traditional security approaches are no longer sufficient to protect against sophisticated cyber threats. This is where the concept of Zero Trust Network (ZTN) comes into play. In this blog post, we will explore the fundamentals of ZTN, its key components, and its significance in enhancing digital security.
Zero Trust Network, often referred to as ZTN, is a security framework that operates on the principle of granting access based on user identity verification and contextual information, rather than blindly trusting a user's location or network. Unlike traditional perimeter-based security models, ZTN treats every user and device as potentially untrusted, thereby minimizing the attack surface and reducing the risk of data breaches.
1. Identity and Access Management (IAM): IAM plays a crucial role in ZTN by providing robust authentication and authorization mechanisms. It ensures that only authorized users with valid credentials can access sensitive resources, regardless of their location or network.
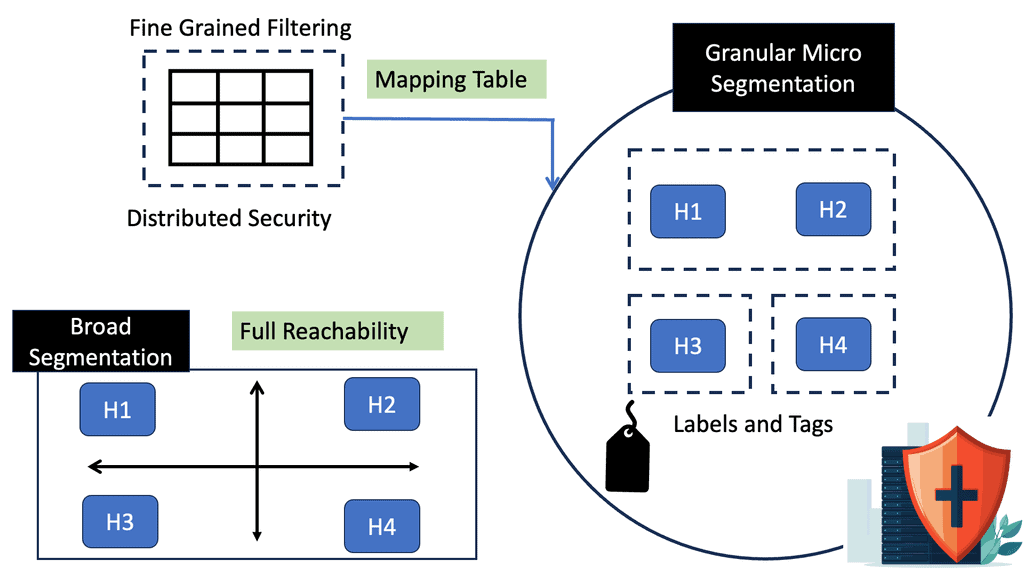
2. Micro-segmentation: Micro-segmentation is another vital component of ZTN that involves dividing the network into smaller segments or zones. Each segment is isolated from others, allowing for granular control over access permissions and minimizing lateral movement within the network.
3. Multi-factor Authentication (MFA): MFA adds an extra layer of security to the ZTN framework by requiring users to provide multiple forms of verification, such as passwords, biometrics, or security tokens. This significantly reduces the risk of unauthorized access, even if the user's credentials are compromised.
- Enhanced Security: ZTN provides a proactive security approach by continuously verifying user identity and monitoring their behavior. This significantly reduces the risk of unauthorized access and data breaches.
- Improved Compliance: ZTN assists organizations in meeting regulatory compliance requirements by enforcing strict access controls, monitoring user activity, and maintaining comprehensive audit logs.
- Flexibility and Scalability: With ZTN, organizations can easily adapt to changing business needs and scale their security infrastructure without compromising on data protection.
Zero Trust Network (ZTN) represents a paradigm shift in the field of cybersecurity. By adopting a user-centric approach and focusing on identity verification and contextual information, ZTN offers enhanced security, improved compliance, and flexibility to organizations in the modern digital landscape. Embracing ZTN is crucial for staying ahead of evolving cyber threats and safeguarding sensitive data in today's interconnected world.
Matt Conran
Highlights: Zero Trust Network ZTN
Zero Trust Network ZTN
Zero Trust Networks, also known as Zero Trust Architecture, is an innovative security framework that operates on the principle of “never trust, always verify.” Unlike traditional network security models that rely heavily on perimeter defenses, Zero Trust Networks take a more granular and comprehensive approach. The core idea is to assume that every user, device, or application attempting to access the network is potentially malicious. This approach minimizes the risk of unauthorized access and data breaches.
Certain fundamental principles must be embraced to implement a Zero Trust Network effectively. These include:
1. Least Privilege: Users and devices are only granted the minimum level of access necessary to perform their tasks. This principle ensures that the potential damage is limited even if one component is compromised.
2. Micro-segmentation: Networks are divided into smaller segments or zones, and access between these segments is strictly controlled. This prevents lateral movement within the network and limits the spread of potential threats.
3. Continuous Authentication: Instead of relying solely on static credentials, Zero Trust Networks continuously verify the identity and security posture of users, devices, and applications. This adaptive authentication helps detect and mitigate threats in real time.
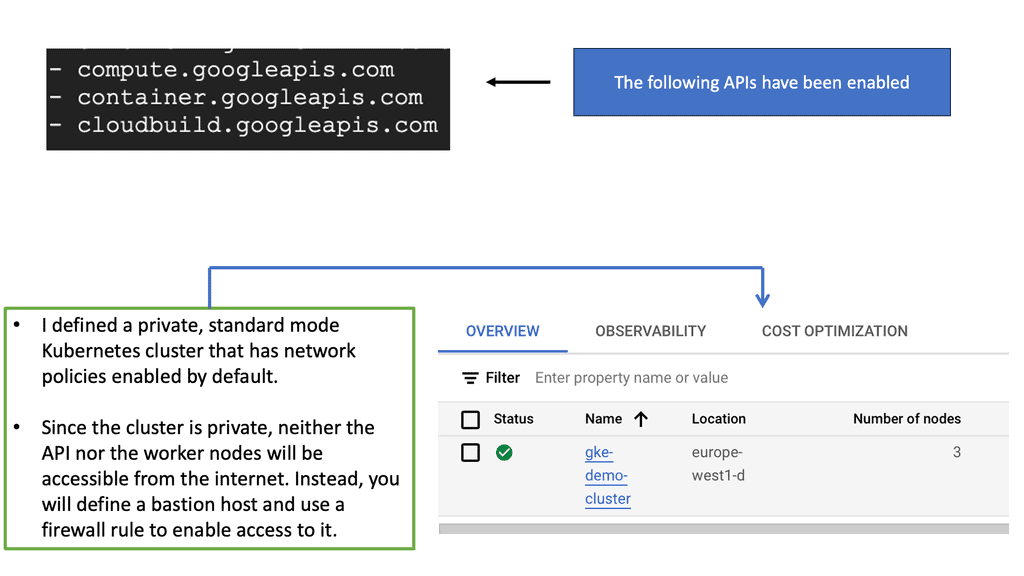
Google Cloud GKE Network Policies
**Understanding Google Kubernetes Engine (GKE) Network Policies**
Google Kubernetes Engine offers a powerful platform for orchestrating containerized applications, but with great power comes the need for robust security measures. Network policies in GKE allow you to define rules that control the communication between pods and other network endpoints. These policies are essential for managing traffic flows and ensuring sensitive data remains protected from unauthorized access.
—
**Implementing Zero Trust Networking in GKE**
The zero trust networking model is a security concept centered around the belief that organizations should not automatically trust anything inside or outside their perimeters. Instead, they must verify anything and everything trying to connect to their systems before granting access.
To implement zero trust in GKE, you need to:
1. **Define Strict Access Controls:** Ensure that only authorized entities can communicate with each other by applying stringent network policies.
2. **Continuously Monitor Traffic:** Use tools to monitor and log network traffic patterns, allowing for real-time threat detection and response.
3. **Segment the Network:** Divide your network into smaller, isolated segments to limit the lateral movement of threats.
These steps are not exhaustive, but they provide a solid foundation for deploying a zero trust environment in GKE.
—
**Best Practices for Configuring Network Policies**
When configuring network policies in GKE, following best practices can significantly enhance your security posture:
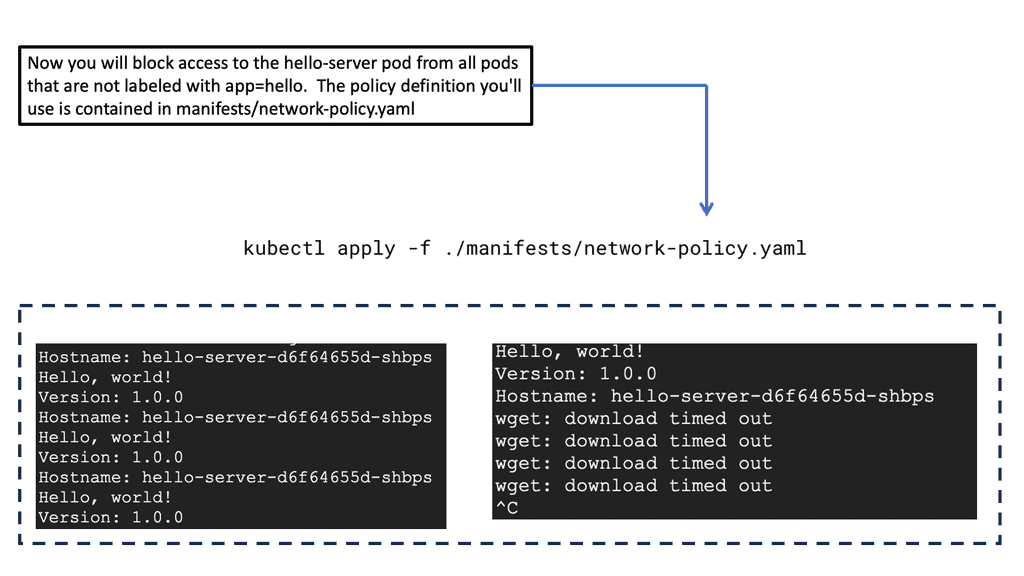
– **Begin with a Deny-All Policy:** Start with a default deny-all policy to block all incoming and outgoing traffic, then explicitly define permissible traffic.
– **Use Labels for Isolation:** Leverage Kubernetes labels to isolate pods and create specific rules that apply only to certain workloads.
– **Regularly Review and Update Policies:** As your application evolves, ensure your network policies are updated to reflect any changes in your deployment architecture.
These practices will contribute to a more secure and efficient network policy implementation in your GKE environment.
Zero Trust VPC Service Controls
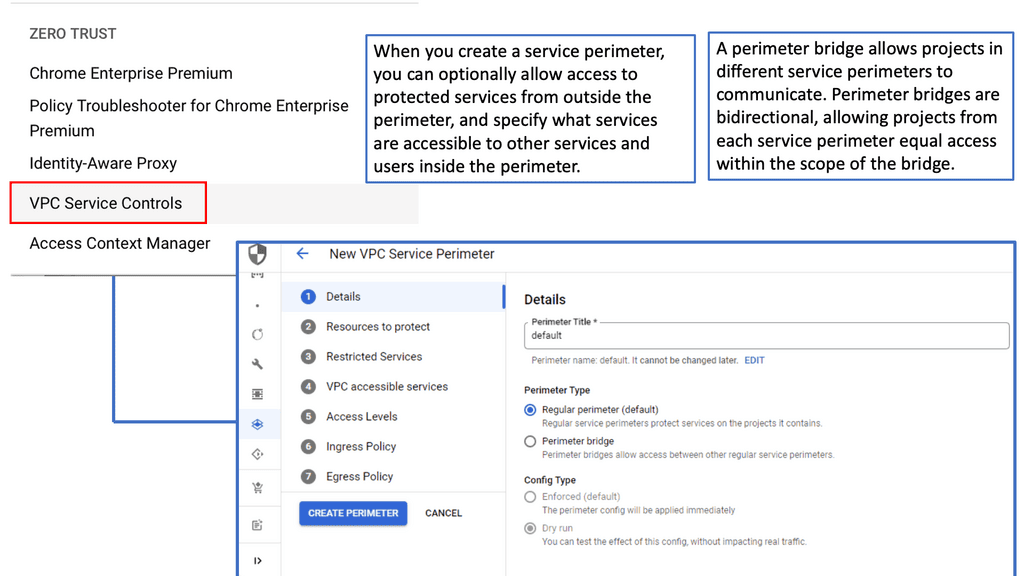
**What are VPC Service Controls?**
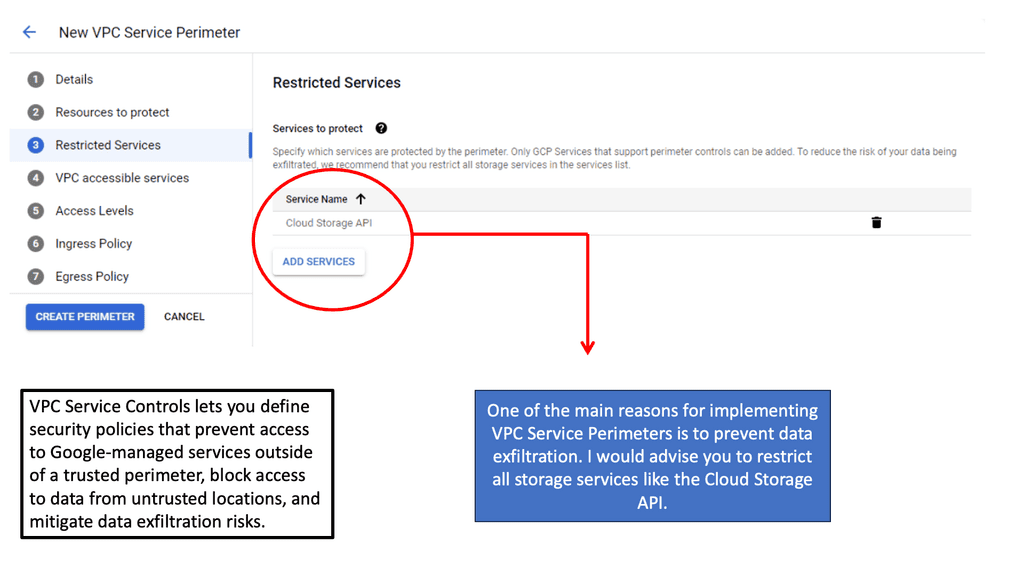
VPC Service Controls enable organizations to establish a security perimeter around Google Cloud services, providing a more granular level of access control. This ensures that only authorized users and devices can access sensitive data, significantly reducing the risk of unauthorized access. By leveraging VPC Service Controls, companies can enforce security policies with ease, thus enhancing the overall security framework of their cloud infrastructure.
**Zero Trust Network Design: A Paradigm Shift**
The concept of zero trust network design is a transformative approach to security that assumes no user or device, whether inside or outside the network, should be inherently trusted. Instead, every access request is verified, authenticated, and authorized before granting access. By integrating VPC Service Controls into a zero trust architecture, organizations can ensure that their cloud environment is not just protected from external threats but also from potential insider threats.
**Implementing VPC Service Controls in Google Cloud**
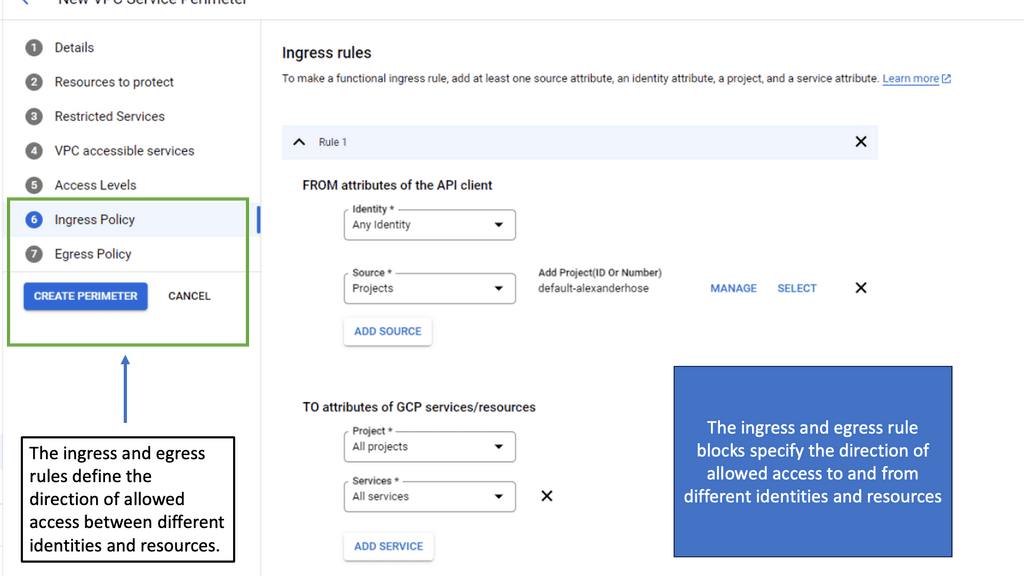
Implementing VPC Service Controls in Google Cloud involves several strategic steps. Firstly, defining service perimeters is crucial; this involves specifying which services are to be protected and determining access policies. Next, organizations should continuously monitor access requests to detect any anomalies or unauthorized attempts. Google Cloud provides tools that allow for comprehensive logging and monitoring, aiding in maintaining the integrity of the security perimeter.
**Benefits of VPC Service Controls**
VPC Service Controls offer numerous benefits, including enhanced data protection, compliance with industry regulations, and improved threat detection capabilities. By establishing a robust security perimeter, organizations can ensure the confidentiality and integrity of their data. Additionally, the ability to enforce granular access controls aligns with many regulatory standards, making it easier for businesses to meet compliance requirements.
Zero Trust IAM
*Understanding the IAM Core Components**
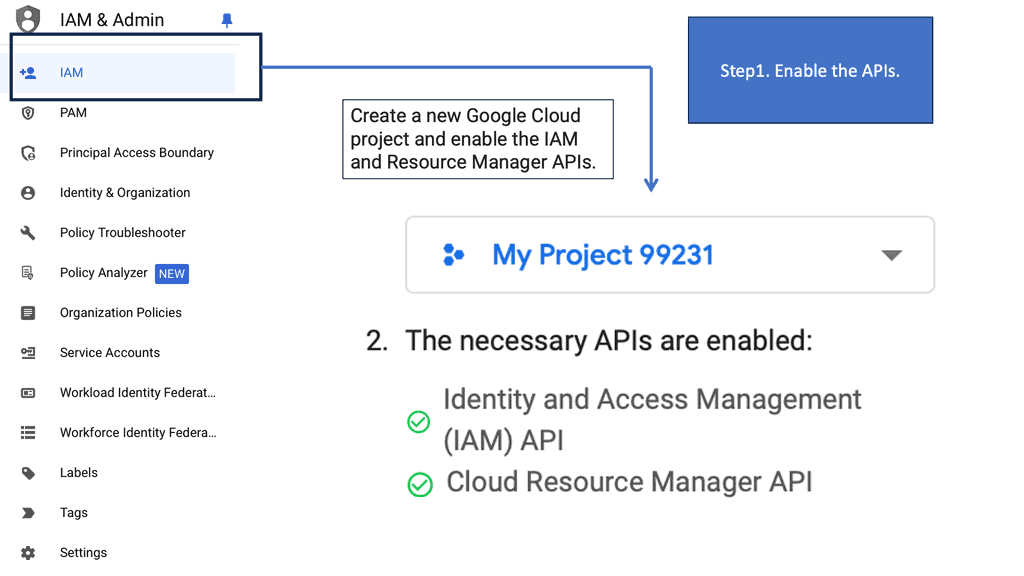
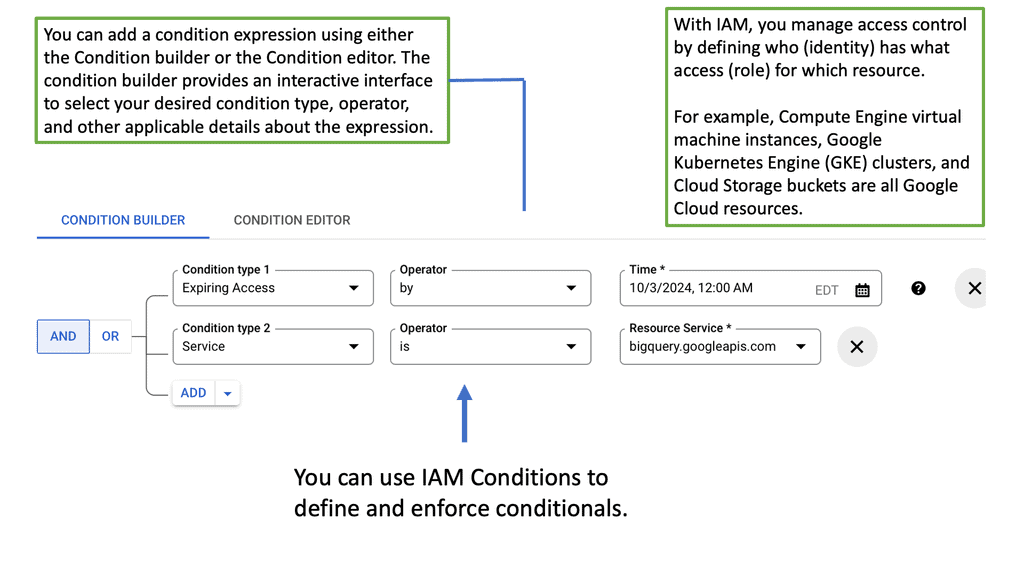
Google Cloud IAM is designed to provide a unified access control interface that enables administrators to manage who can do what across their cloud resources. At its core, IAM revolves around three primary components: roles, members, and policies.
– **Roles**: Roles define a set of permissions. They can be predefined by Google or customized to suit specific organizational needs. Roles are assigned to members to control their access to resources.
– **Members**: Members refer to the entities that need access, such as users, groups, or service accounts.
– **Policies**: Policies bind members to roles, specifying what actions they can perform on resources.
By accurately configuring these components, organizations can ensure that only authorized users have access to specific resources, thereby reducing the risk of data breaches.
**Integrating Zero Trust Network Design**
The zero trust network design is a security concept centered around the idea that organizations should not automatically trust anything inside or outside their perimeters. Instead, they must verify anything and everything trying to connect to their systems. Google Cloud IAM can seamlessly integrate with a zero trust architecture by implementing the principle of least privilege—granting users the minimum levels of access they need to perform their functions.
With Google Cloud IAM, administrators can enforce strong authentication, conduct regular access reviews, and monitor user activities to ensure compliance with zero trust principles. This integration not only boosts security but also enhances operational efficiency by minimizing the attack surface.
Google Cloud’s Zero Trust framework ensures that every request, regardless of its origin, is authenticated and authorized before granting access. This model reduces the attack surface and significantly mitigates the risk of data breaches, making it an ideal choice for organizations prioritizing security in their service networking strategies.
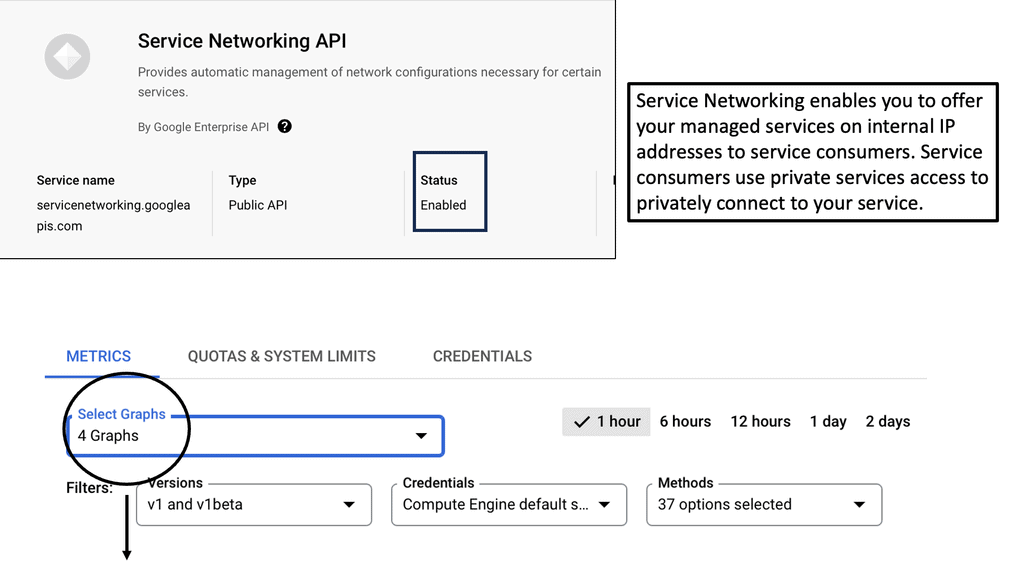
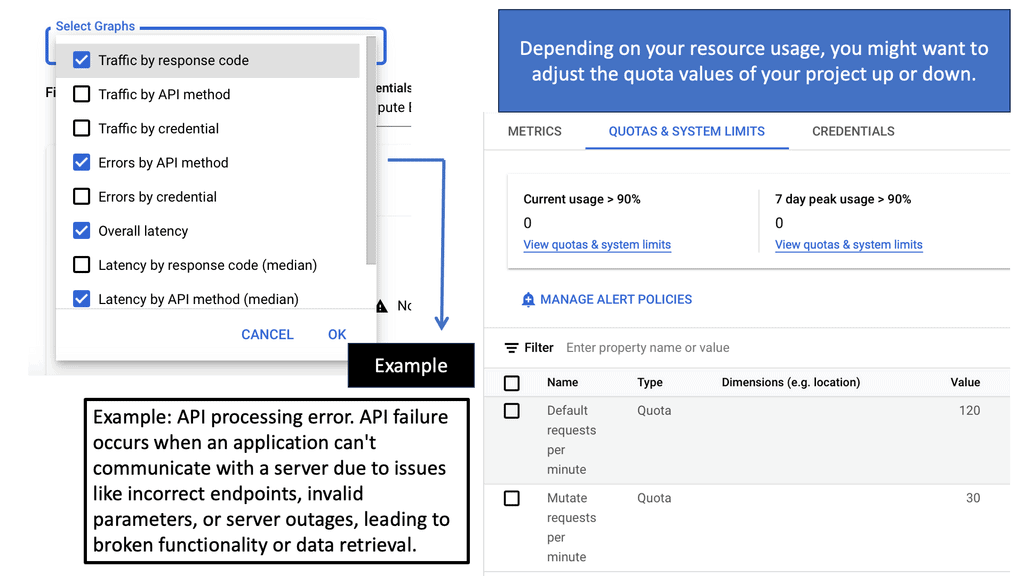
Service Networking APIs
### Benefits of Integrating Zero Trust with Service Networking APIs
Integrating Zero Trust principles with service networking APIs offers numerous advantages. First, it enhances security by ensuring that only verified and authenticated requests can access services. Second, it provides better visibility and control over network traffic, allowing organizations to detect and respond to threats in real time. Third, it supports compliance with industry regulations by implementing strict access controls and audit trails. By combining Zero Trust with service networking APIs, businesses can achieve a more secure and resilient network architecture that aligns with their operational goals.
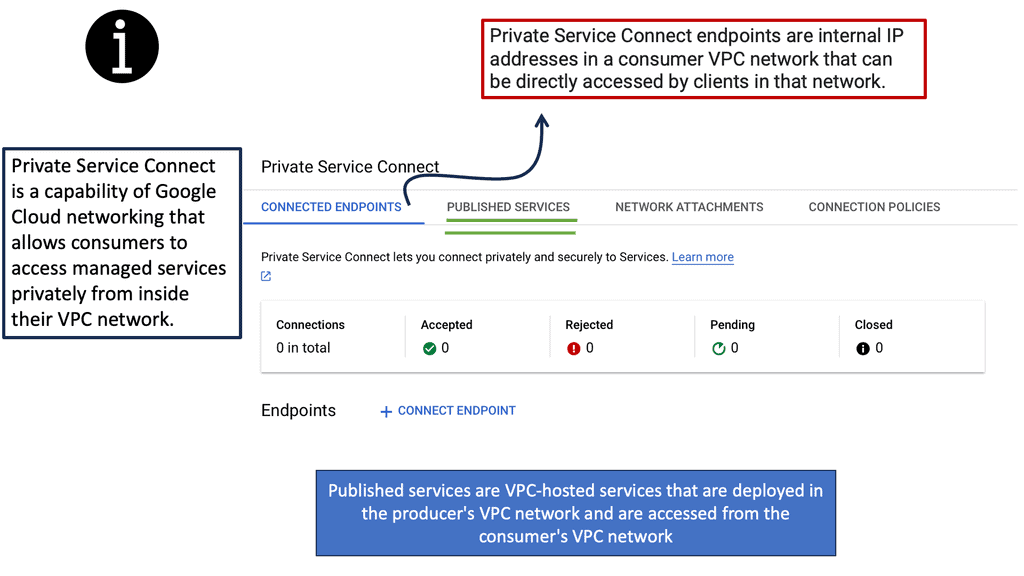
Understanding Private Service Connect
Private Service Connect is a Google Cloud service that allows you to establish private and secure connections between your Virtual Private Cloud (VPC) networks and Google services or third-party services. By leveraging this service, you can consume services while keeping your network traffic private, eliminating the exposure of your data to the public internet. This aligns perfectly with the zero trust security model, which presumes that threats can exist both inside and outside the network and therefore requires strict user authentication and network segmentation.
—
### The Role of Zero Trust in Cloud Security
Zero trust is no longer just a buzzword; it’s a necessary paradigm in today’s cybersecurity landscape. The model operates on the principle of “never trust, always verify,” which means every access request is thoroughly vetted before granting permission. Private Service Connect supports zero trust by ensuring that your data does not traverse the public internet, reducing the risk of data breaches. It also allows for detailed control over who and what can access specific services, enforcing strict permissions and audits.
—
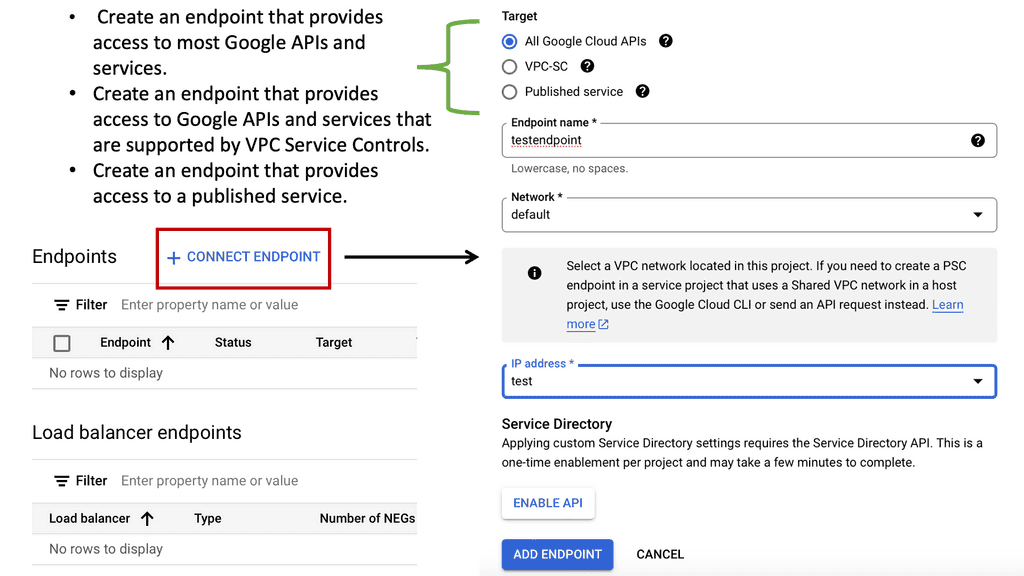
### How to Implement Private Service Connect
Implementing Private Service Connect is a strategic process that starts with understanding your network architecture and identifying the services you want to connect. You can create endpoints in your VPC network that securely connect to Google services or partner services. Configuration involves defining policies that determine which services can be accessed and setting up rules that manage these interactions. Google Cloud provides comprehensive documentation and support to guide you through the setup, ensuring a seamless integration into your existing cloud infrastructure.
Network Connectivity Center
**What is Google’s Network Connectivity Center?**
Google’s Network Connectivity Center (NCC) is a centralized platform designed to simplify and streamline network management for enterprises. It acts as a hub for connecting various network environments, whether they are on-premises, in the cloud, or across hybrid and multi-cloud setups. By providing a unified interface and advanced tools, NCC enables businesses to maintain consistent and reliable connectivity, reducing complexity and enhancing performance.
**Key Features of NCC**
1. **Centralized Management**: NCC offers a single pane of glass for managing all network connections. This centralized approach simplifies monitoring and troubleshooting, making it easier for IT teams to maintain optimal network performance.
2. **Scalability**: Whether you’re a small business or a large enterprise, NCC scales to meet your needs. It supports a wide range of network configurations, ensuring that your network infrastructure can grow alongside your business.
3. **Security**: Google’s emphasis on security is evident in NCC. It provides robust security features, including encryption, access controls, and continuous monitoring, to protect your network from threats and vulnerabilities.
4. **Integration with Google Cloud**: NCC seamlessly integrates with other Google Cloud services, such as VPC, Cloud VPN, and Cloud Interconnect. This integration enables businesses to leverage the full power of Google’s cloud ecosystem for their connectivity needs.
**Benefits of Using NCC**
1. **Improved Network Performance**: By providing a centralized platform for managing connections, NCC helps businesses optimize network performance. This leads to faster data transfer, reduced latency, and improved overall efficiency.
2. **Cost Savings**: NCC’s efficient management tools and automation capabilities can lead to significant cost savings. By reducing the need for manual intervention and minimizing downtime, businesses can achieve better ROI on their network investments.
3. **Enhanced Flexibility**: With NCC, businesses can easily adapt to changing network requirements. Whether expanding to new locations or integrating new technologies, NCC provides the flexibility needed to stay ahead in a dynamic market.
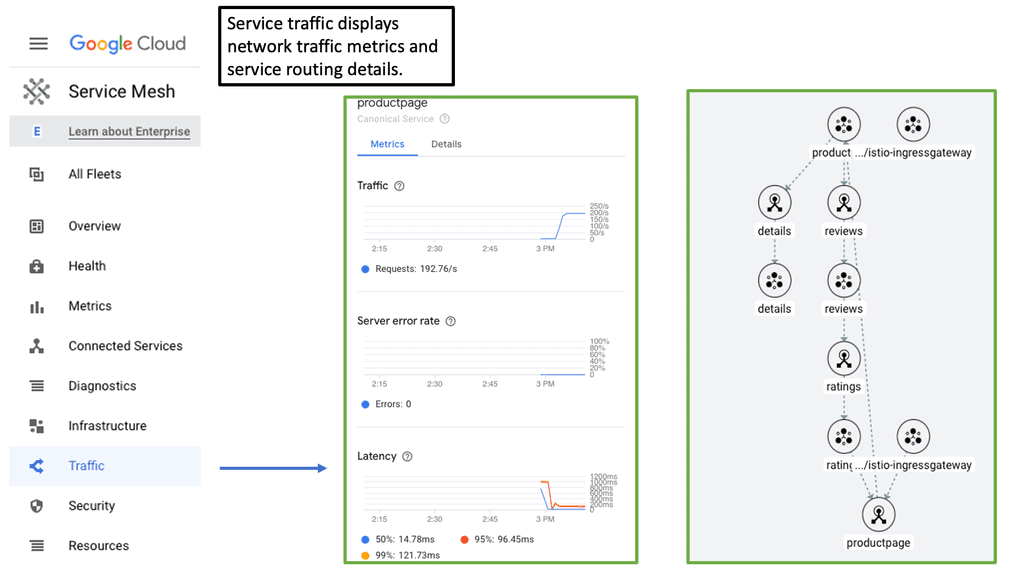
Zero Trust Service Mesh
#### What is a Cloud Service Mesh?
A Cloud Service Mesh is a dedicated infrastructure layer that enables seamless communication between microservices. It provides a range of functionalities, including load balancing, service discovery, and end-to-end encryption, all without requiring changes to the application code. Essentially, it acts as a transparent proxy, managing the interactions between services in a cloud-native environment.
#### The Role of Zero Trust Network in Cloud Service Mesh
One of the standout features of a Cloud Service Mesh is its alignment with Zero Trust Network principles. In traditional networks, security measures often focus on the perimeter, assuming that anything inside the network can be trusted. However, the Zero Trust model flips this assumption by treating every interaction as potentially malicious, requiring strict identity verification for every user and device.
A Cloud Service Mesh enhances Zero Trust by providing granular control over service-to-service communications. It enforces authentication and authorization at every step, ensuring that only verified entities can interact with each other. This drastically reduces the attack surface and makes it significantly harder for malicious actors to compromise the system.
#### Benefits of Implementing a Cloud Service Mesh
Implementing a Cloud Service Mesh offers numerous benefits that can transform your cloud infrastructure:
1. **Enhanced Security:** With built-in features like mutual TLS, service segmentation, and policy-driven security controls, a Cloud Service Mesh fortifies your network against threats.
2. **Improved Observability:** Real-time monitoring and logging capabilities provide insights into traffic patterns, helping you identify and resolve issues more efficiently.
3. **Scalability:** As your application grows, a Cloud Service Mesh can easily scale to accommodate new services, ensuring consistent performance and reliability.
4. **Simplified Operations:** By abstracting away complex networking tasks, a Cloud Service Mesh allows your development and operations teams to focus on building and deploying features rather than managing infrastructure.
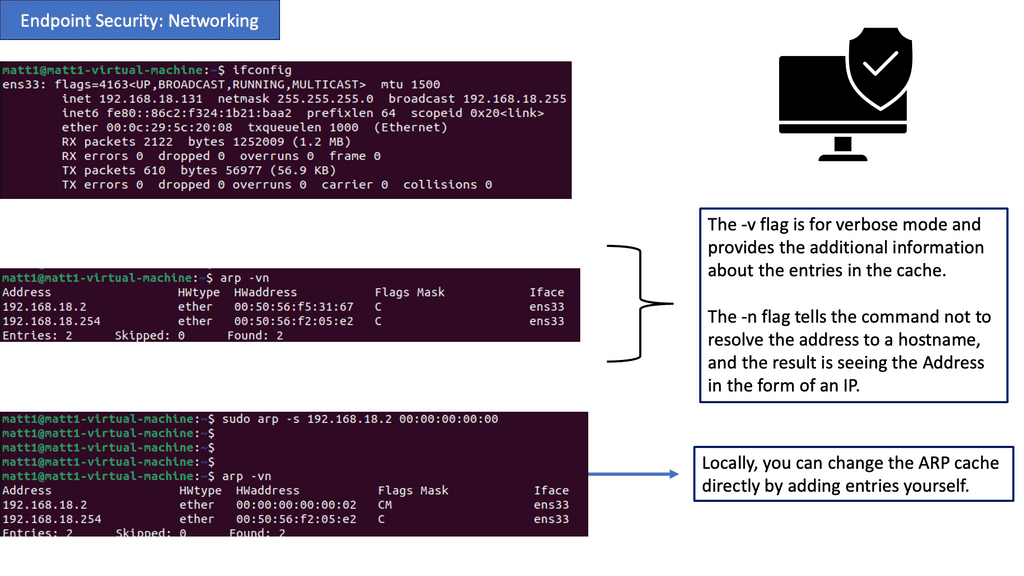
Understanding Endpoint Security
– Endpoint security refers to protecting endpoints, such as desktops, laptops, smartphones, and servers, from unauthorized access, malware, and other threats. It involves a combination of software, policies, and practices that safeguard these devices and the networks they are connected to.
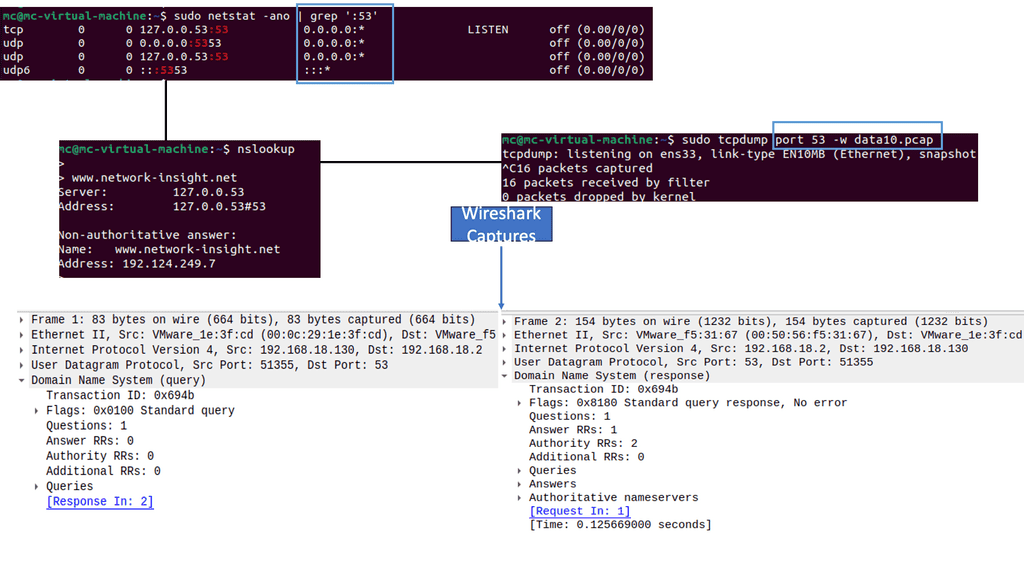
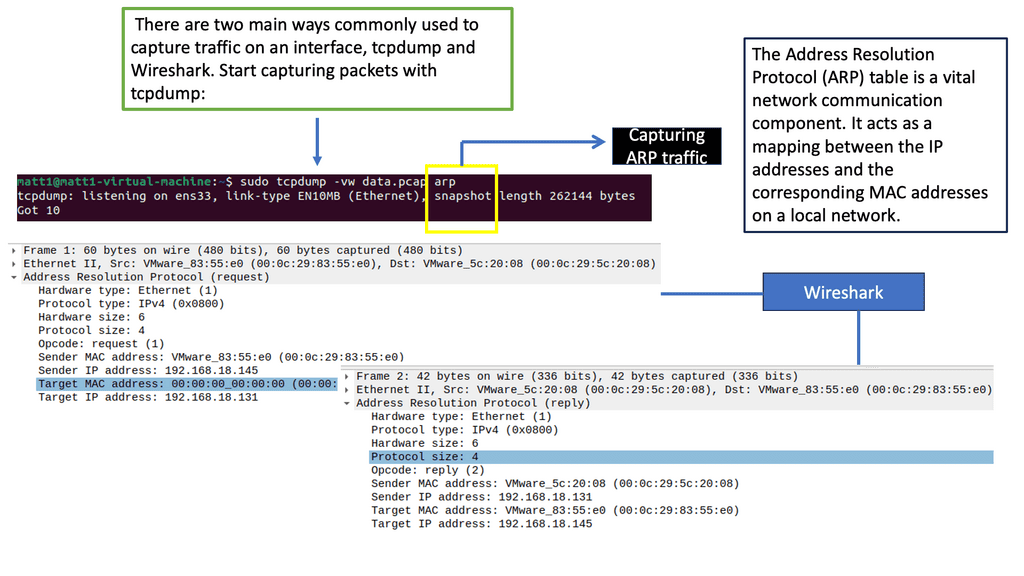
– ARP plays a vital role in endpoint security. It is responsible for mapping an IP address to a physical or MAC address, facilitating communication between devices within a network. Understanding how ARP works and implementing secure ARP protocols can help prevent attacks like ARP spoofing, which can lead to unauthorized access and data interception.
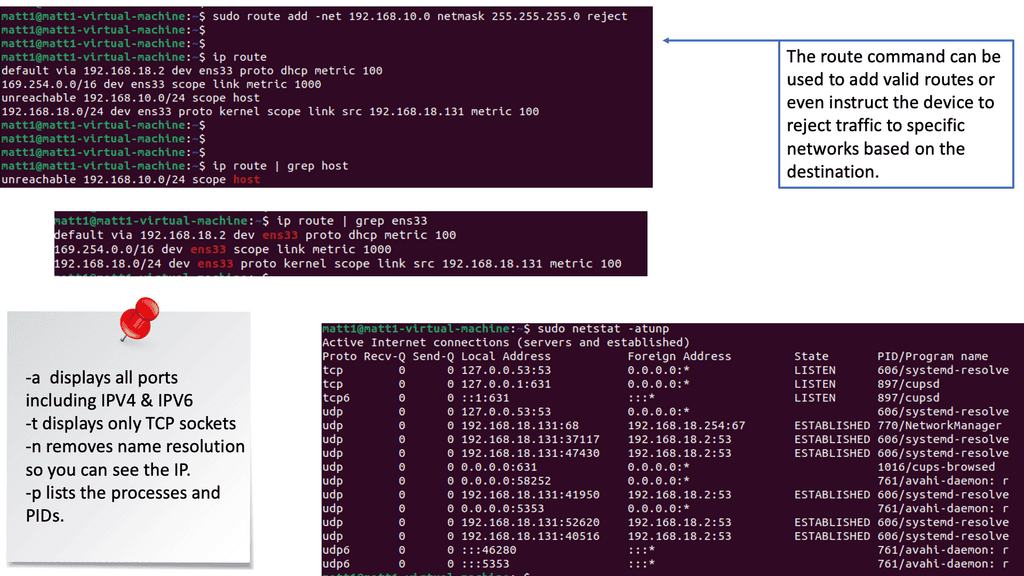
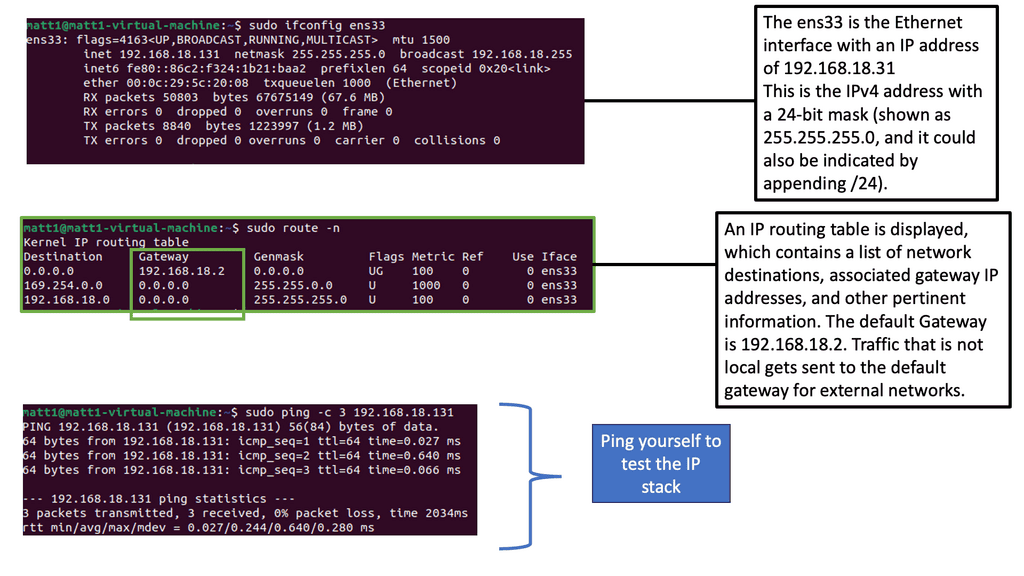
– Routing is crucial in network communication, and secure routing is essential for endpoint security. By implementing secure routing protocols and regularly reviewing and updating routing tables, organizations can ensure that data packets are directed through trusted and secure paths, minimizing the risk of interception or tampering.
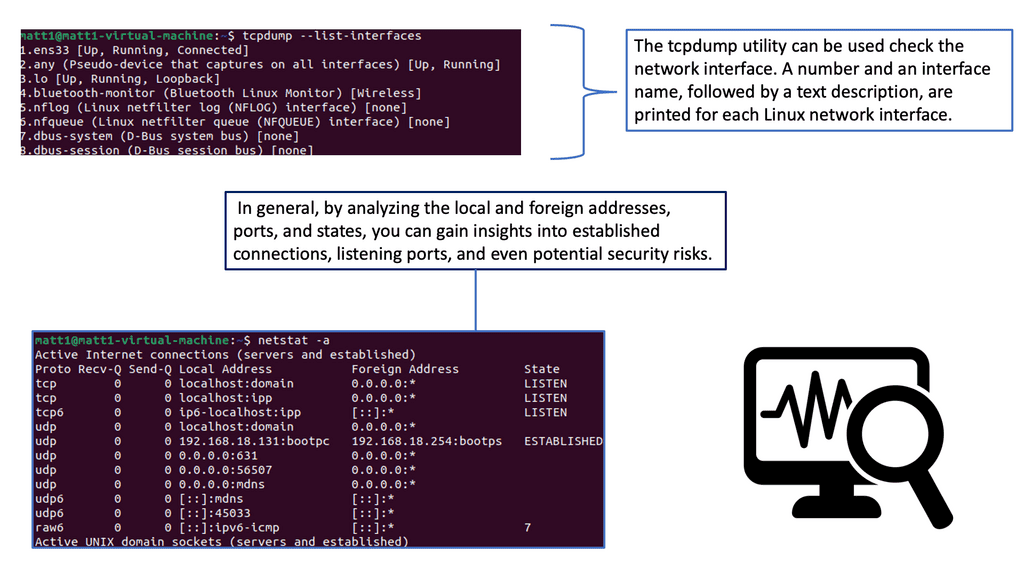
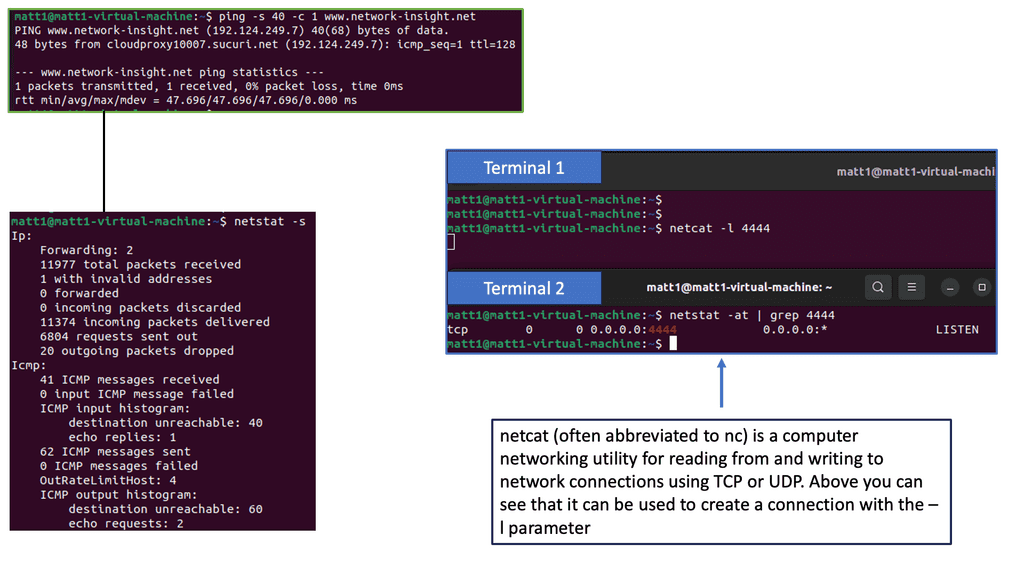
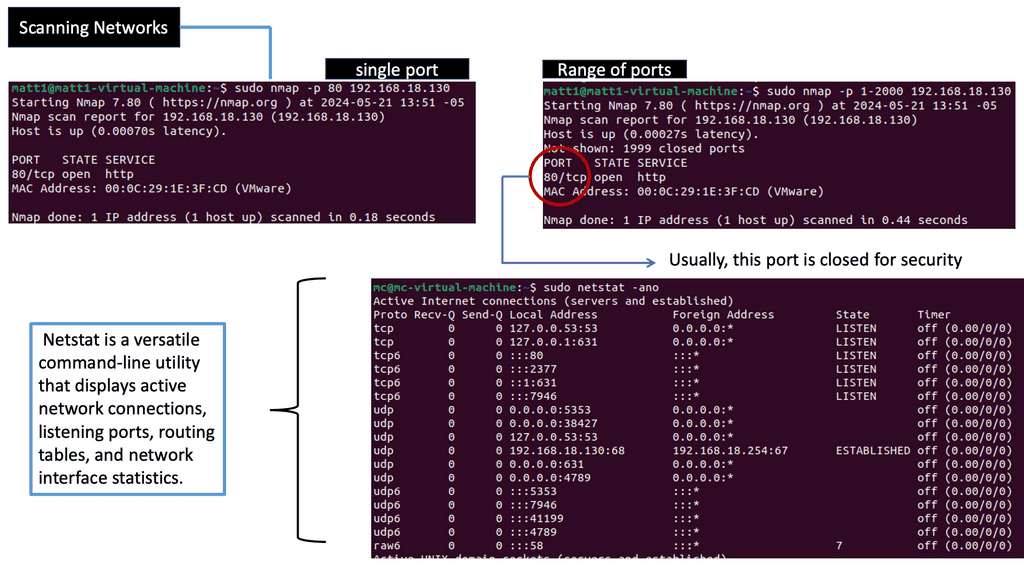
– Netstat, a command-line tool, provides valuable insights into network connections and interface statistics. It allows administrators to monitor active connections, identify potential security risks, and detect suspicious or unauthorized activities. Regularly utilizing netstat as part of endpoint monitoring can help identify and mitigate security threats promptly.
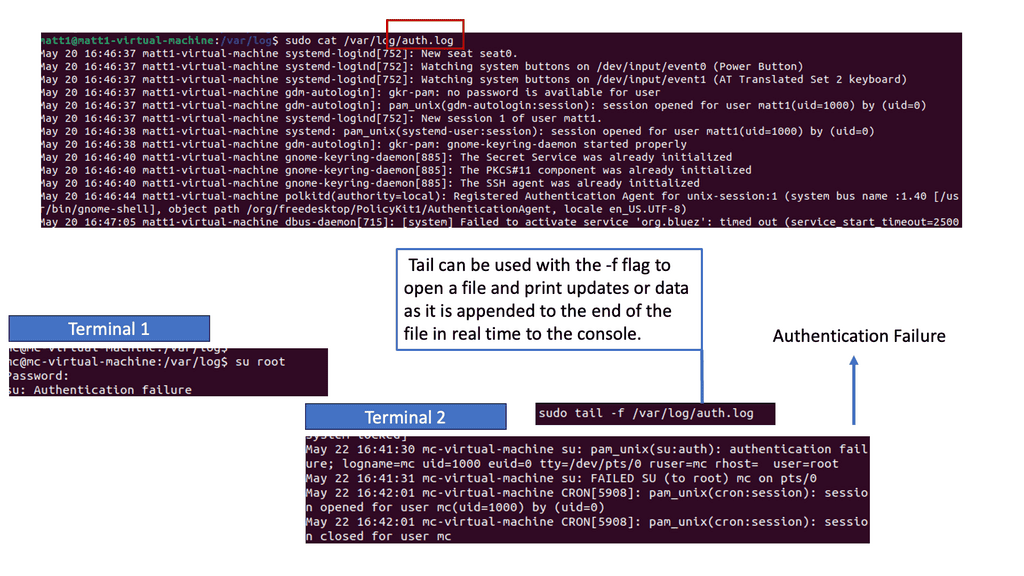
Example: Detecting Authentication Failures in Logs
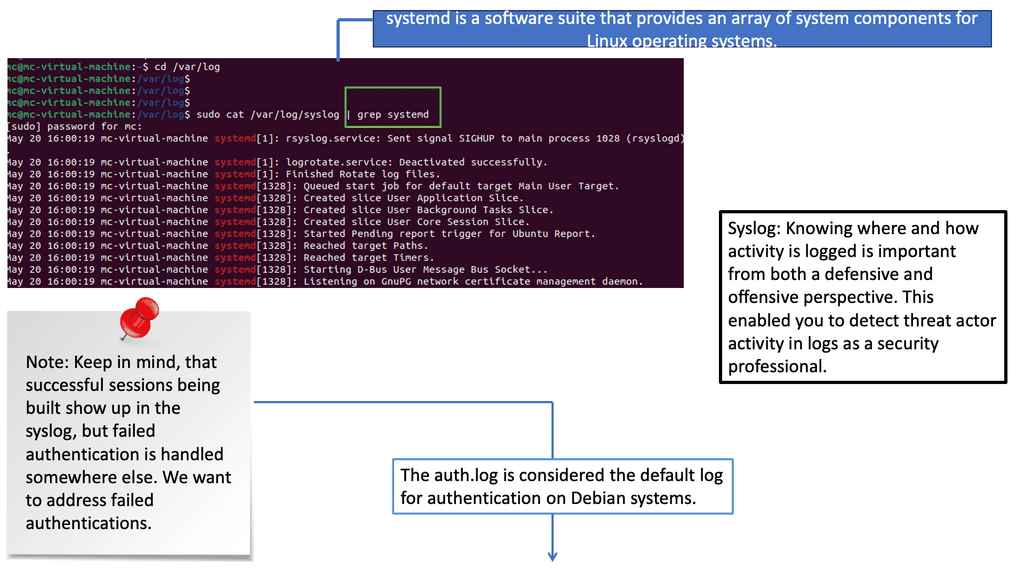
Understanding Syslog
Syslog is a centralized logging system that collects and stores messages from various devices and applications. It provides a standardized format for log messages, making them easier to analyze and interpret. By examining syslog entries, security analysts can uncover valuable insights about events occurring within a system.
Auth.log, on the other hand, focuses specifically on authentication-related events. It records login attempts, password changes, and other authentication activities. This log file is a goldmine for detecting potential unauthorized access attempts and brute-force attacks. Analyzing auth.log entries enables security teams to respond to security incidents proactively, strengthening the overall system security.
Analysts employ various techniques to detect security events in logs effectively. One common approach is pattern matching, where predefined rules or regular expressions identify specific log entries associated with known security threats. Another technique involves anomaly detection, establishing a baseline of normal behavior and flagging any deviations as potential security incidents. By combining these techniques and leveraging advanced tools, security teams can improve their ability to promptly detect and respond to security events.
Starting Zero Trust Networks
Assessing your network infrastructure thoroughly is the foundation of a robust zero-trust strategy. By mapping out all network elements, including devices, software, and data flows, you can identify security gaps and opportunities for enhancement. Identifying vulnerabilities and determining where and how zero trust principles can be applied effectively requires a comprehensive view of your network’s current state. Any security measures must be aligned with your organization’s specific needs and vulnerabilities to be effective. A clear blueprint of your existing infrastructure will be used to integrate zero trust into your existing network seamlessly.
Implementing a Zero Trust Network requires a combination of advanced technologies, robust policies, and a change in mindset. Organizations must adopt multi-factor authentication, encryption, network segmentation, identity and access management (IAM) tools, and security analytics platforms. Additionally, thorough employee training and awareness programs are vital to ensure everyone understands the importance of the zero-trust approach.
Example Technology: Network Monitoring
Understanding Network Monitoring
Network monitoring refers to continuously observing network components, devices, and traffic to identify and address anomalies or potential issues. By monitoring various parameters such as bandwidth utilization, device health, latency, and security threats, organizations can gain valuable insights into their network infrastructure and take proactive actions.
Effective network monitoring brings numerous benefits to individuals and businesses alike. Firstly, it enables early detection of network issues, minimizing downtime and ensuring uninterrupted operations. Secondly, it aids in capacity planning, allowing organizations to optimize resources and avoid bottlenecks. Additionally, network monitoring is vital in identifying and mitigating security threats and safeguarding sensitive data from potential breaches.
Example Technology: Network Scanning
Understanding Network Scanning
Network scanning is a proactive method for identifying vulnerabilities and security weaknesses within a network infrastructure. By systematically examining a network, organizations can gain valuable insights into potential threats and take preemptive measures to mitigate risks.
Security professionals employ various network scanning techniques. Some common ones include port scanning, vulnerability scanning, and wireless network scanning. Each method serves a specific purpose, allowing organizations to assess different aspects of their network security.
Network scanning offers several key benefits to organizations. First, it provides an accurate inventory of network device configurations, aiding network management. Second, it helps identify unauthorized devices or rogue access points that may compromise network security. Third, regular network scanning allows organizations to detect and patch vulnerabilities before malicious actors can exploit them.
Organizations should adhere to certain best practices to maximize the effectiveness of network scanning. These include conducting regular scans, updating scanning tools, and promptly analyzing scan results. It is also crucial to prioritize and promptly address vulnerabilities based on severity.
Scope the Zero Trust Network design
Before a zero-trust network can be built, it must be appropriately scoped. In a very mature zero-trust network, many systems will interact with each other. The complexity and number of systems may make building these systems difficult for smaller organizations.
The goal of a zero trust architecture is to achieve it rather than require it to meet all requirements from the beginning. A perimeter-based network is no different from this. Networks with less maturity may begin with a simple design to reduce administration complexity. As systems mature and breaches become more likely, networks must be redesigned to isolate them further.
Although a zero-trust network design is ideal, not all features are equally valuable. Identifying the necessary and excellent components is essential to ensuring the success of a zero-trust implementation.
Example: Identifying and Mapping Networks
To troubleshoot the network effectively, you can use a range of tools. Some are built into the operating system, while others must be downloaded and run. Depending on your experience, you may choose a top-down or a bottom-up approach.
Everything is Untrusted
Stop malicious traffic before it even gets on the IP network. In this world of mobile users, billions of connected things, and public cloud applications everywhere – not to mention the growing sophistication of hackers and malware – the Zero Trust Network Design and Zero Trust Security Strategy movement is a new reality. As the name suggests, Zero Trust Network ZTN means no trusted perimeter.
Single Packet Authorization
Everything is untrusted; even after authentication and authorization, a device or user only receives the least privileged access. This is necessary to prevent all potential security breaches. Identity and access management (IAM) is the foundation of excellent IT security and the key to providing zero trust, along with crucial zero-trust technologies such as zero-trust remote access and single-packet authorization.
Before you proceed, you may find the following posts helpful:
Zero Trust Network ZTN
A zero-trust network is built upon five essential declarations:
- The network is always assumed to be hostile.
- External and internal threats exist on the network at all times
- Network locality alone is not sufficient for deciding trust in a network.
- Every device, user, and network flow is authenticated and authorized.
- Policies must be dynamic and calculated from as many data sources as possible.
Zero Trust Remote Access
Zero Trust Networking (ZTN) applies zero-trust principles to enterprise and government agency IP networks. Among other things, ZTN integrates IAM into IP routing and prohibits the establishment of a single TCP/UDP session without prior authentication and authorization. Once a session is established, ZTN ensures all traffic in motion is encrypted. In the context of a common analogy, think of our road systems as a network and the cars and trucks on it as IP packets.
Today, anyone can leave his or her house and drive to your home and come up your driveway. That driver may not have a key to enter your home, but he or she can cause it and wait for an opportunity to join. In a Zero Trust world, no one can leave their house to travel over the roads to their home without prior authentication and authorization. This is required in the digital, virtual world to ensure security.
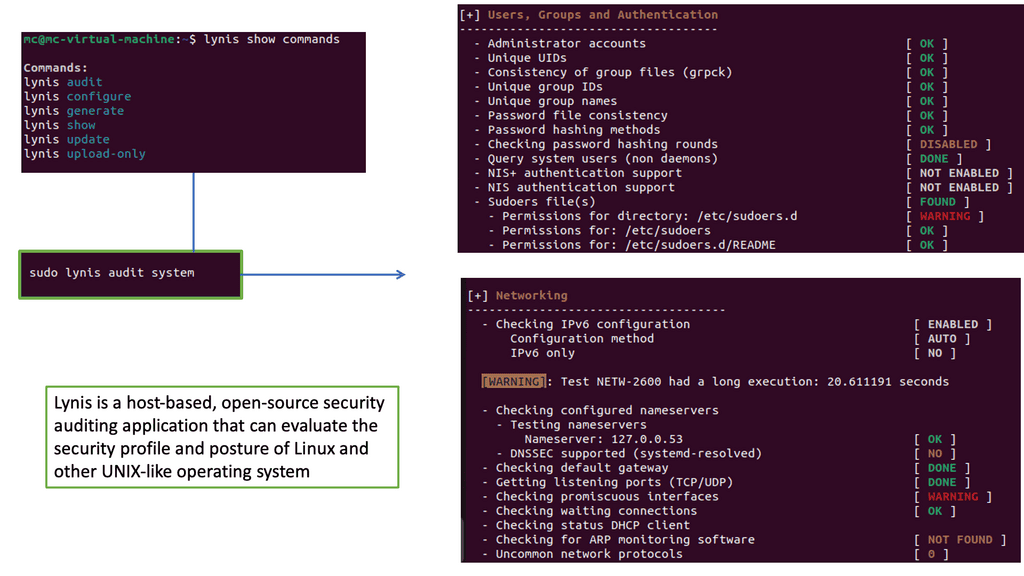
Example: What is Lynis?
Lynis is an open-source security auditing tool designed to evaluate the security configurations of UNIX-like systems, including Linux and macOS. Developed by CISOfy, Lynis is renowned for its simplicity, flexibility, and effectiveness. By performing various tests and checks, Lynis provides valuable insights into potential vulnerabilities and suggests remediation steps.
**The challenges of the NAC**
In the voice world, we use signaling to establish authentication and authorization before connecting the call. In the data world, this can be done with TCP/UDP sessions and, in many cases, in conjunction with Transport Layer Security, or TLS. The problem is that IP routing hasn’t evolved since the mid-‘90s.
IP routing protocols such as Border Gateway Protocol are standalone; they don’t integrate with directories. Network admission control (NAC) is an earlier attempt to add IAM to networking, but it requires a client and assumes a trusted perimeter. NAC is IP address-based, not TCP/UDP session state-based.
Zero trust remote access: Move up the stack
The solution is to make IP routing more intelligent and bring up the OSI stack to Layer 5, where security and session state reside. The next generation of software-defined networks is taking a more thoughtful approach to networking with Layer 5 security and performance functions.
Over time, organizations have added firewalls, session border controllers, WAN optimizers, and load balancers to networks because they can manage session state and provide the intelligent performance and security controls required in today’s networks.
For instance, firewalls stop malicious traffic in the middle of a network and do nothing within a Layer 2 broadcast domain. Every organization has directory services based on IAM that define who is allowed access to what. Zero Trust Networking takes this further by embedding this information into the network and enabling malicious traffic to be stopped at the source.
**ZTN Anomaly Detection**
Another great feature of ZTN is anomaly detection. An alert can be generated when a device starts trying to communicate with other devices, services, or applications to which it doesn’t have permission. Hackers use a process of discovery, identification, and targeting to break into systems; with Zero Trust, you can prevent them from starting the initial discovery.
In an era where cyber threats continue to evolve, traditional security models are no longer sufficient to protect sensitive data. Zero Trust Networking offers a paradigm shift in cybersecurity, shifting the focus from trust to verification. Organizations can strengthen their defenses and mitigate the risk of data breaches by adopting the principles of least privilege, micro-segmentation, and continuous authentication. Embracing Zero Trust Networking is a proactive step towards ensuring the security and integrity of critical assets in today’s digital landscape.
Summary: Zero Trust Network ZTN
In today’s rapidly evolving digital landscape, the need for robust cybersecurity measures has never been more critical. One concept that has gained significant attention is the Zero Trust Network (ZTN). In this blog post, we delved into the world of ZTN, its fundamental principles, and how it revolutionizes security protocols.
Understanding Zero Trust Network (ZTN)
Zero Trust Network is a security framework that challenges the traditional perimeter-based security model. It operates on the principle of “never trust, always verify.” Every user, device, or network component is treated as potentially malicious until proven otherwise. By adopting a ZTN approach, organizations can significantly reduce the risk of unauthorized access and data breaches.
Key Components of ZTN
To implement ZTN effectively, several critical components come into play. These include:
1. Micro-segmentation: This technique divides the network into smaller, isolated segments, limiting lateral movement and minimizing the impact of potential security breaches.
2. Multi-factor Authentication (MFA): Implementing MFA ensures that users provide multiple pieces of evidence to verify their identities, making it harder for attackers to gain unauthorized access.
3. Continuous Monitoring: ZTN relies on real-time monitoring and analysis of network traffic, user behavior, and device health. This enables prompt detection and response to any anomalies or potential threats.
Benefits of ZTN Adoption
By embracing ZTN, organizations can reap numerous benefits, such as:
1. Enhanced Security: ZTN’s strict access controls and continuous monitoring significantly reduce the risk of successful cyberattacks, protecting critical assets and sensitive data.
2. Improved Agility: ZTN enables organizations to embrace cloud-based services, remote work, and BYOD policies without compromising security. It provides granular control over access privileges, ensuring only authorized users can access specific resources.
3. Simplified Compliance: ZTN aligns with various regulatory frameworks and industry standards, helping organizations meet compliance requirements more effectively.
Conclusion:
In conclusion, the Zero Trust Network (ZTN) is a game-changer in cybersecurity. By adopting a ZTN approach, organizations can fortify their defenses against the ever-evolving threat landscape. With its focus on continuous monitoring, strict access controls, and micro-segmentation, ZTN offers enhanced security, improved agility, and simplified compliance. As organizations strive to protect their digital assets, ZTN is a powerful solution in the fight against cyber threats.
- DMVPN - May 20, 2023
- Computer Networking: Building a Strong Foundation for Success - April 7, 2023
- eBOOK – SASE Capabilities - April 6, 2023










[…] the topic at the network level, I couldn’t resist giving him a call to discuss the generals on Zero Trust Networking (ZTN). During the conversation, he shone a light on numerous known and unknown facts about Zero […]
[…] the topic at the network level, I couldn’t resist giving him a call to discuss the generals on Zero Trust Networking (ZTN). During the conversation, he shone a light on numerous known and unknown facts about Zero […]
[…] the topic at the network level, I couldn’t resist giving him a call to discuss the generals on Zero Trust Networking (ZTN). During the conversation, he shone a light on numerous known and unknown facts about Zero […]
[…] the topic at the network level, I couldn’t resist giving him a call to discuss the generals on Zero Trust Networking (ZTN). During the conversation, he shone a light on numerous known and unknown facts about Zero […]
[…] the topic at the network level, I couldn’t resist giving him a call to discuss the generals on Zero Trust Networking (ZTN). During the conversation, he shone a light on numerous known and unknown facts about Zero […]
[…] zero-trust approach is becoming more popular across security and network architectures. Objectively, […]