UDP Scan
In the realm of network security, understanding different scanning techniques is crucial. One such technique is UDP (User Datagram Protocol) scanning. While TCP (Transmission Control Protocol) scanning is more widely known, UDP scanning serves its unique purpose. In this blog post, we will delve into the fundamentals of UDP scanning, explore its significance, and understand how it differs from TCP scanning.
UDP scanning involves sending UDP packets to specific ports on a target system to identify open, closed, or filtered ports. Unlike TCP, UDP is a connectionless protocol, which makes scanning UDP ports trickier. UDP scans are typically used to discover services running on a target system, especially those that may not respond to traditional TCP scans.
UDP (User Datagram Protocol) scan is a network scanning technique used to identify open UDP ports on a target system. Unlike TCP, which establishes a connection before data transmission, UDP is connectionless, making it a popular choice for certain applications. UDP scan operates by sending UDP packets to various ports on a target system and analyzing the responses received.
UDP scan finds its utility in various scenarios. One prominent use case is the identification of open ports on a target network. By discovering open UDP ports, network administrators can gain insights into potential vulnerabilities and take appropriate mitigation measures. Additionally, UDP scan can be employed for monitoring and troubleshooting network devices, especially those that rely heavily on UDP-based protocols.
While UDP scan can be a powerful tool, it also comes with certain vulnerabilities and limitations. One significant limitation is the lack of reliable response verification. Unlike TCP, which sends acknowledgments for successful packet delivery, UDP does not provide such mechanisms. This makes UDP scan prone to false positives and inconclusive results. Moreover, some firewalls and intrusion detection systems may block or limit UDP traffic, hindering the effectiveness of UDP scan.
To mitigate the risks associated with UDP scan, network administrators can implement several strategies. First and foremost, maintaining up-to-date firewall rules and configurations is crucial. This includes selectively allowing or blocking UDP traffic based on specific requirements. Additionally, implementing network segmentation can limit the attack surface and minimize the impact of potential UDP scan attempts. Regular vulnerability assessments and patch management also play a vital role in mitigating vulnerabilities that could be exploited through UDP scan.
Matt Conran
Highlights: UDP Scan
Understanding UDP Scan
Security professionals and enthusiasts employ UDP (User Datagram Protocol) scans to probe target systems for open UDP ports. Unlike TCP, UDP is connectionless, making the scanning process more challenging. By sending UDP packets to various ports, the scanner aims to detect potential services or applications that respond, revealing the presence of open ports.
**How UDP Scanning Works**
UDP scanning involves sending a series of UDP packets to various ports on a target machine and analyzing the responses. Unlike TCP scanning, which relies on a three-way handshake to establish a connection, UDP scanning requires an understanding of how different systems respond to unsolicited packets.
When a UDP packet is sent to a closed port, the target typically responds with an ICMP “port unreachable” message. If no response is received, it may indicate that the port is open or that the packet was dropped by a firewall. However, this ambiguity makes UDP scanning more challenging and time-consuming compared to TCP scanning.
**Challenges and Limitations of UDP Scanning**
While UDP scanning is an essential technique, it is not without its challenges. One major limitation is the lack of standardization in how systems respond to UDP packets, leading to potential false positives or false negatives. Firewalls and intrusion detection systems can further complicate the process by blocking or dropping UDP packets, making it difficult to obtain accurate results.
Moreover, the stateless nature of UDP means that there is no reliable way to confirm whether a port is open or closed, as the absence of a response could mean either scenario. Despite these challenges, understanding the nuances of UDP scanning is crucial for effective network security assessments.
– Advantages and Disadvantages of UDP Scan: While UDP scanning offers unique benefits, such as speed and minimal footprint, it also presents certain limitations. One of the advantages lies in UDP’s connectionless nature, which allows for faster scanning compared to TCP. Additionally, UDP scans can uncover vulnerabilities that might be missed by TCP scanning alone. However, UDP scanning can be more prone to false positives and false negatives due to the lack of confirmation of successful packet delivery.
– Use Cases and Applications: UDP scanning finds applications in various scenarios, including network security assessments, penetration testing, and troubleshooting. Security professionals leverage UDP scanning to identify potential vulnerabilities in network devices such as firewalls, routers, and IoT devices. Additionally, UDP scan assists in identifying services running on non-standard ports, uncovering hidden services that might pose security risks.
– Tips and Best Practices: To ensure effective UDP scanning, it is crucial to follow certain best practices. First, prioritize target selection and focus on critical systems that could have UDP vulnerabilities. Second, employ reliable scanning tools that provide accurate results and allow customization of scan parameters. Finally, analyze the scan results carefully, considering false positives and false negatives, to make informed decisions regarding network security measures.
Core Activity: Understanding Networking
Network-based security testing requires an understanding of how protocol stacks are defined. Using the Open Systems Interconnection (OSI) model, one can define protocols and, more specifically, their interactions. Through the OSI model, we can break down communications into different functional elements and identify where other information is added to network packets. Furthermore, you can see how systems interact across functional elements.
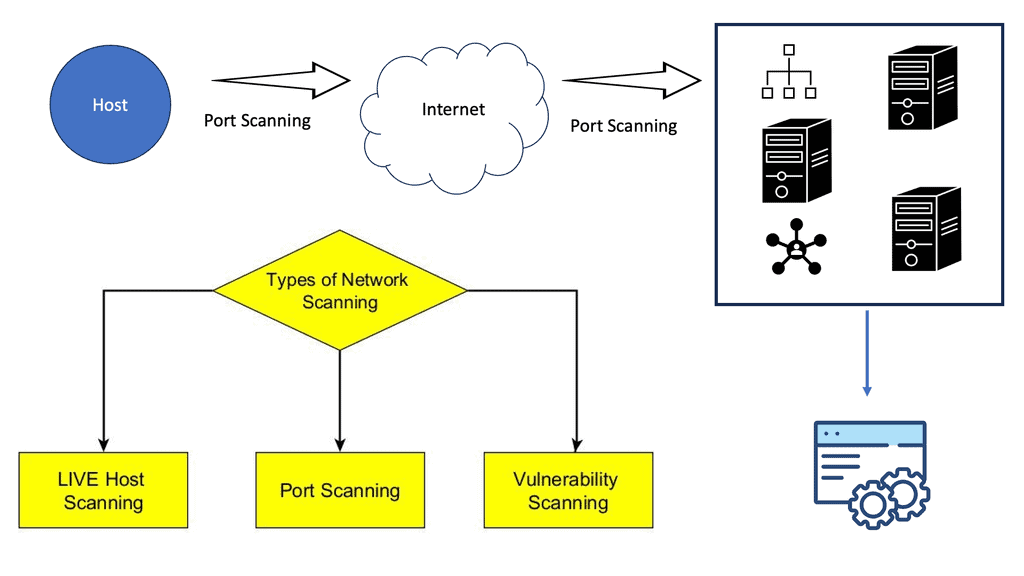
Identifying vulnerabilities and assessing your attack surface requires scanning your network for open ports and services. Network Mapper (Network Mapper) identifies hosts, open TCP and UDP ports, services running on those ports, and the operating system on your network.
Port scanning – what is it?
As a network grows and more devices connect, an administrator may find keeping track of devices and services helpful. NMAP can scan a network for open ports and services connected to the environment. Network audits are primarily conducted using NMAP port scans but can also be used to find exploitable vulnerabilities.
NMAP displays open ports on the targeted system after scanning the host with the command.
NMAP stands for Network Mapper. What is it?
NMAP has a graphical user interface (GUI) and a command-line interface. The tool also scans open ports on computers on the network. NMAP can also check other devices, including computers. It scans all networked devices, desktops, mobile devices, routers, and IoT devices.
NMAP is available for free on the developer’s website. Windows, Mac, and Linux are supported. Identifying vulnerable devices on a network is one of the utility’s most important functions, and it has been a part of many network administrators’ and hackers’ tools for years.
**Stress Testing**
Stress testing aims to generate vast amounts of traffic and send it to a device or application. A device or application may be stressed if unexpected data is sent. There are certain expectations about the type and structure of data that applications will receive, even when they run on limited-use devices (such as thermostats, locks, and light switches). A failure to send what was expected may fail in an application. Knowing this is useful. Stress testing the logic of an application is another type of stress testing.
**SIP and UDP Testing**
SIP can use TCP or User Datagram Protocol (UDP) as a transport protocol, although earlier versions preferred UDP. Thus, older tools, particularly older ones, tend to use UDP. TCP is supported by modern implementations and Transport Layer Security (TLS) to prevent headers from being read.
The SIP protocol is based on HTTP, so all the headers and other information are text-based, unlike H.323, another binary VoIP protocol that cannot be read visually without a protocol decoder. Switching from UDP to TCP when using the tool invite flood is impossible. Although there is no time wasted waiting for the connection to be established, this does allow the flood to happen faster.
Conducting a UDP Scan
When conducting a UDP scan, the scanner sends UDP packets to a range of ports on the target system. If a UDP port is open, the target system responds with an ICMP (Internet Control Message Protocol) port unreachable message.
If a UDP port is closed, the target system may respond with an ICMP message indicating it is closed or ignore the packet. In some cases, if a firewall filters a UDP port, the target system may not respond, making it harder to determine the port’s status.
Significance of UDP Scan
UDP scanning plays a crucial role in network security and vulnerability assessment. It helps identify potential vulnerabilities and misconfigurations in network devices and services. By discovering open UDP ports, network administrators can assess the risks associated with those services and take appropriate measures to secure them.
Additionally, UDP scanning enables the detection of UDP-based services that may not be visible through traditional TCP scans.
Best Practices for UDP Scanning:
1. Be mindful of the network bandwidth: UDP scans can generate significant traffic. It is essential to consider the network capacity and prioritize critical systems to avoid overwhelming the network.
2. Use appropriate scanning tools: Various network scanning tools, such as Nmap or Nessus, offer UDP scanning capabilities. Choose a tool that aligns with your specific requirements and provides accurate results.
3. Understand the limitations: Due to UDP’s connectionless nature, scanning accuracy might be compromised. Some ports may be filtered or unresponsive, leading to inconclusive results. It is crucial to analyze the results holistically and consider other factors.
Related: Before you proceed, you may find the following posts helpful:
UDP Scan
Network Scanning
UDP scanning is network scanning that discovers services running on a computer or network. It also detects any open ports on a system that may be used for malicious activities.
System administrators and security professionals commonly use UDP scanning to identify potential weaknesses in their network security.UDP scanning involves sending a packet to a specific port on the target host.
If the port is open, the host will respond with an acknowledgment packet. If the port is closed, the host will not respond. By sending multiple UDP packets to various ports, it is possible to determine which services are running on the target host.
UDP scanning can quickly identify potential targets for malicious activities and vulnerable services that attackers may exploit. It is often used with other network scanning techniques, such as port and vulnerability scanning.
UDP scanning is an essential tool for network security professionals. It provides valuable information about a system’s open ports, allowing system administrators to secure their networks better and help prevent malicious activities.
Guide: Network Scanning with NMAP
Nmap (Network Mapper) is an open-source and versatile network scanning tool that enables users to discover hosts and services on a computer network.
It operates by sending packets and analyzing the responses received from target devices. Nmap scanning provides valuable insights into network topology, open ports, operating systems, and potential vulnerabilities. The following will teach you the foundational knowledge of NMAP to scan a network to see which hosts and ports are online on each host you know about.
Note:
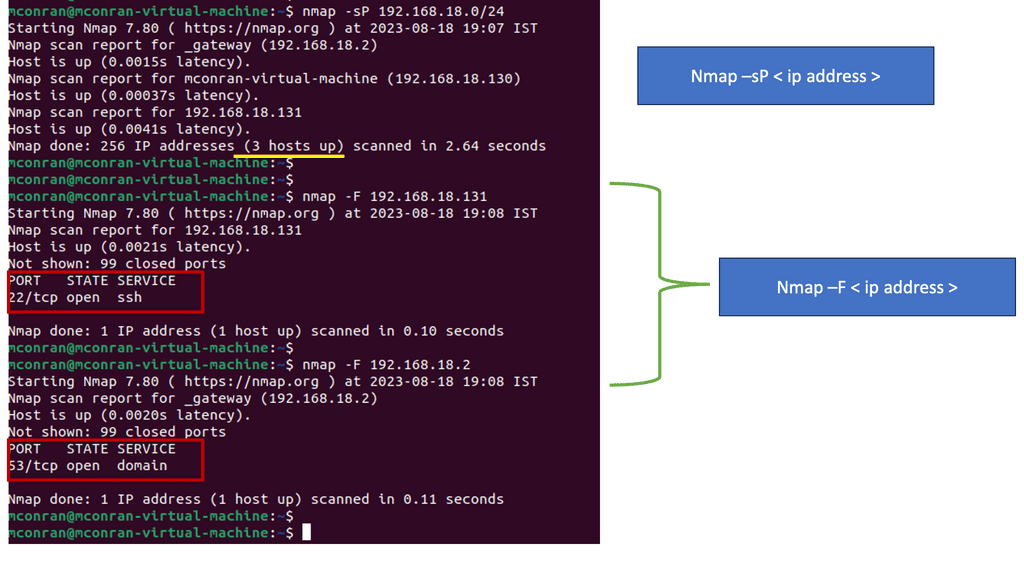
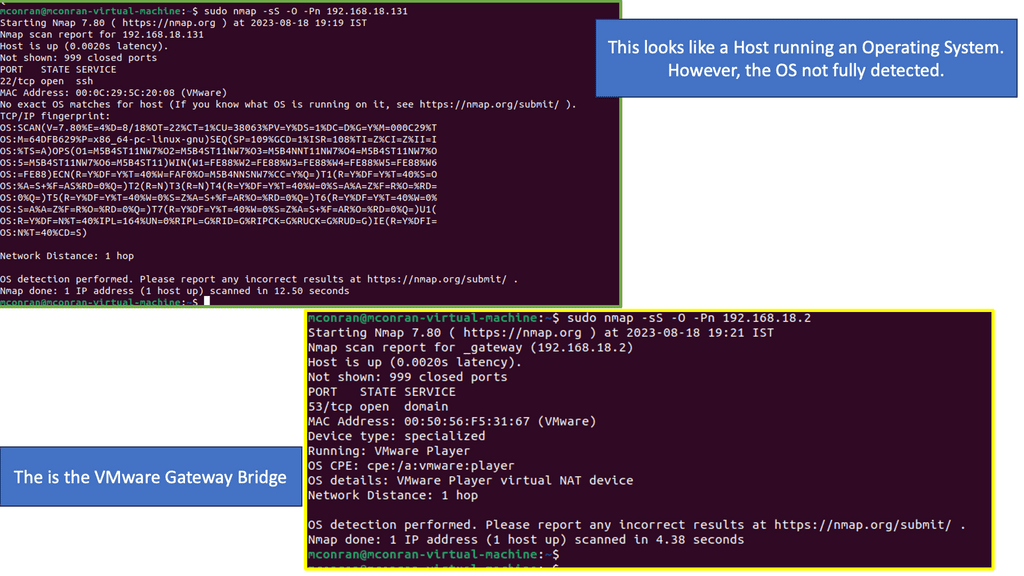
- You will use NMAP to scan the 192.168.18.0/24 network. For this first test, we want to see which hosts respond and not care what ports they have open. I have a small network that is isolated using VMware.
- Use the “Ping Scan” option in this example, either—sn or—sP. I am using the—sP option in the example below. I also used the -F option. The -F argument will tell NMAP to scan the host only for the 100 most common open ports.
Analysis:
- There are three hosts online: 192.168.18.2, 192.168.18.130, and 192.168.18.131.
- You will also see how long it took for this NMAP scan to complete and how many IP addresses were scanned.
- The example shows that 256 IP addresses were scanned on the screen, which took 2.64 seconds.
- We can also see the open ports. On 192.168.18.131, port 22 for SSH is open; on 192.168.18.2, port 53 is open.
Note: When performing NMAP scans on a network, intrusion detection systems (IDS) and intrusion prevention systems (IPS) can easily detect the scans. There are ways to avoid this, such as completing a Stealth Scan and limiting the speed at which the scans are performed. We will look at Stealth Scans in the following lab guide.
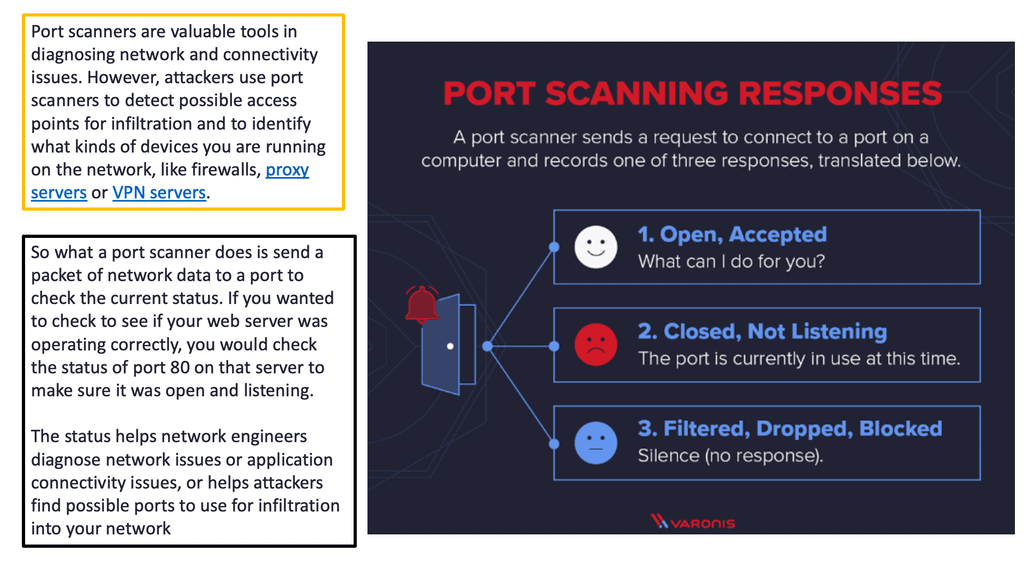
Port Scanning
Port scanning is a method computer networks use to identify open ports on a system and check for vulnerabilities. It is commonly used to detect security weaknesses in networks and systems by probing for open ports and services that may be vulnerable to attack. Port scanning is done by either manually entering commands or using specialized software.
Port scans are used as a reconnaissance step to identify open ports on a system and assess the target’s security posture. A port scan will typically look for open ports on a target system and then attempt to identify the service running on that port. This helps to identify possible vulnerabilities in the design and determine what kind of attack may be possible.
Port scanning is essential for network security, as it can help to identify any potential weaknesses in a system that an attacker could exploit. However, it is also necessary to ensure that all ports and services are adequately secured, as an open port can be an easy target for an attacker.
**Port scanning with NMAP**
NMAP can be used to perform host discovery. Once you’ve identified confirmed hosts within your network, you can continue by performing port scanning, which will help you identify risk areas. Additionally, you can perform TCP and UDP port scans. This post focuses on the UDP scan with the process of UDP scanning. Remember that the information that should be exposed to the outside world is down to security policy.
Any IP scanning starts with an ICMP. This is the first step; you can block all incoming ICMPs at the perimeter network. This will make Ping ineffective and filter ICMP unreachable messages to block Traceroute. Consider this to be the first line of defense. But does this solve all of the problems? No, port scan works on TCP/UDP ports as well.
**Connectionless vs Connection Orientated**
Connectionless protocols ( UDP ) spread the state required to carry the data through every possible device. In contrast, connection-oriented protocols ( TCP ) constrain the state to only those involved in two-way communication. These differences affect network convergence and how applications react to network failure.
Connectionless moves the data onto another path, while connections-orientated must build up the state again. The packet header below shows that UDP is a lightweight protocol with few options to set. On the other hand, TCP has many options and flags that can influence communication.
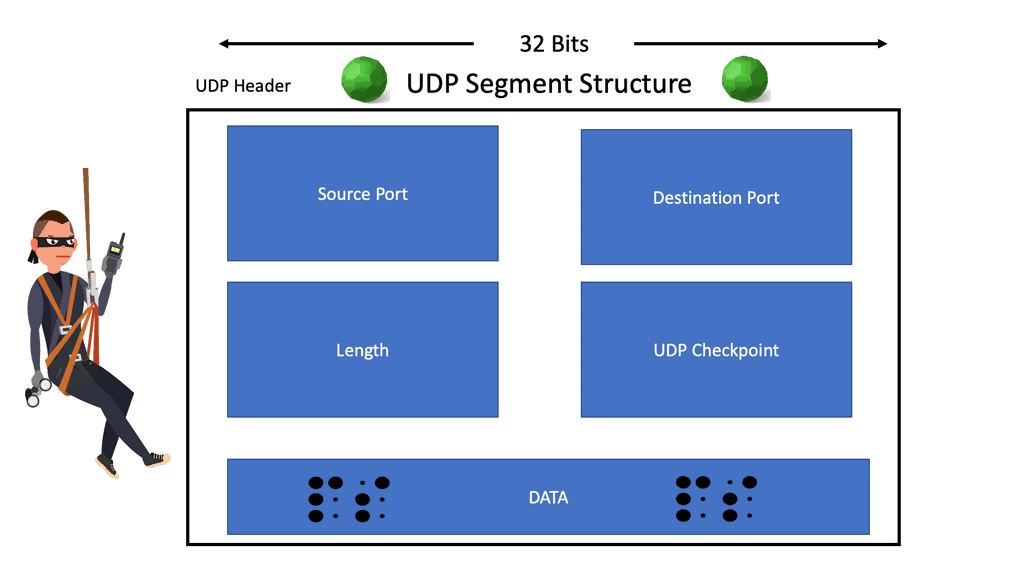
UDP header
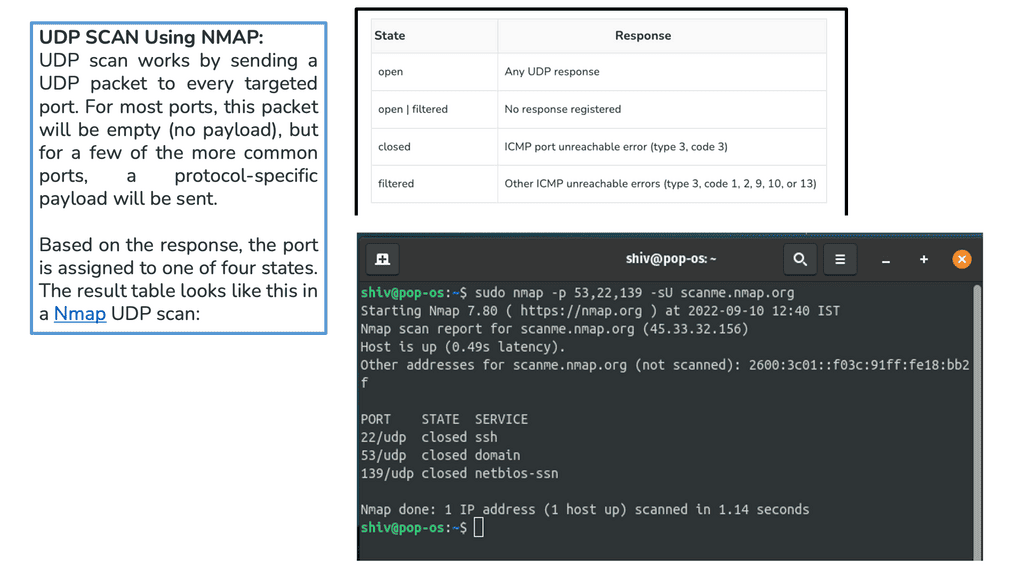
UDP (User Datagram Protocol) is a communications protocol for sending data over an IP network. It is an alternative to the more commonly used Transmission Control Protocol (TCP). Unlike TCP, UDP does not provide reliable data delivery, meaning that there is a chance that packets of data sent over UDP may be dropped or lost. However, UDP is faster than TCP and is more suitable for applications that require speed.
The following diagram shows the UDP Header. UDP uses headers when packaging message data to transmit. UDP headers include a set of parameters. These parameters are called fields defined by the protocol’s technical specifications. The UDP header has four fields, each of which is 2 bytes. The UDP header’s four fields are listed as follows:
- The source port number is the sender’s source port.
- The destination port number is the port to which the datagram is addressed and destined.
- Length, the length in bytes of the UDP header.
- A checksum is used for error checking.
In summary, the UDP header is 8 bytes long and consists of four fields: source port, destination port, length, and checksum. The source port is a 16-bit field that identifies the source application used for the communication.
The destination port is a 16-bit field that identifies the application used for the transmission. The length field specifies the length of the UDP header and data. The checksum is a 16-bit field used to verify the integrity of the header and data.
UDP handshake
A UDP handshake is a method computers use to connect to the User Datagram Protocol (UDP). It is an essential part of setting up a network connection and allows two devices to communicate.
The UDP handshake starts with the sending device sending a request to the receiving device. This request is usually an IP address and a port number. The receiving device then sends a confirmation packet, indicating it is ready to receive data.
Once this packet is received, the sending device can send data to the receiving device. The UDP handshake is often used for streaming audio and video, as it is a fast way of establishing a connection between two devices. In addition, it does not require the same security level as a TCP connection, so it is often preferred for streaming applications.
Once the UDP handshake is complete, the two devices are connected and can begin exchanging data. The connection remains active until one of the devices closes it. This is done either by sending a particular packet or by the connection timing out. A UDP handshake is a fast and reliable way to connect two devices.
- No three-way UDP handshake:
UDP has a source and destination port but does not mandate that the source and destination establish a three-way UDP handshake before transmission occurs. Further, there is no requirement for an end-to-end connection. This is in comparison to TCP.
TCP establishes a connection between a sender and receiver before sending data. The UDP handshake does not establish a connection before sending data. So, in a TCP-based connection, a three-way handshake is used to create a connection. TCP uses handshake protocols like SYN, SYN-ACK, and ACK, while in the case of UDP, we have no UDP handshake protocols.
- Differences from TCP Scan:
Unlike TCP scanning, which establishes a connection with the target system, UDP scanning works without a handshake process. This makes UDP scanning faster but less reliable. Furthermore, due to the nature of unsolicited packets being sent, UDP scans are more likely to trigger intrusion detection systems (IDS) or firewalls. It is essential to configure these security systems accordingly to avoid false alarms.
Capabilities: | TCP | UDP |
|
|
|
Transmission Control Protocol | User Datagram Protocl |
Getting Started with UDP Scanning
Consider how these protocols work and respond to scans when enabled at your perimeter. How these protocols interact with the network affects how they are viewed and scanned by the outside world. For example, UDP sends a packet to the receiver with no mechanism for ensuring packet delivery and does not require a response from the target machine.
This type of communication is often referenced as dropping a letter into a mailbox and not knowing if the receiver has opened it. So, how does the design of these protocols affect the type of scans and results they offer?
50% UDP Scanning Checklist
|
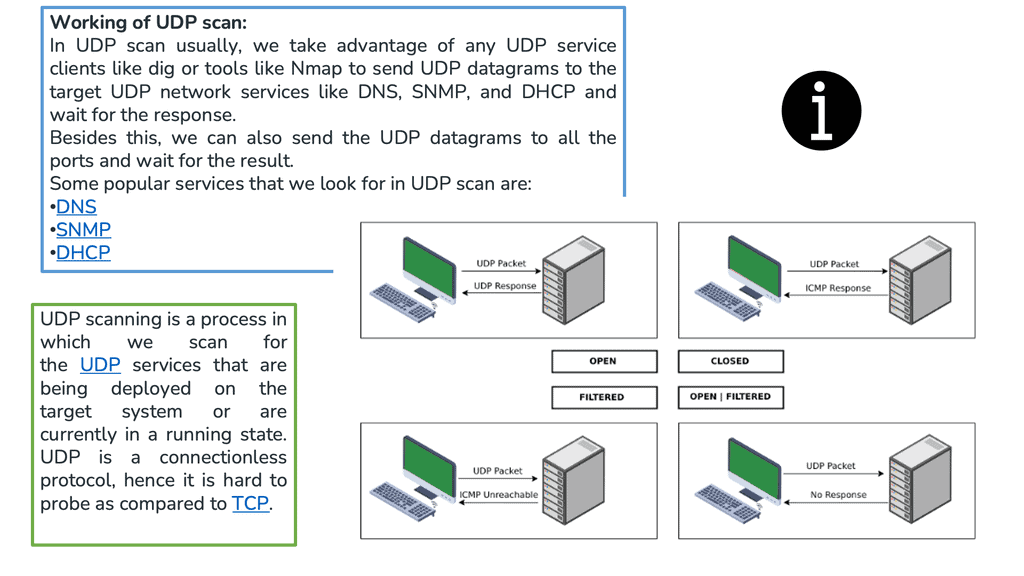
What Is a UDP Scan?
A classic problem with UDP fingerprinting is that you will unlikely get a response from the receiver. If the service is available and accepting UDP packets, the expected behavior for this service is to accept the packet but not send back a response to the sender. Likewise, a common firewall strategy is to absorb the packet and not send a reply to the sender—the “if you can’t see me, you can’t attack me” approach.
This is common with UDP scans, which tend to result in false positives. As a result of this behavior, most UDP scans provide very little information and mark nearly every port as “open|filtered.” Generally, a port is considered “open” if the scanning host does not receive an unreachable message from an Internet Control Message Protocol ( ICMP ) port.
NMAP UDP Scan
To elicit more of a response, you can optimize NMAP ( Network Mapper ) to include the “-sV” switch. This switch will send specially crafted packets to the ports listed as “open|filtered.” This can hopefully help us narrow down the results and generate ports that become “open|open.”
Now, the NMAP UDP scan can help inventory UDP ports. So, it is activated with the—sU option. Consider combining the NMAP UDP scan with an SYN or TCP scan type. This can be carried out with the—sS option. It allows you to check both protocols during the same scan run.
Alternatively, you could go above Layer 4. For example, if you are doing an SNMP scanning, you would send an “SNMP ping” instead of looking for open UDP ports. An SNMP ping is not like an ICMP ping. Instead, it operates above Layer 4 and requests the OID/object name universally present on all SNMP agents.
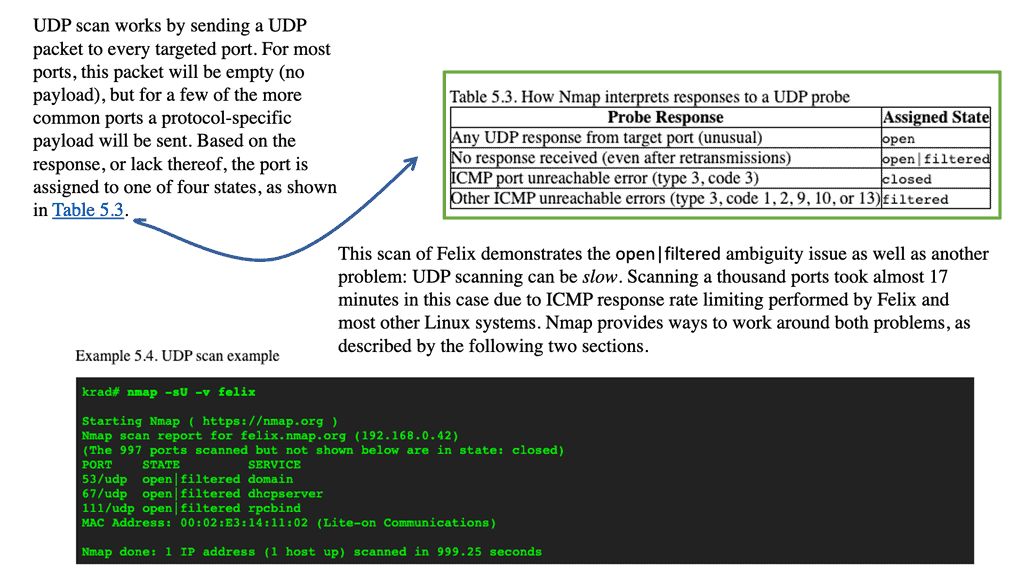
**UDP scans are slow**
Another problem with UDP scans is that they are slow. UDP does not provide error checking; sometimes, the UDP CRC32 checksum is not supported by the IP stack being used. As a result, the scanning host usually sends three successive UDP packets and waits for at least one ICMP port unreachable message ( if the receiving host decides to generate a response ).
The only way to do this is to offset your stealth and generate multiple UDP scans in parallel. In contrast, TCP is a connection-oriented protocol that creates the communication session using a three-way handshake.
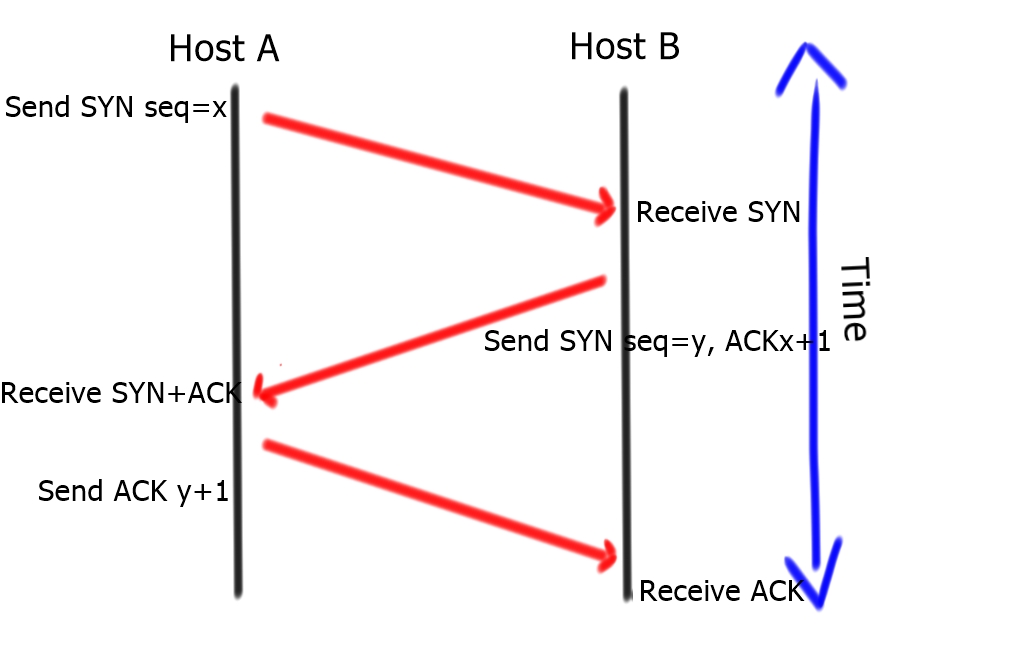
Its design allows it to undergo several different scans, which offer better results than a UDP scan. The most basic and stable type of scan is a TCP Connect scan. The scanning host attempts to complete the three-way handshake and gracefully tears down the session.
This type of scan is not a “Stealth” scan; most applications will log the completion of a three-way handshake. Instead, you could go for a TCP SYN scan if you want a faster or stealthier scan. SYN scans are faster because they only complete the process’s first two steps rather than completing the entire three-way handshake.
If we consider comparing the TCP three-way handshake to the analogy of someone making a phone call, an SYN scan would be similar. However, once the receiver picks up, you say nothing and hang up. An SYN scan is the default NMAP scan.

NMAP and Stealth Scans
Note: When performing NMAP scans on a network, intrusion detection systems (IDS) and intrusion prevention systems (IPS) can easily detect you. There are ways to avoid this, such as completing a Stealth Scan and limiting the speed at which the scans are performed.
When performing a Stealth Scan, Nmap sends a SYN packet to the target host. If the target host responds with a SYN/ACK packet, the port is open and listening. At this point, Nmap sends an RST packet to terminate the connection without completing the handshake. This approach allows Nmap to gather information about open ports without establishing a full connection, making detecting the scan difficult for intrusion detection systems.
Note:
- The—sS argument performs a Stealth Scan. This is accomplished by not completing the TCP three-way handshake. The computer performing the NMAP scan sends the TCP SYN message, and when the host responds with the TCP SYN-ACK message, the computer doesn’t send the final TCP ACK message, completing the handshake.
- The -O argument tells NMAP to guess the host’s operating system. NMAP can detect the operating system by looking at the responses to various TCP/IP messages, such as TTL messages.
- The -Pn argument tells NMAP not to send an ICMP (or Ping) packet used for host discovery.
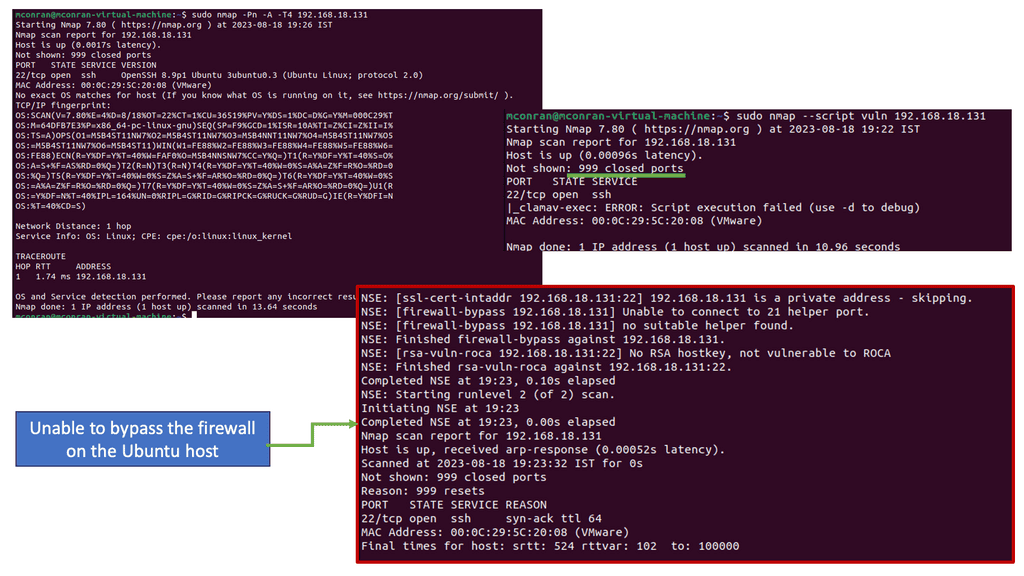
Note: NMAP has numerous scripts that can be run. You tell NMAP to run a script by adding the –script argument and then immediately specifying which script you want to run. In this command, you run the vuln script to check the host for 105 vulnerabilities.
I am on a lockdown Unbuntu host that is pretty secure by default. Also, I run a different Nmap scan and not a stealth scan. In production, this scan out be detected. However, at least now you can see that it has detected my Ubuntu OS as a version of Linux.
**Benefits of a Stealth Scan**
1. Reduced network footprint: The Stealth Scan minimizes the network footprint by avoiding unnecessary connections and reducing the chances of detection by IDS and intrusion prevention systems (IPS).
2. Faster scanning: Since the Stealth Scan only partially completes the TCP three-way handshake, it can scan many ports, making it an efficient scanning technique.
3. Evasion of firewall rules: The Stealth Scan can bypass specific firewall rules that only filter incoming connections but do not inspect outgoing SYN packets.
**Limitations and Considerations**
While the Stealth Scan is an effective scanning technique, it has its limitations and considerations:
1. Limited application with stateful firewalls: Stateful firewalls that track the status of network connections can detect and block Stealth Scans by recognizing the incomplete three-way handshake.
2. Inaccurate results with heavily filtered ports: Some hosts may be configured to drop incoming SYN packets instead of responding with an SYN/ACK packet. In such cases, the Stealth Scan may yield inaccurate results.
3. Detection by advanced IDS/IPS systems: Advanced intrusion detection and prevention systems may implement behavior analysis and anomaly detection techniques to identify and block Stealth Scans. Therefore, it’s important to remember the scan’s stealthiness when conducting security assessments.
The Use of XMAS scans
An XMAS scan is another helpful scan that sets specific flags in the TCP header. XMAS scans get their name due to the analogy of being “lit up like a Christmas tree.” The “lighting up” refers to the fact that the FIN, PSH, and URG packet flags are all set to “on,” and the packet is “lit up like a Christmas tree.”
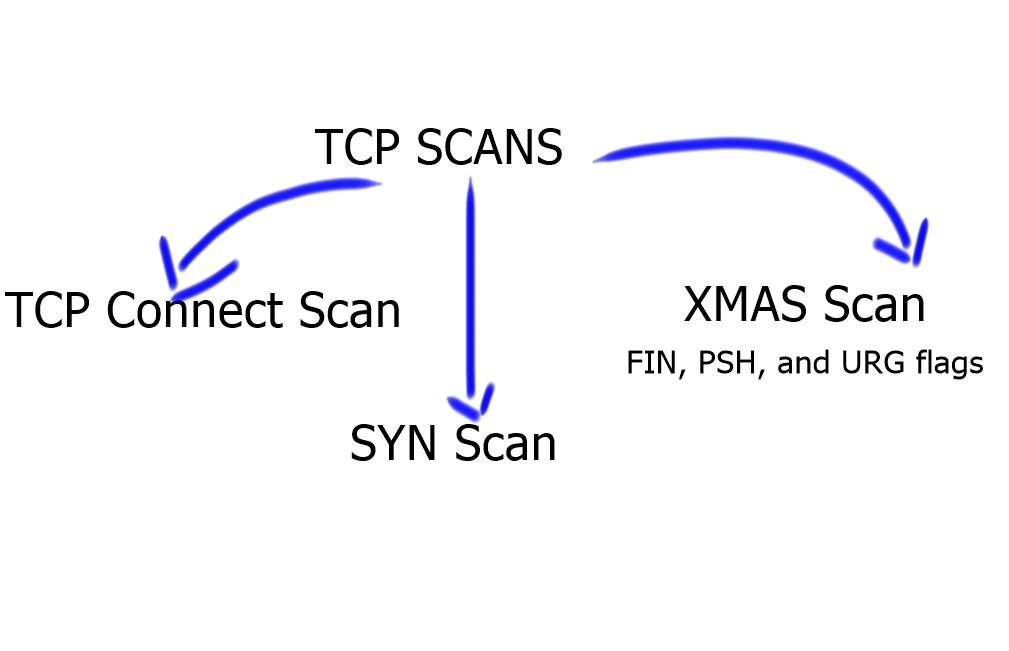
An XMAS-crafted packet is highly unusual because it doesn’t have an SYN, ACK, or RST flag set, violating traditional TCP communications. Why would you not set these flags? To elicit a response or no response from the receiver.
The RFC states that the packet should be ignored if an opened port receives a packet without an SYN, ACK, or RST flag set. As a result, NMAP can determine the port state without initiating or completing a connection to the target system, but only if the target host’s operating system fully complies with the TCP RFC.
XMASS scan creates packets without the SYN flag set
Early packet filters block inbound SYN packets to stop a TCP three-way handshake. If no TCP three-way handshake occurs, no TCP communication can originate outside the filter.
However, it would help if you considered that the NMAP XMASS scan does not attempt to establish an entire TCP session to determine what ports are open. This filter will indeed prevent a TCP Connect scan, but because an XMASS scan creates packets without the SYN flag set, it will bypass the filter.
**Closing Points: UDP Scanning**
UDP scanning involves probing target systems for open UDP ports. Unlike TCP, UDP is connectionless, making verifying whether a port is open or closed is challenging. UDP scanning attempts to determine the state of UDP ports by sending packets and analyzing the responses.
UDP scanning provides valuable insights into network security. By identifying open UDP ports, security professionals can assess potential vulnerabilities and take appropriate measures to protect against threats. Additionally, it allows for the discovery of services and applications running on these ports, aiding in network mapping and a better understanding of the network infrastructure.
Types of UDP Scanning Techniques:
1. UDP Connect Scanning: This technique emulates a connection-oriented approach, similar to TCP scanning. It sends a UDP packet to a specific port and waits for a response, indicating whether the port is open, closed, or filtered.
2. UDP Stealth Scanning: Also known as UDP Idle Scanning, this technique leverages the concept of zombie hosts. UDP stealth scanning can glean information about open ports without directly interacting with the target by exploiting the trust relationship between a zombie host and the target.
3. UDP Fragmentation Scanning: This technique involves splitting UDP packets into smaller fragments to bypass firewall filters and evade detection. The scanner can identify open UDP ports by reassembling the fragmented packets at the receiving end.
Vulnerabilities Revealed by UDP Scanning:
1. Open UDP Ports: UDP scanning exposes open UDP ports that can be potential entry points for attackers. Services running on these ports may have vulnerabilities that can be exploited.
2. Misconfigured Firewalls: UDP scanning can uncover misconfigured firewalls that allow unauthorized access through open UDP ports.
3. Amplification Attacks: Certain UDP-based services can be exploited to launch amplification attacks, where a small request generates a significant response. UDP scanning helps identify such susceptible services and enables their mitigation.
While TCP scanning is more widely recognized, UDP scanning plays a crucial role in network security assessments. Security professionals can identify open UDP ports and potential vulnerabilities by leveraging various scanning techniques. Understanding UDP scanning and its significance helps organizations strengthen their network defenses against threats. Regular UDP scanning and robust security measures ensure a more resilient and secure network infrastructure.
Summary: UDP Scan
Understanding different scanning techniques is crucial in the vast world of network security. One such technique is UDP scanning, which allows for the identification of potential vulnerabilities in a network. In this blog post, we delved into the intricacies of UDP scanning, its benefits, and how it can be utilized effectively.
What is UDP Scanning?
UDP (User Datagram Protocol) scanning is used to discover open UDP ports on a target system. While TCP scanning focuses on establishing a connection with a host, UDP scanning involves sending a series of UDP packets to specific ports and analyzing the response. This technique helps identify potential entry points that hackers may exploit.
Benefits of UDP Scanning
UDP scanning provides several advantages in the realm of network security. Firstly, it allows administrators to assess the security posture of their network by identifying open ports that may be susceptible to unauthorized access. Secondly, it helps identify services running on non-standard ports, enabling better network management. Lastly, UDP scanning aids in detecting potential misconfigurations or outdated protocols that may pose security risks.
Techniques for Effective UDP Scanning
To ensure accurate and efficient UDP scanning, it is essential to employ the right techniques. One common approach is the ICMP-based scan, which involves sending UDP packets and analyzing the ICMP error messages received in response. Another technique is the reverse identification method, where the scanner sends packets to closed ports and examines the reaction to identify open ports. Employing a combination of these techniques enhances the overall effectiveness of the scanning process.
Overcoming Challenges and Limitations
While UDP scanning is a valuable technique, it comes with its challenges and limitations. One of the primary challenges is the lack of reliable responses from closed ports, which can lead to false positives or negatives. Additionally, firewalls and network filtering devices may block or alter UDP packets, making scanning more challenging. Understanding these limitations helps in interpreting scan results accurately.
Conclusion:
UDP scanning is a vital tool in the arsenal of network security professionals. Administrators can effectively utilize UDP scanning techniques to identify potential vulnerabilities, enhance network security, and mitigate risks. Understanding the intricacies and limitations of UDP scanning enables organizations to fortify their networks and stay one step ahead of potential threats.
- DMVPN - May 20, 2023
- Computer Networking: Building a Strong Foundation for Success - April 7, 2023
- eBOOK – SASE Capabilities - April 6, 2023