VPNOverview
In today's digital age, where our lives are intertwined with the virtual world, ensuring our online privacy and security has become more crucial than ever. One powerful tool that has gained immense popularity is a Virtual Private Network, commonly known as a VPN. In this blog post, we will delve into the world of VPNs, understanding what they are, how they work, and why they are essential.
A VPN is a technology that establishes a secure and encrypted connection between your device and the internet. It acts as a tunnel, routing your internet traffic through an encrypted server, providing you with a new IP address and effectively hiding your online identity. This layer of encryption ensures that your online activities remain private and protected from prying eyes.
Enhanced Online Security: By encrypting your internet connection, a VPN shields your personal information from hackers, cybercriminals, and other malicious entities. It prevents unauthorized access to your sensitive data, such as passwords, credit card details, and browsing history, while using public Wi-Fi networks or even at home.
Anonymity and Privacy: One of the primary advantages of a VPN is the ability to maintain anonymity online. With a VPN, your real IP address is masked, making it difficult for websites and online services to track your online activities. This ensures your privacy and allows you to browse the internet without leaving a digital footprint.
Bypassing Geo-restrictions: Another remarkable feature of VPNs is the ability to bypass geo-restrictions. By connecting to a server in a different country, you can access content that is otherwise restricted or blocked in your region. Whether it's streaming platforms, social media, or accessing websites in censored countries, a VPN opens up a world of possibilities.
Server Network and Locations: When selecting a VPN, consider the size and diversity of its server network. The more server locations available, the better chances of finding a server close to your physical location. This ensures faster connection speeds and a smoother browsing experience.
Ensure that the VPN provider uses robust encryption protocols like OpenVPN, IKEv2, or WireGuard. These protocols offer high levels of security and can safeguard your data effectively. Additionally, check for features like a kill switch that automatically disconnects your internet if the VPN connection drops, preventing any potential data leaks.
User-Friendly Interface: A user-friendly and intuitive interface is essential for a smooth VPN experience. Look for VPN providers that offer easy-to-use apps for various devices and operating systems. A well-designed interface makes it effortless to connect to a VPN server and customize settings according to your preferences.
A VPN is an indispensable tool for anyone concerned about their online privacy and security. Not only does it encrypt your internet connection and protect your sensitive data, but it also offers the freedom to browse the internet without limitations. By choosing the right VPN provider and understanding its features, you can enjoy a safe and private online experience like never before.
Matt Conran
Highlights: VPNOverview
### What is a VPN?
A Virtual Private Network, or VPN, is a service that creates a secure, encrypted connection between your device and a remote server operated by the VPN provider. This connection masks your IP address, making your internet activity virtually untraceable. Think of it as a private tunnel through which your data travels, hidden from anyone trying to peek in.
### Why Use a VPN?
Using a VPN offers several advantages, primarily focusing on privacy and security. When you connect to the internet through a VPN, your data is encrypted, protecting sensitive information like passwords and credit card numbers from hackers and snoopers. Additionally, by masking your IP address, a VPN helps maintain your anonymity, preventing websites and advertisers from tracking your online behavior.
### Accessing Geo-Restricted Content
One of the most popular reasons people turn to VPNs is to bypass geo-restrictions. Many streaming services, websites, and online platforms restrict content based on geographic location. By connecting to a server in a different country, a VPN allows you to access content as if you were physically present in that region. This feature has made VPNs a favorite tool for travelers and those looking to explore a broader range of online entertainment.
### Choosing the Right VPN
With numerous VPN providers available, selecting the right one can be overwhelming. Key factors to consider include the level of encryption, server locations, connection speed, and privacy policies. Some VPNs offer additional features like ad-blocking, malware protection, and no-log policies, which are crucial for ensuring your data remains confidential. It’s essential to research and choose a VPN that aligns with your needs and values.
Generic VPNs: Virtual Private Networks:
A: – ) A virtual private network (VPN) is a secure way to connect to a remote computer or network over the internet, allowing users to access otherwise unavailable resources. It is a private network that uses encryption technology to protect data traveling between two points, such as computers or a computer and a server. Companies commonly use VPNs to secure remote access to their internal networks and are also popular among individuals for protecting their privacy on the internet.
B: – ) A VPN creates an encrypted tunnel between the user’s computer and the remote network. All data that passes through this tunnel is secured and encrypted, making it much more difficult for hackers to intercept. This also allows users to access websites and services that their local government or ISP may block. VPNs can also spoof a user’s location, allowing them to access geo-restricted content.
C: – ) When setting up a VPN, users have several options. They can use a dedicated VPN service or configure their own VPN using open-source software. The type of VPN protocol used can also vary depending on the security requirements and desired performance.
The Concept of Tunneling:
VPNs provide a secure and private connection between your device and the internet by encrypting your data and routing it through a remote server. They offer several benefits, such as masking your IP address, protecting your data from hackers, and granting access to geo-restricted content.
Tunneling, on the other hand, is a technique used to encapsulate data packets within another protocol for secure transmission. It creates a “tunnel” by wrapping the original data with an additional layer of encryption, effectively hiding your online activities from prying eyes. Tunneling can be used independently or as part of VPN technology.
While both VPNs and tunneling provide security and privacy, their functionalities differ. VPNs act as a comprehensive solution by providing encryption, IP masking, and routing through remote servers. Tunneling, on the other hand, focuses primarily on data encapsulation and secure transmission.
**Understanding IPv6 Tunneling**
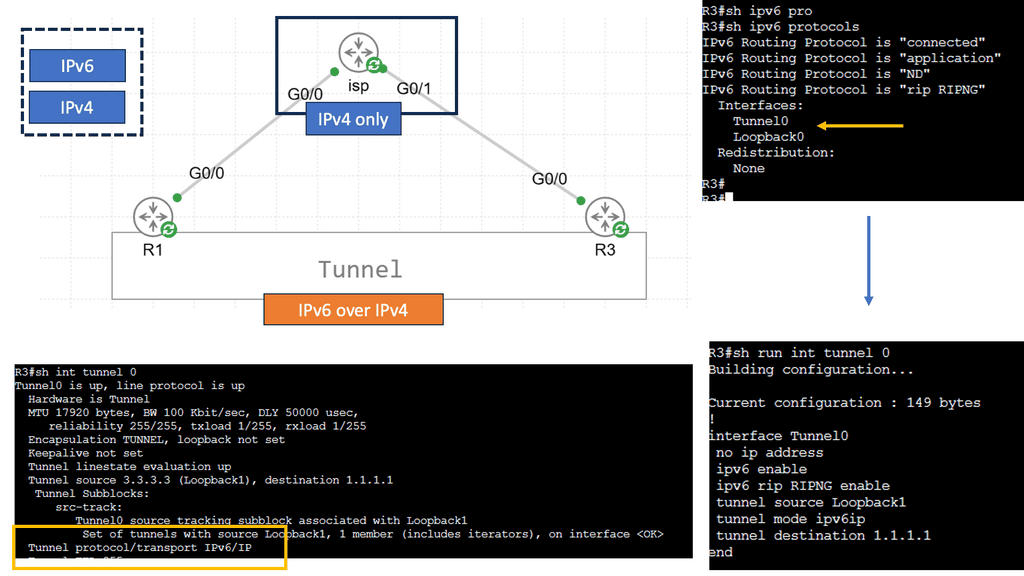
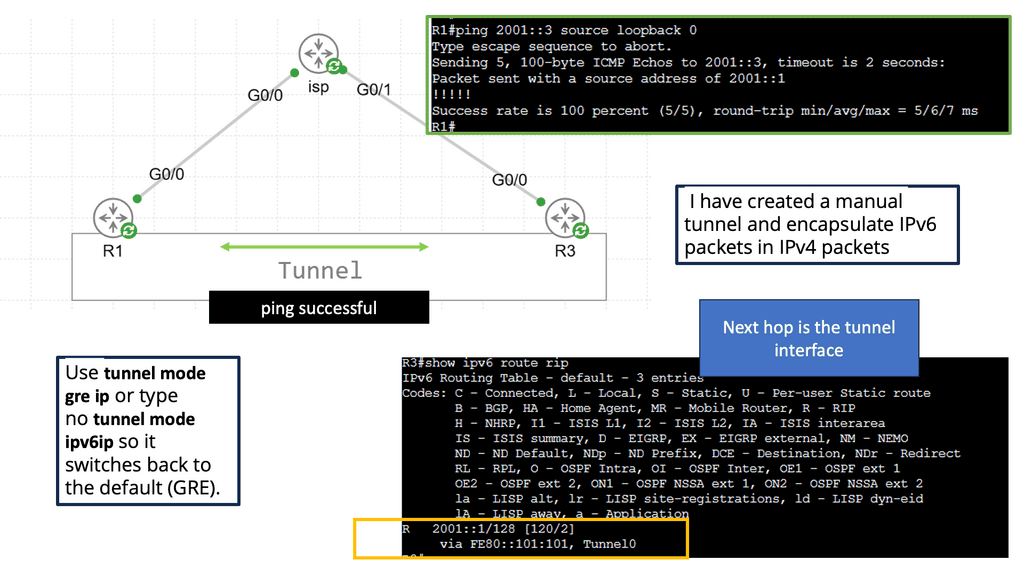
IPv6 tunneling is a mechanism that encapsulates IPv6 packets within IPv4 packets, allowing them to traverse an IPv4-only network infrastructure. The encapsulated IPv6 packets are then decapsulated at the tunnel endpoints, enabling communication between IPv6 networks over an IPv4 network.
There are several tunneling techniques commonly used in IPv6 deployments. Let’s explore a few of them:
– Manual Tunneling: Manual tunneling involves configuring the tunnel endpoints and the encapsulation mechanism. It requires explicit configuration on both ends of the tunnel and is often used for point-to-point connections or small-scale deployments.
– Automatic tunneling, also known as 6to4 tunneling, allows for automatic encapsulation and decapsulation of IPv6 packets within IPv4 packets. It utilizes the 2002::/16 prefix to create a virtual IPv6 network over the existing IPv4 infrastructure. While easy to set up, automatic tunneling may suffer from scalability issues and potential conflicts with private IPv4 addresses.
– Teredo Tunneling: Teredo tunneling is another automatic technique that enables IPv6 connectivity for hosts behind IPv4 NAT devices. It encapsulates IPv6 packets within UDP packets, allowing them to traverse NAT boundaries. Teredo benefits home and small office networks, as it doesn’t require manual configuration.
The Concepts of Encapsulation:
Encapsulation is a fundamental concept in networking that involves enclosing data packets within additional layers of information. This process enhances data security and facilitates its seamless transfer across networks. By encapsulating packets, valuable information is shielded from unauthorized access and potential threats.
There are several widely-used encapsulation protocols, each with its own unique features and applications. Let’s explore a few of them:
1. IPsec (Internet Protocol Security): IPsec provides a secure framework for encrypted communication over IP networks. It ensures data integrity, confidentiality, and authentication, making it ideal for secure remote access and virtual private networks (VPNs).
2. GRE (Generic Routing Encapsulation): GRE is a versatile encapsulation protocol commonly used to establish point-to-point connections between networks. It encapsulates various network layer protocols, enabling the transmission of non-IP traffic over IP networks.
3. MPLS (Multi-Protocol Label Switching): MPLS is a powerful encapsulation protocol that efficiently routes data packets through complex networks using labels. It enhances network performance, improves traffic engineering, and simplifies network management.
**Understanding GRE and Its Purpose**
GRE is a tunneling protocol designed to encapsulate a wide variety of network layer protocols, enabling them to travel over an IP network as if they were part of a point-to-point connection. This encapsulation allows for the creation of virtual point-to-point links over an IP network, providing flexibility in routing and the ability to connect disparate networks seamlessly. GRE supports multicast packet encapsulation, making it an excellent choice for transporting protocols like OSPF and EIGRP across non-multicast networks.
**Configuring GRE on Cisco Devices**
To configure GRE on Cisco devices, network administrators must establish a GRE tunnel interface and configure the source and destination IP addresses. This section will walk you through the step-by-step process of setting up a GRE tunnel on Cisco routers. We’ll dive into the necessary command-line interface (CLI) commands and explore configuration tips that can enhance your network’s performance. Understanding these configurations will empower you to implement GRE tunnels effectively, ensuring seamless communication between networks.
VPN network
Layer 2 and Layer 3 technologies
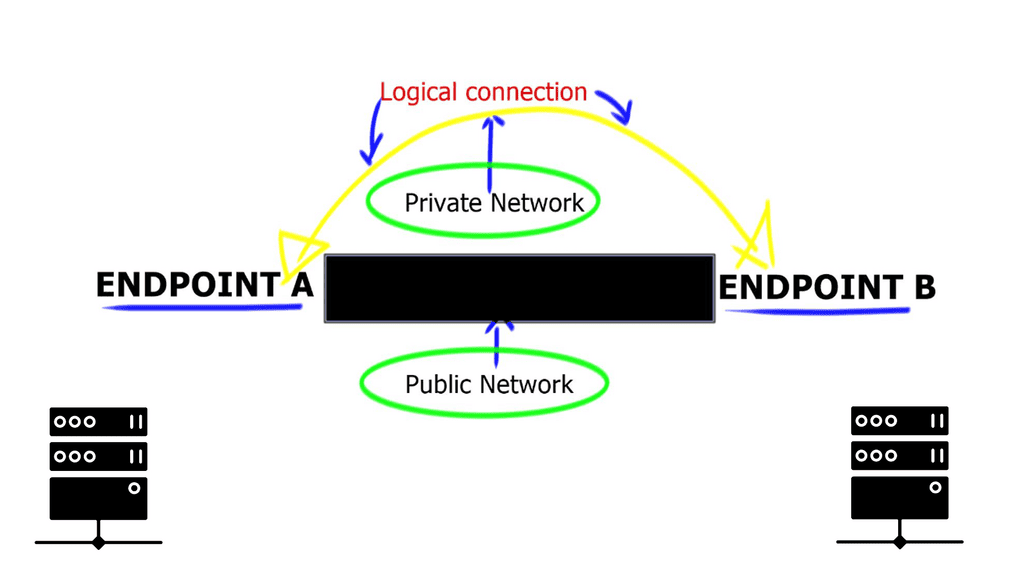
Virtual Private Networks ( VPNs ) are top-rated among businesses and individuals who access the Internet regularly and are provided by various suppliers. They are available as Layer 2 and Layer 3 technologies. They act as extensions, expanding private networks over public networks. Groups of different users share public networks; if privacy is required, encryption must be deployed to secure endpoint communication. The Internet is the most prevalent and widely known “public” network. In its simplest form, a VPNoverview, VPN connects two endpoints to form a logical connection.
VPN Technologies: Layer 2 and Layer 3 VPN
A VPN is a logical connection between two endpoints over a public network. Based on these logical connection models, VPN technologies can be classified as Layer 2 or Layer 3 VPNs based on their logical connections. The concept of establishing connectivity between sites over a Layer 2 or Layer 3 VPN is the same.
The concept involves adding a “delivery header” before the payload to get it to the destination site. The delivery header is placed at Layer 2 in Layer 2 VPNs and at Layer 3 in Layer 3 VPNs. GRE, L2TP, MPLS, and IPSec are examples of Layer 3 VPNs; ATM and Frame Relay are examples of Layer 2 VPNs.
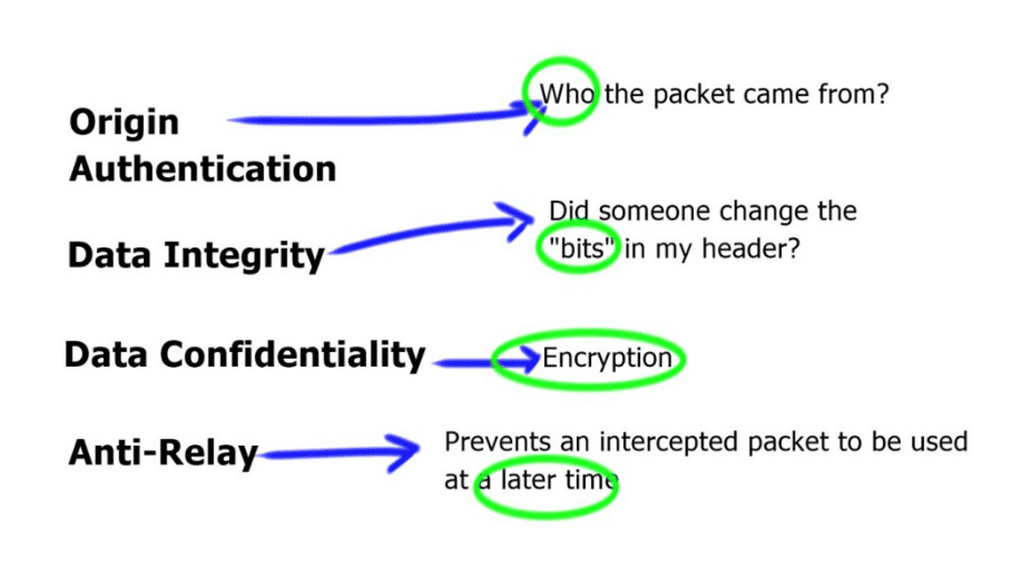
VPNs provide a couple of features such as:
- Confidentiality: preventing anyone from reading your data. This is implemented with encryption.
- Authentication: verifying that the router/firewall or remote user sending VPN traffic is a legitimate device or router.
- Integrity: verifying that the VPN packet wasn’t changed somehow during transit.
- Anti-replay: preventing someone from capturing traffic and resending it, trying to appear as a legitimate device/user.
VPN Types
There are two common VPN types that we use:
Site-to-site VPN
Organizations must deploy compatible VPN gateways or routers to implement a site-to-site VPN at each network location. These devices establish a secure tunnel between the networks, encrypting data packets and ensuring secure communication. Example: VPN protocols such as IPsec (Internet Protocol Security) or SSL/TLS (Secure Sockets Layer/Transport Layer Security) are commonly used to secure the connection.
With the site-to-site VPN, we have a network device at each site. Between these two network devices, we build a VPN tunnel. Each end of the VPN tunnel encrypts the original IP packet, adds a VPN header and a new IP header, and then forwards the encrypted packet to the other end.
Client-to-site VPN
Client-to-site VPNs, or remote access VPNs, provide a secure connection between individual users or devices and a private network. Unlike site-to-site VPNs that connect entire networks, client-to-site VPNs are designed to grant remote access to authorized users. Establishing an encrypted tunnel ensures data confidentiality and integrity, protecting sensitive information from prying eyes.
The client-to-site VPN is also called the remote user VPN. The user installs a VPN client on his/her computer, laptop, smartphone, or tablet. The VPN tunnel is established between the user’s and remote network devices.
VPN Protocols
IPSec:
IPSEC, short for Internet Protocol Security, is a protocol for secure Internet communication. VPN, or Virtual Private Network, extends a private network across a public network, enabling users to send and receive data as if their devices were directly connected to the private network. IPSEC VPN combines the power of both these technologies to create a secure and private connection over the internet.
IPSec was created because the IP itself lacks security features. On layer three of the OSI model, IPSec provides confidentiality, integrity, authentication, and anti-replay features, but it isn’t a protocol.
Frameworks use a variety of protocols, and the advantage is that they can be changed in the future. If a new encryption algorithm is developed, such as DES, 3DES, or AES, IPSec may use it.
IPSec can be used for a variety of purposes:
- Setting up a VPN tunnel from one site to another.
- Tunneling a client-to-site VPN (remote user).
- Traffic is authenticated and encrypted between two servers.
Example: IPSec VTI
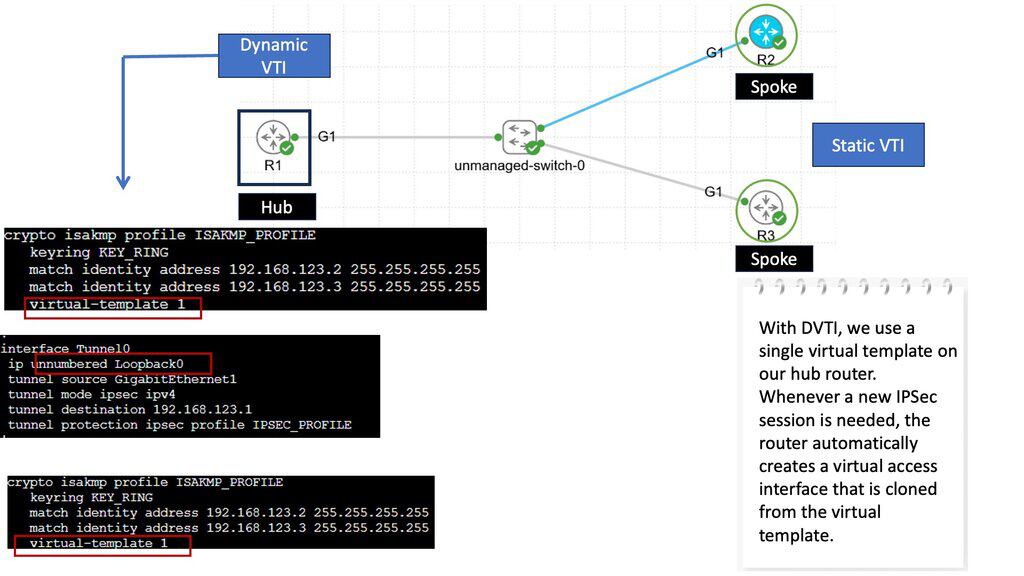
### What is IPSec VTI?
IPSec VTI, or Virtual Tunnel Interface, is a method that simplifies the configuration and management of IPSec tunnels. Unlike traditional IPSec configurations, which require multiple steps and complex policies, VTI offers a straightforward approach. By treating the tunnel as a virtual interface, network administrators can apply routing protocols directly to the tunnel, making the process seamless and efficient.
### How Does IPSec VTI Work?
IPSec VTI functions by encapsulating IP packets within an IPSec-protected tunnel. Here’s a simplified breakdown of the process:
1. **Establishing the Tunnel**: A virtual interface is created on each end of the tunnel, which acts as the endpoints for the secure communication.
2. **Encapsulation**: Data packets are encapsulated within IPSec headers, providing encryption and authentication.
3. **Routing**: The encapsulated packets are routed through the virtual tunnel interface, ensuring that they reach their destination securely.
4. **Decapsulation**: Upon arrival, the IPSec headers are stripped away, and the original data packets are delivered to the intended recipient.
IPSec Components
An IPSec implementation has several components. These include Security Associations (SAs), which define the parameters for secure communication, and Key Management protocols, such as Internet Key Exchange (IKE), which establish and maintain the cryptographic keys used for encryption and authentication. Additionally, IPSec employs encryption algorithms, such as AES or 3DES, and hash functions, like SHA-256, for data integrity.
IPSec Modes of Operation
IPSec supports two modes of operation: Transport mode and Tunnel mode. Transport mode encrypts only the payload of IP packets, leaving the IP header intact. It is typically used for end-to-end communication between hosts. On the other hand, Tunnel mode encapsulates the entire IP packet within a new IP packet, adding an extra layer of security. This mode is often employed for secure communication between networks.
**PPTP VPN**
Developed by Microsoft, PPTP VPN is a widely used VPN protocol that creates a secure and encrypted tunnel between your device and the Internet. It operates at the data link layer of the OSI model and is supported by most operating systems, including Windows, macOS, Linux, Android, and iOS. Its simplicity and compatibility make it an attractive choice for many users.
An older VPN protocol, PPTP (Point to Point Tunneling Protocol), was released around 1995. A GRE tunnel is used for tunneling, and PPP is used for authentication (MS-Chap or MS-Chap v2). MPPE is used for encryption.
As PPTP has been around for a while, many clients and operating systems support it. PPTP, however, has been proven to be insecure, so you shouldn’t use it anymore.
Simplicity of Setup
Setting up PPTP is relatively straightforward, even for users with minimal technical expertise. Most operating systems offer built-in support for PPTP, eliminating the need for third-party software. Users can configure PPTP connections by entering server details provided by their VPN service provider, making it accessible to many users.
Security Considerations
While PPTP offers convenience and speed, it is essential to note that it may not provide the same level of security as other VPN protocols. PPTP uses MPPE (Microsoft Point-to-Point Encryption) to encrypt data packets, which has been criticized for potential vulnerabilities. Therefore, users with heightened security concerns may opt for alternative VPN protocols like OpenVPN or L2TP/IPSec.
**L2TP VPN**
L2TP VPN is a protocol for creating a secure connection between two endpoints over an existing network infrastructure. It operates at the data link layer of the OSI model and combines the best features of the L2F (Layer 2 Forwarding) and PPTP (Point-to-Point Tunneling Protocol) technologies. L2TP VPN ensures confidentiality and integrity during transmission by encapsulating and encrypting data packets.
In L2TP (Layer Two Tunneling Protocol), layer two traffic is tunneled over layer three connections, as the name suggests. Using L2TP, you can connect two remote LANs using a single subnet on both sites if you need to “bridge” them together. Because L2TP does not offer encryption, we often use it with IPSec. L2TP/IPSec is a combination of L2TP and IPSec
How L2TP Works
L2TP operates by establishing a tunnel between the sender and receiver. This tunnel encapsulates the data packets and ensures secure transmission. L2TP relies on other protocols, such as IPsec (Internet Protocol Security), to provide encryption and authentication, further enhancing the connection’s security.
**SSL VPN**
SSL VPN is a technology that allows users to establish a secure encrypted connection to a private network over the internet. Unlike traditional VPNs, which often require dedicated software or hardware, SSL VPN leverages the widely used web browser for connectivity. This makes it highly convenient and accessible for users across different devices and platforms.
HTTPS (Secure Sockets Layer) is a protocol for encrypting traffic between a web browser and a web server. HTTP allows you to browse the web in clear text. HTTPS is used for secure connections. The same technology can be used for VPNs as well.
Since SSL VPN uses HTTPS, you can use it pretty much anywhere. Most public WiFi hotspots allow HTTPS traffic, while others may block other traffic, such as IPSec. SSL VPN is also popular because you don’t have to use client software. Most SSL VPN solutions can access applications through a web browser portal. However, a software client might need some advanced features.
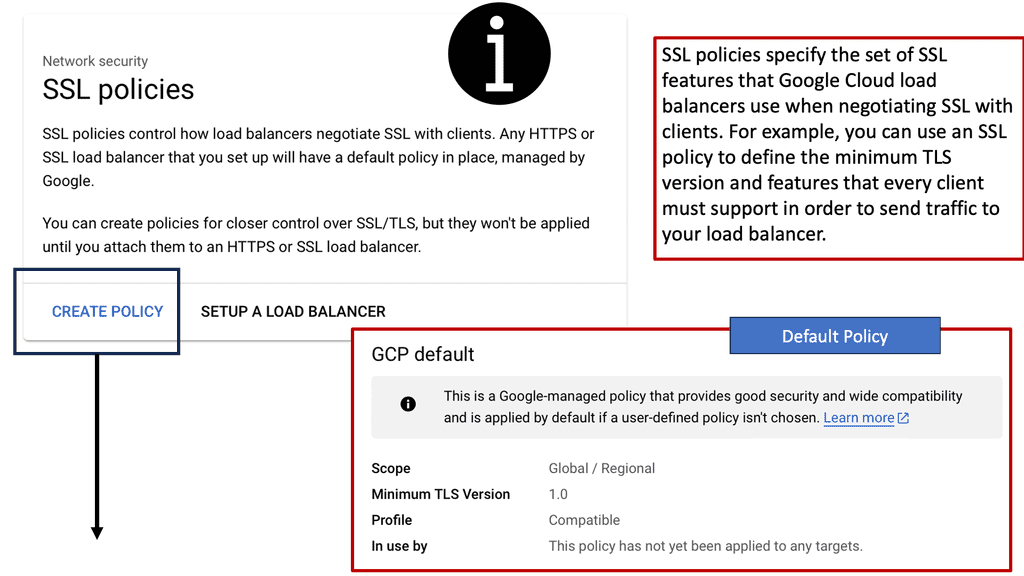
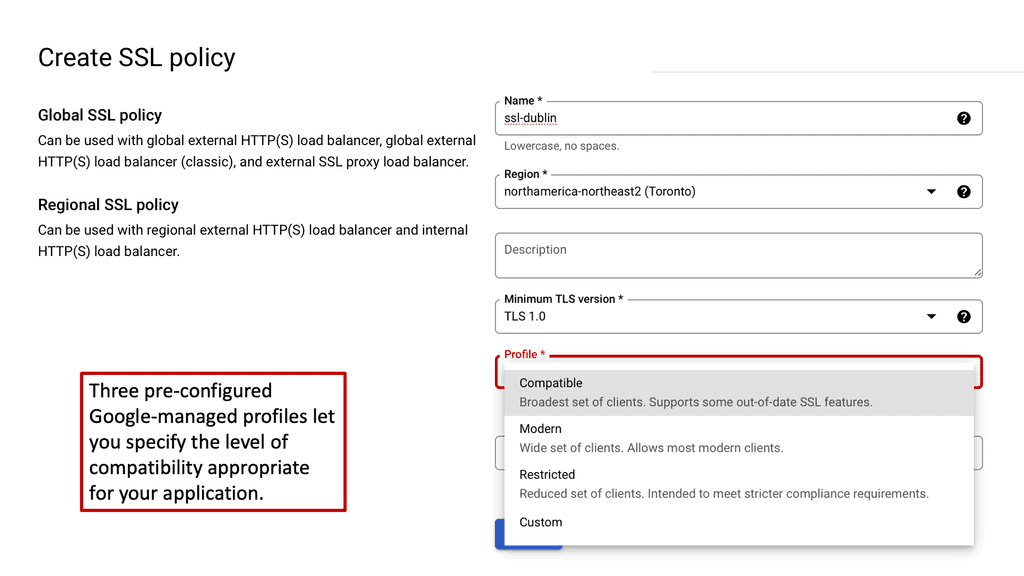
**Configuring SSL Policies on Google Cloud**
Google Cloud offers robust tools and services for managing SSL policies effectively. To configure SSL policies, you can utilize Google Cloud’s Load Balancing services. These services allow you to specify the minimum TLS version and select the appropriate cipher suites for your applications. By setting these parameters, you can ensure that your applications only support secure and up-to-date protocols, thus enhancing your overall security posture.
**Best Practices for SSL Policy Management**
Implementing SSL policies on Google Cloud requires a strategic approach. Here are some best practices to consider:
1. **Regularly Update Protocols and Ciphers**: Stay abreast of the latest security standards and update your SSL policies accordingly. This ensures that your applications are protected against emerging threats and vulnerabilities.
2. **Monitor and Audit SSL Configurations**: Regularly monitor your SSL configurations to identify any anomalies or misconfigurations. Conduct audits to ensure compliance with industry standards and internal security policies.
3. **Educate Your Team**: Ensure that your IT and security teams are well-versed in SSL policies and their importance. Conduct training sessions to keep them informed about the latest developments in cloud security.
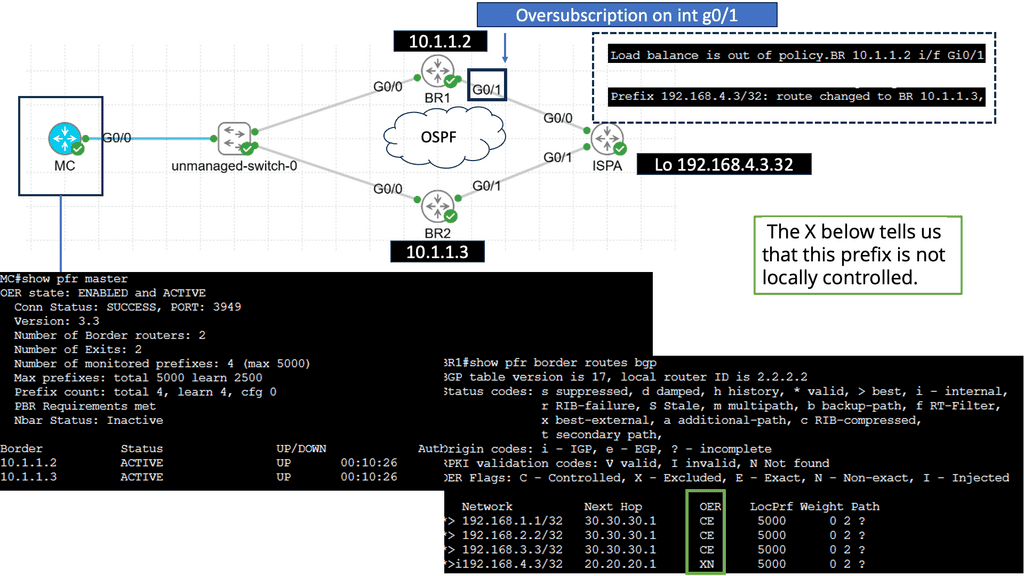
Use Case: Understanding Performance-Based Routing
– Performance-based routing is a dynamic routing technique that selects the best path for network traffic based on real-time performance metrics. Unlike traditional static routing, which relies on predetermined routes, performance-based routing analyzes factors such as network latency, packet loss, and bandwidth utilization to determine the most efficient path for data transmission.
– While performance-based routing offers numerous benefits, certain factors must be considered before implementation. First, organizations need to ensure that their network infrastructure is capable of collecting and analyzing real-time performance data. Monitoring tools and network probes may be required to gather the necessary metrics. Additionally, organizations must carefully plan their routing policies and prioritize traffic to align with their needs and objectives.
– Implementing performance-based routing requires a systematic approach. Organizations should start by conducting a comprehensive network assessment to identify potential bottlenecks and areas for improvement.
– Next, they should select suitable performance monitoring tools and establish baseline performance metrics. This information allows organizations to configure their routers and switches to enable performance-based routing. Regular monitoring and fine-tuning of routing policies are essential to maintain optimal network performance.
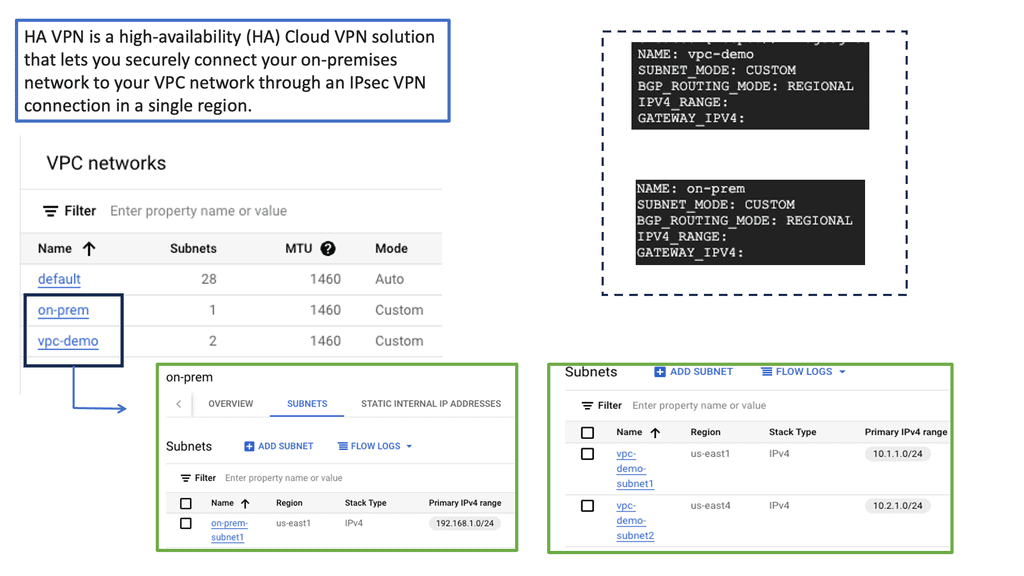
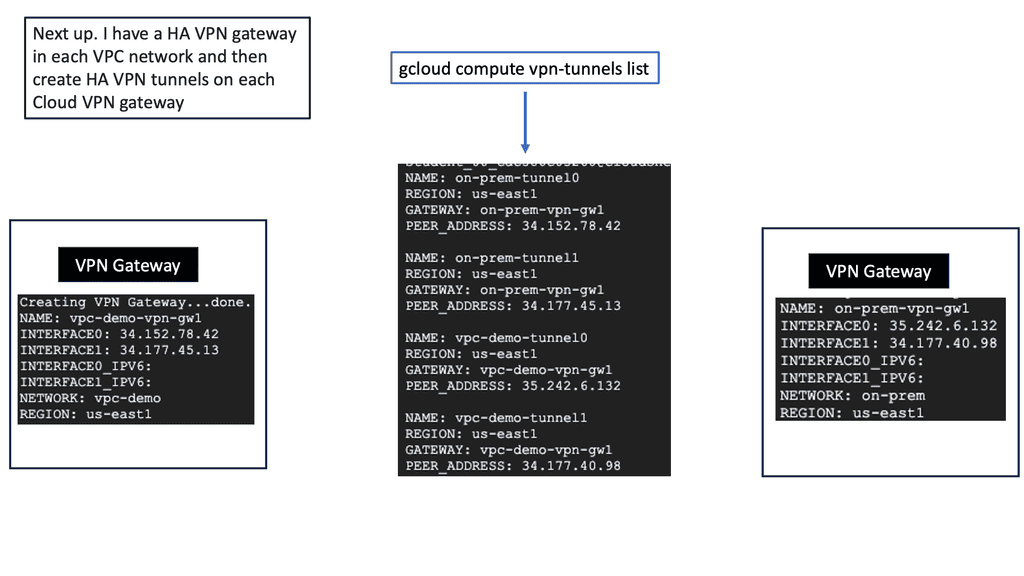
Google Data Centers – HA VPN
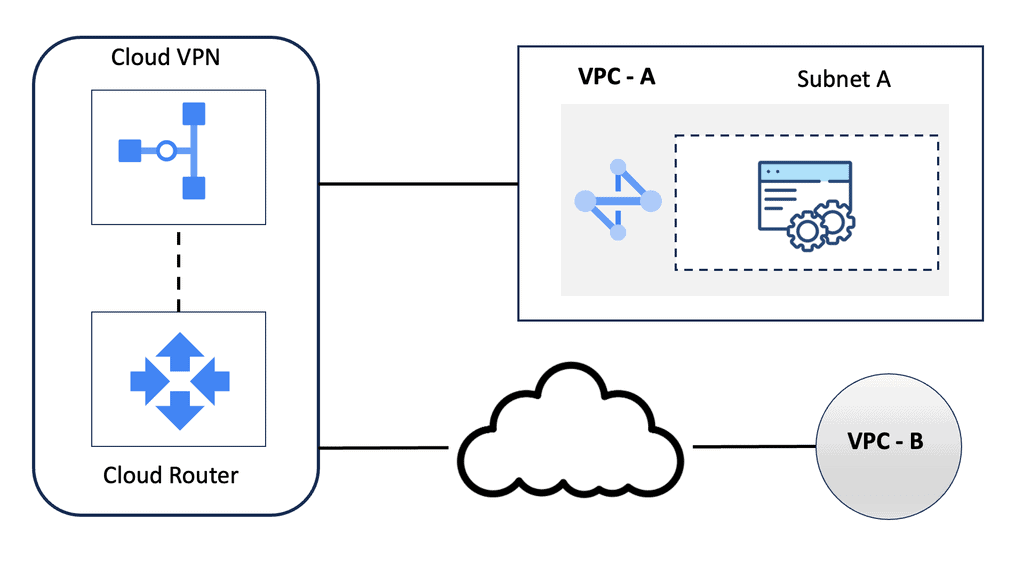
Understanding HA VPN
HA VPN, short for High Availability VPN, is a feature Google Cloud provides that allows for redundant and highly available VPN connections. It ensures that even if one VPN tunnel fails, traffic seamlessly switches to the backup tunnel, minimizing downtime and ensuring continuous connectivity. This resilience is crucial for businesses that rely heavily on uninterrupted network access.
The HA VPN Configuration offers several advantages over traditional VPN setups. Firstly, it provides automatic failover, reducing the risk of service disruptions. Secondly, it offers improved network reliability, as the redundant tunnels ensure continuous connectivity. Additionally, HA VPN Configuration simplifies network management by eliminating the need for manual intervention during failover events.
Configuring HA VPN in Google Cloud is straightforward. First, you need to create a virtual private network (VPC) in Google Cloud. Next, you’ll set up the HA VPN gateway and configure the VPN tunnels. Make sure to select the appropriate routing options and encryption settings. Lastly, you’ll establish the VPN connection between your on-premises network and the HA VPN gateway in Google Cloud.
 WAN Edge Services
WAN Edge Services
What is Network Address Translation?
Network Address Translation, commonly known as NAT, is a fundamental concept in computer networking. It is a technique used to modify network address information in IP packet headers while traversing through a router or firewall. The primary objective of NAT is to enable multiple devices on a private network to share a single public IP address, thus conserving IP address space.
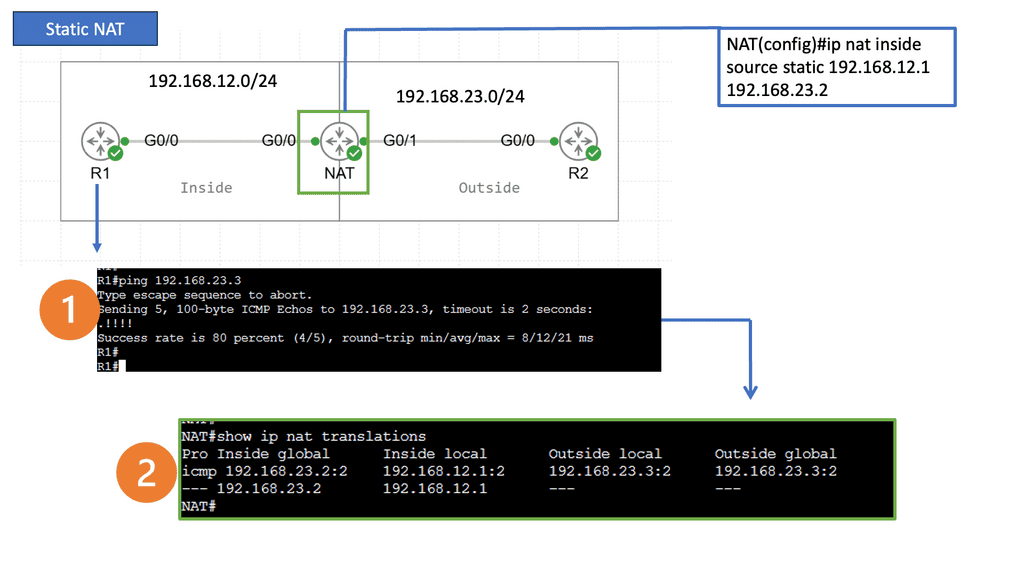
Static NAT: Static NAT, also known as one-to-one NAT, involves mapping a public IP address to a specific private IP address. This type of NAT is commonly used when a particular device within a private network needs to be accessible from the public internet.
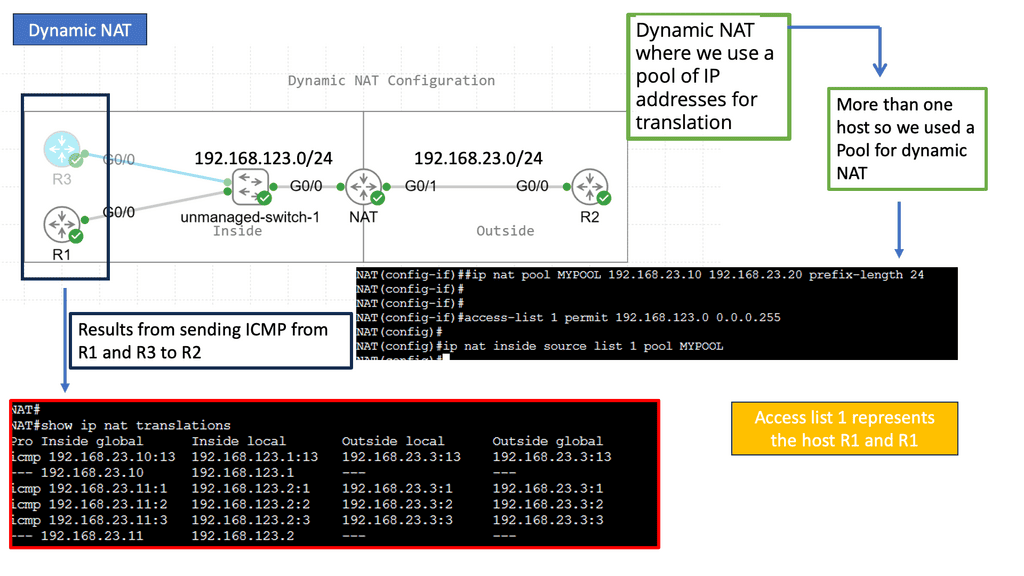
Dynamic NAT: Dynamic NAT operates similarly to Static NAT but with a significant difference. Instead of using one-to-one mapping, Dynamic NAT allows a pool of public IP addresses to be shared among multiple private IP addresses, allowing for a more efficient use of the available IP addresses.
Port Address Translation (PAT): PAT, also called NAT Overload, is a variation of Dynamic NAT. In PAT, multiple private IP addresses are mapped to a single public IP address using different port numbers. This technique enables many devices on a private network to access the internet simultaneously, utilizing a single public IP address.
– IP Address Conservation: NAT helps conserve the limited pool of public IP addresses by allowing multiple devices to share a single IP.
Enhanced Security: By hiding the internal IP addresses, NAT provides an additional layer of security, making it harder for external entities to access devices directly within the private network.
– End-to-End Connectivity: NAT can introduce challenges in establishing direct communication between devices on different private networks, limiting specific applications and protocols.
– Impact on IP-based Services: Some IP-based services, such as VoIP or peer-to-peer applications, may not function optimally when NAT is involved.
Advanced VPNs
Understanding DMVPN:
DMVPN is a dynamic VPN technology that enables the creation of secure overlay networks over existing infrastructure. Utilizing multipoint GRE tunnels allows for the seamless establishment of encrypted connections between multiple sites, regardless of geographical location. This flexibility makes DMVPN an appealing choice for organizations with distributed networks.
A -: Multipoint GRE Tunnels: Multipoint GRE (mGRE) tunnels serve as the foundation of DMVPN. These tunnels establish a virtual network that connects multiple sites, enabling direct communication between them. Using a single tunnel interface for all connections, mGRE simplifies the network architecture and reduces complexity.
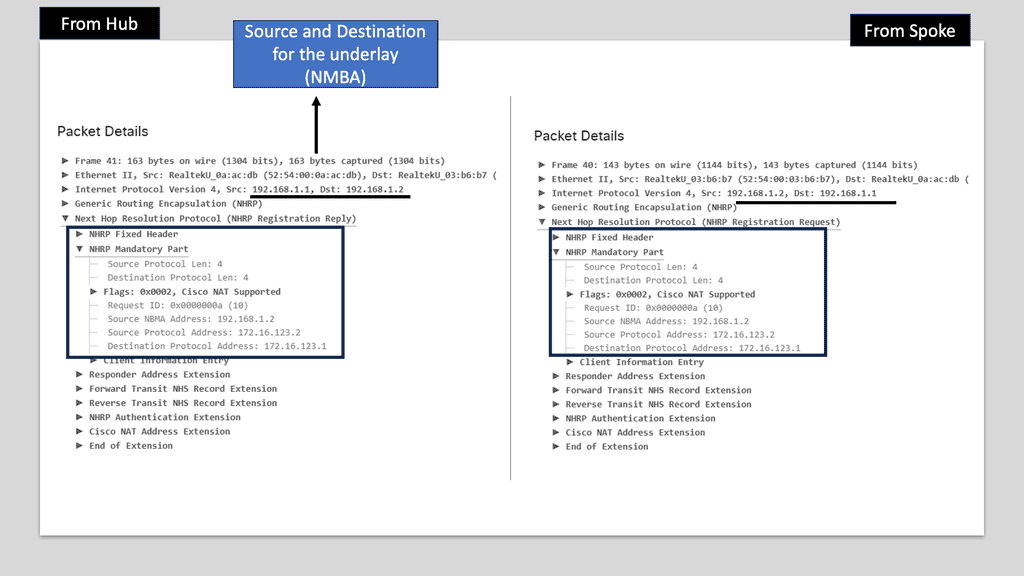
B -: Next-Hop Resolution Protocol (NHRP): NHRP plays a crucial role in DMVPN by providing dynamic mapping of tunnel IP addresses to physical addresses. It allows spoke routers to dynamically register their IP addresses with a hub router, eliminating the need for static mappings. NHRP also handles traffic forwarding among the spoke routers, ensuring efficient routing within the DMVPN network.
C: – IPsec Encryption: IPsec encryption ensures the security of data transmitted over the DMVPN network. IPsec provides a secure tunnel between the participating routers, encrypting the traffic and preventing unauthorized access. This encryption ensures the data’s confidentiality, integrity, and authenticity over the DMVPN network.
Understanding MPLS VPN
MPLS VPN, short for Multiprotocol Label Switching Virtual Private Network, is a networking technique that combines the advantages of both MPLS and VPN technologies. At its core, MPLS VPN allows for creating private and secure networks over a shared infrastructure. Unlike traditional VPNs, which rely on encryption and tunneling protocols, MPLS VPN utilizes labels to route traffic efficiently.
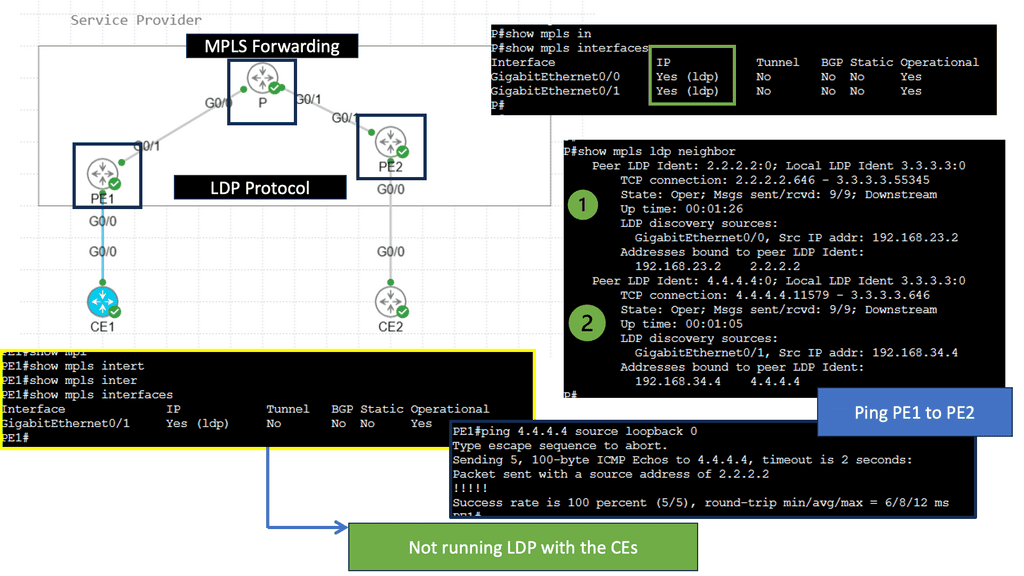
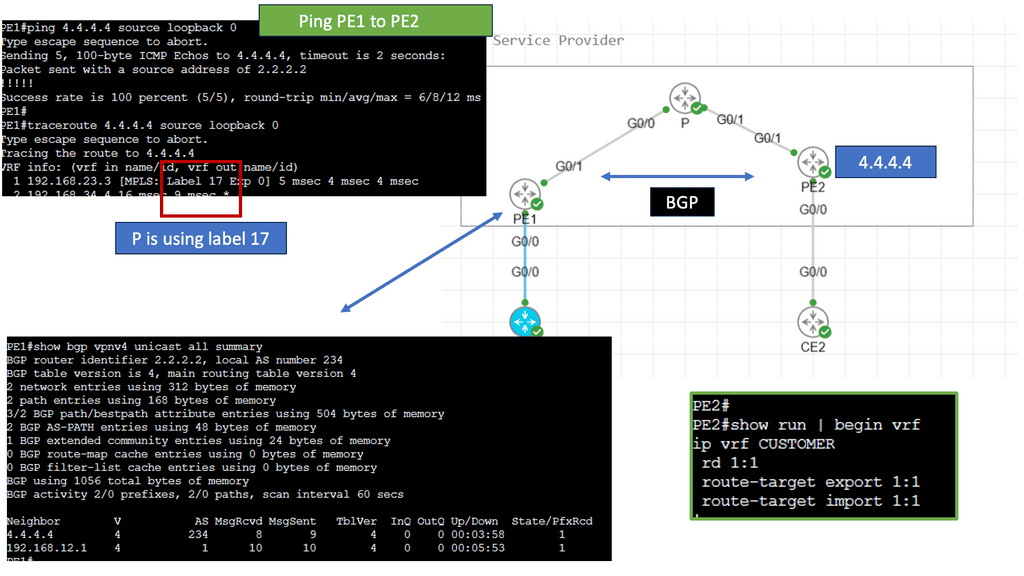
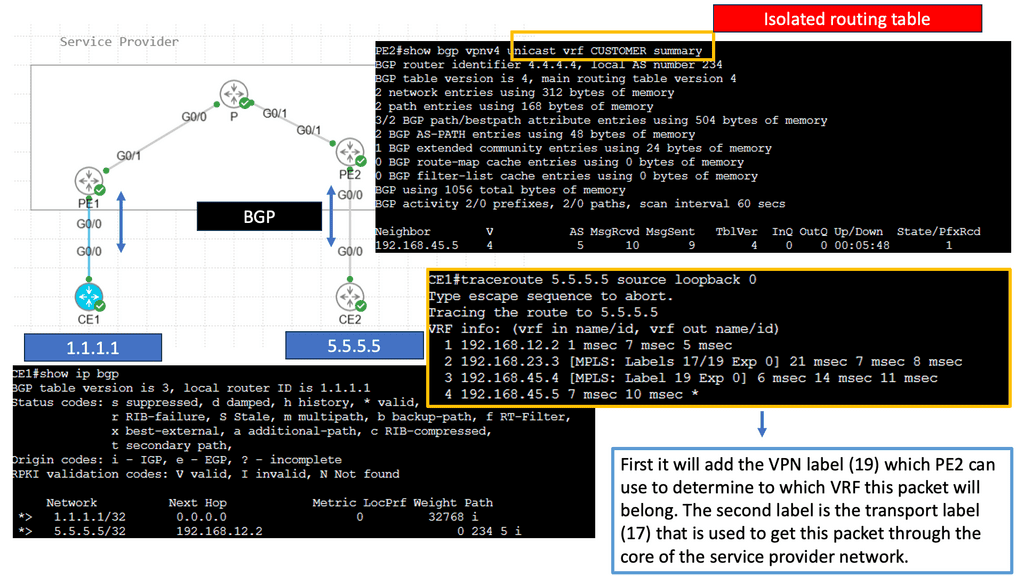
Understanding the magic of MPLS VPN’s underlying operation is essential to comprehending its magic. In this section, we’ll explore the key components: Provider Edge (PE) routers, Provider (P) routers, and Customer Edge (CE) routers. We’ll uncover the label-switching mechanism, where labels are assigned to packets at the ingress PE router, facilitating fast and efficient forwarding across the MPLS network.
Understanding GETVPN
GETVPN, short for Group Encrypted Transport VPN, is a network technology that provides secure communication across wide area networks. Unlike traditional VPN solutions, GETVPN focuses on providing encryption at the network layer, ensuring data transmission confidentiality, integrity, and authenticity.
GETVPN offers a range of powerful features, making it an attractive choice for organizations seeking robust network security. One such feature is its ability to provide scalable encryption for large-scale networks, allowing seamless expansion without compromising performance. Additionally, GETVPN supports multicast traffic, enabling efficient communication across multiple sites.
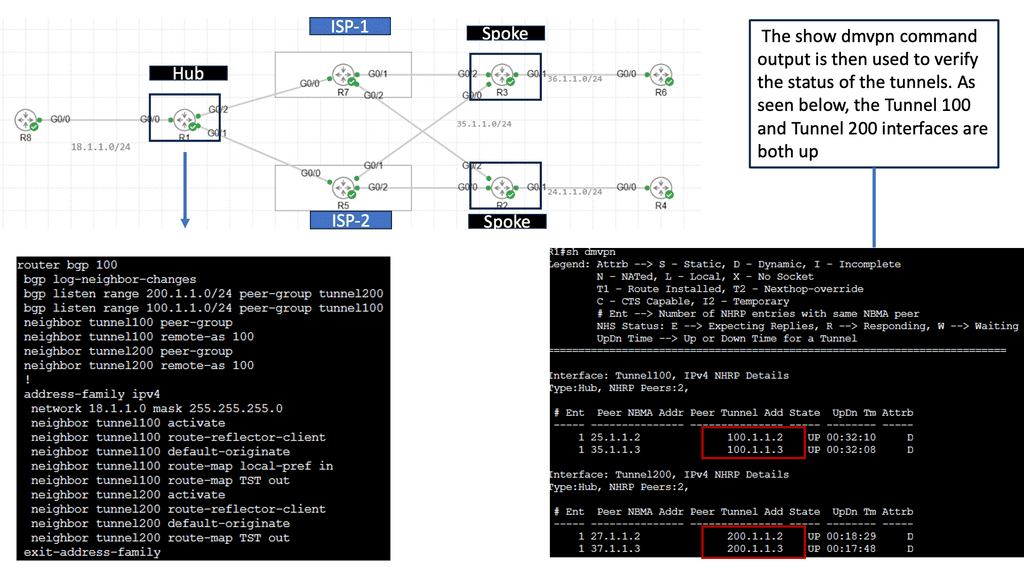
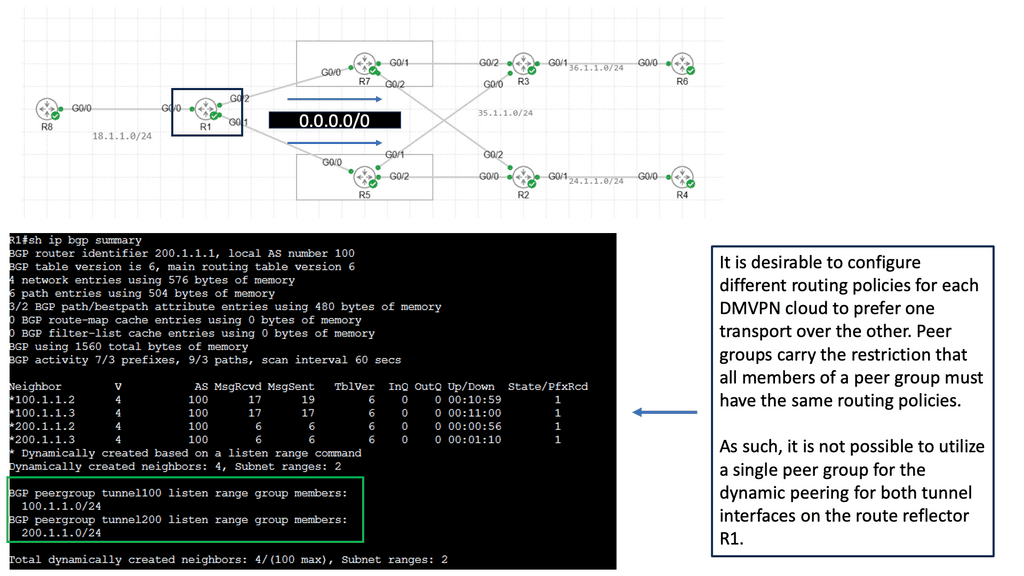
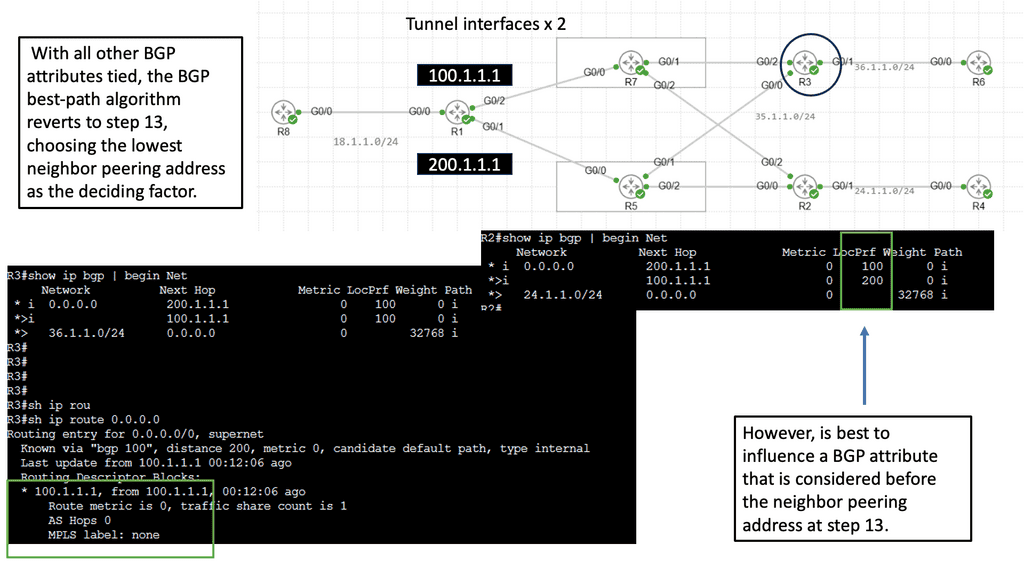
Use Case: DMVPN Dual Cloud, Single Hub
Exploring Single Hub Dual Cloud Architecture
The single hub dual cloud deployment model is an advanced DMVPN configuration that offers enhanced redundancy and scalability. In this architecture, a single hub site is the central point for all remote sites, while two separate cloud service providers (CSPs) are used for internet connectivity. This setup ensures that even if one CSP experiences an outage, connectivity remains intact through the other CSP.
– Improved Redundancy: By leveraging two separate CSPs, the single hub dual cloud DMVPN architecture minimizes the risk of connectivity loss due to a single point of failure.
– Enhanced Scalability: With this deployment model, businesses can quickly scale their network infrastructure by adding new remote sites without disrupting existing connections.
– Optimized Performance: Using multiple CSPs allows for load balancing and traffic optimization, ensuring efficient utilization of available bandwidth.
**Layer 2 and Layer 3 VPN comparison**
Therefore, Layer 2 and Layer 3 VPNs differ in the following ways:
As far as Layer 2 is concerned, there is no routing interaction between the customer and the service provider. Routes can be exchanged between CE and PE routers in L3VPN.
Customers can run any Layer 3 protocol between sites using Layer 2. The SP network does not recognize Layer 3 protocol since it transports Layer 2 frames. Even though IP is prevalent in many enterprise networks, non-IP protocols like IPX or SNA are also commonly used. This would preclude using a Layer 3 VPN for transporting such traffic.
In the Layer 2 case, multiple (logical) interfaces are required between each CE and the corresponding PE, one per remote CE. When the CE routers are fully meshed, and there are 10 CE routers, each CE has nine interfaces (DLCIs, VCs, and VLANs, depending on the media type) to the PE. Since the PE will route traffic to the appropriate egress CE in the Layer 3 VPN, one connection between each CE and the PE is sufficient.
Before you proceed, you may find the following posts helpful:
VPNOverview
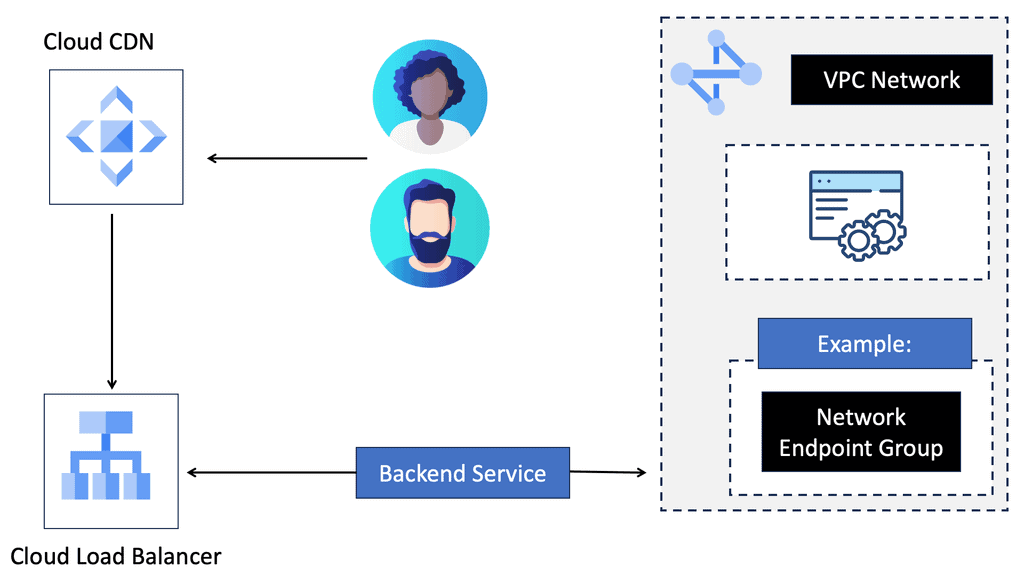
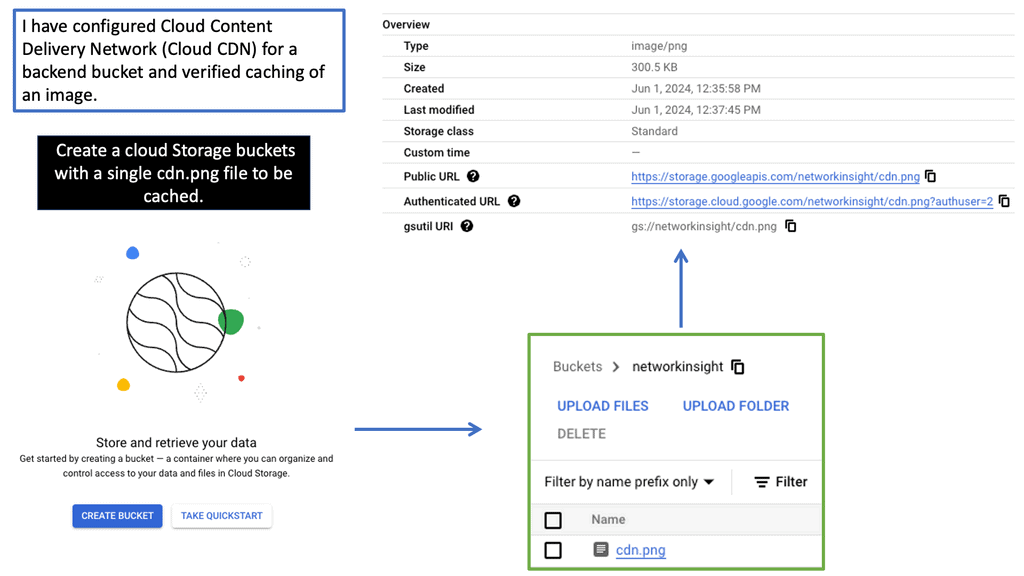
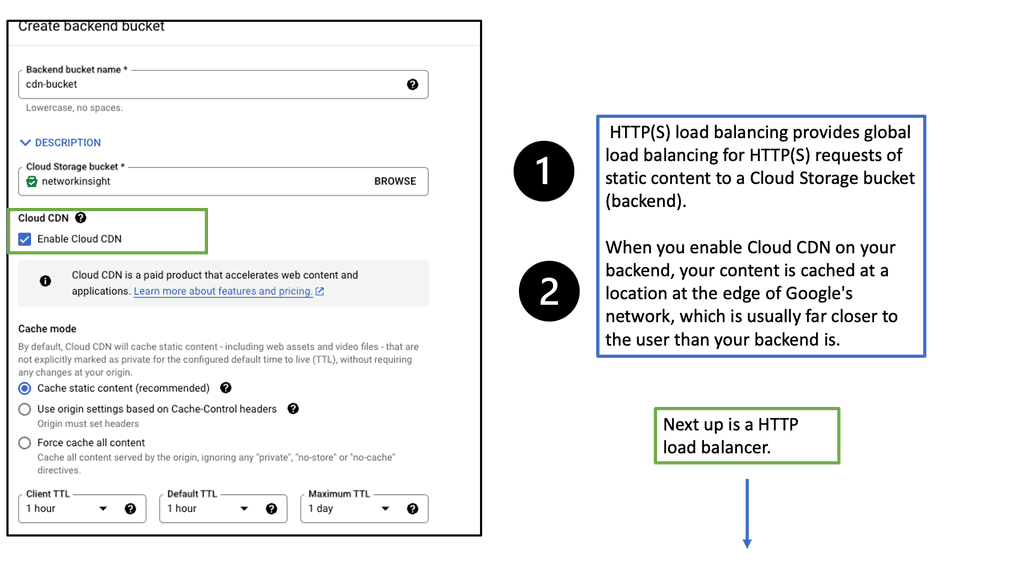
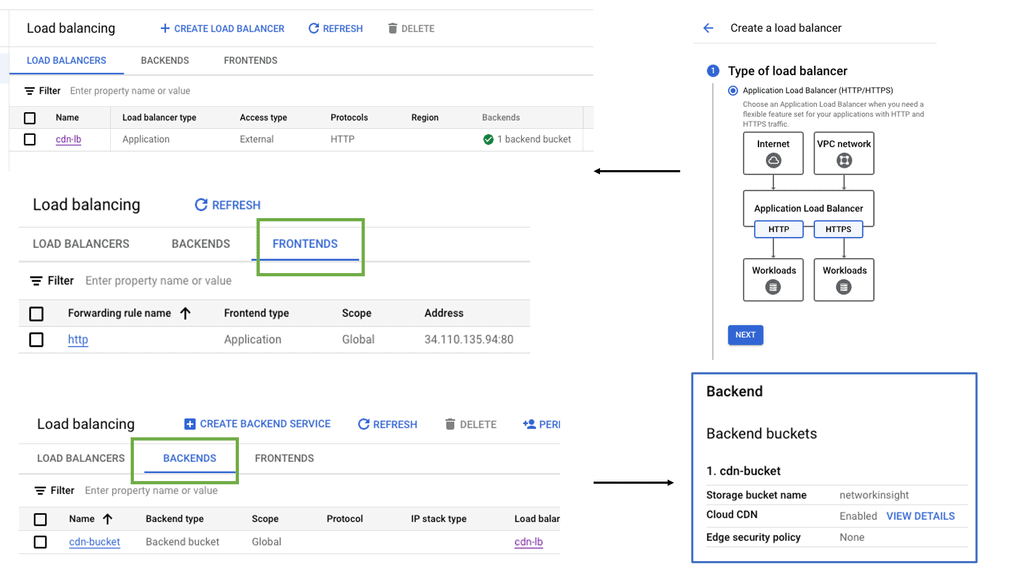
Google Cloud CDN
Understanding Cloud CDN
Cloud CDN is a globally distributed network of edge points of presence (PoPs) that caches your website’s static and dynamic content. By storing copies of your content closer to your users, Cloud CDN significantly reduces latency and improves response times. It leverages Google’s robust infrastructure to deliver content efficiently, making it an ideal choice for websites with a global audience.
Cloud CDN offers a range of features designed to optimize content delivery. Firstly, it automatically caches static content, such as images, CSS files, and JavaScript, reducing the load on your origin servers. This caching mechanism ensures that subsequent requests for the same content are served from the edge locations, minimizing the need to fetch data from the origin.
Additionally, Cloud CDN supports dynamic content caching, enabling it to cache personalized or frequently accessed content on the edge, improving response times. It also integrates seamlessly with other Google Cloud services, such as Load Balancing and Cloud Storage, providing a comprehensive solution for your website’s performance needs.
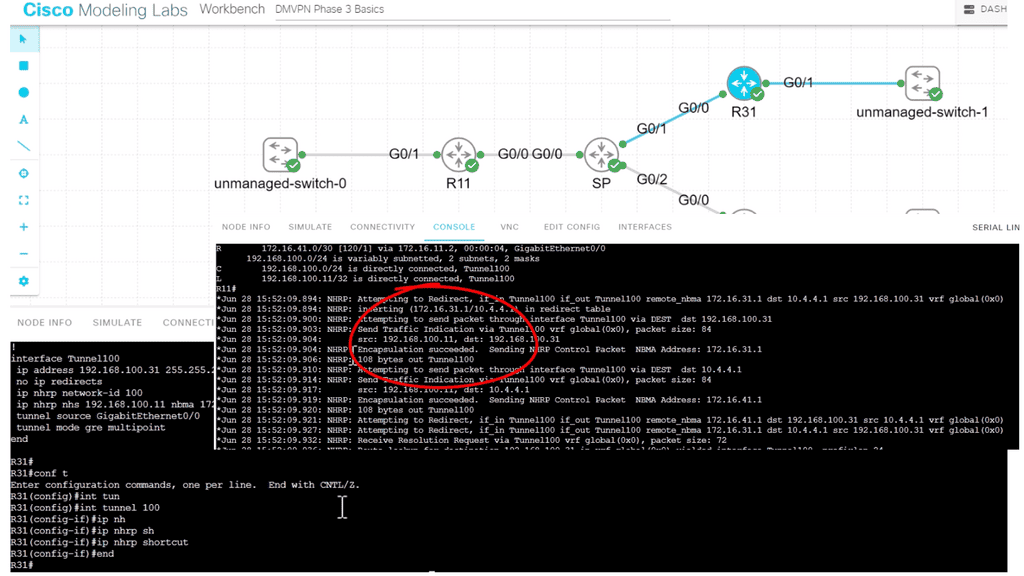
DMVPN. A layer 3 VPN over the WAN.
DMVPN can be used as an overlay with IPsec or GRE. It enables a VPN from the DMVPN hub and the spokes, creating a DMVPN network. Depending on the DMVPN phase, we will have different VPN characteristics and routing techniques. We started with DMVPN Phase 1, the traditional hub, and spoke to what is more widely used today, DMVPN Phase 3, which offers on-demand spoke-to-spoke tunnels.
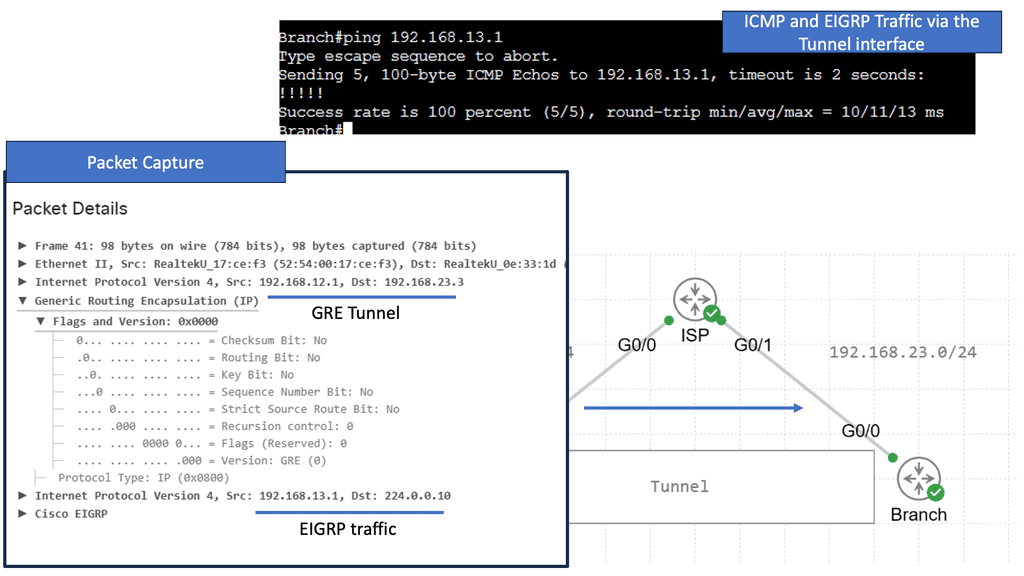
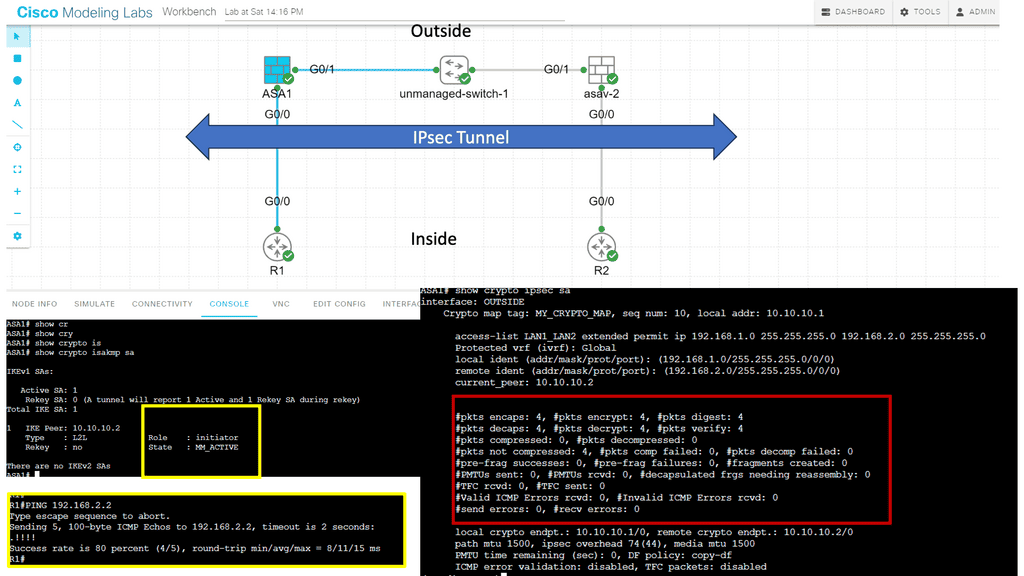
The screenshot from the lab guide below shows that we have R11 as the hub and R31 as the spoke. We are operating with DMVPN phase 3. We know this as we have a “Traffic Indication” message sent from R11 to the spokes. A “Traffic Indication” is core to DMVPN Phase 3 and is used when there has been spoken-to-spoke traffic.
The hub tells the spoke that there is a more optimal path and to go directly to the other spoke instead of going via the hub. Another key VPN configuration value for DMVPN Phase 3 is the command: Tunnel mode gre multipoint on the spokes. Both spokes and hubs use multipoint GRE instead of point-to-point GRE.
Back to basics with VPNOverview
Concepts of VPN
A VPN allows users to expand a private network across an untrusted network. The term “Virtual” emphasizes that a logical private connection virtually extends the private network. A VPN can be secure or insecure. We can use IPsec to secure VPNs. In addition, when IPsec VPNs are used, traffic will be protected to ensure that an observer cannot view the plaintext data.
Almost every operating system ships with an IPsec VPN client, and numerous hardware devices provide various IPsec VPN gateway functionality. As a result, IPsec VPNs are a popular choice now for secure connectivity over the Internet or for delivering secure communications over untrusted networks.
Concepts of IPSec
– IPsec (Internet Protocol Security) is a network security protocol that encrypts IP packets. It protects data communications between two or more computers by providing authentication and encryption. It is one of the world’s most widely used security protocols, as it is the de facto standard for protecting data in transit across the Internet. It also secures private networks, such as those used by corporations and government agencies.
– IPsec works by authenticating and encrypting each IP packet of a communication session. It uses two main protocols to provide this security: Authenticated Header (AH) and Encapsulated Security Payload (ESP). AH provides authentication and data integrity, while ESP includes encryption. The two protocols can be used together or separately to provide the desired level of security.
– IPsec can secure various communication protocols, including TCP, UDP, and ICMP. It is also used to protect mobile devices, such as smartphones, which require secure communication between them and the network they are attached to. IPsec also provides an additional layer of security by providing access control. This means that only authenticated users can access the data. This is especially important when protecting sensitive information and corporate data.
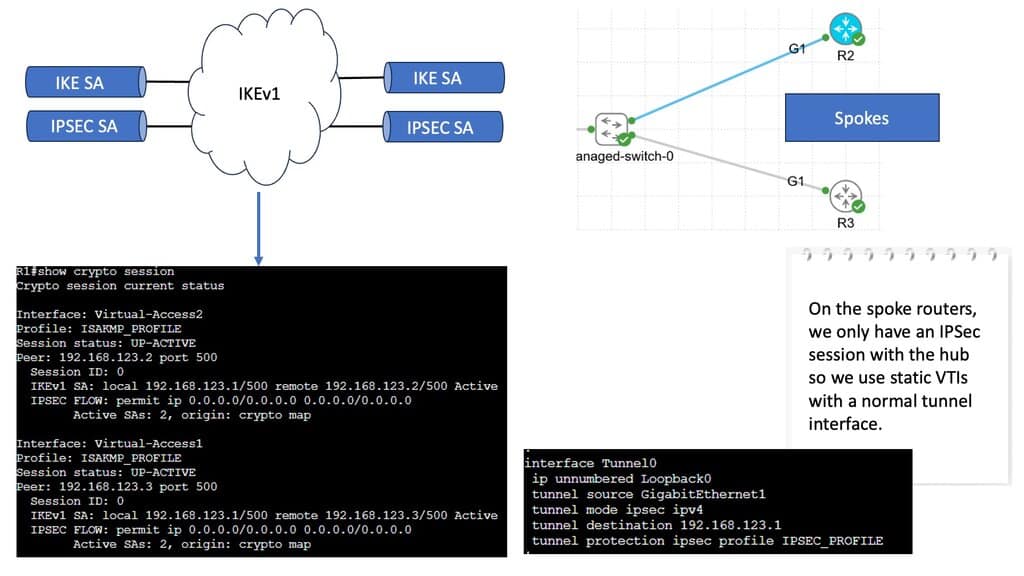
Concepts of IKEv1 vs IKEV2
IKEv1 and IKEv2 are two major versions of the Internet Key Exchange (IKE) protocol; both are used to create secure Virtual Private Networks (VPNs). IKEv1 was the original version, developed in 1998, and IKEv2 was released in 2005.
Both versions of IKE use the same cryptographic algorithms and protocols, but IKEv2 is the more secure version due to its additional features. For example, IKEv2 is capable of automatic re-keying, which IKEv1 does not support, and the IKEv2 protocol is implemented more structured and modularly than IKEv1. Additionally, IKEv2 has more advanced authentication methods, such as EAP and XAUTH, and supports the authentication of multiple peers.
IKEv2 is also more efficient than IKEv1, as it is designed to reduce the amount of data sent over the network. This helps to increase the speed of the VPN connection. Finally, IKEv2 is more resilient in the face of network issues and disruptions, as it supports the ability to reconnect automatically.
It is important to note that IKEv1 and IKEv2 have advantages and drawbacks. For example, IKEv1 is more straightforward to deploy and configure but is less secure than IKEv2. On the other hand, IKEv2 is more secure but may require more effort to set up.
When deciding between IKEv1 and IKEv2, the network’s security requirements and the VPN connection’s desired performance must be considered.
Layer 3 and Layer 2 VPNs
Firstly, for a VPNoverview, let’s start with the basics of Layer 2 and 3 VPNs. Layer 2 virtual private network: Frame Relay or ATM Permanent Virtual Circuits ( PVC ) utilize someone else’s public transport to build private tunnels with ( VC ) virtual circuits. A Virtual Private LAN Service ( VPLS ) network creates tunnels over the Multi-Protocol Label Switched ( MPLS ) core. Ethernet VLAN or QinQ is also an example of a Layer 2 VPN.
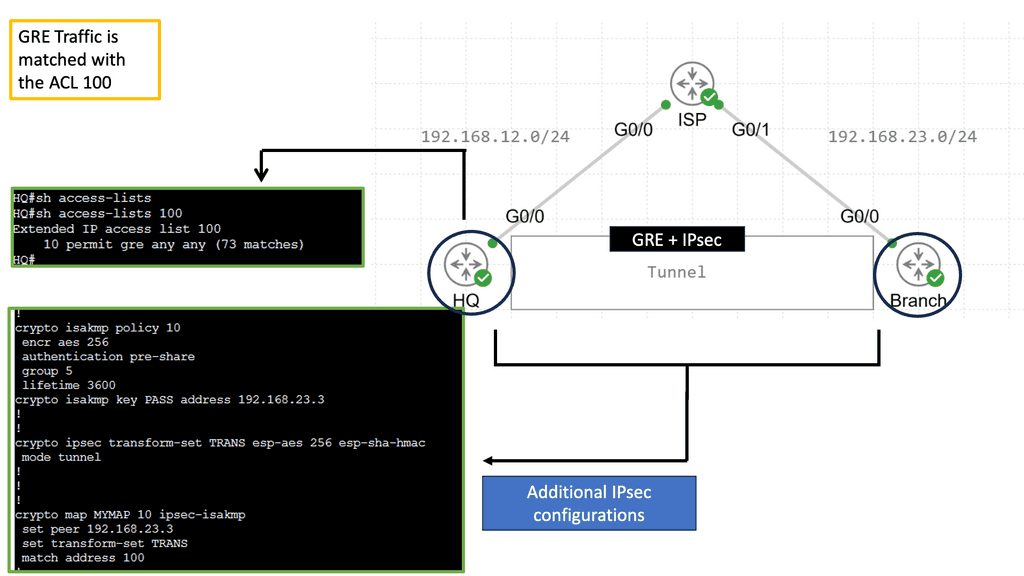
Layer 3 virtual private network: Generic Routing Encapsulation ( GRE ) tunnels and MPLS tunnels between Service providers and customers are examples of a Layer 3 VPN. Also, IP Protocol Security ( IPsec ) tunnels, which are the focus of this post, are an example of a Layer 3 VPN. The critical advantage of Layer 3 IPsec VPNs is the independence of the access method. You can establish a VPN if you establish IPv4 or IPv6 connectivity between two endpoints. VPNs do not require encryption, but encryption can take place if needed.
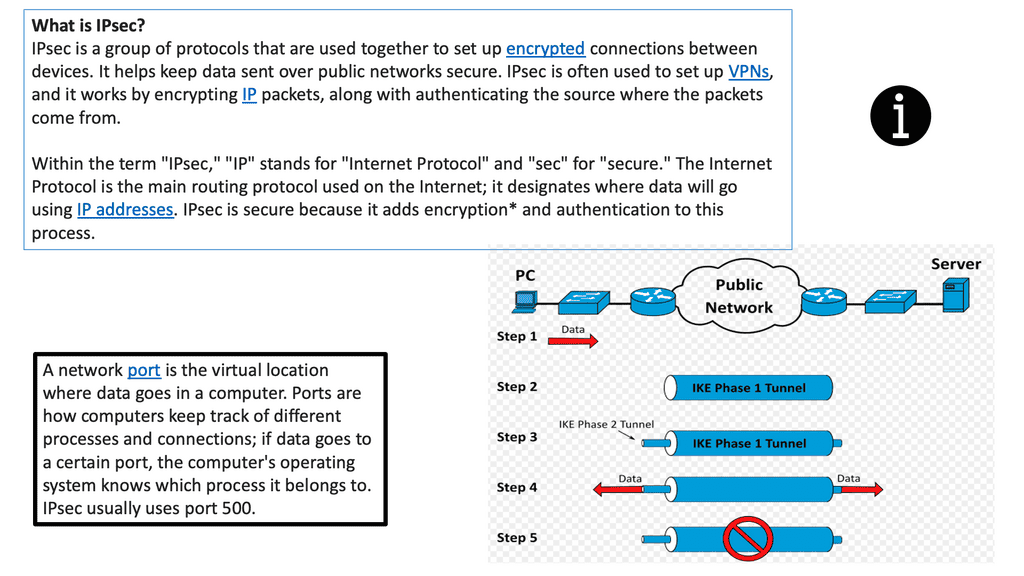
What is IP protocol security ( IPsec )?
IPsec is a protocol suite that provides security services for IP packets at the network layer. IPsec creates P2P associations between tunnel endpoints. Authenticates and encrypts packets. A broad term that encompasses the following features;
VPNoverview and encryption
In the next stage of this VPNoverivew, we will discuss encryption. VPNs encrypt packets with symmetric ciphers, e.g., DES, 3DES, and AES. Ciphers work with the concept of key exchange. In particular, the symmetric cipher key used to encrypt on one side is the same key to decrypt on another side. The same key is used at both endpoints.
Symmetric encryption contrasts with asymmetric encryption ( public key algorithms ), which utilizes separate public and private keys – one for encryption and another for decryption. The encryption key is known as the public key and is made public. The private key is kept secret and used for decryption.
Encryption takes plain text and makes it incomprehensible to unauthorized recipients. A matching key is required to decode the “incomprehensible” text into readable form. Decryption is the reverse of encryption. It changes the encrypted data back to plain text form. Encryption takes effect AFTER Network Address Translation ( NAT ) and Routing.
IPsec and ISAKMP
ASA uses ISAKMP negotiations and IPsec security features to establish and maintain tunnels for LAN-to-LAN and client-to-LAN VPNs. Tunnels are dynamically negotiated with control plane protocols, IKEv1/IKEv2, over UDP port 500. ISAKMP is a protocol that allows two VPN endpoints to agree and build IPsec security associations. ASA supports both ISAKMP version 1 and ISAKMP version 2. IKEv1 supports connections from legacy Cisco VPN clients, and IKEv2 supports the AnyConnect VPN client.
There are two main phases for tunnel establishment. The first phase objective is to establish and create a tunnel. The second Phase governs traffic within the tunnel. ISAKMP security associations govern tunnel establishment, and IPsec security associations govern traffic within the tunnel.
Key elements agreed upon in Phase 1 before endpoints proceed to Phase 2
| Phase 1 | Establishes-preliminary tunnel; used to protect later ISAKMP negotiation messages. Securely negotiate the encryption parameters for Phase 2. Phase 1 results in ISAKMP SA |
| Phase 2 | Creates the secure tunnel used to protect end-point data. IPSEC SA is used to transport protected traffic. Tunnel mode, AH** & ESP are negotiated. Phase 1 results in IPSEC SA |
**AH only supports authentication and is therefore rarely used for VPN. AH can be used in IPv6 OSPFv3 for neighbor authentication.
KEY POINT: Phase 1 is bidirectional, and Phase 2 uses two unidirectional messages. Phase 2 ESP and AH cannot be inspected by default ASA policies, which may become problematic for stateful firewalls. Phase 1 uses IKE UDP and UDP, which are inspected by default.
IKEv1 vs IKEv2
The main difference between IKEv1 and IKEv2 is authentication methods. With IKEv1, both endpoints must use the same authentication method; the encryption method must be symmetric.
IKEv2 is more flexible and does not need symmetric authentication types—it is possible to have certificates at one end and pre-shared keys at the other end.
IKE initiator sends all of the policies through a proposal. It’s up to the remote end to respond, check its policies, and agree if the receiving policies are acceptable. Policies are matched sequentially. The first match was utilized with an implicit deny at the bottom. IKEv2 allows multiple encryptions and asymmetric authentication types for a single policy.
**Two IKE modes: Main and aggressive mode*8
IKE has two modes of operation: Main Mode and Aggressive Mode.
Main Mode uses more ( 6 ) messages than Aggressive Mode and takes longer to process. It’s slower but protects the identity of communicating with peers.
Aggressive, useless ( 3 ) messages are quicker but less secure. Aggressive mode lets people know the endpoint identity, such as an IP address or Fully Qualified Domain Name ( FQDN ). It does not wait for the secure tunnel before you exchange your identity, allowing flexible authentication.
NAT-T and IPsec
IPsec uses ESP to encrypt data. It does this by encapsulating the entire inner TCP/UDP datagram within the ESP header. Like TCP and UDP, ESP is an IP protocol, but unlike TCP and UDP, it does not have any port information. No ports prevent ESP from passing through NAT / PAT devices. Nat-T auto-detects transit NAT / PAT devices and encapsulates IPsec traffic in UDP datagrams using port 4500. By encapsulating ESP into UDP, it now has port numbers, enabling the pass-through of PAT/NAT gateways.
ISAKMP does not have the same problem, as its control plane already works on UDP. As with any data encryption, it is always important to compare what is on the market to keep your data safe.
Guide: GetVPN Overview
GETVPN, or Group Encrypted Transport Virtual Private Network, is designed to provide secure communication over a public network infrastructure. It allows for creating a virtual private network (VPN) that enables secure communication between different locations or branches of an organization. Unlike traditional VPNs, GETVPN operates at the network layer, ensuring confidentiality, integrity, and authenticity.
Implementing GETVPN requires careful planning and configuration. The deployment process involves critical components such as Key Servers (KS), Group Members (GM), and Group Domain of Interpretation (GDOI). By carefully configuring these elements, organizations can establish a secure network architecture that aligns with their specific requirements. Proper key management and pre-shared keys are also critical aspects of GETVPN deployment.
We have 1 Key Server and 2 Group Members in the diagram below. A description of their roles and protocol used as follows:
Key Servers:
At the heart of GETVPN are the key servers responsible for generating and distributing encryption keys. All the devices within the group use these keys to encrypt and decrypt network traffic. Key Servers ensure that all network devices have synchronized encryption keys, maintaining a secure communication channel.
Group Members:
Group Members refer to the network devices that participate in the GETVPN network. These can be routers, switches, or even firewalls. Group Members establish secure tunnels with each other and exchange encrypted traffic. They utilize the encryption keys provided by the Key Servers to protect the confidentiality and integrity of the data.
Group Domain of Interpretation (GDOI):
GDOI is a protocol GETVPN uses to manage the encryption keys and maintain synchronization among the Key Servers and Group Members. It handles key distribution, rekeying, and critical management operations, ensuring that all devices within the group have up-to-date encryption keys.
OSPF is the routing protocol used on the WAN. The unmanaged switch in the middle represents a private WAN. OSPF is configured on the GM routers to advertise the loopback interfaces.
Below, we can verify that the GM has registered with the KS; we can see the access list used for encryption and the KEK/TEK policies, including the IPSec SA that the GM will use. Let’s take a closer look at IPSec SA. This will be the same for all GMs. 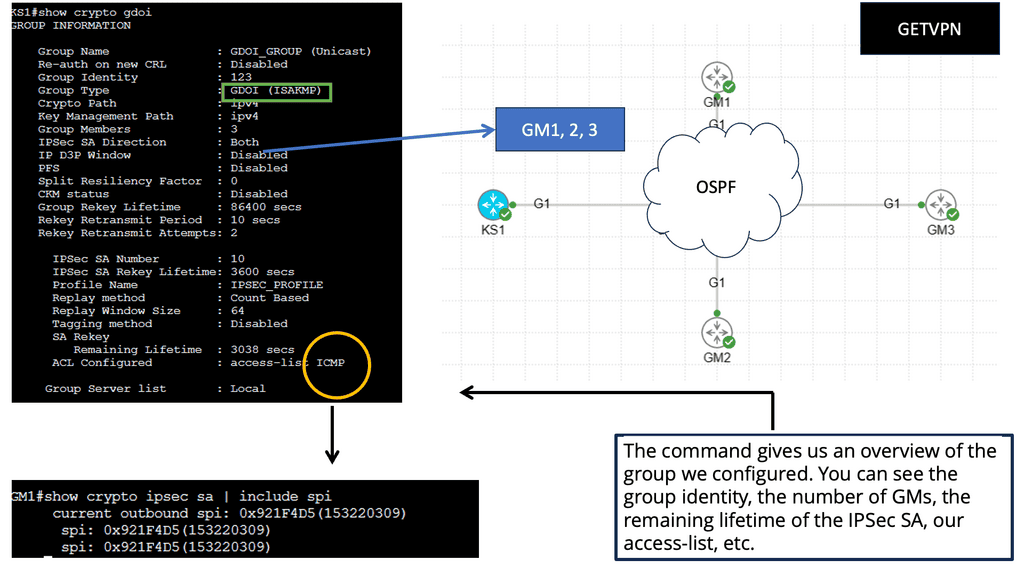
Summary: VPNOverview
In the digital age, where our lives are increasingly intertwined with the internet, safeguarding our online privacy has become more crucial than ever. One powerful tool that has gained significant popularity in recent years is the Virtual Private Network (VPN). In this blog post, we explored the world of VPNs, their benefits, and how they work to protect our online privacy.
What is a VPN?
A VPN, or Virtual Private Network, is a technology that creates a secure and encrypted connection between your device and the internet. It acts as a tunnel, routing your internet traffic through remote servers, effectively hiding your IP address, and encrypting your data. This provides a layer of privacy and security, making it difficult for anyone to track your online activities.
Benefits of Using a VPN
Enhancing Online Privacy: One of the primary reasons people use VPNs is to enhance their online privacy. By masking their IP addresses and encrypting their data, VPNs prevent third parties, such as hackers or government agencies, from monitoring their online activities. This is particularly important when using public Wi-Fi networks, where their data is more vulnerable to interception.
Accessing Geo-Restricted Content: Another significant advantage of VPNs is the ability to bypass geo-restrictions. With a VPN, you can connect to servers in different countries, effectively changing your virtual location. This allows you to access region-restricted content, such as streaming services, websites, or social media platforms that may otherwise be unavailable in your region.
How VPNs Work
Encryption and Tunnelling: When you connect to a VPN, your internet traffic is encrypted before it leaves your device. This encryption ensures that even if someone intercepts your data, it is unintelligible without the encryption key. Additionally, the tunneling aspect of VPNs ensures that your data is securely transmitted across the internet, protecting it from prying eyes.
VPN Protocols: VPNs use different protocols to establish secure connections. Some popular protocols include OpenVPN, IKEv2, and L2TP/IPsec. Each protocol has its strengths and weaknesses, such as security level, speed, or compatibility with different devices. Choosing a VPN provider that supports reliable and secure protocols is essential.
Conclusion:
In conclusion, VPNs have become vital tools in safeguarding our online privacy. By encrypting our data, masking our IP addresses, and accessing geo-restricted content, VPNs provide a robust layer of security and privacy in the digital realm. Whether you’re concerned about protecting sensitive information or want to enjoy a more open and unrestricted internet experience, using a VPN is a smart choice.
- DMVPN - May 20, 2023
- Computer Networking: Building a Strong Foundation for Success - April 7, 2023
- eBOOK – SASE Capabilities - April 6, 2023







[…] Best VPN Canada Sustaining a reliable connection is also very important in determination of methods fast a VPN will go. It will always be advisable to pick a VPN server with the least level of data packet loss and when feasible %. Your firewall environment ought to be done in a manner that will allow your VPN to circulate unrestrictedly. Even though the firewall may not be limiting your VPN, it could be slowing the CPU velocity when scrutinizing all network packets. It is additionally essential to use a good internet provider to maintain a reliable connection. […]
[…] Best VPN Sustaining a reliable connection is also essential in perseverance of methods fast a VPN may go. It is always advisable to pick a VPN server using the least quantity of data packet loss and if possible %. Your firewall environment should be done in a way that allows your VPN to circulate unrestrictedly. Even though the firewall will not be limiting your VPN, it might be slowing the CPU velocity when scrutinizing all network packets. It is also essential to utilize a good internet provider to maintain a reliable connection. […]
[…] Best VPN Fingerprints, like endeavours to detect VPN usage, are tough to bypass because of the period of sending deals from your consumer to the website and from your website to the user’s IP address (without taking into account obstructing only particular inbound requests). You are able to cheat one or two checks, but you can’t be sure that a whole new “nightmare” won’t show up overnight. This is why you require a distant workplace so terribly, and also a clear virtual machine. So it’s the best recommendation you may get right now. The cost of such a remedy starts from just $40 a month. But take note you ought to pay out with Bitcoin only. […]