Cisco Secure Firewall with SASE Cloud
In today's digital era, network security is of paramount importance. With the rise of cloud-based services and remote work, businesses require a comprehensive security solution that not only protects their network but also ensures scalability and flexibility. Cisco Secure Firewall with SASE (Secure Access Service Edge) Cloud is a cutting-edge solution that combines the robustness of firewall protection with the agility of cloud-based security services. In this blog post, we will delve into the features and benefits of Cisco Secure Firewall with SASE Cloud.
Cisco Secure Firewall is an advanced network security solution designed to safeguard organizations from cyber threats. Built on industry-leading technology, it provides next-generation firewall capabilities, intrusion prevention, and application control. With granular security policies, deep visibility, and advanced threat intelligence, Cisco Secure Firewall empowers businesses to protect their networks from internal and external threats effectively.
SASE (Secure Access Service Edge) is a transformative approach to network security and connectivity. By converging networking and security functions into a unified cloud-based service, SASE offers organizations scalable and flexible security solutions. Cisco Secure Firewall with SASE Cloud takes advantage of this architecture, providing businesses with integrated security services that are delivered from the cloud. This enables seamless scalability, simplified management, and enhanced protection against evolving threats.
Cloud-Native Firewall: Cisco Secure Firewall with SASE Cloud leverages the power of cloud-native architecture, enabling organizations to easily scale their security infrastructure based on demand. It ensures consistent security policies across various locations and eliminates the need for hardware-based firewalls.
Advanced Threat Protection: With integrated threat intelligence and advanced analytics, Cisco Secure Firewall with SASE Cloud offers robust protection against sophisticated threats. It provides real-time threat detection and prevention, ensuring that businesses stay one step ahead of cybercriminals.
Simplified Management: The centralized management console allows organizations to effortlessly manage their security policies and configurations. From a single interface, administrators can efficiently deploy and enforce security policies, reducing complexity and enhancing operational efficiency.
As organizations continue to embrace digital transformation, the network landscape is constantly evolving. Cisco Secure Firewall with SASE Cloud future-proofs your network by providing a scalable and adaptable security solution. Its cloud-native architecture and integration with SASE enable businesses to stay agile and easily adapt to changing security requirements, ensuring long-term protection and resilience.
Matt Conran
Highlights: Cisco Secure Firewall with SASE Cloud
Understanding the Cisco Secure Firewall
Cisco Secure Firewall is a cutting-edge network security appliance that provides advanced threat protection, secure connectivity, and simplified management. It combines next-generation firewall capabilities with intrusion prevention, application visibility and control, and advanced malware protection. With its comprehensive suite of security features, it offers a multi-layered defense against a wide range of cyber threats.
Key Cisco Secure Firewall Features:
– Advanced Threat Protection: The Cisco Secure Firewall employs advanced intelligence to detect and prevent sophisticated attacks, including malware, ransomware, and zero-day exploits. Its integrated security technologies work in tandem to identify and mitigate threats in real-time, ensuring your network infrastructure’s highest level of protection.
– Secure Connectivity: The Cisco Secure Firewall enables secure remote access and site-to-site connectivity with built-in VPN capabilities. It establishes encrypted tunnels, allowing authorized users to access network resources from anywhere while ensuring data confidentiality and integrity.
– Application Visibility and Control: Gaining visibility into network traffic and effectively managing application usage is crucial for optimizing network performance and ensuring security. The Cisco Secure Firewall offers granular application control, allowing administrators to define policies and prioritize critical applications while restricting or blocking unauthorized ones.
**Broken Firewall Rules**
One-third of your firewall rules are broken. You can use the Cisco AI Assistant for Security to identify and report policies, augment troubleshooting, and automate policy lifecycle management with the Cisco AI Assistant for Security. Also, take back control of your encrypted traffic and application environments. Cisco Talos lets you see and detect more across your infrastructure while ensuring security resilience across billions of signals.
**Advanced Clustering & HA**
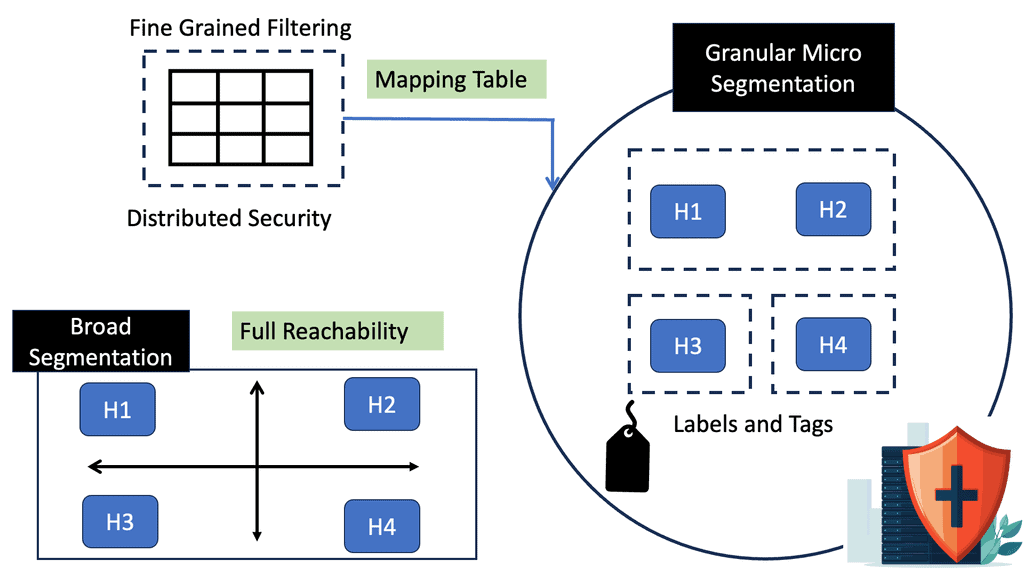
This enabled you to drive efficiency at scale. Secure Firewall’s advanced clustering, high availability, and multi-instance capabilities allow you to scale, be reliable, and be productive. Finally, by integrating network, microsegmentation, and app security, Secure Firewall makes zero-trust achievable and cost-effective. It automates access and anticipates what comes next.
Knowledge Check: Cisco’s Firewalling
Cisco integrated its original Sourcefire’s next-generation security technologies into its existing firewall solutions, the Adaptive Security Appliances (ASA). In that early implementation, Sourcefire technologies ran as a separate service module. Later, Cisco designed new hardware platforms to support Sourcefire technologies natively.
They are named Cisco Firepower, later rebranded as Cisco Secure Firewall, which is the current implementation of Firewalling. In the new implementation, Cisco converges Sourcefire’s next-generation security features, open-source Snort, and ASA’s firewall functionalities into a unified software image. This unified software is called the Firepower Threat Defense (FTD). After rebranding, this software is now known as the Cisco Secure Firewall.
Example Security Technology: IPS IDS
Understanding Suricata
Suricata is an open-source network threat detection engine that offers high-performance intrusion detection and prevention capabilities. Built with speed, scalability, and robustness, Suricata analyzes network traffic and detects various threats, including malware, exploits, and suspicious activities. Its multi-threaded architecture and rule-based detection mechanism make it a formidable weapon against cyber threats.
Suricata boasts an impressive array of features that elevate its effectiveness in network security. Suricata covers various security needs, from protocol analysis and content inspection to file extraction and SSL/TLS decryption. Its extensive rule set allows for fine-grained control over network traffic, enabling tailored threat detection and prevention. Additionally, Suricata supports various output formats, making it compatible with other security tools and SIEM solutions.
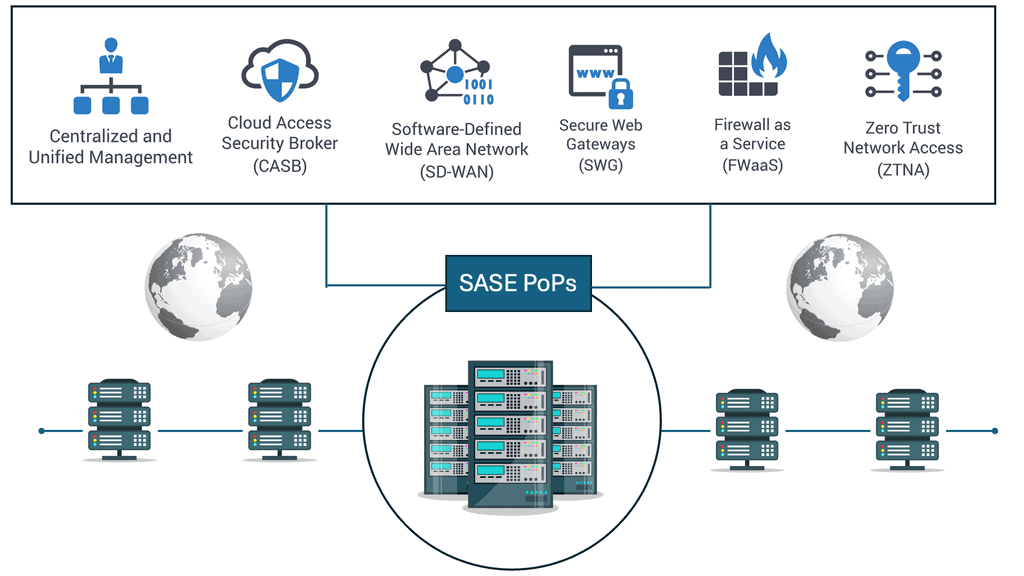
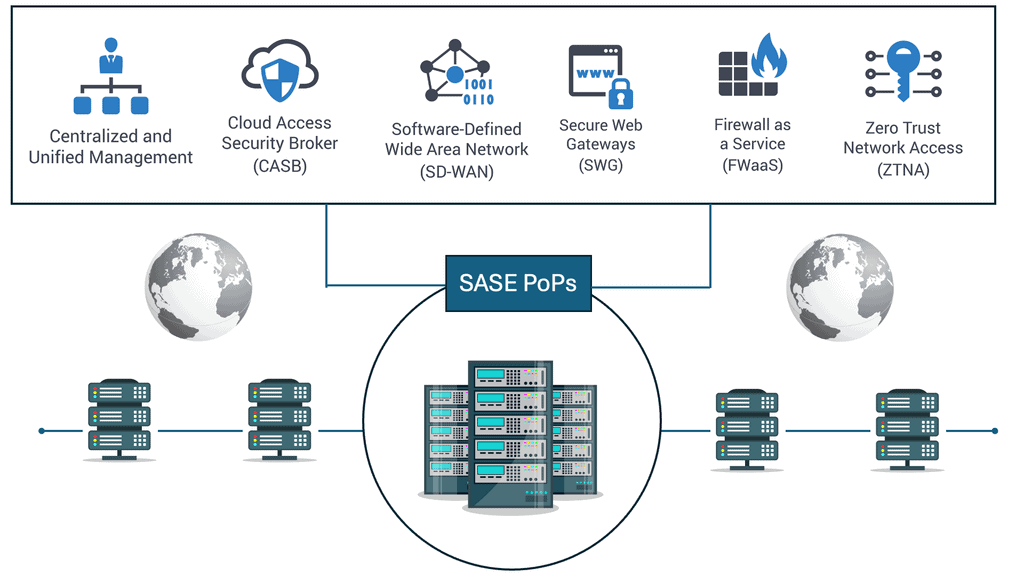
Understanding SASE Cloud
Cisco SASE Cloud, short for Secure Access Service Edge Cloud, is a comprehensive networking and security platform that combines wide area networking (WAN) capabilities with robust security features. It offers a unified solution for remote access, branch connectivity, and cloud security, all delivered from the cloud. This convergence of networking and security into a single cloud-native platform allows organizations to simplify their infrastructure, reduce costs, and enhance agility.
SASE Cloud Key Points:
Enhanced Security: One of Cisco SASE Cloud’s standout features is its advanced security capabilities. By leveraging a combination of next-generation firewalls, secure web gateways, data loss prevention, and other security services, it provides comprehensive protection against cyber threats. With SASE Cloud, organizations can ensure secure access to applications and data from anywhere, anytime, without compromising security.
Scalability and Flexibility: Cisco SASE Cloud offers unmatched scalability and flexibility. As an organization grows, SASE Cloud can quickly adapt to evolving needs. Whether it’s adding new branches, onboarding remote employees, or expanding into new markets, the cloud-native architecture of SASE Cloud enables seamless scalability without the need for extensive infrastructure investments.
Simplified Management: Managing complex networking and security infrastructure can be daunting for IT teams. However, Cisco SASE Cloud simplifies this process by centralizing management and providing a single pane of glass for visibility and control. This streamlined approach allows IT teams to monitor and manage network traffic efficiently, apply security policies, and troubleshoot issues, improving operational efficiency.
Secure Access Anywhere & Anytime
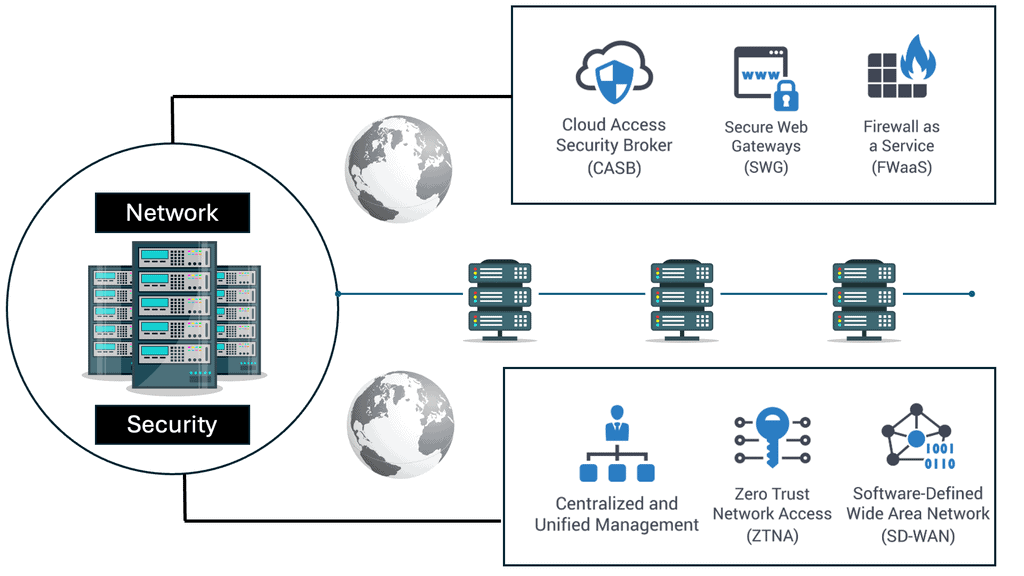
Converged Networking and Security: Cisco SASE combines networking and security functions, such as secure web gateways, firewalls, and data loss prevention, into a single solution. This convergence eliminates the need for multiple standalone appliances, reducing complexity and improving operational efficiency.
Cloud-Native Architecture: Built on a cloud-native architecture, Cisco SASE leverages the scalability and flexibility of the cloud. This enables organizations to dynamically adapt to changing network demands, scale their resources as needed, and integrate new security services without significant infrastructure investments.
Enhanced User Experience and Security: With Cisco SASE, users can enjoy a seamless and secure experience regardless of location or device. Cisco SASE protects users and data from threats through its integrated security capabilities, including zero-trust network access and secure web gateways, ensuring a safe and productive digital environment.
Related: For additional pre-information, you may find the following helpful:
Evolution of the Network Security
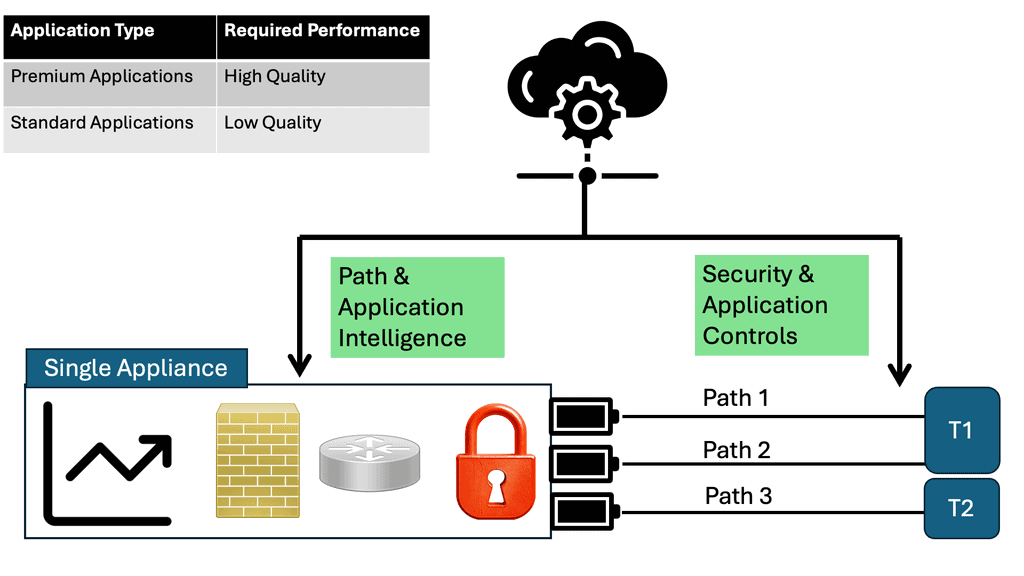
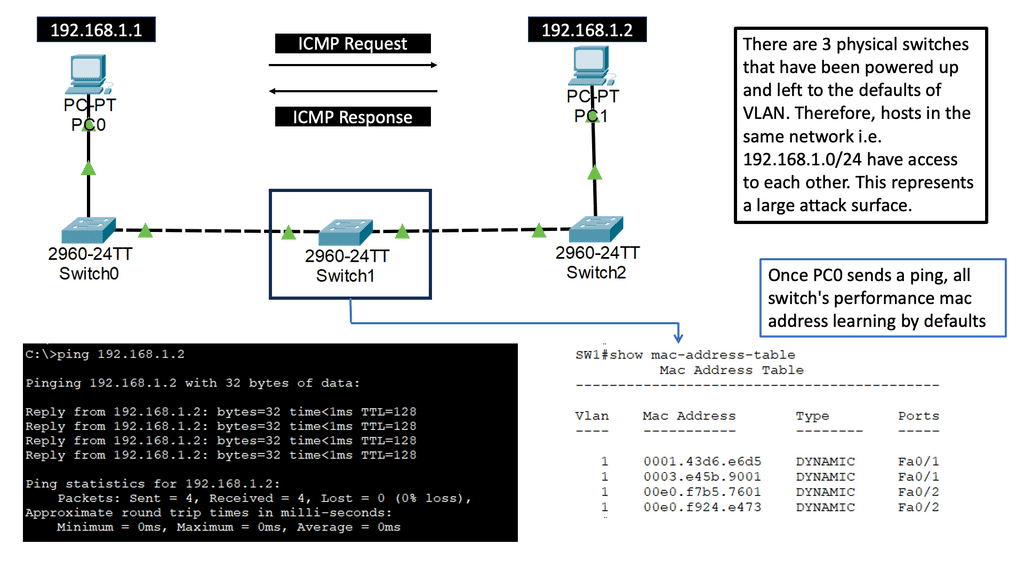
In the past, network security was typically delivered from the network using the Firewall. However, these times, network security extends well beyond just firewalling. We now have different points in the infrastructure that we can use to expand our security posture while reducing the attack surface.
You would have commonly heard of Cisco Umbrella Firewall and SASE, along with Cisco Secure Workload security, which can be used with your Cisco Secure firewall, which is still deployed at the network’s edge. Unfortunately, you can’t send everything to the SASE cloud.
You will still need an on-premise firewall, such as the Cisco Secure Firewall, that can perform standard stateful filtering, intrusion detection, and threat protection. This post will examine the Cisco Secure Firewall and its integration with Cisco Umbrella via the SASE Cloud. Firstly, let us address some basics of firewalling.
A. Redesigning Traditional Security:
Let’s examine the evolution of network security before we get into some inbound and outbound traffic use cases. Traditionally, the Firewall was placed at the network edge, acting as a control point for the network’s ingress/egress point. The Firewall was responsible for validating communications with rule sets and policies created and enforced at this single point of control to ensure that desired traffic was allowed into and out of the network and undesirable traffic was prevented. This type of design was known as the traditional perimeter approach to security.
B: Numerous Firewalling challenges:
Today, branch office locations, remote employees, and increasing use of cloud services drive more data away from the traditional “perimeter,” The cloud-first approach completely bypasses the conventional security control point.
Further, the overwhelming majority of business locations and users also require direct access to the Internet, where an increasing prevalence of cloud-based critical applications and data now lives. As a result, applications and data become further de-centralized, and networks become more diverse.
C: Conventional Appliance Sprawl:
This evolution of network architectures has dramatically increased our attack surfaces and did the job of protecting more complicated ones. So, we started to answer this challenge with point solutions. Typically, organizations have attempted to address these challenges by adding the "best" point security solution to address each new problem as it emerges.
Because of this approach, we have seen tremendous device sprawl. Multiple security products from different vendors can pose significant management problems for network security teams, eventually leading to complexity and blind spots.
Consequently, our "traditional" firewall devices are being augmented by a mixture of physical and virtual appliances—some are embedded into the network. In contrast, others are delivered as a service, host-based, or included within public cloud environments. Regardless of the design, you will stall inbound and outbound traffic to protect.Matt Conran
**Basics of Firewalling**
A firewall is an entity or obstacle deployed between two structures to prevent fire from spreading from one system to another. This term has been taken into computer networking, where a firewall is a software or hardware device that enables you to filter unwanted traffic and restrict access from one network to another. The Firewall is a vital network security component in securing network infrastructure and can take many forms. For example, we can have a host-based or network-based Firewall.
Firewalling Types:
A. Host-based Firewall
A host-based firewall service is installed locally on a computer system. In this case, the end user’s computer system takes the final action—to permit or deny traffic. Every operating system has some Firewall. It consumes the resources of a local computer to run the firewall services, which can impact the other applications running on that particular computer. Furthermore, in a host-based firewall architecture, traffic traverses all the network components and can consume the underlying network resources until the traffic reaches its target.
B. Network-based Firewall
On the other hand, a network-based firewall can be entirely transparent to an end user and is not installed on the computer system. Typically, you deploy it in a perimeter network or at the Internet edge where you want to prevent unwanted traffic from entering your network. The end-user computer system remains unaware of any traffic control by an intermediate device performing the filtering. In a network-based firewall deployment, you do not need to install additional software or daemon on the end-user computer systems. However, it would help if you used both firewall types for a defense-in-depth approach.
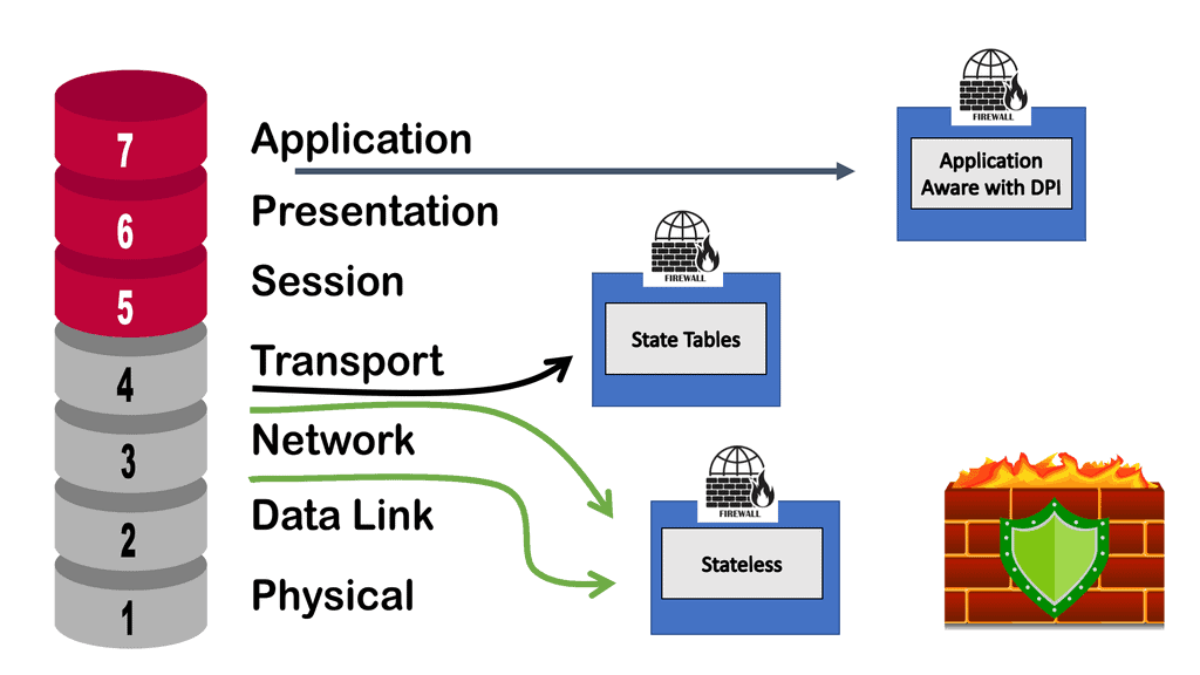
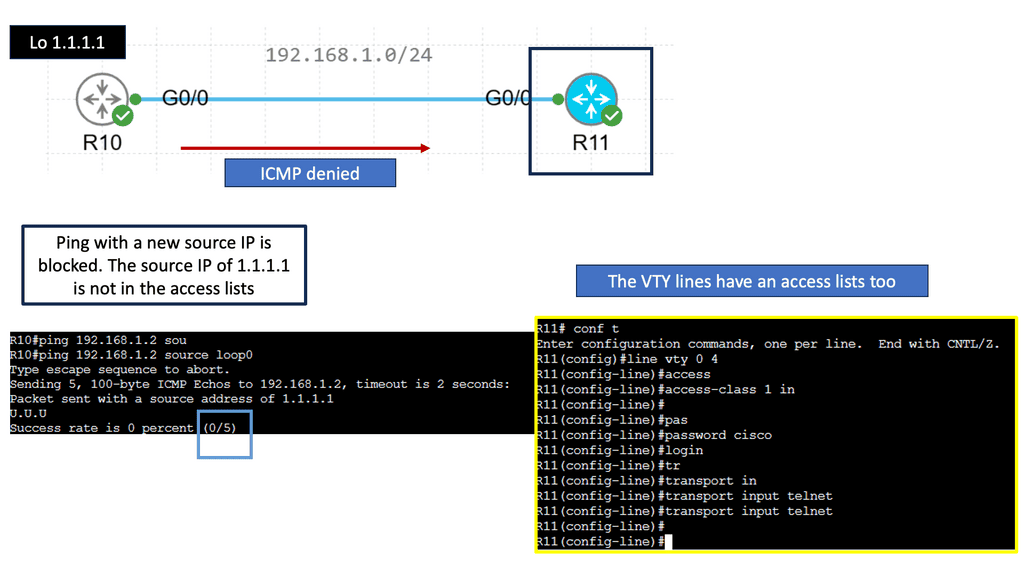
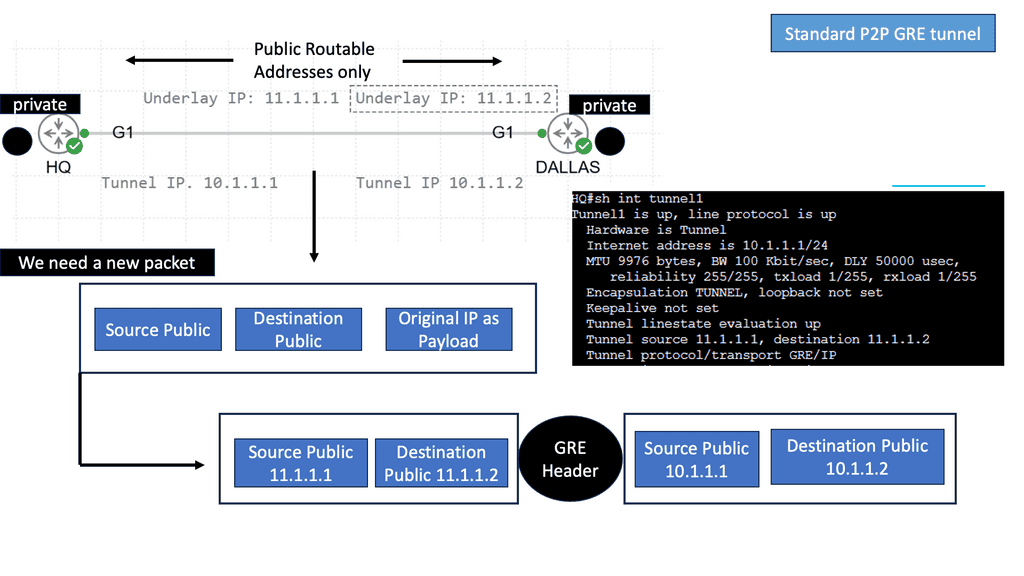
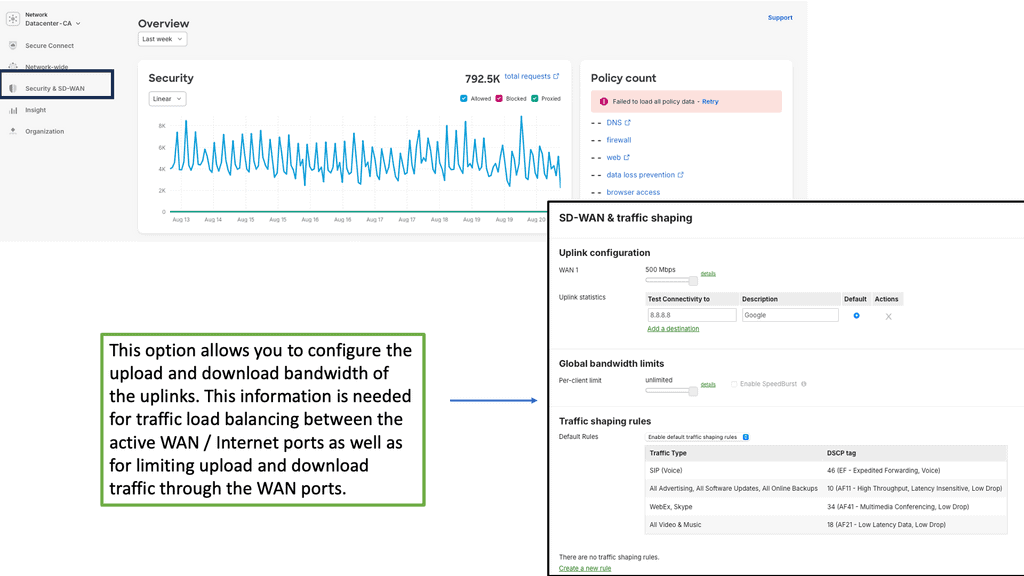
The early generation of firewalls could allow or block packets only based on their static elements, such as a packet’s source address, destination address, source port, destination port, and protocol information. These elements are also known as the 5-tuple.
Example Technology Cisco Packet Filter
### Implementing Packet Filtering in Your Network
To effectively implement packet filtering, it’s crucial to have a clear understanding of your network architecture and traffic patterns. Begin by identifying the critical assets that need protection and the types of traffic that should be allowed. Develop a detailed access list, considering both inbound and outbound traffic.
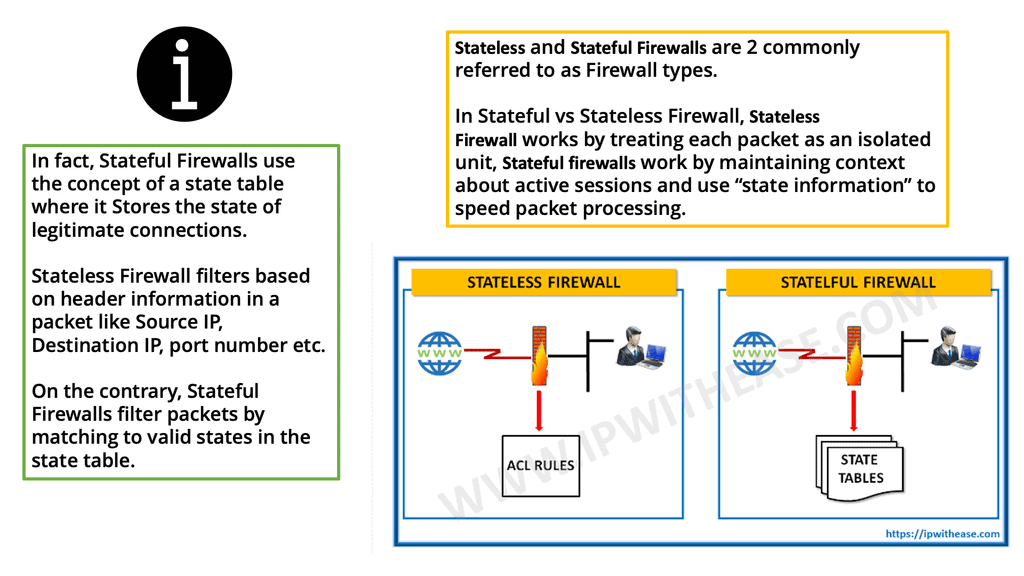
C. Stateless Firewalling
When an early-generation firewall examined a particular packet, it was unaware of any prior packets that passed through it because it was agnostic of the Transmission Control Protocol (TCP) states that would have signaled this. Due to the nature of its operation, this type of Firewall is called a stateless firewall.
A stateless firewall is unable to distinguish the state of a particular packet. So, for example, it could not determine if a packet is part of an existing connection, trying to establish a legitimate new connection, or whether it is a manipulated, rogue packet. We then moved to a stateful inspection firewall and an application-aware form of next-generation firewalling.
D. Stateful Firewaling
The stateful inspection examines the TCP and UDP port numbers, while an application-aware firewall examines Layer 7. So now we are at a stage where the Firewall does some of everything, such as the Cisco Secure Firewall.
**Firewalling Use Cases**
1.Inbound Use case
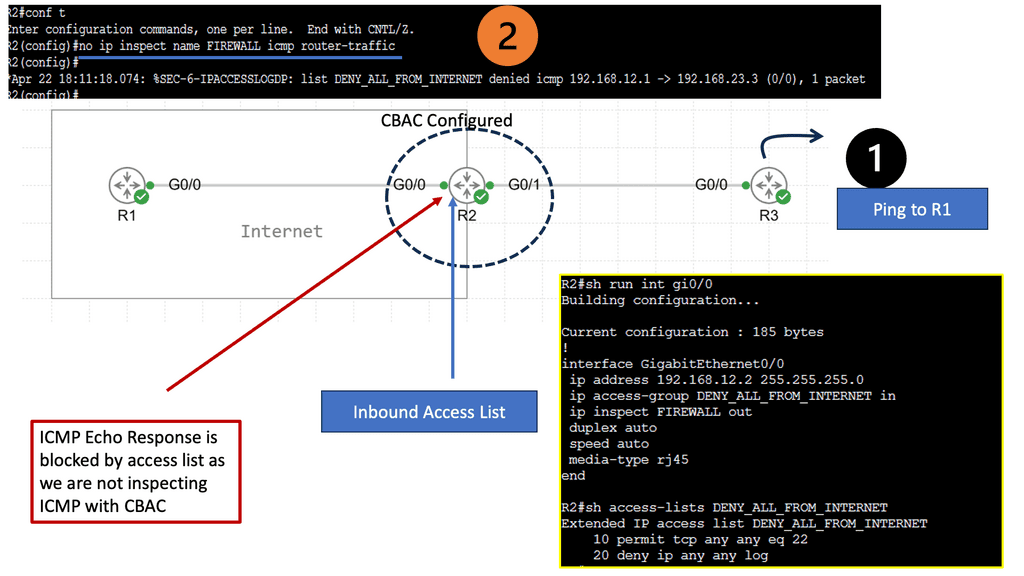
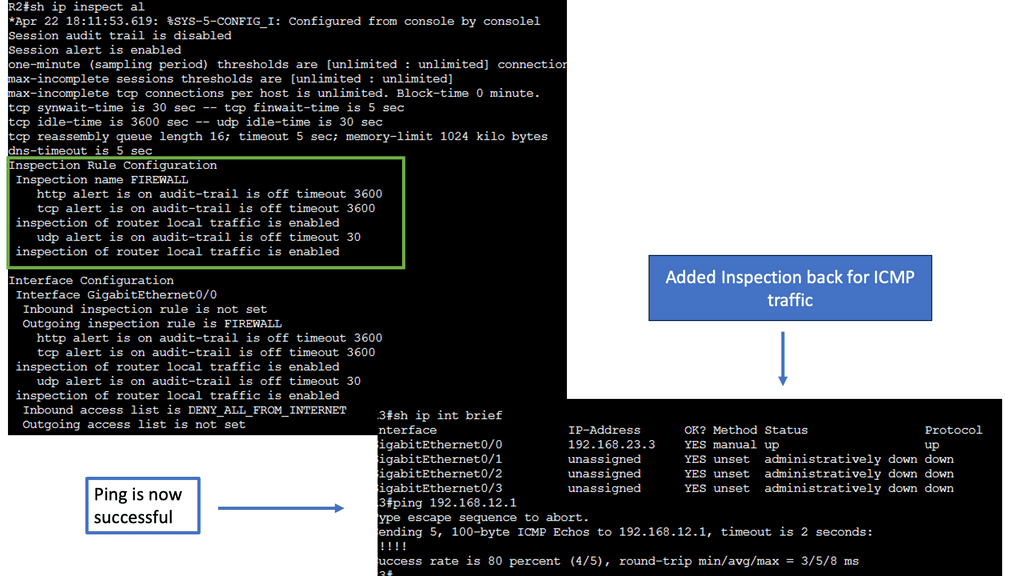
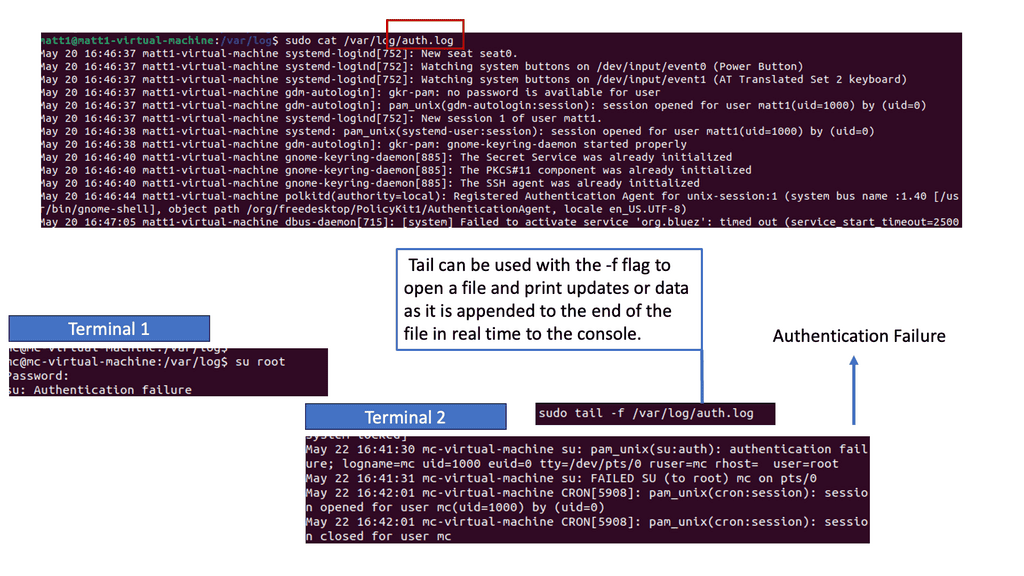
The Firewall picks up every packet, looks at different fields, examines for signatures that could signal an attack is in process, and then re-packs and sends the packet out its interfaces. Still, the technique is relevant. It tracks inbound traffic to tell if someone outside or inside is accessing the private applications you want to keep secure. So, looking at every packet is still relevant for the inbound traffic use case.
While everything is encrypted these days, you need to decrypt traffic to gain security value. Deep Packet Inspection (DPI) is still very relevant for inbound traffic. So, we will continue to decrypt inbound traffic for complete application threat protection with the hope of minimal functional impact.
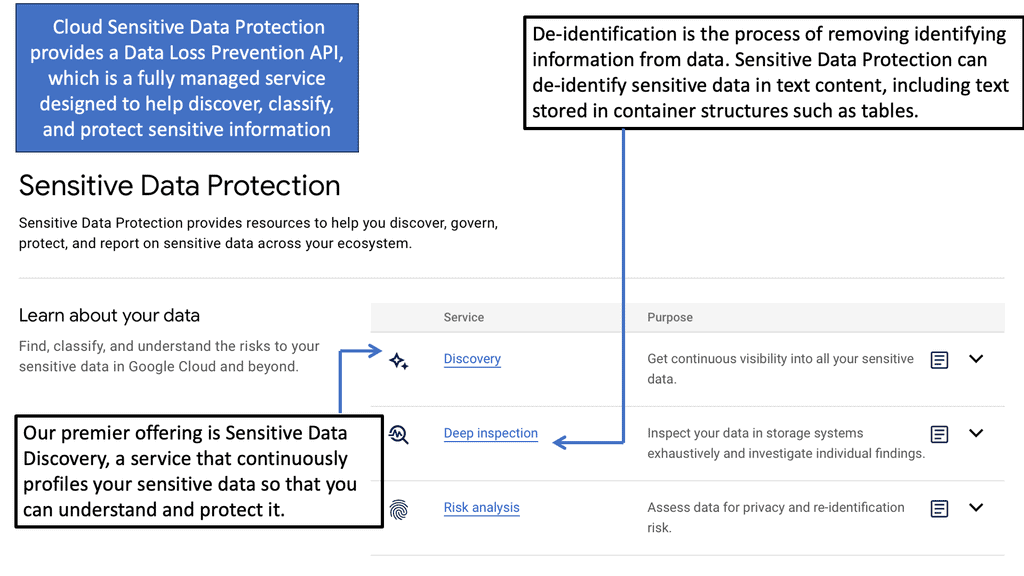
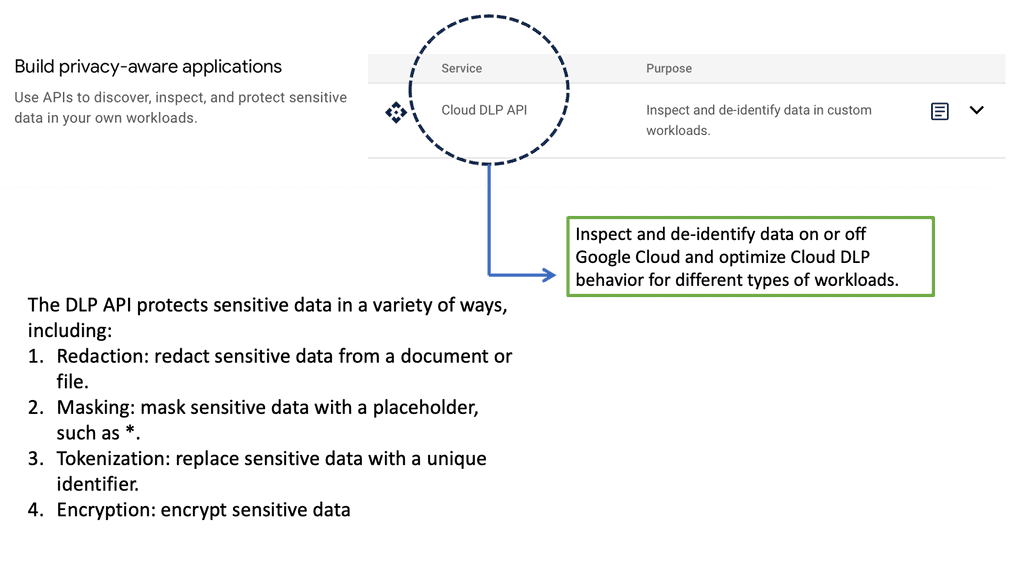
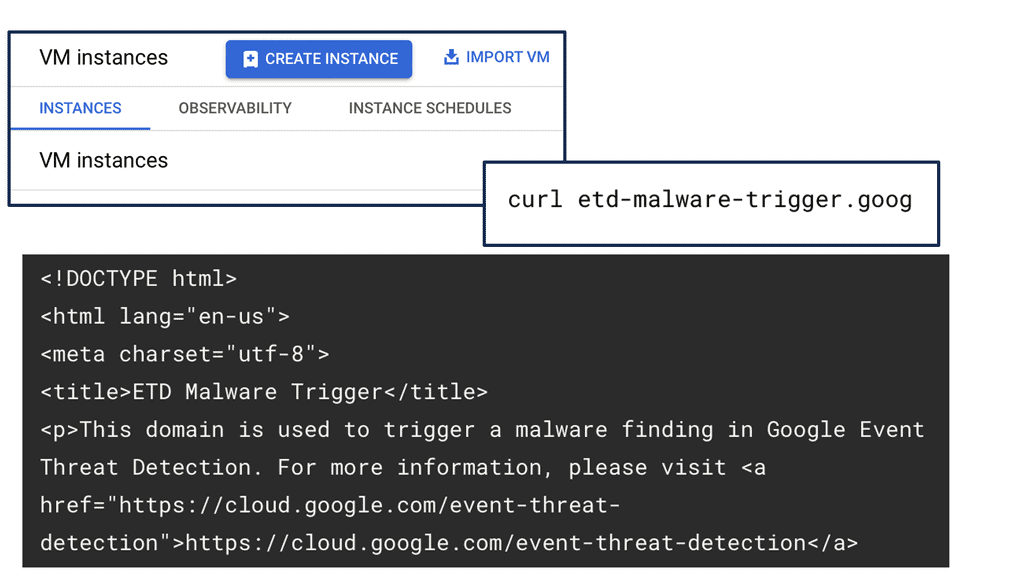
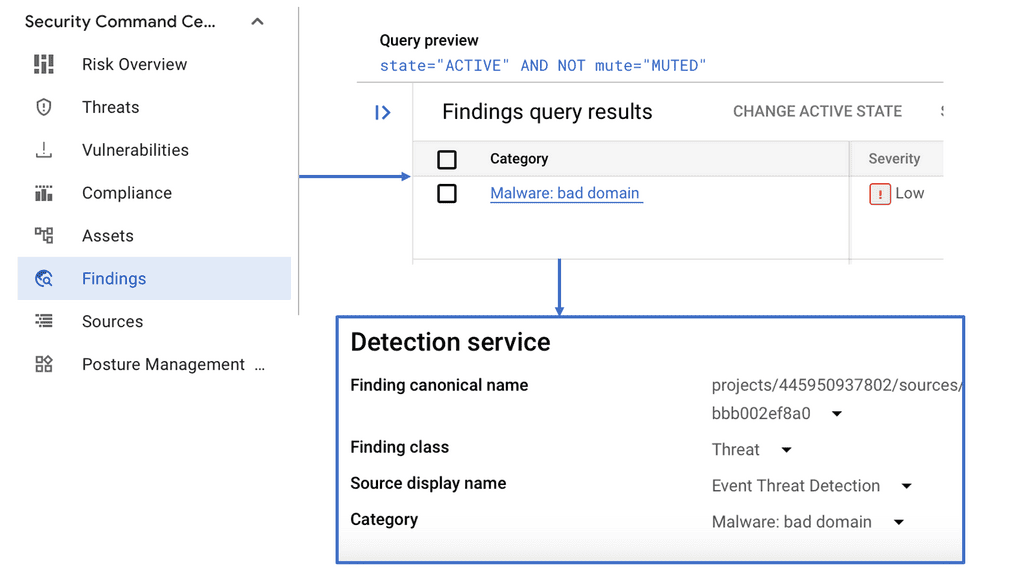
Example Technology: Sensitive Data Protection with Google Cloud
2.Outbound Use Case
Then, we need to look at outbound traffic. Here, things have changed considerably. Some users need to catch up to a firewall and then go to applications hosted outside the protection of your on-premise security stack and network. These are applications in the cloud, such as SaaS applications, that do not like when the network devices in the middle interfere with the traffic.
Therefore, applications such as Office365 make an effort with their design to reduce the chances of the potential of any network and security device from peeking into their traffic. For example, you could have mutual certificate authentication with the service in the cloud. So, there are a couple of options here besides the traditional DPI use case for inbound traffic use case.
**Improving Security: Understanding the network**
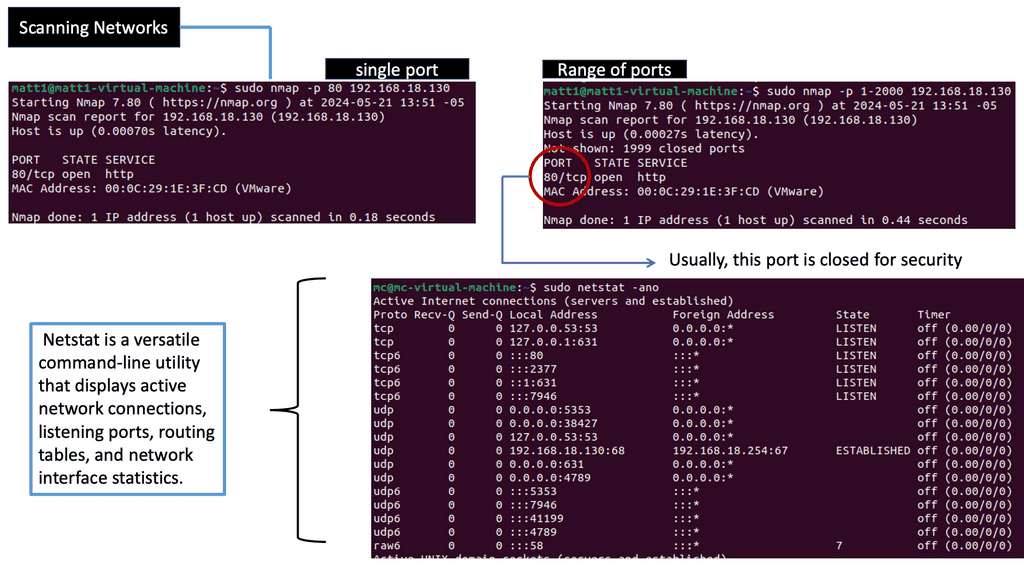
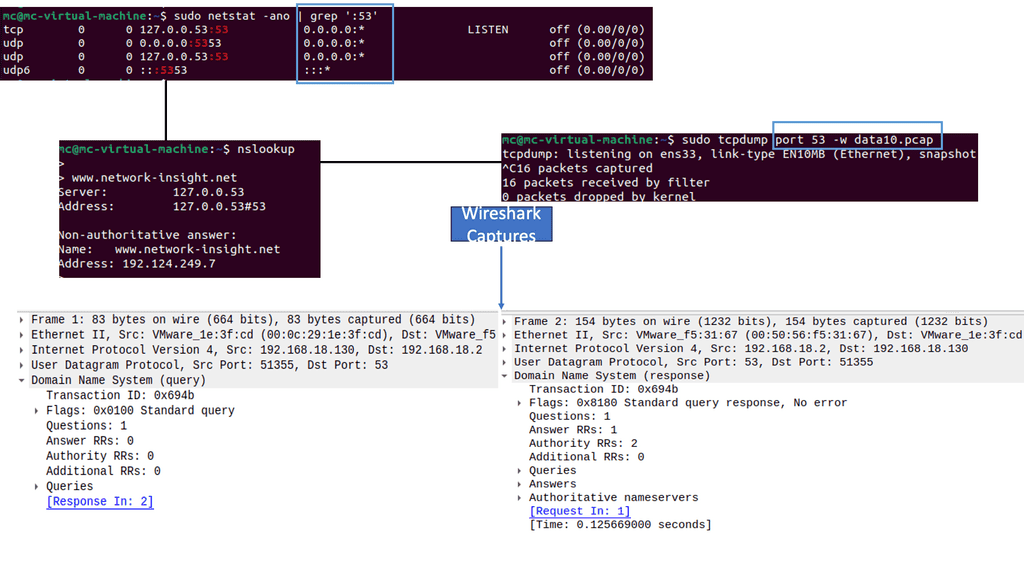
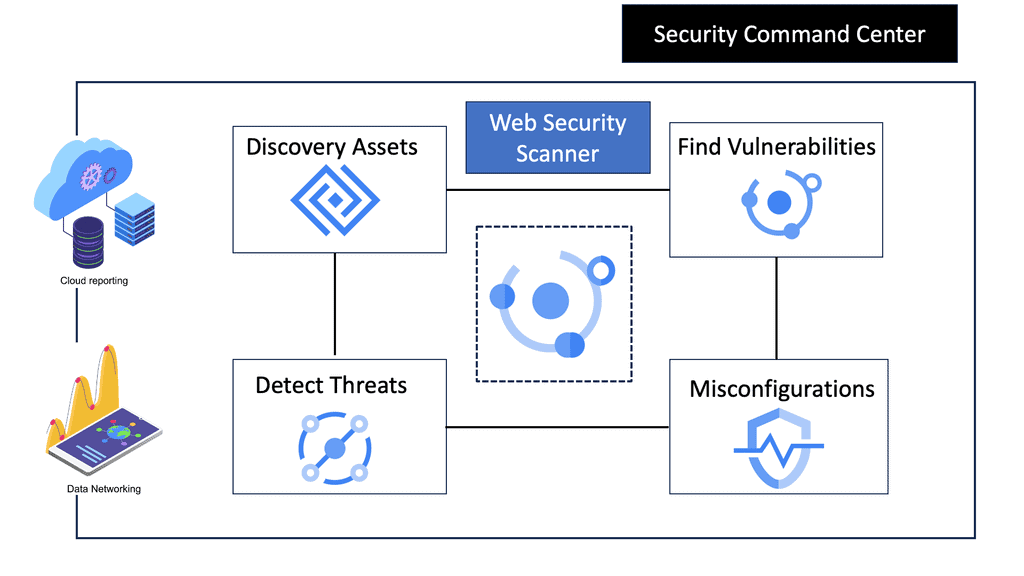
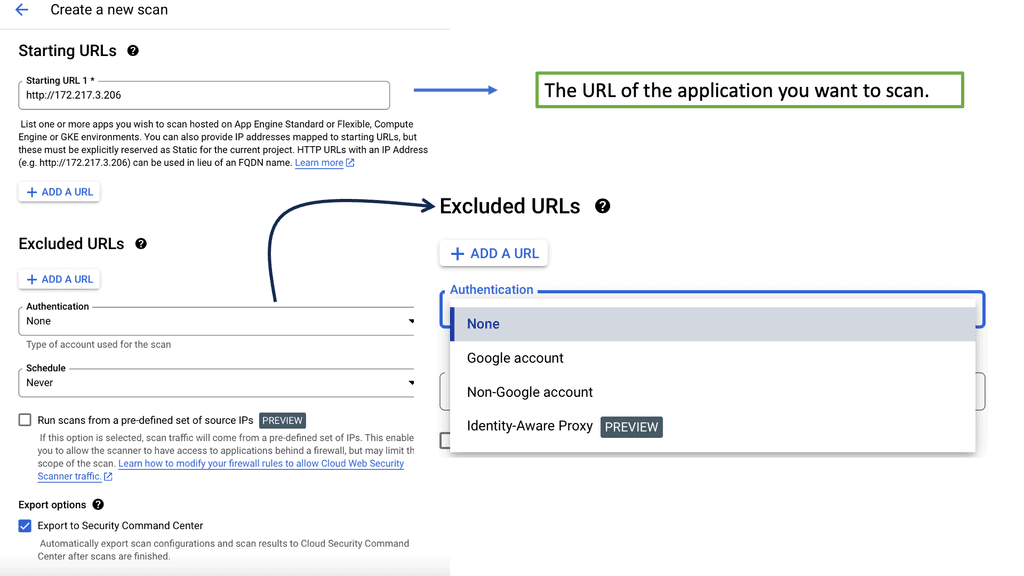
Understanding Network Scanning
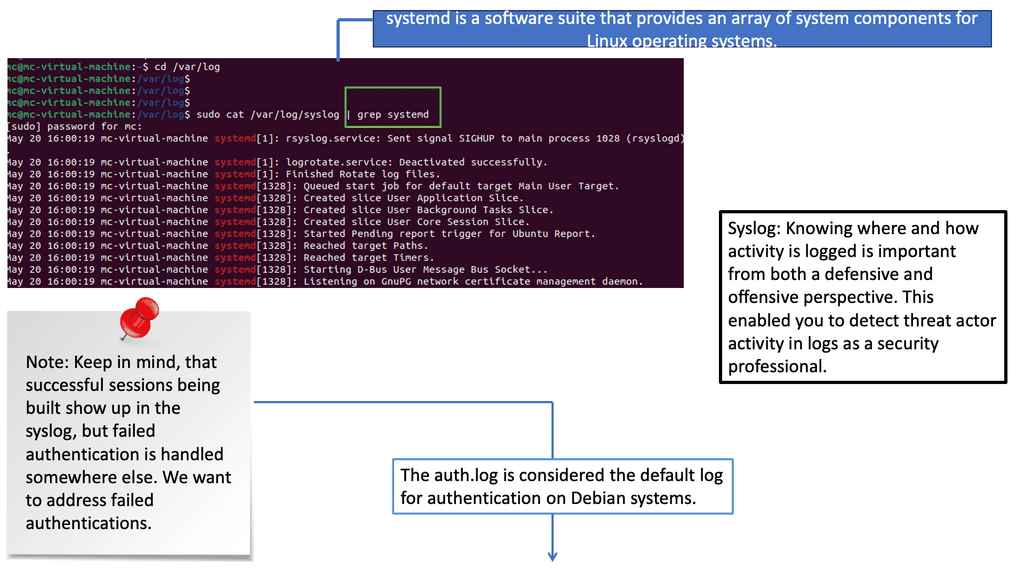
Network scanning involves exploring computer networks to gather information about connected devices, open ports, and system vulnerabilities. Cybersecurity professionals gain valuable insights into the network’s architecture, potential entry points, and security risks by utilizing various scanning techniques and tools.
There are different types of network scans, each serving a specific purpose. Port scans identify open ports and services running on them, while vulnerability scans aim to pinpoint weaknesses within network devices, applications, or configurations. Additionally, network mapping scans visually represent the network’s structure, aiding in better understanding and management.
Example: Cisco Secure Firewall 3100
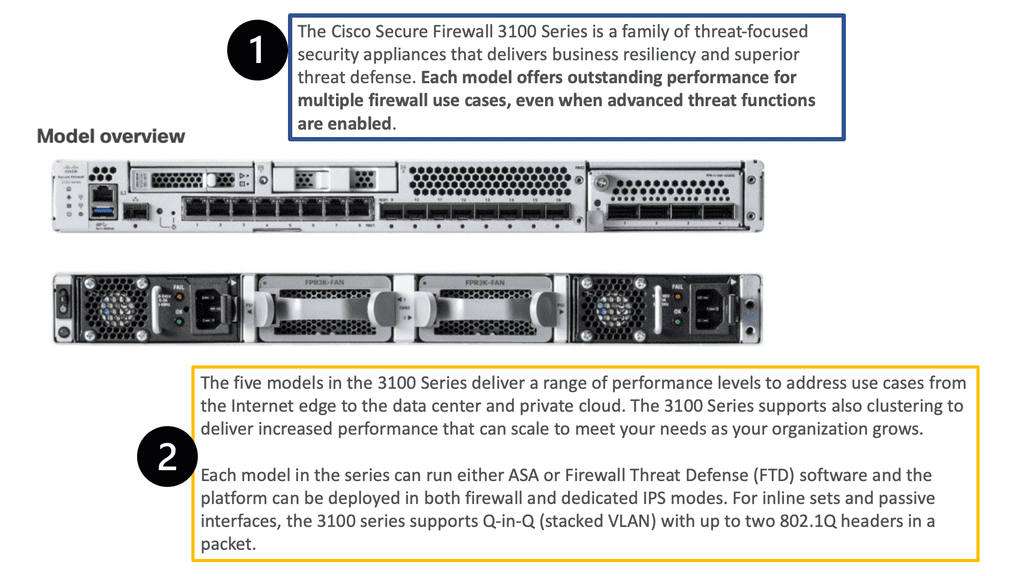
Cisco has the Cisco Secure Firewall 3100, a mid-range model that can be an Adaptive Security Appliance (ASA) for standard stateful firewall inspection or Firewall Threat Defense (FTD) software.
So it can perform one or the other. It also has clustering, a multi-instance firewall, and high availability, which we will discuss. In addition, the Cisco Series Firewall throughput range addresses use cases from the Internet edge to the data center and private cloud.
Cisco Secure Firewall 3100 is an advanced next-generation firewall that provides comprehensive security and high performance for businesses of all sizes. Its advanced security features can protect an organization’s most critical assets, from data, applications, and users to the network infrastructure. Cisco Secure Firewall 3100 offers an integrated threat defense system that combines intrusion prevention, application control, and advanced malware protection. This firewall is designed to detect and block malicious traffic and protect your network from known and unknown threats.
Adaptive Security Appliance (ASA) and Firewall Threat Defense (FTD)
The platforms can be deployed in Firewall (ASA) and dedicated IPS (FTD) modes. In addition, the 3100 series supports Q-in-Q (stacked VLAN) up to two 802.1Q headers in a packet for inline sets and passive interfaces. The platform also supports FTW (fail-to-wire) network modules.
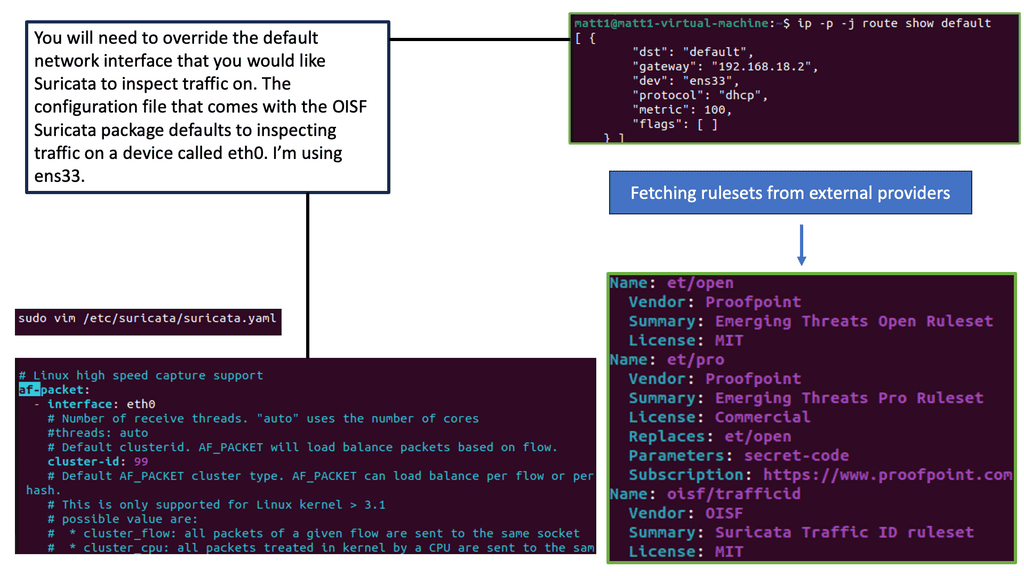
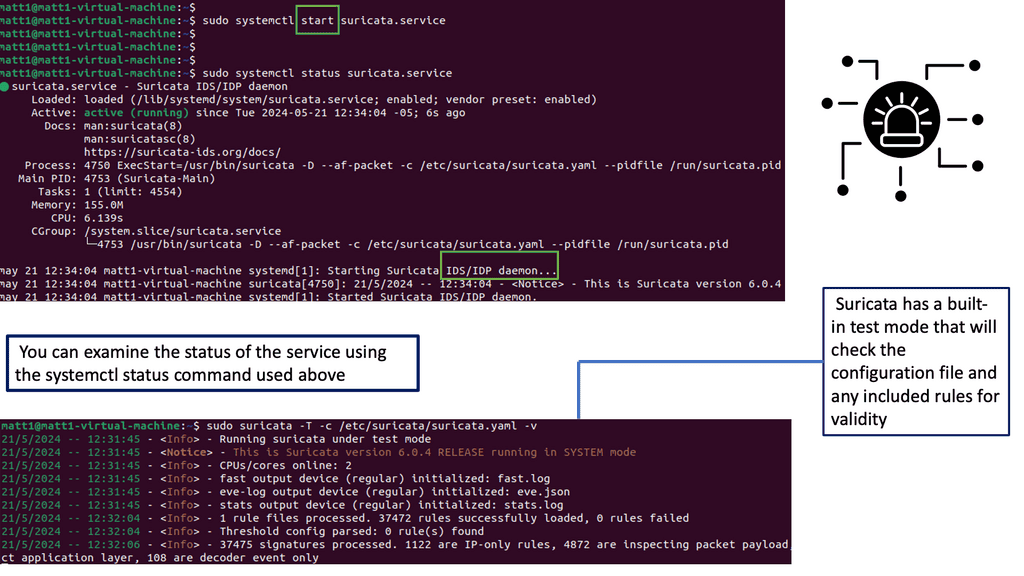
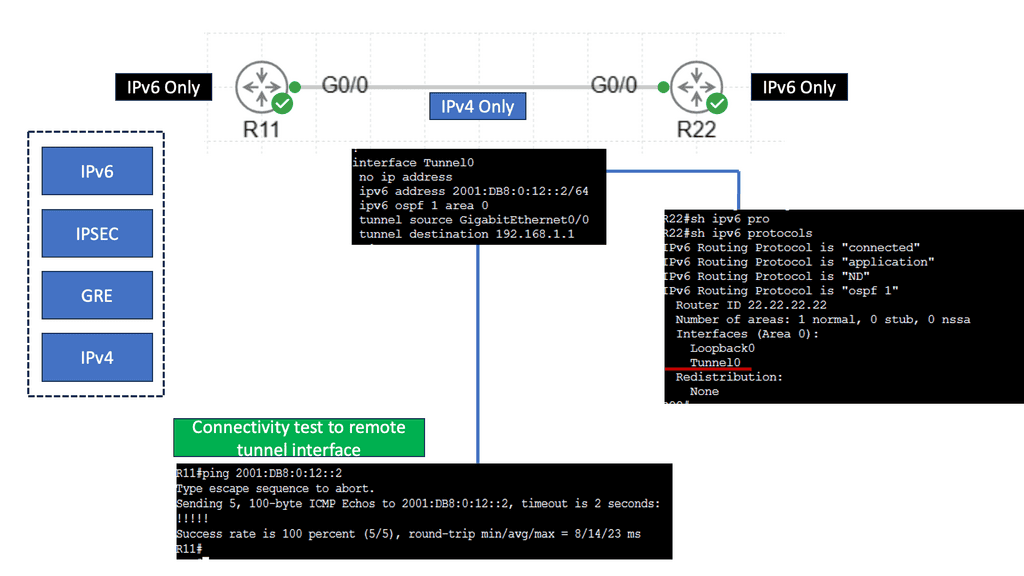
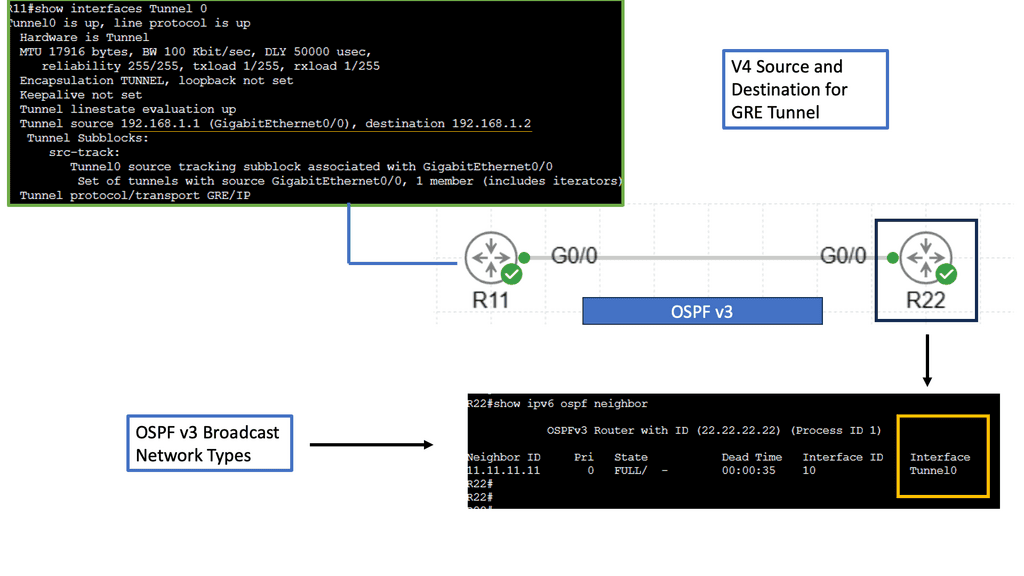
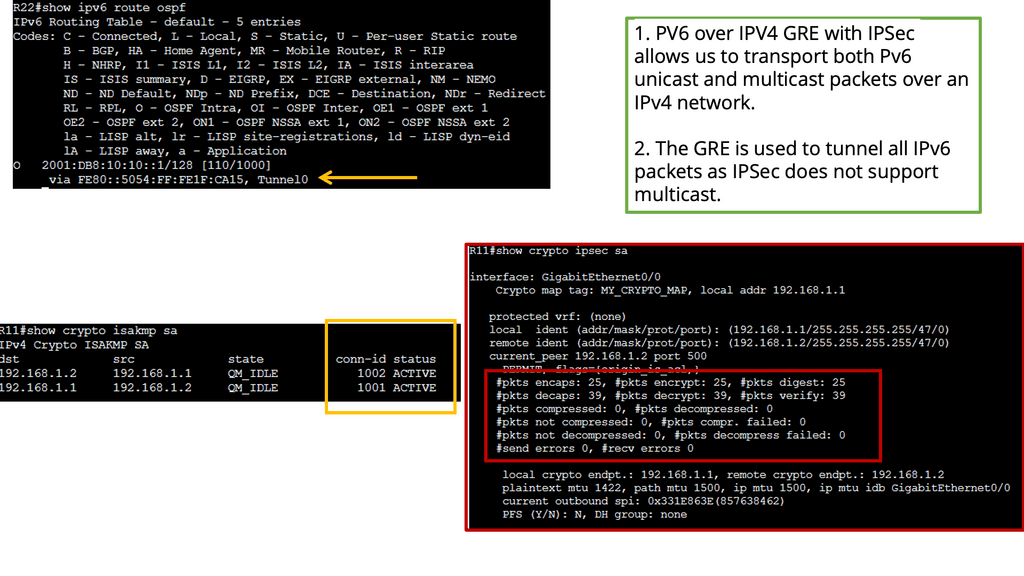
Remember that you cannot mix and match ASA and FTD modes. However, you can make FTD operate similarly to the ASA. For example, the heart of the Cisco Secure Firewall is Snort, one of the most popular open-source intrusion detection and prevention systems capable of real-time traffic inspection.
**IPS Engine – Snort**
What’s powerful about the Cisco Secure Firewall is its high decryption performance due to the Crypto Engine. The Firewall has an architecture built around decrypting traffic and has impressive performance. In addition, you can tune your CPU cores to perform more traditional ASA functionality, such as termination IPsec and some stateful firewall inspection.
In such a scenario, we have an IPS engine ( based on Snort ) but give it only 10%. We can provide 90% of the data plane to traditional firewalling in this case. So, a VPN headend or basic stateful Firewall would use more data plane cores.
On the other hand, any heavy IPS and file inspection would be biased toward more “Snort” Cores. Snort provides the IPS engine to tailor the performance profiles to your liking. We have configurable CPU Core allocation, which can be set statically, not dynamically.
Secure Firewalling Features:
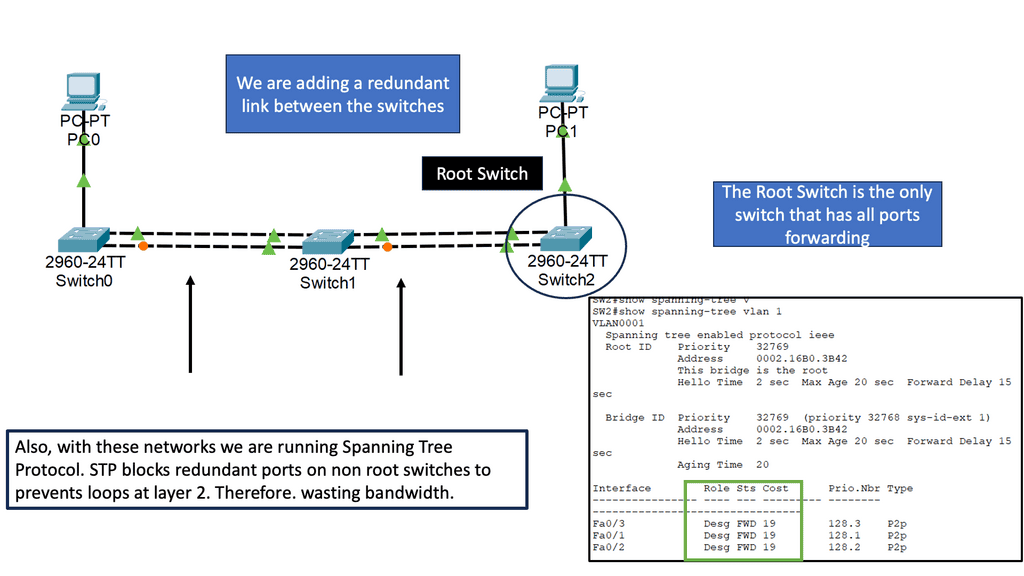
1.Secure Firewall Feature: Clustering
Your Secure Firewall deployment can also expand as your organization grows to support its network growth. You do not need to replace your existing devices for additional horsepower; you can add threat defense devices to your current deployment and group them into a single logical cluster to support additional throughput.
A clustered logical device offers higher performance, scalability, and resiliency simultaneously. You can create a cluster between multiple chassis or numerous security modules of the same chassis. When a cluster is built with various independent chassis, it is called inter-chassis clustering.
2.Secure Firewall Feature: Multi-Instance
The Secure Firewall offers multi-instance capability powered by Docker container technology. It enables you to create and run multiple application instances using a small subset of a chassis’s hardware resources. You can independently manage the threat defense application instances as separate threat defense devices. Multi-instance capability enables you to isolate many critical elements.
3.Secure Firewall Feature: High Availability
In a high-availability architecture, one device operates actively while the other stays on standby. A standby device does not actively process traffic or security events. For example, suppose a failure is detected in the active device, or there’s any discontinuation of keepalive messages from the active device.
In that case, the standby device takes over the role of the active device and starts operating actively to maintain continuity in firewall operations. An active device periodically sends keepalive messages and replicates its configurations to a standby device. Therefore, the communication channel between the peers of a high-availability pair must be robust and with much less latency.
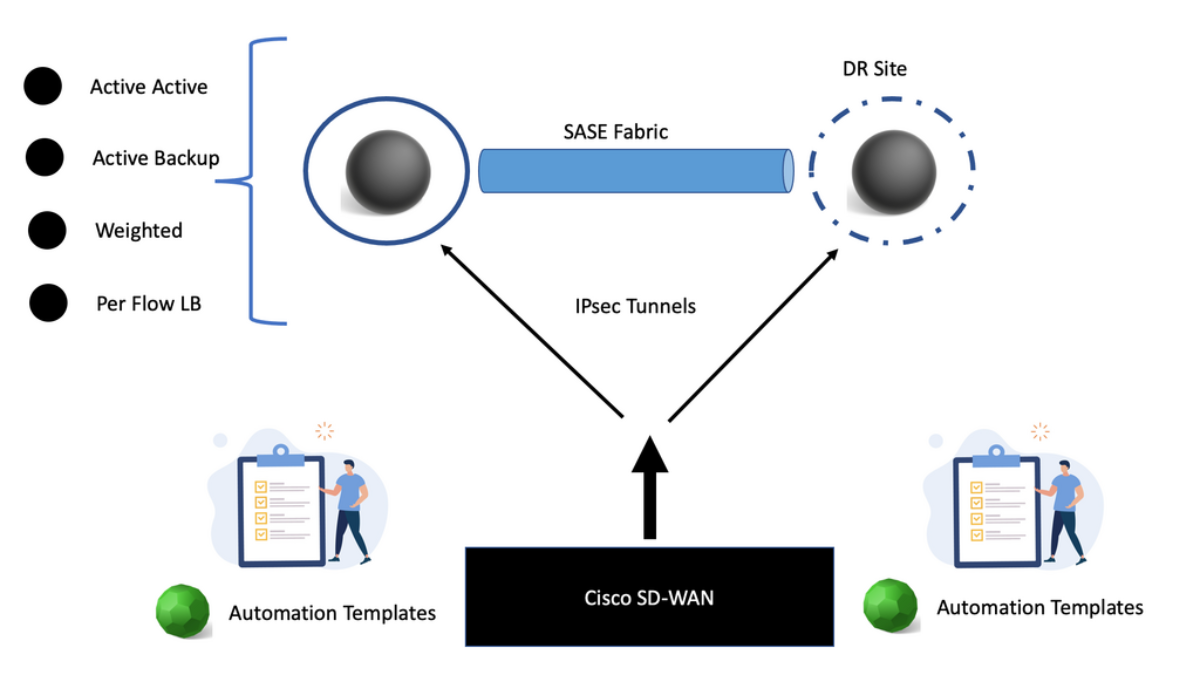
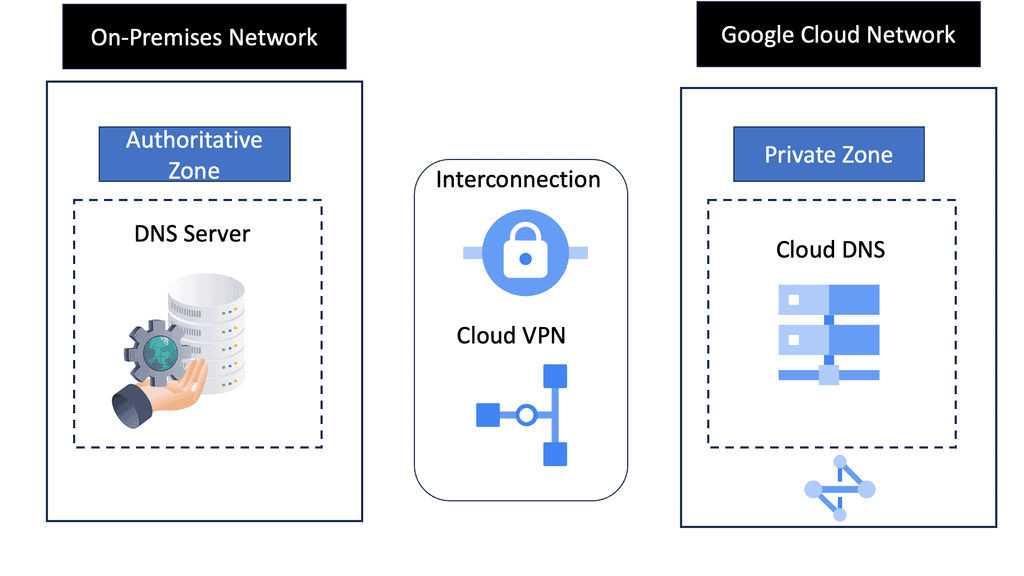
Exploring SASE Cloud
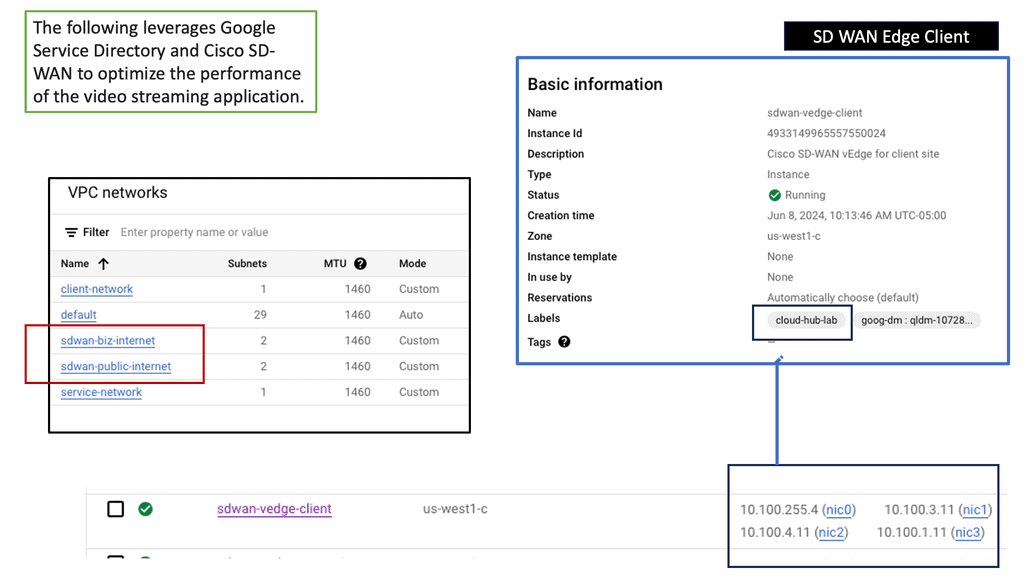
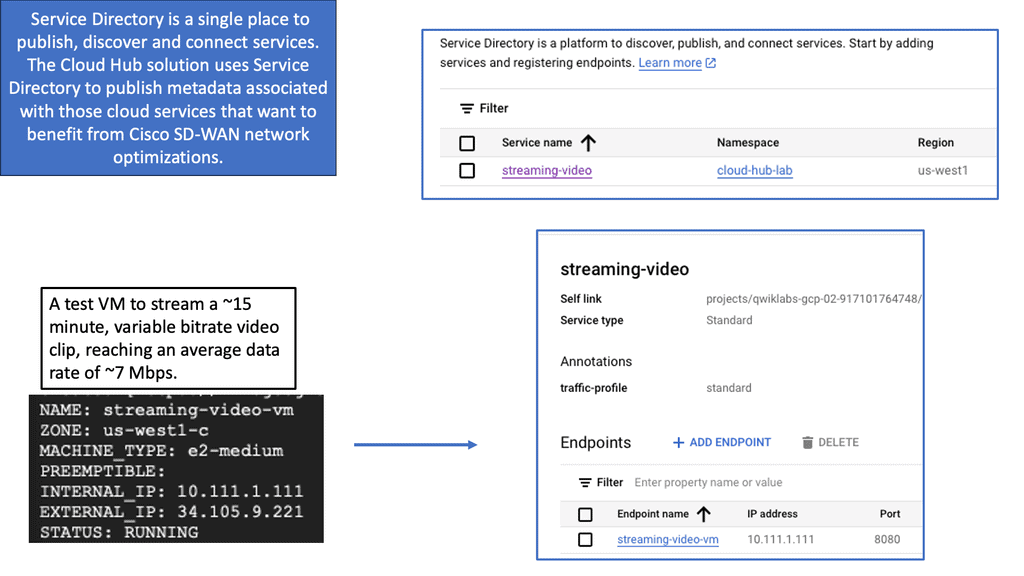
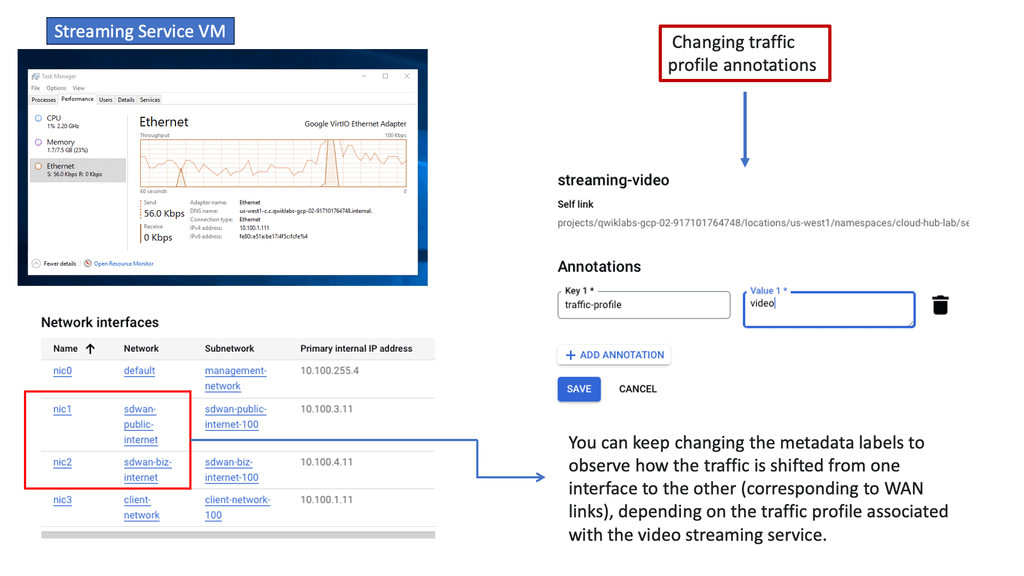
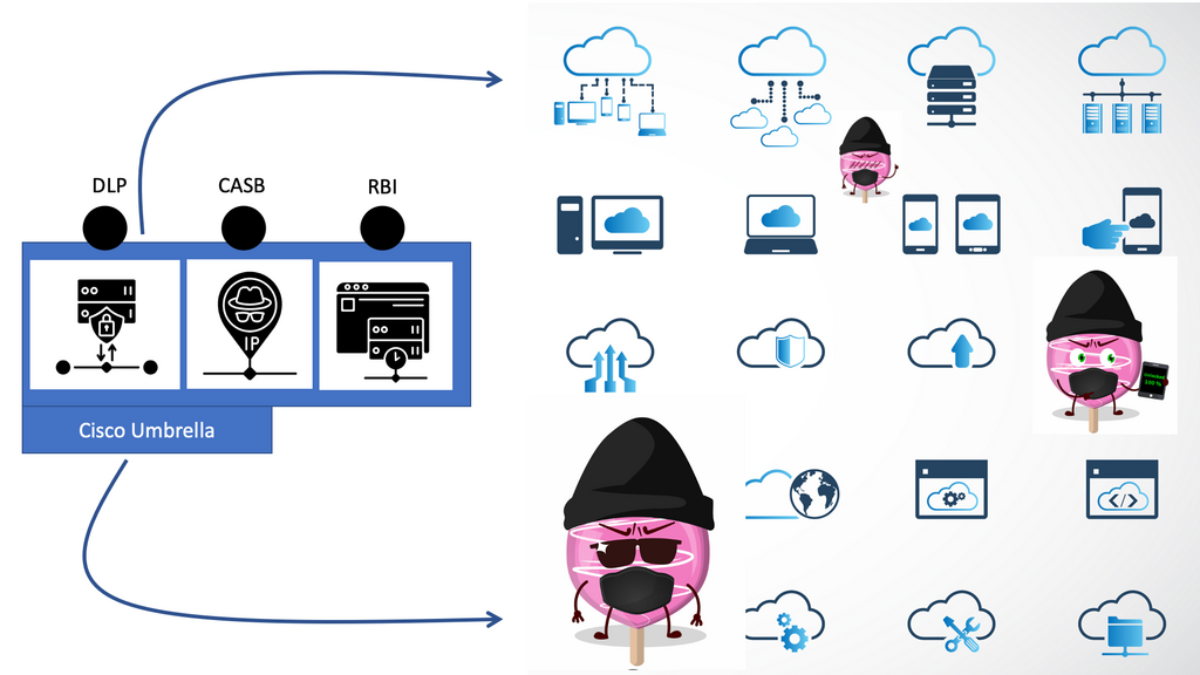
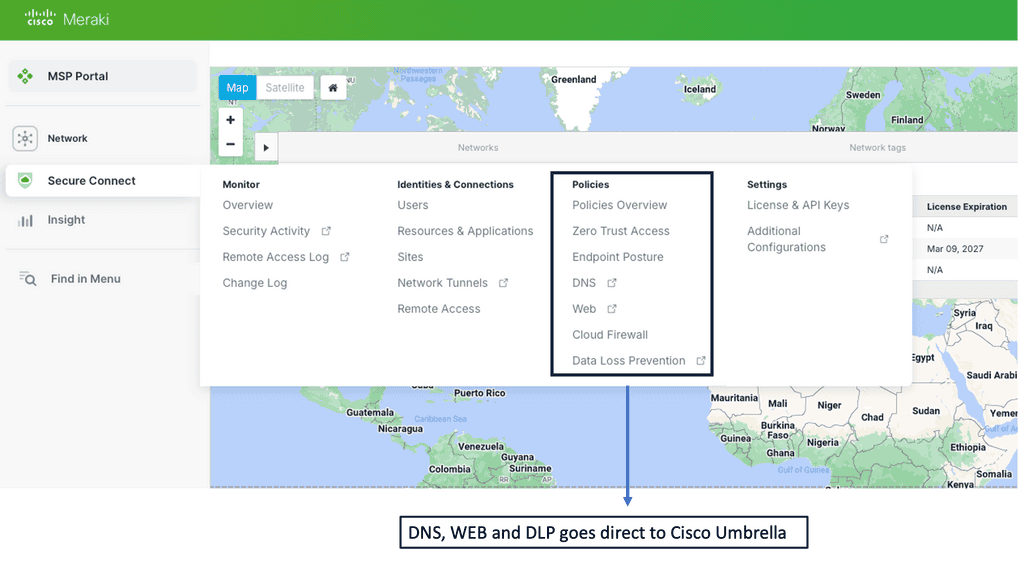
One way to examine SaaS-based applications and introduce some cloud security is by using Cisco Umbrella with the SASE Cloud. The SASE Cloud can also have a cloud access security broker known as Cloudlock. The Cisco Umbrella CASB is like a broker that hooks into the application’s backend to determine users’ actions. It does this by asking for the service via an Application Programming Interface (API) call and not by DPI.
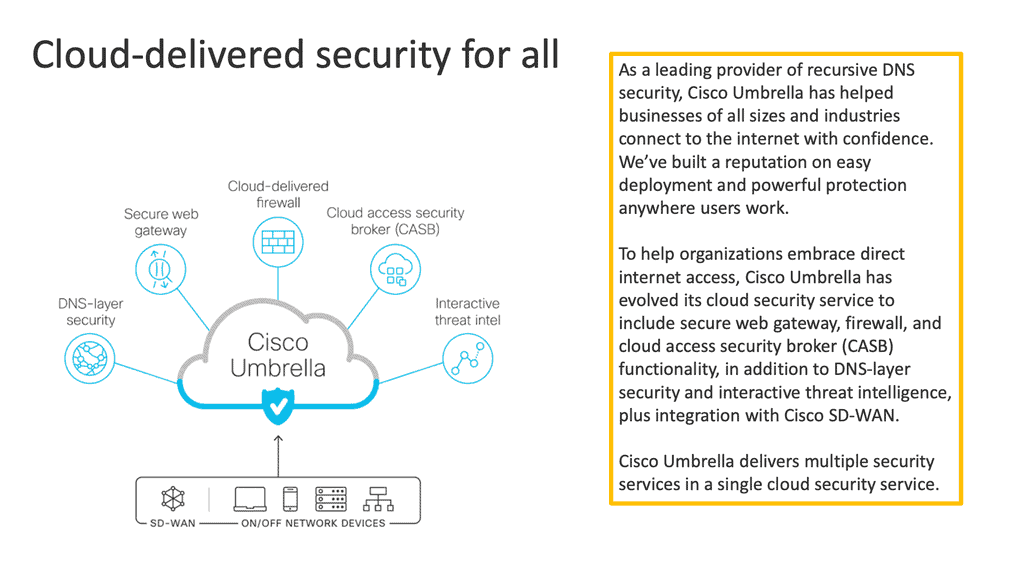
Cisco Cloudlock is part of the SASE cloud that provides a cloud-native cloud access security broker (CASB) that protects your cloud users, data, and apps. Cloud lock’s simple, open, and automated approach uses APIs to manage the risks in your cloud app ecosystem. With Cloudlock, you can more quickly combat data breaches while meeting compliance regulations.
Cisco Umbrella also has a firewall known as the Cisco Umbrella Firewall. We can take the Cisco Umbrella Firewall to improve its policy decision using information gleaned from the CASB. In addition, we map network flows to a specific user action via cloud applications and CASB solutions. So this is one area you can look into.
Extending the Firewall with SASE Cloud
Cisco Umbrella Firewall:
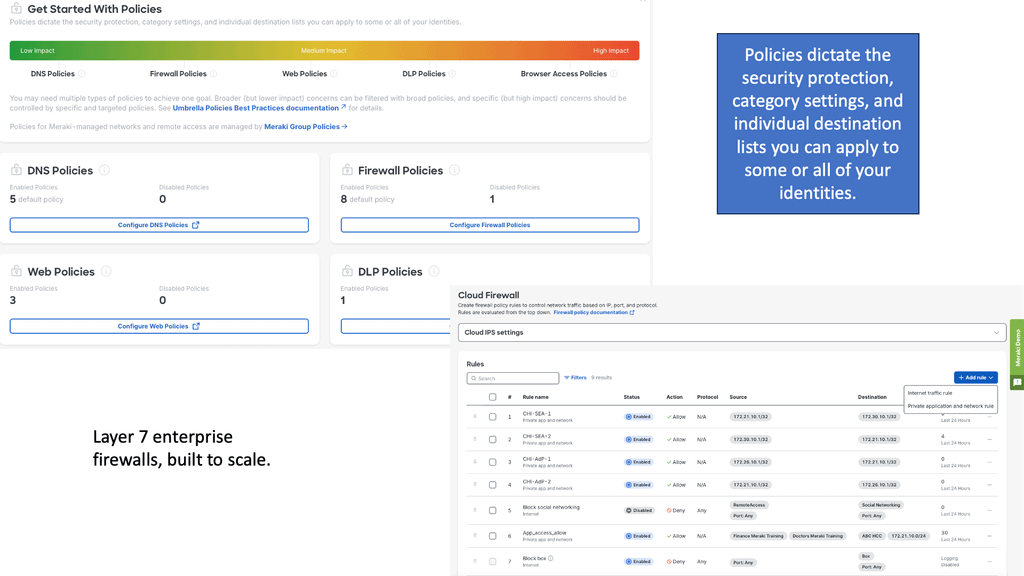
The SASE Cloud with Cisco Umbrella firewall is a good solution that can be combined with the on-premise Firewall. So, if you have FDT at the edge of your network, why would you need to introduce a Cisco Umbrella Firewall or any other SASE technologies? Or if you have a SASE cloud with a Cisco Umbrella, why would you need FDT?
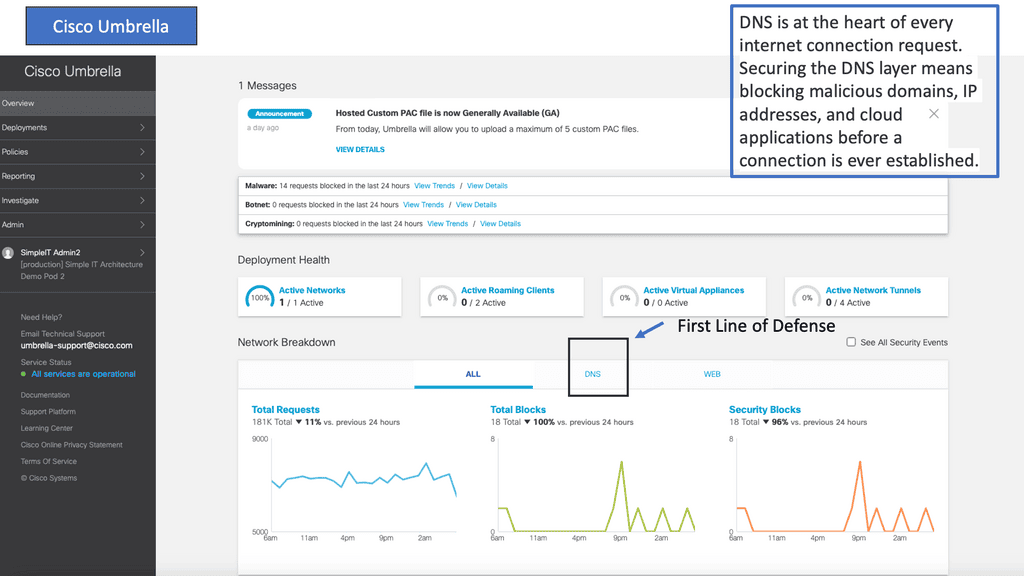
First, it makes sense to process specific traffic locally. However, the two categories of traffic that Cisco Umbrella excels in beyond any firewall are DNS and CASB. Your edge firewall is less effective against some outbound traffic, such as dynamically changing DNS and undecryptable TLS connections. DNS is Cisco Umbrella’s bread and butter.
DNS Request Proceed The IP Connection
Knowledge Check: Cisco DNS-layer security.
DNS requests precede the IP connection, enabling DNS resolvers to log requested domains over any port or protocol for all network devices, office locations, and roaming users. As a result, you can monitor DNS requests and subsequent IP connections to improve the accuracy and detection of compromised systems, security visibility, and network protection.
You can also block requests to malicious destinations before a connection is even established, thus stopping threats before they reach your network or endpoints. Cisco Umbrella under the hood can clean your DNS traffic and stop the attacks before they get to any malicious connection.
SASE Cloud: Cisco Umbrella CASB.
Also, you can not decrypt SaaS-based applications and CASB on the edge firewall. The Firewall can’t detect if the user is carrying out any data exfiltration.
With SASE cloud, Cisco Umbrella, and its integrated CASB offering, we get better visibility in this type of traffic and apply a risk category to certain kinds of activity. So now we have an excellent combination. The cloud security stack does what it does best: processing cycles away from the Firewall.
**Cisco Umbrella Integration**
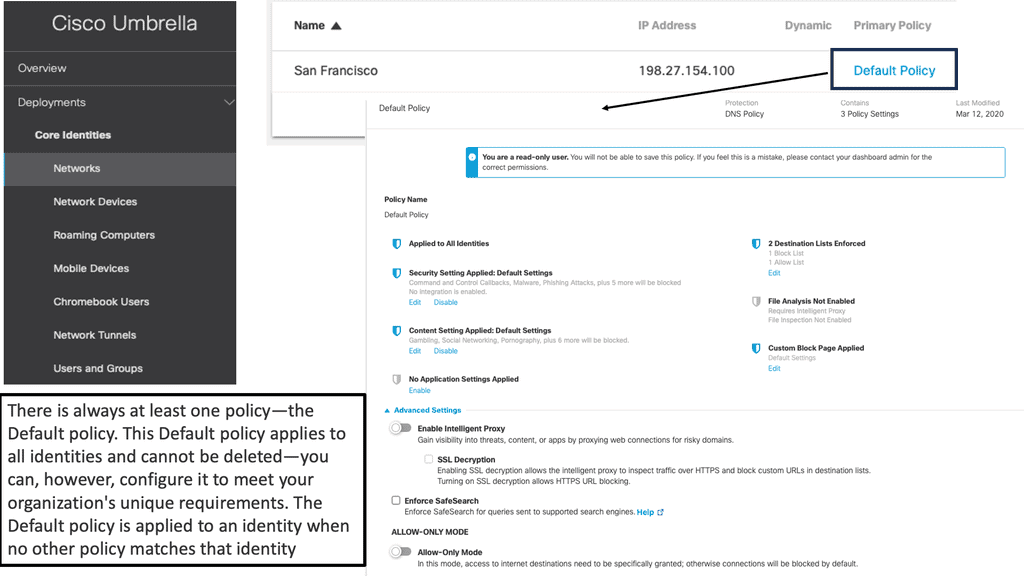
With the Cisco Secure Firewall, they have nice DNS redirection to the Cisco Umbrella Firewall. The on-premise Firewall communicates API to Cisco Umbrella and pulls in the existing DNS policy so the Umbrella DNS policies can be used with the current firewalling policies. Recently, Cisco has gone one step further, and you can have a SIG tunnel between the Cisco Secure Firewall Management Center (FMC) and the Cisco Umbrella.
So there is a tunnel and have per tunnel IKE ID and bundle multiple tunnels to Umbrella. Now, we can have load balance across multi-spoke tunnels with per-tunnel custom IKE ID. Once set up, we can have certain kinds of traffic going down each tunnel.
**Endpoint controls**
Then, we have the endpoint, such as your desktop computer or phone. We can collect a wealth of information about each network connection. This information can be fed into the Firewall via metadata. So you can provide both the Cisco Umbrella Firewall and the Cisco Secure Firewall. Again, for improved policy.
The Firewall, either the Cisco Secure Firewall or the Cisco Umbrella Firewall, does not need to decrypt any traffic. Instead, we can get client context discovery via passive fingerprinting using an agent on the endpoint. We can get a wealth of attributes you can’t get with DPI. So we can move from DPI to everything and augment that with all other components to get better visibility.
Summary: Cisco Secure Firewall with SASE Cloud
In today’s rapidly evolving digital landscape, organizations face the challenge of ensuring robust security while embracing the benefits of cloud-based solutions. Cisco Secure Firewall with SASE (Secure Access Service Edge) Cloud offers a comprehensive and streamlined approach to address these concerns. This blog post delved into the features and benefits of this powerful combination, highlighting its ability to enhance security, simplify network management, and optimize performance.
Understanding Cisco Secure Firewall
Cisco Secure Firewall serves as the first line of defense against cyber threats. Its advanced threat detection capabilities and deep visibility into network traffic provide proactive protection for organizations of all sizes. Cisco Secure Firewall ensures a secure network environment by preventing unauthorized access, blocking malicious content, or detecting and mitigating advanced threats.
Introducing SASE Cloud
On the other hand, SASE Cloud revolutionizes how organizations approach network and security services. SASE Cloud offers a scalable and agile solution by converging network functions and security services into a unified cloud-native platform. It combines features such as secure web gateways, data loss prevention, firewall-as-a-service, and more, all delivered from the cloud. This eliminates the need for costly on-premises infrastructure and allows businesses to scale their network and security requirements effortlessly.
The Power of Integration
When Cisco Secure Firewall integrates with SASE Cloud, it creates a formidable combination that enhances security posture while delivering optimal performance. The integration allows organizations to extend their security policies seamlessly across the entire network infrastructure, including remote locations and cloud environments. This unified approach ensures consistent security enforcement, reducing potential vulnerabilities and simplifying management overhead.
Simplified Network Management
One of the key advantages of Cisco Secure Firewall with SASE Cloud is its centralized management and control. Administrators can easily configure and enforce security policies, monitor network traffic, and gain valuable insights through a single glass pane of glass. This simplifies network management, reduces complexity, and enhances operational efficiency, enabling IT teams to focus on strategic initiatives rather than mundane tasks.
Conclusion
In conclusion, the combination of Cisco Secure Firewall with SASE Cloud provides organizations with a robust and scalable security solution that meets the demands of modern networks. By integrating advanced threat detection, cloud-native architecture, and centralized management, this potent duo empowers businesses to navigate the digital landscape confidently. Experience the benefits of enhanced security, simplified management, and optimized performance by adopting Cisco Secure Firewall with SASE Cloud.