OpenStack Neutron Security Groups
OpenStack, an open-source cloud computing platform, offers a wide range of features and functionalities. Among these, Neutron Security Groups play a vital role in ensuring the security and integrity of the cloud environment. In this blog post, we will delve into the world of OpenStack Neutron Security Groups, exploring their significance, key features, and best practices.
Neutron Security Groups serve as virtual firewalls for instances within an OpenStack environment. They control inbound and outbound traffic, allowing administrators to define and enforce security rules. By grouping instances and applying specific rules, Neutron Security Groups provide a granular level of security to the cloud infrastructure.
Neutron Security Groups offer a variety of features to enhance the security of your OpenStack environment. These include:
1. Rule-Based Filtering: Administrators can define rules based on protocols, ports, and IP addresses to allow or deny traffic flow.
2. Port-Level Security: Each instance can be assigned to one or more security groups, ensuring that only authorized traffic reaches the desired ports.
3. Dynamic Firewalling: Neutron Security Groups support the dynamic addition or removal of rules, allowing for flexibility and adaptability.
1. Default Deny: Start with a default deny rule and only allow necessary traffic to minimize potential security risks.
2. Granular Rule Management: Avoid creating overly permissive rules and instead define specific rules that align with your security requirements.
3. Regular Auditing: Periodically review and audit your Neutron Security Group rules to ensure they are up to date and aligned with your organization's security policies.
Neutron Security Groups can be seamlessly integrated with other OpenStack components to enhance overall security. Integration with Identity and Access Management (Keystone) allows for fine-grained access control, while integration with the OpenStack Networking service (Neutron) ensures efficient traffic management.
OpenStack Neutron Security Groups are a crucial component of any OpenStack deployment, providing a robust security framework for cloud environments. By understanding their significance, leveraging key features, and implementing best practices, organizations can strengthen their overall security posture and protect their valuable assets.Matt Conran
Highlights: OpenStack Neutron Security Groups
What is OpenStack Neutron?
OpenStack Neutron is a networking service that provides on-demand network connectivity for cloud-based applications and services. It acts as a virtual network infrastructure-as-a-service (IaaS) platform, allowing users to create and manage networks, routers, subnets, and more. By abstracting the underlying network infrastructure, Neutron provides flexibility and agility in managing network resources within an OpenStack cloud environment.
OpenStack Neutron offers a wide range of features that empower users to build and manage complex network topologies. Some of the key features include:
1. Network Abstraction: Neutron allows users to create and manage virtual networks, enabling multi-tenancy and isolation between different projects or tenants.
2. Routing and Load Balancing: Neutron provides routing functionalities, allowing traffic to flow between different networks. It also supports load balancing services, distributing traffic across multiple instances for improved performance and reliability.
3. Security Groups: With Neutron, users can define security groups that act as virtual firewalls, controlling inbound and outbound traffic for instances. This enhances the security posture of cloud-based applications.
Neutron Security Groups
Neutron Security Groups serve as virtual firewalls, controlling inbound and outbound traffic to instances within an OpenStack cloud environment. They allow administrators to define and manage firewall rules, thereby enhancing the overall security posture of the network. By grouping instances with similar security requirements, Neutron Security Groups simplify the management of network access policies.
Implementing Security Groups:
To configure Neutron Security Groups, start by creating a security group and defining its rules. These rules can specify protocols, ports, and IP ranges for both inbound and outbound traffic. By carefully crafting these rules, administrators can enforce granular security policies and restrict access to specific resources or services.
Once Neutron Security Groups are configured, they can be easily applied to instances within the OpenStack cloud. By associating instances with specific security groups, administrators can ensure that only authorized traffic is allowed to reach them. This provides an additional layer of protection against potential threats and unauthorized access attempts.
Security Groups Advanced Features:
Neutron Security Groups offer advanced features that further enhance network security. These include the ability to define security group rules based on source and destination IP addresses, as well as the option to apply security groups at the port level. Additionally, Neutron Security Groups support the use of security group logging and can integrate with other OpenStack networking services for seamless security management.
Best Practices:
To maximize the effectiveness of Neutron Security Groups, it is crucial to follow certain best practices. Firstly, adopting a least-privilege approach is recommended, ensuring that only necessary ports and protocols are allowed. Regularly reviewing and updating the security rules is also vital to maintain an up-to-date and secure environment. Additionally, leveraging security groups in conjunction with other OpenStack security features, such as firewalls and intrusion detection systems, can provide a multi-layered defense strategy.
Virtual Networks
A monolithic plugin configured the virtual network in the early days of OpenStack Neutron (formerly known as Quantum). As a result, virtual networks could not be created using gear from multiple vendors. Even when single network vendor devices were used, virtual switches or virtual network types could not be selected. Prior to the Havana release, the Linux bridge and OpenvSwitch plugins could not be used simultaneously. As a result of the creation of the ML2 plugin, this limitation has been addressed
**Open vSwitch & Linux Bridge**
Both OVS and Linux bridge-based virtual switch configurations are supported by ML2 plugins. For network segmentation, it also supports VLANs, VXLANs, and GRE tunnels. In addition to writing drivers, it allows you to implement new types of networks. ML2 drivers fall into two categories: type drivers and mechanism drivers. The type drivers implement the network isolation types VLAN, VXLAN, and GRE. Mechanism drivers implement mechanisms for orchestrating physical or virtual switches:
With OpenStack, virtual networks are protected by network security.A virtual network’s security policies can be self-serviced, just like other network services.Using security groups, firewalls provide security services at the network boundary or at the port level.
Incoming and outgoing traffic are subject to security rules based on match conditions, which include:
- Source and destination addresses should be subject to security policies
- Source and destination ports of network flows
- Traffic direction, egress/ingress
**Security groups**
Network access rules can be configured at the port level with Neutron security groups. Tenants can set access policies for resources within the virtual network using security groups. IPtables uses security groups to filter traffic.
**Network-as-a-Service**
The power of open-source cloud environments is driven by Liberty OpenStack and the Neutron networks forming network-as-a-service. OpenStack can now be used with many advanced technologies – Kubernetes network namespace, Clustering, and Docker Container Networking. By default, Neutron handles all the networking aspects for OpenStack cloud deployments and allows the creation of network objects such as routers, subnets, and ports.
For example, Neutron creates three subnets and defines the conditions for tier interaction with a standard multi-tier application with a front, middle, and backend tier. The filtering is done centrally or distributed with tenant-level firewall OpenStack security groups.
**OpenStack is Modular**
OpenStack is very modular, which allows it to be enhanced by commercial and open-source network technologies. The plugin architecture allows different vendors to strengthen networking and security with advanced routers, switches, and SDN controllers. Every OpenStack component manages a resource made available and virtualized to the user as a consumable service, creating a network or permitting traffic with ingress/egress rule chains. Everything is done in software – a powerful abstraction for cloud environments.
For pre-information, you may find the following helpful
OpenStack Neutron Security Groups
Security Groups
Security groups are essential for maintaining access to instances. They permit users to create inbound and outbound rules that restrict traffic to and from models based on specific addresses, ports, protocols, and even other security groups.
Neutron creates default security groups for every project, allowing all outbound communication and restricting inbound communication to instances in the same default security group. Following security groups are locked down even further, allowing only outbound communication and not allowing any inbound traffic at all unless modified by the user.
Benefits of OpenStack Neutron Security Groups:
1. Granular Control: With OpenStack Neutron Security Groups, administrators can define specific rules to control traffic flow at the instance level. This granular control enables the implementation of stricter security measures, ensuring that only authorized traffic is allowed.
2. Enhanced Security: By utilizing OpenStack Neutron Security Groups, organizations can strengthen the security posture of their cloud environments. Security Groups help mitigate risks by preventing unauthorized access, reducing the surface area for potential attacks, and minimizing the impact of security breaches.
3. Simplified Management: OpenStack Neutron Security Groups offer a centralized approach to managing network security. Administrators can define and manage security rules across multiple instances, making it easier to enforce consistent security policies throughout the cloud infrastructure.
4. Dynamic Adaptability: OpenStack Neutron Security Groups allow dynamic adaptation to changing network requirements. As instances are created or terminated, security rules can be automatically applied or removed, ensuring that security policies remain up-to-date and aligned with the evolving infrastructure.
Security Group Implementation Example:
To illustrate the practical implementation of OpenStack Neutron Security Groups, let’s consider a scenario where an organization wants to deploy a multi-tier web application in its OpenStack cloud. They can create separate security groups for each tier, such as web servers, application servers, and database servers, with specific access rules for each group. This segregation ensures that traffic is restricted to only the necessary ports and protocols, reducing the attack surface and enhancing overall security.
OpenStack Neutron Security Groups: The Components
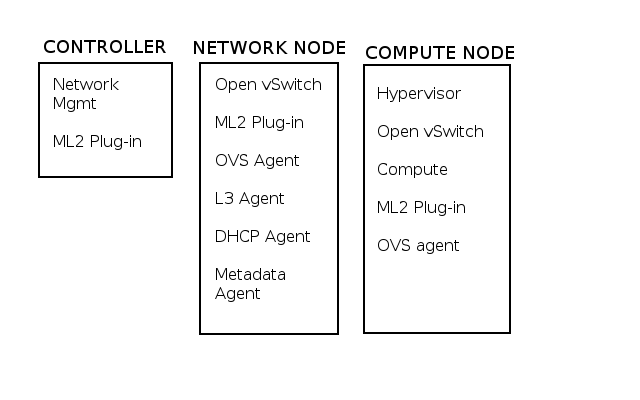
Control, Network, and Compute
The OpenStack architecture for network-as-a-service Neutron-based clouds is divided into Control, Network, and Compute components. At a very high level, the control tier runs the Application Programming Interfaces (API), compute is the actual hypervisor with various agents, and the network component provides network service control.
All these components use a database and message bus. Examples of databases include MySQL, PostgreSQL, and MariaDB; for message buses, we have RabbitMQ and Qpid. The default plugins are Modular Layer 2 (ML2) and Open vSwitch.
Ports, Networks, and Subnets
Neutrons’ network-as-a-service core and the base for the API are elementary. It consists of Ports, Networks, and Subnets. Ports hold the IP and MAC address and define how a VM connects to the network. They are an abstraction for VM connectivity.
A network is a Layer 2 broadcast domain represented as an external network (reachable from the Internet), provider network (mapped to an existing network), and tenant network, created by cloud users and isolated from other tenant networks. Layer 3 routers connect networks; subnets are the subnet spaces attached to networks.
OpenStack Neutron: Components
OpenStack networking with Neutron provides an API to create various network objects. This powerful abstraction allows the creation of networks in software and the ability to attach multiple subnets to a single network. The Neutron Network is isolated or connected with Layer 3 routers for inter-network connectivity.
Neutron employs floating IP, best understood as a 1:1 NAT translation. The term “floating” comes from the fact that it can be modified on the fly between instances.
It may seem that floating IPs are assigned to instances, but they are actually assigned to ports. Everything gets assigned to ports—fixed IPs, Security Groups, and MAC addresses. SNAT (source NAT) or DNAT (destination NAT) enables inbound and outbound traffic to and from tenants. DNAT modifies the destination’s IP address in the IP packet header, and SNAT modifies the sender’s IP address in IP packets.
Open vSwitch and the Linux bridge
Neutrons can be integrated for switching functionality with Open vSwitch and Linux bridge. By default, it integrates with the ML2 plugin and Open vSwitch. Open vSwitch and Linux bridges are virtual switches orchestrating the network infrastructure.
For enhanced networking, the virtual switch can be controlled outside Neutron by third-party network products and SDN controllers via plugins. The Open vSwitch may also be replaced or used in parallel. Recently, many enhancements have been made to classic forwarding with Open vSwitch and Linux Bridge.
We now have numerous high availability options with L3 High Availability & VRRP and Distributed Virtual Routing (DVR) feature. DVR essentially moves to route from the Layer 3 agent to compute nodes. However, it only works with tunnels and L2pop enabled, requiring the compute nodes to have external network connectivity.
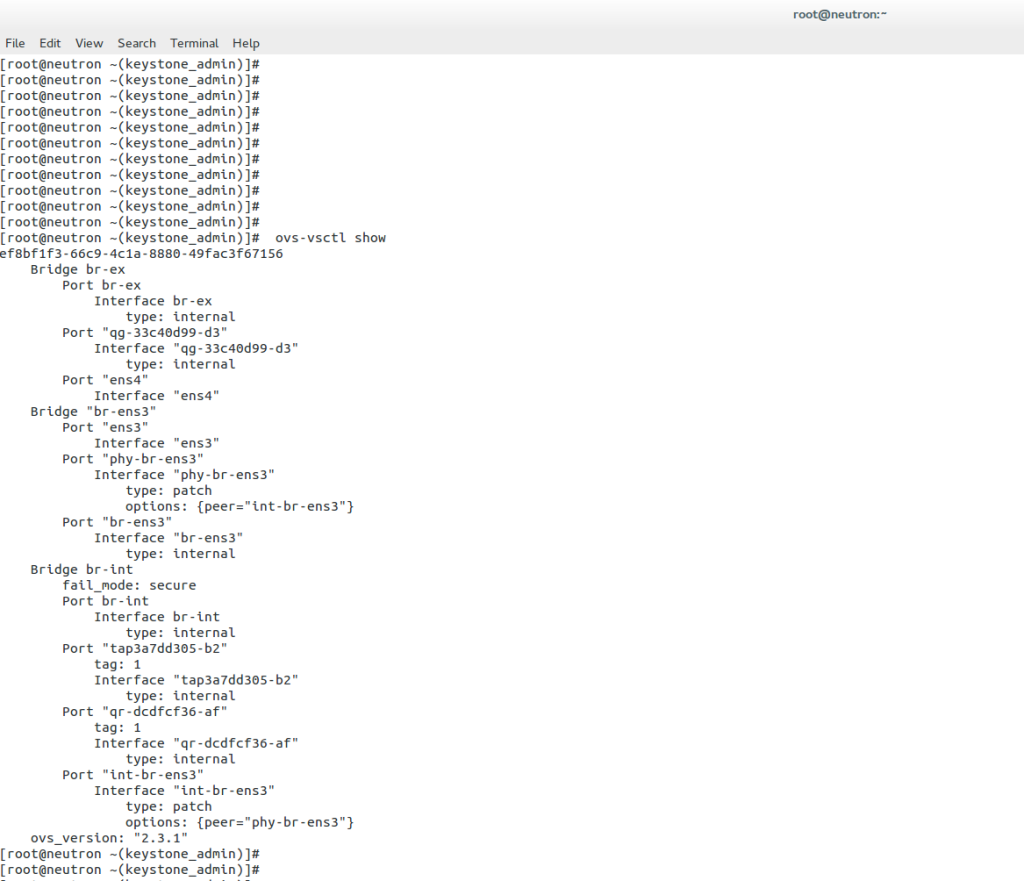
For production environments, these HA features are a welcomed update. The following shows three bridges created in Open vSwitch – br-ex, br-ens3, and br-int. The br-int is the main integration bridge; all others connect via particular patch ports.
Network-as-a-service and agents
Neutron has several parts backed by a relationship database. The Neutron server is the API, and the RPC service talks to the agents (L2 agent, L3 agent, DHCP agent, etc.) via the message queue. The Layer 2 agent runs on the compute and communicates with the Neutron server with RPC. Some deployments don’t have an L2 agent, for example, if you are using an SDN controller.
Also, if you deploy the Linux bridge instead of the Open vSwitch, you don’t have the Open vSwitch agent; instead, use the standard Linux Bridge utilities. The Layer 3 agent runs on the Neutron network node and uses Linux namespaces to implement multiple copies of the IP stack. It also runs the metadata agent and supports static routing.
Linux Namespaces
An integral part of Neutron networking is the Linux namespace for object isolation. Namespaces enable multi-tenancy and allow overlapping IP address assignment for tenants – an essential requirement for many cloud environments. Every network and network service a user creates is a namespace.
For example, the qdhcp namespace represents the DHCP services, qrouter namespace represents the router namespace and the qlbaas represents the load balance service based on HAProxy. The qrouter namespaces provide routing amongst networks – north-south and east-west traffic. It also performs SNAT and DNAT in classic non-DVR scenarios. For certain cases with DVR, the snat namespaces perform SNAT for north-south network traffic.
OpenStack Neutron Security Groups
OpenStack has the concept of OpenStack Neutron Security Groups. They are a tenant-level firewall enabling Neutron to provide distributed security filtering. Due to the limitations of Open vSwitch and iptables, the Linux bridge controls the security groups. Neutron security groups are not directly added to the Integration bridge. Instead, they are implemented on the Linux bridge that connects to the integrated bridge.
The reliance on the Linux bridge stems from Neutron’s inability to place iptable rules on tap interfaces connected to the Open vSwitch. Once a Security Group has been applied to the Neutron port, the rules are translated into iptable rules, which are then applied to the node hosting the respective instance.
Neutron also can protect instances with perimeter firewalls, known as Firewall-as-a-service.
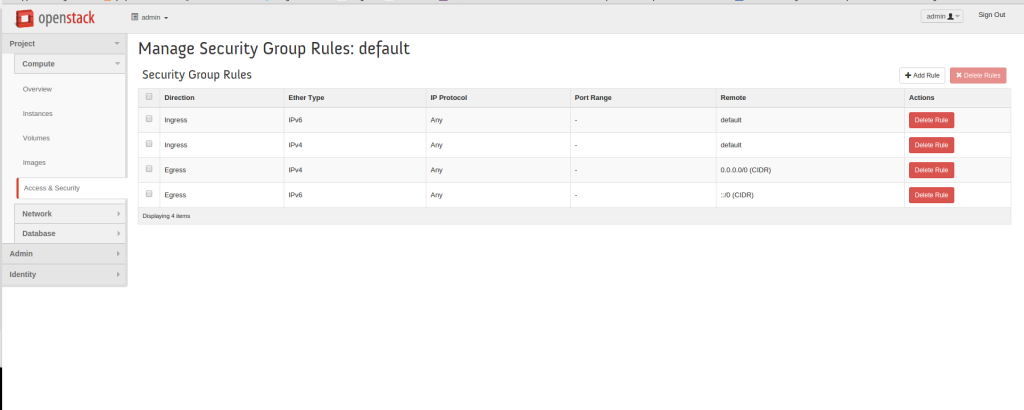
Firewall rules implemented with perimeter firewalls utilizing iptables within a Neutron routers namespace instead of configuring on every compute host. The following diagram displays ingress and egress rules for the default security group. Tenants that don’t have a security group are placed in the default security group.
Closing Points on OpenStack Neutron Security Groups
In the realm of cloud computing, security is paramount. OpenStack, a popular open-source cloud platform, offers various components to ensure robust security within its environment. One of the core elements of this security architecture is Neutron Security Groups. These act as virtual firewalls, providing a layer of protection for instances by controlling inbound and outbound traffic at the network interface level. But what exactly are Neutron Security Groups, and how do they function?
Neutron Security Groups in OpenStack are designed to enhance the security of your cloud infrastructure. They are essentially sets of IP filter rules that define networking access to the instances. Each instance can be associated with one or more security groups, and each group contains a collection of rules that specify the type of traffic allowed to and from instances.
These rules are based on IP protocols, source, and destination IP ranges, and port numbers. By default, a security group allows all outbound traffic and denies all inbound traffic. Users can then customize the rules to fit their specific security needs, providing a flexible and dynamic security solution.
To effectively use Neutron Security Groups, one must understand how to create and manage them within the OpenStack environment. Creating a security group involves defining a set of rules that determine the traffic allowed to reach the associated instances. This is done through the Horizon dashboard or OpenStack CLI, where users can specify the security protocols and port ranges.
Managing these groups involves regularly updating the rules to adapt to changing security requirements. This might include adding new rules, modifying existing ones, or deleting those that are no longer necessary. Effective management ensures that the cloud environment remains secure while allowing necessary traffic to pass through.
Implementing best practices when using Neutron Security Groups can significantly enhance your cloud’s security posture. First, it’s crucial to follow the principle of least privilege, allowing only the necessary traffic to and from your instances. Regular audits of security group rules help identify and eliminate redundancies or outdated rules that might expose vulnerabilities.
Additionally, documenting each rule’s purpose and the rationale behind it can aid in maintaining a clear security strategy. It’s also advisable to automate security group updates and monitoring using tools and scripts, ensuring real-time responsiveness to potential threats.
Summary: OpenStack Neutron Security Groups
OpenStack, a powerful cloud computing platform, offers a range of networking features to manage virtualized environments efficiently. One such feature is OpenStack Neutron, which enables the creation and management of virtual networks. In this blog post, we will delve into the realm of OpenStack Neutron security groups, understanding their significance, and exploring their configuration and best practices.
Understanding Neutron Security Groups
Neutron security groups act as virtual firewalls, allowing administrators to define and enforce network traffic rules for instances within a particular project. These security groups provide an added layer of protection by controlling inbound and outbound traffic, ensuring network security and isolation.
Configuring Neutron Security Groups
Configuring Neutron security groups requires a systematic approach. Firstly, you need to define the necessary security group rules, specifying protocols, ports, and IP ranges. Secondly, associate the security group rules with specific instances or ports to control the traffic flow. Finally, ensure that the security group is applied correctly to the virtual network or subnet to enforce the desired restrictions.
Best Practices for Neutron Security Groups
To maximize the effectiveness of Neutron security groups, consider the following best practices:
1. Implement the Principle of Least Privilege: Only allow necessary inbound and outbound traffic, minimizing potential attack vectors.
2. Regularly Review and Update Rules: As network requirements evolve, periodically review and update the security group rules to align with changing needs.
3. Combine with Other Security Measures: Neutron security groups should complement other security measures such as network access control lists (ACLs) and virtual private networks (VPNs) for a comprehensive defense strategy.
4. Logging and Monitoring: Enable logging and monitoring of security group activities to detect and respond to any suspicious network behavior effectively.
Conclusion:
OpenStack Neutron security groups are a vital component in ensuring the safety and integrity of your cloud network. By understanding their purpose, configuring them correctly, and following best practices, you can establish robust network security within your OpenStack environment.