ASA Failover
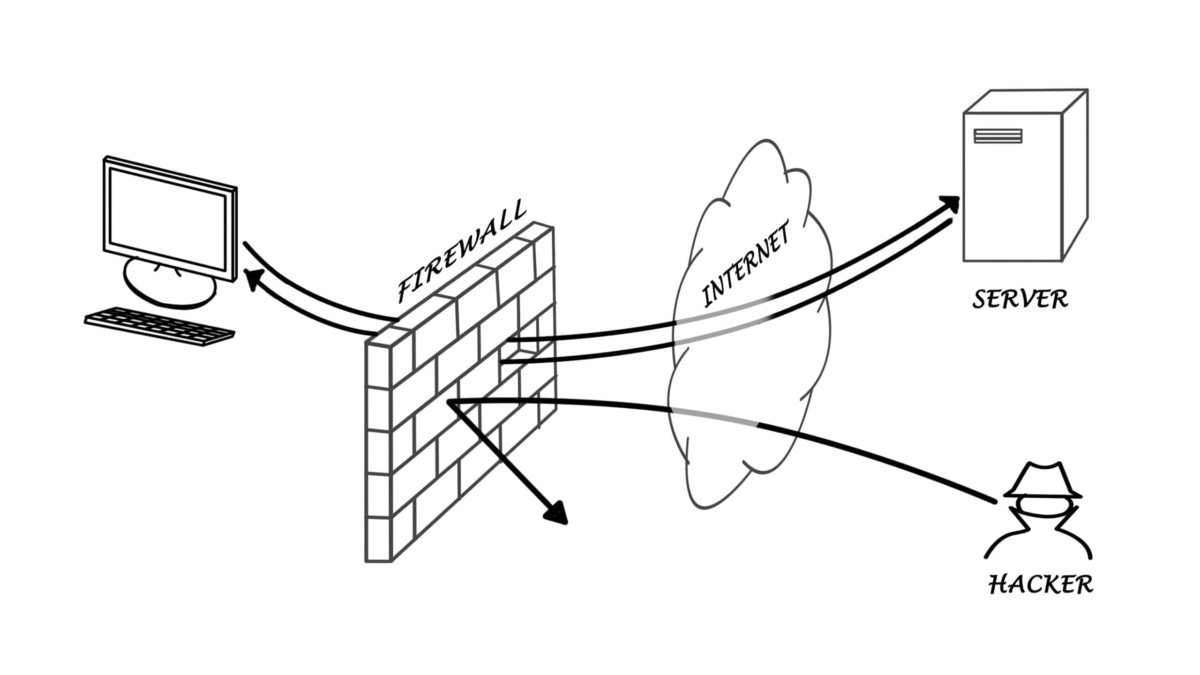
Cisco ASA (Adaptive Security Appliance) firewalls are widely used by organizations to protect their networks from unauthorized access and threats. One of the key features of Cisco ASA is failover, which ensures uninterrupted network connectivity and security even in the event of hardware failures or other issues. In this blog post, we will explore the concept of Cisco ASA failover and its importance in maintaining network resilience.
Cisco ASA failover is a mechanism that allows two Cisco ASA firewalls to work together in an active-passive setup. In this setup, one firewall assumes the role of the primary unit, while the other serves as the secondary unit. The primary unit handles all network traffic and actively performs firewall functions, while the secondary unit remains in standby mode, ready to take over in case of primary unit failure.
Active/Standby Failover: One of the most common types of ASA Failover is Active/Standby Failover. In this setup, the primary unit actively handles all network traffic, while the secondary unit remains in a standby mode. Should the primary unit fail, the secondary unit seamlessly takes over, ensuring minimal disruption and downtime for users.
Active/Active Failover: Another type of ASA Failover is Active/Active Failover. This configuration allows both ASA units to actively process traffic simultaneously. With load balancing capabilities, Active/Active Failover optimizes resource utilization and ensures high availability even during peak traffic periods.
Configuring ASA Failover: Configuring ASA Failover involves establishing a failover link between the primary and secondary units, defining failover policies, and synchronizing configuration and state information. Cisco provides intuitive command-line interfaces and graphical tools to simplify the configuration process, making it accessible to network administrators of varying expertise levels.
ASA Failover offers numerous benefits for businesses. Firstly, it provides redundancy, ensuring that network operations continue uninterrupted even in the event of device failures. This translates to increased uptime and improved productivity. Additionally, ASA Failover enhances security by providing seamless failover for security policies, preventing potential vulnerabilities during critical moments.
Matt Conran
Highlights: ASA Failover
The Cisco ASA Family
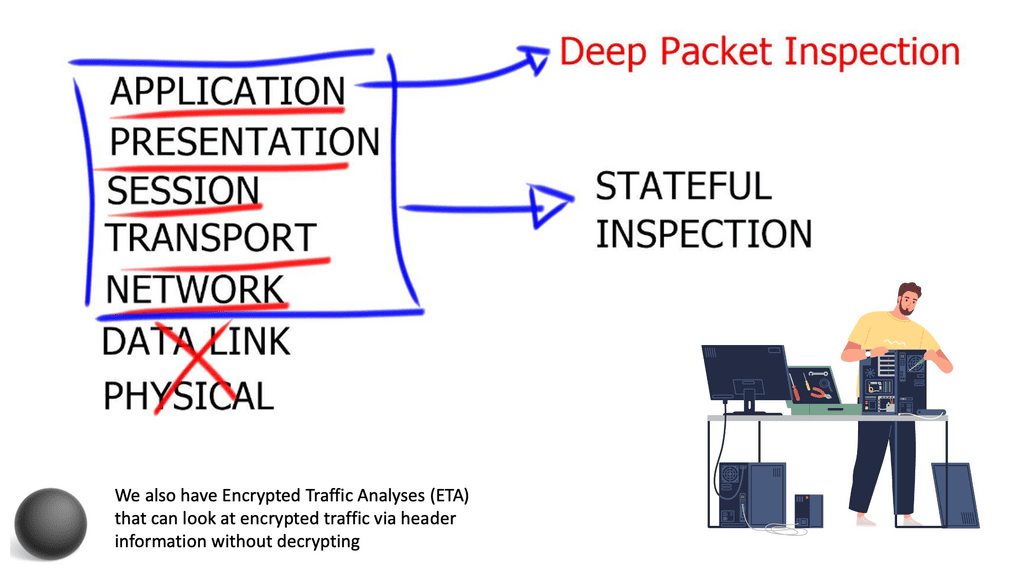
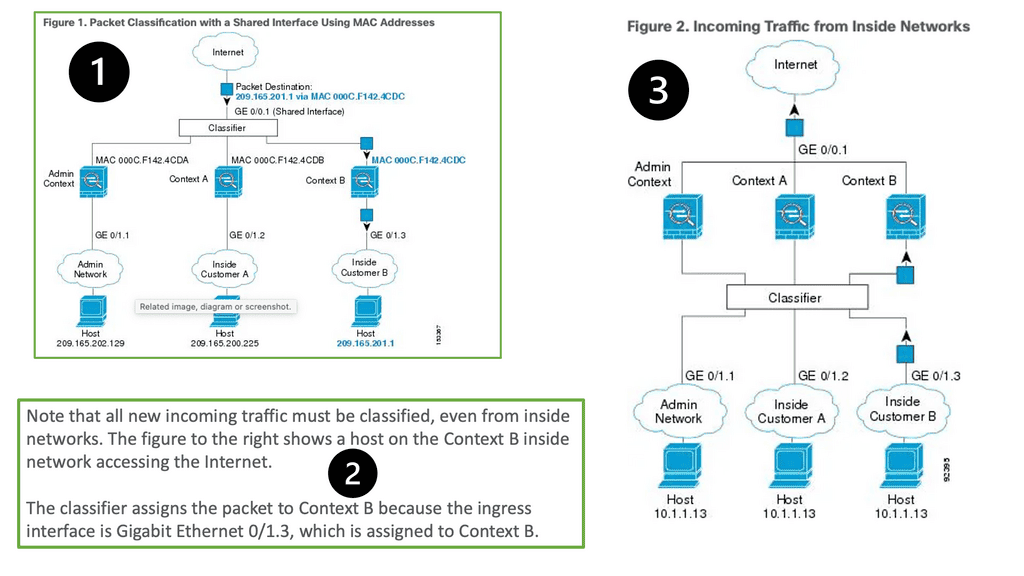
The Cisco ASA family offers a wide range of next-generation security features. Its features include simple packet filtering (usually configured with access control lists [ACLs]) and stateful inspection. Additionally, Cisco ASA provides application inspection and awareness. Devices on one side of the firewall can speak to devices on the other through a Cisco ASA device.
Common Security Features
NAT, Dynamic Host Configuration Protocol (DHCP), and the ability to act as a DHCP server or client are also supported by the Cisco ASA family. In addition to Routing Information Protocol (RIP), Enhanced Interior Gateway Routing Protocol (EIGRP), and Open Shortest Path First (OSPF), the Cisco ASA family supports most of the interior gateway routing protocols. Static routing is also supported. It is also possible to implement Cisco ASA devices as traditional Layer 3 firewalls, which assign IP addresses to each of their routable interfaces.
Firewall Implementation
If a firewall is implemented as a transparent (Layer 2) firewall, the actual physical interfaces are not configured with individual IP addresses but rather as a pair of bridge-like interfaces. The ASA can still implement rules and inspect traffic crossing this two-port bridge. Cisco ASA devices are often used as headends or remote ends for VPN tunnels for remote-access VPN users and site-to-site VPN tunnels. VPNs based on IPsec and SSL can be configured on Cisco ASA devices. Clientless SSL VPN.
Understanding Failover
Failover configurations require two identical security appliances connected by an optional Stateful Failover link. The health of the active interfaces and units is monitored to determine if specific failover conditions are met. Failover occurs if those conditions are met.
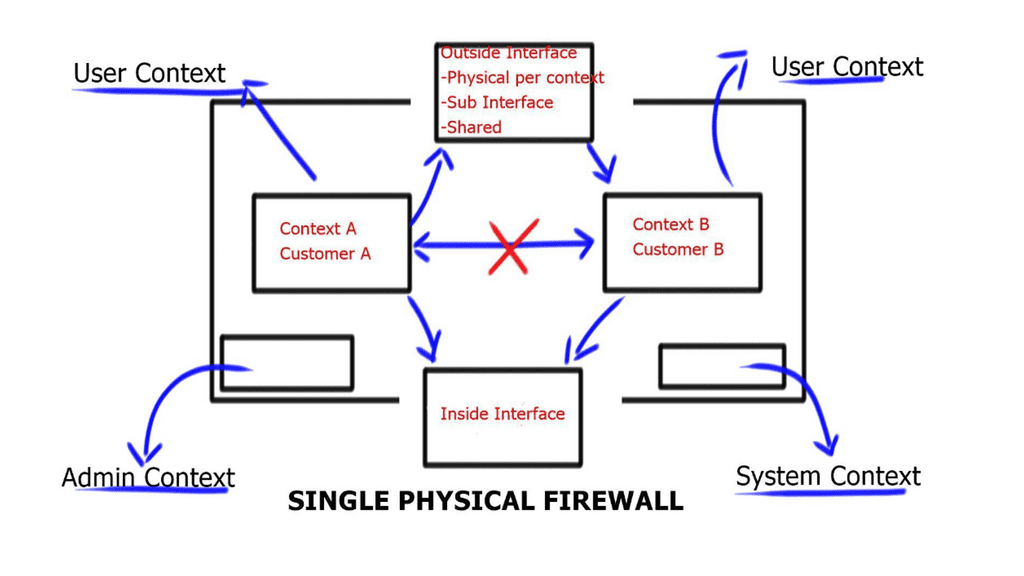
– Activate/Active failover and Activate/Standby failover are available for the security appliance. A failover configuration determines and performs failover according to its method.
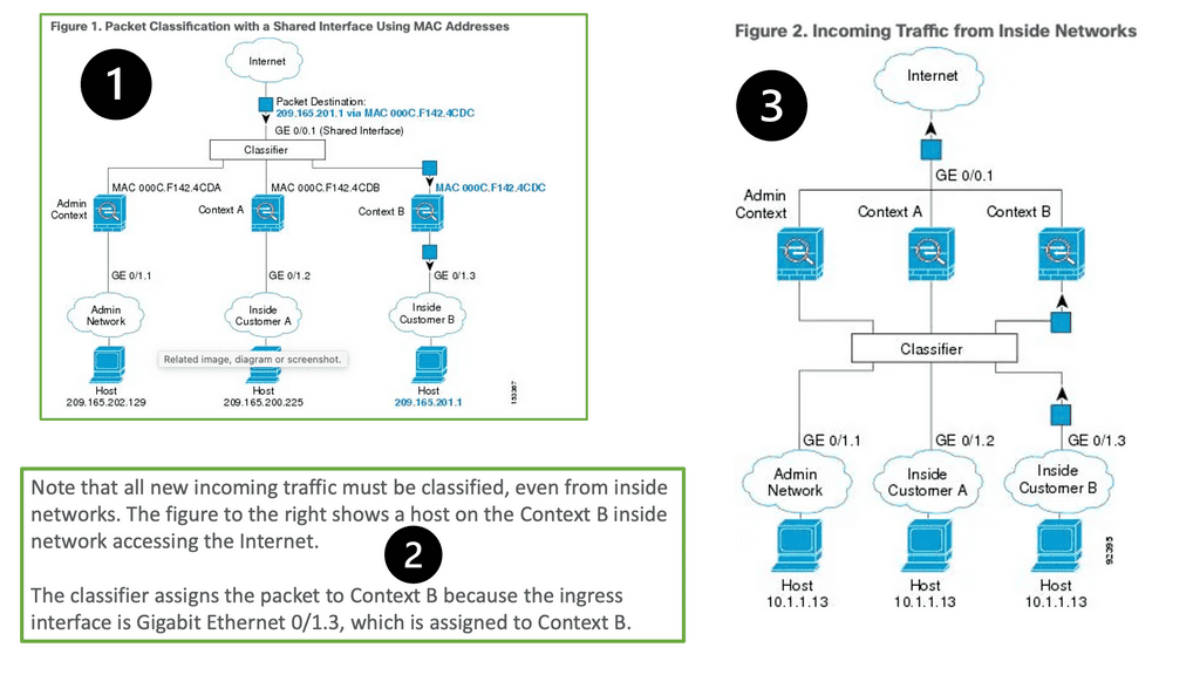
Active/Active failover allows both units to pass network traffic, allowing you to configure load balancing on your network. It is only available on units running in multiple context modes.
-Active/Standby failover replaces one unit with an active unit and one with a standby unit. Performing active/standby failover on single context or multiple context units is possible.
Stateful and stateless failover configurations are both supported.
Recap: Cisco ASA Failover Modes
Active/Standby Failover: The primary unit handles traffic in this mode while the secondary unit remains in standby mode. If the primary unit fails, the secondary unit takes over, assuming the active role.
Active/Active Failover: With active/active failover, both units handle traffic simultaneously, effectively load-balancing the network traffic between them. In the event of a failure, the surviving unit takes over the traffic of the failed unit.
Benefits of Cisco ASA Failover
Enhanced Network Uptime: Organizations can achieve uninterrupted network connectivity with Cisco ASA failover. In the event of a primary unit failure, the secondary unit seamlessly takes over, ensuring minimal disruption to network operations.
Improved Scalability: Failover setup allows for easy scalability, as additional units can be added to the configuration. This helps accommodate growing network demands without compromising on security or performance.
Load Balancing: Cisco ASA failover enables load balancing, distributing incoming network traffic across multiple units. This optimizes resource utilization and prevents any single unit from becoming overloaded.
Failover Capabilities
The Cisco ASA failover enables firewall failover and offers the following:
Link High Availability: A generic solution achieved by dynamic routing running between interfaces. Dynamic routing enables rerouting around failures. ASA offers up to three equal-cost routes per interface to the same destination network. However, it does not support ECMP ( Equal Cost Multipath ) on multiple interfaces.
Reliable static routing with IP SLA instance: Redundancy achieved through enhanced object tracking and floating static routes.
Redundancy interface: Bind multiple physical interfaces together into one logical interface. It is not the same as EtherChannel. One interface is active and forwarding at any time, unlike EtherChannel, which can forward over all interfaces in a bundle. ASA redundancy interface is an active / standby technology; one interface is active, and the other is on standby.
Node Availability: Firewall Failover, which is the focus of this post.
Related: Before you proceed, you may find the following helpful:
- Context Firewall
- Stateful Inspection Firewall
- Data Center Failover
- Virtual Data Center Design
- GTM Load Balancer
- Virtual Device Context
ASA Failover Key ASA Failover Discussion Points: Introduction to ASA failover and what is involved. Highlighting the details of the different types of failover modes. Critical points on the failover link. Technical details on the challenges with asymmetric routing. A final note on ASA health monitoring.
Back to Basics: Cisco ASA Failover
Stateful inspection Firewalls
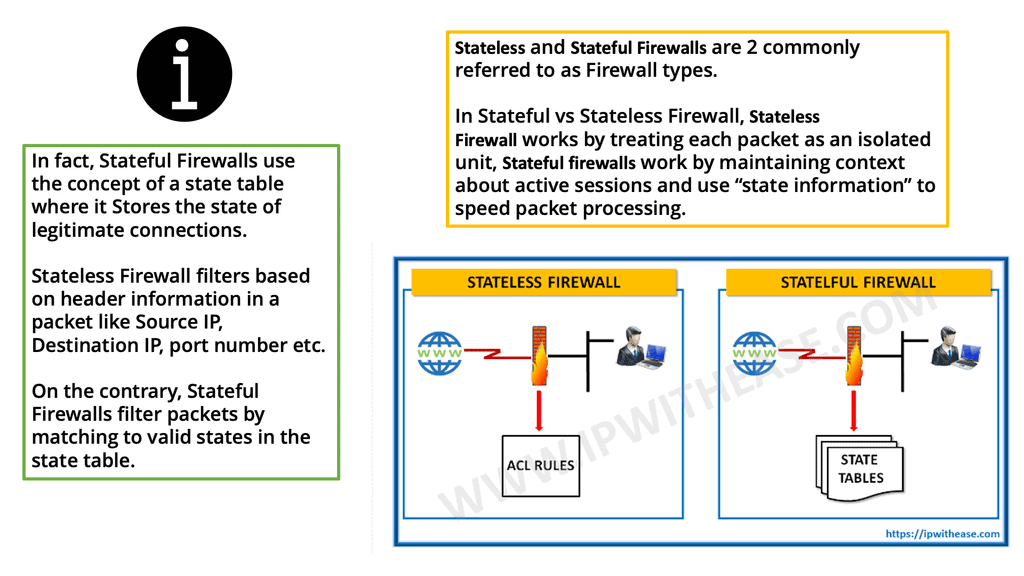
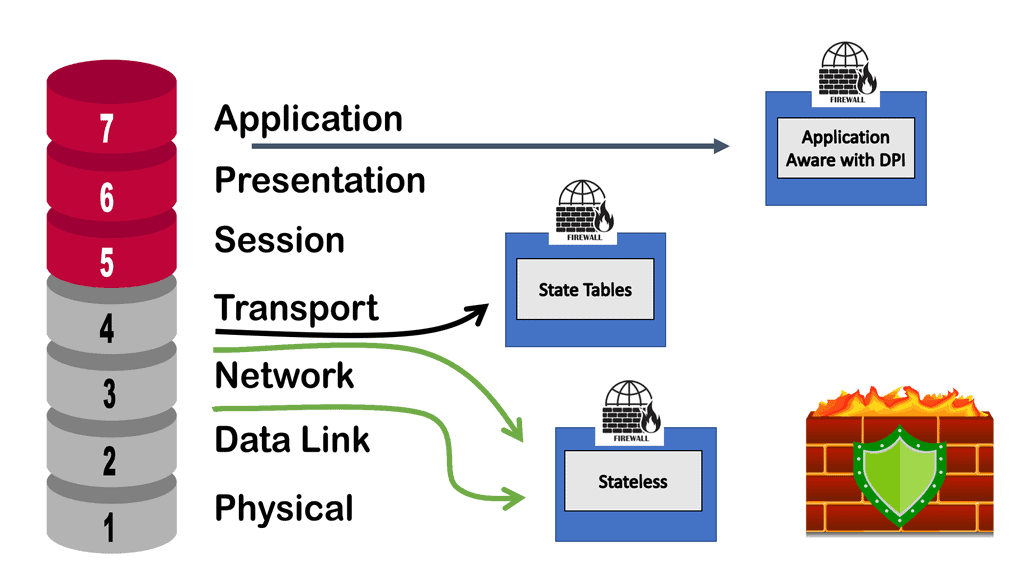
Stateful inspection firewalls are network security devices operating at the OSI model’s network layer (Layer 3). Unlike traditional packet-filtering firewalls, which only examine individual packets, stateful inspection firewalls analyze the context and state of network connections. By maintaining a state table, these firewalls can decide which packets to allow or block based on the connection’s history and the application-layer protocols being used.
Compared to simple packet-filtering firewalls, stateful inspection firewalls offer enhanced benefits. They track every packet passing through their interfaces and verify that every packet is a good, established connection. In addition to the packet header contents, they examine the application layer information within the payload. The firewall can then be configured to permit or deny traffic based on specific payload patterns.
A stateful firewall, such as the Cisco ASA, goes beyond traditional packet-filtering firewalls by inspecting and maintaining context-aware information about network connections. It examines the entire network conversation, not just individual packets, to make informed decisions about allowing or blocking traffic. This approach provides enhanced security and helps prevent malicious attacks.
Generic failover information
Failover is an essential component of any high-availability system, as it ensures that the system will remain operational and provide services even when the primary system fails. When a system fails, the failover system will take over, allowing operations to continue with minimal interruption.
Several types of failover systems are available, such as active/passive, active/active, and cluster-based. Each type has its advantages and disadvantages, and the type of system used should be determined based on the system’s specific requirements.
Configuring Cisco ASA Failover
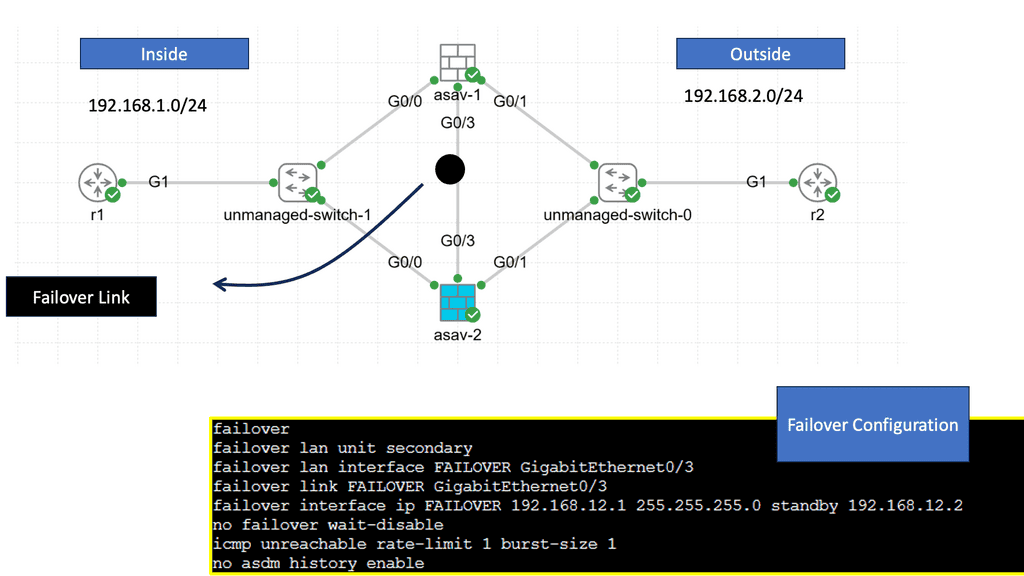
Hardware Requirements: To implement Cisco ASA failover, organizations need compatible hardware, including two ASA appliances, a dedicated failover link, and, optionally, a stateful failover link.
Failover Configuration: Setting up Cisco ASA failover involves configuring both units’ interfaces, IP addresses, and failover settings. Proper planning and adherence to best practices are crucial to ensure a seamless failover setup.
1st Lab Guide Cisco ASA firewall and NAT
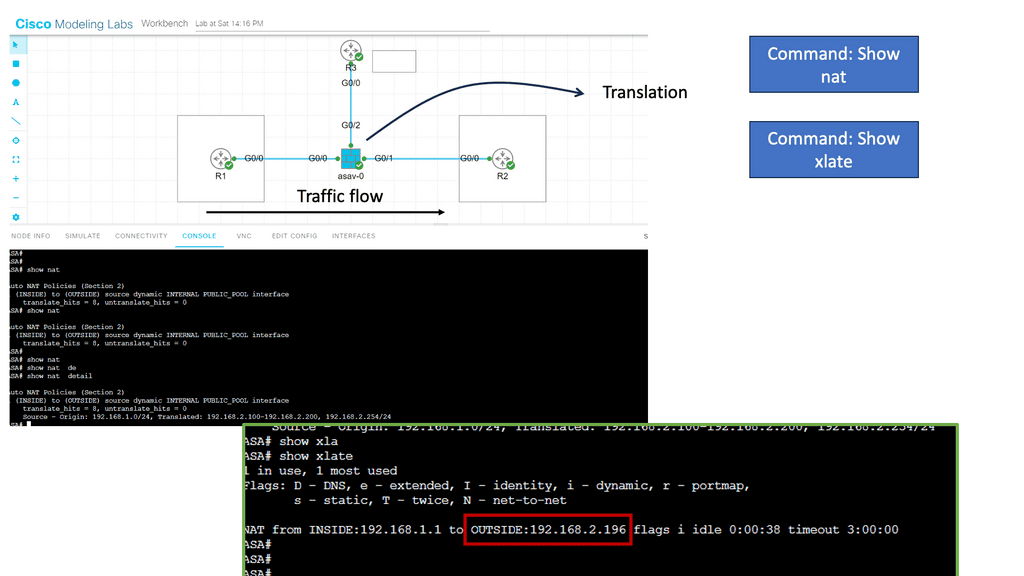
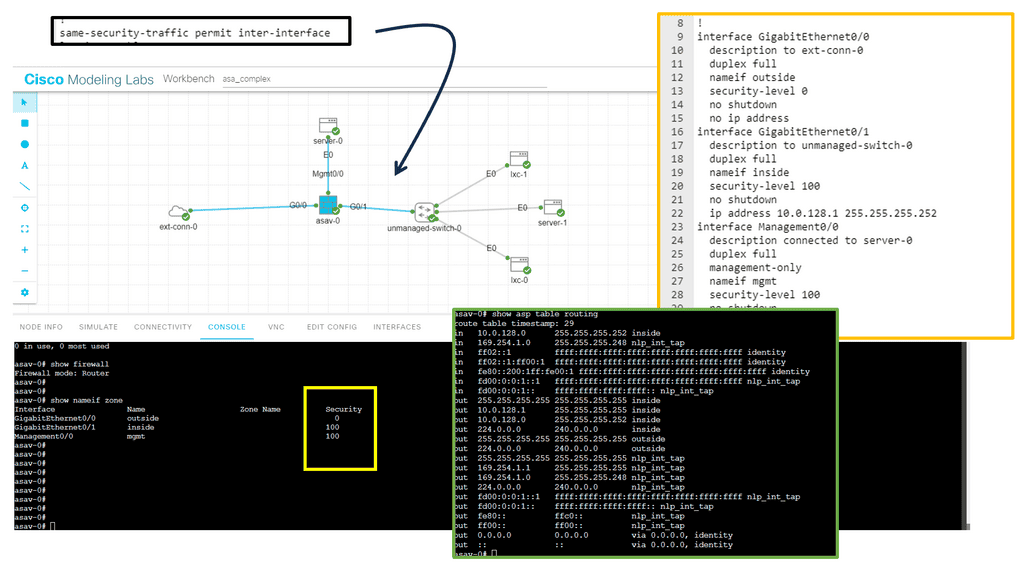
In the following lab guide, we have a typical firewall setup. There are inside, outside, and DMZ networks. These security zones govern how traffic flows by default. For example, the interface connected to R2 is the outside, and R1 is the inside. So, by default, traffic cannot flow from Outside to Inside. In this lab, we demonstrate NAT, where traffic from Inside to Outside is NATD. View the output below in the screenshots.
Network Address Translation (NAT) modifies network address information in IP packet headers while in transit across a traffic routing device. NAT plays a crucial role in conserving IP addresses, enabling multiple devices within a private network to share a single public IP address. Additionally, NAT provides an extra layer of security by hiding internal IP addresses and making them inaccessible from external sources.
By combining ASA Firewall with NAT, organizations can achieve enhanced security and network optimization. The benefits include:
1. Enhanced Security: ASA Firewall protects networks from unauthorized access, malware, and other cyber threats. NAT adds an extra layer of security by concealing internal IP addresses, making it difficult for attackers to target specific devices.
2. IP Address Conservation: NAT allows organizations to conserve public IP addresses by using private IP addresses internally. This is particularly useful in scenarios where the number of available public IP addresses is limited.
3. Increased Network Flexibility: ASA Firewall and NAT enable organizations to establish secure connections between network segments, ensuring controlled access and improved network flexibility.
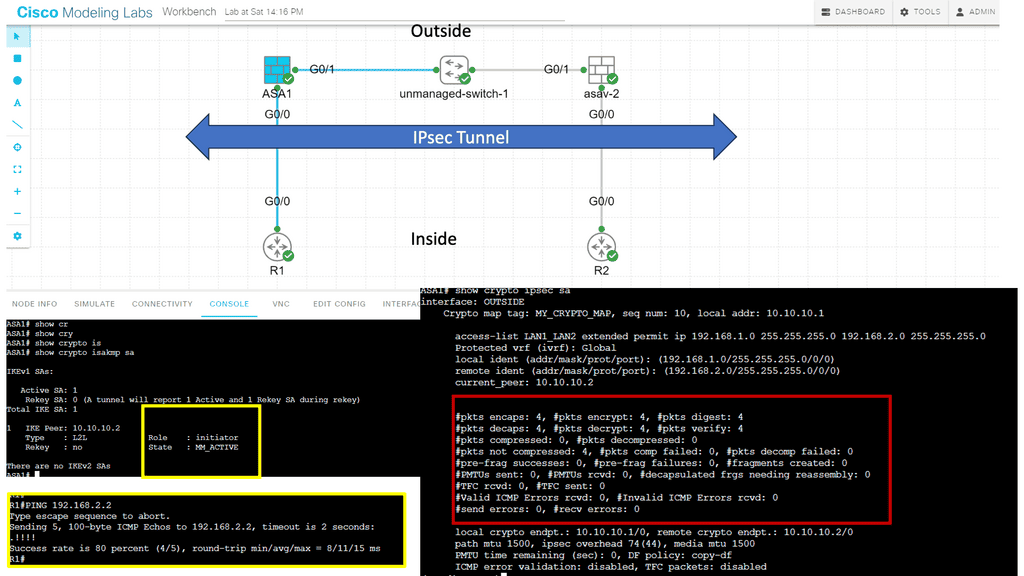
2nd Lab guide on ASA failover:
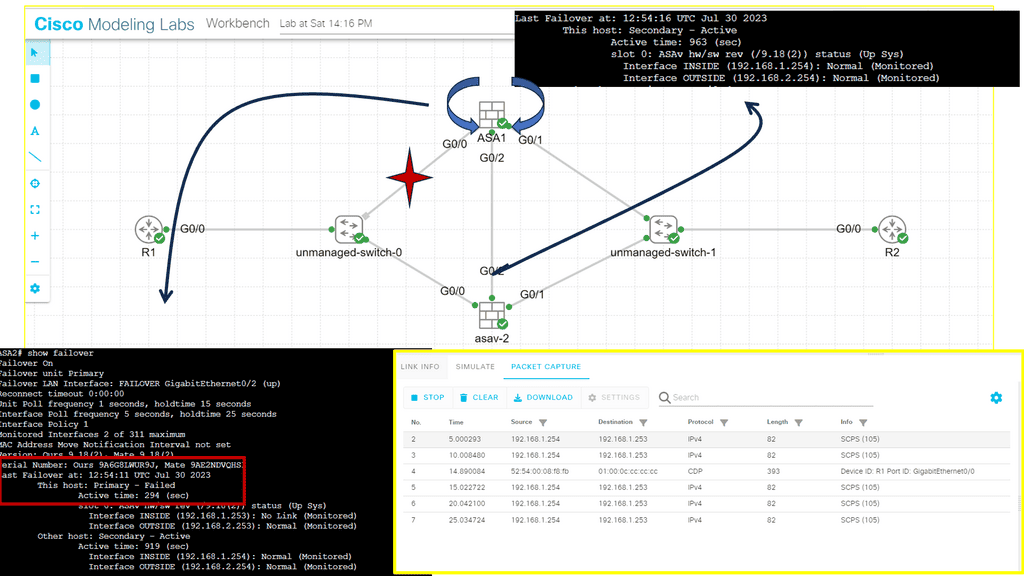
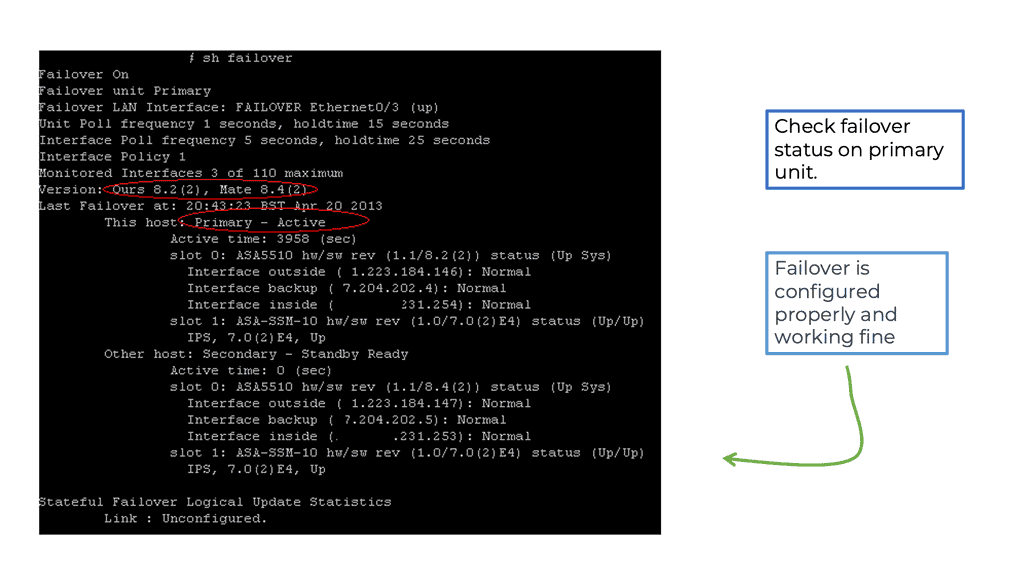
In this lab, we will address the Active / Standby ASA configuration. We know that the ASA supports active/standby failover, which means one ASA becomes the active device and handles everything while the backup ASA is the standby device. For something to happen, there needs to be a failure event.
In our example, ASA1 is ( was ) the primary, and ASA2 is the standby. I disconnected the switch links connected to Gi0//0 on ASA1, triggering the failover event. The screenshot shows the SCPS protocol exchanged between the two ASA nodes. The hello packets are exchanged between active and standby to detect failures using messages sent using IP protocol 105. IP protocol 105 refers to SCPS (Space Communications Protocol Standards).”
The failover mechanism is stateful, meaning the active ASA sends all stateful connection information to the standby ASA. This includes TCP/UDP states, NAT translation tables, ARP tables, and VPN information.
Highlighting Cisco ASA Failover
The Cisco ASA failover is the high availability mechanism that mainly provides redundancy rather than capacity scaling. While Active/Active failover can help distribute traffic load across a failover pair or devices, its scalability has significant practical implications. With this design, we can leverage failover to group identical ASA appliances or modules into a fully redundant firewall entity with centralized configuration management and stateful session replication ( if needed ).
When one unit in the failover pair can no longer pass transit traffic, its identical peer seamlessly assumes firewall functionality with minimal impact on traffic flows. This type of firewalling design is helpful for an active active data center design.
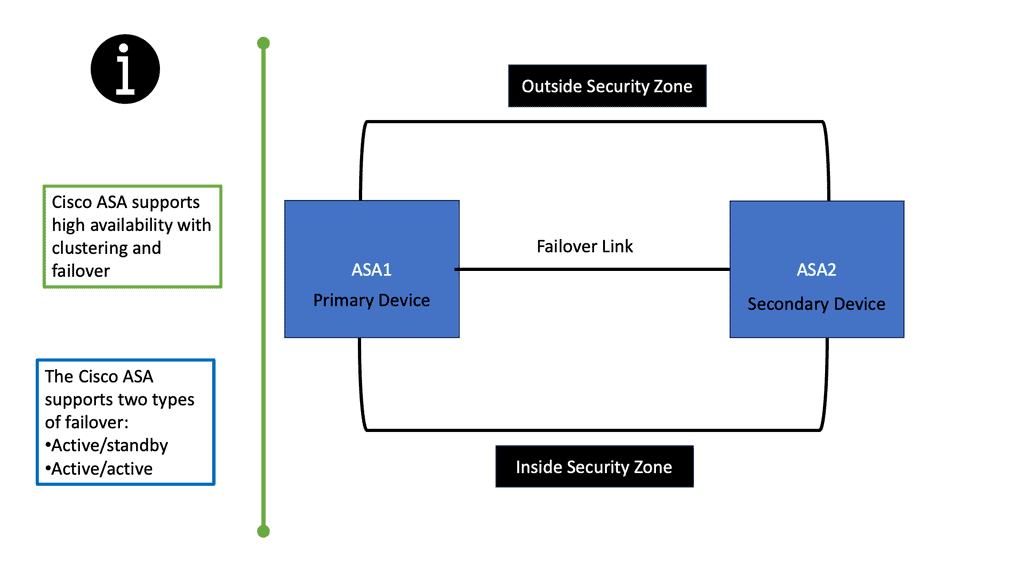
Unit Roles and Functions in Firewall Failover
If configuring a firewall failover pair, designate one unit as primary and the other as secondary. The roles are statically configured and do not change during failover. The failover subsystem could use this designation to resolve some operational conflicts. Still, either the primary or secondary units may pass transit traffic while in an active role while their peers remain on standby. Depending on the operational state of the failover pair, dynamic active and standby roles pass between the statically defined primary and secondary units.
3rd Lab Guide: ASA Failover
Cisco ASA firewalls are often essential network devices. Our company uses them for (remote access) VPNs, NAT/PAT, filtering, and more. Since they’re so important, having a second ASA if the first fails is a good idea.
It supports active/standby failover, which means one ASA is the active device, handling everything, while the backup ASA is the standby. Without a failing active ASA, it doesn’t do anything.
Stateful failover means all stateful connection information is sent from the active ASA to the standby ASA. It includes TCP/UDP states, NAT translation tables, ARP tables, and VPN information.
Your users won’t notice anything if the active ASA fails because the standby ASA has all the connection information…
If you want to use failover, you must meet the following requirements:
- The platform must be the same, for example, 2x ASA 5510 or 2x ASA 5522.
- Hardware must be identical: same number and type of interfaces. There must be the same amount of flash memory and RAM.
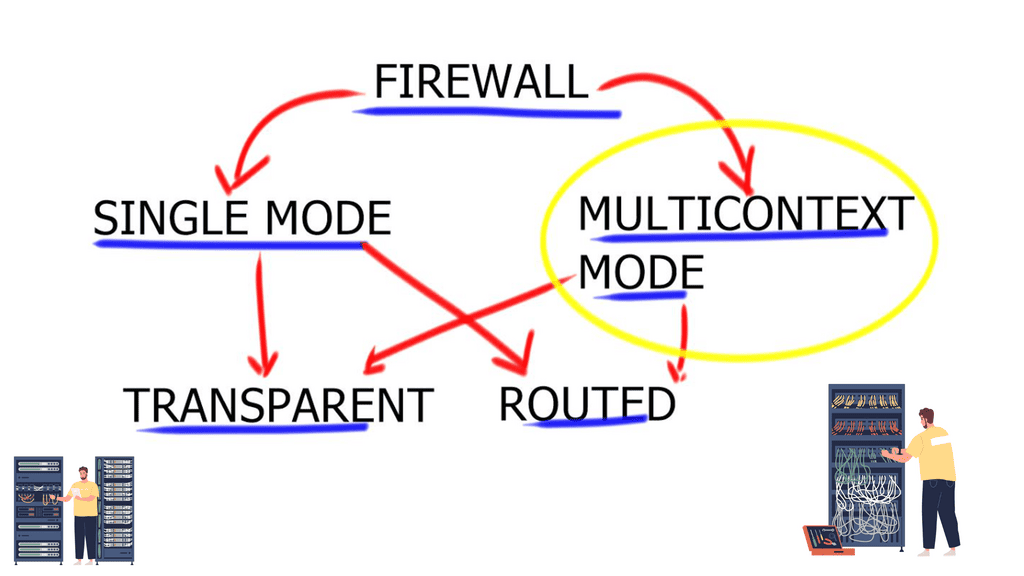
- There are two operating modes: routed and transparent and single and multiple contexts.
- The license must be the same, including the number of VPN peers, encryption, etc.
- License correctly issued. ASA 5510 is an example of a “lower” model that requires Security Plus licenses for failover
Adaptive Security Appliance: ASA Failover
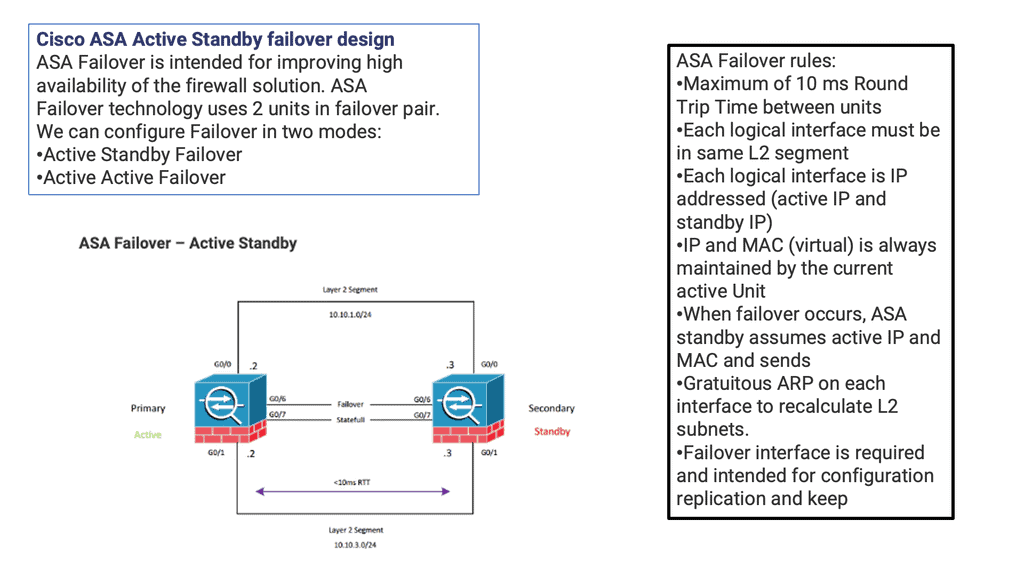
A failover group for ASA’s high availability consists of identical ASAs connected via a dedicated failover link and an optional state link. Two failover modes, Active / Standby or Active / Active, work in Routed and Transparent modes. Depending on the IOS version, you can use a mixture of routed and transparent modes per context.
There are two types of Cisco ASA failover: Active/Standby failover and Active/Active failover.
Active / Standby
In an Active/Standby failover configuration, the primary unit handles all traffic while the secondary unit remains idle, continuously monitoring the primary unit’s status. If the primary unit fails, the secondary unit becomes the new active unit. This failover process occurs seamlessly, ensuring uninterrupted network connectivity and minimal downtime.
Active / Standby: One-forwarding path and active ASA. The standby forwards traffic when the active device fails over. Traffic is not evenly distributed over both units. Active / standby uses single or multiple context modes. Failover allows two firewall units to operate in hot standby mode.
For two units to operate as a firewall failover pair, their hardware and software configurations must be identical (flash disk and minor software version differences are allowed for zero downtime upgrade of a failover pair). One firewall unit is designated as primary and another as secondary, and by default, the primary unit receives the active role, and the secondary receives the standby role.
Active / Active for context groups
Active/Active failover, as the name suggests, allows both Cisco ASA firewalls to handle network traffic simultaneously actively. Each firewall can have its own set of interfaces and IP addresses, providing load balancing and increased throughput. In a failure, the remaining active firewall takes over the failed unit’s responsibilities, ensuring uninterrupted network services.
Active / Active for context groups: This feature is not supported in single context mode and is only available in multiple context mode. When configuring failover, it is mandatory to set both firewalls in single or multiple context modes simultaneously, with multiple context modes supporting a unique failover function known as Active/Active failover.
With Active/Active failover, the primary unit is active for the first group of security contexts and standby for the second group. In contrast, the secondary unit is active for the second group and standby for the first group. Only two failover groups are supported because only two ASAs are within a failover pair, and the admin context is always a group one member.
Both ASAs forward simultaneously by splitting the context into logical failover groups. Still, technically active / standby. It is not like the Gateway Load Balancing Protocol ( GLBP ). Two units do not forward for the same context at the same time.
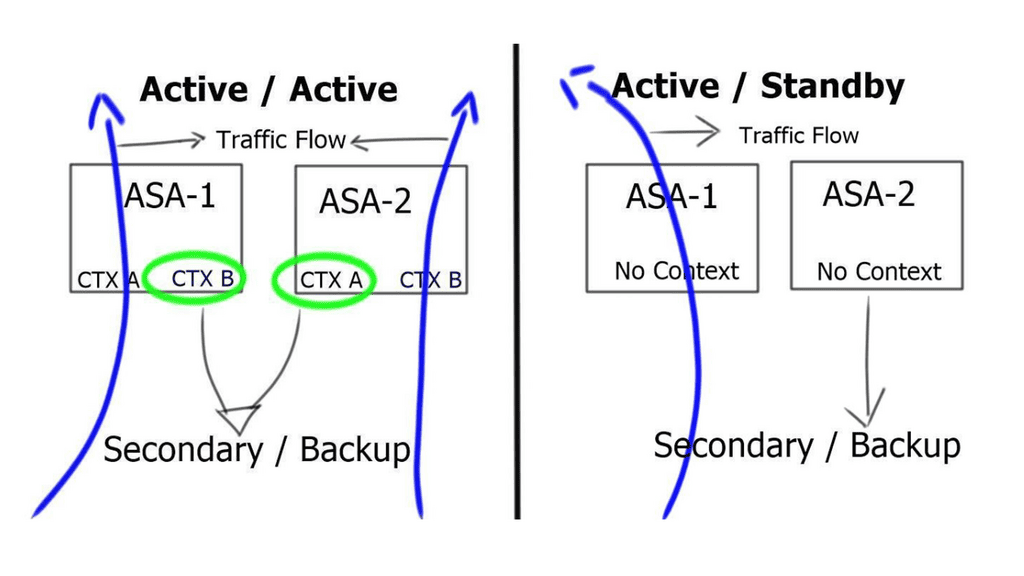
It permits a maximum of two failover groups. For example, one group was active on the primary ASA, and another was active on the secondary ASA. Active / Active failover occurs in a group and not on a system basis.
Upon failover event, either by primary unit or context group failure, the secondary takes over the primary IP and Media Access Control Address ( MAC ) address and begins forwarding traffic immediately. The failover event is seamless; no change in IP or MAC results in zero refreshes to Address Resolution Protocol ( ARP ) tables at Layer 3 hosts. If the failover changed MAC addresses, all other Layer 3 devices on the network would have to flush their ARP tables.
ASA high availability: Type of firewall failover
For ASA high availability, there are two types of failovers are available
- Stateful failover and
- Stateless failover.
Cisco ASA Failover: Stateless failover
The default mode is Stateless; no state/connection information is maintained, and upon failover, existing connections are dropped and must be re-established. It uses a dedicated failover link to poll each other. Upon failover, which can be manual or detected, the unit changes roles, and standby assumes the IP and MAC of the primary unit.
Cisco ASA Failover: Stateful failover
Failover operates statelessly by default. The active unit only synchronizes its configuration with the standby device in this configuration. After a failover event, all stateful flow information remains local to the active ASA, so all connections must be re-established. In most high-availability configurations, stateful failover is required to preserve ASA processing resources. You must configure a stateful failover link to communicate state information to the standby ASA, as discussed in the “Stateful Link” section. When stateful replication is enabled, an active ASA synchronizes the following additional information to the standby peer.
Stateful table for TCP and UDP connections. Certain short-lived connections are not synchronized by default by ASA to preserve processing resources. For example, unless you configure the failover replication http command, HTTP connections over TCP port 80 remain stateless.
In the same way, ICMP connections synchronize only in Active/Active failover scenarios with configured Asymmetric Routing (ASR) groups. The maximum connection setup rate supported by the particular ASA platform may be reduced by up to 30 percent when stateful replication is enabled for all connections.
ASA stateful failover: Pass state/connection
Stateful failover: Both units pass state/connection information to each other. Connection information could be Network Address Translation ( NAT ) tables, TCP / UDP connection states, IPSEC SA, and ARP tables. The active unit constantly replicates the state table. Whenever a new connection is added to the table, it’s copied to the standby unit. It is processor-intensive, so you need to understand the design requirements.
Does your environment need stateful redundancy? Does it matter if users must redial or establish a new AnyConnect session? Stateful failover requires a dedicated “stateful failover link.” The stateless failover link can be used, but separating these functions is recommended.
Dynamic routing protocols are maintained with stateful failover. The routes learned by the active unit are carried across to the Routing Information Base ( RIB ) table on the standby unit. However, hypertext Transfer Protocol ( HTTP ) connections are short-lived, and HTTP clients usually retry failed connection attempts. As a result, by default, the HTTP state is not replicated. The command failover replication HTTP enables HTTP connections in replication.
Firewall Failover Link
The failover link is for Link-Local communication between ASAs and determines the status of each ASA. Layer 2 polling via HELLO Keepalives transmitted and configurations synchronized. Have the connecting switch ports in port fast mode, ensuring if a flap of the link occurs, no other Layer 2 convergence will affect the failover convergence.
For redundancy purposes, use port channels and do not use the same link for stateless connectivity. It is recommended that the failover and data links be connected through different physical paths. Failover links should not use the same switch as the data interfaces, as the state information may generate excessive traffic. In addition, you don’t want the replication of the state information to interfere with normal Keepalives.
Failover link connectivity
The failover link can be connected directly or by an Ethernet switch. If the failover link connects via an ethernet switch, use a separate VLAN with no other devices in that Layer 2 broadcast domain. ASA supports Auto-MDI/MDIX, enabling crossover or straight-through cable. MDI-MDIX automatically detects the cable type and swaps transmit/receive pairs to match the cable seen.
ASA’s high availability and asymmetric routing
Asymmetric routing means that a packet does not follow the same logical path both ways (outbound client-to-server traffic uses one path, and inbound server-to-client uses another path). Because firewalls track connection states and inspect traffic, asymmetric routing is not firewall-friendly by default, traffic is dropped, and TCP traffic is significantly affected.
The problem with asymmetric traffic flows is that if ASA receives a packet without connection/state information, it will drop it. The issue may arise in the case of an Active / Active design connected to two different service providers. It does not apply to Active / Standby as the standby is not forwarding traffic and, as a result, will not receive returning traffic sent from the active unit. It is possible to allow asymmetrically routed packets by assigning similar interfaces to the same ASR group.
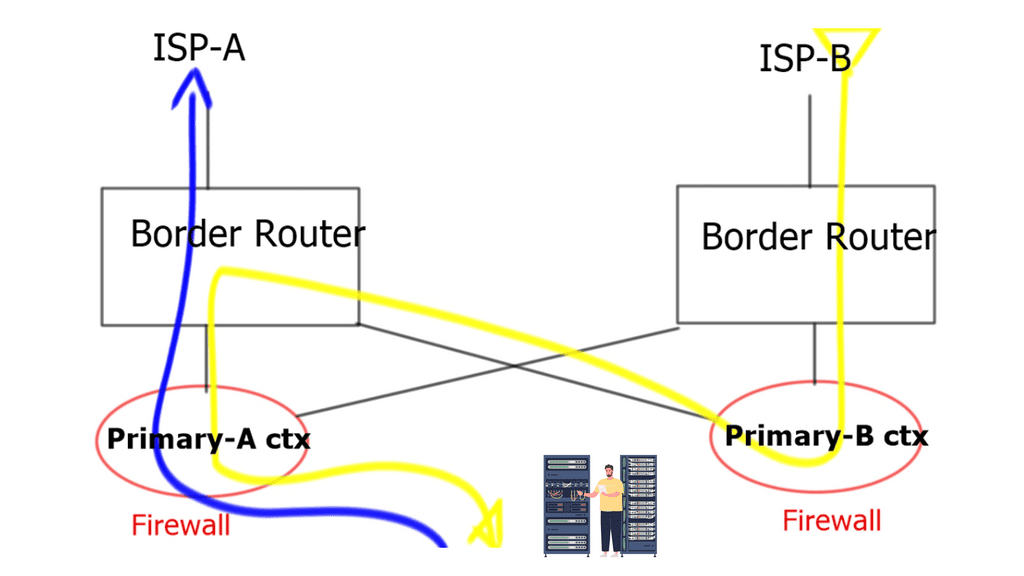
ASA Failover and Traffic Flow Considerations
|
Stateful failover and HTTP replication are required.
Although in all real deployments, you should avoid asymmetric routing (with or without a firewall in the path), there are certain cases when this is required or when you need more control. If a firewall is in the path, there are several options to still allow traffic through:
- If outbound traffic transits the firewall, but inbound traffic does not, use TCP state bypass for the respective connection or use static NAT with nailed option (effectively disables TCP state tracking and sequence checking for the connection).
- If both outbound and inbound traffic transit the firewall but on different interfaces, use the exact solutions as above.
- If outbound traffic transits one context of the ASA and inbound traffic transits another context of the ASA, use ASR groups; this applies only for multi-context mode and requires active-active stateful failover configured.
Unit Monitoring
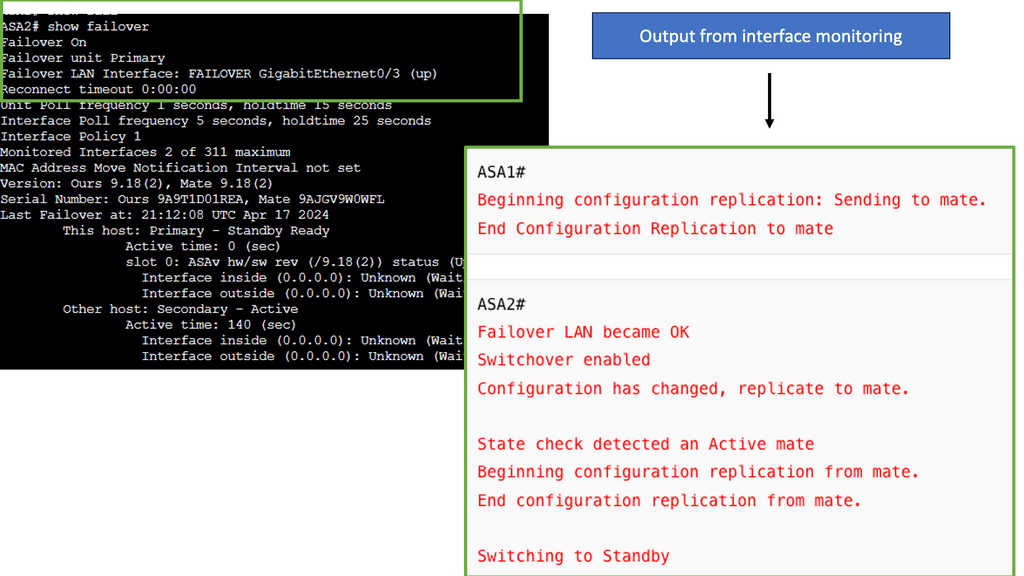
The failover link determines the health of the overall unit. HELLO packets are sent over the failover link. The lack of three consecutive HELLOs causes ASA to send an additional HELLO packet out of ALL data interfaces, including the failover link, ruling out the failure of the actual failover link.
The ASA’s action depends on the additional HELLO packets. No action occurs if a response is received over the failover or data links, and failover actions occur if no response is received on any of the links. With interface monitoring, the number of monitored interfaces depends on the IOS version. It would help if you always tried to monitor essential interfaces.
A final note on ASA’s high availability: In an IPv6 world, ASA uses IPv6 neighbor discovery instead of ARP for its health monitoring tests. If it has to broadcast to all nodes, it uses IPv6 FE02::1. FE02::1 is an all-IPv6 speakers-multicast group.
Recap: Benefits of Cisco ASA Failover:
Implementing Cisco ASA failover provides several benefits, including:
1. High Availability: Failover ensures continuous network connectivity and security, even in the event of hardware failures or other issues. This enhances the network’s overall availability and minimizes the impact of potential disruptions.
2. Redundancy: By having a secondary unit ready to take over, failover provides redundancy and eliminates single points of failure. This ensures that network services remain uninterrupted and minimizes the risk of downtime.
3. Enhanced Performance: Active/Active failover allows both firewalls to handle network traffic simultaneously, leading to increased throughput and improved performance. This is particularly beneficial for organizations with high network traffic demands.
4. Simplified Maintenance: With failover, organizations can perform maintenance tasks on one firewall without impacting network services. The secondary unit takes over during maintenance, ensuring continuous network operation.
Summary: ASA Failover
In today’s fast-paced digital landscape, network downtime can be catastrophic for businesses. As companies rely heavily on their network infrastructure, having a robust failover mechanism is crucial to ensure uninterrupted connectivity. In this blog post, we delved into the world of ASA failover and explored its importance in achieving network resilience and high availability.
Section 1: Understanding ASA Failover
ASA failover refers to the capability of Cisco Adaptive Security Appliances (ASAs) to automatically switch to a backup unit in the event of a primary unit failure. It creates a seamless transition, maintaining network connectivity without any noticeable interruption. ASA failover operates in Active/Standby and Active/Active modes.
Section 2: Active/Standby Failover Configuration
In an Active/Standby failover setup, one ASA unit operates as the active unit, handling all traffic. In contrast, the standby unit remains hot, ready to take over instantly. This configuration ensures network continuity even if the active unit fails. The standby unit constantly monitors the health of the active unit, ensuring a swift failover when needed.
Section 3: Active/Active Failover Configuration
Active/Active failover allows both ASA units to process traffic simultaneously, distributing the load and maximizing resource utilization. This configuration is ideal for environments with high traffic volume and resource-intensive applications. In a failure, the remaining active unit seamlessly takes over the entire workload, offering uninterrupted connectivity.
Section 4: Configuring ASA Failover
Configuring ASA failover involves several steps, including interface and IP address configuration, failover link setup, and synchronization settings. Cisco provides a comprehensive set of commands to configure ASA failover efficiently. Following best practices and thoroughly testing the failover configuration is essential to ensure its effectiveness during real-world scenarios.
Section 5: Monitoring and Troubleshooting Failover
Proactive monitoring and regular testing are essential to maintain the reliability and effectiveness of ASA failover. Cisco ASA provides various monitoring tools and commands to monitor failover status, track synchronization, and troubleshoot any issues that may arise. Establishing a monitoring routine and promptly address any detected problems to prevent potential network disruptions is crucial.
Conclusion:
ASA failover is a critical component of network resilience and high availability. By implementing an appropriate failover configuration, organizations can minimize downtime, ensure uninterrupted connectivity, and provide a seamless experience to their users. Whether it is Active/Standby or Active/Active failover, the key lies in proper configuration, regular monitoring, and thorough testing. Invest in ASA failover today and safeguard your network against potential disruptions.