Brownfield Network Automation
In today's rapidly advancing technological landscape, the efficient management and automation of networks has become crucial for businesses to thrive. While greenfield networks are often designed with automation in mind, brownfield networks present a unique set of challenges. In this blog post, we will explore the world of brownfield network automation, its benefits, implementation strategies, and the future it holds.
Brownfield networks refer to existing networks that have been established over time, typically with a mix of legacy and modern infrastructure. These networks often lack the built-in automation capabilities of newer networks, making the implementation of automation a complex endeavor.
Automating brownfield networks brings forth numerous advantages. Firstly, it enhances operational efficiency by reducing manual interventions and human errors. Secondly, it enables faster troubleshooting and improves network reliability. Additionally, automation allows for better scalability and prepares networks for future advancements.
Implementing automation in brownfield networks requires a systematic approach. Firstly, a comprehensive network assessment should be conducted to identify existing infrastructure, equipment, and protocols. Next, a phased approach can be taken, starting with low-risk areas and gradually expanding automation to critical components. It is crucial to ensure seamless integration with existing systems and thorough testing before deployment.
Automation in brownfield networks can face challenges such as outdated equipment, incompatible protocols, and lack of standardized documentation. To overcome these obstacles, a combination of hardware and software upgrades, protocol conversions, and meticulous planning is essential. Collaboration among network engineers, IT teams, and vendors is also crucial to address these challenges effectively.
As technologies like Software-Defined Networking (SDN) and Network Function Virtualization (NFV) continue to evolve, brownfield network automation is poised for significant advancements. The integration of artificial intelligence and machine learning will further streamline network operations, predictive maintenance, and intelligent decision-making.
Brownfield network automation opens up a world of possibilities for businesses seeking to optimize their existing networks. Despite the challenges, the benefits are substantial, ranging from increased efficiency and reliability to future-proofing the infrastructure. By embracing automation, organizations can unlock the full potential of their brownfield networks and stay ahead in the ever-evolving digital landscape.Matt Conran
Highlights: Brownfield Network Automation
### The Challenges of Automation
Automating brownfield networks presents unique challenges. Unlike greenfield projects, where you start from scratch, brownfield automation must work within the constraints of existing systems. This includes dealing with legacy hardware that may not support modern protocols, software that lacks API integration, and a complex web of dependencies that have built up over time. Identifying these challenges early is crucial for any successful automation project.
### Strategies for Successful Automation
To tackle these challenges, businesses need a strategic approach. This often involves conducting a thorough audit of the existing network to understand its current state and dependencies. Once this is completed, companies can start by implementing automation in less critical areas, gradually expanding as they refine their processes. This incremental approach helps in mitigating risks and allows for testing and optimization before full-scale deployment. Leveraging modern tools such as network controllers and orchestration platforms can simplify this process.
### The Role of Artificial Intelligence
Artificial Intelligence (AI) is playing a significant role in the automation of brownfield networks. By utilizing AI, businesses can predict network issues before they occur, optimize resource allocation, and enhance overall network performance. AI-driven analytics provide insights that were previously inaccessible, allowing for more informed decision-making. As AI technology continues to evolve, its integration into brownfield automation strategies becomes not only beneficial but essential.
Understanding Brownfield Networks
Brownfield networks refer to existing network infrastructures that have been operating for some time. These networks often consist of legacy and modern components, making automation complex. However, the right approach can transform brownfield networks into agile and automated environments.
Automating brownfield networks offers numerous advantages. Firstly, it streamlines network management processes, reducing human errors and increasing operational efficiency. Secondly, automation enables quicker troubleshooting and problem resolution, minimizing downtime and enhancing network reliability. Additionally, brownfield network automation allows easier compliance with security and regulatory requirements.
While the benefits are substantial, implementing brownfield network automation does come with its fair share of challenges. One major hurdle is integrating legacy systems with modern automation tools. Legacy systems often lack the necessary APIs and standardization required for seamless automation. Overcoming this challenge necessitates careful planning, testing, and potentially using intermediary solutions.
Strategies for Successful Implementation:
A systematic approach is crucial to successfully implementing brownfield network automation. Thoroughly assess the existing network infrastructure, identifying areas that can benefit the most from automation. Prioritizing automation tasks and starting with smaller, manageable projects can help build momentum and demonstrate the value of automation to stakeholders. Collaboration between network engineers, automation experts, and stakeholders is critical to ensuring a smooth transition.
Implementing brownfield network automation may face resistance from stakeholders comfortable with the status quo. Clear communication about automation’s benefits and long-term vision is vital to overcome this. Demonstrating tangible results through pilot projects and showcasing success stories from early adopters can help build trust and gain buy-in from decision-makers.
Challenges of Brownfield Automation:
Implementing network automation in a brownfield environment poses unique challenges. Legacy systems, diverse hardware, and complex configurations often hinder the seamless integration of automation tools. Additionally, inadequate documentation and a lack of standardized processes can make it challenging to streamline the automation process. However, with careful planning and a systematic approach, these challenges can be overcome, leading to significant improvements in network efficiency.
Benefits of Brownfield Network Automation:
1. Enhanced Efficiency: Brownfield Network Automation enables organizations to automate repetitive manual tasks, reducing the risk of human errors and increasing operational efficiency. Network engineers can focus on more strategic initiatives by eliminating the need for manual configuration changes.
2. Improved Agility: Automating an existing network allows businesses to respond quickly to changing requirements. With automation, network changes can be made swiftly, enabling organizations to adapt to evolving business needs and market demands.
3. Cost Savings: By automating existing networks, organizations can optimize resource utilization, reduce downtime, and improve troubleshooting capabilities. This leads to substantial operational expense savings and increased return on investment.
4. Seamless Integration: Brownfield Network Automation allows for integrating new technologies and services with existing network infrastructure. Businesses can seamlessly introduce new applications, services, and security measures by leveraging automation without disrupting existing operations.
5. Enhanced Network Security: Automation enables consistent enforcement of security policies, ensuring compliance and reducing the risk of human error. Organizations can strengthen their network defenses and safeguard critical data by automating security configurations.
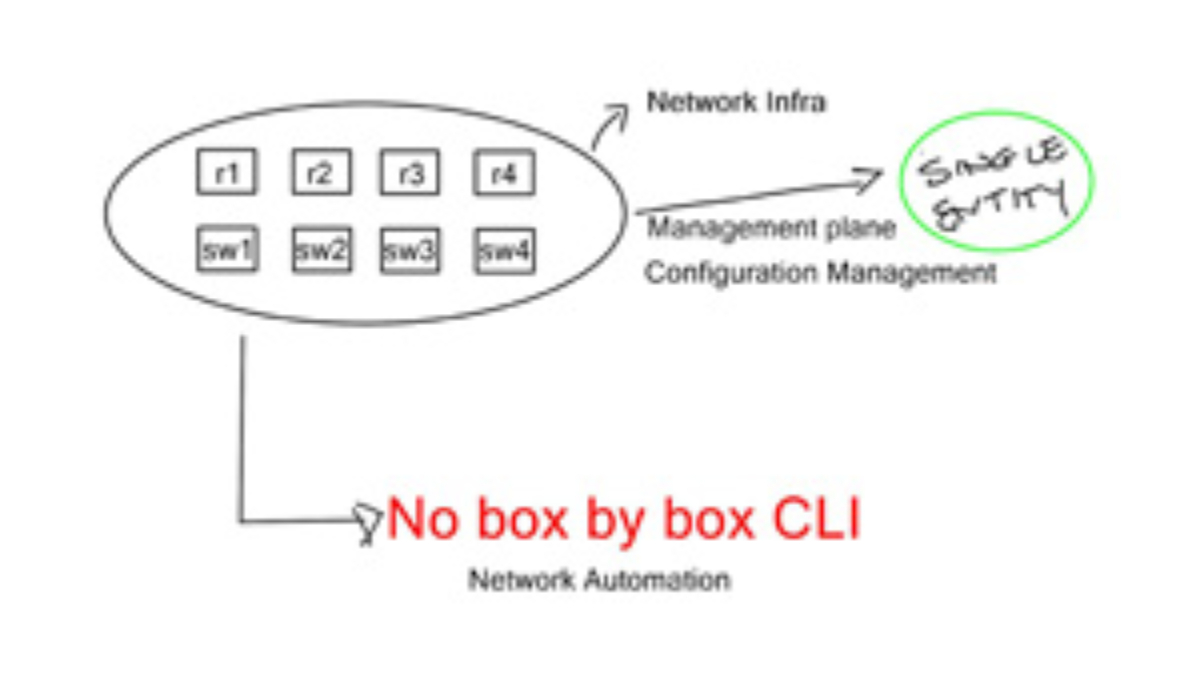
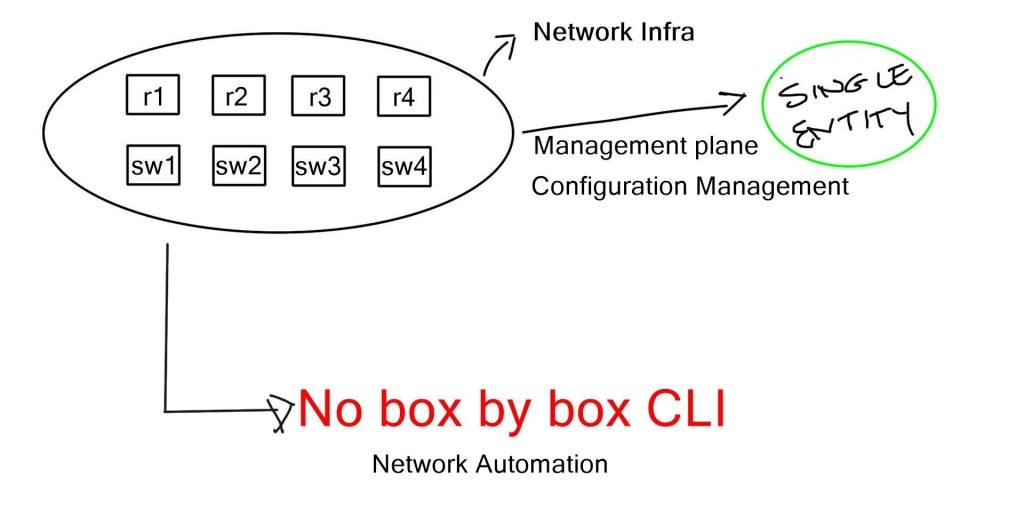
Role of automation
As a result, network devices are still configured like snowflakes (having many one-off, nonstandard configurations), and network engineers take pride in solving transport and application problems by making one-time network changes that ultimately make the network harder to maintain, manage, and automate.
Automation and management of network infrastructure should not be treated as add-ons or secondary projects. Budgeting for personnel and tools is crucial. It is common for tooling to be cut first during budget shortages.
**Deterministic outcomes**
An enterprise organization’s change review meeting examines upcoming network changes, their impacts on external systems, and rollback plans. Typing the wrong command can have catastrophic consequences in a world where humans use the CLI. Many different teams can work together, whether they are three-person teams, four-person teams, or fifty-person teams. Every engineer can implement that upcoming change differently. A CLI and GUI do not eliminate or reduce the possibility of error during a change control window.
The executive team will be able to achieve deterministic outcomes by automating the network, which increases the chances that the task will be completed correctly the first time by making changes manually rather than automating the network. Changing VLANs to onboard a new customer may be necessary, which requires several network changes.
**The Traditional CLI**
Software companies that build automation for network components have an assumption that traditional management platforms don’t apply to what is considered to be the modern network. Networks are complex and contain many moving parts and ways to be configured. So, what does it mean to automate the contemporary network when considering brownfield network automation? Innovation in this area has been lacking for so long until now with ansible automation.
If you have multi-vendor equipment and can’t connect to all those devices, breaking into the automation space is complex, and the command line interface (CLI) will live a long life. This has been a natural barrier to entry for innovation in the automation domain.
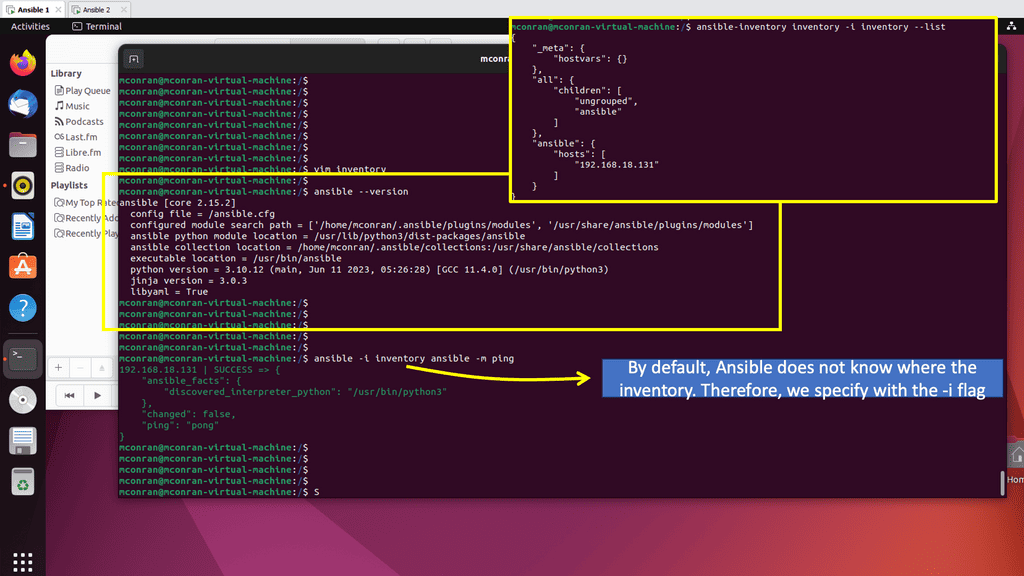
**Automation with Ansible**
But now we have the Ansible architecture using Ansible variables, NETCONF, and many other standard modeling structures that allow automation vendors to communicate to all types of networks, such as brownfield networks, greenfield networks, multi-vendor networks, etc. These data modeling tools and techniques enable an agnostic programmable viewpoint into the network.
The network elements still need to move to a NETCONF-type infrastructure, but we see all major vendors, such as Cisco, moving in this direction. Moving off the CLI and building programmable interfaces is a massive move for network programmability and open networking.
For pre-information, visit the following.
Brownfield Network Automation
Network devices have massive static and transient data buried inside, and using open-source tools or building your own gets you access to this data. Examples of this type of data include active entries in the BGP table, OSPF adjacencies, active neighbors, interface statistics, specific counters and resets, and even counters from application-specific integrated circuits (ASICs) themselves on newer platforms. So, how do we get the best of this data, and how can automation help you here?
A key point: Ansible Tower
To operationalize your environment and drive automation to production, you need everything centrally managed and better role-based access. For this, you could use Ansible Tower, which has several Ansible features, such as scheduling, job templates, and a project, that help you safely enable automation in the enterprise at scale.
Best Practices for Brownfield Network Automation:
1. Comprehensive Network Assessment: Conduct a thorough assessment of the existing network infrastructure, identifying areas that can benefit from automation and potential obstacles.
2. Standardization and Documentation: Establish standardized processes and documentation to ensure consistency across the network. This will help streamline the automation process and simplify troubleshooting.
3. Gradual Implementation: Adopt a phased approach to brownfield automation, starting with low-risk tasks and gradually expanding to more critical areas. This minimizes disruption and allows for easy troubleshooting.
4. Collaboration and Training: Foster collaboration between network engineers and automation specialists. Training the network team on automation tools and techniques is crucial to ensure successful implementation and ongoing maintenance.
5. Continuous Monitoring and Optimization: Regularly monitor and fine-tune automated processes to optimize network performance. This includes identifying and addressing any bottlenecks or issues
Brownfield Network Automation; DevOps Tools
Generally, you have to use DevOps tools, orchestrators, and controllers to do the jobs you have always done yourself. However, customers are struggling with the adoption of these tools. How do I do the jobs I used to do on the network with these new tools? That’s basically what some software companies are focused on. From a technical perspective, some vendors don’t talk to network elements directly.
This is because you could have over 15 tools touching the network, and part of the problem is that everyone is talking to the network with their CLI. As a result, inventory is out of date, network errors are common, and CMD is entirely off, so the ability to automate is restricted based on all these prebuilt silo legacy applications. For automation to work, a limited number of elements should be talking to the network. With the advent of controllers and orchestrators, we will see a market transition.
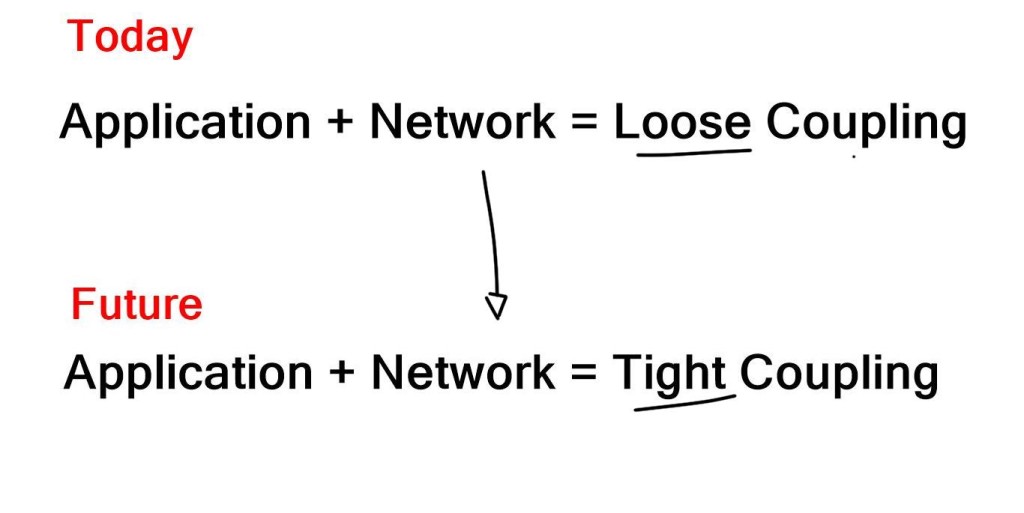
DevOps vs. Traditional
If you look back, when we went from time-division multiplexing (TDM) to Internet Protocol (IP) address, the belief is that network automation will eventually have the same impact. The ability to go from non-programmability to programmability will represent the most significant shift we will see in the networking domain.
Occasionally, architects design something complicated when it can be done in a less complex manner with a more straightforward handover. The architectural approach is never modeled or in a database. The design process is uncontrolled, yet the network is an essential centerpiece.
There is a significant use case for automating and controlling the design process. Automation is an actual use case that needs to be filled, and vendors have approached this in various ways. It’s not a fuzzy buzzword coming out of Silicon Valley. Intent-based networking? I’m sometimes falling victim to this myself. Is intent-based networking a new concept?
OpenDaylight (ODL)
I spoke to one vendor building an intent-based API on top of OpenDaylight (ODL). An intent-based interface has existed for five years, so it’s not a new concept to some. However, there are some core requirements for this to work: It has to be federated, programmable, and modeled.
Some have hijacked intent-based to a very restricted definition, and an intent-based network has to consist of highly complex mathematical algorithms. Depending on who you talk to, these mathematical algorithms are potentially secondary for intent-based networking.
One example of an architectural automation design is connecting to the northbound interface like Ansible. These act as trustworthy sources for the components under their management. You can then federate the application programming interface (API) and speak NETCONF, JSON, and YAML types. This information is then federated into a centralized platform that can provide a single set of APIs into the IT infrastructure.
So if you are using ServiceNow, you can request a through a catalog task. That task will then be patched down into the different subsystems that tie together that service management or device configuration. It’s a combination of API federation data modeling and performing automation.
The number one competitor of these automation companies is users who still want to use the CLI or vendors offering an adapter into a system. Yet, these are built on the foundation of CLIs. These adapters can call a representational state transfer (REST) interface but can’t federate it.
This will eventually break. You need to make an API call to the subsystem in real-time. As networking becomes increasingly dynamic and programmable, federated API is a suitable automation solution.
Brownfield Network Automation offers organizations a powerful opportunity to unlock the full potential of existing network infrastructure. By embracing automation, businesses can enhance operational efficiency, improve agility, and achieve cost savings. While challenges may exist, implementing best practices and taking a systematic approach can pave the way for a successful brownfield automation journey. Embrace the power of automation and revolutionize your network for a brighter future.
Summary: Brownfield Network Automation
In the ever-evolving world of technology, network automation has emerged as a game-changer, revolutionizing the way organizations manage and optimize their networks. While greenfield networks have been quick to adopt automation, brownfield networks present unique challenges with their existing infrastructure and complexities. This blog post explored the importance of brownfield network automation, its benefits, and practical strategies for successful implementation.
Understanding Brownfield Networks
Brownfield networks refer to existing network infrastructures that have been operating for some time. These networks often comprise a mix of legacy systems, diverse hardware and software vendors, and complex configurations. Unlike greenfield networks, which start from scratch, brownfield networks require a thoughtful approach to automation that considers their specific characteristics and limitations.
The Benefits of Brownfield Network Automation
Automating brownfield networks brings a plethora of benefits to organizations. Firstly, it enhances operational efficiency by reducing manual tasks, minimizing human errors, and streamlining network configurations. Automation also enables faster deployment of network services and facilitates scalability, allowing businesses to adapt swiftly to changing demands. Moreover, it improves network reliability and security by enforcing consistent configurations and proactively detecting and mitigating potential vulnerabilities.
Strategies for Successful Brownfield Network Automation
Successfully automating brownfield networks requires a well-planned approach. Here are some key strategies to consider:
1. Comprehensive Network Assessment: Begin by conducting a thorough assessment of the existing network infrastructure, identifying potential bottlenecks, legacy systems, and areas for improvement.
2. Define Clear Objectives: Establish specific automation goals and define key performance indicators (KPIs) to measure the effectiveness of the automation efforts. This clarity will guide the automation process and ensure alignment with business objectives.
3. Prioritize and Start Small: Identify critical network functions or processes that can benefit the most from automation. Start with smaller projects to build confidence, gain experience, and demonstrate the value of automation to stakeholders.
4. Choose the Right Automation Tools: Select automation tools compatible with the existing network infrastructure and provide the required functionality. Integration capabilities, ease of use, and vendor support should be key factors in the selection process.
5. Collaboration and Training: Foster collaboration between network operations and IT teams to ensure a smooth transition towards automation. Provide comprehensive training to enhance the skills of network engineers and equip them with the knowledge needed to manage and maintain automated processes effectively.
Conclusion
In conclusion, brownfield network automation holds immense potential for organizations seeking to optimize their network infrastructure. By understanding the unique challenges of brownfield networks, recognizing the benefits of automation, and implementing the right strategies, businesses can unlock improved operational efficiency, enhanced reliability, and increased agility. Embracing automation is not just a trend but a crucial step towards achieving a future-ready network infrastructure.