IDS IPS Azure
In today's rapidly evolving digital landscape, securing your Azure environment is of paramount importance. With the increasing number of cyber threats, organizations must take proactive measures to protect their assets and data. In this blog post, we will explore the significance of Intrusion Prevention Systems (IPS) and Intrusion Detection Systems (IDS) in fortifying your Azure infrastructure. Let's dive in!
To comprehend the importance of IPS and IDS, it's crucial to grasp their definitions and functionalities. An Intrusion Prevention System (IPS) is a proactive security measure designed to detect and prevent potential threats from entering your network. It acts as a shield, continuously monitoring network traffic and actively blocking any suspicious activities or malicious attempts. On the other hand, an Intrusion Detection System (IDS) focuses on identifying and alerting system administrators about potential threats or vulnerabilities in real-time.
Strengthening Azure Security with IPS: Azure's expansive cloud infrastructure requires robust security measures, and IPS plays a pivotal role in safeguarding it. By deploying an IPS solution in your Azure environment, you gain the ability to detect and prevent network-based attacks, such as Distributed Denial of Service (DDoS) attacks, brute-force attacks, and SQL injections. The IPS continuously analyzes network traffic, looking for patterns and signatures of known attacks, thereby providing an additional layer of defense to your Azure infrastructure.
Enhancing Threat Detection with IDS: While IPS focuses on proactive prevention, IDS specializes in real-time threat detection. By implementing an IDS solution in your Azure environment, you gain valuable insights into potential security breaches and anomalous activities. The IDS monitors network traffic, logs events, and raises alerts when it detects suspicious behavior or unauthorized access attempts. With IDS, you can swiftly respond to security incidents, investigate breaches, and take necessary steps to mitigate the risks.
Achieving Optimal Security with IPS and IDS Integration: To establish a comprehensive security posture in your Azure environment, combining IPS and IDS is highly recommended. While IPS acts as a robust first line of defense, IDS complements it by providing continuous monitoring and incident response capabilities. The integration of IPS and IDS empowers organizations to proactively prevent attacks, swiftly detect breaches, and respond effectively to evolving threats. This dynamic duo forms a powerful security framework that fortifies your Azure infrastructure.
Securing your Azure environment is a critical undertaking, and IPS and IDS play instrumental roles in this endeavor. Leveraging Intrusion Prevention Systems (IPS) and Intrusion Detection Systems (IDS) ensures that your Azure infrastructure remains protected against potential threats, unauthorized access attempts, and malicious activities. By integrating IPS and IDS, organizations can establish a robust security framework that maximizes threat prevention, detection, and response capabilities. Safeguard your Azure environment today and embark on a journey towards a secure cloud ecosystem.
Matt Conran
Highlights: IDS IPS Azure
### What are IDS and IPS?
Before diving into their role in Azure, it’s important to understand what IDS and IPS are. An Intrusion Detection System (IDS) is a tool or software that monitors network traffic for suspicious activity and alerts administrators when such activity is detected. On the other hand, an Intrusion Prevention System (IPS) goes a step further by not only detecting but also taking action to prevent the threat from causing harm. Both systems are integral to maintaining the integrity and security of your cloud infrastructure.
### Implementing IDS and IPS in Azure
Azure offers a comprehensive suite of security tools to help protect your data and applications. When it comes to IDS and IPS, Azure provides Azure Security Center and Azure Firewall as primary resources. Azure Security Center offers a unified security management system that can help detect threats and vulnerabilities across your cloud workloads. Meanwhile, Azure Firewall, a fully stateful firewall service, can be configured to block or allow traffic based on specific security rules, effectively functioning as an IPS.
### Benefits of IDS and IPS in Azure
Integrating IDS and IPS into your Azure workflow can provide multiple benefits. First, they enhance the visibility of your network activities, allowing you to quickly identify and respond to potential threats. This proactive approach can significantly reduce the risk of data breaches and cyber-attacks. Additionally, these systems help maintain compliance with industry regulations by ensuring that your security practices are up to standard. Lastly, they offer peace of mind, allowing businesses to focus on their core operations without constantly worrying about security vulnerabilities.
### Best Practices for Cloud Security
To maximize the effectiveness of IDS and IPS in Azure, it’s essential to follow best practices. Regularly update and patch your security systems to protect against new vulnerabilities. Implement strong access controls and ensure that only authorized personnel have access to critical systems. Continuously monitor and analyze network traffic to detect anomalies early. Additionally, conduct regular security audits to assess the effectiveness of your existing measures and identify areas for improvement.
Understanding IDS and IPS
A – : IDS is a security mechanism that monitors network traffic and identifies potential security breaches or suspicious activities. On the other hand, IPS acts as an active shield, preventing any identified threats from penetrating the network. By working hand in hand, these systems form a formidable line of defense against cyberattacks.
B – : Microsoft Azure, as a leading cloud platform, offers a robust suite of security services, including IDS and IPS. By seamlessly integrating IDS and IPS solutions into Azure, businesses can harness the power of these tools to safeguard their data. This section will explore the various features and capabilities of IDS and IPS in Azure, highlighting their ease of deployment and scalability.
**Key Advantages**
The advantages of utilizing IDS and IPS in Azure are manifold. In this section, we will discuss some key benefits that businesses can reap by leveraging these security measures. These include real-time threat detection, proactive threat prevention, enhanced visibility into network traffic, and compliance with regulatory standards. Through these benefits, IDS and IPS in Azure offer a robust security framework for businesses of all sizes.
**Implementation**
Implementing IDS and IPS effectively requires adherence to best practices. This section will provide valuable insights and recommendations on how to maximize the effectiveness of IDS and IPS in Azure. Topics covered will include proper configuration, regular updates and patching, leveraging advanced analytics, and continuous monitoring. By following these best practices, businesses can optimize their security posture in Azure.
Azure Security Services
A- Poor cybersecurity practices still result in a significant number of breaches. One of the top causes of breaches continues to be insecure configurations of cloud workloads. As a result of the COVID-19 pandemic, many companies had to speed up their digital transformation and rush to move their workloads to the public cloud without much consideration for security.
B- Public cloud platforms exposed virtual machines (VMs) to attacks over the internet. An organization’s environment was accessed unauthorizedly by attackers using leaked credentials. Source code repositories were left unencrypted and exposed. These poor practices commonly cause cloud security breaches.
C- How can you secure Azure environments against common cloud security incidents and threats? A set of native security services are available in Azure to help solve this problem, most commonly known as Azure security services.
Gaining access to resources:
A bad actor may access your environment, compromise an account, and access more resources through the compromised account. Furthermore, they can spread to other resources, such as databases, storage, and IoT devices. Bad actors move between different types of resources to access as many. A bad actor will establish control over the environment to achieve their goals. For example, ransomware attacks hold an organization’s environment hostage and demand a ransom payment.
Unfortunately, there are many other types of attacks as well. A kill chain model describes how breaches occur and what steps bad actors may take to compromise your public cloud environment. The kill chain model consists of five steps: exposure, access, lateral movement, actions on objective, and goal.
Azure network security:
You can implement a secure network infrastructure in Azure using Azure network security services. You will learn about the following network security services in this chapter:
- Azure Firewall Standard
- Azure Firewall Premium
- Azure Web Application Firewall
- Azure DDoS Protection Basic
- Azure DDoS Protection Standard
For more advanced use cases, you could also use third-party network security appliances. Understanding how these appliances work is essential, and using them in Azure usually incurs additional charges. These services are native to Azure, meaning they are well-integrated into the Azure platform and protect against common attacks.
Example: **Azure IDS**
Azure offers a native IDS solution called Azure Security Center. This cloud-native security service provides threat detection and response capabilities across hybrid cloud workloads. By leveraging machine learning and behavioral analytics, Azure Security Center can quickly identify potential security threats, including network-based attacks, malware infections, and data exfiltration attempts.
Example: **Azure Cloud**
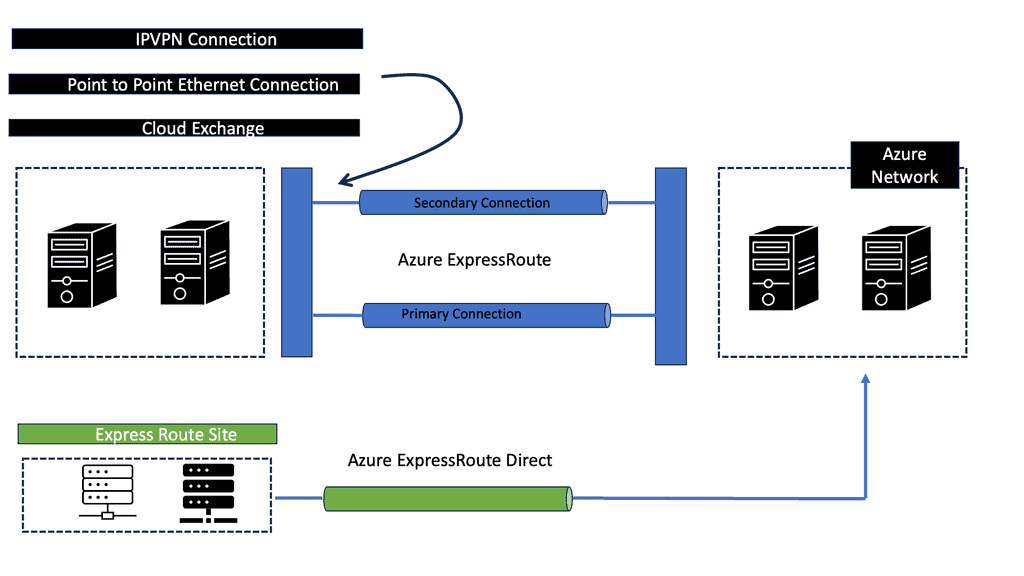
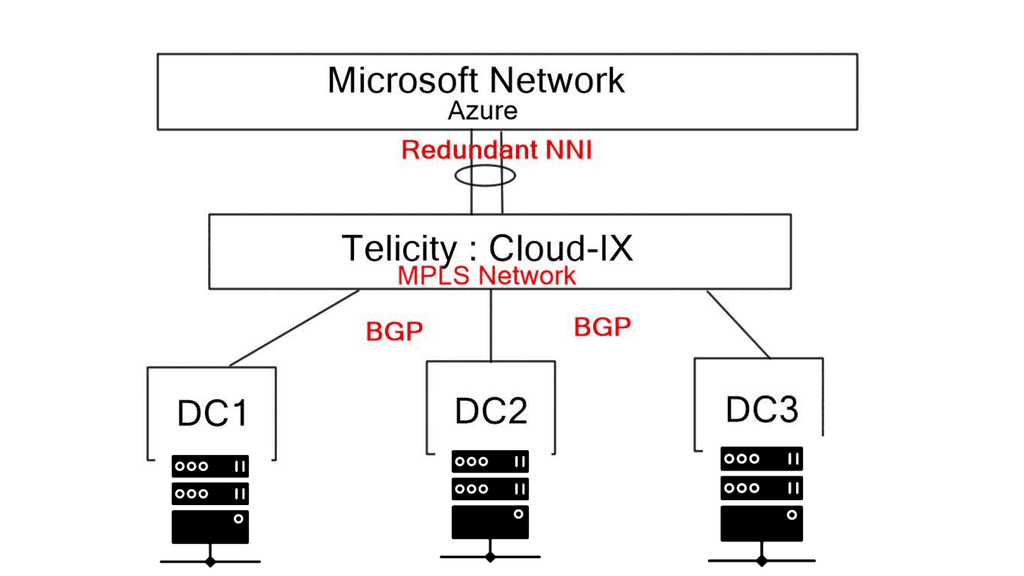
Microsoft Azure Cloud consists of functional design modules and services such as Azure Internet Edge, Virtual Networks (VNETs), ExpressRoute, Network Security Groups (NSGs), and User-Defined Routing (UDR). Some resources are controlled solely by Azure; others are within the customer’s remit. The following post discusses some of those services and details a scenario design use case incorporating Barracuda Next Generation (NG) appliances and IDS IPS Azure.
For pre-information, you may find the following post helpful:
IDS IPS Azure
Network Intrusion
Network intrusion detection determines when unauthorized people attempt to break into your network. However, keeping bad actors out or extracting them from the network once they’ve gotten in are two different problems. Keeping intruders out of your network is only meaningful if you know when they’re breaking in. Unfortunately, it’s impossible to keep everything out all the time.
Detecting unauthorized connections is a good starting point, but it is only part of the story. For example, network intrusion detection systems are great at detecting attempts to log in to your system and access unprotected network shares.
Key Features of Azure IDS:
1. Network Traffic Analysis:
Azure IDS analyzes network traffic to identify patterns and anomalies that may indicate potential security breaches. It leverages machine learning algorithms to detect unusual behavior and promptly alerts administrators to take appropriate action.
2. Threat Intelligence Integration:
Azure Security Center integrates with Microsoft’s global threat intelligence network, enabling it to access real-time information about emerging threats. This integration allows Azure IDS to stay up-to-date with the latest threat intelligence, providing proactive defense against known and unknown threats.
3. Security Alerts and Recommendations:
The IDS solution in Azure generates detailed security alerts, highlighting potential vulnerabilities and offering actionable recommendations to mitigate risks. It empowers organizations to address security gaps and fortify their cloud environment proactively.
IDS IPS Azure: Network & Cloud Access
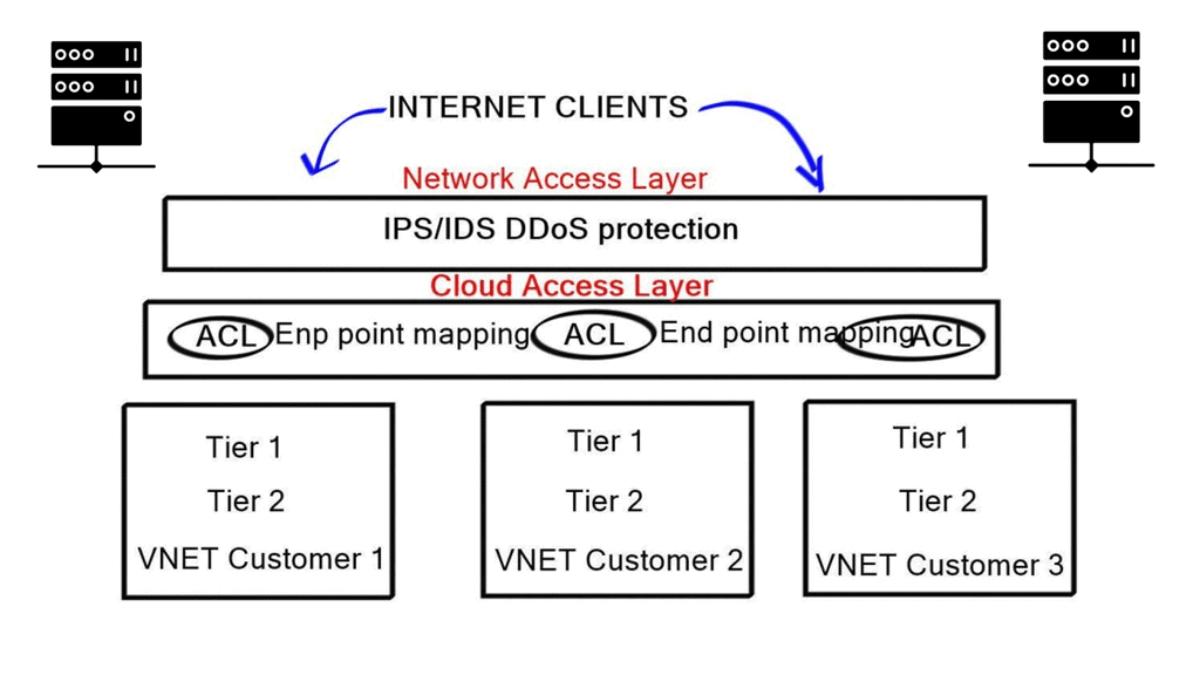
Azure Network Access Layer:
Azure Network Access Layer is the Azure Internet edge security zone, consisting of IDS/IPS for DDoS and IDS protection. It isolates Azure’s private networks from the Internet, acting as Azure’s primary DDoS defense mechanism. Azure administrators ultimately control this zone; private customers do not have access and can not make configuration changes.
However, customers can implement their IDS/IPS protection by deploying third-party virtual appliances within their private virtual network (VNET), ideally in a services sub-VNET. Those appliances can then be used in conjunction with Azure’s IDS/IPS but can not be used as a replacement. The Azure Internet Edge is a mandatory global service offered to all customers.
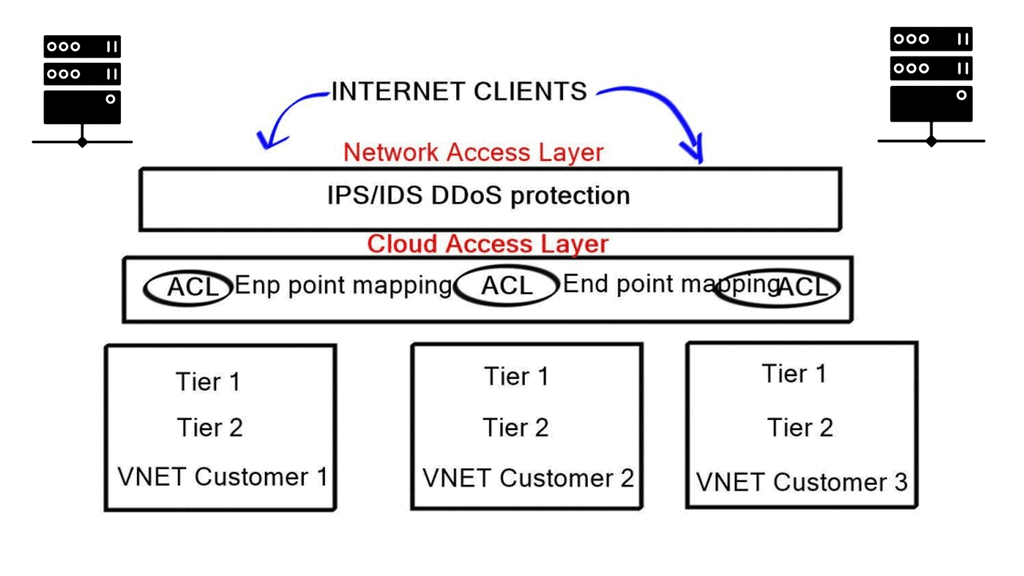
Azure Cloud Access Layer
This is the first point of control for customers, and it gives administrators the ability to administer and manage network security on their Azure private networks. It is comparable to the edge of a corporate network that faces the Internet, i.e., Internet Edge.
The Cloud Access Layer contains several Azure “free” services, including virtual firewalls, load balancers, and network address translation ( NAT ) functionality. It allows administrators to map ports and restrict inbound traffic with ACL. A VIP represents the cloud access load balance appliance to the outside world.
Any traffic destined for your services first hit the VIP. You can then configure what ports you want to open and match preferred traffic sources. If you don’t require using cloud access layer services, you can bypass it, allowing all external traffic to go directly to that service. Beware that this will permit all ports from all sources.
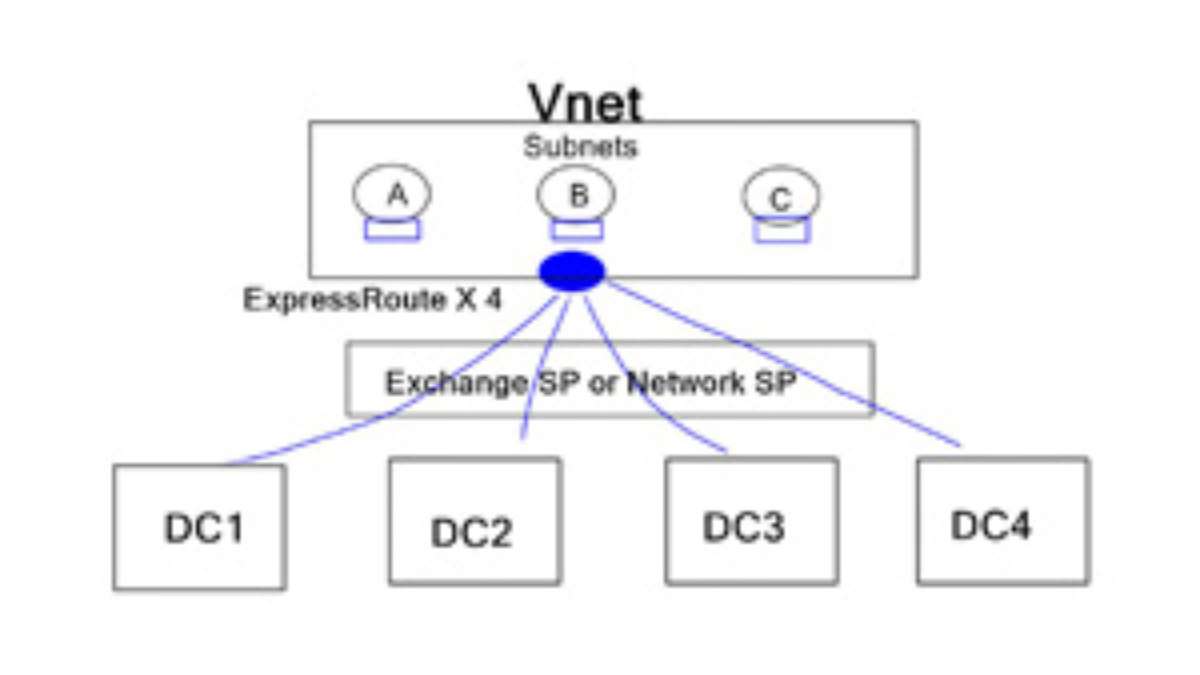
Inside Azure cloud
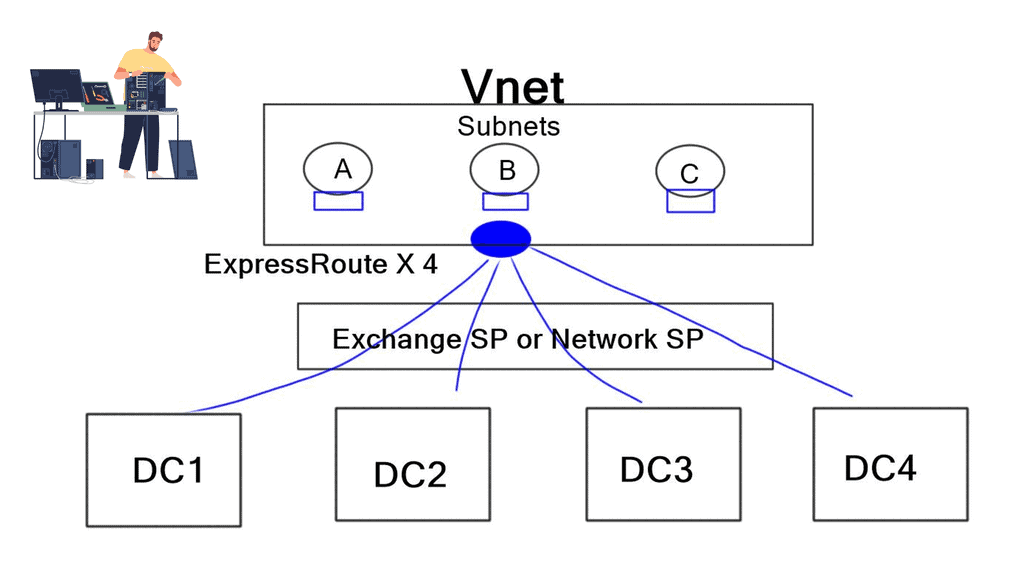
Customers can create VNETs to represent subscriptions or services. For example, you can have a VNET for Production services and another VNET for Development. Within the VNET, you can further divide the subnet to create DMZ, Application tiers, Database, and Active Directory ADFS subnets. A VNET is a control boundary, and subnets configured within a VNET are usually within the VNET’s subnet boundary. Everything within a VNET can communicate automatically. However, VNET-to-VNET traffic is restricted and enabled via configuring gateways.
Network security groups
To segment traffic within a VNET, you can use Azures Network Security Groups (NSGs). They are applied to a subnet or a VM and, in some cases, both. NSGs are more enhanced than standard 5-tuple packet filters, and their rules are stateful. For example, if an inbound rule allows traffic on a port, then a matching rule on the outbound side is not required for the packets to flow on the same port.
User-defined routing
User-defined routing modifies the next hop of outbound traffic flows. It can point traffic to appliances for further actions or scrubbing, providing more granular traffic engineering. UDR could be compared to Policy-Based Forwarding (PBR) and a similar on-premise feature.
Multi VNET with multi NG firewalls
The following sections will discuss the design scenario for Azure VNET-to-VNET communication via Barracuda NG firewalls, TINA tunnels, and Azures UDR. The two VNETs use ExpressRoute gateways for “in” cloud Azure fabric communication. Even though the Azure ExpressRoute gateway is for on-premise connectivity, it can be used for cloud VNET-to-VNET communication.
DMZ subnet consists of Barracuda NG firewalls for security scrubbing and Deep Packet Inspection (DPI). Barracuda’s Web Application Firewalls (WAF) could also be placed a layer ahead of the NG and have the ability to perform SSL termination and offload. To route traffic to and from the NG appliance, use UDR. For example, TOO: ANY | FROM: WEB | VIA: NG
To overcome Azure’s lack of traffic analytics, the NG can be placed between service layers to provide analytics and traffic profile analyses. Traffic analytics helps determine outbound traffic flows if VMs get compromised and attackers attempt to “beachhead.” If you ever compromised, it is better to analyze and block traffic yourself than call the Azure helpline 🙂
**VNET-to-VNET TINA tunnels**
Barracuda NG supports TINA tunnels for encryption to secure VNET-to-VNET traffic. Depending on the number of VNETs requiring cross-communication, TINA tunnels can be deployed as full mesh or hub-and-spoke designs terminating on the actual NG. TINA tunnels are also used to provide backup traffic engineering over the Internet. They are transport agnostic and can route different flows via the ExpressRoute and Internet gateways. They hold a similar analogy to SD-WAN but without the full feature set.
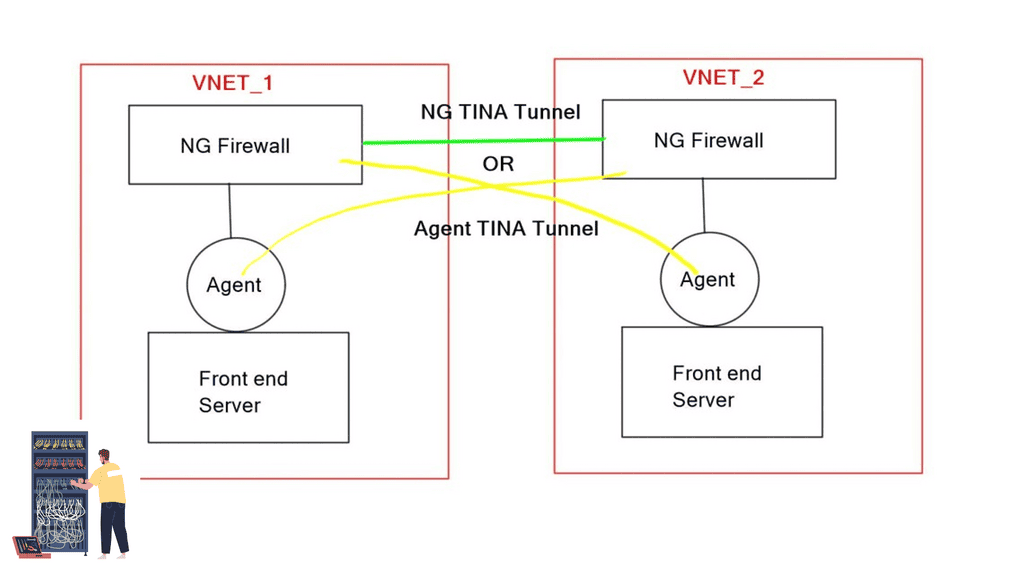
A similar design case exists using Barracuda TINA agents on servers to create TINA tunnels directly to NGS in remote VNET. This concept is identical to an Agent VPN configured on hosts. However, instead of UDR, you can use TINA agents to enable tunnels from hosts to NG firewalls.
The agent method reduces the number of NGS and is potentially helpful for hub and spoke VNET design. The main drawbacks are the lack of analytics in the VNET without the NG and the requirement to configure agents on participating hosts.
Implementing robust security measures is paramount in today’s digital landscape, where cyber threats are becoming increasingly sophisticated. Azure IDS and IPS solutions, offered through Azure Security Center, provide organizations with the tools to detect, prevent, and respond to potential security breaches in their cloud environment.
By leveraging the power of machine learning, behavioral analytics, and real-time threat intelligence, Azure IDS and IPS enhance the overall security posture of your Azure infrastructure, enabling you to focus on driving business growth with peace of mind.
Closing Points on Azure IDS IPS
To protect cloud environments, organizations need robust security mechanisms. Two essential components of cloud security are Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS), especially within platforms like Microsoft Azure.
IDS and IPS are critical in safeguarding IT environments by monitoring network traffic for suspicious activities. An IDS primarily detects and alerts administrators about possible threats, whereas an IPS goes a step further by actively blocking potential attacks. In an Azure environment, these systems help maintain the integrity and confidentiality of data, ensuring compliance with security standards.
Azure offers various tools and services to implement IDS and IPS effectively. Azure Security Center provides advanced threat protection, leveraging machine learning and analytics to identify and mitigate threats. The integration of Azure Sentinel, a cloud-native security information and event management (SIEM) solution, enhances these capabilities by offering real-time threat intelligence and incident investigation.
Implementing IDS and IPS in Azure brings several advantages. Firstly, they offer improved visibility into network activities, helping identify vulnerabilities before they can be exploited. Secondly, these systems automate threat responses, reducing the need for manual intervention and thus minimizing response times. Lastly, they ensure compliance with industry regulations by continuously monitoring and securing sensitive data.
While IDS and IPS provide numerous benefits, there are challenges in their deployment. Organizations must consider the potential for false positives, which can lead to unnecessary alerts and resource consumption. Additionally, the complexity of configuring these systems to match specific security requirements necessitates skilled personnel and ongoing maintenance.
Summary: IDS IPS Azure
In today’s rapidly evolving digital landscape, ensuring the security of your systems and data has become more critical than ever before. With the increasing sophistication of cyber threats, organizations need robust intrusion detection and prevention systems (IDS/IPS) to safeguard their assets. Azure IDS/IPS, powered by Microsoft Azure, offers a comprehensive solution that combines cutting-edge technology, intelligent threat detection, and seamless scalability. This blog post explored the key features, benefits, and best practices of Azure IDS/IPS, empowering you to fortify your digital infrastructure confidently.
Understanding Azure IDS/IPS
Azure IDS/IPS is an advanced security service provided by Microsoft Azure. It acts as a proactive defense mechanism, continuously monitoring network traffic and identifying potential threats. By leveraging machine learning algorithms and threat intelligence, Azure IDS/IPS can detect and prevent malicious activities, including unauthorized access attempts, malware infections, and data breaches.
Key Features and Benefits
Azure IDS/IPS offers an array of powerful features that elevate your security posture:
1. Real-time Threat Detection: Azure IDS/IPS monitors real-time network traffic, swiftly identifying suspicious patterns and potential threats. This proactive approach ensures timely response and mitigation, minimizing the impact of attacks.
2. Intelligent Threat Intelligence: By harnessing the power of machine learning and AI, Azure IDS/IPS continuously evolves and adapts to emerging threats. It leverages vast threat intelligence sources to enhance detection accuracy and stay ahead of malicious actors.
3. Seamless Integration with Azure Ecosystem: As a part of the comprehensive Azure ecosystem, Azure IDS/IPS seamlessly integrates with other Azure services, such as Azure Security Center and Azure Sentinel. This integration enables holistic security management and centralized monitoring, streamlining security operations.
Best Practices for Implementing Azure IDS/IPS
To maximize the effectiveness of Azure IDS/IPS, consider the following best practices:
1. Define Clear Security Policies: Establish well-defined security policies and access controls to ensure the IDS/IPS system aligns with your organization’s security requirements.
2. Regular Updates and Patching: Stay updated with the latest security patches and updates Microsoft Azure provides. Regularly applying these updates ensures that your IDS/IPS system remains equipped to tackle emerging threats.
3. Continuous Monitoring and Analysis: Implement a robust monitoring and analysis strategy to identify potential threats proactively. Leverage the insights Azure IDS/IPS provided to fine-tune your security policies and response mechanisms.
Conclusion
Azure IDS/IPS empowers organizations to safeguard their digital assets with confidence. By combining real-time threat detection, intelligent threat intelligence, and seamless integration with the Azure ecosystem, Azure IDS/IPS provides a comprehensive security solution. By following best practices and staying vigilant, organizations can harness the power of Azure IDS/IPS to fortify their digital landscape against evolving cyber threats.