IPv6 Attacks
In today's digital age, the internet has become an integral part of our lives. The transition from IPv4 to IPv6 was necessary to accommodate the growing number of devices connected to the internet. However, with this transition, new security challenges have emerged. This blog post will delve into IPv6 attacks, exploring their potential risks and how organizations can protect themselves.
Before discussing potential attacks targeting IPv6, it is essential to understand why the transition from IPv4 to IPv6 was necessary. IPv4, with its limited address space, could no longer sustain the increasing number of internet-connected devices. IPv6, on the other hand, provides an enormous number of unique addresses, ensuring the growth of the internet for years to come.
Common IPv6 Attack Vectors: In this section, we will explore the various attack vectors that exist within the IPv6 landscape. From address scanning and spoofing to router vulnerabilities and neighbor discovery manipulation, attackers have ample opportunities to exploit weaknesses in the protocol.
Implications of IPv6 Attacks: The consequences of successful IPv6 attacks can be severe. With the potential to disrupt communication networks, compromise sensitive data, and even launch large-scale DDoS attacks, it is crucial to understand the implications of such security breaches.
Mitigating IPv6 Attacks: Thankfully, there are several measures that can be taken to mitigate the risks associated with IPv6 attacks. This section will discuss best practices for securing IPv6 networks, including implementing strong firewall rules, monitoring network traffic, and keeping network devices up to date with the latest security patches.
The Role of Network Administrators: Network administrators play a crucial role in maintaining the security and integrity of IPv6 networks. This section will highlight the responsibilities and proactive steps that administrators should take to safeguard their networks against potential threats.Matt Conran
Highlights: IPv6 Attacks
**The Limitations of IPv4**
IPv4 has served us well, but it has a critical limitation: a finite number of addresses. With only about 4.3 billion unique addresses available, the rapid growth of internet-enabled devices has led to an imminent exhaustion of available IPv4 addresses. This limitation has necessitated the development of IPv6, which offers a virtually limitless pool of IP addresses, ensuring that every device can have its unique identifier.
**Understanding IPv6: The Technical Leap**
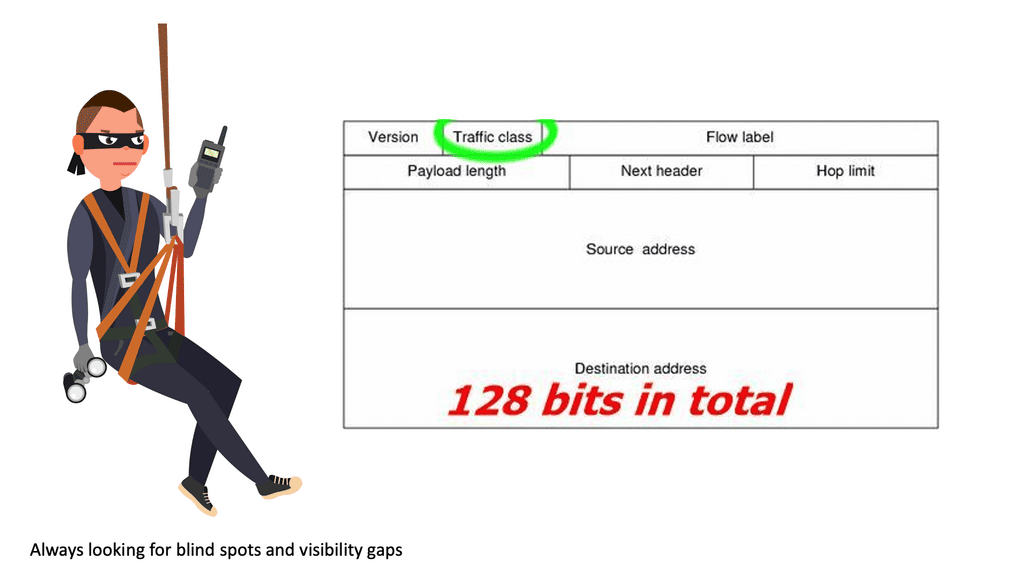
IPv6 is designed to overcome the limitations of its predecessor with a much larger address space. It uses 128-bit addresses, compared to the 32-bit system of IPv4, which translates to approximately 340 undecillion unique addresses. This expansion not only accommodates future growth but also simplifies address allocation and management, reducing the need for complex network address translation (NAT) processes.
**Benefits of Adopting IPv6**
The transition to IPv6 offers several advantages beyond just a larger address space. It includes improved security features, such as mandatory support for Internet Protocol Security (IPsec), which enhances the confidentiality and integrity of data. Additionally, IPv6 simplifies network configuration through automatic address configuration and improves routing efficiency, leading to faster data transmission and reduced latency.
**Challenges in Transitioning to IPv6**
Despite its advantages, the transition from IPv4 to IPv6 is not without challenges. One major hurdle is the compatibility issue; many existing systems and applications were designed with IPv4 in mind. This requires organizations to invest in upgrading their infrastructure, which can be costly and time-consuming. Moreover, the coexistence of both protocols during the transition phase demands careful planning to ensure seamless communication across networks.
IPv6 Security Challenges
1:- ) Before diving into the intricacies of IPv6 attacks, let’s first understand the basics of IPv6. IPv6, or Internet Protocol version 6, is the next-generation Internet Protocol that succeeds IPv4. It was introduced to address the limitations of IPv4, such as its limited address space. IPv6 brings numerous improvements, including a larger address space, enhanced security features, and improved efficiency.
2:- ) The transition from IPv4 to IPv6 has been a significant technological shift, designed to accommodate the ever-expanding number of devices connected to the internet. IPv6 offers a virtually limitless number of IP addresses, addressing a pressing need that IPv4 can no longer manage. However, with this transition comes a new landscape for cybersecurity threats. Understanding IPv6 attacks is crucial for anyone responsible for network security.
IPv6 attacks encompass a wide range of techniques employed by cybercriminals to exploit vulnerabilities in the protocol. Here are some common types of IPv6 attacks:
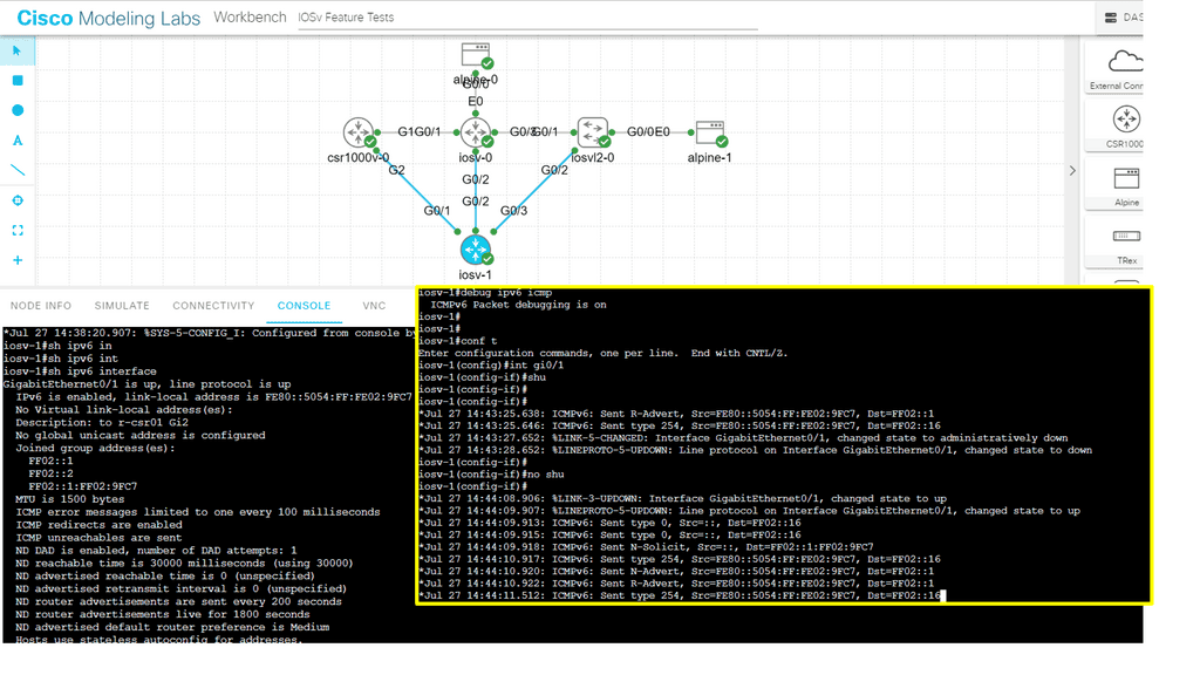
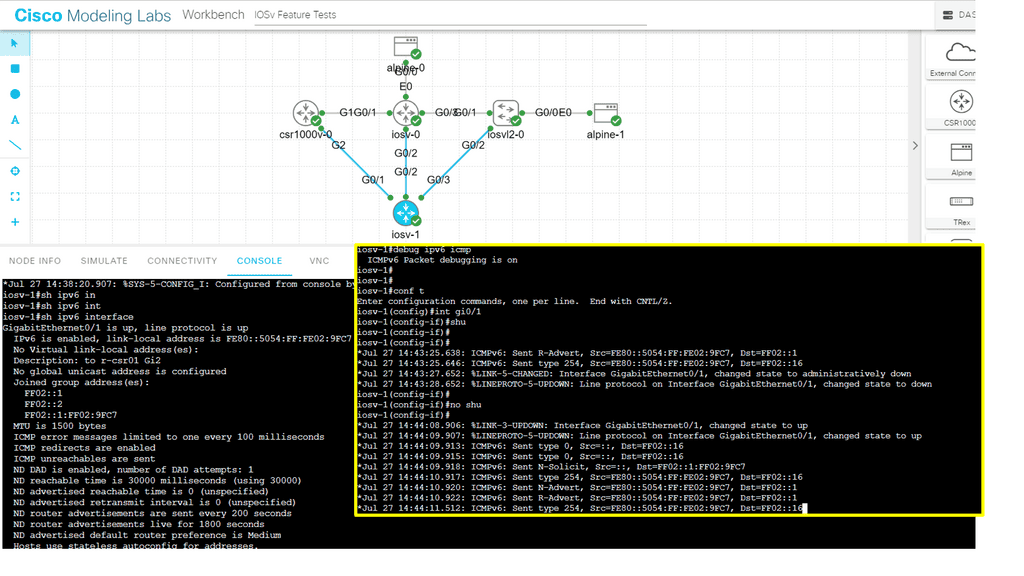
a) – ICMPv6 Attacks: ICMPv6 (Internet Control Message Protocol version 6) attacks exploit weaknesses in the ICMPv6 protocol to disrupt network connectivity, launch denial-of-service attacks, or gather sensitive information.
b) – Neighbor Discovery Protocol (NDP) Attacks: NDP is a vital component of IPv6, responsible for address resolution and neighbor interaction. Attackers can exploit flaws in NDP to perform various malicious activities, such as address spoofing, router impersonation, or network reconnaissance.
c) – Fragmentation Attacks: Fragmentation attacks take advantage of IPv6 packet fragmentation mechanisms to overwhelm network devices or evade security measures. By sending specially crafted fragmented packets, attackers can disrupt network operations or bypass firewalls.
**Impacts of IPv6 Attacks**
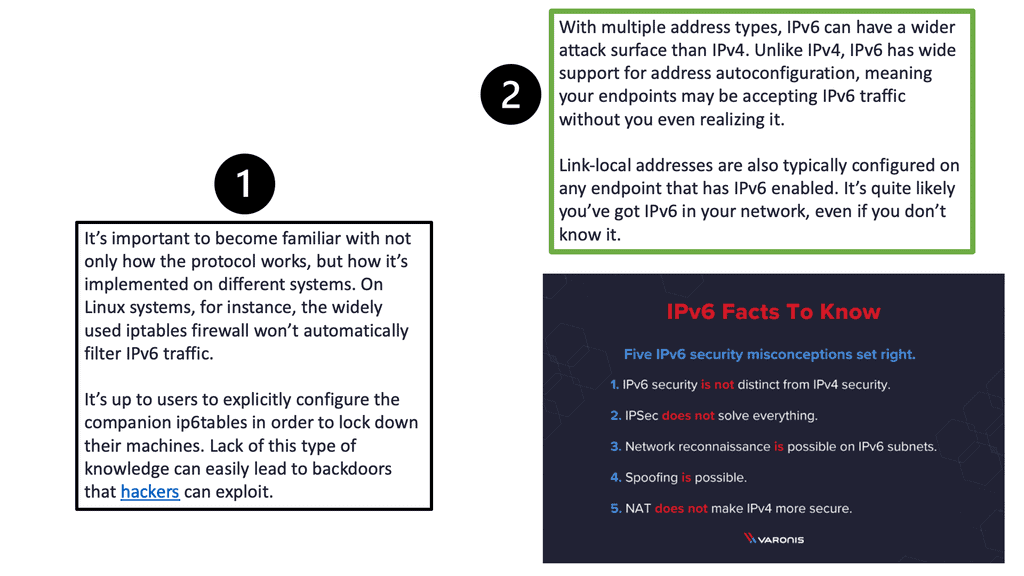
Detecting IPv6 attacks can be particularly challenging due to the sheer complexity and scale of IPv6 networks. The vast address space makes it difficult to monitor traffic effectively. Additionally, many existing security tools are optimized for IPv4, meaning they may not fully support IPv6 or may require significant updates to do so. Security professionals need to ensure that their tools and protocols are compatible with IPv6 to maintain effective network protection.
The consequences of successful IPv6 attacks can be severe and far-reaching. Here are a few potential impacts:
a) Network Disruption: IPv6 attacks can lead to network outages, causing significant disruption to organizations and their services. This can result in financial losses, reputational damage, and customer dissatisfaction.
b) Data Breaches: Attackers may exploit IPv6 vulnerabilities to gain unauthorized access to sensitive data traversing the network. This can lead to data breaches, compromising the confidentiality and integrity of critical information.
c) System Compromise: In some cases, IPv6 attacks can result in the complete compromise of network devices or systems. This grants attackers control over the compromised assets, enabling them to launch further attacks or use them as a stepping stone for lateral movement within the network.
**Mitigation Strategies**
To protect against IPv6 attacks, organizations should implement robust mitigation strategies. Here are a few key measures:
a) Network Segmentation: Segmenting the network into smaller, isolated subnets can limit the potential impact of IPv6 attacks. By employing proper access controls and traffic filtering, organizations can contain attacks within specific network segments.
b) Intrusion Detection and Prevention Systems: Deploying intrusion detection and prevention systems specifically designed for IPv6 can aid in detecting and blocking malicious activities. These systems can identify attack patterns and automatically take preventive measures.
c) Regular Patching and Updates: Keeping network devices, operating systems, and applications up to date is crucial for mitigating IPv6 vulnerabilities. Regularly applying patches and updates ensures that known security flaws are addressed, reducing the attack surface.
Transition to IPv6: Bigger Attack Surface
IPv6, or Internet Protocol version 6, is designed to succeed IPv4, which has been the dominant protocol for decades. Unlike IPv4, which uses 32-bit addresses, IPv6 employs a 128-bit space, offering numerous unique addresses. This expansion allows for the growth of connected devices and the Internet of Things (IoT). However, as the number of connected devices increases, so do the potential security risks.
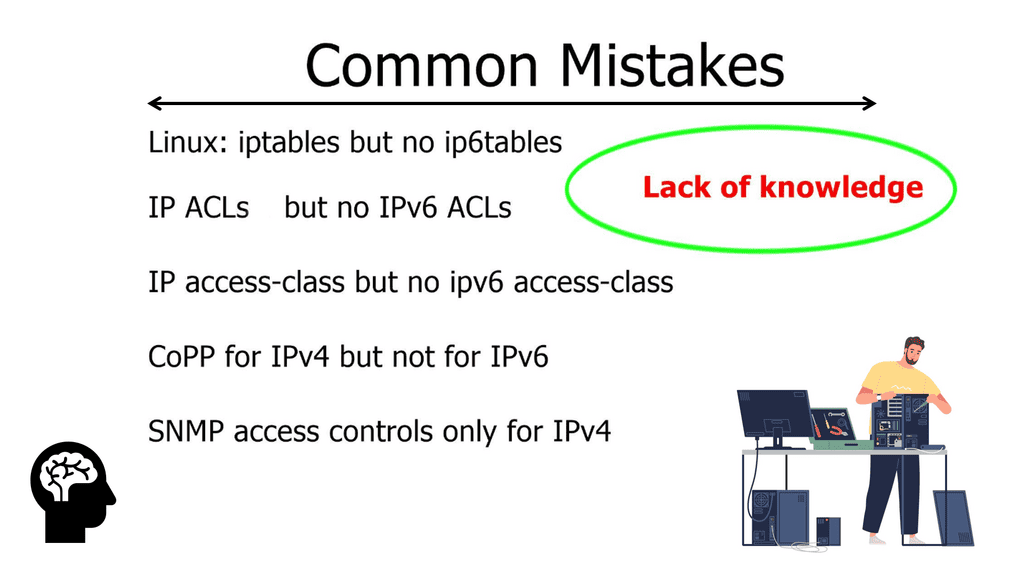
The transition to IPv6 brings forth a new set of security challenges. One of the primary concerns is the lack of awareness and understanding surrounding IPv6 security. Many network administrators and security professionals are still more familiar with IPv4, which can lead to oversight and vulnerabilities in IPv6 implementations. Additionally, the larger address space of IPv6 provides a bigger attack surface, making it more challenging to monitor and secure networks effectively.
Best Practices for IPv6 Security
To mitigate the risks associated with IPv6, adopting best practices for network security is crucial. These include:
- Comprehensive Network Monitoring: Implementing robust network monitoring solutions allows for detecting suspicious activities or vulnerabilities in real time.
- Firewalls and Intrusion Detection Systems: Deploying firewalls and intrusion detection systems (IDS) that are IPv6 capable helps filter and analyze network traffic, identifying potential threats and unauthorized access attempts.
- Security Assessments and Audits: Regular security assessments and audits help identify vulnerabilities, misconfigurations, and weaknesses in the IPv6 infrastructure, allowing for timely remediation actions.
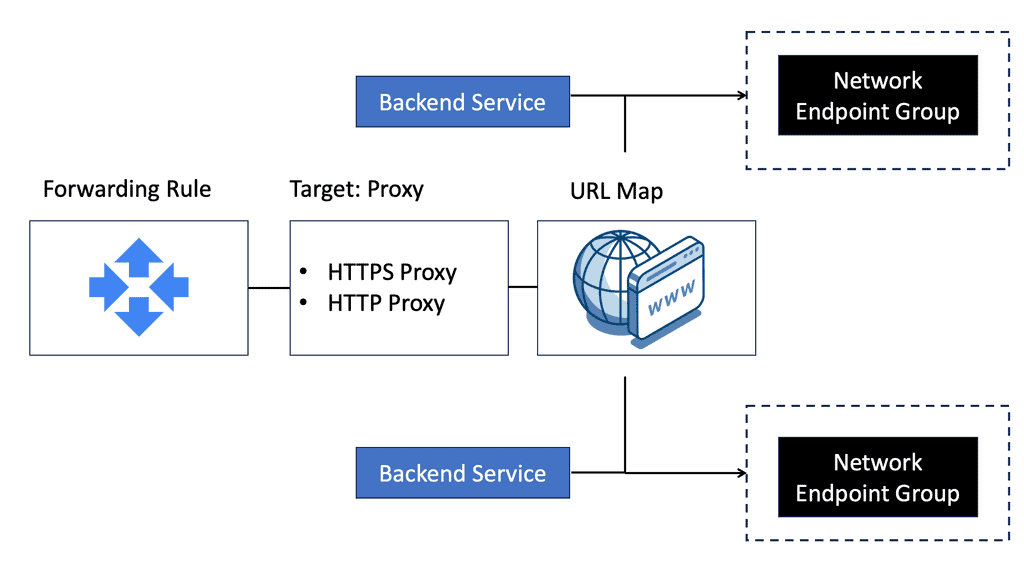
Recap Technology: IPv6 Connectivity
Understanding IPv6 Multicast
IPv6 multicast allows efficient communication to a group of nodes, allowing packet delivery to multiple destinations simultaneously. Unlike unicast, where packets are sent to a single node or broadcast, where packets are sent to all nodes, multicast balances efficiency and scalability.
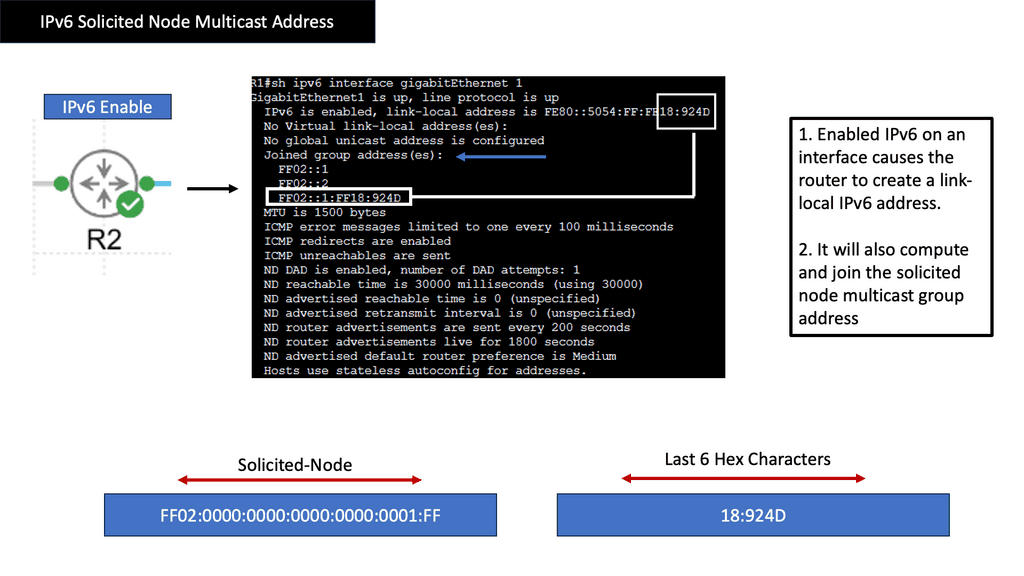
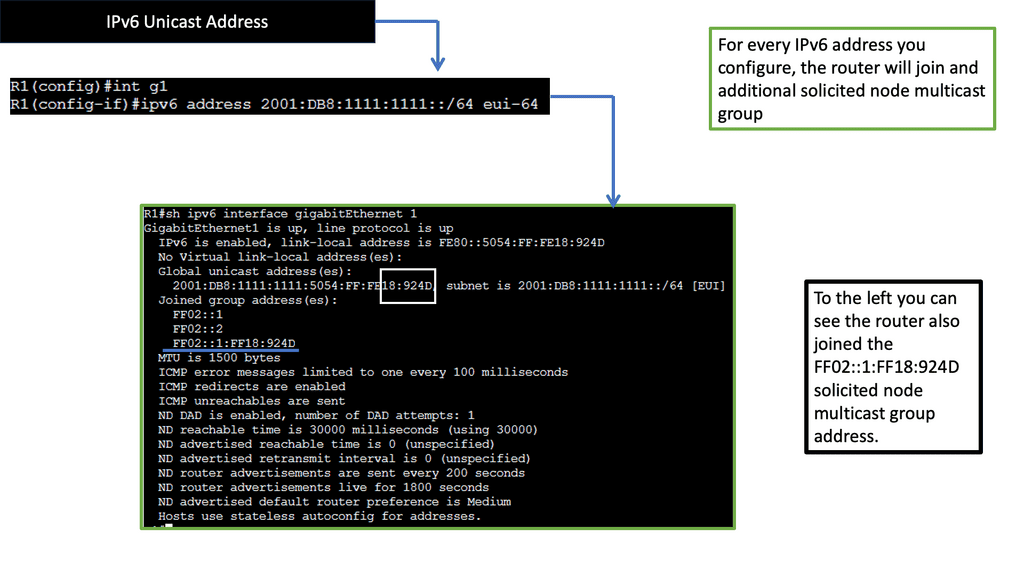
Solicited Node Multicast Address is a specialized form of multicast in IPv6. It serves a crucial purpose in the Neighbor Discovery Protocol (NDP) and is vital in efficiently resolving IPv6 addresses to link-layer addresses. SNMA is generated based on a node’s IPv6 address, ensuring that network resolution traffic is sent only to relevant nodes rather than flooding the entire network.
SNMA Structure and Formation
To form a Solicited Node Multicast Address, the lower 24 bits of the multicast address are set to the organizationally unique identifier (OUI) value FF02:0:0:0:0:1:FF, followed by the last 24 bits of the corresponding unicast IPv6 address. This structure ensures that nodes with similar addresses share the same multicast address prefix, promoting efficient communication within a subnet.
SNMA offers several benefits in the IPv6 ecosystem. First, it enhances network efficiency by reducing unnecessary traffic and preventing congestion. Second, it enables efficient address resolution, reducing the overhead associated with traditional unicast-based methods. Lastly, SNMA plays a crucial role in neighbor discovery, ensuring seamless communication between nodes in an IPv6 network.
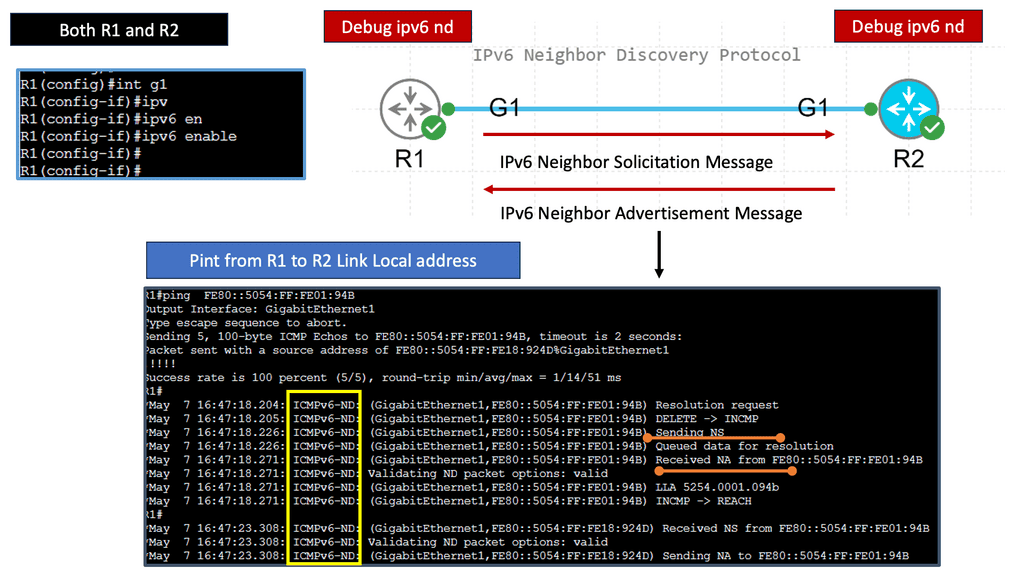
Understanding Neighbor Discovery Protocol:
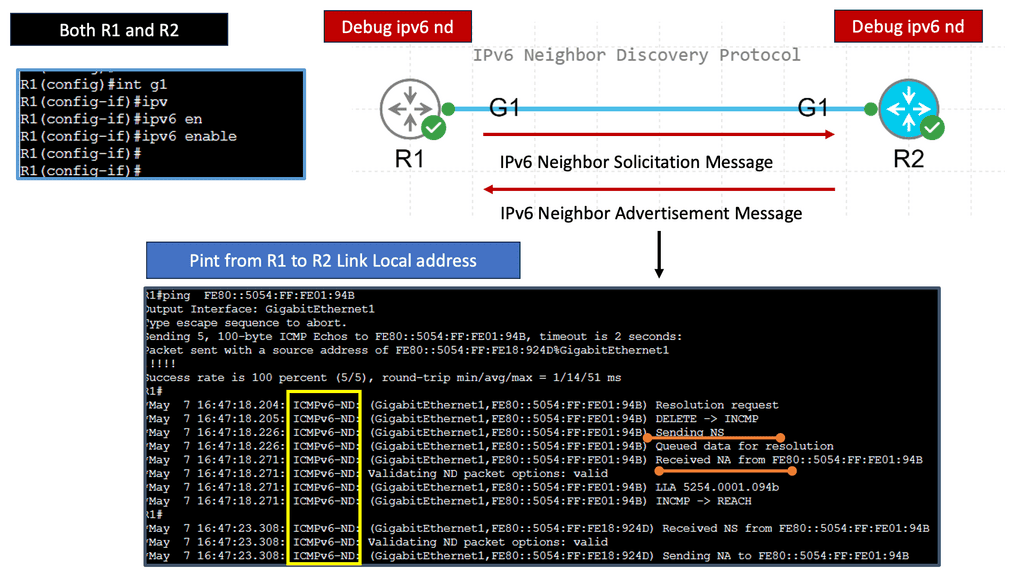
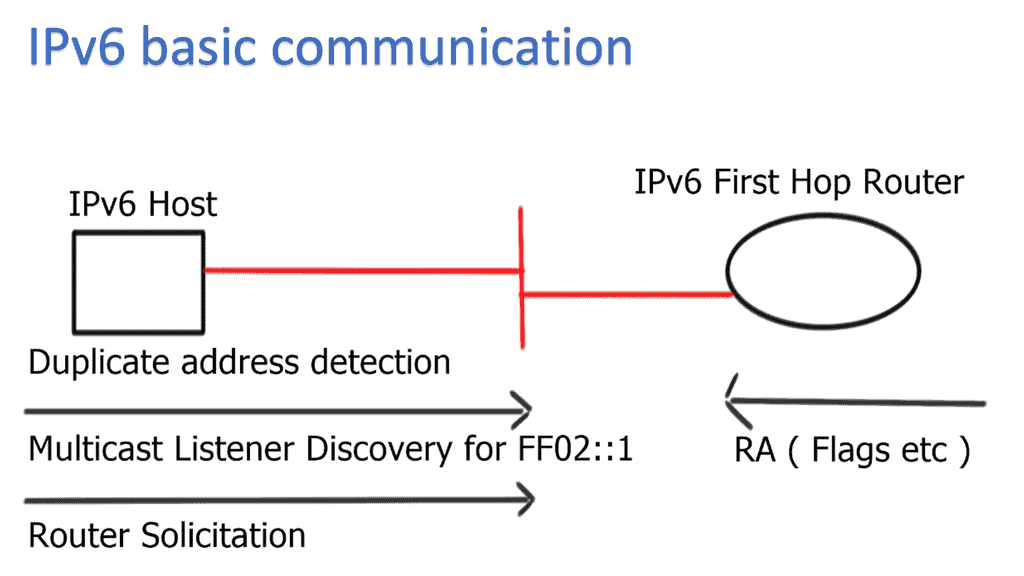
The Neighbor Discovery Protocol (NDP) is responsible for various functions in an IPv6 network. It facilitates address resolution, duplicate address detection, router discovery, and the maintenance of neighbor relationships. By performing these functions, NDP enables efficient and seamless communication within an IPv6 network.
One of NDP’s standout features is its ability to discover routers present on a network autonomously. This eliminates the need for manual configuration and simplifies network setup and management. Additionally, NDP employs techniques such as Duplicate Address Detection (DAD) to ensure the uniqueness of IPv6 addresses, enhancing network reliability and security.
Address Resolution with Neighbor Discovery Protocol:
Address resolution is a vital aspect of any networking protocol. With NDP, address resolution is achieved through Neighbor Solicitation and Neighbor Advertisement messages. These messages allow nodes to determine the link-layer address associated with a particular IPv6 address, facilitating seamless communication within the network.
Neighbor Discovery and Router Advertisement:
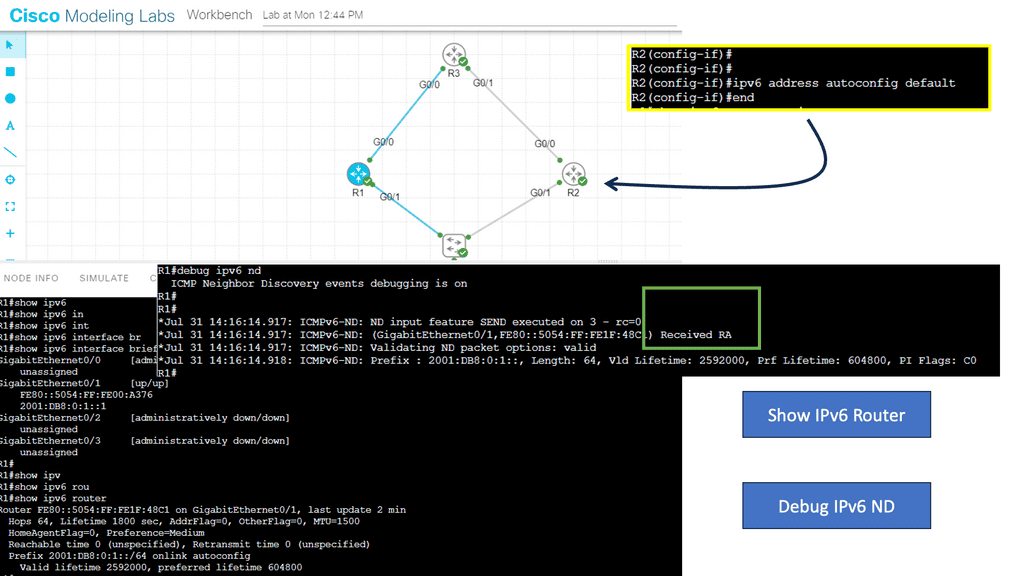
Router Advertisement (RA) messages play a crucial role in IPv6 networks. Routers periodically send RAs to announce their presence and provide essential network configuration information to neighboring nodes. By leveraging NDP, routers and hosts can dynamically adapt to network changes, ensuring efficient routing and seamless connectivity.
**Neighbor Discovery Protocol (NDP) Attacks**
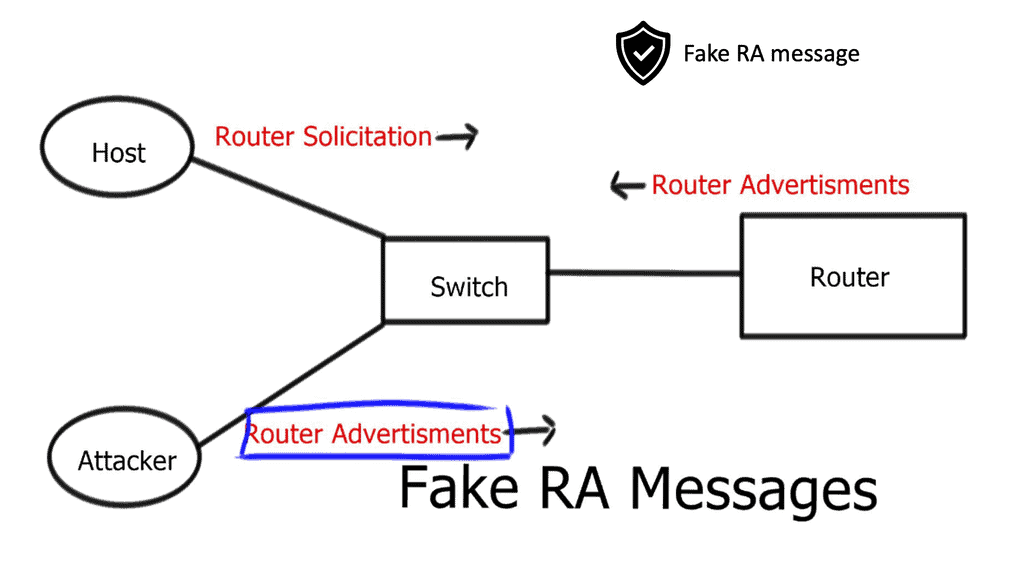
– The Neighbor Discovery Protocol (NDP) is a fundamental component of IPv6, responsible for address autoconfiguration and neighbor discovery. However, it is susceptible to attacks such as Neighbor Advertisement Spoofing and Router Advertisement Flooding. We explore these attacks in detail, highlighting their potential consequences.
– The Neighbor Discovery Protocol (NDP) is a vital component of IPv6. It facilitates network-related functions such as address autoconfiguration, router discovery, and neighbor reachability detection. By comprehending NDP’s inner workings, we gain insight into the vulnerabilities that attackers can exploit.
– NDP attacks come in various forms, each with its objectives and techniques. From rogue router advertisements to neighbor solicitation floods, attackers can disrupt network operations, intercept sensitive information, or launch further attacks. Understanding these attack vectors is crucial in developing effective defense mechanisms.
– Successful NDP attacks can have far-reaching and detrimental consequences. By compromising the integrity of network communications, attackers can intercept sensitive data, redirect traffic, or even launch man-in-the-middle attacks. The potential impact on businesses, organizations, and individuals necessitates proactive measures to mitigate these risks.
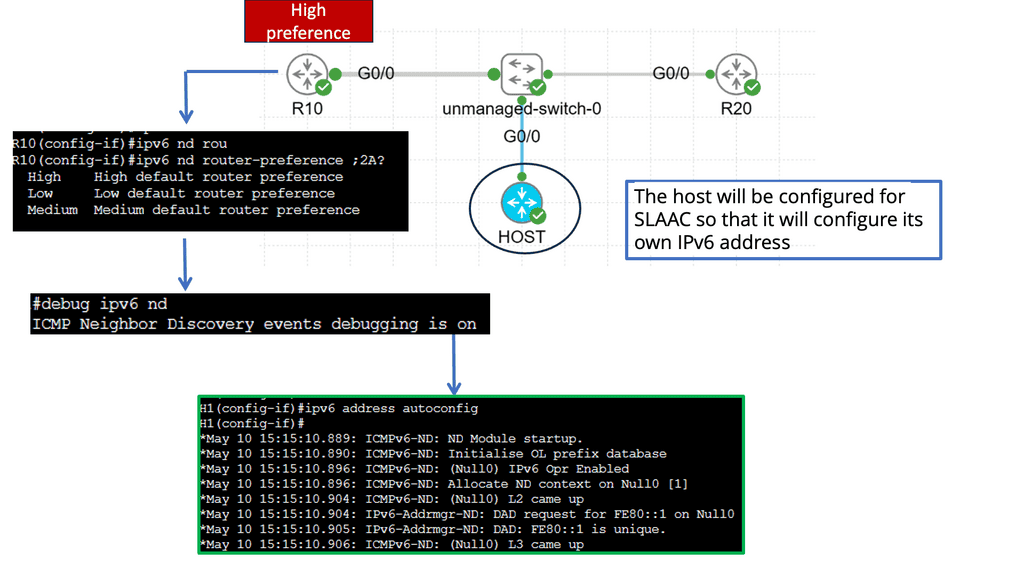
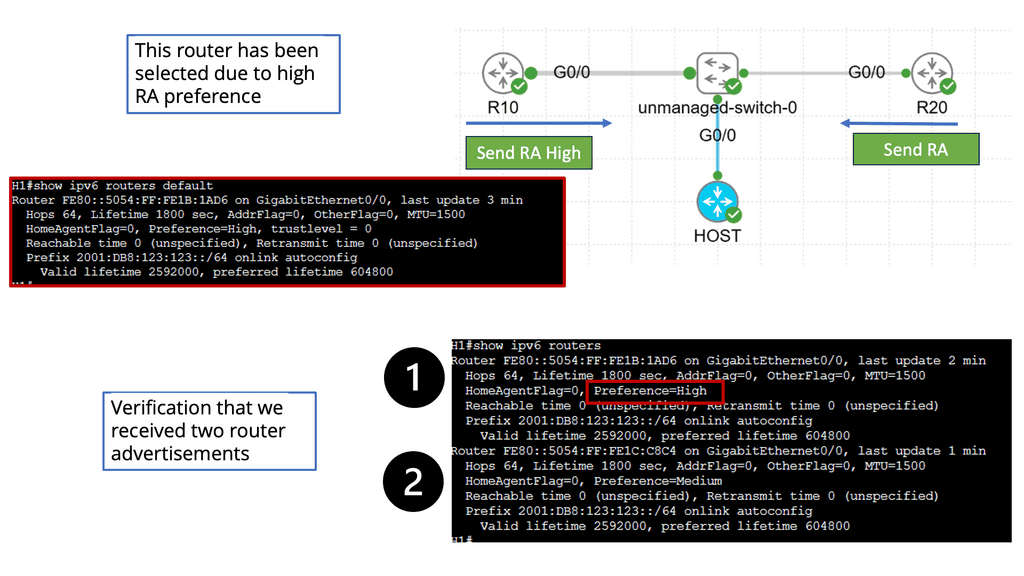
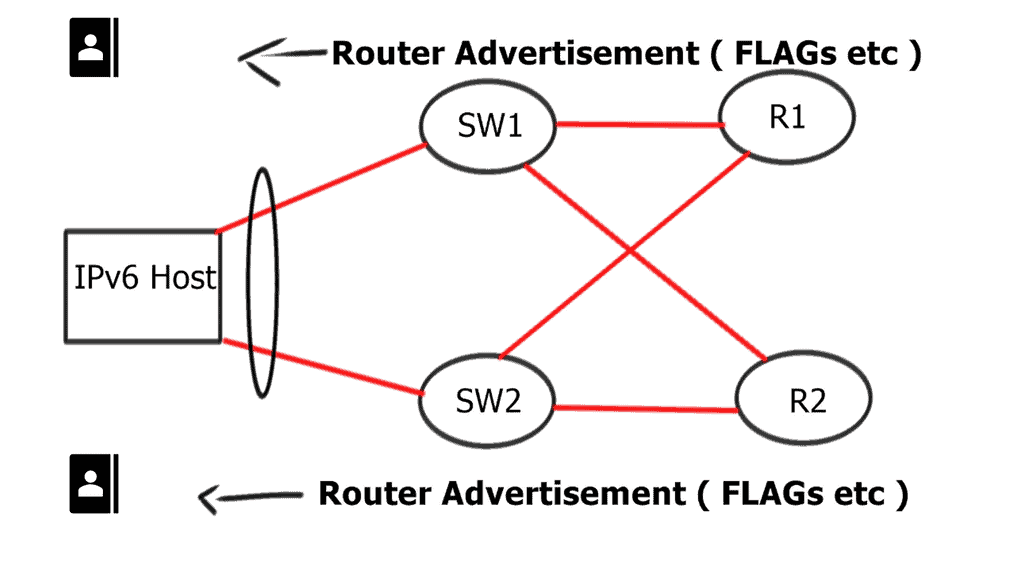
**Understanding IPv6 Router Advertisement Preference**
RA forms the backbone of IPv6 network configuration, allowing routers to advertise their presence and provide essential network details to neighboring hosts. The router advertisement preference is vital in determining how hosts choose the most suitable router for communication.
The preference value assigned to a router advertisement influences the host’s decision to select the default gateway. By carefully configuring the preference, network administrators can optimize traffic flow, enhance network performance, and ensure efficient routing.
IPv6 Router Advertisement Preference offers several configuration options to fine-tune network behavior. We will explore the different methods to configure the preference value, including manual configuration, dynamic preference assignment, and the utilization of routing protocols.
Understanding the implications of router advertisement preference is crucial for maintaining a stable and efficient network. We will discuss the impact of preference values on routing decisions, load balancing, failover mechanisms, and the overall resilience of the network infrastructure.
**Address Spoofing and Spoofed IPv6 Traffic**
Address spoofing in IPv6 poses a significant threat, allowing attackers to impersonate legitimate entities and launch various malicious activities. From source address spoofing to spoofed IPv6 traffic, we unravel the techniques employed by attackers and the impact they can have on network security.
Address spoofing refers to forging the source IP address of a packet to deceive the recipient or hide the true origin of the communication. Cybercriminals often employ this technique to launch various malicious activities, including distributed denial-of-service (DDoS) attacks, phishing attempts, and man-in-the-middle (MITM) attacks. By disguising their true identity, attackers can bypass security measures, making it challenging to trace and mitigate their actions.
The Rise of Spoofed IPv6 Traffic
With the transition from IPv4 to IPv6, new challenges have arisen in address spoofing. IPv6, with its vast address space, offers cybercriminals an opportunity to exploit the system and launch spoofed traffic with greater ease. The abundance of available addresses allows attackers to generate seemingly legitimate packets, making it harder to detect and prevent spoofed IPv6 traffic. As organizations adopt IPv6, developing robust security measures to mitigate the risks associated with this evolving threat landscape becomes crucial.
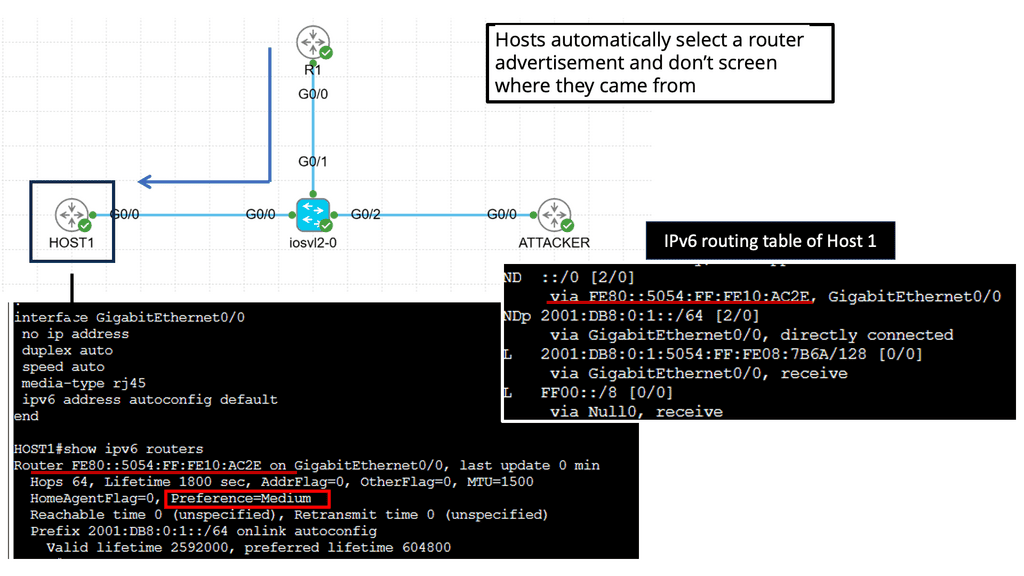
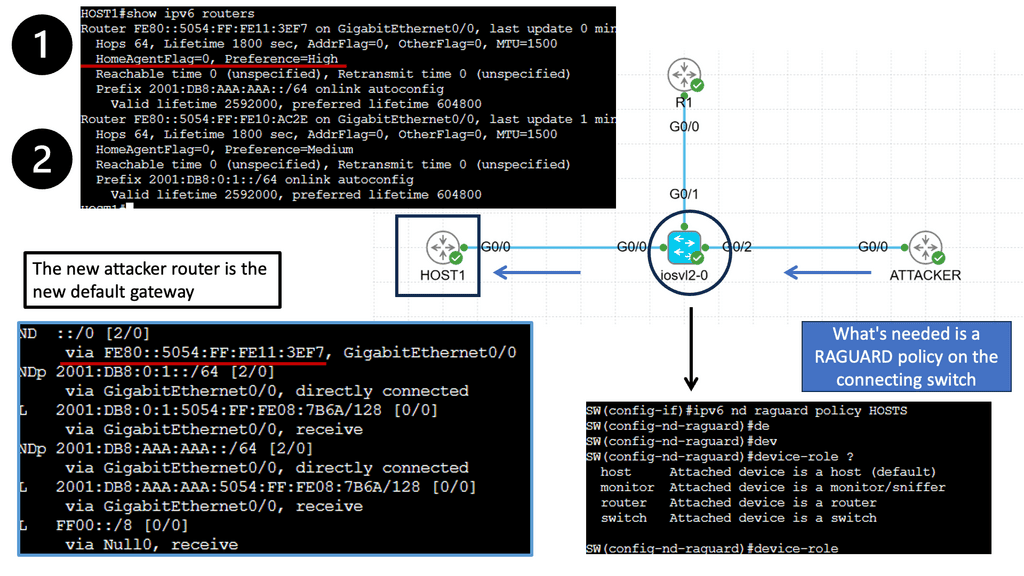
Understanding IPv6 RA Guard
To comprehend the significance of IPv6 RA Guard, it is essential to grasp the concept of Router Advertisements in IPv6 networks. These advertisements are used by routers to communicate network configuration information to neighboring hosts. RA Guard acts as a security mechanism to prevent rogue or unauthorized devices from sending malicious RAs, thus protecting the integrity and stability of the network.
Implementing IPv6 RA Guard requires careful configuration and consideration of network infrastructure. It involves enabling RA Guard on network switches or routers, which then analyze and filter incoming RAs based on specific criteria. These criteria include source MAC address, VLAN, or interface. By selectively allowing or blocking RAs, RA Guard helps ensure that only legitimate router advertisements are accepted.
To maximize the effectiveness of the IPv6 RA Guard, it is crucial to follow some best practices. Firstly, network equipment firmware must be regularly updated to ensure compatibility with the latest RA Guard features and improvements. Secondly, RA Guard can be deployed with other security measures, such as DHCPv6 Guard or Secure Neighbor Discovery (SEND), to create a multi-layered defense against potential threats. Monitor and analyze network traffic to identify anomalies or potential evasion attempts.
**Denial of Service (DoS) Attacks in IPv6**
Denial of Service (DoS) attacks can cripple networks, rendering them inaccessible to legitimate users. In the context of IPv6, attackers leverage its features to launch devastating DoS attacks, such as the ICMPv6 Flood, Fragmentation-based Attacks, and TCP SYN Flood. We examine these attacks and suggest mitigation strategies.
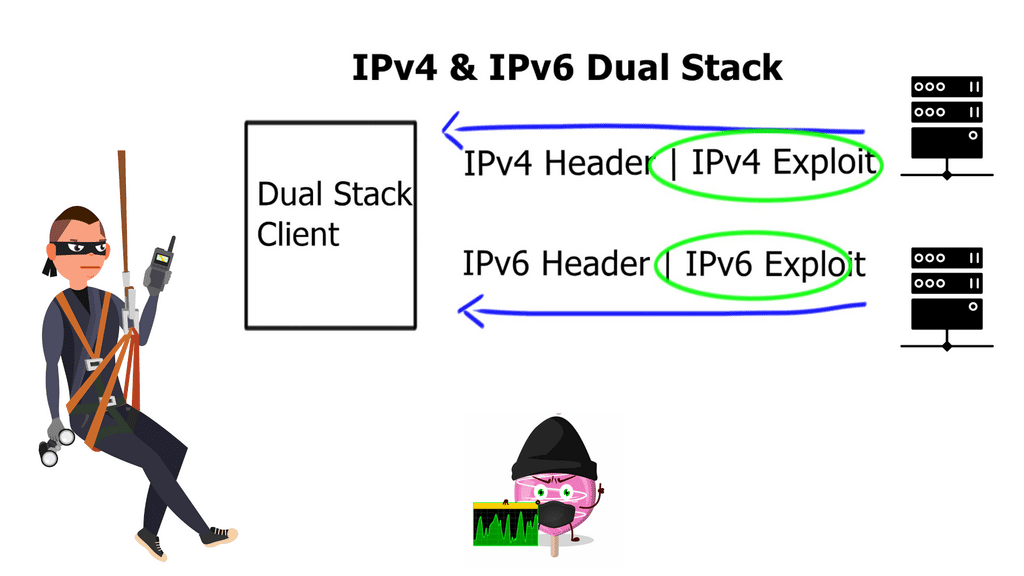
IPv6, with its larger address space, enhanced security features, and improved header structure, was designed to mitigate some of the vulnerabilities inherent in IPv4. However, this advancement has also opened up new avenues for attackers to exploit. The stateless nature of IPv6 and the complexity of its addressing scheme have introduced novel attack vectors that cybercriminals are quick to exploit.
**Types of DoS Attacks in IPv6**
In the realm of IPv6, attackers have a diverse arsenal at their disposal. From flooding attacks, such as ICMPv6 and NDP-based floods, to resource depletion attacks, like TCP SYN floods, attackers can cripple networks and exhaust system resources. Moreover, the transition mechanisms between IPv4 and IPv6 create additional attack surfaces, making it imperative for organizations to stay vigilant.
**Change in perception and landscape**
In the early days of the Internet, interconnected systems comprised research organizations and universities. There wasn’t a sinister dark side, and the Internet was used for trusted sharing, designed without security. However, things rapidly changed, and now the Internet consists of interconnected commercial groups of systems running IPv4 and IPv6. Now, Internet-facing components are challenged with large-scale Internet threats, such as malware, worms, and various service exhaustion DoS attacks.
**New types of IPv6 attacks**
Along with the birth of new IPv6 attacks based on, for example, IPv6 broadcast that requires new mitigation techniques such as IPv6 filtering and the ability to manage against security issues from IPv6 fragmentation. IP networks carry data and control packets in a common “pipe.” The common “pipe” and its payload require secured infrastructure. Legacy is the same for both versions of the IP protocol. IPv4 and IPv6 systems need security to protect the “pipe” from outside intrusion.
Related: Before you proceed, you may find the following useful:
IPv6 Attacks
IPv6 Security
In those early days of IPv4-connected hosts, the Internet consisted of a few trusted networks of well-known researchers. If security was needed, it was usually just the fundamentals of authentication/authorization, which could have been included in the application code. Numerous years later, IPsec was introduced when IPv4 had already been widely deployed.
However, it was cumbersome to deploy into existing networks. As a result, IPsec could be more commonly deployed in many IPv4 scenarios. This is in contrast to IPv6, which initially had the notion that fundamental security functionality had to be included in the base protocol to be used on any Internet platform.
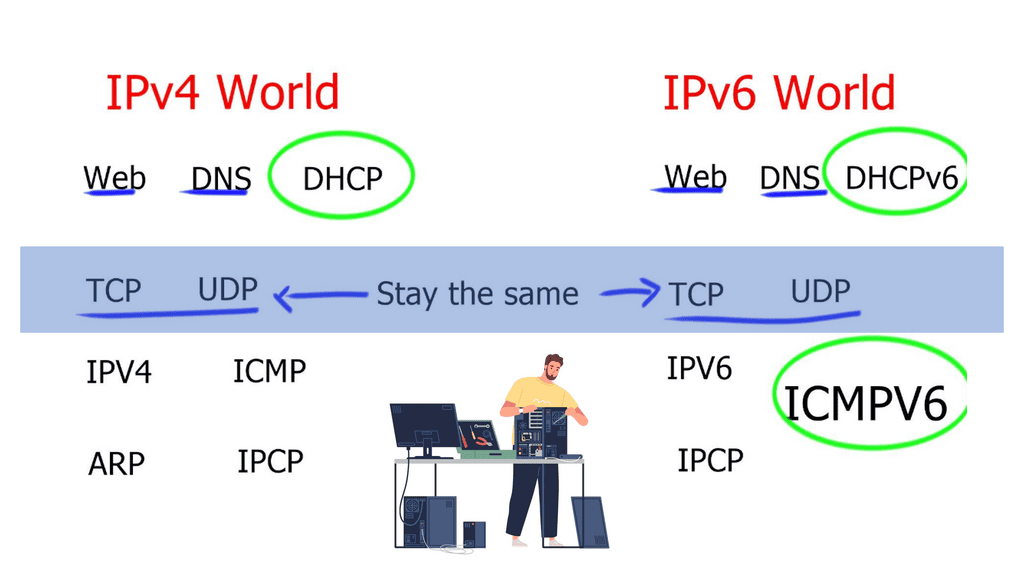
The main difference between IPv6 and IPv4 is the size of addresses: 128 bits for IPv6 versus 32 bits for IPv4—the increase in address size results in a larger IPv6 header. The minimum size of the IPv6 header is twice the size of the IPv4 minimum header. The Internet has evolved to use IPv6 and its new structures. Threats have also evolved to cope with the size and hierarchical nature of IPv6.
Guide: Using IPv6 Filters
In the following, we have an IPv6 filter configured on R1. An IPv6 filter is similar to that of IPv4 access lists. However, it would be best if you kept in mind the following:
- IPv4 access-lists can be standard or extended, numbered or named. IPv6 only has named extended access-lists.
- IPv4 access-lists have an invisible implicit deny any at the bottom of every access-list. IPv6 access-lists have three invisible statements at the bottom:
- permit icmp any any nd-na
- permit icmp any any nd-ns
- deny ipv6 any any
As a security best practice, I would also have the command: no ipv6 unreachables on the interface.
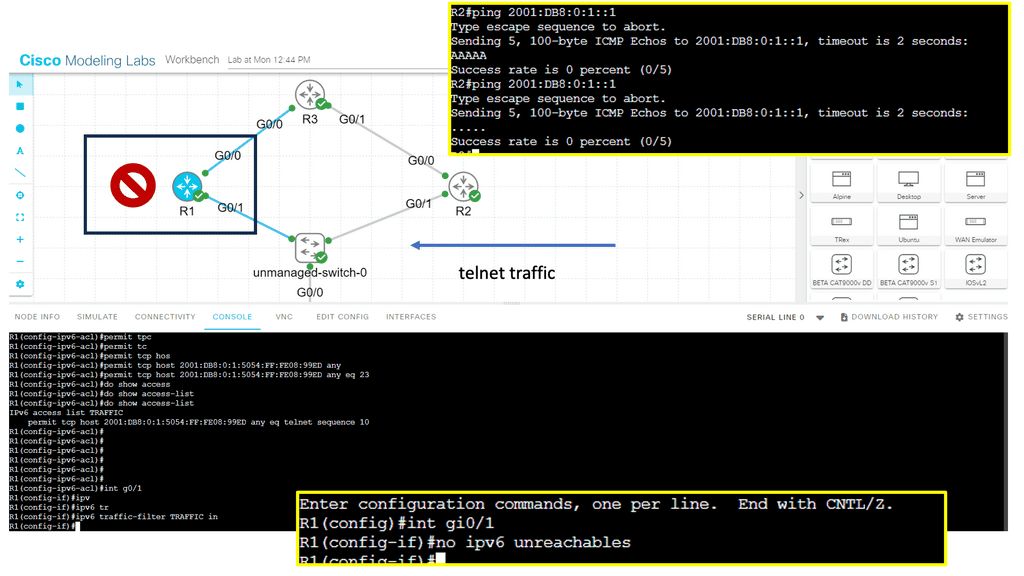
**Highlighting the types of IPv6 Attacks**
Neighbor Discovery Protocol (NDP) Attacks:
The Neighbor Discovery Protocol (NDP) is a fundamental component of IPv6 networks. Attackers can exploit vulnerabilities in NDP to launch various attacks, such as Neighbor Advertisement Spoofing, Router Advertisement Spoofing, and Neighbor Unreachability Detection (NUD) attacks. These attacks can result in traffic interception, denial of service, or even network infiltration.
Flood Attacks:
IPv6 flood attacks, similar to their IPv4 counterparts, aim to overwhelm a target device or network with excessive traffic. These attacks can lead to network congestion, service disruption, and resource exhaustion. Flood attacks targeting IPv6, such as ICMPv6, NDP, or UDP floods, can exploit vulnerabilities in network infrastructure or exhaust network resources like bandwidth or CPU.
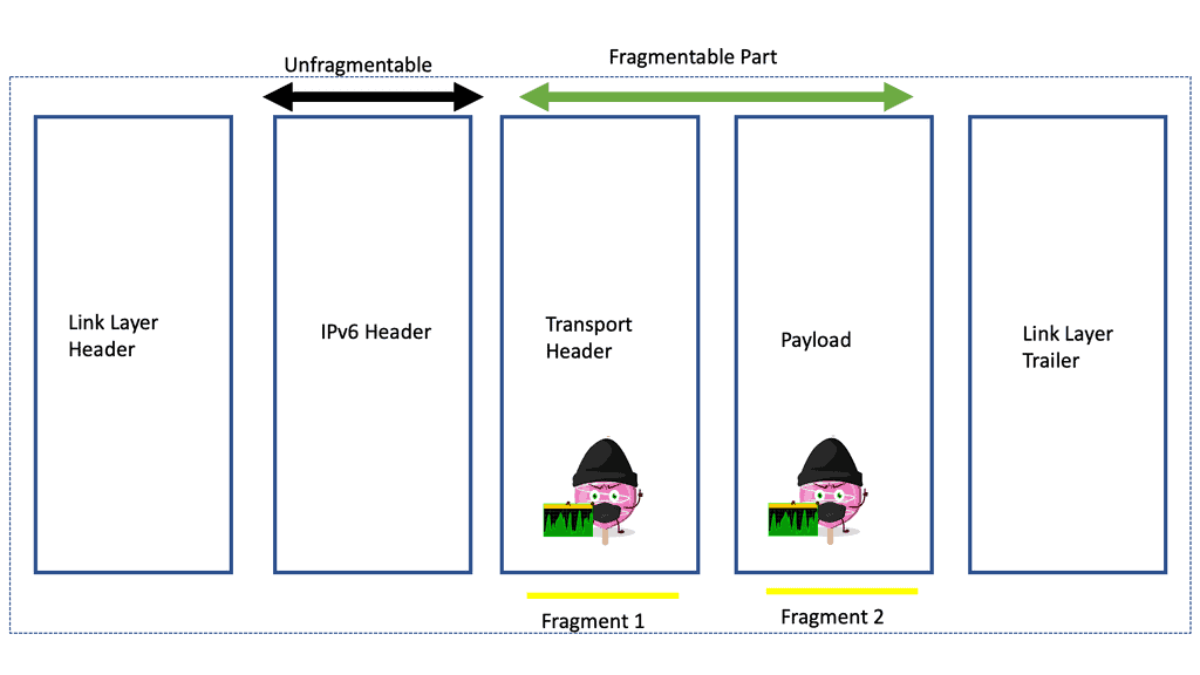
Fragmentation Attacks:
IPv6 fragmentation allows large packets to be divided into smaller fragments, which are reassembled at the receiving end. Attackers can exploit fragmentation vulnerabilities to bypass security measures, evade detection, or launch Denial of Service (DoS) attacks. Fragmentation attacks can overload network resources or cause packet loss, disrupting communication.
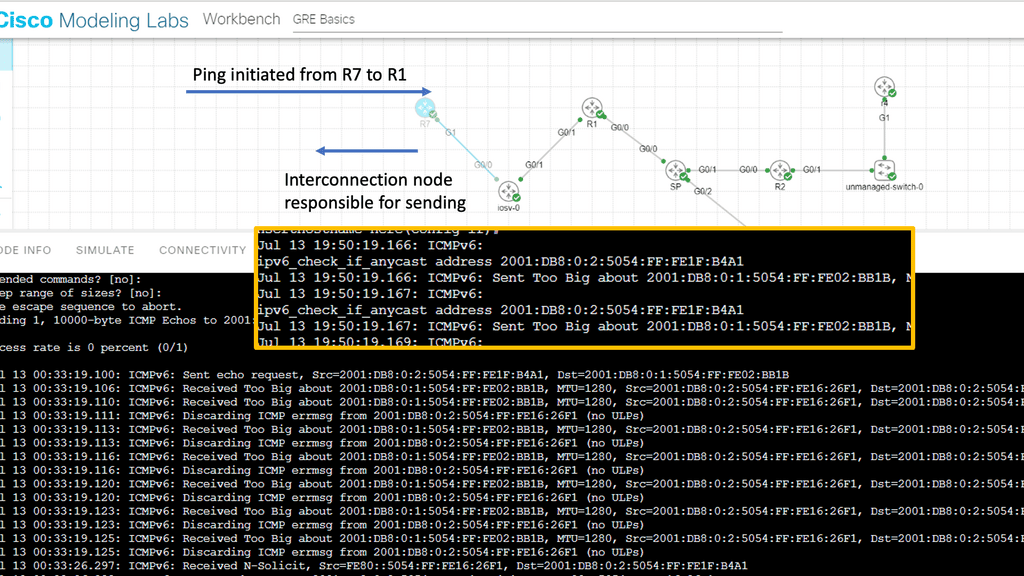
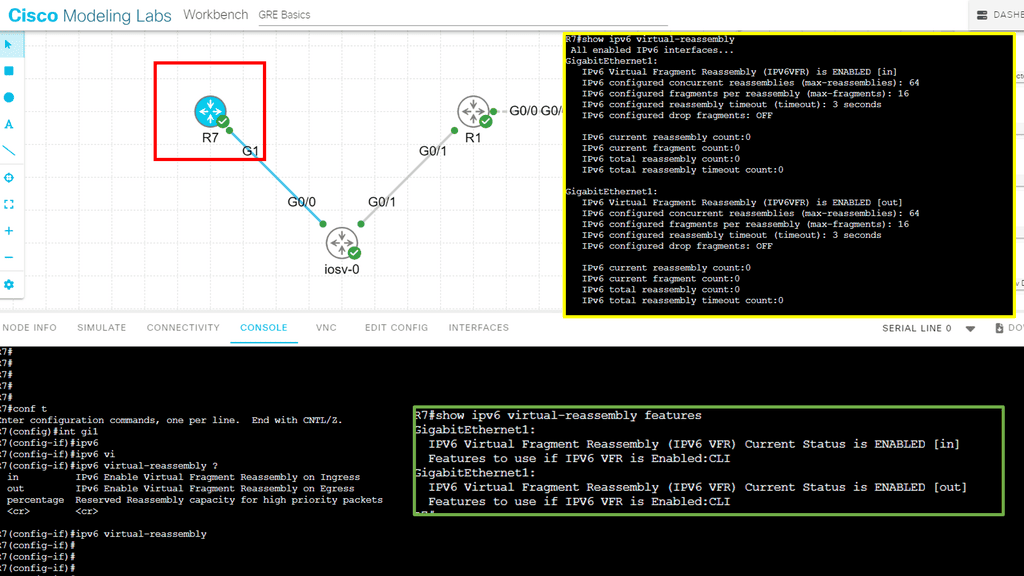
Guide on IPv6 fragmentation attacks
You can set IPv6 virtual reassembly on the interface to prevent fragmentation attacks.IPv6 virtual reassembly is a process that reconstructs fragmented packets at the receiving end of a network transmission. When transmitted across the Internet, packets are divided into smaller units. Due to various factors, such as network congestion, these packets may arrive out of order or get fragmented.
Virtual reassembly ensures these packets are correctly reassembled and delivered to the intended recipient. This mechanism is crucial for maintaining data integrity, reducing latency, and optimizing network performance.
Detailing IPv6 Attacks
One of the most basic forms of IPv6 security is ingress and egress filtering at Internet Edge. However, attackers can forge an IPv6 packet with specially crafted packets and spoofed IPv6 addresses, so filtering based on IP addresses is required. Spoofing modifies source IP addresses or ports to appear if packets are initiated from another location.
IPv4 networks are susceptible to “Smurf” broadcast amplification attacks where a packet from a forged unknowing victim’s address is sent to the subnet broadcast of an IPv4 segment. The attack type employs the Spoofing technique, in which the victim’s IP address is used as the source of the attack. The broadcast subnet is the all-one host address of each subnet (example 192.168.1.255 255.255.255.0).
As we send to the broadcast address, all hosts on the subnet receive a packet consisting of an ICMP-ECHO with a payload. Hosts automatically send back an ECHO-REPLY to the victim’s spoofed address. As a result, the victim gets bombarded with packets (ECHO-REPLIES), forcing CPU interrupts, eventually resulting in a Denial of Service (DoS) attack. Cisco IOS has the command “no IP directed-broadcast” on by default, but some poorly designed networks use directed broadcast for next-hop processing.
So we don’t have to worry about this in IPv6? IPv6 uses multicasts and is not broadcast for communication.
Multicast amplification attacks
IPv6 does not use a type of IPv6 broadcast as its communication, but it uses various multicast addresses. You are essentially doing the same thing but differently. Multicast is the method for one-to-many communications. For this reason-IPv6, multicast addresses can be used for traffic amplification.
The Smurf6 tools are a type of Smurf attack run with Kali Linux. It generates lots of local ICMPv6 traffic used to DoS attack-local systems. Smurf6 sends locally generated ICMPv6 ECHO REQUEST packets toward the “all routers” multicast address of FF02::2.
As this multicast address represents all routers on the segment, they all respond with ICMPv6 ECHO RESPONSE to the victims’ source address. The multicast address can be used for DoS attacks. It is essential to control who can send to these multicast addresses and who can respond to a multicast packet.
**IPv6 security and important IPv6 RFCs**
RFC 2463 “Internet Control Message Protocol (ICMPv6) for the Internet Protocol Version 6 Specification” states that no ICMP message can be generated in response to an IPv6 packet destined for multicast groups. This protects your host’s IPv6 stack and is designed with RFC 2463 specifications. Smurf attacks should not be a threat if all hosts comply with RFC 2463. However, there are two exemptions to this rule. “The “packet too big” and “parameter problem ICMP” are generated in response to packets destined for a multicast group.
Prevent uncontrolled forwarding of these ICMPv6 message types, and filter based on the ICMPv6 type. To prevent packet amplification attacks for “packet too big” and “parameter problem ICMP” filter based on ICMPv6 Type 2: “Packet too big” and ICMPv6 Type 4: “Parameter problem.” You can also rate-limit these message types with the ipv6 ICMP rate-limit command.
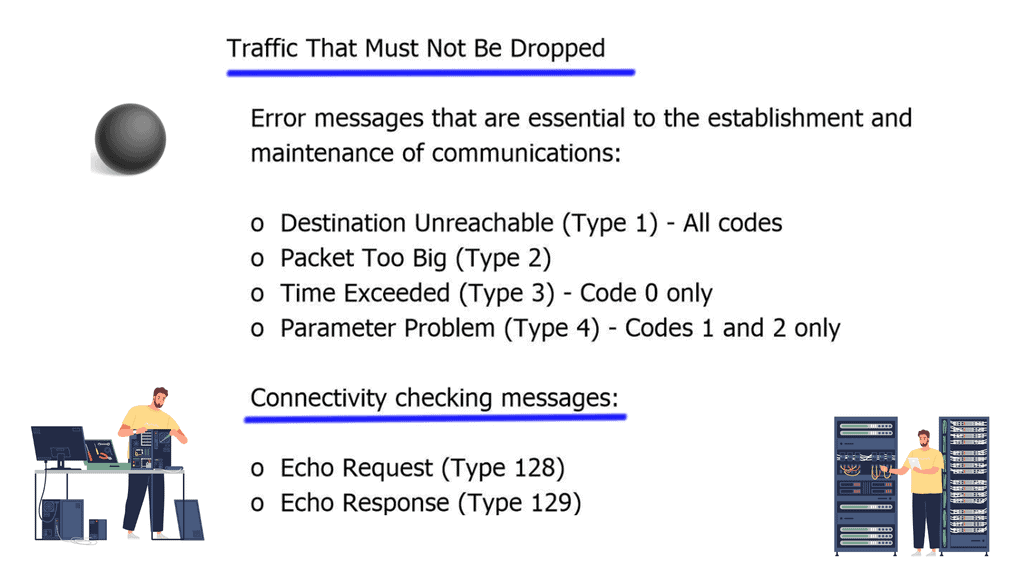
RFC 4890 outlines guidelines for filtering ICMPv6 messages in firewalls. Filter these options or only allow trusted sources and deny everything else. If you are unsure hosts comply with these RFCs, perform ingress filtering of packets with IPv6 multicast source addresses. As a recommendation, purchase firewalls that support stateful filtering of IPv6 packets and ICMPv6 messages. It’s always better to prevent an attack than react to one.
Recap: Mitigating IPv6 Attacks:
a) Network Segmentation:
Segmenting networks into smaller subnets can limit the impact of potential attacks by containing them within specific network segments. By implementing strict access controls, organizations can minimize the lateral movement of attackers within their network infrastructure.
b. Intrusion Detection and Prevention Systems (IDPS):
Deploying IDPS solutions can help organizations detect and prevent IPv6 attacks. IDPS solutions monitor network traffic, identify suspicious patterns, and take appropriate actions to mitigate the attacks in real-time.
c. Regular Security Audits:
Regular security audits of network infrastructure, systems, and applications can help identify and address vulnerabilities before attackers exploit them. Organizations should also keep their network equipment and software patched and up to date.
Final Points: IPv6 Attacks
As the world becomes more connected, robust security measures to protect against IPv6 attacks are paramount. Understanding the risks associated with IPv6 and implementing appropriate security measures can help organizations safeguard their networks and data. By staying vigilant and proactive, we can ensure a secure and reliable internet experience for all users in the IPv6 era.
While IPv6 was designed with better security features than IPv4, these features need to be correctly implemented to be effective. For instance, IPv6 supports IPsec, a suite of protocols for securing internet protocol communications by authenticating and encrypting each IP packet. However, IPsec must be properly configured and managed to provide the intended protection.
As we continue to embrace the vast potential of IPv6, understanding the associated security risks becomes imperative. By familiarizing yourself with common attack vectors, employing effective mitigation strategies, and leveraging IPv6’s security features, you can better protect your network from potential threats. Staying informed and proactive is key to navigating the complexities of the digital frontier securely.
Summary: IPv6 Attacks
In today’s interconnected digital landscape, Internet Protocol version 6 (IPv6) has emerged as a critical infrastructure for enabling seamless communication and accommodating the ever-growing number of devices. However, with the rise of IPv6, new vulnerabilities and attack vectors have also surfaced. In this blog post, we explored the world of IPv6 attacks, shedding light on their mechanisms, potential risks, and mitigation strategies.
Understanding IPv6 Attacks
IPv6 attacks encompass a wide range of malicious activities targeting the protocol’s vulnerabilities. From address scanning and spoofing to router vulnerabilities and neighbor discovery exploits, attackers have found various ways to exploit IPv6’s weaknesses. Understanding these attack vectors is crucial for effective protection.
Common Types of IPv6 Attacks
1. Address Resolution Protocol (ARP) Spoofing: This attack involves manipulating the ARP cache to redirect traffic, intercept sensitive information, or launch further attacks.
2. Router Advertisement (RA) Spoofing: By sending forged RAs, attackers can misconfigure routing tables, leading to traffic hijacking or DoS attacks.
3. Neighbor Discovery Protocol (NDP) Attacks: Attackers can exploit vulnerabilities in the NDP to perform address spoofing, router redirection, or even denial of service attacks.
4. Fragmentation Attacks: Fragmentation header manipulation can cause packet reassembly issues, leading to resource exhaustion or bypassing security measures.
Implications and Risks
IPv6 attacks pose significant risks to organizations and individuals alike. These risks include unauthorized network access, data exfiltration, service disruption, compromised confidentiality, integrity, and availability of network resources. With the expanding adoption of IPv6, the impact of these attacks can be far-reaching.
Mitigation Strategies
1. Network Monitoring and Intrusion Detection Systems: Implementing robust monitoring solutions can help detect and respond to suspicious activities promptly.
2. Access Control Lists and Firewalls: Configuring ACLs and firewalls to filter and restrict IPv6 traffic can mitigate potential attack vectors.
3. Secure Network Architecture: Secure network design principles, such as proper segmentation and VLAN configuration, can limit the attack surface.
4. Regular Patching and Firmware Updates: It is crucial to keep network devices up to date with the latest security patches and firmware versions to address known vulnerabilities.
Conclusion:
As the world becomes increasingly reliant on IPv6, understanding the threats it faces is paramount. Organizations can better protect their networks and data from potential harm by being aware of the different types of attacks and their implications and implementing robust mitigation strategies. Stay vigilant, stay informed, and stay secure in the ever-evolving landscape of IPv6.