Technology Insight For Microsegmentation
In today's digital landscape, cybersecurity has become a critical concern for organizations. With the ever-evolving threat landscape, traditional security measures are no longer sufficient to protect sensitive data and systems. Enter microsegmentation - a cutting-edge security technique that offers granular control and enhanced protection. This blog post will explore microsegmentation and its benefits for modern businesses.
Microsegmentation is a security strategy that divides a network into small, isolated segments, allowing for more refined control over data traffic and access privileges. Unlike traditional network security approaches that rely on perimeter defenses, microsegmentation focuses on securing each segment within a network. By implementing this technique, organizations can establish strict security policies and reduce the risk of lateral movement within their networks.
Microsegmentation offers several compelling benefits for organizations. Firstly, it enhances overall network security by limiting the attack surface and reducing the chances of unauthorized access. Secondly, it enables organizations to enforce security policies at a granular level, ensuring that each segment adheres to the necessary security measures. Additionally, microsegmentation facilitates better network visibility and monitoring, allowing for prompt detection and response to potential threats.
Implementing microsegmentation requires careful planning and consideration. Organizations must begin by conducting a comprehensive network assessment to identify critical segments and determine the appropriate security policies for each. Next, they must choose a suitable microsegmentation solution that aligns with their specific requirements. It is crucial to involve all relevant stakeholders and ensure seamless integration with existing network infrastructure. Regular testing and monitoring should also be part of the implementation process to maintain optimal security posture.
While microsegmentation holds immense potential, it is not without its challenges. One common challenge is the complexity of managing a highly segmented network. To address this, organizations should invest in robust management tools and automation capabilities. Additionally, effective training and education programs can empower IT teams to navigate the intricacies of microsegmentation successfully. Regular audits and vulnerability assessments can also help identify any potential gaps or misconfigurations.
Microsegmentation represents a powerful technology insight that can revolutionize network security. By implementing this approach, organizations can bolster their defense against cyber threats, enhance visibility, and gain more granular control over their network traffic. While challenges exist, careful planning, proper implementation, and ongoing management can ensure the successful deployment of microsegmentation. Embracing this cutting-edge technology can pave the way for a more secure and resilient network infrastructure.
Matt Conran
Highlights: Technology Insight For Microsegmentation
Understanding Microsegmentation
Microsegmentation is a network security technique that divides a network into small, isolated segments. Each segment, known as a microsegment, operates independently and has security policies and controls. By implementing microsegmentation, organizations can achieve granular control over their network traffic, limiting lateral movement and minimizing the impact of potential security breaches.
Microsegmentation offers several compelling benefits that can significantly enhance network security. Firstly, it strengthens the overall security posture by reducing the attack surface. The impact of a potential breach is contained by isolating critical assets and separating them from less secure areas.
Additionally, microsegmentation enables organizations to implement zero-trust security models, where every network segment is untrusted until proven otherwise. This approach provides an additional layer of protection by enforcing strict access controls and authentication measures.
**Implementing Microsegmentation**
– While microsegmentation is enticing, its implementation requires careful planning and consideration. Organizations must assess their network architecture, identify critical assets, and define segmentation policies. Additionally, selecting the right technology solution is crucial. Advanced network security tools with built-in microsegmentation capabilities simplify the implementation process, providing intuitive interfaces and automation features.
– Implementing microsegmentation may come with certain challenges that organizations need to address. One such challenge is the potential complexity of managing and monitoring multiple microsegments. Adequate network visibility tools and centralized management platforms can help mitigate this challenge by providing holistic oversight and control.
– Additionally, organizations must ensure clear communication and collaboration among IT teams, security personnel, and other stakeholders to align on segmentation policies and avoid any unintended disruptions to network connectivity.
**Key Techniques in Microsegmentation**
There are several techniques used to implement microsegmentation effectively:
1. **Policy-Based Segmentation**: This approach uses security policies to dictate how and when traffic can flow between segments. Policies are often based on factors like user identity, device type, or application being accessed.
2. **Identity-Based Segmentation**: By relying on the identity of users or devices, this technique allows organizations to ensure that only authenticated and authorized entities gain access to sensitive data or resources.
3. **Network-Based Segmentation**: This technique focuses on traffic patterns and behaviors, using them to determine segment boundaries. It’s often combined with machine learning to adapt to new threats or changes in network behavior dynamically.
**Challenges and Considerations**
Despite its advantages, implementing microsegmentation is not without its challenges. Organizations must carefully plan their network architecture and ensure they have the right tools and expertise to execute this strategy. Key considerations include understanding the network’s current state, defining clear security policies, and continuously monitoring traffic. Additionally, organizations should be prepared for the initial complexity and potential costs associated with transitioning to a microsegmented network.
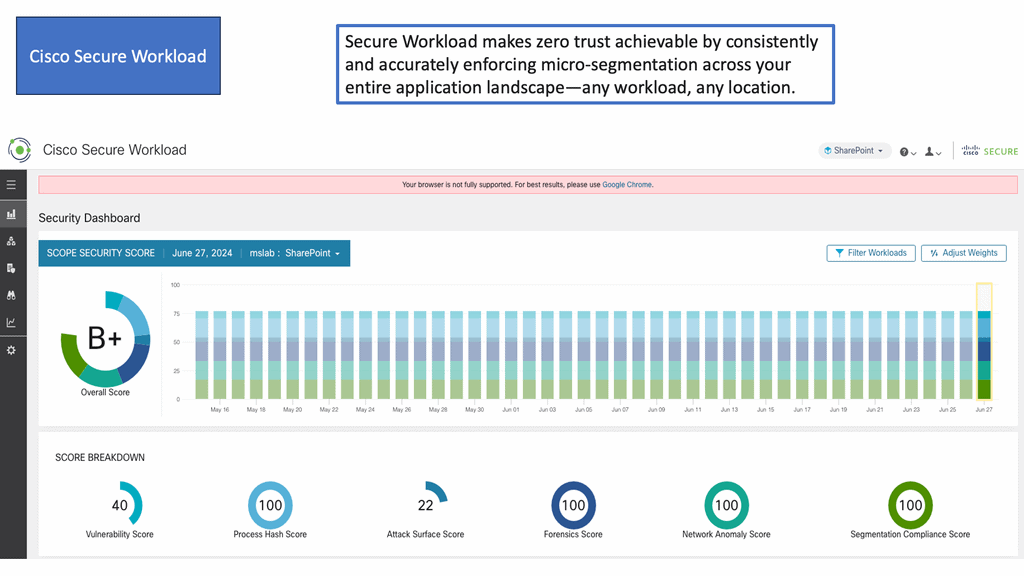
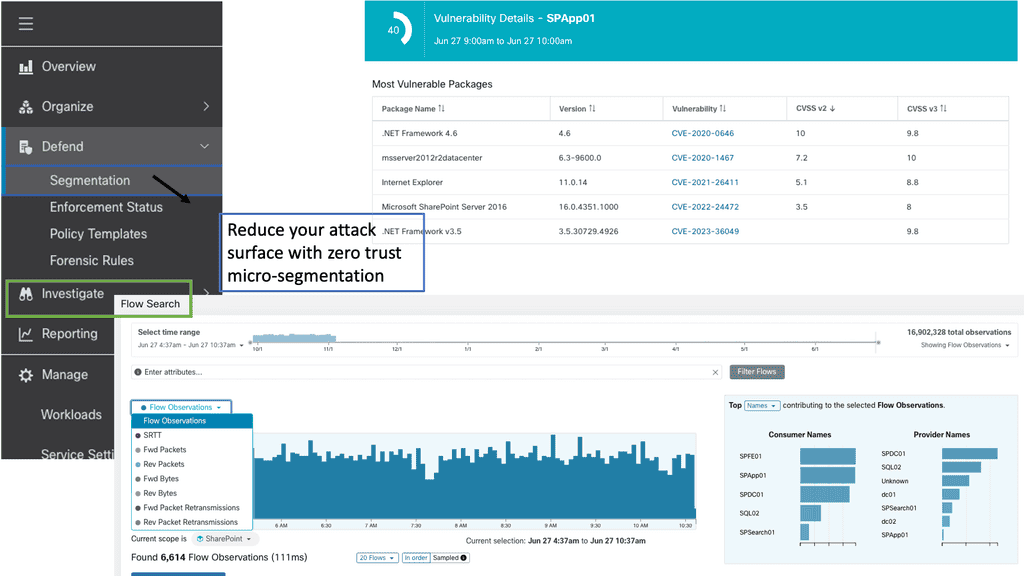
Example Product: Cisco Secure Workload
### Key Features of Cisco Secure Workload
**Visibility Across Multicloud Environments:** One of the standout features of Cisco Secure Workload is its ability to provide detailed visibility into your entire application landscape. Whether your applications are running on-premises, in private clouds, or across multiple public clouds, Cisco Secure Workload ensures you have a clear and comprehensive view of your workloads.
**Micro-Segmentation:** Cisco Secure Workload enables micro-segmentation, which allows you to create granular security policies tailored to specific workloads. This reduces the attack surface by ensuring that only authorized communications are permitted, thereby containing potential threats and minimizing damage.
**Behavioral Analysis and Anomaly Detection:** By leveraging advanced machine learning algorithms, Cisco Secure Workload continuously monitors the behavior of your applications and detects any anomalies that could indicate a security breach. This proactive approach allows you to address potential threats before they escalate.
### Benefits of Implementing Cisco Secure Workload
**Enhanced Security Posture:** Implementing Cisco Secure Workload significantly enhances your security posture by providing comprehensive visibility and control over your workloads. This ensures that you can quickly identify and respond to potential threats, reducing the risk of data breaches and other security incidents.
**Operational Efficiency:** With Cisco Secure Workload, you can automate many security tasks, freeing up your IT team to focus on more strategic initiatives. This not only improves operational efficiency but also ensures that your security measures are consistently applied across your entire infrastructure.
**Compliance and Reporting:** Cisco Secure Workload simplifies compliance by providing detailed reports and audit trails that demonstrate your adherence to security policies and regulatory requirements. This is particularly beneficial for organizations in highly regulated industries, such as healthcare and finance.
### How to Implement Cisco Secure Workload
**Assessment and Planning:** The first step in implementing Cisco Secure Workload is to conduct a thorough assessment of your current security posture and identify any gaps or vulnerabilities. This will help you develop a comprehensive plan that outlines the steps needed to deploy Cisco Secure Workload effectively.
**Deployment and Configuration:** Once your plan is in place, you can begin deploying Cisco Secure Workload across your environment. This involves configuring the solution to align with your specific security requirements and policies. Cisco provides detailed documentation and support to guide you through this process.
**Ongoing Management and Optimization:** After deployment, it’s essential to continuously monitor and optimize Cisco Secure Workload to ensure it remains effective in protecting your applications. This includes regularly reviewing security policies, updating configurations, and leveraging the solution’s advanced analytics to identify and mitigate potential threats.
The Road to Zero Trust
The number of cybersecurity discoveries has increased so much that the phrase “jump on the bandwagon” has become commonplace. It is rare for a concept or technology to have been discussed years ago, only to die out and gain traction later. One example of this is zero trust.
As architects, we identify the scope of the engagement and maintain a balance between security controls and alignment with the customer’s business. It is equally important for Zero Trust consultants to understand the “why” factor as a baseline for what the enterprise needs. Zero Trust involves more moving parts than a typical security augmentation project that identifies and implements a set of security controls.
Zero Trust is based on knowing who has access to what and building policies independently for each transaction. Zero Trust, however, cannot be completed within a single project cycle. Key stakeholders must be carefully introduced to a detailed roadmap spanning multiple technologies and teams. Self-improvement begins months before a conversation takes place and continues for years afterward.
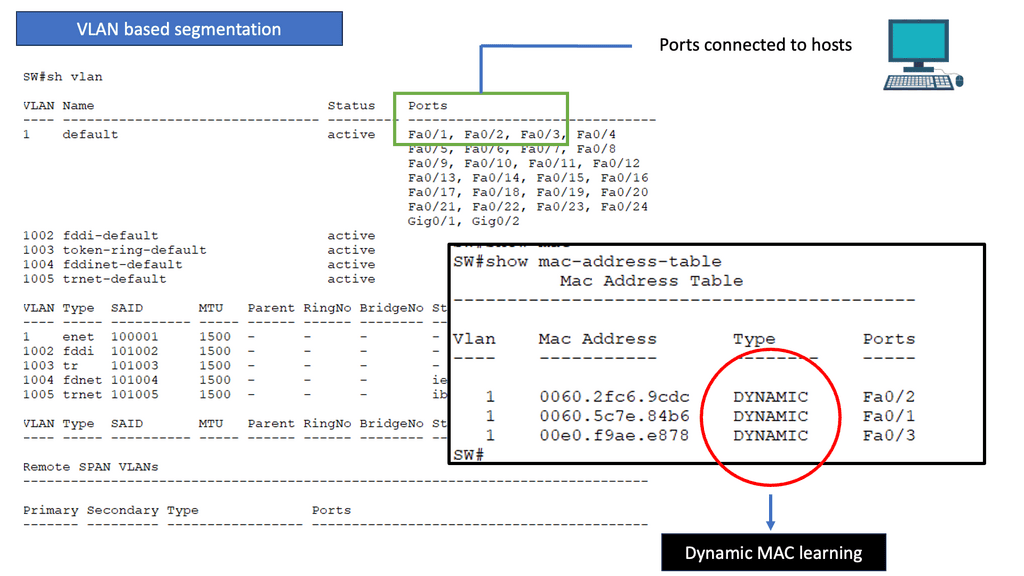
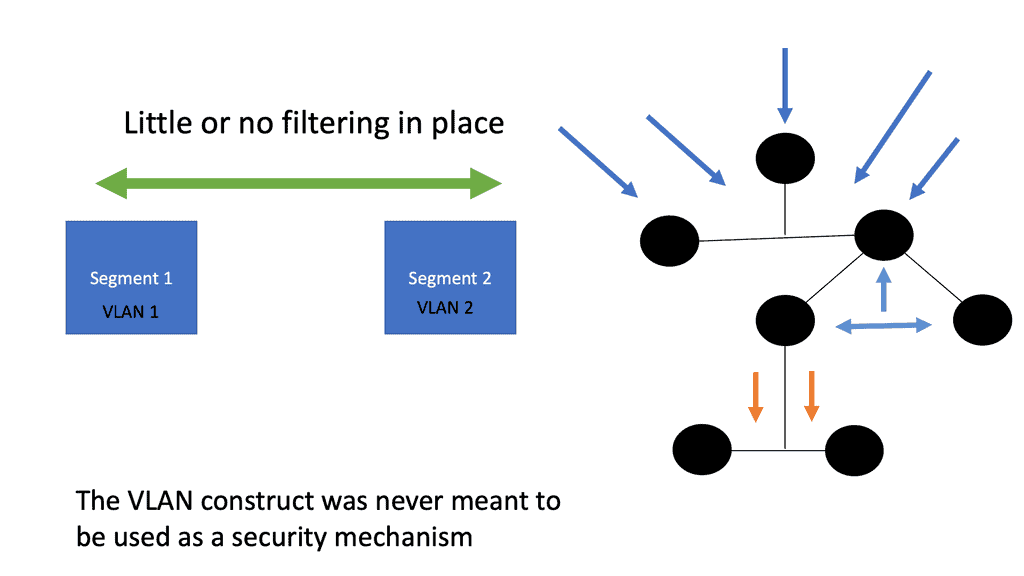
Issues of VLAN segmentation
To begin with, let’s establish a clear understanding of VLAN segmentation. VLANs, or Virtual Local Area Networks, allow networks to be logically divided into smaller, isolated segments. This division helps improve network performance, enhance security, and simplify network administration.
As networks grow and evolve, scalability becomes a crucial consideration. VLAN segmentation can become complex to manage as the number of VLANs and network devices increases. Network administrators must carefully plan and design VLAN architectures to accommodate future growth and scalability requirements.
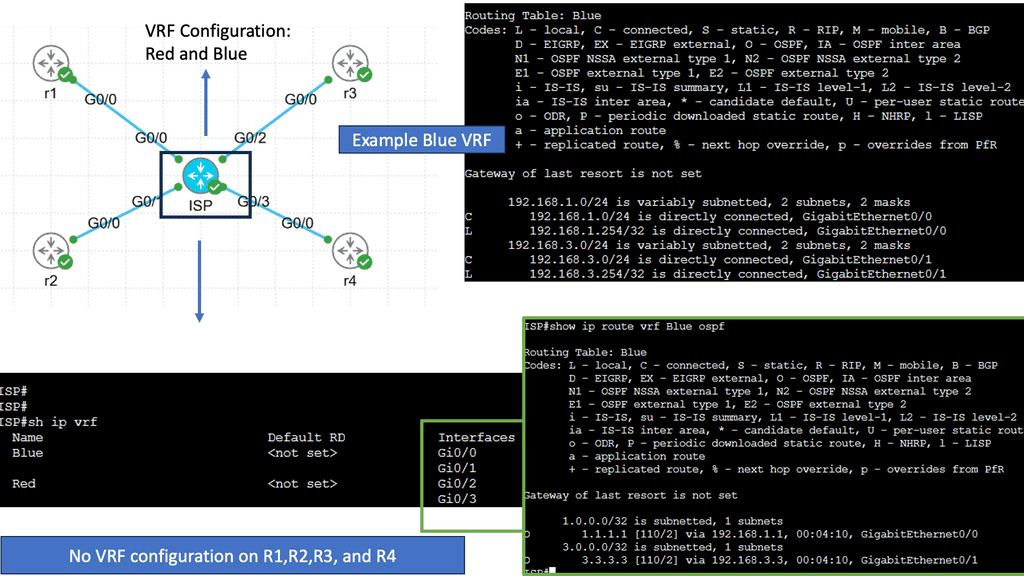
Segmentation with Virtual Routing and Forwarding
VRF is a mechanism that enables the creation of multiple virtual routing tables within a single routing infrastructure. Each VRF instance operates independently, maintaining its routing table, forwarding table, and associated network resources. This segregation allows for secure and efficient network virtualization, making VRF an essential tool for modern network design.
One of VRF’s key advantages is its ability to provide network segmentation. By employing VRF, organizations can create isolated routing domains, ensuring the separation of traffic and improving network security. Additionally, VRF enables efficient resource utilization by allowing different virtual networks to share a common physical infrastructure without interference or conflicts.
Use Cases for Virtual Routing and Forwarding
VRF finds extensive application in various scenarios. It is commonly used in Service Provider networks to provide virtual private networks (VPNs) to customers, ensuring secure and scalable connectivity. VRF is also utilized in enterprise networks to facilitate multi-tenancy, enabling different departments or business units to have their virtual routing instances.
Zero trust and microsegmentation
A- As a result of microsegmentation, a network is divided into smaller, discrete sections, each of which has its security policies and can be accessed separately. By confining threats and breaches to the compromised segment, microsegmentation increases network security.
B- A large ship is often divided into compartments below deck, each of which can be sealed off from the others. As a result, even if a leak fills one compartment with water, the rest will remain dry, and the ship will remain afloat. Network microsegmentation works similarly: one segment of the network may become compromised, but it can be easily isolated.
C- A Zero-Trust architecture relies heavily on microsegmentation. This architecture assumes that any traffic entering, leaving, or moving within a network could pose a threat. By microsegmenting, threats can be isolated before they spread, which prevents them from spreading laterally.
The call for microsegregation and zero trust
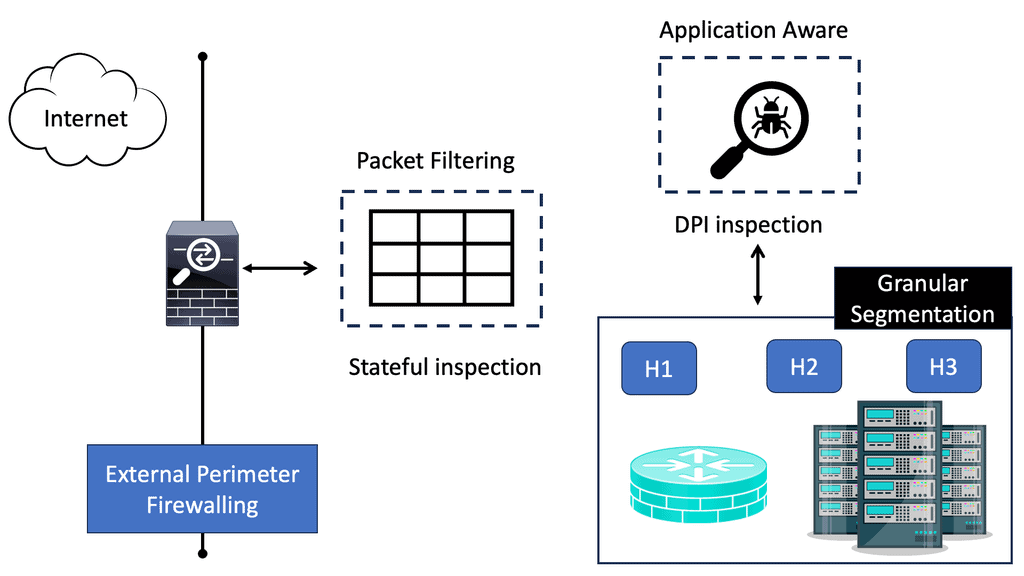
This diagram is turned inside out by the zero trust model. In the modern landscape of cyberattacks, stopgaps are significantly lacking in comparison to the designs of the past. Among the disadvantages are:
- Inadequate traffic inspections within zones
- Physical and logical host placement are inflexible
- A single point of failure
By removing network locality requirements, VPNs are no longer required. An IP address can be obtained remotely through a virtual private network (VPN). In the remote network, the traffic is decapsulated and routed after tunneling from the device. No one ever suspected that it was the greatest backdoor.
VPN, along with other modern network constructs, is suddenly rendered obsolete by declaring network location to be of no value. By putting enforcement at the edge of the network, this mandate reduces the core’s responsibility while pushing enforcement as far as possible.
In addition, stateful firewalls are available in all major operating systems, and advances in switching and routing have made it possible to install advanced capabilities at the edge. It is time for a paradigm shift based on all of these gains.
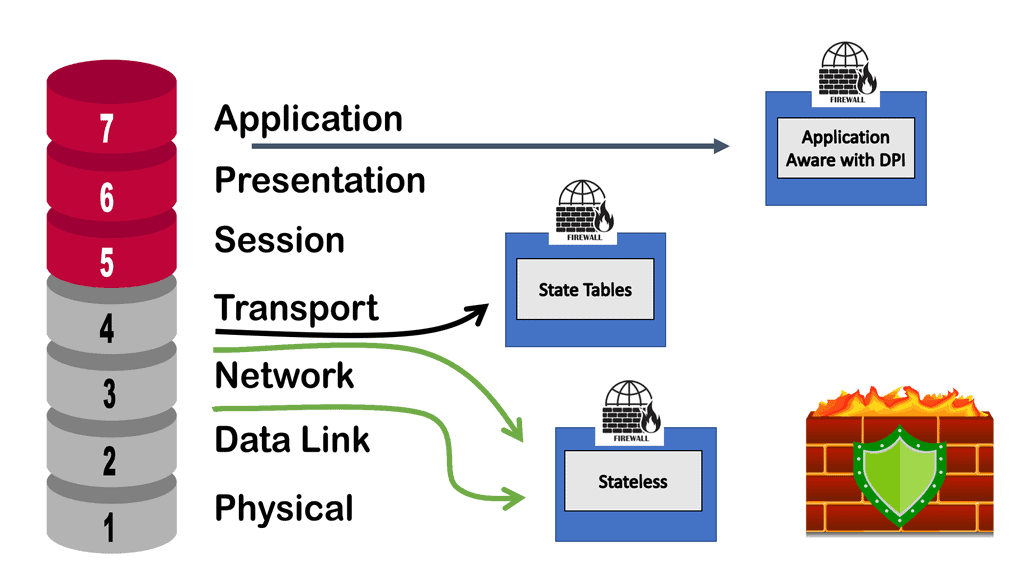
Implementing Zero Trust & Microsegmentation
Micro-segmentation is a fundamental component of implementing a zero-trust network. It divides the network into smaller, more manageable, and secure zones, enabling organizations to precisely regulate data flow between different sectors of the network.
Zero trust emphasizes verification over blind trust, which requires this level of control. Regardless of the network environment, each segment is subject to strict access and security policies.
Microsegmentation enables the following capabilities:
- Due to their isolation and relatively small size, segments can be closely monitored because they are more visible.
- By defining associated policies, granular access control is possible.
Micro-segmentation is crucial to mitigating the risk of threats spreading within the network in today’s ever-growing threat landscape. It prevents breaches from spreading and causing broader compromises by isolating them to specific segments. Micro-segmentation enables organizations to manage and secure diverse network environments with a unified framework as they adopt hybrid and multi-cloud architectures.
Key Technology – Software-defined Perimeter
Logically air-gapped, dynamically provisioned, on-demand software-defined perimeter networks minimize the risk of network-based attacks and isolate them from unsecured networks. Drop-all firewalls enable SDPs to enhance security by requiring authentication and authorization before users or devices can access assets concealed by the SDP system. SDP also restricts connections into the trusted zone based on who may connect, from what devices to what services and infrastructure, and other factors.
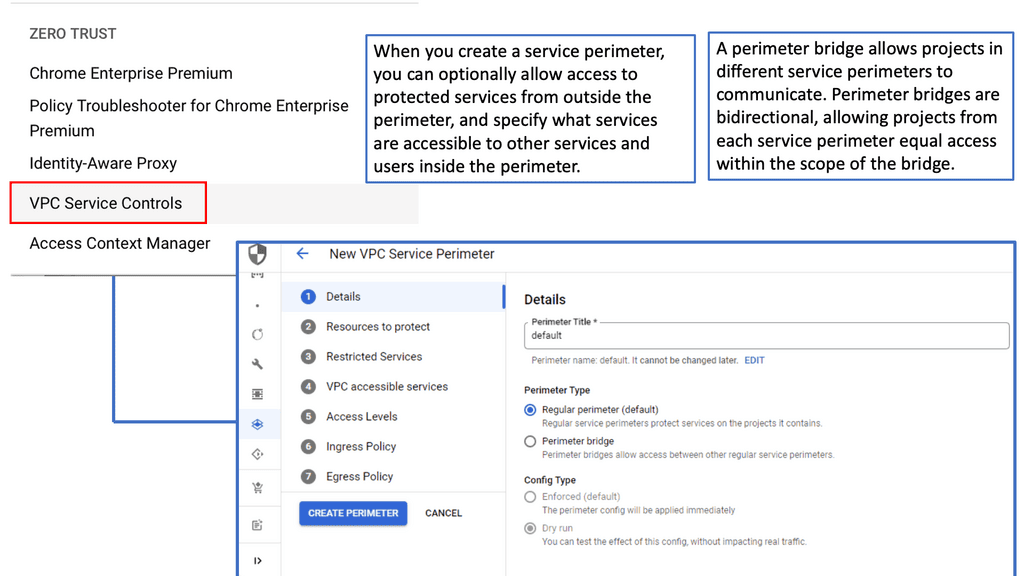
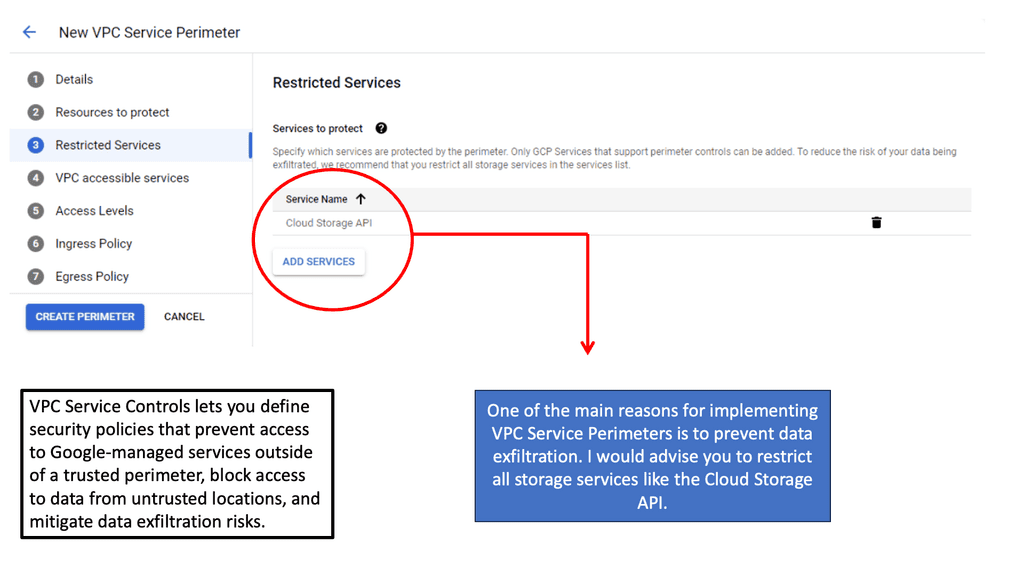
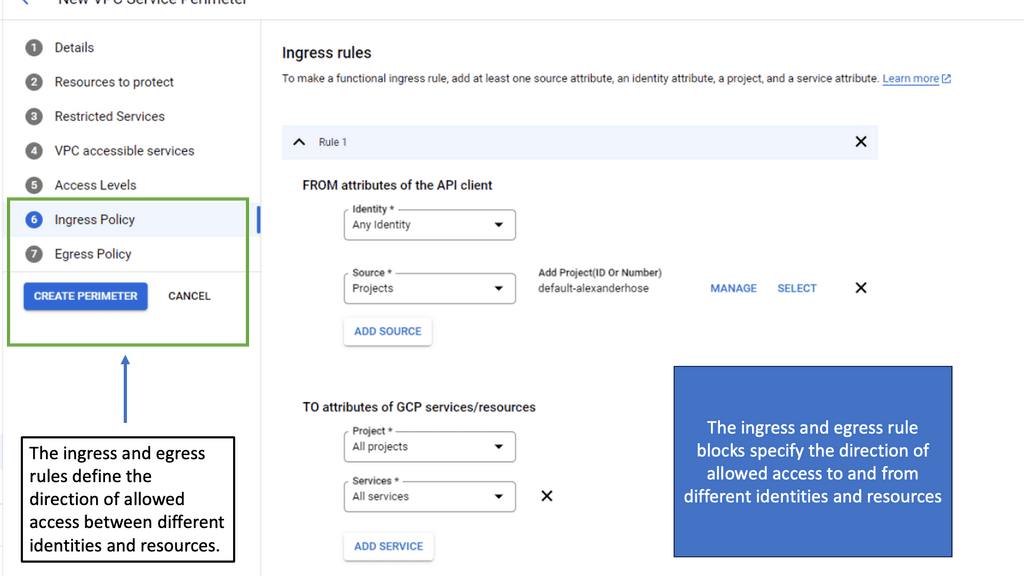
SDP with VPC Service Controls
### Understanding VPC Service Controls
VPC Service Controls offer an additional layer of security for your Google Cloud resources by defining a security perimeter around your services. This feature is particularly valuable in preventing data exfiltration, ensuring that only authorized access occurs within specified perimeters. By creating these controlled environments, organizations can enforce stricter access policies and reduce unauthorized data transfers, a critical concern in today’s data-centric world.
### The Role of Microsegmentation
Microsegmentation is a security technique that involves dividing a network into smaller, isolated segments to enhance control over data traffic. When integrated with VPC Service Controls, microsegmentation becomes even more powerful. It allows for granular security policies that are not just based on IP addresses but also on identity and context. This synergy ensures that each segment of your cloud environment is independently secure, minimizing the risk of lateral movement by potential attackers.
### Implementing VPC Service Controls in Google Cloud
Setting up VPC Service Controls in Google Cloud is a straightforward process that begins with defining your service perimeters. These perimeters act as virtual boundaries around your cloud resources. By leveraging Google Cloud’s comprehensive suite of tools, administrators can easily configure and manage these perimeters. The integration with Identity and Access Management (IAM) further strengthens these controls, allowing for precise access management based on user roles and responsibilities.
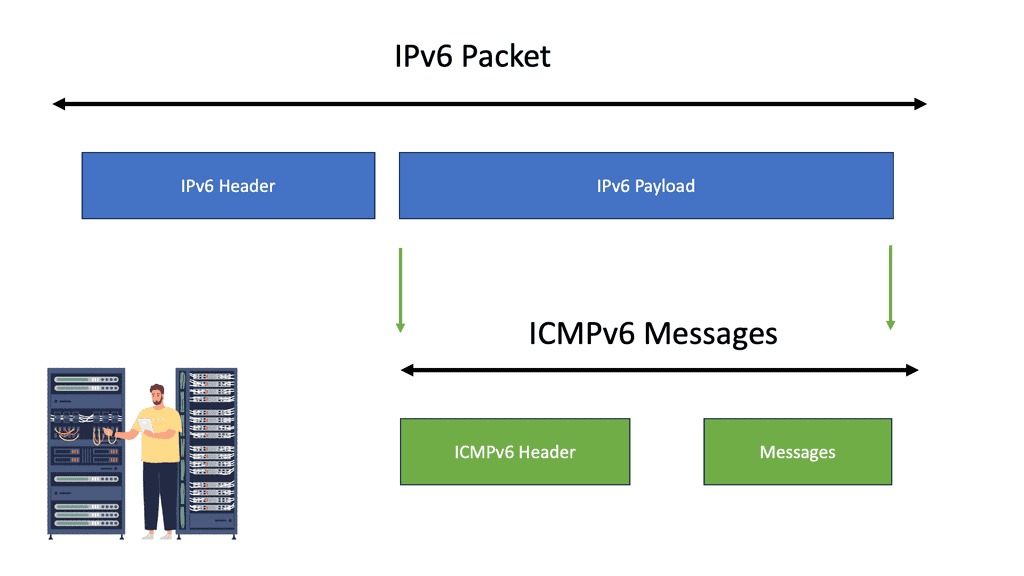
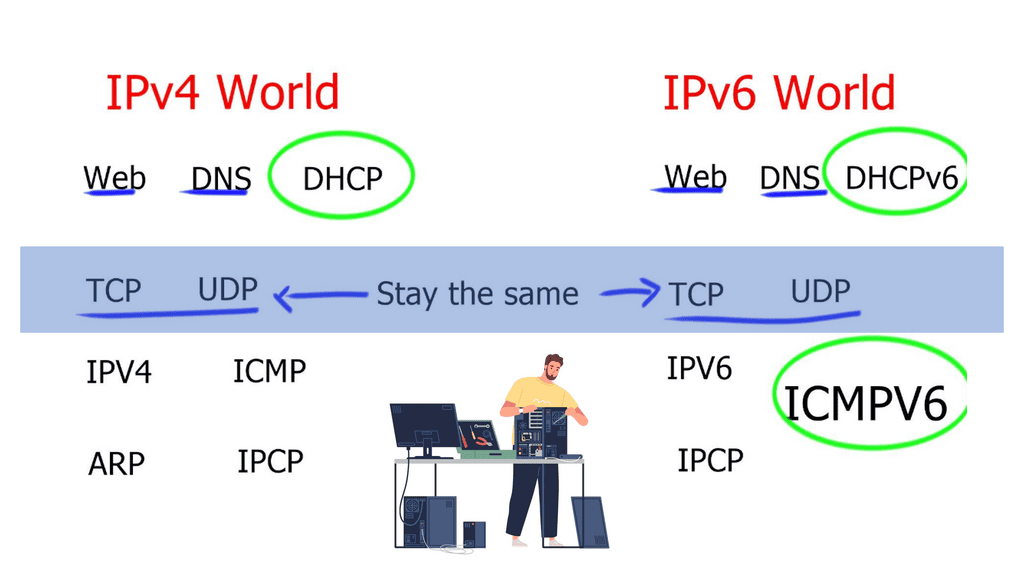
IPv6 Data Center Microsegmentation
When examining a technology insight for microsegmentation, we can consider using IPv6 for the data center network microsegmentation. Datacenter micro-segmentation techniques vary depending on the data center design requirements. However, the result will be more or less the same with your technique.
Network microsegmentation is a network security technique that enables security architects to logically divide the data center into distinct security segments down to the individual workload level, then define security controls and deliver services for each segment. In this technology insight for microsegmentation, we will address IPv6 micro-segmentation.
**Implementing IPv6 Microsegmentation: Best Practices**
Successfully deploying IPv6 microsegmentation requires careful planning and execution. Organizations should begin by conducting a thorough assessment of their existing network infrastructure to identify areas that would benefit most from segmentation. It’s crucial to define clear segmentation policies and ensure that they align with the organization’s overall security strategy. Additionally, leveraging automation tools can help streamline the implementation process and ensure that segmentation policies are consistently applied across the network.
**Overcoming Challenges in IPv6 Microsegmentation**
Despite its many advantages, implementing IPv6 microsegmentation can present certain challenges. One of the main obstacles is the need for adequate training and expertise to manage the more complex network configurations that come with microsegmentation. Organizations may also face difficulties in integrating microsegmentation with existing network infrastructure and security tools. To overcome these challenges, it’s essential to invest in training and seek out solutions that offer seamless integration with current systems.
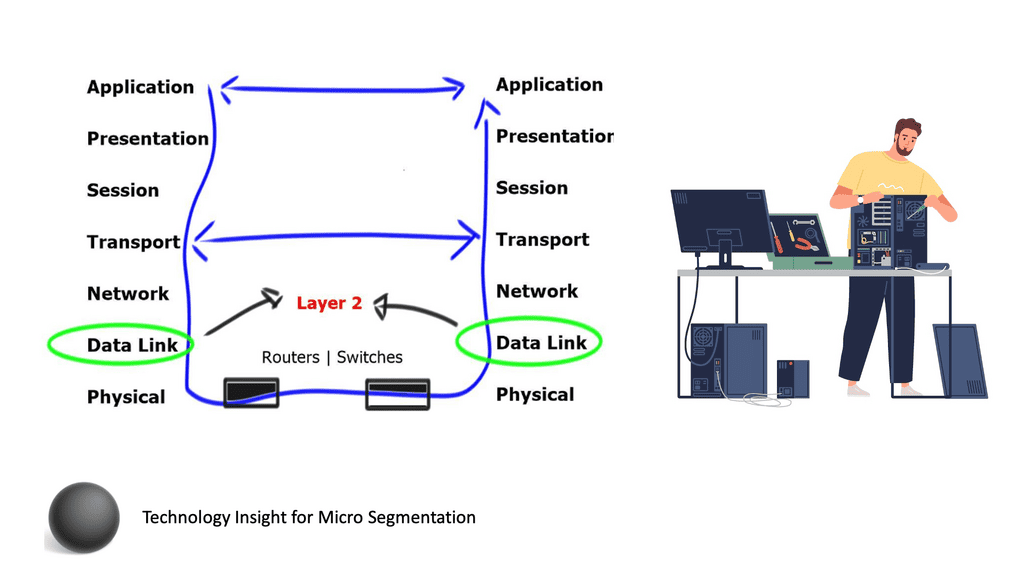
A Key Consideration: Layer-2 Security Issues
When discussing our journey on IPv6 data center network microsegmentation, we must consider that Layer-2 security mechanisms for IPv6 are still as complicated as those for IPv4. Nothing has changed. We are still building the foundation of our IPv6 and IPv4 networks on the same forwarding paradigm, relying on old technologies that emulate thick coaxial cable, known as Ethernet. Ethernet should be limited to where Ethernet was designed: the data link layer between adjacent devices. Unfortunately, the IP+Ethernet mentality is tightly coupled with every engineer’s mind.
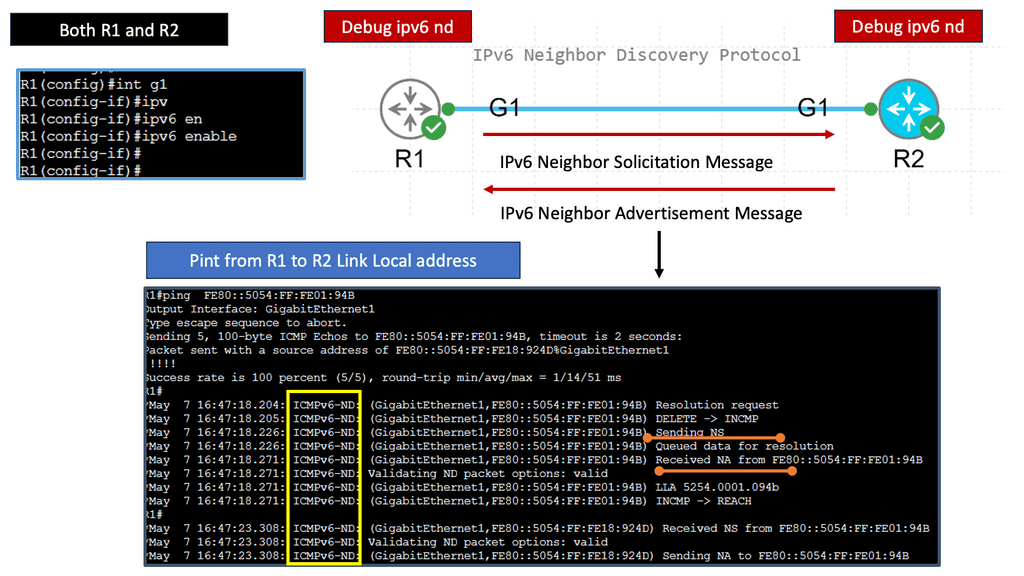
Recap on IPv6 Connectivity
Before you proceed, you may find the following helpful post for pre-information.
Technology Insight For Microsegmentation
Securing Networks with Segmentation
Securing network access and data center devices has always been a challenging task. The new network security module is Zero Trust (ZT); it is a guiding concept that indicates the network is always assumed to be hostile and external and internal threats always exist. As a result, the perimeter has been moved closer to the workload.
Zero Trust mandates a “never trust, always verify, enforce least privilege” approach, granting least privilege access based on a dynamic evaluation of the trustworthiness of users and their devices and any transaction risk before they can connect to network resources. A core technology for zero Trust is the use of microsegmentation.
Enhanced Security
One of the key benefits of microsegmentation is its ability to enhance network security. Organizations can isolate critical data and applications by segmenting the network into smaller parts, limiting their exposure to potential threats. In a security breach, microsegmentation prevents lateral movement, containing the attack and minimizing the possible impact. This fine-grained control significantly reduces the attack surface, making it harder for cybercriminals to infiltrate and compromise sensitive information.
Improved Compliance
Compliance with industry standards and regulations is a top priority for organizations operating in heavily regulated industries. Microsegmentation plays a crucial role in achieving and maintaining compliance. By isolating sensitive data, organizations can ensure that only authorized individuals have access to it, meeting the requirements of various regulations such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). Microsegmentation provides the necessary controls to enforce compliance policies and protect customer data.
Efficient Resource Utilization
Another advantage of microsegmentation is its ability to optimize resource utilization. Organizations can allocate resources more efficiently based on specific requirements by segmenting the network. For example, critical applications can be assigned dedicated resources, ensuring their availability and performance. Additionally, microsegmentation allows organizations to prioritize network traffic, ensuring mission-critical applications receive the necessary bandwidth while less critical traffic is appropriately managed. This efficient resource allocation leads to improved performance and reduced latency.
Simplified Security Management
Contrary to what one might expect, microsegmentation can simplify security management for organizations. With a traditional security approach, managing complex network policies and access controls can be challenging, especially as networks grow in size and complexity. Microsegmentation simplifies this process by breaking the network into smaller, more manageable segments. Security policies can be easily defined and enforced at the segment level, reducing the complexity of managing security across the entire network.
Example Technology: Network Endpoint Groups
**Implementing NEGs for Enhanced Segmentation**
To harness the full potential of NEGs, it’s essential to implement them strategically within your Google Cloud environment. Start by identifying the endpoints that require segmentation and determine the criteria for grouping them. This could be based on geographical location, application function, or security requirements. Once grouped, configure your load balancing settings to utilize NEGs, ensuring that traffic is directed efficiently and securely.
Additionally, regularly review and update your NEG configurations to adapt to changing network demands and security threats. This proactive approach ensures that your infrastructure remains optimized and resilient against potential disruptions.
Data Center Micro-Segmentation
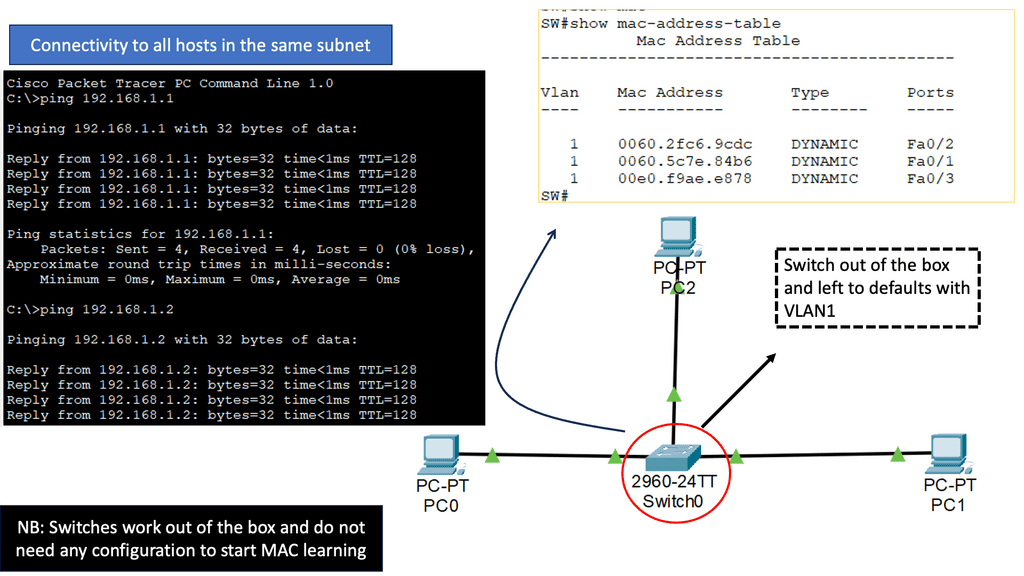
What is Layer 2? And why do we need it? Layer 2 is the layer that allows adjacent network devices to exchange frames. Every layer 2 technology has at least three components:
- Start-of-frame indication.
- End-of-frame indication.
- Error correction mechanism in case the physical layer cannot guarantee the error-free transmission of zeroes and ones.
**A Key Point: Layer 2 MAC address**
You may have realized I haven’t mentioned the layer 2 MAC address as a required component. MAC addresses are required when more than two devices are attached to the same physical network. MAC addresses are in Ethernet frames because the original Ethernet standard used a coax cable with multiple nodes connected to the same physical medium.
Therefore, layer 2 addressing on point-to-point Fiber Channel networks is not required, while you need layer 2 addressing on shared cable-based Ethernet networks. One of the main reasons for the continuation of MAC addresses in Ethernet frames is backward compatibility. More importantly, no one wants to change device drivers in every host deployed in a data center or Internet.
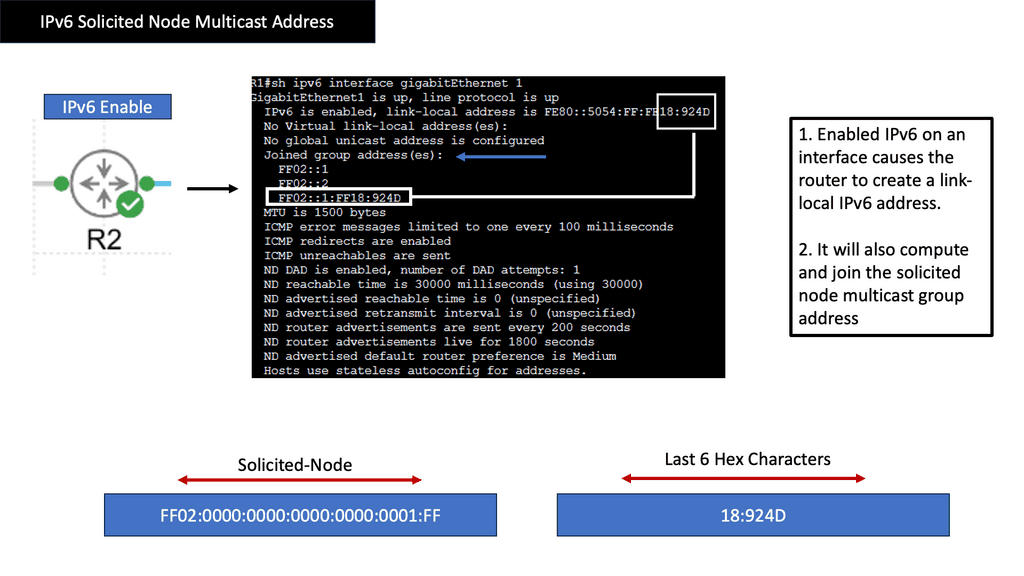
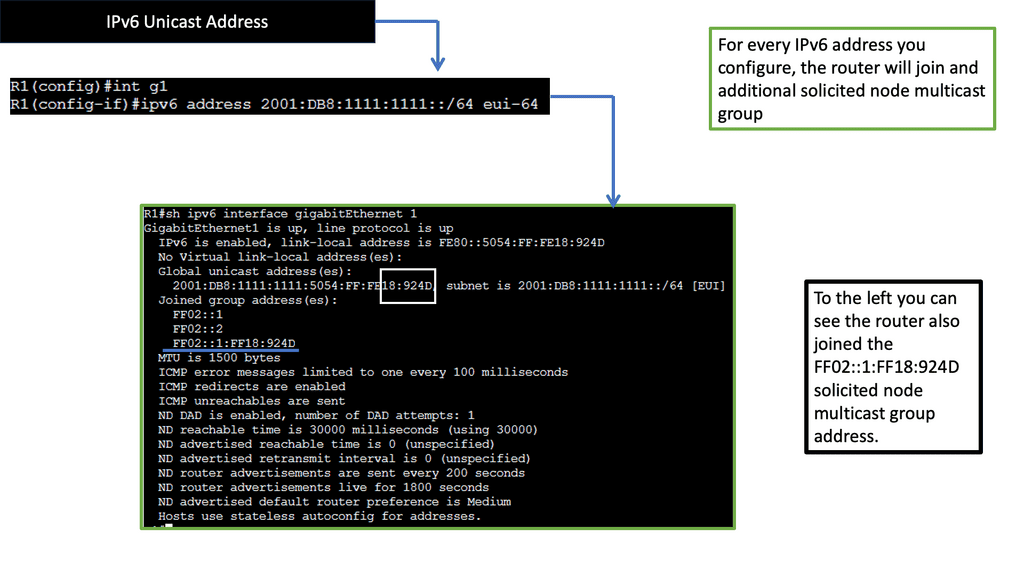
Technology Insight for Microsegmentation and IPv6
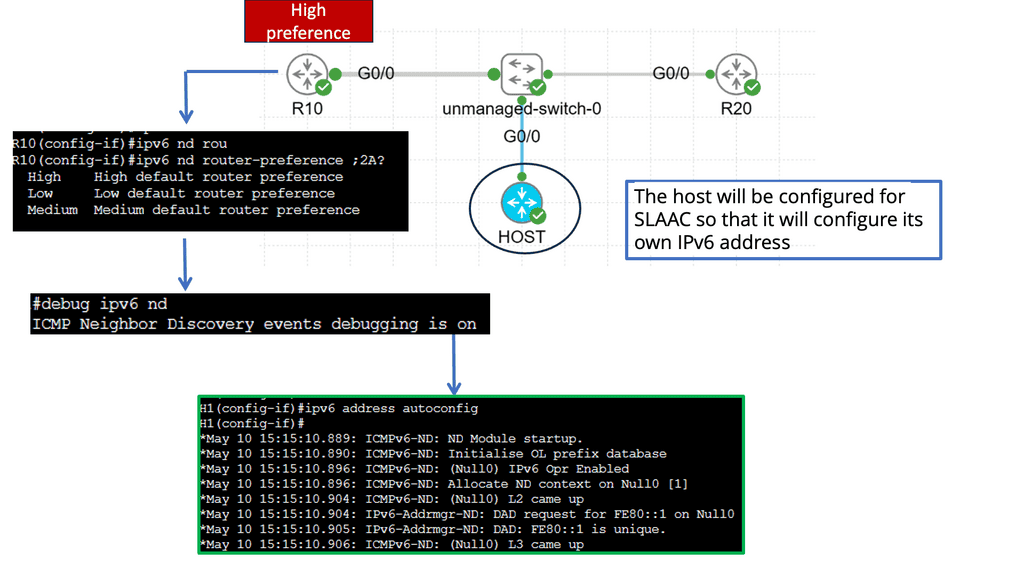
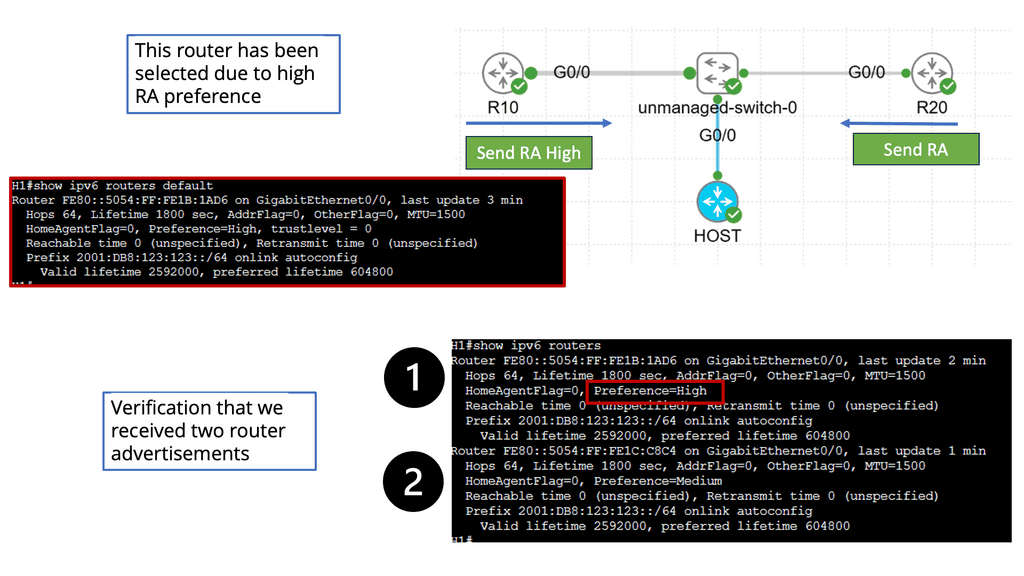
“IPv6 microsegmentation is an approach used to solve security challenges in IPv6.”
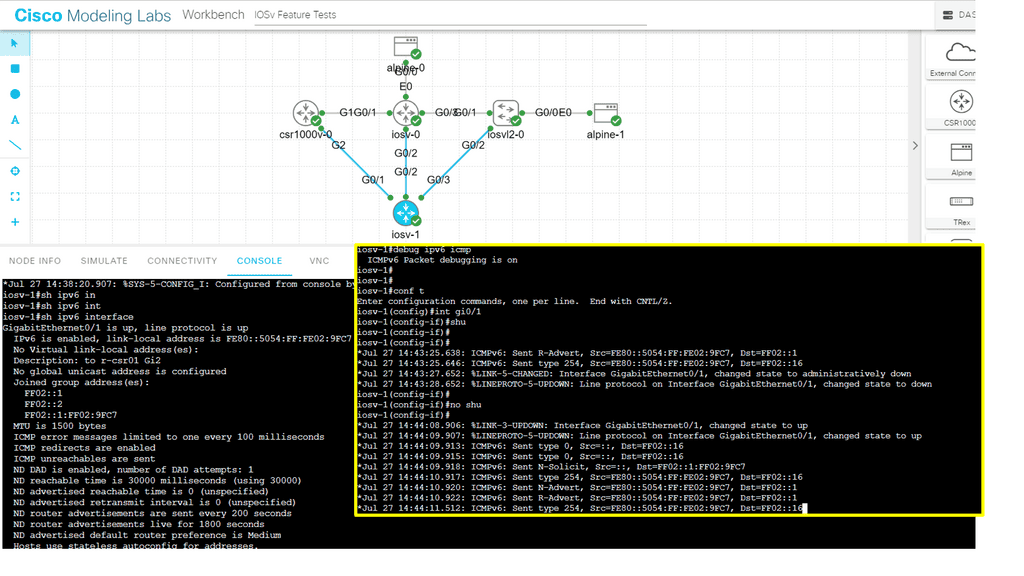
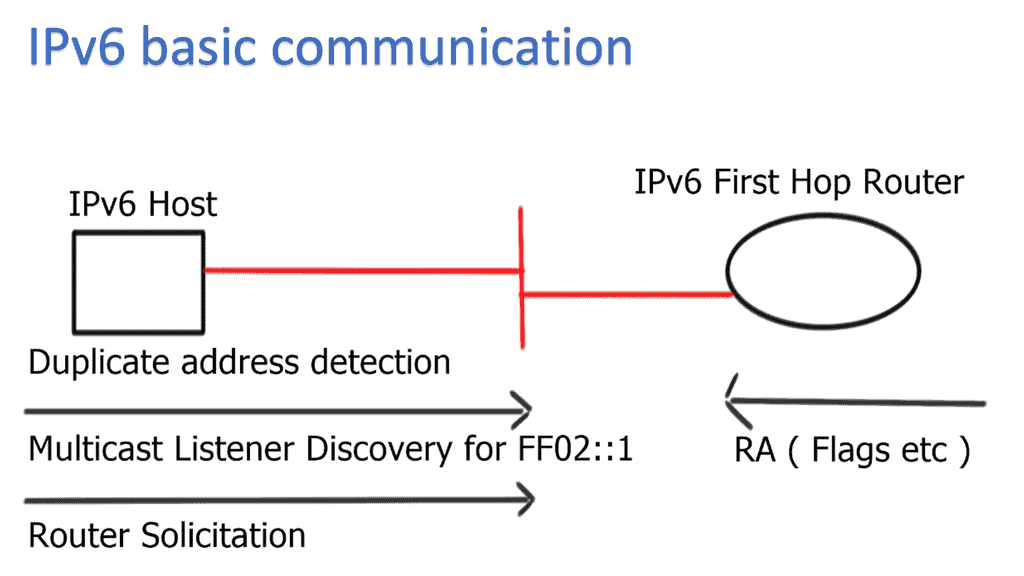
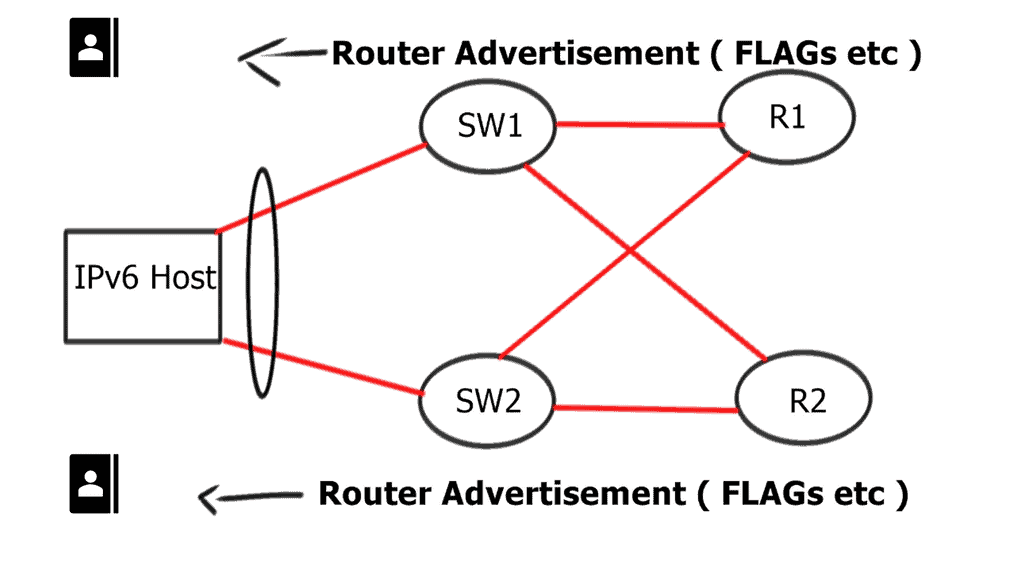
Firstly, when discussing data center network microsegmentation, with IPv6 micro-segmentation, we have many layer-2 security challenges. Similar to the IPv4 world, the assumption is one subnet is one security zone. This can be represented as a traditional VLAN with a corresponding VLAN ID or a more recent technology of VXLAN with a corresponding VXLAN ID.
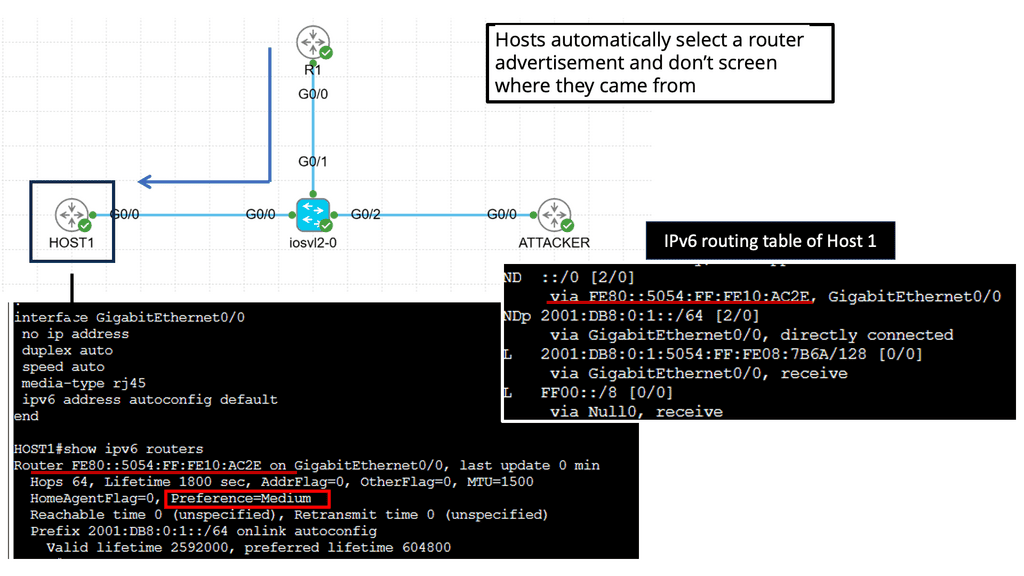
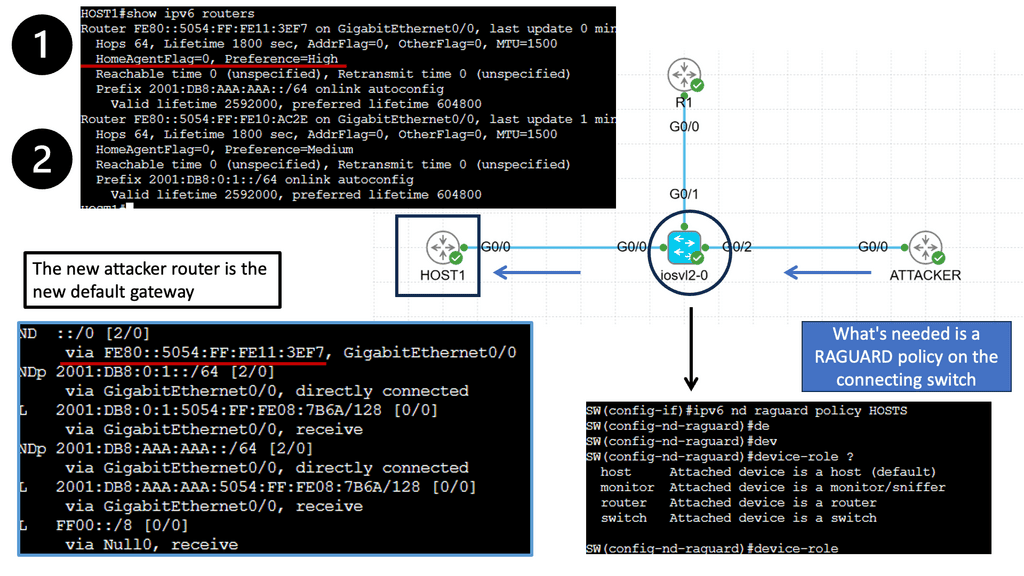
Devices in that domain are in one security domain, and all enjoy the same level of trust, representing several IPv6 security challenges. If intruders break into that segment, they can exploit that implicit trust between all devices. The main disadvantage is that intra-subnet communication is not secured, and multiple IPv6 first-hop vulnerabilities ( RA and NA spoofing, DHCPv6 spoofing, DAD DoS attacks, and ND DoS attacks).
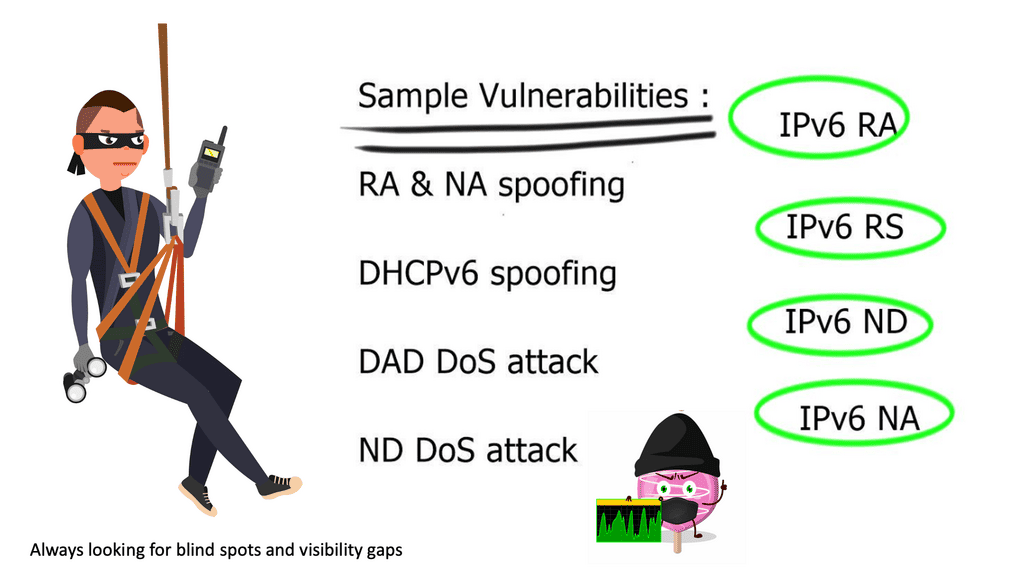
A review of IPv6 security
– The attacker can spoof the neighbor advertisement messages and affect the ND cache on the host. Thus, it takes over and intercepts traffic sent to other hosts. It can also intercept DHCP requests and pretend to be a DHCP server, redirecting traffic to itself or DoS attacks with incorrect DNS records. The root cause is that everything we operate on today simulates the thick coaxial cable we use for Ethernet. In the early days, Ethernet segments had one coaxial cable segment, and all stations could attach to this segment, resulting in one large security domain. Networks evolved, and new technologies were introduced.
– The coaxial cable was later replaced with thin cable and hubs to switches. Unfortunately, we haven’t changed the basic forwarding paradigm we used 40 years ago. We still emulate thick coaxial cable while relying on the same traditional basic forwarding paradigm. The networking industry is trying to fix the problem without addressing and resolving the actual source of the problem.
– The networking industry is retaining the existing forwarding paradigm while implementing a layer-2 security mechanism to overcome its limitations. All these layer-2 security measures ( first-hop security ) lead to complex networks from design and operational aspects. They are adding more kludges; hence, every technology tries to fix the shortcomings when they should be addressing the actual source of the problem.
In the layer 2 world, everyone tries to retain the existing forwarding paradigm, even with the most recent data center overlay technologies. For example, they are still trying to emulate the thick coaxial cable over the VXLAN segment over IP. VXLAN uses historic flooding behavior. In the IPv6 world, to overcome shortcomings with layer 2, vendors started implementing a list of first-hop layer-2 security mechanisms. Implementing these to secure the layer 2 IPv6 domain would be best.
Note: Multicast Listener Discovery Protocol
All these features are complicated technologies to implement. They are used solely to fix the broken forwarding paradigm of layer 2—recent issues with MLD ( multicast listener discovery protocol ), which is part of IPv6. MLD can break into multicast streams on Local Area Networks ( LAN ) and gain control of first-hop router communication.
So, in the future, we will need to implement MLD guard as a new first-hop security mechanism. The list goes on and on—a constant cat-and-mouse game. So, we need to ask ourselves whether we can do better than that. And what can we implement or design to overcome these shortcomings? Just get rid of layer 2? :
Note: Can we Remove Layer 2?
We can remove layer 2 from “some” networks. If the first-hop router is a layer 3 device, we don’t need to implement all the security kludges mentioned above. However, as end hosts have Ethernet cards, we would still need Ethernet between the end host and router. Using a layer 3 device as the first hop immediately removes all IPv6 spoofing attacks.
For example, RA Gaurd is unnecessary as the router will not listen to RA messages. ND spoofing is impossible as you can’t bridge ND across segments. However, DoS attacks are still possible. This layer 3-only design is implemented on xDSL and Mobile networks—designed by putting every host in a /64 subnet. But; now, we are returning to 64-bit segments to implement security between segments.
- Is this possible to use in the data center when moving VMs across mobility domains?
Technology Insight For Microsegmentation
IPv6 micro-segmentation for the data center
In data centers, we have issues with live VM migration. We must move VMs between servers while retaining IPv6 addresses to keep all Transmission Control Protocol ( TCP ) sessions intact. Layer 3 solutions exist but are much slower ( as layer 3 routing protocol convergence is slower than layer 2 convergence ) than we can get with simple flooding of MAC address with reverse Address Resolution Protocol ( ARP ) and gratuitous ARP.
Note: VXLAN Segments
We usually have some VLAN that spans the domain with an actual VLAN or VXLAN segment. VLANs must span the entire mobility domain, expanding the broadcast domain throughout the network. Expanding the broadcast domain also broadens the scope of layer 2 security attacks. Private VLANs exist, but on a large scale, private VLANs are messy and complex.
You can use one VLAN per VM, which would cause an explosion of VLAN numbers. You still need to terminate layer 3 on Core switches, meaning all traffic between two VM must traverse to Core. Inter-VLAN communication is sent to Core ( layer 3 devices) even when the VM sits on the same hypervisor. Not a good design.
Also, if you want mobility across multiple core switches, you can’t aggregate traffic and must pass the IPv6 prefixes to support VM mobility. Now, we have loads of /64 prefixes in the IPv6 forwarding table when using one prefix per VM. Vendors like Brocade only support 3k IPv6 prefixes, and Juniper supports up to 1k. In the future, this scale limitation will represent design problems. So, do we need some other type of design? We need to change the forwarding paradigm. In an ideal world, use layer-3 only networks, layer-3 devices as first-hop devices, and still support VM mobility. At the same time, it does not generate many IPv6 prefixes.
Intra-subnet ( host route ) layer 3 forwarding
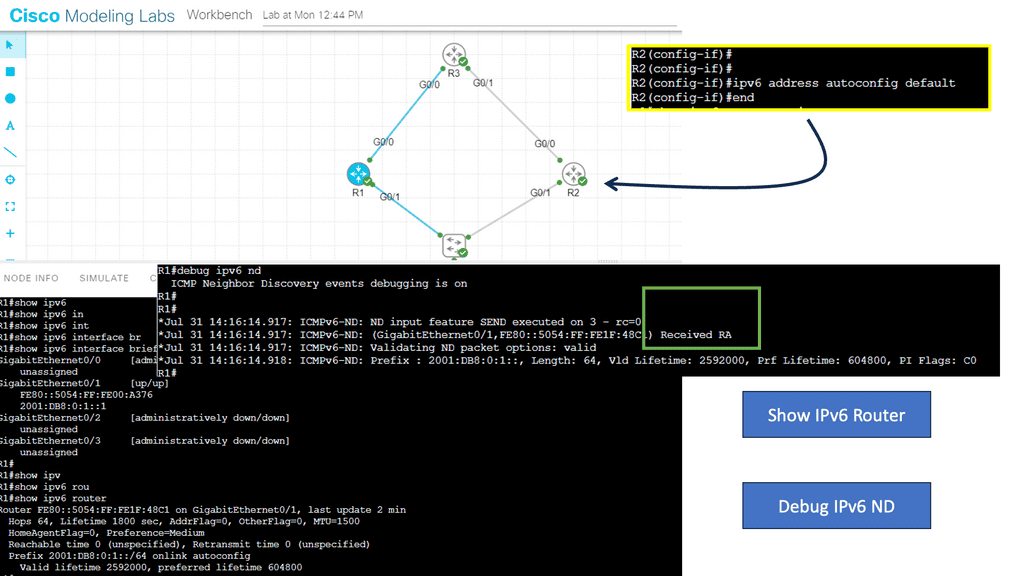
Is it possible to design and build layer-3-only IPv6 networks without assigning a /64 prefix to every host?
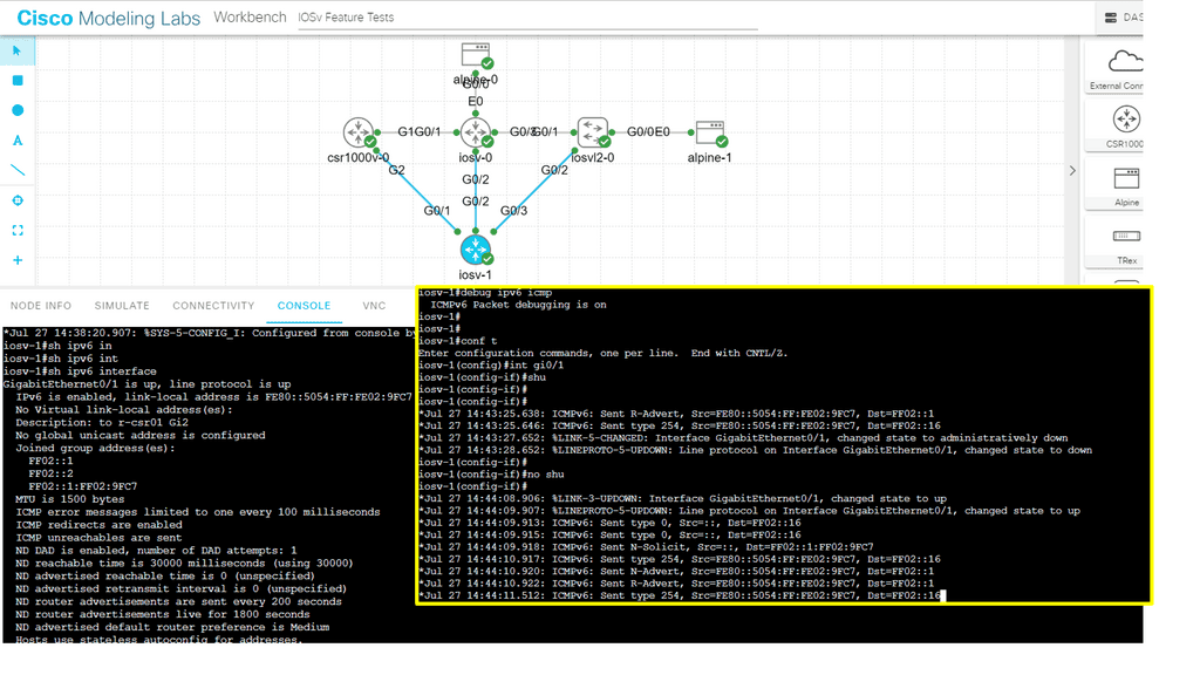
Intra-subnet layer 3 forwarding implements /128 for hosts, which is propagated with updates across the network. At a host level, nothing changes. It can use DHCP or other mechanisms to get its address. Now that we are using /128, we don’t need to use the IPv6 forwarding table for this prefix. Instead, we can put the /128 into IPv6 Neighbor Discovery ( ND ) entries.
This is how the ND cache is implemented on hardware-based platforms. There is no difference between ND entities and 128-host routes in the IPv6 routing table. The critical point is that you can use ND entries instead of the IPv6 forwarding table, which, by default, has small table sizes on most platforms.
For example, the Juniper EX series can have 32k ND entities but only 1K IPv6 entries. This design trick can significantly increase the number of hosts under an IPv6 microsegmentation design.
Cisco dynamic fabric automation ( DFA )
Virtual Machine microsegmentation with Cisco DFA allows you to implement a VLAN per VM addressing scheme without worrying about VLAN sprawl and all those problems experienced with provisioning. More importantly, all layer 3 traffic is not terminated on the core switch but on the leaf switch.
Closing Points: IPv6 Microsegmentation
While the benefits of IPv6 microsegmentation are clear, implementing it is not without challenges. Organizations must consider the complexity of transitioning from IPv4 to IPv6, which may require substantial changes to existing infrastructure. Additionally, developing effective segmentation policies requires a deep understanding of the network’s topology and traffic patterns. However, with careful planning and execution, these challenges can be overcome, paving the way for a more secure and efficient network environment.
In conclusion, IPv6 microsegmentation represents a significant leap forward in network security and management. By combining the advanced features of IPv6 with the precision of microsegmentation, organizations can build a resilient, scalable, and secure network infrastructure that meets the demands of the modern digital landscape. As we move towards a more connected world, embracing these technologies will be crucial in staying ahead of the curve and protecting our digital assets.
Summary: Technology Insight For Microsegmentation
In today’s interconnected world, network security has become a critical concern for organizations of all sizes. The traditional perimeter-based security measures are no longer sufficient to combat the ever-evolving threat landscape. This is where microsegmentation comes into play, offering a revolutionary approach to network security. In this blog post, we will delve deep into the concept of microsegmentation, its benefits, implementation strategies, and real-world use cases.
What is Microsegmentation?
Microsegmentation is a network security technique that divides the network into smaller, isolated segments to enhance security and control. Unlike traditional network security approaches, which rely on perimeter defenses, microsegmentation operates at the granular level. It enables organizations to define security policies based on specific criteria such as user roles, applications, and workloads, allowing for fine-grained control over network traffic.
The Benefits of Microsegmentation
Microsegmentation offers many benefits to organizations seeking to strengthen their network security posture. First, it limits the lateral movement of threats within the network, making it significantly harder for cyber attackers to traverse laterally and gain unauthorized access to critical assets. Moreover, microsegmentation enhances visibility, allowing security teams to monitor and detect anomalies more effectively. It also simplifies compliance efforts by clearly separating sensitive data and other network components.
Implementing Microsegmentation: Best Practices
Implementing microsegmentation requires careful planning and strategic execution. Firstly, organizations must conduct a comprehensive network assessment to identify critical assets, traffic patterns, and potential vulnerabilities. Based on this assessment, a well-defined segmentation strategy can be developed. To ensure a seamless implementation process, it is crucial to involve all stakeholders, including network administrators, security teams, and application owners. Additionally, leveraging automation tools and solutions can streamline the deployment and management of microsegmentation policies.
Real-World Use Cases
Microsegmentation has gained immense popularity across various industries due to its effectiveness in enhancing network security. In the healthcare sector, for instance, microsegmentation helps safeguard patient data by isolating medical devices and limiting access to sensitive information. Similarly, financial institutions utilize microsegmentation to protect critical assets, such as transactional systems and customer databases. The use cases for microsegmentation are vast, and organizations across industries can benefit from its robust security capabilities.
Conclusion:
Microsegmentation has emerged as a game-changer in network security. By adopting this innovative approach, organizations can fortify their defenses, mitigate risks, and protect their valuable assets from cyber threats. With its granular control and enhanced visibility, microsegmentation empowers organizations to stay one step ahead in the ever-evolving cybersecurity landscape. Embrace the power of microsegmentation and unlock a new level of network security.