IPv6 Fragmentation
In the vast landscape of networking and internet protocols, IPv6 stands as a crucial advancement. With its expanded address space and improved functionality, IPv6 brings numerous benefits. However, one aspect that requires attention is IPv6 fragmentation. In this blog post, we will dive deep into the intricacies of IPv6 fragmentation, explore its significance, and discuss how to navigate this aspect effectively.
Before we delve into fragmentation in IPv6, along with the details of the IPv6 fragment and an IPv6 fragmentation example, let us start with the basics. IPv6 fragmentation divides an IPv6 packet into smaller packets to facilitate transmission across networks with a smaller Maximum Transmission Unit (MTU). Unlike IPv4, fragmentation is not mandatory in IPv6, as all networks support an MTU of at least 1280 bytes.
However, fragmentation may still be necessary. When a packet is fragmented, the original packet is divided into smaller pieces, known as fragments. Each fragment contains a portion of the original packet and additional information that allows the receiving device to reassemble the packet correctly.
IPv6 fragmentation refers to the process of breaking down IPv6 packets into smaller units, known as fragments, to accommodate varying network MTU (Maximum Transmission Unit) sizes. Unlike IPv4, IPv6 relies on the source device instead of intermediary routers for fragmentation. This shift has implications on network performance, security, and overall efficiency.Matt Conran
Highlights: IPv6 Fragmentation
**Understanding IPv6 and Its Importance**
In the rapidly evolving landscape of the internet, IPv6 stands as a beacon of progress and innovation. With IPv4 addresses running scarce, the introduction of IPv6 brings a virtually limitless pool of IP addresses, ensuring the continued growth and expansion of the internet. But beyond the numbers, IPv6 also introduces new features and enhancements that improve the efficiency and security of data transmission. One significant aspect, which we’ll explore in this blog post, is IPv6 fragmentation.
**What is IPv6 Fragmentation?**
Fragmentation in network communication refers to the process of breaking down a large data packet into smaller pieces to ensure it can be transmitted across networks that cannot handle the original size. Unlike its predecessor, IPv4, where routers along the path could fragment packets, IPv6 requires the sending device to perform this task. This shift in responsibility is designed to optimize network performance and reduce the burdens on intermediate routers.
**How IPv6 Fragmentation Works**
In IPv6, fragmentation is handled exclusively by the source node. When a large packet is sent, it is up to the source to determine the path’s maximum transmission unit (MTU) and fragment the packet accordingly. This process ensures that packets are transmitted without causing congestion or packet loss due to size limitations. Once fragmented, these packets are reassembled by the destination node, not by routers along the way, which streamlines the transmission process.
**The Impact of Fragmentation on Network Security**
While IPv6 fragmentation offers efficiency, it also brings new challenges in terms of security. Fragmented packets can be exploited by attackers to bypass security measures, leading to potential vulnerabilities such as Denial of Service (DoS) attacks. Network administrators must implement robust security protocols to inspect and verify fragmented packets accurately, ensuring that malicious activities are detected and mitigated.
**Best Practices for Handling IPv6 Fragmentation**
To effectively manage IPv6 fragmentation, organizations should adopt a set of best practices. These include configuring devices to avoid unnecessary fragmentation, setting appropriate MTU sizes, and employing advanced security measures to monitor and analyze fragmented traffic. Regular updates to network security systems are also vital to keep up with evolving threats related to fragmentation.
IPv6 Fragmentation
A: ) Fragmentation in IPv6 can occur at either the source or destination device. The source device may fragment packets if it determines that the packet size is larger than the MTU of a network along the path to the destination. Alternatively, the destination device may request that the source device fragment a packet if the packet size exceeds the MTU of the local network.
B: ) In IPv4 and IPv6, end hosts have never been able to determine the maximum payload size when communicating with remote hosts through the IP protocol stack. IP packets are routed independently from each other and can take different routes with different MTU sizes, so a network-wide MTU mechanism is not necessary. Nevertheless, the absence of end-to-end information can lead to oversized packets being received by intermediate routers, which cannot forward them.
C: ) A convenient solution to this problem is provided by the IPv4 and IPv6 protocols: IP fragmentation, which splits a single inbound IP datagram into two or more outbound IP datagrams. It is done by copying the IP header from the original IP datagram into the fragments, setting special bits to indicate that the fragments are not complete IP packets (IPv6 uses extension headers), and spreading the payload across the fragments. As opposed to IPv4, IPv6 does not support fragmentation during transit – if fragmentation is needed, the sending host must do it.
Factors Influencing Fragmentation
Several factors can influence IPv6 fragmentation. First and foremost is the network’s MTU size. Each network has its own MTU; fragmentation becomes necessary when a packet exceeds this size. Additionally, path MTU discovery plays a crucial role in determining whether fragmentation is required along the network path. Understanding these factors is essential for effectively handling fragmentation-related challenges.
**Impact on Network Performance**
Fragmentation can have a notable impact on network performance. When packets are fragmented, additional processing overhead is introduced on both the source device and the recipient. This can lead to increased latency, reduced throughput, and potential performance bottlenecks. Minimizing fragmentation and optimizing MTU settings is crucial to ensure optimal network performance.
**Addressing Security Concerns**
IPv6 fragmentation also introduces security considerations. Fragmentation-based attacks, such as fragmentation overlap, can exploit vulnerabilities and impact network security. Proper security measures, including fragmentation detection and prevention mechanisms, must be implemented to mitigate potential risks.
**Best Practices for IPv6 Fragmentation**
Navigating IPv6 fragmentation requires a proactive approach and adherence to best practices. Some key recommendations include optimizing network MTU sizes, enabling path MTU discovery mechanisms, implementing firewall rules to detect and prevent fragmented packets, and staying updated with the latest security practices.
Knowledge Check: Troubleshoot with Traceroute
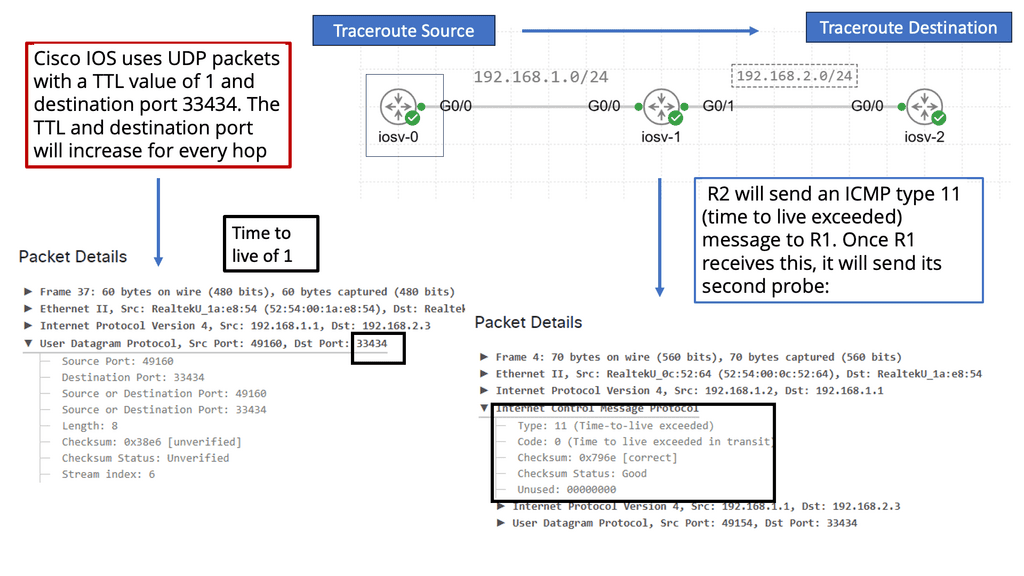
### How Traceroute Works
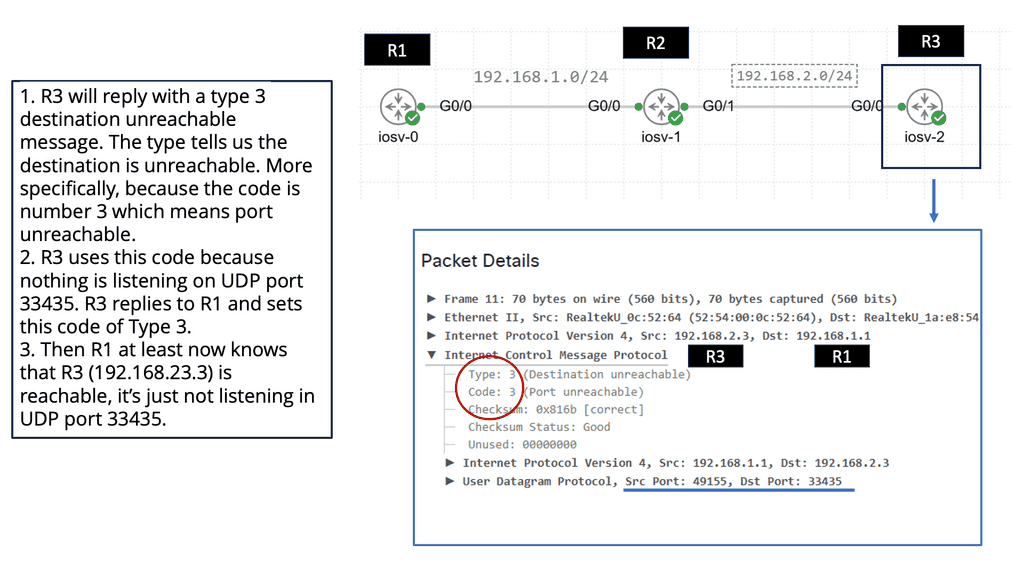
To understand how traceroute functions, you need to know a bit about how data packets work. When you send a request to access a website, your data is broken into small packets that traverse the internet. Traceroute sends a series of these packets to the destination while incrementally increasing the time-to-live (TTL) value. Each router along the path decrements the TTL by one before passing the packet along. When the TTL reaches zero, the router returns an error message to the sender. By analyzing these error messages, traceroute compiles a list of routers the packets passed through.
### Applications and Benefits of Traceroute
Traceroute is not only a fascinating tool for network enthusiasts but also an essential utility for network administrators. By revealing the path data takes, it helps in diagnosing network slowdowns, identifying bottlenecks, and uncovering routing inefficiencies. Traceroute can also assist in uncovering potential security vulnerabilities by highlighting unexpected routes or unknown servers that data might be passing through.
IPv6 Fragmentation: IPv6 Source Only
– Unlike IPv4, an IPv6 router does not fragment a packet unless it is the packet’s source. Intermediate nodes (routers) do not fragment. The fields used in IPv4 headers for fragmentation do not exist in IPv6 headers. You will see how an IPv6 device fragments packets when it is the source of the packet with the use of extension headers.
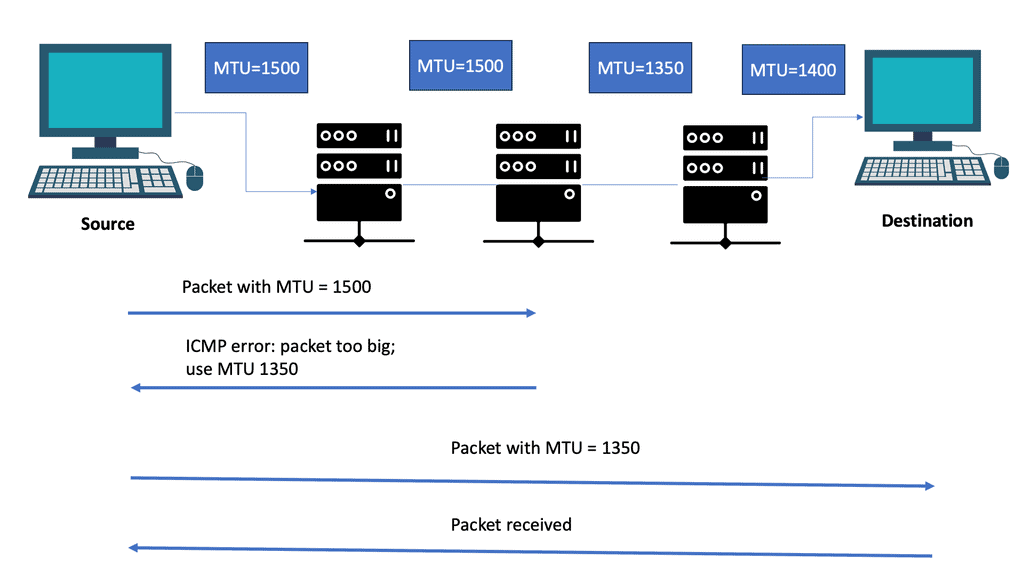
– An IPv6 router drops packets too large for the egress interface and sends an ICMPv6 Packet Too Big message back to the source. Packet Too Big messages include the link’s MTU size in bytes so the source can resize the packet.
– Data is usually transmitted as a series of packets, sometimes called a packet train. Larger packets may require fewer packets to be transmitted. Therefore, using the largest packet size supported by all the links from the source to the destination is preferable.
– Path MTUs (PMTUs) are used for this purpose. Devices can use Path MTU discovery to determine the minimum link MTU along a path. RFC 1981, Path MTU Discovery for IP Version 6, suggests that IPv6 devices should perform ICMPv6 PTMU discovery to avoid source fragmentation.
Drawbacks of Fragmentation
IP fragmentation always increases layer-3 overhead (and user bandwidth is reduced). For example, if an end-host thinks it can use 1500-byte IP packets, but there is a hop in the path with MTU size 1472, each oversized IP packet will be split into two packets, resulting in two additional 20-byte IPv4 headers or 40-byte IPv6 headers.
Furthermore, application-layer information isn’t copied into all non-first IP fragments since the TCP or UDP headers aren’t copied. It has been widely used to break firewalls using overlapping fragments, where the second fragment rewrites the TCP/UDP header from the first fragment. Consequently, some firewalls might drop IP fragments (resulting in blocked communication between end hosts).
Reassembling fragments and inspecting their contents consumes additional CPU resources. To detect intrusion signatures effectively, intrusion detection and prevention systems (IDS/IPS) must provide similar functionality. IPv6’s unlimited extension header chains exacerbated the problem.
Related: For pre-information, before you proceed, you may find the following IPv6 information of use:
IPv6 Fragmentation
IPv6 fragmentation Process:
IPv6 fragmentation is a process that divides large IPv6 packets into smaller fragments to facilitate their transmission over networks with a smaller maximum transmission unit (MTU) size. This is necessary because not all networks can handle the full packet size of IPv6, which is 1280 bytes.
IPv6 fragmentation occurs at the source node, dividing the original packet into smaller fragments. Each fragment contains a fragment header that includes information such as the offset of the fragment within the original packet, a flag indicating whether more fragments are expected, and the identification number of the original packet.
 When they reach their destination, the fragments are reassembled into the original packet by the destination node. The fragments are identified using the identification number in the fragment header, and the offset information is used to determine the correct order of the fragments. However, IPv6 fragmentation should be avoided whenever possible, as it can introduce additional overhead and processing delays.
When they reach their destination, the fragments are reassembled into the original packet by the destination node. The fragments are identified using the identification number in the fragment header, and the offset information is used to determine the correct order of the fragments. However, IPv6 fragmentation should be avoided whenever possible, as it can introduce additional overhead and processing delays.
Fragmentation can also affect network performance and reliability. To minimize fragmentation, IPv6 nodes should be configured with an appropriate MTU size that can accommodate the most extensive packets they are likely to encounter.
Fragment Attacks ( DDoS )
Fragmented packets can fool a firewall into allowing otherwise prohibited traffic. The firewall must be capable of enforcing its filtering policy on fragmented packets. For this to work, the firewall must find the complete header data set, including extension headers and protocol/port values at the upper layer. Additionally, the packet must not be susceptible to fragment overlap attacks. Since extension headers can push upper-layer protocol/port information outward (toward packet boundaries), fragment overlaps are a more severe problem in IPv6 than in IPv4.
Path MTU Discovery
In addition, IPv6 nodes can use the Path MTU Discovery (PMTUD) mechanism to dynamically determine the maximum MTU size along the path to a destination. PMTUD sends packets with the “Don’t Fragment” (DF) flag set and progressively reduces the packet size until a smaller MTU is found. Once the maximum MTU size is determined, the source node can adjust its packet size accordingly to avoid fragmentation.
While IPv6 fragmentation is a valuable mechanism for ensuring packet delivery over networks with smaller MTU sizes, it should be used sparingly. Minimizing the need for fragmentation through proper MTU configuration and utilizing PMTUD can help improve network performance and reliability.
Example: Fragmentation in IPv6.
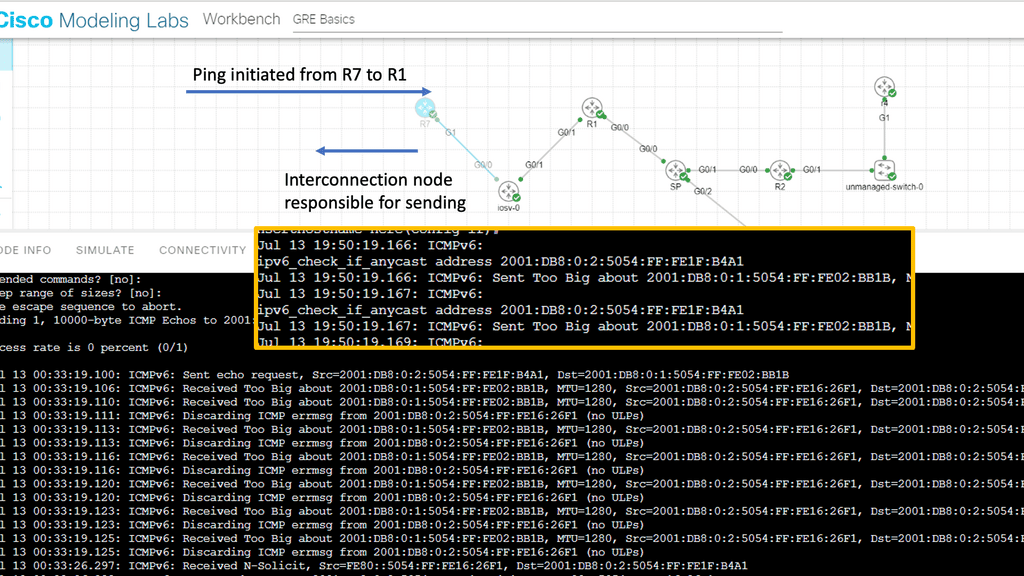
The following screenshot is taken from my Cisco modeling labs. We have a small network of three routers: R7, iosv-o, and R1. These routers are IPv6 enabled with the command IPv6 unicast-routing and the command IPv6 enabled under the corresponding interfaces, along with IPv6 addressing. The middle router, “iosv-o,” acts as an IPv6 interconnection point, and I lowered the IPv6 MTU here. An extended ping was initiated from R7 to R1 with a large datagram size.
IPv6 fragmentation: R1 receives an ICMPv6: Received Too Big, and the interconnection router is responsible for sending the ICMPV6: Sent Too Big. The intended destination does not get involved, preserving resources on R1.
As you can see from the screenshot below. An IPv6 router cannot fragment an IPv6 packet, so if the packet is too large for the next hop, the router is required to generate an ICMP6 Type 2 packet addressed to the source of the packet with a Packet Too Big (PTB) code and also providing the MTU size of the next hop.
While an IPv6 router cannot perform packet fragmentation, the IPv6 sender may fragment an IPv6 packet at the source. So, keep in mind that we lost the first ping. Subsequent packets will get through once the fragmentation has been performed at the source after receiving the packet’s big message.
Knowledge Check: ICMPv6
Before we get to the first lab guide, I’d like to do a knowledge check on ICMPv6. ICMPv6, an integral part of the IPv6 protocol suite, is a communication protocol between network devices. It primarily handles network error reporting, congestion feedback, and diagnostic functions. Unlike its predecessor, ICMP for IPv4, ICMPv6 offers several additional features, making it an essential component of modern network infrastructures.
Key Functionalities of ICMPv6
ICMPv6 encompasses a range of functionalities that contribute to the smooth functioning of IPv6 networks. From Neighbor Discovery Protocol (NDP) to Path MTU Discovery (PMTUD) and Router Advertisement (RA), each feature plays a crucial role in maintaining efficient communication and connectivity. Let’s explore these functionalities in detail.
The Role of ICMPv6 in Network Troubleshooting
ICMPv6 proves to be a valuable tool in network troubleshooting. ICMPv6 helps network administrators identify and resolve issues promptly by providing error reporting mechanisms. From unreachable hosts to time-exceeding messages, ICMPv6 messages offer valuable insights into network connectivity problems, aiding in efficient problem resolution.
Security Considerations and Best Practices
While ICMPv6 is a vital protocol, it is not immune to security vulnerabilities. Network administrators must implement proper security measures to protect their networks from threats. This section will highlight some recommended security practices and considerations when dealing with ICMPv6, ensuring a secure and reliable network environment.
Guide: ICMPv6 IPv6
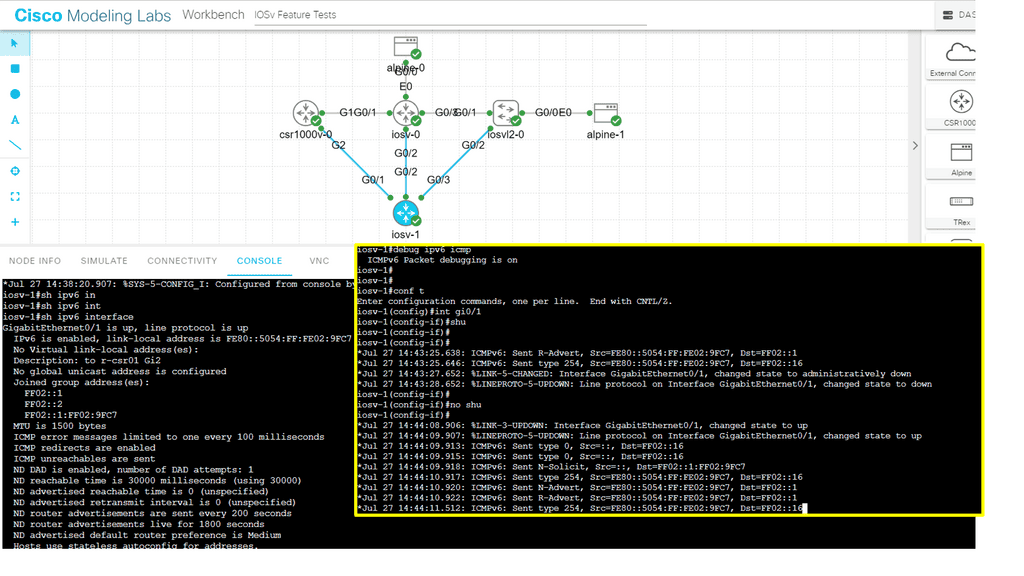
In the following, I have enabled IPv6 on only one router – IOSv-1. I have not configured any specific IPv6 IP configuration, so we have the link-local addresses that come by default when you enable IPv6 on an interface. Once I enabled IPv6 on the interface, I ran a debug ipv6 icmpv6. Notice we are sending icmpv6 router advertisements.
ICMPv6 Router Advertisement (RA) is a critical component of the Neighbor Discovery Protocol (NDP) in IPv6. Its primary function is to allow routers to inform neighboring devices about their presence and configuration parameters.
Routers periodically send RA messages to all nodes on a local network, providing critical information for automatic address configuration and maintaining network connectivity. However, we don’t receive any RA messages because IPv6 is not enabled in other network parts.
ICMPv6 Security
Layer 2 was designed with a plug-and-play approach; connect a switch, and it simply works. This ease often causes people to forget security and securing the switched infrastructure. Compromising a network at layer 2 can affect traffic at all layers above it. Once layer 2 is compromised, it is easier to launch man-in-the-middle attacks for secure upper-layer protocols such as Secure Sockets Layer ( SSL ) and Secure Shell ( SSH ).
When discussing IPv6, why concern ourselves with layer two security?IPv6 is IP and operates at Layer 3, right?
IPv6 has to discover other adjacent IPv6 nodes over layer 2. It uses Neighbor Discovery Protocol ( NDP ) to discover IPv6 neighbors, and NDP operates over ICMPv6, not directly over Ethernet, unlike Address Resolution Protocol ( ARP ) for IPv4.
ICMPv6 offers functions equivalent to IPv4 ARP and additional functions such as SEND ( Secure Neighbor Discovery ) and MLD ( Multicast Listener Discovery ). If you expand layer 2 and adjacent IPv6 hosts connect via layer 2 switches and not layer 3 routers, you will face IPv6 layer 2 first-hop security problems.
Of course, if you have a “properly” configured network, use layer 2, which should only be used for adjacent node discovery. The first hop could then be a layer 3 switch, which removes IPv6 layer 2 vulnerabilities. For example, the layer 3 switches cannot listen to RA messages and could also provide uRFP to verify the source of IPv6, mitigating IPv6 spoofing.
ICMP and ICMPv6
The Internet Control Messaging Protocol ( ICMP ) was initially introduced to aid network troubleshooting by providing tools to verify end-to-end reachability. ICMP also reports back errors on hosts. Unfortunately, due to its nature and lack of built-in security, it quickly became a target for many attacks. For example, an attacker can use ICMP REQUESTS for network reconnaissance.
ICMP’s lack of inherent security opened it up to some vulnerabilities. This results in many security teams blocking all ICMP message types, which harms useful ICMP features such as Path MTU. ICMP for v4 and v6 are entirely different. Unlike ICMP for IPv4, ICMPv6 is an integral part of v6 communication, and ICMPv6 has features required for IPv6 operation. For this reason, it is not possible to block ICMPv6 and all its message types. ICMPv6 is a legitimate part of V6; you must select what you can filter. ICMPv6 should not be completely filtered.
ICMPv6 and Hop Count
Most ICMPv6 messages have their hop count set to 255, with the exemption on PMTU and ICMPv6 error messages. This means that any device that receives an ICMPv6 message with a max hop count of less than 255 should drop the packet as crafted by an illegal source. By default, ICMPv6 with hop count of 255 messages are dropped at layer 3 boundaries. This is used as a loop prevention mechanism.
The default behavior can cause security concerns. For example, if a FW received an ICMPv6 packet with a hop count of 1. By default, it decrements the hop count and sends back an ICMPv6 time exceeded. If a firewall follows this default behavior, an attacker could be overwhelmed by many packets with TTL 1. Potential DoS attack the firewall device.
Prevent ICMPv6 Address Spoofing
The best practice is to check the source and destination address in an ICMPv6 packet. For example, in MLD ( Multicast Listener Discovery ), the source should always be a link-local address. If a check proves that this is not the case, it is likely that the packet originated from an illegal source and should be dropped.
You may also block any ICMPV6 address not assigned by the IANA. However, this is a manual process, and ACL adjustments are made whenever IANA changes the list.
Try hardening your device by limiting the number of ICMPv6 error messages. This will prevent a DoS attack by an attacker sending a barrage of malformed packets requiring many ICMPv6 error messages. – ipv6 icmp error interval.
Back To: The fragmentation process
The IP protocol stack needs a reliable mechanism where the end hosts can figure out the maximum payload size to use when communicating across a network to a remote IPv6 host. So, we end up with the absence of a network-wide mechanism. Destination-based routing results in IP packets being routed independently of each other. Each router in the paths decides where to route the packet.
As a result, we have different packets between the same end hosts that could take different routes with varying MTU sizes. The primary issue is that the need for end-to-end information can quickly result in oversized packets being received by intermediate routers that cannot be sent onward. To overcome this, we have a process known as IP fragmentation that comes into play, and we have this for IPv4 and IPv6 networks.
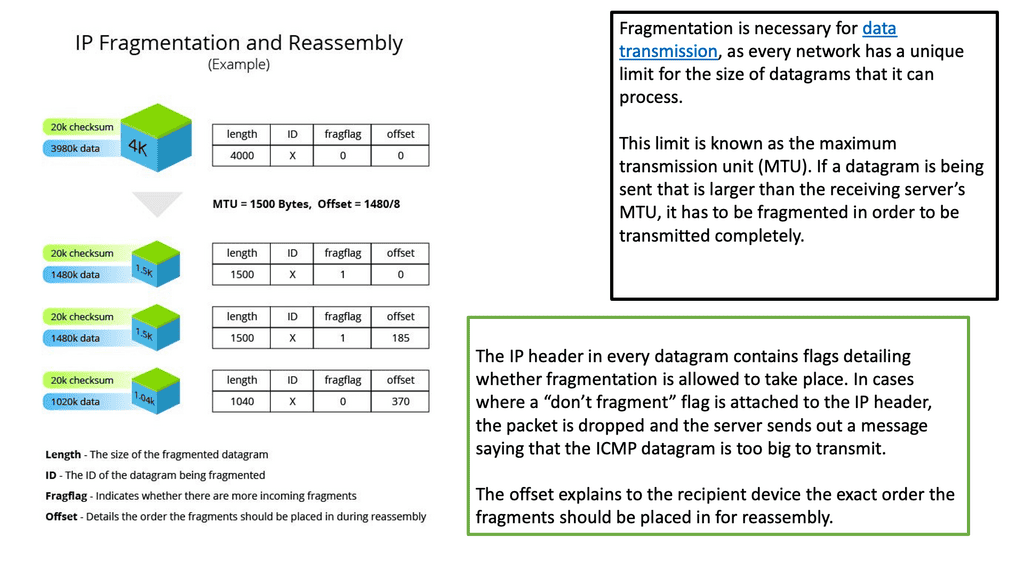
**Fragmentation is normal**
Fragmentation is a normal process on packet-switched networks. It occurs when a large packet is received, and the corresponding outbound interface’s maximum transmission unit (MTU) size is too small. Fragmentation dissects the IP packet into smaller packets before transmission. The receiving host performs fragment reassembly and passes the complete IP packet up the protocol stack.
Fragmentation is an IP process; TCP and other layers above IP are not involved. Reassembly is intended in the receiving host, but in practice, it may be done by an intermediate router. For example, network address translation (NAT) may need to reassemble fragments to translate data streams. This is where some differences between fragmentation in IPv4 and IPv6 are apparent.
In summary, IP fragmentation occurs at the Internet Protocol (IP) layer. Packets are fragmented to pass through a link with a smaller maximum transmission unit (MTU) than the original packet size. The receiving host then reassembles the fragments.
Impact on networks
In networks with multiple parallel paths, technologies such as LAG and CEF split traffic according to a hash algorithm. All packets from the same flow are sent out on the same path to minimize packet reordering. IP fragmentation can cause excessive retransmissions when fragments encounter packet loss. This is because reliable protocols such as TCP must retransmit all fragments to recover from the loss of a single fragment.
Senders typically use two approaches to determine the IP packet size to send over the network. In the first case, the sending host sends an IP packet equal to the MTU of the first hop of the source-destination pair. Secondly, the Path MTU Discovery algorithm can determine the path MTU between two IP hosts to prevent IP fragmentation.
**Fragmentation in IPv4 and IPv6**
A: ) Fragmentation in IPv6 is splitting a single inbound IP datagram into two or more outbound IP datagrams. The IP header is copied from the original IP datagram into the fragments. With IPv6, special bits are set in the fragments’ IPv6 headers to indicate that they are not complete IP packets. In the case of IPv6, we use IPv6 extension headers. Then, the payload is spread across the fragments.
B: ) In IPv4, fragmentation is done whenever required, at the destination or routers, whereas, in IPv6, only the source, not the routers, is supposed to do fragmentation. This can only be done when the source knows the Maximum Transmission Unit (MTU) path.
C: ) The IPv6 “do not fragment” bit is always 1, whereas the case is not the same in IPv4, and the ‘More fragment’ bit is the only flag in the fragmentation header, which is one bit. Two bits are reserved for future use, as shown in the picture below. The following diagram displays the Internet Protocol Version 6 Fragmentation Header.
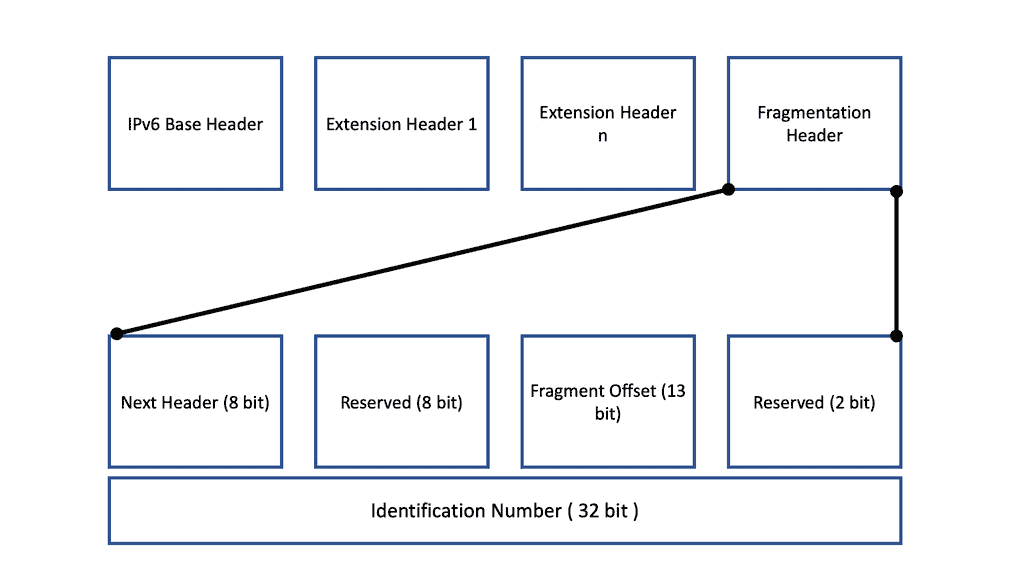
IPv6 Fragmentation Header
|
In an IPv4 world, several flags and fields control fragmentation, including the Fragment Offset, Don’t Fragment (DF) bit, and More Fragments (MF) flags. All fragmentation information is contained in the IPv4 header. The fragment offset tells the receiving device exactly where the fragment should be placed in the overall message. The DF bit tells hosts not to fragment.
If set, packets are dropped, and fragmentation along the path is required. This mechanism is used for Path MTU Discovery to determine the maximum MTU size on the network. It is set automatically with host software or manually with command-line tools. Finally, when an IP packet undergoes fragmentation, the MF bit is set for all datagrams except the last one. For unfragmented packets, the MF flag is cleared.
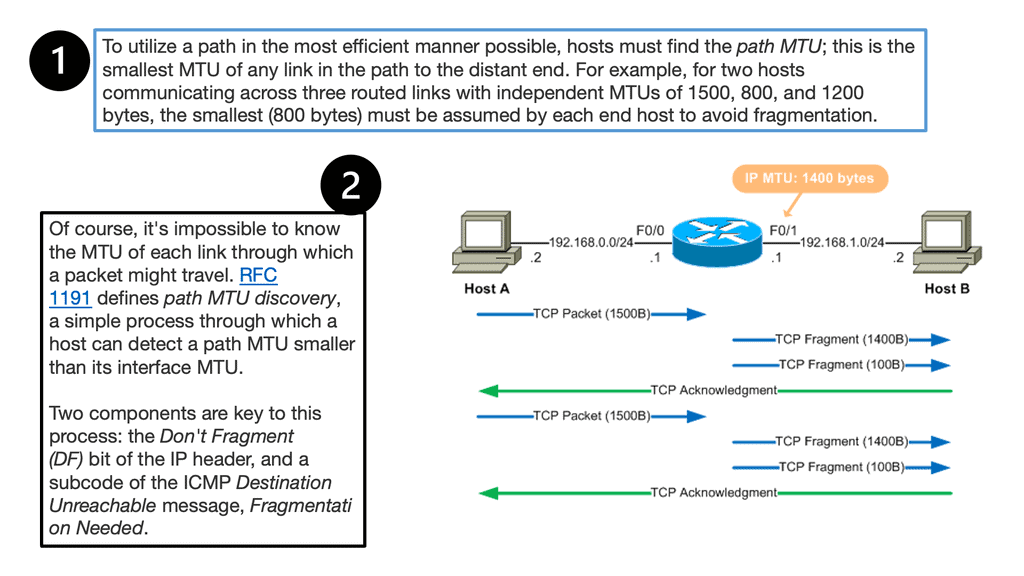
In IPv4 networks, when a router receives a network packet more significant than the next hop’s MTU, it has two options: either drop the packet if the Don’t Fragment (DF) flag bit is set and send an Internet Control Message Protocol (ICMP) message indicating Fragmentation Needed (ICMP Type 3 and ICMP Code 4), or fragment the packet and send it on the link with a smaller MTU. Despite originators producing fragmented packets, IPv6 routers cannot fragment further. Therefore, IPv6 hosts must determine the optimal MTU using Path MTU Discovery before sending packets, rather than network equipment delivering IPv6 packets or fragments smaller than or equal to 1280 bytes.
Guide: IPv6 fragmentation
In the following lab setup, we have a three-router node design. The 2911 routers are running IPv6, and I have enabled IPv6 RIP for reachability. The 2960 switch has its out-of-the-box configuration, so everything is in the default VLAN, and MAC address learning is working. One difference is that the MTU has been set to 1280 Bytes, as shown below. Running an extended ping with a higher MTU, we get an ICMPv6 packet that is too big a message. As a test, you can put an IPv6 access list inbound on Router0, tracking the ICMPv6 packet with too many big messages.
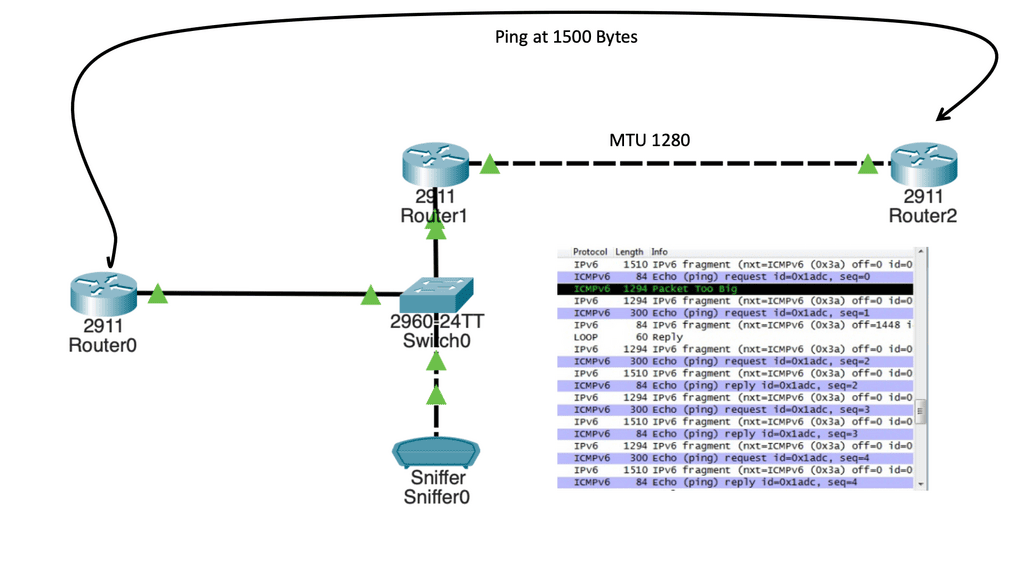
- Question: What is Path MTU Discovery (or PMTUD)
A PMTUD is a mechanism used on the Internet to determine how large packets can be transmitted to a specific destination. Here’s how it works: Your host will send a potentially large packet marked “Do Not Fragment.” Then, whenever a router cannot forward a packet due to its size, it responds with, “Too big! Try this size instead.”
- Question: How does this relate to IPv6?
All IPv6 packets are “Do Not Fragment.” Routers no longer have to send the correct-sized packets; this is expensive. A significant difference between fragmentation in IPv4 and IPv6 is that IPv6 instead mandates PMTUD.
- Question: What does the firewall need to allow?
To work correctly on the public Internet, IPv6 firewalls must allow ICMPv6, type 2 (Packet Too Big). Therefore, if you implement an IPv6 firewall for your website, enterprise, or other organization, you should permit this specific ICMPv6 message.
The final difference between IPv4 and IPv6 fragmentation
IPv4 hosts must use their best efforts to reassemble fragmented IP packets up to 576 bytes in size. They may also attempt to reassemble fragmented IP packets larger than 576 bytes, but these larger packets may be silently discarded. Therefore, applications should only send packets larger than 576 bytes if they know the remote host can accept or reassemble them.
In IPv6, hosts must try to reassemble fragmented packets with a total reassembled size of up to 1500 bytes. This is because IPv6 has a minimum MTU of 1280 bytes. Fragmented packets more significant than 1500 bytes are silently discarded. The packet must be explicitly fragmented at the origin for IPv6 applications to overcome path MTU limitations. However, unless the remote host can reassemble, they should not attempt to send fragmented packets with a total size exceeding 1500 bytes. Now that we understand the difference between IPv4 and IPv6 fragmentation, let’s focus on IPv6.
Fragmentation in IPv6
A – ) The IPv6 sender may perform fragmentation at the source because an IPv6 router cannot perform fragmentation. Therefore, if the packet is too large for the next hop router, the router will generate an ICMP packet to inform the sending source that the packet is too large. The fragmentation header tries to minimize fragmentation as much as possible by supporting a minimum packet size of 1280 Bytes.
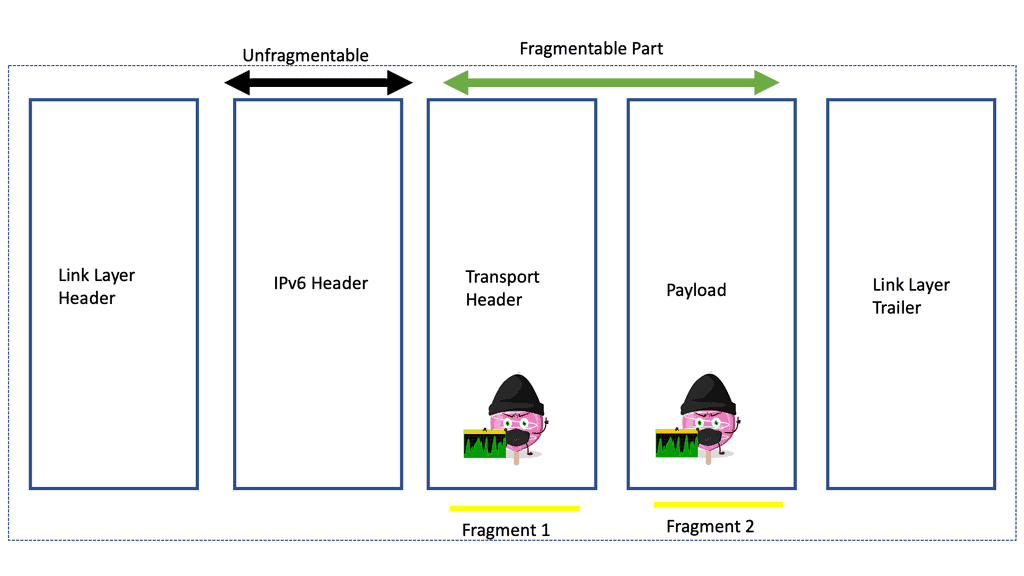
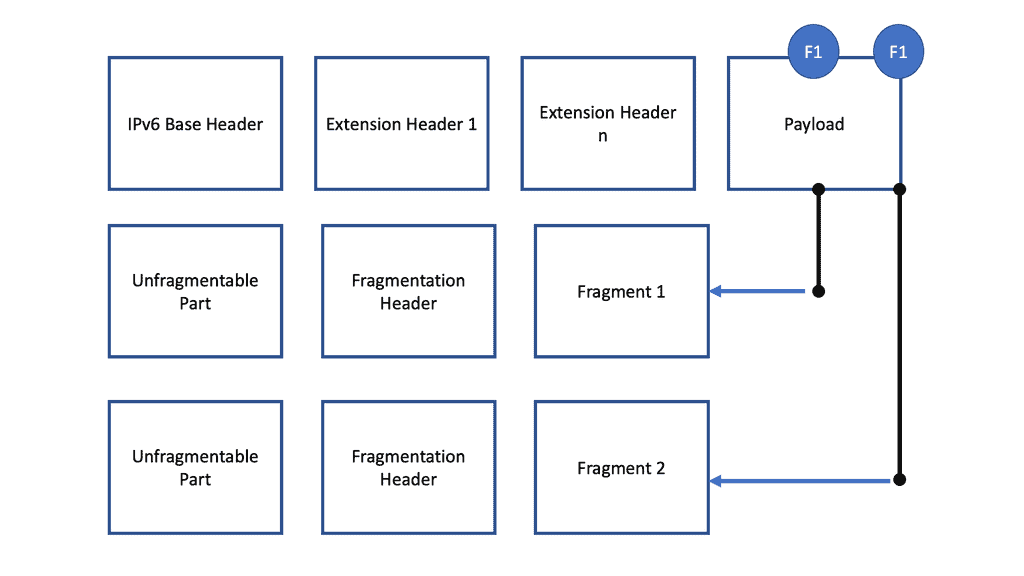
B – ) IPv6 and other extension headers are unfragmentable because every fragment has to go through nodes or routers, and at every router, information stored in these extension headers is required. That is why the IPv6 packet is divided into two parts. The diagram below shows that one is an unfragmentable part, and the other is fragmentable. The unfragmentable part does not encounter any modification in between, and another part is fragmentable and is divided into many small fragments such as fragment 1, fragment 2, and so on.
C – ) After creating small fragments, the fragmentation header and particular fragments (such as fragment 1 ) are connected to the unfragmentable part and sent to the destination. Payload length may change after fragmentation, and the header is added after fragmentation. Corresponding fields, such as header, identification number, fragment offset, and more fragment bits, are filled out appropriately. We will discuss this in more detail in just a moment.
Fragmentation in IPv6: A source of security vulnerabilities
Fragmentation has been a frequent source of security vulnerabilities in IPv4, and for a good reason. With fragmented IPv4 packets, the layer 4 header information is unavailable in the second through the last fragment.
As a result, fragmentation and fragment reassembly can create unexpected and harmful behaviors in an intermediate node. The process of fragmentation in networks can lead to IP security issues. Fragmentation can be exploited for various attacks, such as fingerprinting, IPS insertion/evasion, firewall evasion, and remote code execution. As we move to IPv6, are we exposed to the same type of attacks?
Security Risks: IPv6 Virtual Reassembly
The issue of non-initial fragments
Due to the lack of the L4 header, usually only available on the initial fragment of a fragmented IPv6 packet, non-initial fragments pass through IPsec and NAT64 without examination. The IPv6 Virtual Fragmentation Reassembly (VFR) feature collects fragments and provides L4 info for all fragments for IPsec and NAT64 features.
Most non-initial fragments do not have a Layer 4 header, as it usually travels with the initial fragments (except for micro-fragmentation and tiny fragments). Therefore, some features (such as NAT, Cisco IOS XE Firewall, and IPSec) cannot gather port information from packets. To check the Layer 7 payload, these features may need to reassemble and refragment the fragments.
The use of IPv6 virtual fragmentation reassembly
VFR works with any feature that requires fragment reassembly (such as Cisco IOS XE Firewall, NAT, and IPSec). VFR is automatically enabled on Cisco IOS XE Firewalls, Crypto-based IPSecs, NAT64s, and onePK interfaces whenever these features are present.
If more than one feature attempts to enable VFR automatically on an interface, VFR maintains a reference count to keep track of the number of features that have enabled VFR. When the reference count is reduced to zero, VFR is automatically disabled.
For information on layers 4 or 7, virtual fragmentation reassembly (VFR) is automatically enabled by some features (such as NAT, Cisco IOS XE Firewall, and IPSec). The Cisco IOS XE Firewall can use VFR to create dynamic access control lists (ACLs) to prevent fragmentation attacks.
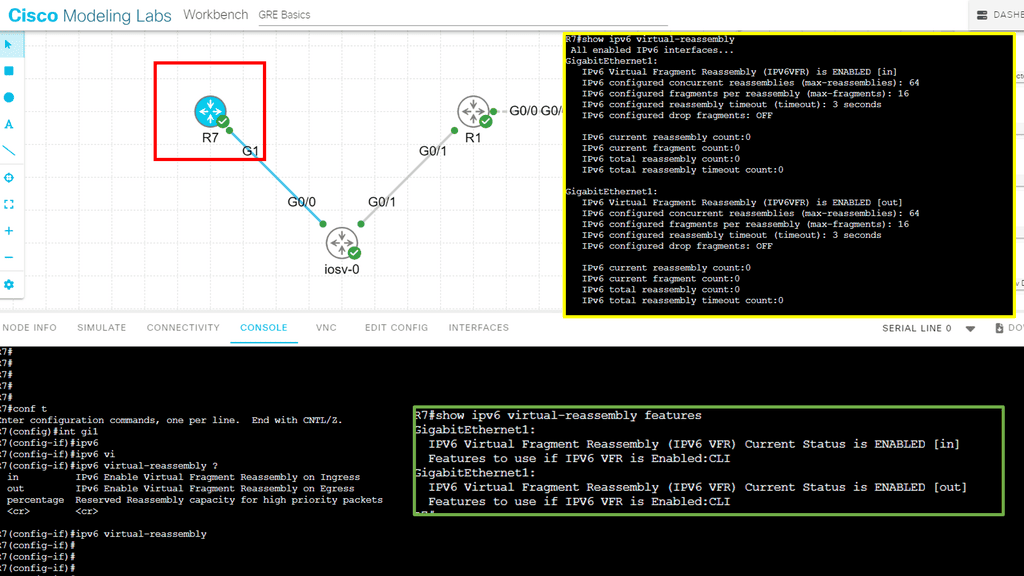
Guide: IPv6 Virtual Reassembly
The following guide shows our options for enabling IPv6 virtual-reassembly. We have in, out, and percentage values. With the command show IPv6 virtual-reassembly, notice the default value.
IPv6 fragmentation example
In an IPv6 world, the IPv6 header length is limited to 40 bytes, yet the IPv4 header has a max of 60. The primary IPv6 header remains a fixed size. IPv6 has the concept of extension headers to add optional IP layer information. Special handling with IPv4 was controlled by “IP options,” but there are no IP options in IPv6. All options are moved to different types of extension headers.
The IPv6 option mechanism is improved over the IPv4 option mechanism. In a packet, IPv6 options are placed in extension headers between the IPv6 header and the transport-layer header. In most cases, IPv6 extension headers are only examined or processed once the packet reaches its final destination. This feature has greatly improved the performance of routers containing options. An IPv4 router must explore all options in the presence of any option.
Unlike IPv4 options, IPv6 extension headers can be of arbitrary length. Also, the number of options a packet carries is not limited to 40 bytes. This feature permits IPv6 options to be used for functions not practical in IPv4. A suitable example of IPv6 options is IPv6 authentication and security encapsulation options.
The following IPv6 extension headers are currently defined.
- Routing – Extended routing, like IPv4 loose source route
- Fragmentation – Fragmentation and reassembly
- Authentication – Integrity and authentication, security
- Encapsulation – Confidentiality
- Hop-by-Hop Option – Special options that require hop-by-hop processing
- Destination Options – Optional information to be examined by the destination node
We now have a fragment header that governs fragmentation. The fragment header contains information that helps the receiving host reassemble the original IP packet.
The IPv6 fragment header
With IPv4, all this was contained in the IPv4 header. There is no separate fragment header in IPv4, and the fragment fields in the IPv4 header are moved to the IPv6 fragment header. The “Don’t fragment” bit (DF) is removed, and intermediate routers are not allowed to fragment. They only permitted end stations to create and reassemble fragments (RFC 2460), not intermediate routers. The design decision stems from the performance hit that fragmentation imposes on nodes.
Routers are no longer required to perform packet fragmentation and reassembly, making dropped packets more significant than the router’s interface MTU. Instead, IPv6 hosts perform PMTU to determine the maximum packet size for the entire path. When a packet hits an interface with a smaller MTU, the routers send back an ICMPv6 type 2 error, known as Packet Too Big, to the sending host. The sending host receives the error message, reduces the size of the sending packet, and tries again.
IPv6 Fragmentation Example
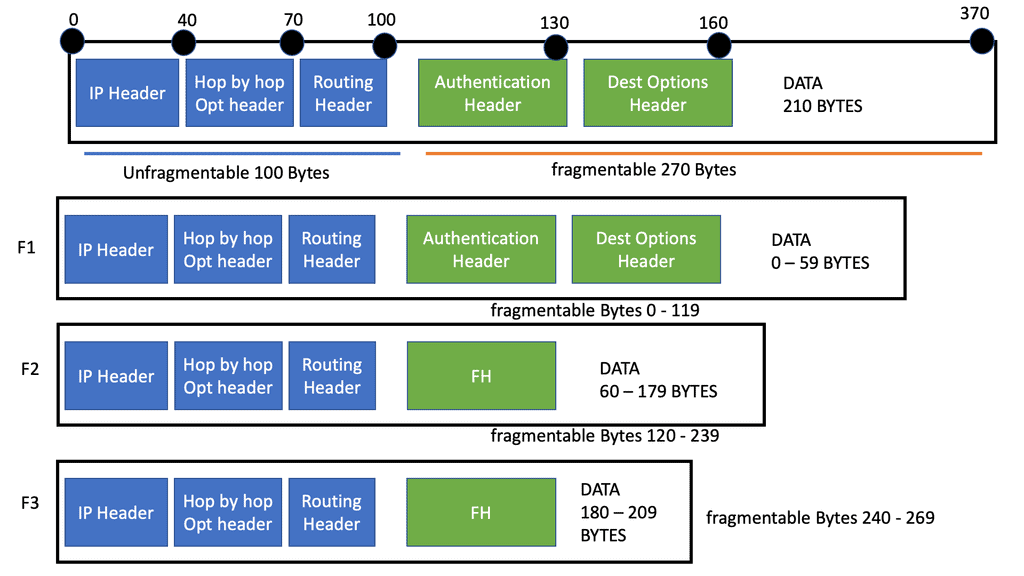
Let us look at a quick IPv6 fragmentation example. For illustration purposes, let us keep the numbers simple. We have an IPv6 datagram that is precisely 370 bytes wide. The IPv6 datagram consists of a 40-byte IP header, four 30-byte extension headers, and 210 bytes of data. Two of the extension headers are unfragmentable, while two are fragmentable.
We must send this over a link with an MTU of only 230 bytes. Three fragments, not the two you might expect, are required because each fragment must contain the two 30-byte unfragmentable extension headers and be a length multiple of 8. In this IPv6 fragmentation example, a 370-byte IPv6 datagram containing four 30-byte extension headers is broken into three fragments.
Fragmentation Security Concerns
When examining an IPv6 fragmentation example, one of the main issues is that the first fragment may not have the required upper-layer (TCP and UDP) information. Security devices require this information to determine if the packet complies with its configured policies and rules. Fragmentation can obfuscate the data, allowing it to pass security devices. Routers and non-stateful devices usually only look at the first fragment containing the header information.
Many small fragments are used to hide or DoS attack a node. The attacker dissects the packet into many small fragmented packets, bypassing security devices. Every small fragment looks legitimate, but once reassembled, the entire packet is used to launch an attack. The attacker is hiding his real intention by pushing the contents of the attack into many small fragments. These might be passed and unseen by devices that only look at the unfragmented part.
Types of IPv6 attacks
1. Neighbor Discovery Protocol (NDP) Attacks:
a) The Neighbor Discovery Protocol (NDP) is a crucial component of IPv6, used for address autoconfiguration and neighbor discovery. Attackers can exploit vulnerabilities in NDP to launch various attacks, including:a) Router Advertisements (RA) Spoofing: Attackers can send malicious router advertisements to redirect traffic or perform man-in-the-middle attacks.
b) Neighbor Solicitation (NS) Spoofing: Attackers can gain unauthorized access to the network by impersonating a legitimate device.
2. Denial of Service (DoS) Attacks:
IPv6 networks are susceptible to Denial of Service (DoS) attacks, which aim to disrupt the availability of network resources. Some common DoS attacks targeting IPv6 include:
a) ICMPv6 Flood: Attackers flood the network with ICMPv6 packets, overwhelming network devices and causing performance degradation.
b) Fragmentation Attacks: Attackers exploit vulnerabilities in the IPv6 fragmentation process, causing network devices to spend excessive resources on reassembling fragmented packets.
3. IPv6 Address Spoofing:
IPv6 address spoofing involves forging the source IPv6 address in packets to deceive network devices. This attack can be used for malicious purposes, such as bypassing access control lists, evading intrusion detection systems, or launching reflection attacks.
4. Man-in-the-Middle (MITM) Attacks:
MitM attacks in IPv6 can enable attackers to intercept and manipulate network traffic. Some standard techniques used in MitM attacks on IPv6 networks include:
a) Router Advertisement (RA) Spoofing: Attackers send malicious RAs to redirect traffic through their devices, allowing them to eavesdrop or modify the communication.
b) Address Resolution Protocol (ARP) Spoofing: Attackers manipulate the IPv6-to-MAC address resolution process, intercepting traffic between devices.
Additional IPv6 Attacks:
Other attacks include overlapping fragments, incomplete sets of fragments, fragments inside a tunnel, and nested fragments. Nested fragments are packets with multiple sets of fragment headers, which should never occur in standard IP networks. The source only creates one fragment header. Overlapping fragments can be used for O/S fingerprinting and IPS/IDS evasions.
Fragmentation attacks may be used on DoS, an end host. If hosts cannot process fragmented packets correctly, attackers can send many fragmented packets, which will be processed by kernel memory, exhausting the kernel from processing legitimate fragments. Many tools like Whisker, Fragrouter, and Scapy can craft these packets.
Proper handling of the IPv6 fragment
IPv6 attempts to minimize the use of fragmentation by supporting the minimum IPv6 datagram size of 1280 bytes. The minimum datagram size in IPv4 is 576 bytes (not to be confused with the minimum MTU for both IP versions). This removes the severe restriction on data size we had with IPv4 and should minimize the need for fragmentation.
Antonios Atlasis conducted an “Attacking IPv6 using fragmentation” webinar for Black Hat Europe. It included several O/S such as Ubuntu, FreeBSD, OpenBSD, and W2K7. Scapy, a packet manipulation tool, was used to test if the O/S responded to the tiny IPv6 fragment.
For the Upper-layer protocol, ICMPv6 was used to send Echo Requests. All major O/S accepted tiny fragments and sent an ECHO-REPLY in response to the ECHO REQUEST. Accepting small fragments has consequences unless Deep Packet Inspection (DPI) performs complete IP datagram reassembly before IP forwarding. However, without proper DPI, it could lead to firewall evasion. A similar problem exists with IPv4.
Going deep on the RFCs and the IPv6 fragment
RFC 5722 recommends disallowing overlapping fragments. The RFC states that if an IPv6 host performs reassembling and contains a fragment determined to be overlapping, then the entire datagram is silently discarded. No error message is sent back to the sending host. Antonios Atlasis’s test proves that none of the O/S is RFC 5722 compliant.
Like the IPv4 world, IPv6 security features consist of ACL with the “fragments” keyword. The ACL matches the non-initial IPv6 fragment. The initial IPv6 fragment contains the information for Layer 3 and Layer 4. Cisco IOS has a feature known as Virtual Reassembly, which inspects fragmented packets. It is secondary to an input ACL, meaning the input ACL has the first chance to check incoming packets. It reassembles fragmented packets, examines any out-of-sequence fragments, puts them back in proper sequence, and sends up the protocol stack.
Closing Points on IPv6 Fragmentation
Unlike IPv4, where routers along the path could fragment packets, IPv6 introduces a more streamlined approach. In IPv6, only the source node is responsible for fragmenting packets. This shift means that routers are relieved from the burden of processing fragmented packets, thus improving overall network efficiency. With the use of the Fragment Extension Header, IPv6 ensures that packets are reassembled only at the destination, reducing potential points of failure and enhancing security.
IPv6 fragmentation comes with its own set of security considerations. One of the major concerns is the potential for fragmentation-based attacks, such as the Tiny Fragment Attack. By sending multiple small fragments, an attacker could potentially evade detection and carry out malicious activities. To mitigate these risks, network administrators must implement robust security measures, such as deep packet inspection and setting fragmentation thresholds, to identify and block suspicious traffic.
While IPv6’s approach to fragmentation reduces the load on routers, it also has specific performance implications. When a packet is fragmented, each fragment carries overhead, which can lead to increased bandwidth usage. Additionally, if any fragment is lost during transmission, the entire packet must be resent, potentially leading to higher latency. Therefore, optimizing packet sizes and understanding the network’s Path Maximum Transmission Unit (PMTU) are essential steps in maintaining efficient performance.
To effectively manage IPv6 fragmentation, IT professionals should adopt a set of best practices. These include configuring devices to handle large packet sizes, employing PMTU discovery techniques, and regularly monitoring network traffic for anomalies. Additionally, training staff on the nuances of IPv6 can further enhance network resilience and performance.
Summary: IPv6 Fragmentation
In this blog post, we explored the intricacies of IPv6 fragmentation, its significance, and how it impacts our digital experiences.
Understanding IPv6 Fragmentation
IPv6 fragmentation refers to dividing IPv6 packets into smaller units, known as fragments, to facilitate transmission across networks with different maximum transmission unit (MTU) sizes. Unlike IPv4, IPv6 prefers path MTU discovery over fragmentation. However, in specific scenarios, fragmentation becomes necessary to ensure data reaches its destination successfully.
The Need for Fragmentation
Fragmentation is crucial in enabling communication between networks with varying MTU sizes. As data traverses different network segments, it may encounter smaller MTUs, leading to packet fragmentation. Without fragmentation, packets may be dropped or severely delayed, hindering effective data transmission.
Fragmentation Process in IPv6
When fragmentation is required, the sending host breaks the original IPv6 packet into smaller fragments. Each fragment is assigned a Fragment Header, which contains essential information for reassembling the original packet at the receiving end. Upon arrival, the receiving host reassembles the fragments based on the information provided in the Fragment Header.
Section 4: Impact on Performance and Efficiency
While fragmentation ensures data delivery across networks with varied MTU sizes, it can affect performance and efficiency. Fragmentation adds overhead to the network, requiring additional processing power and resources. Excessive fragmentation can lead to increased latency and potential packet loss.
Best Practices for IPv6 Fragmentation
To optimize network performance and reduce the need for fragmentation, it is advisable to adhere to best practices. These include ensuring network devices are configured with appropriate MTU sizes, employing path MTU discovery mechanisms, and utilizing techniques such as TCP Maximum Segment Size (MSS) adjustment to avoid fragmentation whenever possible.
Conclusion:
In the realm of IPv6, fragmentation serves as a vital mechanism for ensuring seamless data transmission across networks with different MTU sizes. Understanding the concept of fragmentation, its significance, and its potential impact on performance empowers network administrators and engineers to optimize their networks and provide efficient connectivity in an IPv6-dominated world.