IPFIX Big Data
In today's data-driven world, the ability to extract valuable insights from vast amounts of information has become crucial. One such powerful tool that aids in this endeavor is IPFIX Big Data. In this blog post, we will delve into the world of IPFIX Big Data, exploring its significance, benefits, and applications.
IPFIX (Internet Protocol Flow Information Export) is a standard protocol used for exporting network flow information. It provides a structured format to capture and record data related to network traffic. By leveraging Big Data techniques, organizations can process and analyze IPFIX data on a massive scale, uncovering valuable patterns, trends, and anomalies.
Improved Network Performance Monitoring: IPFIX Big Data enables organizations to gain deep visibility into network traffic, allowing for real-time monitoring and analysis. By identifying bottlenecks, network congestion, and abnormal behavior, administrators can proactively address issues, optimize network performance, and enhance user experience.
Advanced Security Analytics: The abundance of data collected through IPFIX Big Data provides a treasure trove of information for security analysts. By applying sophisticated analytics techniques, organizations can detect and mitigate potential security threats, including intrusion attempts, DDoS attacks, and malware infections. IPFIX Big Data empowers security teams to stay one step ahead of cybercriminals.
Network Capacity Planning: IPFIX Big Data plays a vital role in capacity planning, allowing organizations to anticipate future network demands. By analyzing historical IPFIX data, administrators can accurately forecast resource requirements, optimize network infrastructure, and ensure scalability to meet growing business needs.
Business Intelligence and Decision Making: IPFIX Big Data provides valuable insights into user behavior, application usage, and network performance. By mining this data, organizations can make data-driven decisions, optimize business processes, and uncover new opportunities for growth and innovation.
Data Volume and Scalability: The sheer volume of IPFIX data can pose challenges in terms of storage, processing power, and scalability. Organizations need to have robust infrastructure in place to handle the massive influx of data and employ efficient data management strategies.
Data Privacy and Security: As IPFIX data contains sensitive information about network traffic, ensuring data privacy and security is of utmost importance. Organizations must implement robust security measures and adhere to data protection regulations to safeguard this valuable asset.
IPFIX Big Data has revolutionized the way organizations analyze and leverage network flow information. From improved network performance monitoring to advanced security analytics and driving innovation, the power of IPFIX Big Data is undeniable. By harnessing its potential and overcoming challenges, organizations can unlock valuable insights, enhance operational efficiency, and stay ahead in today's data-driven landscape.
Matt Conran
Highlights: IPFIX Big Data
Understanding IPFIX and Big Data
IPFIX, which stands for Internet Protocol Flow Information Export, is a flexible and extensible protocol that allows for the collection and export of network flow data. It provides essential information about network traffic, including source and destination IP addresses, ports, protocols, and more. By capturing and analyzing this data, organizations can gain deep visibility into their network infrastructure and identify potential bottlenecks, anomalies, or security threats.
Big data analytics has revolutionized decision-making processes across industries, and IPFIX is no exception. By applying advanced analytics techniques to IPFIX data, organizations can uncover hidden patterns, detect anomalies, and derive actionable insights. Whether it is monitoring network performance, optimizing resource allocation, or identifying potential security breaches, IPFIX big data analytics empowers businesses to make data-driven decisions and stay ahead of the curve.
IPFIX Big Data Considerations:
1. Network Performance Optimization:
IPFIX big data enables organizations to monitor and analyze network traffic in real-time, providing valuable insights into bandwidth utilization, latency, and packet loss. By identifying performance bottlenecks and optimizing network resources, businesses can enhance user experience, streamline operations, and reduce costs.
2. Security Threat Detection:
The richness of IPFIX data allows for effective detection and prevention of security threats. By analyzing network flow data, organizations can identify suspicious activities, detect malware infections, and mitigate potential cyber-attacks. IPFIX big data analytics serves as a powerful tool in ensuring network security and safeguarding sensitive information.
3. Capacity Planning:
IPFIX big data analytics provides organizations with the ability to forecast future network demands and plan capacity accordingly. By analyzing historical traffic patterns, businesses can accurately predict resource requirements, optimize infrastructure investments, and ensure scalability to meet growing demands.
4. Quality of Service Enhancement:
With IPFIX big data, organizations can gain insights into network traffic patterns and prioritize critical applications or services. By implementing Quality of Service (QoS) measures based on IPFIX analytics, businesses can optimize network performance, reduce latency, and improve overall user experience.
The Role of Big Data
– Big Data is a field devoted to analyzing, processing, and storage of extensive collections of data that continually originate from disparate sources. Consequently, Big Data solutions and practices are typically required when more than traditional data analysis, processing, and storage technologies and techniques are needed. Mainly, Big Data addresses distinct requirements, such as combining multiple unrelated datasets, processing large amounts of unstructured data, and harvesting hidden information time-sensitively.
– IPFIX, short for IP Flow Information Export, is a protocol that allows for the collection and export of flow records from network devices. It provides valuable insights into network traffic patterns, including source and destination IP addresses, ports, and protocols. By capturing and analyzing IPFIX data, organizations gain a comprehensive understanding of their network infrastructure and can make data-driven decisions to optimize performance and security.
– The true power of IPFIX lies in its ability to handle big data. With the exponential growth of network traffic, traditional analysis methods fall short. IPFIX big data solutions, on the other hand, leverage advanced analytics and machine learning algorithms to process massive amounts of flow data in real time. This enables network administrators to identify anomalies, detect security threats, and troubleshoot performance issues with unmatched precision and speed.
Use Cases of IPFIX Big Data
1. Network Performance Optimization: By analyzing IPFIX data, organizations can identify bandwidth bottlenecks, optimize network configurations, and ensure efficient resource allocation. This leads to enhanced network performance, reduced latency, and improved user experience.
2. Security Threat Detection: With the help of IPFIX big data analytics, organizations can detect and mitigate security threats in real-time. By monitoring flow patterns, identifying suspicious behavior, and employing machine learning algorithms, IPFIX enables proactive threat detection and response, safeguarding networks from cyberattacks.
3. Capacity Planning and Traffic Engineering: IPFIX big data offers valuable insights into network traffic patterns, allowing organizations to plan for future capacity needs. Organizations can ensure smooth operations and avoid costly downtime by analyzing historical data, predicting traffic trends, and optimizing network infrastructure.
IP Flow Information Export
a) IPFIX is overseen by the Internet Engineering Task Force (IETF). Flow information can be exported from routers, switches, firewalls, and other infrastructure devices using IPFIX. Exporters and collectors use IPFIX to format and transfer flow information. Several RFCs, including 7011 through 7015 and RFC 503, describe IPFIX. Version 9 of NetFlow is the basis and primary reference for IPFIX. IPFIX is essentially the same as NetFlow Version 9, except for a few terminologies.
b) Push protocols are considered IPFIX protocols. IPFIX-enabled devices automatically send IPFIX messages to configured collectors (receivers) without user input. In most cases, the sender orchestrates IPFIX data messages. To construct these flow data messages, IPFIX introduces the concept of templates. User-defined data types can also be used in IPFIX messages. IPFIX prefers Stream Control Transmission Protocol (SCTP) as the transport layer protocol; however, Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) can also be used.
c) UDP messages are usually used to export Cisco NetFlow records. On the sending device, the IP address of the NetFlow collector and the destination UDP port must be configured. The NetFlow standard does not specify a specific NetFlow listening port (RFC 3954). In addition to UDP port 2055, NetFlow can use ports such as 9555 or 9995, 9025, and 9026. IPFIX uses UDP port 4739 by default.
Attacking Tools are Readily Available
Attacker tools are readily available, making DDoS defense much harder than attack. It’s hard to blame anyone; the ISP is just transiting traffic, and end users don’t know if they are compromised and part of a BotNet farm. There is no service of abuse or license for the Internet, making tracking and detection between independent service provider locations difficult. Recently, there has been a shift in application footprints. We now have multi-tiered applications dispersed across various sites, all requiring cross-communication.
- New Attack Surface
New application architecture results in new attacks, and with any application segment, you are only as strong as the weakest link, requiring a new set of network visibility. That can help you correlate disparate data points. The birth of the cloud and new technologies increased the attack surface, making quick and accurate DDoS detection using tools such as IPFIX Big data an enchantment to other DDoS solutions such as BGP Flowspec.
- The Ability to Stop DDoS
Companies require mechanisms to stop and slow down DDoS attacks. The IETF introduced best practices with BCP38, and service providers started incorporating ingress filtering into their designs and cross-checking incoming frames. However, ISPs are not forced by contract to implement these features. The only way to adequately mitigate DDoS attacks is adequate detection. How long should this take? What timeframe is acceptable?
All this depends on the traffic analysis solution you have in place. Initially, traffic analysis began monitoring up/down interfaces with introductory statistics. They then moved to Syslog servers and single source basic flow capturing. We need a system that captures enriched flow data and groups infrastructure and application information together. Enriching data from all elements allows the network and its traffic to be viewed as one holistic entity.
Before you proceed, you may find the following helpful:
IPFIX Big Data
The Rise of Big Data:
Big Data refers to the exponential growth and availability of structured and unstructured data. IPFIX Big Data refers to applying Big Data principles to IPFIX data. With the increasing volume, velocity, and variety of network traffic, traditional network monitoring tools struggle to keep up. IPFIX Big Data leverages advanced analytics and processing techniques to extract valuable insights from this massive data.
Benefits of IPFIX Big Data:
Advanced Network Monitoring: Organizations comprehensively understand their network behavior by analyzing IPFIX Big Data. This allows for proactive monitoring, rapid detection of anomalies, and improved security incident response. Additionally, IPFIX Big Data enables the identification of network bottlenecks, performance optimization, and capacity planning.
Enhanced Traffic Analysis: IPFIX Big Data allows for granular analysis of network traffic patterns, allowing organizations to identify trends, troubleshoot issues, and optimize network performance. By leveraging advanced analytics and machine learning algorithms, IPFIX Big Data can detect and classify different types of traffic, leading to a better quality of service and improved user experience.
Real-Time Insights: IPFIX Big Data provides near real-time insights into network traffic, allowing organizations to respond quickly to emerging threats or issues. By combining streaming analytics with historical data analysis, organizations can detect and respond to network incidents faster, minimizing downtime and maintaining service reliability.
Enhanced Network Security: IPFIX big data is pivotal in bolstering network security. By analyzing flow data, organizations can identify and mitigate potential threats in real time. Suspicious traffic patterns, anomalies, and known attack signatures can be detected promptly, enabling swift action to safeguard the network.
Network Performance Optimization: IPFIX big data offers valuable insights into network performance. Organizations can identify bottlenecks, optimize bandwidth allocation, and improve overall network efficiency by monitoring flow data. This enables them to provide a seamless user experience and maximize productivity.
Capacity Planning and Resource Allocation: With IPFIX big data, organizations can accurately forecast resource requirements and plan their network capacity accordingly. They gain insights into traffic patterns, peak usage times, and resource utilization trends through comprehensive flow analysis. This empowers them to allocate resources effectively and avoid potential network congestion.
Challenges and Considerations:
Implementing IPFIX Big Data comes with its own set of challenges. Organizations must ensure they have sufficient storage and processing capabilities to handle large volumes of data. They must also consider privacy and security concerns when collecting and storing IPFIX data. Additionally, the complexity of IPFIX data requires specialized skills and tools for practical analysis and interpretation.
IPFIX Big Data: Enhanced Data Sources
DDoS traffic analysis solutions extract various types of flow data from network devices. The flow record consists of fields from multiple data types, including NetFlow, IPFIX, and sFlow. In addition, DDoS Big Data solutions can enrich records at the ingest layer by performing a lookup of the source and destination in the flow, BGP table, and GeoIP database. These values are added as volumes and fields stored with the original flow. The extra information lets administrators slice the traffic at ingesting, enabling a fantastic multi-dimensional view of network traffic.
Tools like sFlOW and IPFIX variants like IPFIX BGP are critical in DDoS detection. Classic flow fields based on 5-tuples include IP address and source/destination port numbers, which are later expanded to include MAC address, MPLS, and application schematics like URLs, HTTP host headers, DNS queries, and responses.
The availability of advanced fields enables the detection of sophisticated attacks higher up the protocol stack. For example, access to the HTTP host header for each request allows precise identification down to the URL
A key point: Different attacking vectors.
Not all DDoS attacks and DNS reflection attacks are easily detected. Volumetric attacks, such as SynFlood, are more accessible to catch than SlowLoris and RUDY attacks. Layer 7 attacks usually don’t exceed the packet/sec threshold, a standard parameter for detecting volumetric-based attacks.
To combat this, we must go deeper than the standard 5-tuple with augmented flows. Augmented flows contain additional fields to include a variety of advanced metrics such as connection counts, congestion windows, and TCP RTT. Traditional flow data does not provide this level of detailed information.
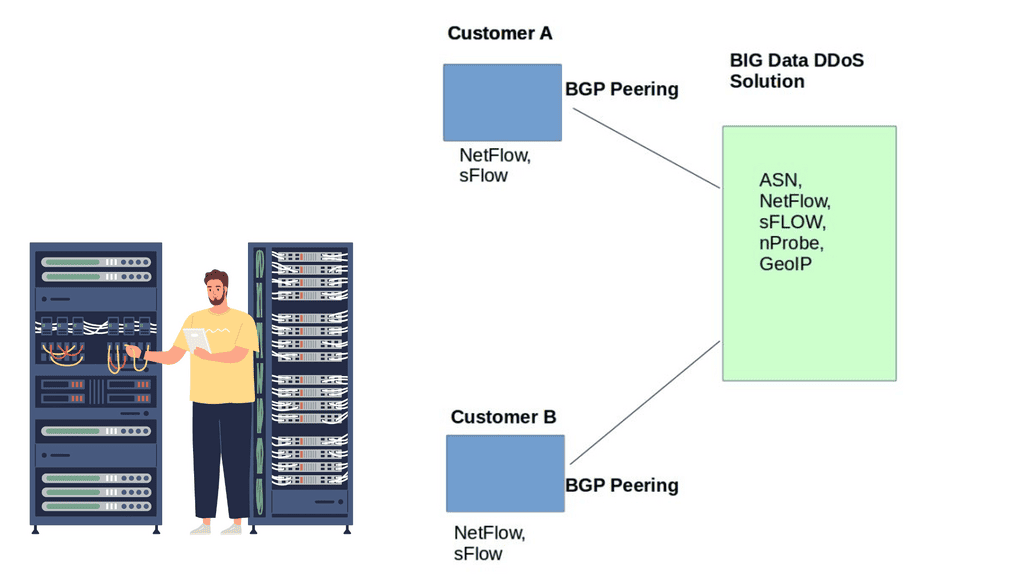
Data source variations
Netflow and IPFIX, flow record creation, is based on packets sharing the same fields. Flow state is held, hitting system resources. To save system resources, flows are exported at predefined times. As a result, traffic measurement is accurate, but it might not hit the detector for up to one minute.
sFlow sends packet samples every 1 in N, streaming flows as soon as they are prepared. sFlOW draws fewer system resources than its Netflow counterpart. It is considered faster and has better accuracy, meaning it’s an excellent tool for DDoS detection.
sFlow is better at carrying the source MAC address than NetFlow and IPFIX. With NetFlow and IPFIX, the source MAC is possible but not usually implemented by all vendors. NetFlow is useful for some requirements, while IPFIX and sFlow are for others.
To get all the possible knobs, it’s better to extract them from all data sources and combine them into one database that can easily be viewed with a single portal. Combining all data sources into one unified store makes the protocol type less relevant.
IPFIX BGP
DDoS solution: Irregularities with ASN Information
DDoS solutions can peer EBGP with customers by giving them a copy of the BGP table. Customer route updates are reflected through the standard BGP propagation procedure. It’s a non-intrusive peering agreement; BGP’s next hops are not altered, meaning customers’ data plane traffic flows as usual. The contents of the BGP table provide access to customers’ control plane information, enabling complete visibility of the data source and destination.
The manual approach with BGP can be cumbersome. BGP offers a string of information about DDoS sources and destinations, but it can be hard to craft regular expressions to extract this information. Not everyone can craft regular expressions, a skill for senior engineers.
Netflow and BGP
Netflow does provide some BGP ASN information, but you only have access to the source and destination of the Peer or Origin ASN. Some high-end platforms do both, but it’s restricted to specific devices and vendor discretion. NetFlow should not hold all BGP-type information; this would be a suboptimal solution.
Also, Netflow does have drawbacks and inaccuracies when determining the source ASN. The destination ASN is never usually a problem. The BGP process/daemon performs a REVERSE BGP Lookup to determine the source ASN and populate the FIB.
However, this type of BGP lookup does not guarantee the correctness of results. A REVERSE BGP Lookup primarily determines how to route back to the source, but this does not correlate with how the source may route to you.
Most networks are asymmetric, meaning the source-destination path differs from the reverse direction. An IP packet traversing from source A to destination B will take a different return path. Due to the shared nature of asymmetric routing, traditional monitoring systems misrepresent the BGP table with inaccurate source ASNs.
Legacy traffic analysis systems that don’t peer EBGP with customers will report inaccurate source ASN. It is not very good when troubleshooting a DDoS attack, and the source ASN information is incorrect.
Most legacy systems don’t offer accurate, complete AS-Path information, leading to false positives and the inability to determine friend from foe. It’s far better for the solution to peer BGP with the customer, extract NetFlow / IPFIX BGP / sFlow locally, and then correlate the data to provide a unified source of truth.
A key point: IPFIX BGP
BGP data can be correlated with IPFIX data so that the paths available in the network are shown, what paths are being used, and the traffic volume on each path between autonomous systems. BGP IPFIX Analysis correlates IPFIX records with BGP routing info to visualize AS paths and how much traffic is traversing these paths in real-time. IPFIX BGP: Analysis correlates IPFIX records with BGP routing info to visualize AS paths and how much traffic is traversing these paths in real-time.
Origin ASN and Peer ASN provide the data flow endpoints, and NetFlow is used in the middle. We can utilize GeoIP Information to analyze the county, region, and city. Correlate this with the complete AS-Path list, and you now have a full view of the source and destination paths with all the details of the middle points.
Closing Points on IPFIX Big Data
IPFIX is a protocol developed for exporting flow information from routers, switches, and other network devices. It allows organizations to capture detailed information about IP traffic, thus providing a comprehensive view of network behavior. By exporting flow records to a collector, IPFIX facilitates real-time monitoring and analysis, making it an indispensable tool in network management.
In the realm of Big Data, the ability to process and analyze vast amounts of information quickly is crucial. IPFIX contributes significantly by providing structured, high-fidelity data that can be easily ingested into Big Data platforms. This integration allows organizations to conduct deeper network analysis, detect anomalies, and optimize traffic flow efficiently. The granularity of IPFIX data ensures that even the most minute details are available for scrutiny, enhancing the overall analytical capability.
1. **Enhanced Network Security:** By providing detailed insights into network traffic, IPFIX helps in identifying potential security threats and breaches, allowing for timely intervention.
2. **Optimized Network Performance:** With IPFIX data, organizations can monitor network performance in real-time, identifying bottlenecks and ensuring optimal operation.
3. **Cost Efficiency:** By enabling precise traffic analysis, IPFIX aids in resource allocation and bandwidth management, leading to reduced operational costs.
While the benefits are substantial, integrating IPFIX with Big Data analytics poses certain challenges. These include the need for robust data storage solutions to handle the volume of data generated and ensuring data privacy and security. Additionally, organizations must invest in skilled personnel to interpret and act on the insights provided by IPFIX data effectively.
Summary: IPFIX Big Data
In today’s digital age, the amount of data generated is growing exponentially. This data holds immense potential for businesses and organizations to gain valuable insights and make informed decisions. One such powerful tool for harnessing this data is IPFIX Big Data. In this blog post, we delved into the world of IPFIX Big Data, its applications, and the impact it can have on various industries.
Understanding IPFIX Big Data
IPFIX, which stands for Internet Protocol Flow Information Export, is a standard protocol for collecting and exporting network flow data. It provides detailed information about network traffic, including source and destination IP addresses, protocols, ports, and more. When this flow data is collected on a large scale and processed using big data analytics techniques, it becomes IPFIX Big Data. This rich dataset opens up a world of possibilities for analysis and insights.
Applications of IPFIX Big Data
The applications of IPFIX Big Data are vast and diverse. In cybersecurity, it can be used for real-time threat detection and network anomaly detection. By analyzing network flow data at a large scale, security professionals can identify patterns and behaviors that indicate potential security breaches or attacks. This proactive approach allows for faster response times and better protection against cyber threats.
IPFIX Big Data can offer valuable insights into network performance, bandwidth utilization, and traffic patterns in network optimization. By identifying bottlenecks and optimizing network resources, organizations can enhance the efficiency and reliability of their networks, leading to improved user experiences and cost savings.
Leveraging IPFIX Big Data in Business Intelligence
Businesses can leverage IPFIX Big Data to gain deep insights into user behavior, customer preferences, and market trends. Organizations can analyze network flow data to understand how users interact with their digital platforms, which features are most popular, and what drives user engagement. This information can then be used to optimize products, personalize marketing campaigns, and improve overall business strategies.
The Future of IPFIX Big Data
As the volume and complexity of network data continue to grow, the importance of IPFIX Big Data will only increase. Advancements in machine learning and artificial intelligence will further enhance the capabilities of IPFIX Big Data analytics, enabling more accurate predictions, automated responses, and proactive decision-making. Additionally, integrating IPFIX Big Data with other emerging technologies like the Internet of Things (IoT) will unlock new possibilities for data-driven innovation.
Conclusion:
In conclusion, IPFIX Big Data is a powerful tool that can revolutionize how organizations understand and utilize network flow data. Its applications span across various industries, from cybersecurity to business intelligence. By harnessing the potential of IPFIX Big Data, businesses can gain a competitive edge, make informed decisions, and unlock new opportunities for growth and success.
- DMVPN - May 20, 2023
- Computer Networking: Building a Strong Foundation for Success - April 7, 2023
- eBOOK – SASE Capabilities - April 6, 2023

