Stateful Inspection Firewall
Network security is crucial in safeguarding businesses and individuals from cyber threats in today's interconnected world. One of the critical components of network security is a firewall, which acts as a barrier between the internal and external networks, filtering and monitoring incoming and outgoing network traffic. Among various types of firewalls, one that stands out is the Stateful Inspection Firewall.
Stateful Inspection Firewall, also known as dynamic packet filtering, is a security technology that combines the benefits of traditional packet filtering and advanced inspection techniques. It goes beyond simply examining individual packets and considers the context and state of the network connection. Doing so provides enhanced security and greater control over network traffic.
Stateful inspection firewalls boast an array of powerful features. They perform deep packet inspection, scrutinizing not only the packet headers but also the payload contents. This enables them to detect and mitigate various types of attacks, including port scanning, denial-of-service (DoS) attacks, and application-layer attacks. Additionally, stateful inspection firewalls support access control lists (ACLs) and can enforce granular security policies based on source and destination IP addresses, ports, and protocols.
Stateful inspection firewalls maintain a state table that tracks the state of each network connection passing through the firewall. This table stores information such as source and destination IP addresses, port numbers, sequence numbers, and more. By comparing incoming packets against the state table, the firewall can determine whether to permit or reject the traffic. This intelligent analysis ensures that only legitimate and authorized connections are allowed while blocking potentially malicious or unauthorized ones.
Implementing stateful inspection firewalls brings numerous advantages to organizations. Firstly, their ability to maintain session state information allows for enhanced security as they can detect and prevent unauthorized access attempts. Secondly, these firewalls provide improved performance by reducing the processing overhead associated with packet filtering. Lastly, stateful inspection firewalls offer flexibility in handling complex protocols and applications, ensuring seamless connectivity for modern network infrastructures.
Deploying stateful inspection firewalls requires careful planning and consideration. Organizations should conduct a thorough network inventory to identify the optimal placement of these firewalls. They should also define clear security policies and configure the firewalls accordingly. Regular monitoring and updates are essential to adapt to evolving threats and maintain a robust security posture.
Matt Conran
Highlights: Stateful Inspection Firewall
Stateful inspection firewalls, also known as dynamic packet filtering, operate by monitoring the state of active connections and using this information to determine which network packets to allow through the firewall. Unlike their stateless counterparts, which only check the packet’s header, stateful inspection firewalls examine the context of the traffic. They keep track of each session, ensuring that only legitimate packets associated with an active connection are permitted. This sophisticated approach allows them to detect and block unauthorized access attempts more effectively.
The Evolution of Firewalls
1: ) Firewalls have come a long way since their inception. Initially, basic packet-filtering firewalls examined network traffic based on packet headers, such as source and destination IP addresses and port numbers. However, these traditional firewalls lacked the ability to analyze packet contents, leaving potential security gaps.
2: ) Stateful firewalls revolutionized network security by introducing advanced packet inspection capabilities. Unlike their predecessors, stateful firewalls can examine the entire packet, including the payload, and make intelligent decisions based on the packet’s state.
3: ) To comprehend the inner workings of a stateful firewall, imagine it as a vigilant sentry guarding the entrance to your network. It meticulously inspects each incoming and outgoing packet, keeping track of the state of connections. By maintaining knowledge of established connections, a stateful firewall can make informed decisions about allowing or blocking traffic.
Stateful firewalls offer several advantages over traditional packet-filtering firewalls.
Firstly, they provide improved security by actively monitoring the state of connections, preventing unauthorized access and potential attacks. Secondly, stateful firewalls offer granular control over network traffic, allowing administrators to define specific rules based on protocols, ports, or even application-level information.
What is a Stateful Inspection Firewall?
Stateful inspection firewalls go beyond traditional packet filtering mechanisms by analyzing the context and state of network connections. They maintain a record of outgoing packets, allowing them to examine incoming packets and make informed decisions based on the connection’s state. This intelligent approach enables a higher level of security and better protection against advanced threats.
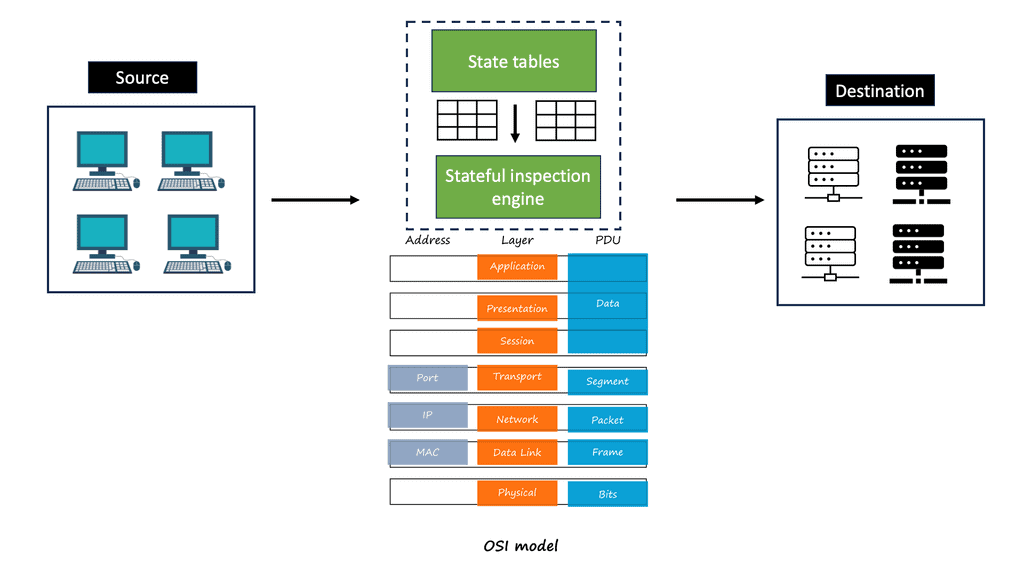
A stateful inspection firewall operates at the network and transport layers of the OSI model. It monitors the complete network session, keeping track of the connection’s state, including source and destination IP addresses, ports, and sequence numbers. By analyzing this information, the firewall can determine if incoming packets are part of an established or valid connection, reducing the risk of unauthorized access.
– Enhanced Security: Stateful inspection firewalls provide a stronger defense against malicious activities by analyzing the complete context of network connections. This ensures that only legitimate and authorized traffic is allowed through, minimizing the risk of potential attacks.
– Improved Performance: These firewalls optimize network performance by efficiently managing network traffic. By keeping track of connection states, they can quickly process incoming packets, reducing latency and enhancing overall network performance.
– Flexibility and Scalability: Stateful inspection firewalls can be customized to meet specific network security requirements. They offer flexibility in configuring security policies, allowing administrators to define rules and access controls based on their organization’s needs. Additionally, they can be seamlessly scaled to accommodate growing network infrastructures.
**Firewall locations**
– In most networks and subnets, firewalls are located at the edge. The Internet poses numerous threats to networks, which are protected by firewalls. In addition to protecting the Internet from rogue users, firewalls prevent rogue applications from accessing private networks.
– To ensure that resources are available only to authorized users, firewalls protect the bandwidth or throughput of a private network. A firewall prevents worthless or malicious traffic from entering your network. A dam protects a river from flooding and overflowing, similar to how a dam works on a river. The dam prevents flooding and damage.
– In short, firewalls are network functions specifically tailored to inspect network traffic. Upon inspection, the firewall decides to carry out specific actions, such as forwarding or blocking it, according to some criteria. Thus, we can see firewalls as security network entities with several different types.
– The different firewall types will be used in other network locations in your infrastructure, such as distributed firewalls at a hypervisor layer. You may have a stateful firewall close to workloads while a packet-filtering firewall is at the network’s edge. As identity is now the new perimeter, many opt for a stateful inspection firewall nearer to the workloads. With virtualization, you can have a stateful firewall per workload, commonly known as virtual firewalls.
Example Firewalling Technology: Linux Firewalling
Understanding UFW
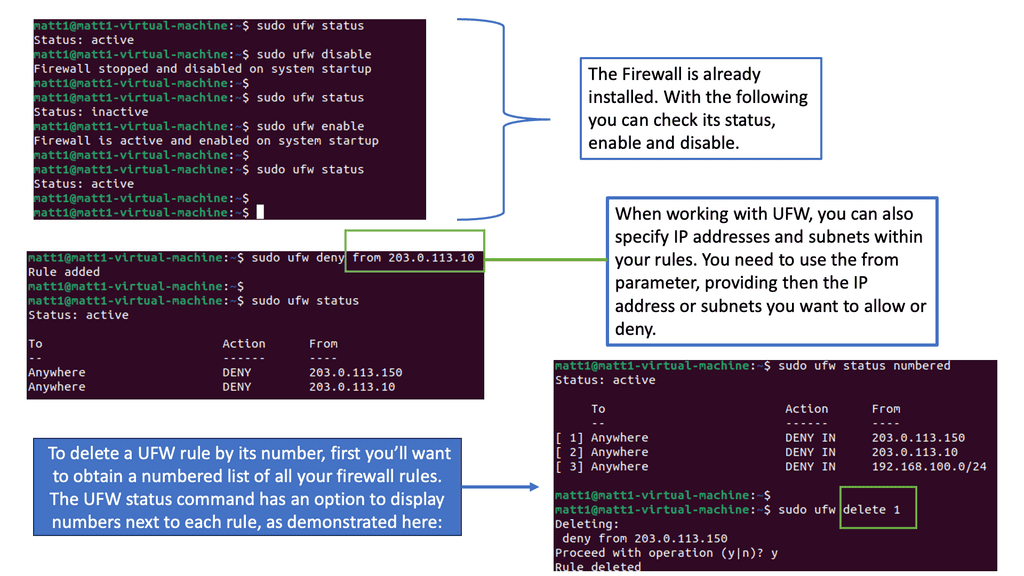
UFW, a front-end for IPtables, is a user-friendly and powerful firewall tool designed for Linux systems. It provides a straightforward command-line interface, making it accessible even to those with limited technical knowledge. UFW enables users to manage incoming and outgoing traffic, creating an additional layer of defense against potential threats.
UFW offers a range of features that enhance system security. Firstly, it allows you to create rules based on IP addresses, ports, and protocols, granting you granular control over network traffic. Additionally, UFW supports IPv4 and IPv6, ensuring compatibility with modern network configurations. Furthermore, UFW seamlessly integrates with other firewall solutions and can be easily enabled or disabled per your needs.
Example Firewall Technology: CBAC Firewall
Cisco CBAC firewall goes beyond traditional stateless firewalls by inspecting and filtering traffic based on contextual information. It operates at the application layer of the OSI model and provides advanced security capabilities.
CBAC firewall offers a range of essential features that contribute to its effectiveness. These include intelligent packet inspection, stateful packet filtering, protocol-specific application inspection, and granular access control policies.
One of the primary objectives of CBAC firewalls is to enhance network security. By actively analyzing traffic flow context, they can detect and prevent various threats, such as Denial-of-Service (DoS) attacks, port scanning, and protocol anomalies.
Stateful Firewall
A stateful firewall is a form of firewall technology that monitors incoming and outgoing network traffic and keeps track of the state of each connection passing through it. It acts as a filter, allowing or denying traffic based on configuration. Stateful firewalls are commonly used to protect private networks from potential malicious activity.
The primary function of a Stateful Inspection Firewall is to inspect the headers and contents of packets passing through it. It maintains a state table that keeps track of the connection state of each packet, allowing it to identify and evaluate the legitimacy of incoming and outgoing traffic. This stateful approach enables the firewall to differentiate between legitimate packets from established connections and potentially malicious packets.
Unlike traditional packet filtering firewalls, which only examine individual packets based on predefined rules, Stateful Inspection Firewalls analyze the entire communication session. This means that they can inspect packets in the context of the whole session, allowing them to detect and prevent various types of attacks, including TCP/IP-based attacks, port scanning, and unauthorized access attempts.
**What is state and context?**
A process or application’s current state refers to its most recent or immediate state. It is possible to compare the connection a user tries to establish with the list of connections stored in a firewall. A tracking device determines which states are safe and which pose a threat.
Analyzing IP addresses, packets, or other kinds of data can identify repeating patterns. In the context of a connection, for instance, it is possible to examine the contents of data packets that enter the network through a stateful firewall. Stateful firewalls can block future packets containing unsafe data.
Stateful Inspection:
A: Stateful packet inspection determines which packets are allowed through a firewall. This method examines data packets and compares them to packets that have already passed through the firewall.
B: Stateful packet filtering ensures that all connections on a network are legitimate. Static packet filtering on the network also examines network connections, but only as they arrive, focusing on packet header data. The firewall can only see where the data comes from and where it is going with this data.
C: Generally, we interact directly with the application layer and have networking and security devices working at the lower layers. So when host A wants to talk to host b, it will go through several communication layers with devices working at each layer. A device that works at one of these layers is a stateful firewall that can perform the stateful inspection.
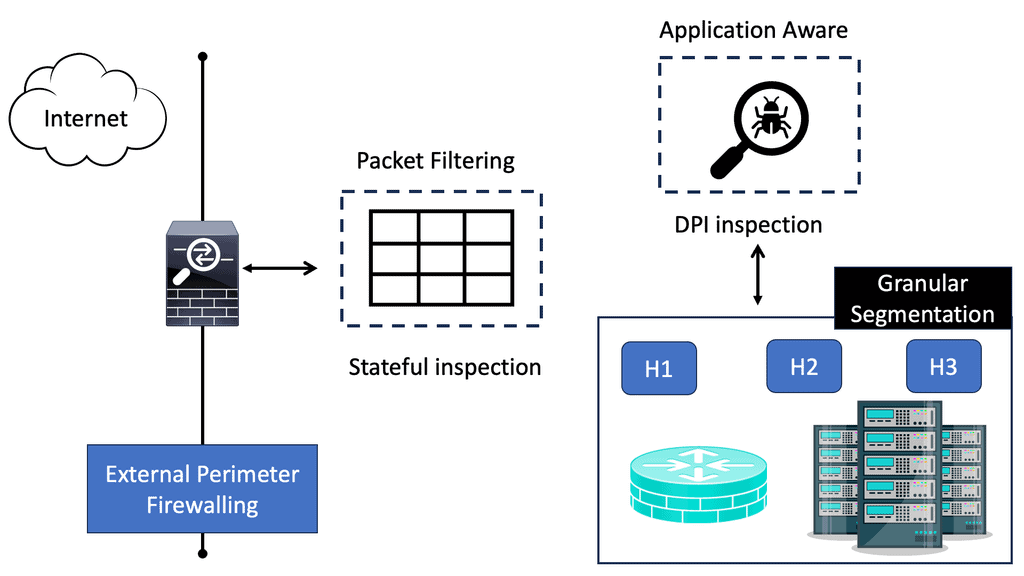
**Deep Packet Inspection (DPI)**
Another significant advantage of Stateful Inspection Firewalls is their ability to perform deep packet inspection. This means that they can analyze the content of packets beyond their headers. By examining the payload of packets, Stateful Inspection Firewalls can detect and block potentially harmful content, such as malware, viruses, and suspicious file attachments. This advanced inspection capability adds an extra layer of security to the network.
Understanding Deep Packet Inspection:
Deep Packet Inspection, often abbreviated as DPI, is a sophisticated technology used to monitor and analyze network traffic at a granular level. Unlike traditional packet inspection, which only examines packet headers, DPI delves deep into the packet payload, allowing for in-depth analysis and classification of network traffic.
DPI plays a vital role in network management and security. By inspecting the contents of packets, it helps network administrators identify and control applications, protocols, and even specific users. This level of visibility allows for better bandwidth management, traffic shaping, and the implementation of security measures to protect against malicious activities and intrusions.
**Applications of DPI**
1. Network Security: DPI enables the detection of malicious activities such as intrusions, malware, and unauthorized access attempts. It helps in identifying and preventing data breaches by monitoring and analyzing network traffic patterns in real-time.
2. Quality of Service (QoS): DPI helps network administrators prioritize and allocate network resources based on specific applications or services. By understanding the nature of traffic passing through the network, DPI can optimize bandwidth allocation, ensuring a seamless and reliable user experience.
3. Regulatory Compliance: In certain industries, such as finance or healthcare, strict regulations govern data privacy and security. DPI assists organizations in meeting compliance requirements by monitoring and controlling network traffic.
They can be combined with other security measures, such as antivirus software and intrusion detection systems. Stateful firewalls can be configured to be both restrictive and permissive and can be used to allow or deny certain types of traffic, such as web traffic, email traffic, or FTP traffic. They can also control access to web servers, databases, or mail servers. Additionally, stateful firewalls can detect and block malicious traffic, such as files, viruses, or port scans.
Transport Control Protocol (TCP):
TCP allows data to be sent and received simultaneously over the Internet. Besides assisting in transmitting information, TCP also contains data that can cause a connection to be reset (RST), resulting in its termination. TCP uses the FIN (finish) command when the transmission should end. When data packets reach their destination, they are grouped into understandable data.
Stateful firewalls examine packets created by the TCP process to keep track of connections. To detect potential threats, a stateful inspection firewall uses the three stages of a TCP connection: synchronize (SYN), synchronize-acknowledge (SYN-ACK), and acknowledge (ACK). During the TCP handshake, stateful firewalls can discard data if they detect bad actors.
Three-way handshake:
During the three-way handshake, both sides synchronize to establish a connection and then acknowledge one another. Each side transmits information to the other as part of this process, which is inspected for errors. In a stateful firewall, the data sent during the handshake can be examined to determine the packet’s source, destination, sequence, and content. The firewall can reject data packets if it detects threats.
Firewall Inspection with Cloud Armor
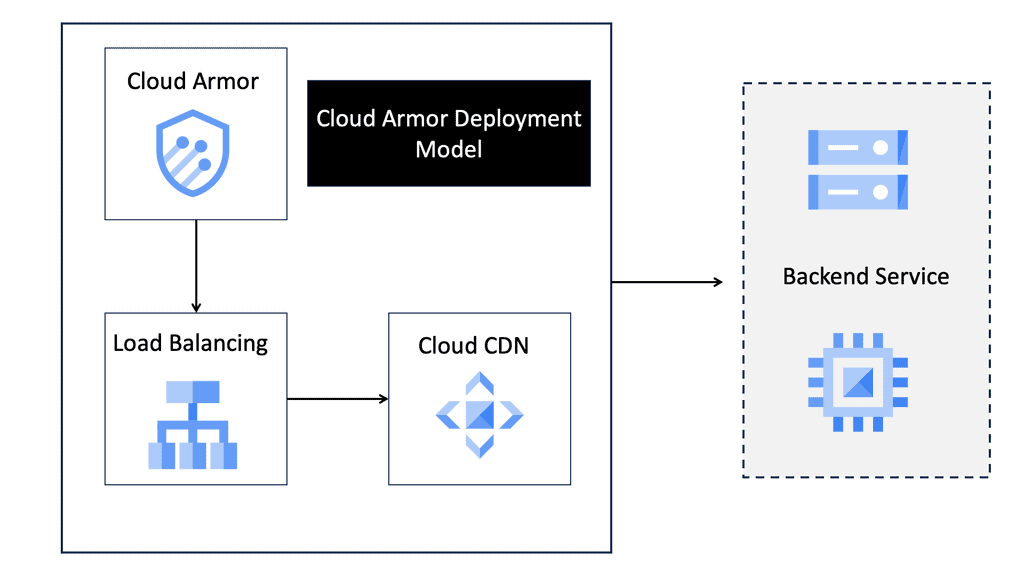
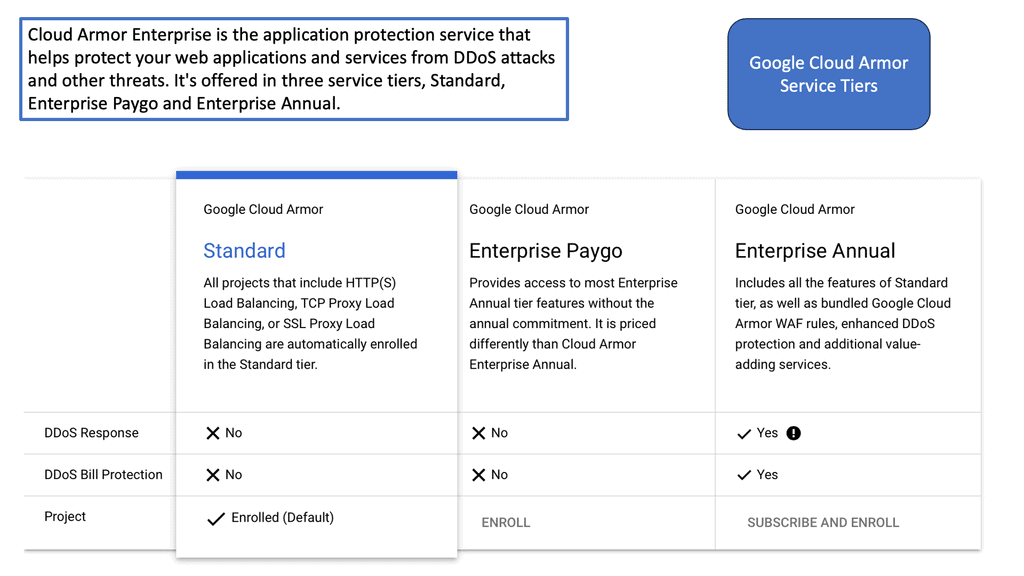
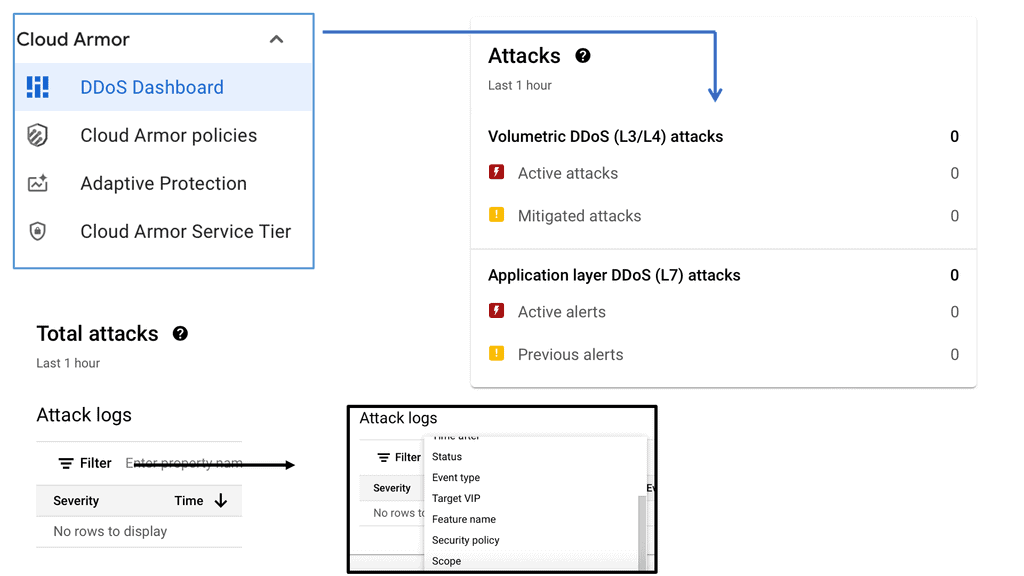
**What is Google Cloud Armor?**
Google Cloud Armor is a cloud-based security service that provides robust protection for web applications hosted on Google Cloud Platform (GCP). It acts as a shield against distributed denial-of-service (DDoS) attacks, SQL injections, cross-site scripting (XSS), and other common threats. With its global reach and scale, Google Cloud Armor helps ensure your applications remain available and secure, even in the face of sophisticated attacks.
**Delving into Stateful Inspection**
Stateful inspection is a critical component of Google Cloud Armor’s security framework. Unlike traditional packet filtering, which inspects packets individually, stateful inspection monitors the entire state of active connections. This means that Google Cloud Armor can track and analyze the context of data packets as they flow through your network, providing a more comprehensive layer of security. By understanding the state and characteristics of each connection, stateful inspection helps effectively distinguish between legitimate traffic and potential threats.
**The Benefits of Stateful Inspection**
The inclusion of stateful inspection within Google Cloud Armor offers several key benefits. First and foremost, it enhances threat detection and mitigation capabilities by allowing for a more granular analysis of network traffic. This means your applications are better protected against sophisticated attacks that might otherwise slip through less comprehensive security measures. Additionally, stateful inspection helps optimize performance by ensuring that only legitimate traffic is processed, reducing the risk of false positives and minimizing latency.
**Implementing Google Cloud Armor with Stateful Inspection**
Setting up Google Cloud Armor with stateful inspection is a straightforward process. First, ensure your applications are hosted on GCP, as this is a prerequisite for using Google Cloud Armor. Next, configure security policies that align with your specific needs and threat landscape. These policies will dictate how stateful inspection is applied, allowing you to tailor the level of scrutiny to your organization’s requirements. Finally, monitor and adjust your settings as necessary to ensure optimal protection and performance.
Google Cloud Compute Security
Google Compute Security
Google Compute Engine allows businesses to leverage the cloud for scalable and flexible computing resources. However, with this convenience comes the need for stringent security measures. Cyberattacks and data breaches pose a significant risk, making it crucial to implement robust security protocols to safeguard your Google Compute resources.
FortiGate is a comprehensive network security platform that offers advanced threat protection, secure connectivity, and granular visibility into your network traffic. With its cutting-edge features, FortiGate acts as a shield, defending your Google Compute resources from malicious activities, unauthorized access, and potential vulnerabilities.
Advanced Threat Protection: FortiGate leverages industry-leading security technologies to identify and mitigate advanced threats, including malware, viruses, and zero-day attacks. Its robust security fabric provides real-time threat intelligence and proactive defense against evolving cyber threats.
Secure Connectivity: FortiGate ensures secure connectivity between your Google Compute resources and external networks. It offers secure VPN tunnels, encrypted communication channels, and robust access controls, enabling you to establish trusted connections while preventing unauthorized access.
Granular Visibility and Control: With FortiGate, you gain granular visibility into your network traffic, allowing you to monitor and control data flows within your Google Compute environment. Its intuitive dashboard provides comprehensive insights, enabling you to detect anomalies, identify potential vulnerabilities, and take proactive security measures.
The Benefits of Deep Packet Inspection with FortiGate
Enhanced Network Visibility: By leveraging DPI with FortiGate, organizations gain unparalleled visibility into their network traffic. Detailed insights into application usage, user behavior, and potential security vulnerabilities allow for proactive threat mitigation and network optimization.
Granular Application Control: DPI enables organizations to enforce granular application control policies. By identifying and classifying applications within network traffic, FortiGate allows administrators to define and enforce policies that govern application usage, ensuring optimal network performance and security.
Intrusion Detection and Prevention: With DPI, FortiGate can detect and prevent intrusions in real-time. By analyzing packet content and comparing it against known threat signatures and behavioral patterns, FortiGate can swiftly identify and neutralize potential security breaches, safeguarding sensitive data and network infrastructure.
Before you proceed, you may find the following helpful post for pre-information:
Stateful Inspection Firewall
The term “Firewall.”
The term “firewall” comes from a building and automotive construction concept of a wall built to prevent the spread of fire from one area into another. This concept was then taken into the world of network security. The firewall’s assignment is to set all restrictions and boundaries described in the security policy on all network traffic that passes the firewall interfaces. Then, we have the concept of firewall filtering that compares each packet received to a set of rules that the firewall administration configures.
These exception rules are derived from the organization’s security policy. The firewall filtering rules state that the contents of the packet are either allowed or denied. Therefore, based on firewall traffic flow, the packet continues to its destination if it matches an allowed rule. If it matches a deny rule, the packet is dropped. The firewall is the barrier between a trusted and untrusted network, often used between your LAN and WAN. It’s typically placed in the forwarding path so that all packets have to be checked by the firewall, where we can drop or permit them.
Apply a multi-layer approach to security.
When it comes to network security, organizations must adopt a multi-layered approach. While Stateful Inspection Firewalls provide essential protection, they should be used in conjunction with other security technologies, such as intrusion detection systems (IDS), intrusion prevention systems (IPS), and virtual private networks (VPNs). This combination of security measures ensures comprehensive protection against various cyber threats.
Stateful Inspection Firewalls are integral to network security infrastructure. By inspecting packets in the context of the entire communication session, these firewalls offer enhanced security and greater control over network traffic. By leveraging advanced inspection techniques, deep packet inspection, and a stateful approach, Stateful Inspection Firewalls provide a robust defense against evolving cyber threats. Organizations prioritizing network security should consider implementing Stateful Inspection Firewalls as part of their security strategy.
Guide on Cisco ASA firewall
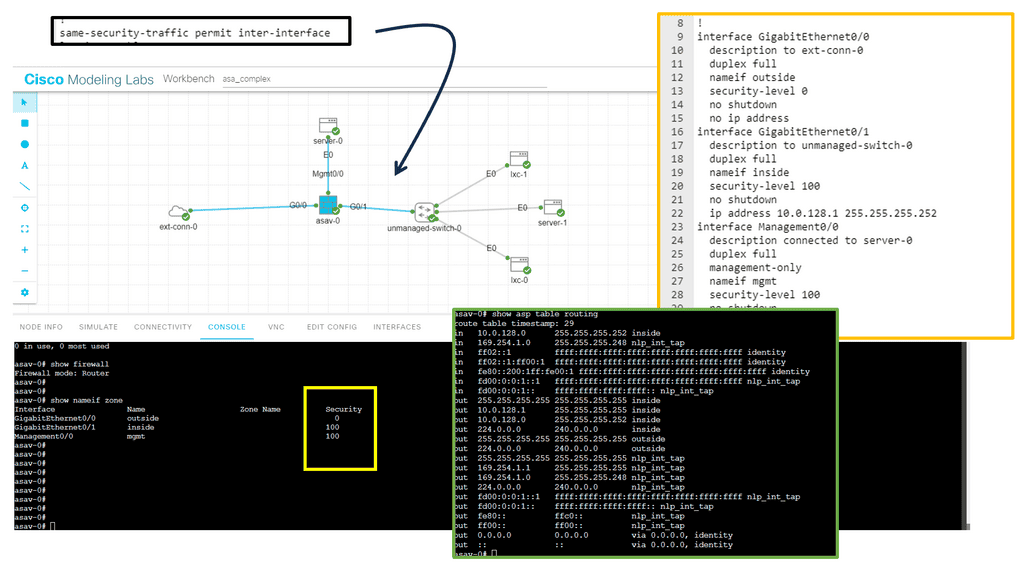
In the following lab guide, you can see we have an ASA working in routed mode. In routed mode, the ASA is considered a router hop in the network. Each interface that you want to route between is on a different subnet. You can share Layer 3 interfaces between contexts.
Traditionally, a firewall is a routed hop and acts as a default gateway for hosts that connect to one of its screened subnets. On the other hand, a transparent firewall is a Layer 2 firewall that acts like a “bump in the wire” or a “stealth firewall” and is not seen as a router hop to connected devices. However, like any other firewall, access control between interfaces is controlled, and the usual firewall checks are in place.
The Adaptive Security Algorithm considers the state of a packet when deciding to permit or deny the traffic. One enforced parameter for the flow is that traffic enters and exits the same interface. The ASA drops any traffic for an existing flow that enters a different interface. Traffic zones let you group multiple interfaces so that traffic entering or exiting any interface in the zone fulfills the Adaptive Security Algorithm security checks.
The command: show asp table routing displays the accelerated security path tables for debugging purposes and the zone associated with each route. See the following output for the show asp table routing command:
**Firewall filtering rules**
Firewall filtering rules help secure a network from unauthorized access and malicious activity. These rules protect the network by controlling traffic flow in and out of the network. Firewall filtering rules can allow or deny traffic based on source and destination IP addresses, ports, and protocols.
Firewall filtering rules should be tailored to the specific needs of a given network. Generally, it is recommended to implement a “deny all” rule and then add rules to allow only the necessary traffic. This helps block any malicious activity while allowing legitimate traffic. When creating firewall filtering rules, it is essential to consider the following:
- Make sure to use the most up-to-date protocols and ports.
- Be aware of any potential risks associated with the traffic being allowed.
- Use logging to monitor traffic and ensure that expected behavior is occurring.
- Ensure that the rules are implemented consistently across all firewalls.
- Ensure that the rules are regularly reviewed and updated as needed.
Guide on default firewall inspection
The Cisco ASA Firewall uses so-called “security levels” that indicate how trusted an interface is compared to another. The higher the security level, the more trusted the interface is. Each interface on the ASA is a security zone, so using these security levels gives us different trust levels for our security zones. Therefore, we have the default firewall inspection. We will discuss this more later.
Below, we have three routers and subnets with 1 ASA firewall.
- Interface G0/0 as the INSIDE.
- Interface G0/1 as the OUTSIDE.
- Interface G0/2 as our DMZ.
The name command is used to specify a name for the interface. As you can see, the ASA recognizes INSIDE, OUTSIDE, and DMZ names. And sets the security level for that interface to a default level. Therefore, restriction of traffic flow.
Remember that the ASA can reach any device in each security zone. This doesn’t work since we are trying to go from a security level of 0 (outside) to 100 (inside) or 50 (DMZ). We will have to use an access list if you want to allow this traffic.
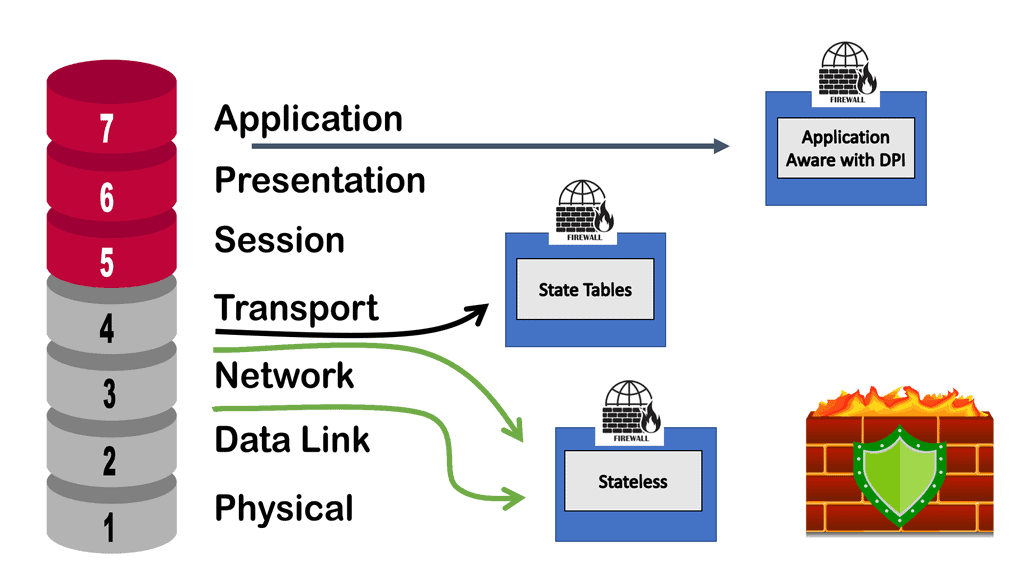
What Is a Stateful Firewall?
The stateful firewall examines Layer 4 headers and above, analyzing firewall traffic flow and enabling support for Application-aware inspections. Stateful inspection keeps track of every connection passing through their interfaces by analyzing packet headers and additional payload information.
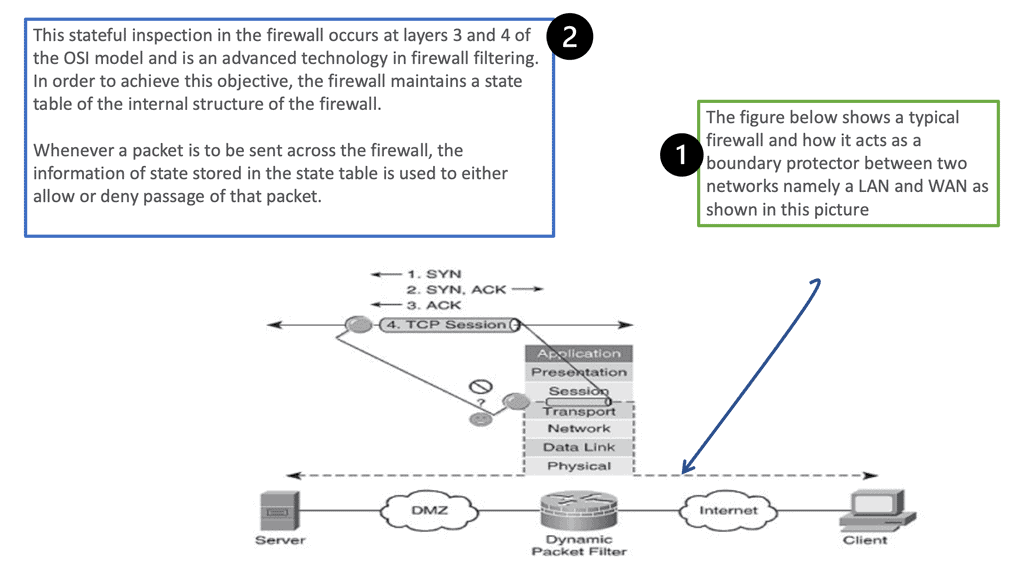
Stateful Firewall Operation
You can see how filtering occurs at layers 3 and 4 and that the packets are examined as a part of the TCP session.
The topmost part of the diagram shows the three-way handshake, which takes place before the commencement of the session and is explained as follows.
- Syn refers to the initial synchronization packet sent from one host to another; in this case, the client to the server.
- The server sends an acknowledgment of the syn, and this is known as syn-ack
- The client again acknowledges this syn-ack, completing the process and initiating the TCP session.
- Both parties can end the connection anytime by sending a FIN to the other side. This is similar to a telephone call where the caller or the receiver could hang up.
State and Context.
The two important terms to understand are state and context information. Filtering is based on the state and context information the firewall derives from a session’s packets. The firewall will store state information in its state table, which is updated regularly. For example, in TCP, this state is reflected in specific flags such as SYN, ACK, and FIN. Then, we have the context. This includes source and destination port, IP address, and sequence numbers of any metadata. The firewall also stores this information and updates regularly based on traffic flowing through the firewall.
Firewall state table
A firewall state table is a data structure that stores information about a network firewall’s connection state. It determines which packets are allowed to pass through the firewall and which are blocked. The table contains entries for each connection, including source and destination IP addresses, port numbers, and other related information.
The firewall state table is typically organized into columns, with each row representing an individual connection. Each row contains the source and destination IP address, the port numbers, and other related information.
For example, the source IP address and port number indicate the origin of the connection, while the destination IP address and port number indicate the destination of the connection. Additionally, the connection’s state is stored in the table, such as whether the connection is established, closed, or in transit.
The state table also includes other fields that help the firewall understand how to handle the connection, such as the connection duration, the type of connection being established, and the protocol used.
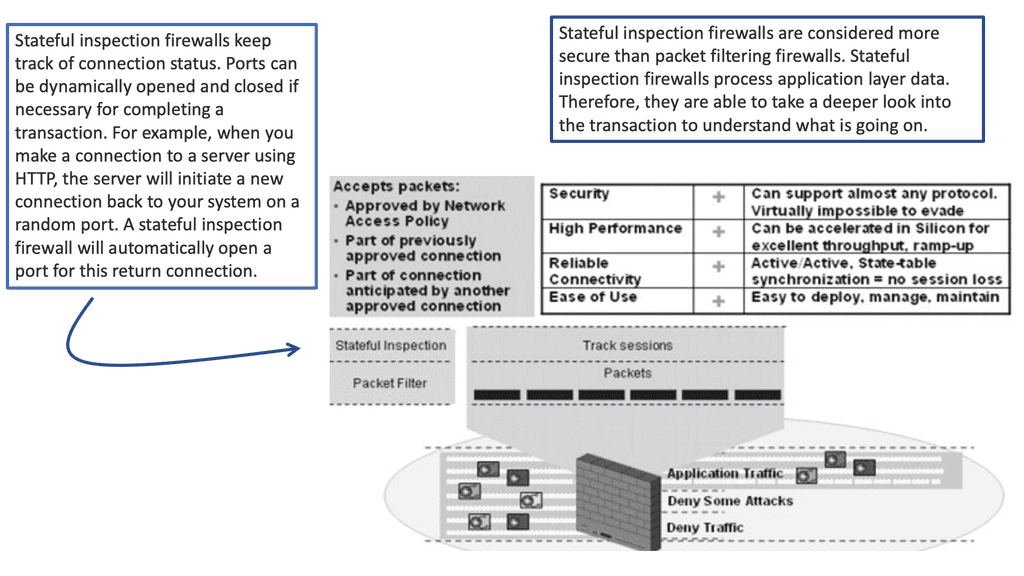
So whenever a packet arrives at a firewall to seek permission to pass through it, the firewall checks from its state table if there is an active connection between the two points of source and destination of that packet. The endpoints are identified by something known as sockets. A socket is similar to an electrical socket at your home, which you use to plug your appliances into the wall.
Similarly, a network socket consists of a unique IP address and a port number and is used to plug one network device into the other. The packet flags are matched against the state of the connection to which it belongs, which is allowed or denied based on that. For example, if a connection already exists and the packet is a Syn packet, it must be rejected since Syn is only required initially.
CBAC Firewalling on Cisco IOS
Understanding CBAC Firewall
CBAC firewall, also known as stateful firewall, is a robust security mechanism developed by Cisco Systems. Unlike traditional packet-filtering firewalls, the CBAC firewall adds layer of intelligence by examining the context of network connections. It analyzes individual packets and the entire session, providing enhanced security against advanced threats.
CBAC firewall offers a range of powerful features, making it a preferred choice for network administrators. First, it provides application-layer gateway functionality, which allows it to inspect and control traffic at the application layer. Second, the CBAC firewall can dynamically create temporary access rules based on a connection’s state. This adaptability ensures that only valid and authorized traffic is allowed through the firewall.
Compared to simple access lists, CBAC (Context-Based Access Control) offers some more features. CBAC can inspect up to layer 7 of the OSI model, and dynamic rules can be created to allow return traffic. Reflexive access lists are similar to this, but the reflexive ACL inspects only layers up to 4.
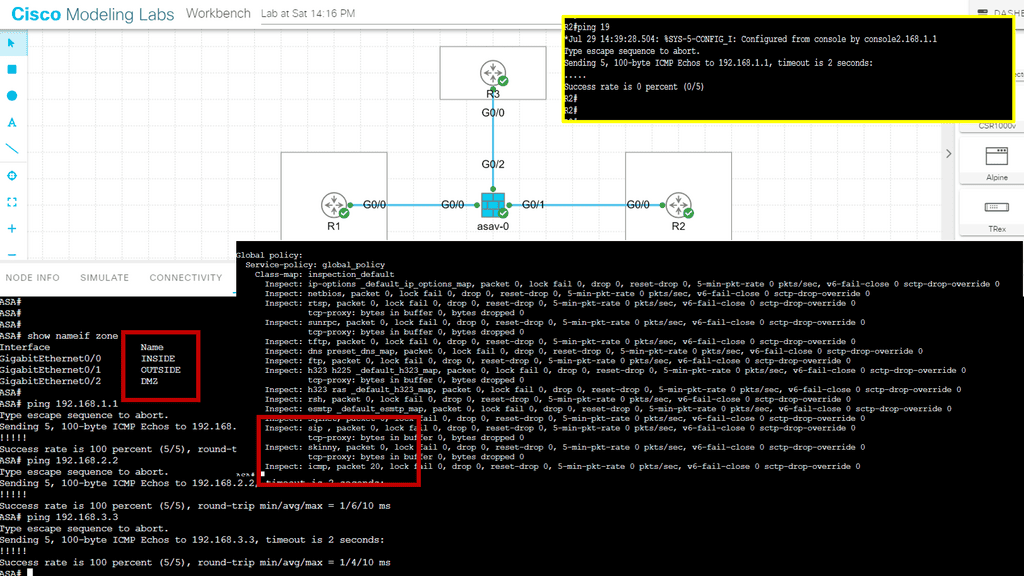
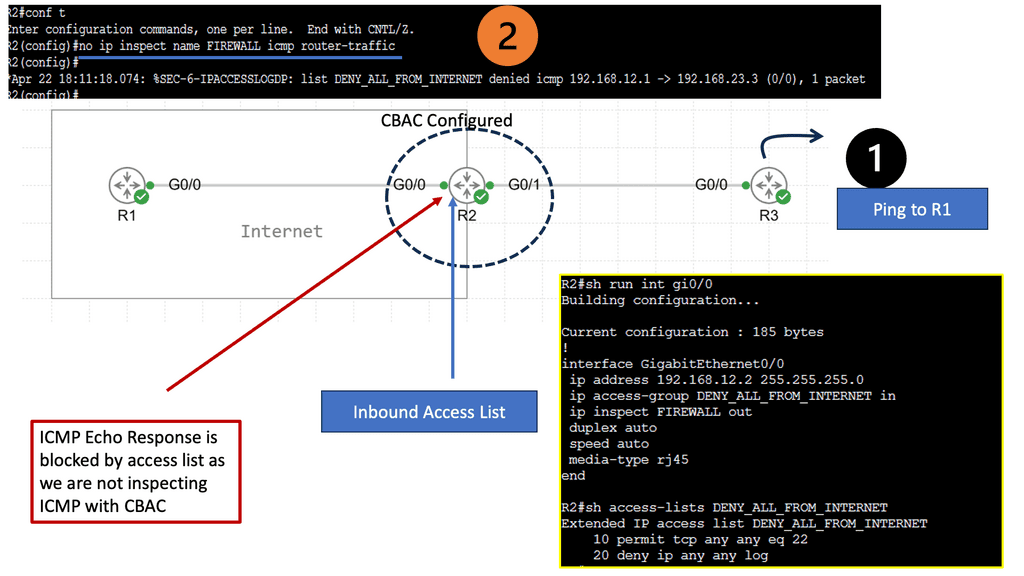
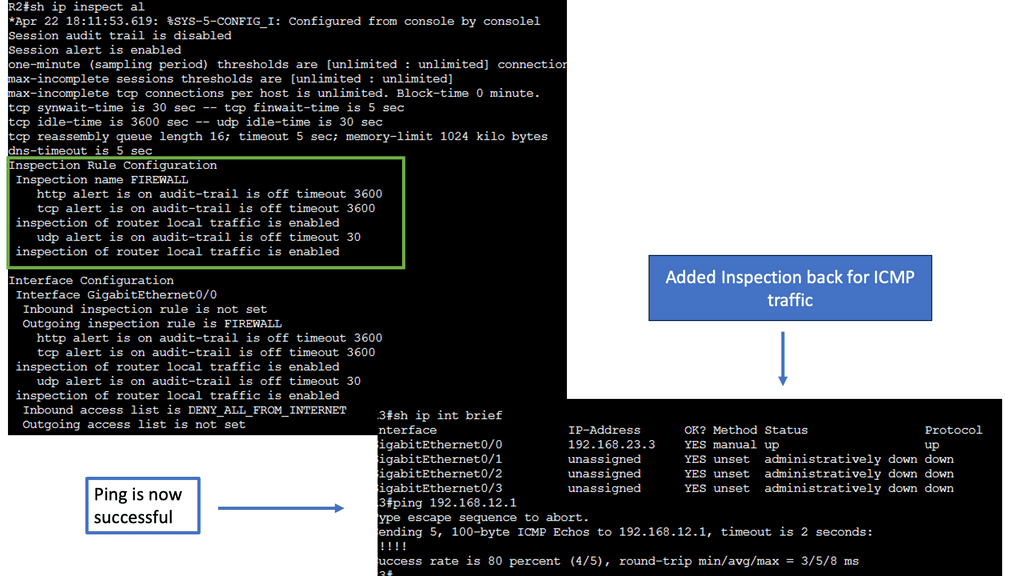
CBAC will be demonstrated in this lab, and you’ll see why this firewall feature is helpful. For this, I will use three routers: In the example above, we have three routers. Please assume that the router on the left (R1) is a device on the Internet, while the host on the right (R3) is a device on our local area network (LAN). We will configure CBAC on R2, the router that protects us from Internet traffic.
These pings are failing, as you can see on the console. The inbound ACL drops these packets on R2. To solve this problem, we must add a permit statement to the access list so the ping makes it through. That’s not a scalable solution since we don’t know what kind of traffic we have on our LAN, and we don’t want a big access list with hundreds of permit statements. What we are going to do is configure CBAC so it will inspect the traffic and automatically allow the return traffic through
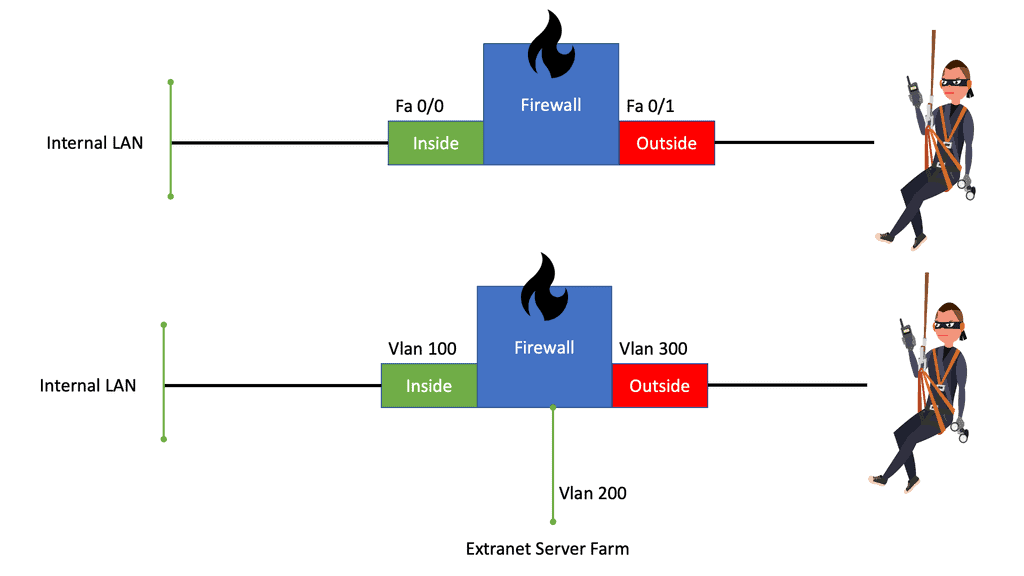
Stateful Firewall and Interface Configuration
It would be best to consider the interfaces in firewall terms when considering a stateful inspection firewall. For example, some interfaces are connected to protected networks, where data or services must be secured. Others connect to public or unprotected networks, where untrusted users and resources are located.
The top portion of the diagram below shows a stateful firewall with only two interfaces connecting to the inside (more secure) and outside (less secure) networks. The bottom portion shows the stateful inspection firewall with three interfaces connecting to the inside (most secure), DMZ (less secure), and outside (least secure) networks. The firewall has no concept of these interface designations or security levels; these concepts are put into play by the inspection processes and policies configured.
So you need to explain to the firewall which interface is at what security level. And this will effect the firewall traffic flow. Some traffic will be denied by default between specific interfaces with default security levels.
Interface configuration specific to ASA
Since version 7.0 of the ASA code, configuring interfaces in the firewall appliance is very similar to configuring interfaces in IOS-based platforms. If the firewall connection to the switch is an 802.1q trunk (the ASA supports 802.1q only, not ISL), you can create sub-interfaces corresponding to the VLANs carried over the trunk. Do not forget to assign a VLAN number to the sub-interface. The native (untagged) VLAN of the trunk connection maps to the physical interface and cannot be assigned to a sub-interface.
Full state of active network connections
So, we know that the stateful firewall monitors the entire state of active network connections and constantly analyses the complete context of traffic and data packets. Then, we have the payload to consider. The payload is part of transmitted data, the intended message, headers, and metadata sent only to enable payload delivery.
Payloads offer transaction information, which can protect against some of the most advanced network attacks. For example, deep packet inspection configures the stateful firewall to deny specific Hypertext Transfer Protocol ( HTTP ) content types or specific File Transfer Protocol ( FTP ) commands, which may be used to penetrate networks.
Stateful inspection and Deep Packet Inspection (DPI)
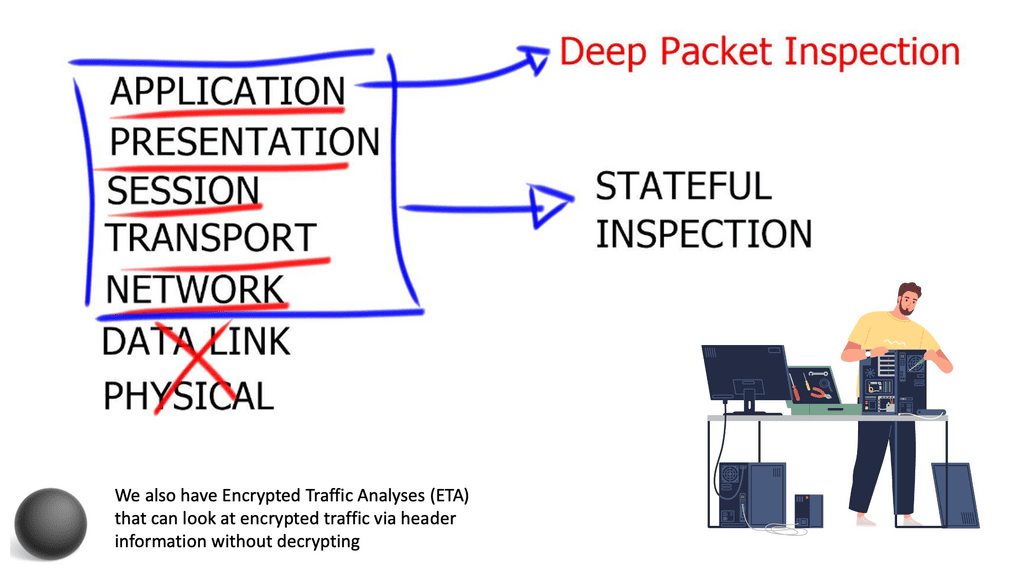
The following diagram shows the OSI layers involved in the stateful inspection. As you can see, Stateful inspection operates primarily at the transport and network layers of the Open Systems Interconnection (OSI) model for how applications communicate over a network. However, it can also examine application layer traffic, if only to a limited degree. Deep Packet Inspection (DPI) is higher up in the OSI layers.
DPI is considered to be more advanced than stateful packet filtering. It is a form of packet filtering that locates, identifies, classifies, and reroutes or blocks packets with specific data or code payloads that conventional packet filtering, which examines only packet headers, cannot detect. Many firewall vendors will have the stateful inspection and DPI on the same appliance. However, a required design may require a separate appliance for compliance or performance reasons.
Stateful Inspection Firewall
What is a stateful firewall?
A stateful firewall tracks and monitors the state of active network connections while analyzing incoming traffic and looking for potential traffic and data risks. The state is a process or application’s most recent or immediate status. In a firewall, the state of connections is stored, providing a list of connections against which to compare the connection a user is attempting to make.
Stateful packet inspection is a technology that stateful firewalls use to determine which packets are allowed through the firewall. It works by examining the contents of a data packet and then comparing them against data about packets that have previously passed through the firewall.
Stateful Firewall Feature | Stateful Firewall |
Better logging than standard packet filters | |
Protocols with dynamic ports | |
TCP SYN cookies | |
TCP session validation | |
No TCP fingerprinting | Not present |
Stateful firewall and packet filters
The stateful firewall contrasts packet filters that match individual packets based on their source/destination network addresses and transport-layer port numbers. Packet filters have no state or check the validity of transport layer sessions such as sequence numbers, Transmission Control Protocol ( TCP ) control flags, TCP acknowledgment, or fragmented packets. The critical advantage of packet filters is that they are fast and processed in hardware.
Reflexive access lists are closer to a stateful tool than packet filters. Whenever a TCP or User Datagram Protocol ( UDP ) session permits, matching return traffic is automatically added. The disadvantage of reflexive access lists is they cannot detect/drop malicious fragments or overlapping TCP segments. Transport layer session inspection goes beyond reflexive access lists and addresses fragment reassembly and transport-layer validation.
Application-level gateways ( ALG ) add additional awareness. They can deal with FTP or Session Initiation Protocol ( SIP ) applications that exchange IP addresses and port numbers in the application payload. These protocols operate by opening additional data sessions and multiple ports.
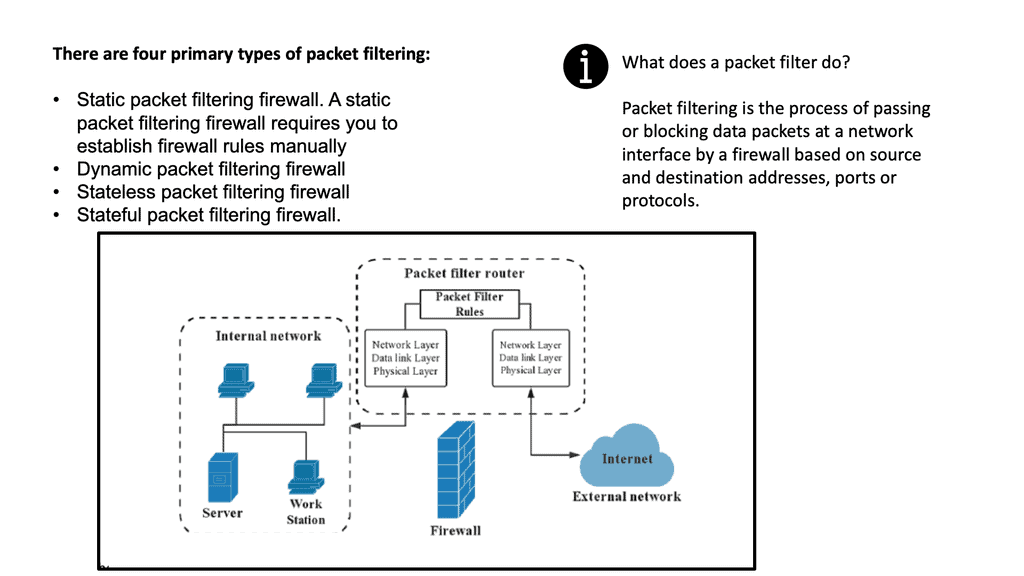
**Simple packet filters for a perfect world*8
In a perfect world where most traffic exits the data center, servers are managed with regular patching, servers listen on standard TCP or UDP ports, and designers could get away with simple packet filters. However, in the real world, each server is a distinct client, has multiple traffic flows to and from the data center and back-end systems, and unpredictable source TCP or UDP port number makes using packet filters impractical.
Instead, additional control should be implemented with deep packet inspection for unpredictable scenarios and poorly managed servers. Stateful firewalls keep state connections and allow traffic to return dynamically. Return traffic is permitted if the state of that flow is already in the connection table. The traffic needs to be part of a return flow. If not, it’s dropped.
**A stateless firewall – predefined rule sets**
A stateless firewall uses a predefined set of rules. If the arriving data packet conforms to the rules, it is considered “safe.” The data packet is allowed to pass through. With this approach to firewalling, traffic is classified instead of inspected. The process is less rigorous compared to what a stateful firewall does.
Remember that a stateless firewall does not differentiate between certain kinds of traffic, such as Secure Shell (SSH) versus File Transfer Protocol (FTP). A stateless firewall may classify these as “safe” and allow them to pass through, which can result in potential vulnerabilities.
A stateful firewall holds context across all its current sessions rather than treating each packet as an isolated entity, as with a stateless firewall. With stateless inspection, lookup functions impact the processor and memory resources much less, resulting in faster performance even if traffic is heavy.
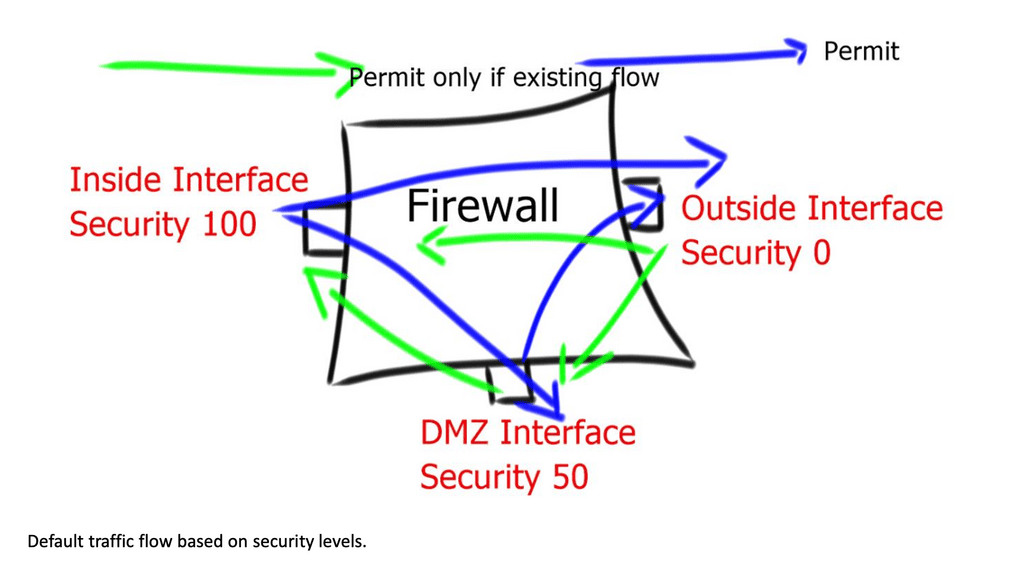
**The Stateful Firewall and Security Levels**
Regardless of the type of firewall mode or single or multiple contexts, the Adaptive Security Appliance ( ASA ) permits traffic based on a concept of security levels configured per interface. This is a crucial point to note for ASA failover and how you design your failover firewall strategy. The configurable range is from level 0 to 100. Every interface on ASA must have a security level.
The security level allows configured interface trust-ability and can range from 0, which is the lowest, to 100, which is the highest—offering ways to control traffic flow based on security level numbering. The default security level is “0”, configuring the name on the interface “inside” without explicitly entering a security level; then, the ASA automatically sets the security level to 100 ( highest ).
By default, based on the configured nameif, ASA assigns the following implicit security levels to interfaces:
- 100 to a nameif of inside.
- 0 to a nameif of outside.
- 0 to all other nameifs.
Without any configured access lists, ASA implicitly allows or restricts traffic flows based on the security levels:
Securty Levels and Traffic Flows
|
Firewall traffic flow between security levels
By default, traffic can flow from highest to lowest without explicit configuration. Also, interfaces on the same security level cannot directly communicate, and packets cannot enter and exit the same interface. Override the defaults, permit traffic by allowing high to low; explicitly configure ACLs on the interface or newer version use-global ACL. Global ACL affects all interfaces in all directions.
Firewall traffic flows
Inter-interface communication ( Routed Mode only ): Enter the command “same-security-traffic permit inter-interface” or permit traffic explicitly with an ACL. This will give design granularity and allow the configuration of more communicating interfaces. Intra-interface communication: This is configured for traffic hair-pining (traffic leaves on the outside interface and goes back out the outside interface ).
This is useful for Hub and Spoke VPN deployments; traffic enters an interface and routes back out the same interface—Spoke-to-Spoke communication. To enable Intra-Interface communication, enter the command “same-security-traffic permit intra-interface.”
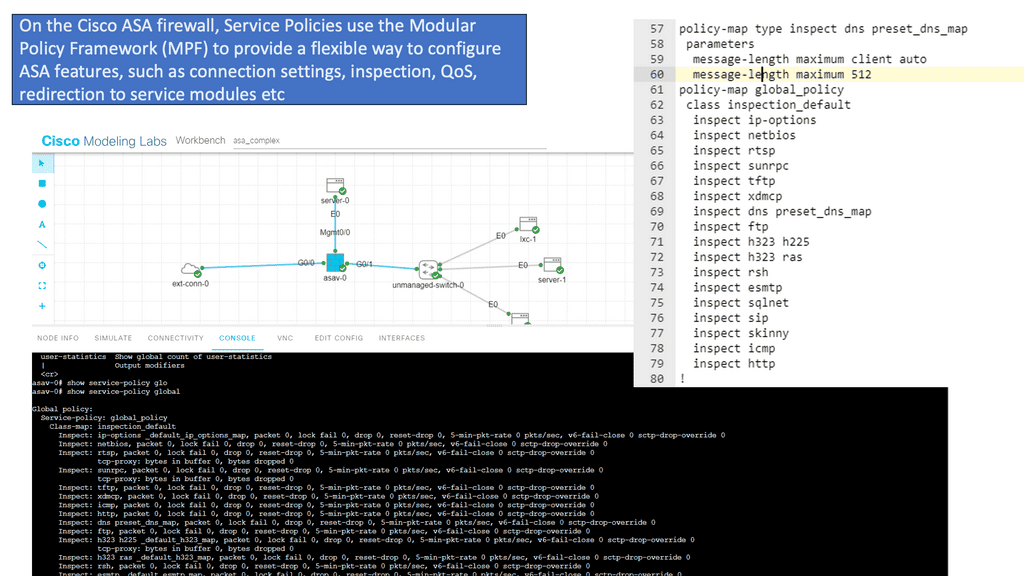
Default inspection and Modular Policy Framework ( MPF )
ASA implements what is known as the Modular Policy Framework ( MPF ). MPF controls WHAT traffic is inspected, such as Layer 3 or Layer 4 inspection of TCP, UDP, ICMP, an application-aware inspection of HTTP, or DNS. It also controls HOW traffic is inspected based on connection limits and QoS parameters.
ASA inspects TCP / UDP from the inside (higher-security level ) to the outside ( lower-security level ). This cannot be disabled. No traffic inspection from outside to inside unless it is from an original flow.
An entry is created in the state table, so when flows return, it checks the state table before it goes to implicit deny ACL. The state is created during traffic leaves, so it checks the specific connection and application data when the return flows come back. It does more than Layer 3 or 4 inspections and depends on the application.
It does not, by default, inspect ICMP traffic. Enable ICMP inspection with a global inspection policy or explicitly allow with an interface or Global ACLs. ASA global policy affects all interfaces in all directions. The state table is checked before any ACL. A good troubleshooting tool, Packet Tracer, goes through all inspections and displays the order the ASA is processing.
Key Stateful Inspection Firewall Summary Points: | Main Checklist Points To Consider
|
Firewalls and secure web gateways (SWGs) play similar and overlapping roles in securing your network. Both analyze incoming information and seek to identify threats before they enter your system. Despite sharing a similar function, they have some key differences, such as the “classical” distinction between secure web gateways and firewalls.
The basic distinctions:
- Firewalls inspect data packets
- Secure web gateways inspect applications
- Secure web gateways set and enforce rules for users
Guide on traffic flows and NAT
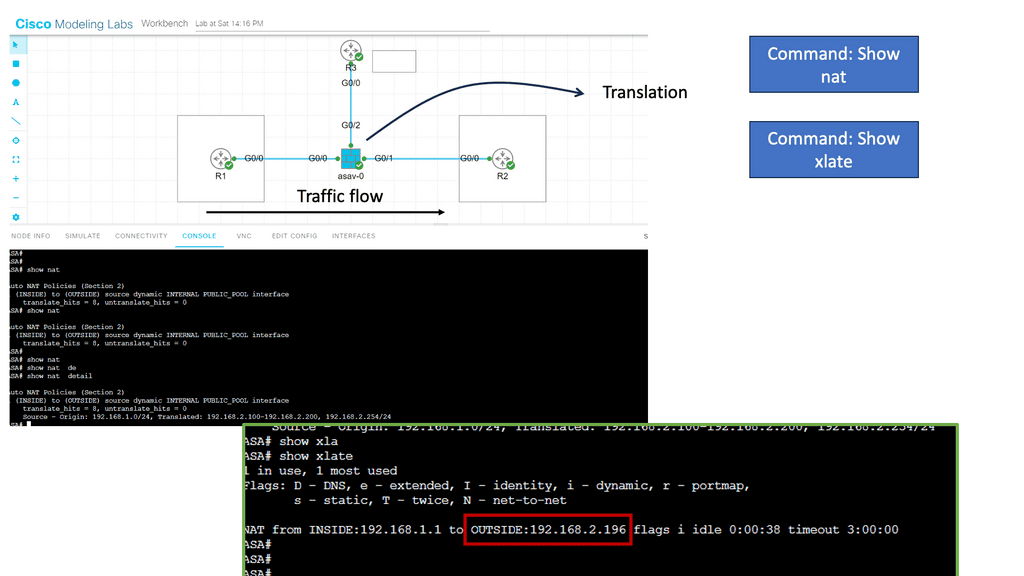
I have the Cisco ASA configured with Dynamic NAT in the following guide. This is the same setup as before. In the middle, we have our ASA; its G0/0 interface belongs to the inside, and the G0/1 interface belongs to the outside. I have not configured anything on the DMZ interfaces.
You need to configure object groups for this ASA version. I have configured a network object that defines the pool with public IP addresses we want to use for translation. The IP address that has been translated is marked in the red box below.
The show nat command shows us that some traffic has been translated from the inside to the outside.
The show xlate command shows that the IP address 192.168.1.1 has been translated to 192.168.2.196. It also tells us what kind of NAT we are doing here (dynamic NAT in our example) and how long this entry has been idle.
Summary: Stateful Inspection Firewall
In today’s interconnected world, where cyber threats are becoming increasingly sophisticated, ensuring the security of our networks is paramount. One effective tool in the arsenal of network security is the stateful inspection firewall. In this blog post, we delved into the inner workings of stateful inspection firewalls, exploring their features, benefits, and why they are essential in safeguarding your network.
Understanding Stateful Inspection Firewalls
Stateful inspection firewalls go beyond traditional packet filtering by actively monitoring the state of network connections. They keep track of the context and content of packets, making intelligent decisions based on the connection’s state. By examining the entire packet, including the source and destination addresses, ports, and sequence numbers, stateful inspection firewalls provide a higher security level than simple packet filtering.
Key Features and Functionality
Stateful inspection firewalls offer a range of essential features that enhance network security. These include:
1. Packet Filtering: Stateful inspection firewalls analyze packets based on predetermined rules, allowing or blocking traffic based on factors like source and destination IP addresses, ports, and protocol type.
2. Stateful Tracking: Maintaining connection state information allows stateful inspection firewalls to track ongoing network sessions. This ensures that only legitimate traffic is allowed, preventing unauthorized access.
3. Application Layer Inspection: Stateful inspection firewalls can inspect and analyze application-layer protocols, providing additional protection against attacks that exploit vulnerabilities in specific applications.
Benefits of Stateful Inspection Firewalls
Implementing a stateful inspection firewall offers several advantages for network security:
1. Enhanced Security: By actively monitoring network connections and analyzing packet contents, stateful inspection firewalls provide stronger protection against various types of cyber threats, such as network intrusions and denial-of-service attacks.
2. Improved Performance: Stateful inspection firewalls optimize network traffic by efficiently managing connection states and reducing unnecessary packet processing. This leads to smoother network performance and better resource utilization.
3. Flexibility and Scalability: Stateful inspection firewalls can be customized to meet specific security requirements, allowing administrators to define rules and policies based on their network’s unique characteristics. Additionally, they can handle high traffic volumes without sacrificing performance.
Considerations for Implementation
While stateful inspection firewalls offer robust security, it’s important to consider a few factors during implementation:
1. Rule Configuration: Appropriate firewall rules are crucial for effective protection. To ensure that the firewall is correctly configured, a thorough understanding of the network environment and potential threats is required.
2. Regular Updates: Like any security solution, stateful inspection firewalls require regular updates to stay effective. Ensuring up-to-date firmware and rule sets are essential for addressing emerging threats.
Conclusion:
Stateful inspection firewalls are a critical defense against cyber threats, providing comprehensive network protection through their advanced features and intelligent packet analysis. Implementing a stateful inspection firewall can fortify your network’s security, mitigating risks and safeguarding sensitive data. Stay one step ahead in the ever-evolving landscape of cybersecurity with the power of stateful inspection firewalls.
- DMVPN - May 20, 2023
- Computer Networking: Building a Strong Foundation for Success - April 7, 2023
- eBOOK – SASE Capabilities - April 6, 2023



Great article! Thanks for sharing.
Thank you!! Remember to come back 🙂