Virtual Device Context
In today's rapidly evolving technological landscape, virtual device context (VDC) has emerged as a powerful tool for network management and optimization. By providing virtualized network environments within a physical network infrastructure, VDC enables organizations to enhance flexibility, scalability, and security. In this blog post, we will explore the concept of VDC, its benefits, and its real-world applications.
Virtual device context, in essence, involves the partitioning of a physical network device into multiple logical devices. Each VDC operates independently and provides a dedicated set of resources, such as routing tables, VLANs, and interfaces. This segregation ensures that different network functions or departments can operate within their isolated environments, preventing interference and enhancing network performance.
Enhanced Flexibility: By leveraging VDC, organizations can dynamically allocate resources to different network segments based on their requirements. This flexibility allows for efficient resource utilization and the ability to respond to changing network demands swiftly.
Improved Scalability: VDC enables horizontal scaling by effectively dividing a single physical device into multiple logical instances. This scalability empowers organizations to expand their network capacity without the need for significant hardware investments.
Enhanced Security: Through VDC, organizations can establish isolated network environments, ensuring that sensitive data and critical network functions are protected from unauthorized access. This enhanced security posture minimizes the risk of data breaches and network vulnerabilities.
Data Centers: Modern data centers are complex ecosystems with diverse network requirements. VDC allows for the logical separation of various departments, applications, or tenants within a single data center infrastructure. This isolation ensures efficient resource allocation, optimized performance, and enhanced security.
Service Providers: Virtual device context finds extensive applications in service provider networks. By utilizing VDC, service providers can offer multi-tenant services to their customers while maintaining strict segregation between each tenant's network environment. This isolation provides enhanced security and allows for efficient resource allocation per customer.
Virtual device context has revolutionized network management by offering enhanced flexibility, scalability, and security. Its ability to partition a physical network device into multiple logical instances opens up new avenues for optimizing network infrastructure and meeting evolving business requirements. By embracing VDC, organizations can take a significant step towards building robust and future-ready networks.
Matt Conran
Highlights: Virtual Device Context
Virtual Device Contexts (VDC) let you carve out numerous virtual switches from a single physical Nexus switch. Each VDC is logically separated from every other VDC on a switch. Thus, just like physical switches to trunk or route traffic between them, physical interfaces and cabling are required to attach two or more VDCs before this can happen.
The number of VDCs that can be created depends upon the version of NX-OS, the Supervisor model, and the license installed. For example, the newer Supervisor 2E can support up to eight VDCs and one Admin VDC.
VDC utilizes the concept of virtualization to create isolated network environments within a single physical switch. By dividing the switch into multiple logical switches, network administrators can allocate resources, such as CPU, memory, and interfaces, to each VDC independently. This enables them to manage and control multiple networks within a single device with distinct configurations.
**Benefits of Virtual Device Context**
1. Enhanced Network Performance: With VDC, network administrators can allocate dedicated resources to each virtual device, ensuring optimal performance. By isolating traffic, VDC prevents any device from monopolizing network resources, improving overall network performance.
2. Increased Network Efficiency: VDC allows administrators to run multiple applications or services on separate virtual devices, eliminating potential conflicts. This segregation enhances network efficiency by minimizing downtime and enabling better resource utilization.
3. Simplified Network Management: By consolidating multiple logical devices into a single physical switch, VDC simplifies network management. Administrators can independently configure and monitor each VDC, reducing complexity and streamlining operations.
4. Cost Savings: Virtual Device Context eliminates the need to purchase and manage multiple physical switches, resulting in organization cost savings. By leveraging VDC, businesses can achieve network segmentation and isolation while optimizing resource utilization, thus reducing capital and operational expenditure.
**Use Cases of Virtual Device Context**
1. Data Centers: VDC is commonly used in data centers to create virtual networks for different departments or tenants, ensuring secure and isolated environments.
2. Service Providers: VDC enables providers to offer virtualized network services to their customers, providing greater flexibility and scalability.
3. Testing and Development Environments: VDC allows organizations to create virtual network environments for testing and development purposes, enabling efficient resource allocation and isolation.
Cisco NX-OS and VDC
Cisco NX-OS provides fault isolation, management isolation, address allocation isolation, service differentiation domains, and adaptive resource management through VDCs. An instance of a VDC can be managed independently within a physical device, and users connected to it perceive it as a unique device. VDCs run as logical entities within physical devices, maintain their configurations, run their software processes, and are managed by a different administrator.
Kernel and Infrastructure Layer
The Cisco NX-OS software is built on a kernel and infrastructure layer. On a physical device, the kernel supports all processes and virtual disks. These TCAMs serve as interfaces between higher-level processes and the hardware resources of the physical device. Scalability of Cisco NX-OS software can be achieved by avoiding duplication of systems management processes at this layer (see figure below).
It is also the infrastructure that enforces isolation across VDCs. When a fault occurs within a VDC, it does not impact services in other VDCs. Thus, software faults are limited, and device reliability is greatly enhanced.
Nonvirtualized services may have only one instance per VDC and the infrastructure layer. These services create VDCs, move resources between VDCs, and monitor protocol services within a VDC.
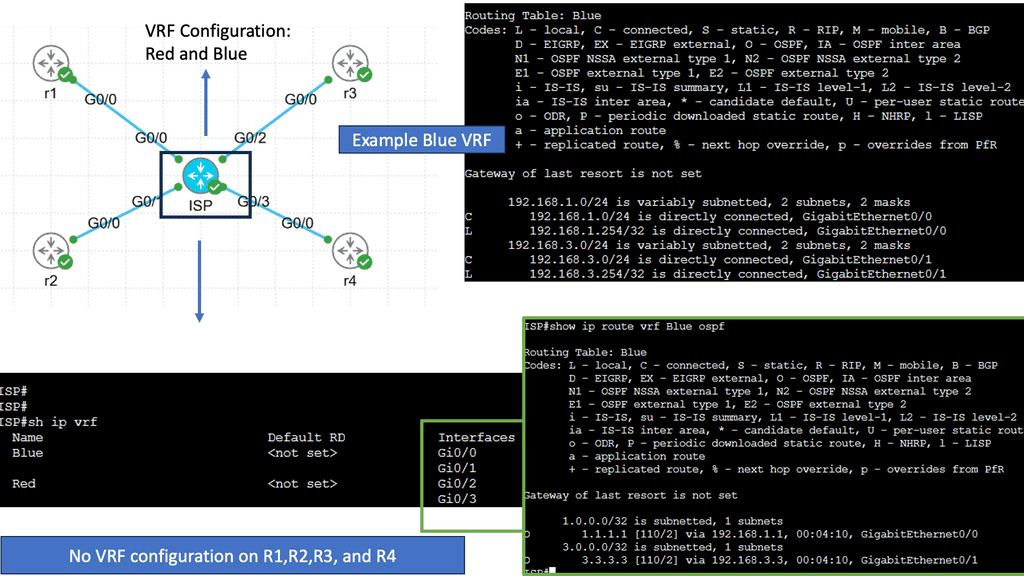
Example Segmentation Technology – VRF
Understanding VRF
VRF, at its core, separates the routing instances within a router, enabling the creation of isolated routing domains. Each VRF instance maintains its routing table, forwarding table, and associated network interfaces. This logical separation allows for the creation of multiple independent virtual networks within a physical infrastructure without the need for additional hardware.
One of the key advantages of VRF is its ability to provide network segmentation. By creating separate VRF instances, organizations can isolate different departments, customers, or applications within their network infrastructure. This isolation enhances security by preventing unauthorized access between virtual networks and enables fine-grained control over routing policies.
Use Cases for VRF
VRF finds wide application in various scenarios. In large enterprises, it can be used to segregate network traffic between different departments, ensuring efficient resource utilization and minimizing the risk of data breaches. Internet Service Providers (ISPs) leverage VRF to provide their customers virtual private network (VPN) services, enabling secure and private communication over shared infrastructure. VRF is also widely used in multi-tenant environments, such as data centers, allowing multiple customers to coexist on the same physical network infrastructure while maintaining isolation and security.
Example: Cisco Nexus Switches
Virtual Device Contexts (VDC) allow you to carve or divide out multiple virtual switches from a single physical Nexus switch. The number of VDCs that can be created depends upon the version of NX-OS, the Supervisor model, and the license installed.
Inter-VDC communication is only via external interfaces; there is no internal switch. As a result, VDCs offer several benefits, such as a separate partition between different groups or organizations while using only a single switch. With device context, there are several virtual device context design options.
Example: Cisco ASA 5500 Series
Multiple approaches exist for firewall and load-balancing services in the data path. Design options exist for a Dedicated External Chassis ( Catalyst 6500 VSS ) with service modules inserted within the chassis or using dedicated External Appliances ( Cisco ASA 5500 Series Next-Generation Firewall).
With both modes, run the services in either “routed” or “transparent” modes. Routed mode creates separate routing domains between the server farm subnet and the services layer. On the other hand, Transparent Mode extends the routing domain down to the server farm layer.
Before you proceed, you may find the following posts helpful:
Virtual Device Context
VDC Design
The virtual Device Context ( VDC ) feature on the Nexus 7000 series is used for another type of virtualization. The concept of VDC design takes a single Nexus 7000 series and divides it into independent devices. In this example, the second independent device creates an additional aggregation layer.
Now, the data center has two-aggregation layers, the Primary Aggregation layer and the Sub-Aggregation layer. The services layer is sandwiched between the two-aggregation VDC blocks ( primary and sub-aggregation layer ), creating a concept known as the “Virtual Device Context Sandwich Model.”
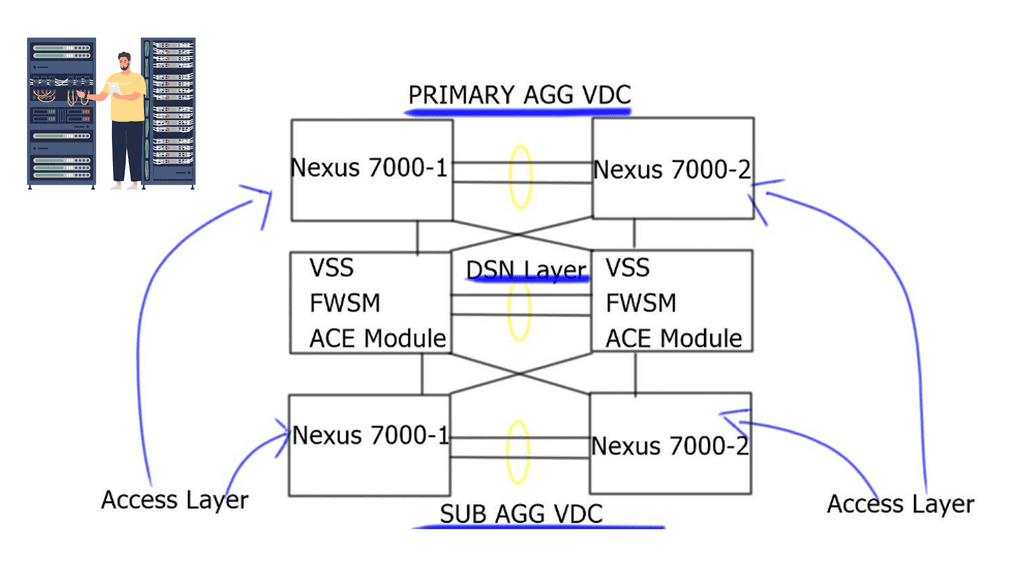
Now, there are two options for access layer connections. Some access layer switches can attach to the new sub-aggregation VDC. Other functional blocks not requiring services can be directly connected to the primary aggregation layer ( top VDC ), bypassing the service function. The central role of the primary aggregation layer is to provide Layer 3 forwarding from the services layer to the other functional blocks of the network. Small sites could collapse the core in the primary aggregation VDC.
Device context validated design.
The design is validated with the Firewall Service Module ( FWSM ) running in transparent mode and the ACE module running in routed mode. The two-aggregation layers are direct IP routing peers and configurations with VLANs, Virtual Routing and Forwarding ( VRFs ), Virtual Device Contexts ( VDC ), and Virtual Contexts. Within each VDC, VLANs map to VRFs, and VRFs can direct independent traffic through multiple virtual contexts on the service devices. If IP multicast is not required, the sub-aggregation VDC can have static pointing to a shared Hot Standby Router Protocol ( HSRP ) address on the primary aggregation VDC.
Benefits of VDCs
- Inserting separate aggregation layers using the VDC approach provides much better isolation than previous designs using VLAN and VRF on a single switch.
- It also offers much better security. Instead of separating VLANs and VRFs on the same switch, the VDC concept creates separate virtual switches with their physical ports.
- The sub-aggregation layer is separate from the primary aggregation layer. You need to connect them directly to route from one VDC to another. It’s as if they are separate physical devices.
Drawback of VDCs
- The service chassis must have separate physical interfaces to each VDC layer. Additional interfaces must be provisioned for the inter-switch link between VDCs. Compared to the traditional method that is extended by adding VLANs on a trunk port.
Closing Points on Virtual Device Context (VDC)
VDC technology enables the division of a physical switch into distinct virtual switches, each with its own set of resources and configurations. This partitioning is akin to server virtualization, where a single physical machine runs multiple virtual servers. In the context of VDC, each virtual switch can be managed separately, allowing administrators to tailor network policies, security settings, and access controls to specific needs without interfering with other virtual switches on the same hardware.
The adoption of VDC offers a myriad of benefits. Firstly, it enhances resource utilization by allowing a single switch to support multiple network environments, reducing the need for additional hardware. This not only lowers capital expenditure but also streamlines network management. Additionally, VDC promotes greater security and fault isolation. By segregating network environments, organizations can minimize the risk of cross-contamination and ensure that failures in one virtual switch do not impact others. This isolation is crucial in multitenant environments where different users or departments share the same physical infrastructure.
VDC technology is particularly beneficial in environments requiring high levels of customization and control. For instance, in data centers, VDC can be used to separate production, development, and testing environments, each with unique configurations and security protocols. Similarly, service providers can use VDC to offer tailored network solutions to clients, providing each with a dedicated virtual switch. This flexibility makes it possible to deliver personalized services while maintaining operational efficiency.
While VDC offers significant advantages, there are challenges to consider. Implementing VDC requires a deep understanding of network architecture and careful planning to ensure optimal configuration and performance. Administrators must also be mindful of resource allocation, as the physical limitations of the hardware can impact the number of VDCs that can be effectively supported. Additionally, ongoing management and monitoring are crucial to maintain the integrity and efficiency of the virtual environments.
Summary: Virtual Device Context
In this digital age, the concept of virtual device context has emerged as a revolutionary tool in technology. With its ability to enhance performance, improve security, and streamline operations, virtual device context has become a game-changer for many organizations. In this blog post, we delved into the intricacies of the virtual device context, its benefits, and how it transforms how we interact with technology.
Understanding Virtual Device Context
Virtual device context, often abbreviated as VDC, refers to the virtualization technique that allows partitioning a physical device into multiple logical devices. Each logical device, or virtual device context, operates independently with its dedicated resources, such as CPU, memory, and interfaces. This virtualization enables the consolidation of multiple devices into a single physical infrastructure, leading to significant cost savings and operational efficiency.
The Benefits of Virtual Device Context
Enhanced Performance:
Organizations can ensure optimal performance for their applications and services by isolating resources for each virtual device context. This isolation prevents resource contention and efficiently utilizes available resources, improving overall performance.
Improved Security:
Virtual device context provides a robust security framework by isolating network traffic and preventing unauthorized access between different contexts. This isolation reduces the attack surface and enhances the overall security posture of the network infrastructure.
Simplified Management:
Network administrators can manage multiple logical devices as separate physical devices in a virtual device context. This simplifies the management and configuration tasks, allowing for easier network infrastructure provisioning, monitoring, and troubleshooting.
Use Cases of Virtual Device Context
Data Centers:
Virtual device context finds extensive use in data centers, enabling the consolidation of network devices and simplifying the management of complex infrastructures. It allows for efficient resource allocation, seamless scalability, and improved agility in deploying new services.
Service Providers:
Service providers leverage virtual device context to offer multi-tenancy services to their customers. Service providers can ensure isolation, security, and customized service offerings by creating separate virtual device contexts for each customer.
Conclusion:
Virtual device context is a powerful technology that has transformed how we design, manage, and operate network infrastructures. Its benefits, including enhanced performance, improved security, and simplified management, make it a valuable tool for organizations across various industries. As technology continues to evolve, virtual device context will undoubtedly play a crucial role in shaping the future of networking.
- DMVPN - May 20, 2023
- Computer Networking: Building a Strong Foundation for Success - April 7, 2023
- eBOOK – SASE Capabilities - April 6, 2023