Virtual Firewalls
In cybersecurity, firewalls protect networks from unauthorized access and potential threats. Traditional firewalls have long been employed to safeguard organizations' digital assets. However, with the rise of virtualization technology, virtual firewalls have emerged as a powerful solution to meet the evolving security needs of the modern era. This blog post will delve into virtual firewalls, exploring their advantages and why they should be considered an integral part of any comprehensive cybersecurity strategy.
Virtual firewalls, or software firewalls, are software-based security solutions operating within a virtualized environment. Unlike traditional hardware firewalls, which are physical devices, virtual firewalls are implemented and managed at the software level. They are designed to protect virtual machines (VMs) and virtual networks by monitoring and controlling incoming and outgoing network traffic.
Virtual firewalls, also known as software firewalls, are security solutions designed to monitor and control network traffic within virtualized environments. Unlike traditional hardware firewalls, which operate at the network perimeter, virtual firewalls are deployed directly on virtual machines or within hypervisors. This positioning enables them to provide granular security policies and protect the internal network from threats that may originate within virtualized environments.
1. Segmentation: Virtual firewalls facilitate network segmentation by isolating virtual machines or groups of VMs, preventing lateral movement of threats within the virtual environment.
2. Intrusion Detection and Prevention: By analyzing network traffic, virtual firewalls can detect and prevent potential intrusions, helping organizations proactively defend against cyber threats.
3. Application Visibility and Control: With deep packet inspection capabilities, virtual firewalls provide organizations with comprehensive visibility into application-layer traffic, allowing them to enforce fine-grained policies and mitigate risks.
1. Enhanced Security: Virtual firewalls strengthen the overall security posture by augmenting traditional perimeter defenses, ensuring comprehensive protection within the virtualized environment.
2. Scalability and Flexibility: Virtual firewalls are highly scalable, allowing organizations to easily expand their virtual infrastructure while maintaining robust security measures. Additionally, they offer flexibility in terms of deployment options and configuration.
3. Centralized Management: Virtual firewalls can be managed centrally, simplifying administration and enabling consistent security policies across the virtualized environment.
1. Performance Impact: Virtual firewalls introduce additional processing overhead, which may impact network performance. It is essential to evaluate the performance implications and choose a solution that meets both security and performance requirements.
2. Integration with Existing Infrastructure: Organizations should assess the compatibility and integration capabilities of virtual firewalls with their existing virtualization platforms and network infrastructure.
Conclusion: Virtual firewalls have become indispensable tools in the fight against cyber threats, providing organizations with a robust layer of protection within virtualized environments. By leveraging their advanced features, such as segmentation, intrusion detection, and application control, businesses can fortify their digital fortresses and safeguard their critical assets. As the threat landscape continues to evolve, investing in virtual firewalls is a proactive step towards securing the future of your organization.
Matt Conran
Highlights: Virtual Firewalls
On-campus networks, mobile devices, and laptops are highly vulnerable to malware and ransomware, as well as to phishing, smishing, malicious websites, and infected applications. Thus, a solid network security design is essential to protect endpoints from such types of security threats and enforce endpoint network access control. End users can validate their identities before granting access to the network to determine who and what they can access.
Virtual firewalls, also known as cloud firewalls or virtualized NGFWs, grant or deny network access between untrusted zones. They provide inline network security and threat prevention in cloud-based environments, allowing security teams to gain visibility and control over cloud traffic. In addition to being highly scalable, virtual network firewalls are ideal for protecting virtualized environments because they are deployed in a virtualized form factor.
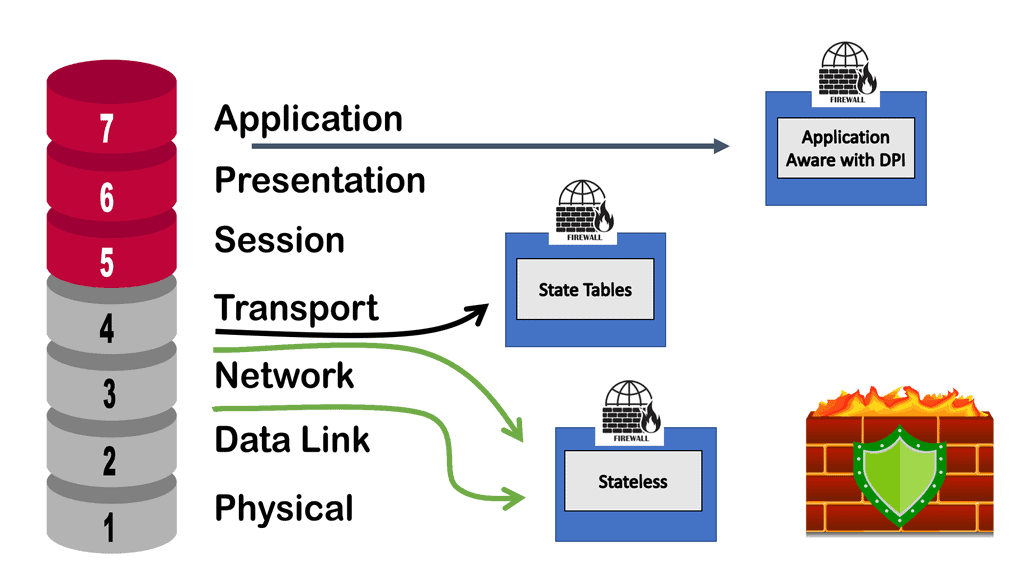
Because Layer 4 firewalls cannot detect attacks at the application layer, virtual firewalls are ideal for cloud service providers (CSPs). Virtual firewalls can determine if requests are allowed based on their content by examining applications and not just their port numbers. This feature can prevent DDoS attacks, HTTP floods, SQL injections, cross-site scripting attacks, parameter tampering attacks, and Slowloris attacks.
Network Security Components
This post discusses the network security components of virtual firewalls and the virtual firewall appliance that enables a zero-trust network design. In the Secure Access Service Edge (SASE ) world, virtual firewalling or any virtual device brings many advantages, such as having a stateful inspection firewall closer to the user sessions. Depending on the firewall design, the inspection and filtering are closer to the user’s sessions or workloads. Firstly, Let us start with the basics of IP networks and their operations.
Virtual SDN Data Centers
In a virtual data center design, IP networks deliver various services to consumers and businesses. As a result, they heavily rely on network availability for business continuity and productivity. As the reliance on IP networks grows, so does the threat and exposure to network-based attacks. New technologies and mechanisms address new requirements but also come with the risk of new threats. It’s a constant cat-and-mouse game. It’s your job as network admins to ensure the IP network and related services remain available.
For additional pre-information, you may find the following post helpful:
Virtual Firewall Appliance. Key Virtual Firewalls Discussion points: |
|
Back to Basics With the Virtual Firewall
The Firewall
The term “firewall” refers to a device or service that allows some traffic but denies other traffic. Positioning a firewall at a network gateway point in the network infrastructure is an aspect of secure design. A firewall so set at strategic points in the network intercepts and verifies all traffic crossing that gateway point. Some other places that firewalls are often deployed include in front of (i.e., on the public Internet side), behind (inside the data center), or in load-balancing systems.
Advantages of Virtual Firewalls:
1. Enhanced Flexibility: Virtual firewalls offer greater flexibility than their hardware counterparts. They are software-based and can be easily deployed, scaled, and managed in virtualized environments without additional hardware. This flexibility enables organizations to adapt to changing business requirements more effectively.
2. Cost-Effectiveness: Virtual firewalls eliminate the need to purchase and maintain physical hardware devices. Organizations can significantly reduce their capital and operational expenses by leveraging existing virtualization infrastructure. This cost-effectiveness makes virtual firewalls an attractive option for businesses of all sizes.
3. Centralized Management: Virtual firewalls can be centrally managed through a unified interface, providing administrators with a consolidated view of the entire virtualized network. This centralized management simplifies the configuration, monitoring, and enforcement of security policies across multiple virtual machines and networks, saving time and effort.
4. Segmentation and Isolation: Virtual firewalls enable organizations to segment their virtual networks into different security zones, isolating sensitive data and applications from potential threats. This segmentation ensures that the rest of the network remains protected even if one segment is compromised. By enforcing granular access control policies, virtual firewalls add a layer of security to prevent lateral movement within the virtualized environment.
5. Scalability: Virtual firewalls are software-based and can be easily scaled up or down to accommodate changing network demands. This scalability allows organizations to expand their virtual infrastructure without investing in additional physical hardware. With virtual firewalls, businesses can ensure that their security solutions grow with their evolving needs.
Traffic Types and Virtual Firewalls
Firstly, a thorough understanding of the traffic types that enter and leave the network is critical. Network devices process some packets differently from others, resulting in different security implications. Transit IP packets, receive-adjacency IP packets, exception, and non-IP packets are all handled differently.
You also need to keep track of the plethora of security attacks, such as resource exhaustion attacks (direct attacks, transit attacks, reflection attacks), spoofing attacks, transport protocol attacks (UDP & TCP), and routing protocol/control plane attacks.
Various attacks target Layer 2, including MAC spoofing, STP, and CAM table overflow. Overlay virtual networking introduces two control planes, both of which require protection.
The introduction of cloud and workload mobility is changing the network landscape and security paradigm. Workload fluidity and the movement of network states are putting pressure on traditional physical security devices. It isn’t easy to move physical appliances around the network. Physical devices cannot follow workloads, which drives the world of virtual firewalls with distributed firewalls, NIC-based Firewalls, Microsegmentation, and Firewall VM-based appliances.
Session state
Simple packet filters match on Layer 2 to 4 headers – MAC, IP, TCP, and UDP port numbers. If they don’t match the TCP SYN flags, it’s impossible to identify established sessions. Tracking the state of the TCP SYN tells you if this is the first packet of a session or a subsequent packet of an existing session. Matching on TCP flags allows you to differentiate between TCP SYN, SYN-ACK, and ACK.
Matching established TCP sessions would match on packets with the ACK/RST/FIN bit set. All packets without a SYN flag will not start a new session, and all packets with ACK/RST/FIN can appear anywhere in the established session.
Checking these three flags indicates if the session is established or not. In any adequately implemented TCP stack, the packet filtering engine will not open a new session unless it receives a TCP packet with the SYN flag. In the past, we used a trick. If a packet arrives with a destination port over 1024, it must be a packet from an established session, as no services were running on a high number of ports.
The term firewall originally referred to a wall to confine a potential fire. Regarding networking, a firewalling device is a barrier between a trusted and untrusted network. It can be classed into several generations. First-generation firewalls are simple packet filters, the second-generation refers to stateful devices, and the third-generation refers to application-based firewalls. A stateful firewall doesn’t mean it can examine the application layer and determine users’ actions.
The starting points of packet filters
Firewalls initially started with packet filters at each end and an application proxy in the middle. The application proxy would inspect the application level, and the packet filters would perform essential scrubbing. All sessions terminate on the application proxy where new sessions are initiated. Second-generation devices came into play, and we started tracking the sessions’ state.
Now, we have a single device that can do the same job as the packet filter combined with the application proxy. But it wasn’t inspected at the application level. The devices were stateful and could track the session’s state but could not go deeper into the application. For example, examine the HTTP content and inspect what users are doing. Generation 2 was a step back in terms of security.
We then moved into generation 3, which marketing people call next-generation firewalls. They offer Layer 7 inspection with packet filtering. Finally, niche devices called Application-Level firewalls, also known as web application Firewalls (WAF), are usually only concerned with HTTP traffic. They have similar functionality to reverse web proxy, terminating the HTTP session.
The rise of virtual firewalls and virtual firewall appliances
Almost all physical firewalls offer virtual contexts. Virtual contexts divide the firewall and solve many multi-tenancy issues. They provide separate management plans, but all the contexts share the same code. They also run over the same interfaces competing for the same bandwidth, so if one tenant gets DoS attacked, the others might be affected. However, virtual contexts constitute a significant drawback because they are tied to the physical device, so you lose all the benefits of virtualization, unlike VM-based firewalls.
A firewall in a VM can run on any transport provided by the hypervisor. The VM thinks it has an ethernet interface, enabling you to put a VM-based firewall on top of any virtualization technology. The physical firewall must be integrated with the network virtualization solution, and many vendors have limited support for overlay networking solutions.
The physical interface supports VXLAN but doesn’t mean it can help the control plane in which the overlay network solution runs. For example, the network overlay solution might use IP multicast, OVSDB, or EVPN over VXLAN. Deploying Virtual firewalling offers underlay transport independence. They are flexible and easy to deploy and manage.
Virtual firewall appliance: VM and NIC-based firewalls
Traditionally, we used VLANs and IP subnets as security zones. This introduced problems with stretched VLANs, so they came with VXLAN and NVGRE. However, we are still using IP as the isolation mechanism. Generally, firewalls are implemented between subnets so all the traffic goes through the firewall, which can result in traffic trombones and network chokepoints.
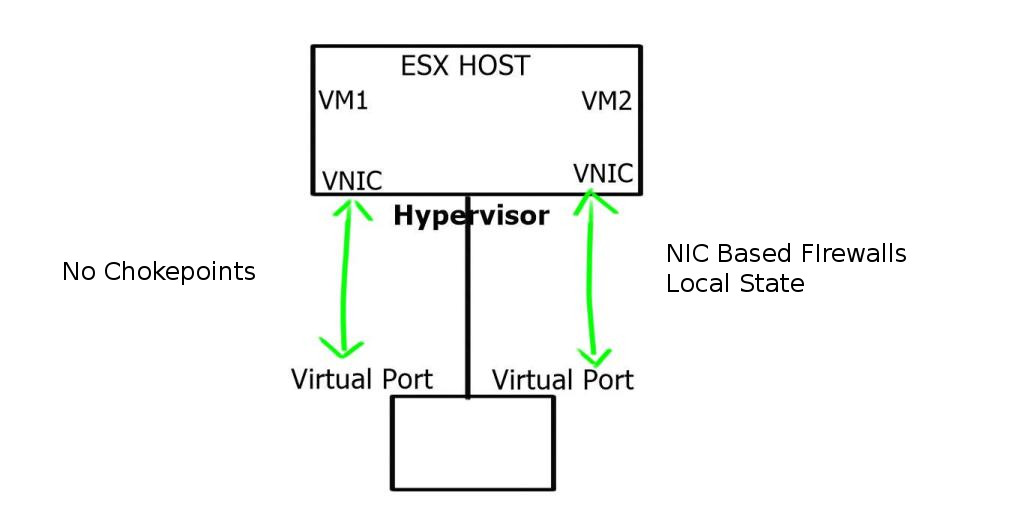
The new world is all about VM and NIC-based firewalls. NIC-based firewalls are mostly packet filters or, at the very most, reflective ACLs. Vmware NSX distributed firewall does slightly more with some application-level functionality for SIP and FTP traffic.
NIC-based firewalls force you to redesign your security policy. Now, all the firewall rules are directly in front of the virtual NIC, offering optimal access to any traffic between VMs, as traffic does not need to go through a central firewall device. The session state is kept local and only specific to that VM. This makes them very scalable. It allows you to eliminate IP subnets as security zones and provides isolation between VMs in the same subnet.
This protects individual VMs by design, so all others are protected even if an attacker breaks into one VM. VMware calls this micro-segmentation in NSX. You can never fully replace physical firewalls with virtual firewalls. Performance and security audits come to mind. However, they can be used to augment each other. NIC is based on the east-to-west traffic and physical firewalls at the perimeter to filter north-to-south traffic.
Virtual firewalls have revolutionized the way organizations approach network security in virtualized environments. Their flexibility, cost-effectiveness, centralized management, segmentation capabilities, and scalability make them a compelling choice for safeguarding virtual machines and networks. As technology advances, virtual firewalls will be increasingly important in protecting organizations against emerging cyber threats. By adopting virtual firewalls, businesses can proactively protect their digital assets and ensure a robust security posture in today’s interconnected world.
Summary: Virtual Firewalls
The need for robust network security has never been greater in today’s interconnected world. With the rise of cyber threats, organizations constantly seek advanced solutions to protect their sensitive data. One such powerful tool that has gained significant prominence is the virtual firewall. In this blog post, we will delve into virtual firewalls, exploring their definition, functionality, benefits, and role in fortifying network security.
Understanding Virtual Firewalls
Virtual firewalls, also known as software firewalls, are security applications that provide network protection by monitoring and controlling incoming and outgoing network traffic. Unlike physical firewalls, which are hardware-based, virtual firewalls operate within virtualized environments, offering a flexible and scalable approach to network security.
How Virtual Firewalls Work
Virtual firewalls examine network packets and determine whether to allow or block traffic based on predefined rule sets. They analyze factors such as source and destination IP addresses, ports, and protocols to make informed decisions. With their deep packet inspection capabilities, virtual firewalls can identify and mitigate potential threats, including malware, hacking attempts, and unauthorized access.
Benefits of Virtual Firewalls
Enhanced Security: Virtual firewalls provide an additional layer of security, safeguarding the network from external and internal threats. By actively monitoring and filtering network traffic, they help prevent unauthorized access and mitigate potential vulnerabilities.
Cost-Effectiveness: As software-based solutions, virtual firewalls eliminate the need for physical appliances, thereby reducing hardware costs. They can be easily deployed and managed within virtualized environments, streamlining network security operations.
Scalability: Virtual firewalls offer scalability, allowing organizations to adapt their security infrastructure to meet evolving demands. By allowing organizations to add or remove virtual instances as needed, they provide flexibility in managing expanding networks and changing business requirements.
Best Practices for Implementing Virtual Firewalls
Define Clear Security Policies: Comprehensive security policies are crucial for effective virtual firewall implementation. Clearly define access rules, traffic filtering criteria, and acceptable use policies to ensure optimal protection.
Regular Updates and Patching: Stay updated with your virtual firewall’s latest security patches and firmware updates. Regularly monitoring and maintaining the firewall’s software ensures it is equipped with the latest threat intelligence and safeguards against emerging risks.
Monitoring and Log Analysis: Implement robust monitoring and log analysis tools to gain insights into network traffic patterns and potential security incidents. Proactive monitoring allows for prompt detection and response to any suspicious activity.
Conclusion:
In conclusion, virtual firewalls have become indispensable tools in the arsenal of network security measures. Their ability to protect virtualized environments, provide scalability, and enhance overall security posture makes them a top choice for organizations seeking holistic network protection. By harnessing the power of virtual firewalls, businesses can fortify their networks, safeguard critical data, and stay one step ahead of cyber threats.
- DMVPN - May 20, 2023
- Computer Networking: Building a Strong Foundation for Success - April 7, 2023
- eBOOK – SASE Capabilities - April 6, 2023