DNS Reflection attack
In today's interconnected world, cyber threats continue to evolve, posing significant risks to individuals, organizations, and even nations. One such threat, the DNS Reflection Attack, has gained notoriety for its potential to disrupt online services and cause significant damage. In this blog post, we will delve into the intricacies of this attack, exploring its mechanics, impact, and how organizations can protect themselves from its devastating consequences.
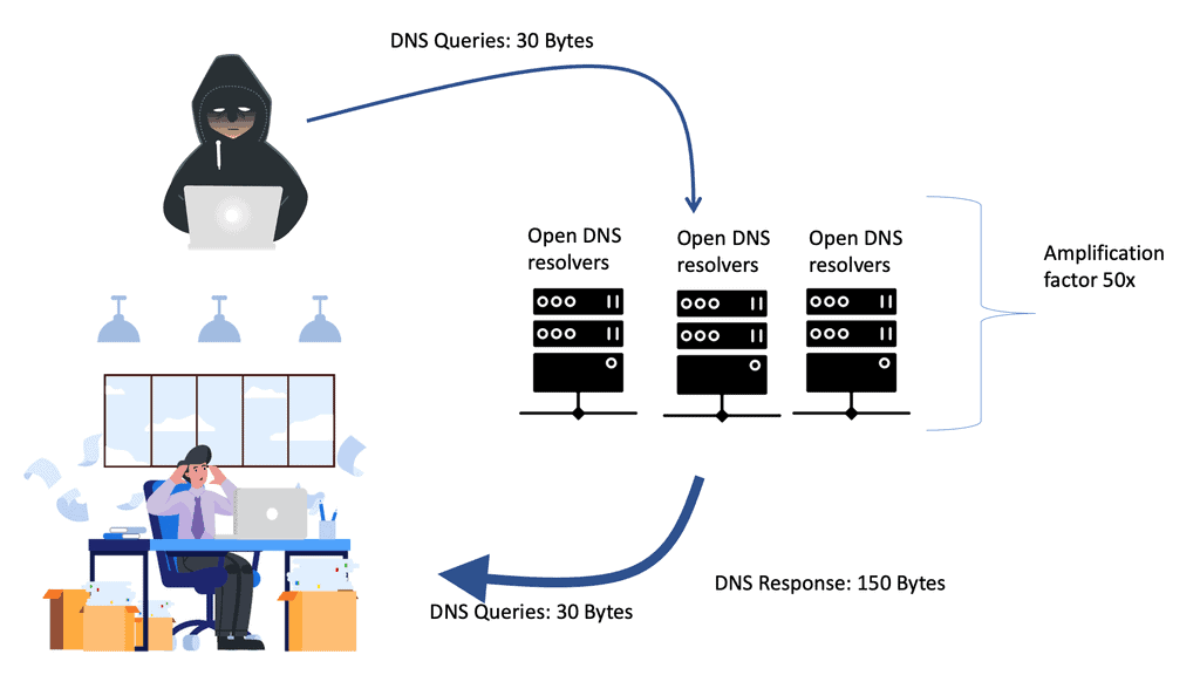
A DNS Reflection Attack, or a DNS amplification attack, is a type of Distributed Denial of Service (DDoS) attack. It exploits the inherent design of the Domain Name System (DNS) to overwhelm a target's network infrastructure. The attacker spoofs the victim's IP address and sends multiple DNS queries to open DNS resolvers, requesting significant DNS responses. The amplification factor of these responses can be several times larger than the original request, leading to a massive influx of traffic directed at the victim's network.
DNS reflection attacks exploit the inherent design of the Domain Name System (DNS) to amplify the impact of an attack. By sending a DNS query with a forged source IP address, the attacker tricks the DNS server into sending a larger response to the targeted victim.
One of the primary dangers of DNS reflection attacks lies in the amplification factor they possess. With the ability to multiply the size of the response by a significant factor, attackers can overwhelm the victim's network infrastructure, leading to service disruption, downtime, and potential data breaches.
DNS reflection attacks can target various sectors, including but not limited to e-commerce platforms, financial institutions, online gaming servers, and government organizations. The vulnerability lies in misconfigured DNS servers or those that haven't implemented necessary security measures.
To mitigate the risk of DNS reflection attacks, organizations must implement a multi-layered security approach. This includes regularly patching and updating DNS servers, implementing ingress and egress filtering to prevent IP address spoofing, and implementing rate-limiting or response rate limiting (RRL) techniques to minimize amplification.
Addressing the DNS reflection attack threat requires collaboration among industry stakeholders. Organizations should actively participate in industry forums, share threat intelligence, and adhere to recommended security standards such as the BCP38 Best Current Practice for preventing IP spoofing.
Conclusion: DNS reflection attacks pose a significant threat to the stability and security of network infrastructures. By understanding the nature of these attacks and implementing preventive measures, organizations can fortify their defenses and minimize the risk of falling victim to such malicious activities.
Matt Conran
Highlights: DNS Reflection attack
DNS Amplification
Domain names are stored and mapped into IP addresses in the Domain Name System (DNS). As part of a two-step distributed denial-of-service attack (DDoS), DNS reflection/amplification is used to manipulate open DNS servers. Cybercriminals use a spoofed IP address to send massive requests to DNS servers.
Therefore, the DNS server responds to the request and attacks the target victim. Many traffic is sent to the victim server since these attacks are more significant than the spoofed request. An attack can render data entirely inaccessible to a company or organization.
Even though DNS reflection/amplification DDoS attacks are common, they pose a severe threat to an organization’s servers. Massive amounts of traffic pushed into the victim server consume company resources, slowing and paralyzing systems to prevent real traffic from accessing the DNS server.
DNS Reflectors
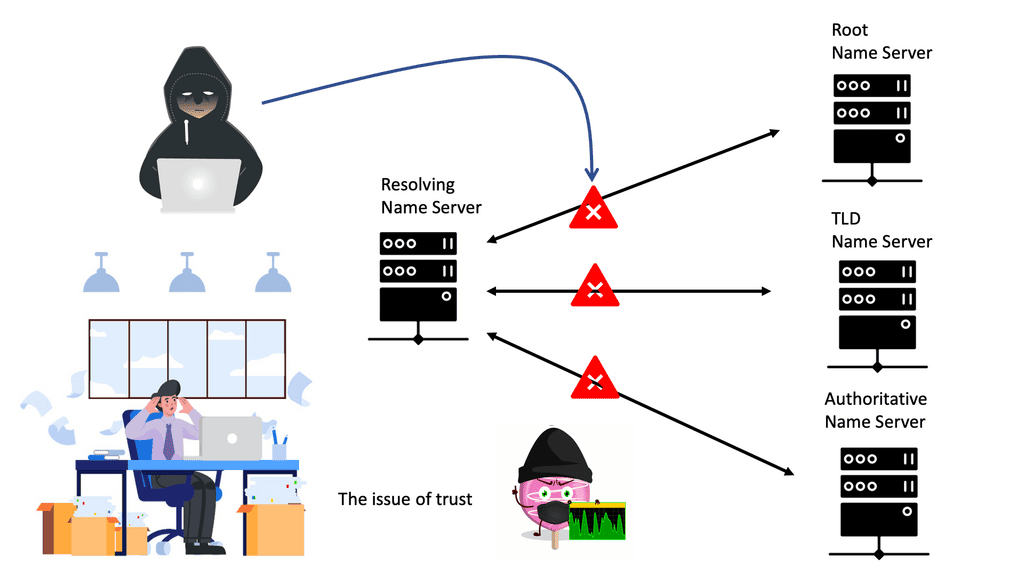
Despite the difficulty of mitigating these attacks, network operators can implement several strategies to combat them. To reduce the possibility of their own DNS servers being used as reflectors, DNS servers should be hosted locally and internally within the organization. Additionally, this allows organizations to separate internal DNS traffic from external DNS traffic, allowing them to block unwanted DNS traffic.
Organizations should block unsolicited DNS replies, allowing only responses requested by internal clients, to protect themselves against DNS reflection/amplification attacks. When DDoS attacks are reflected in DNS Reply sections, detection tools can detect and remove unwanted DNS replies.
The Role of DNS
Firstly, the basics. DNS (Domain Name System) is a host-distributed database that converts domain names to IP addresses. Most clients rely on DNS for communicating services such as Telnet, file transfer, and HTTP web browsing. It goes through a chain of events, usually only taking milliseconds for the client to receive a reply. Quick does not often mean secure. First, let us examine the DNS structure and DNS operations.
The DNS Process
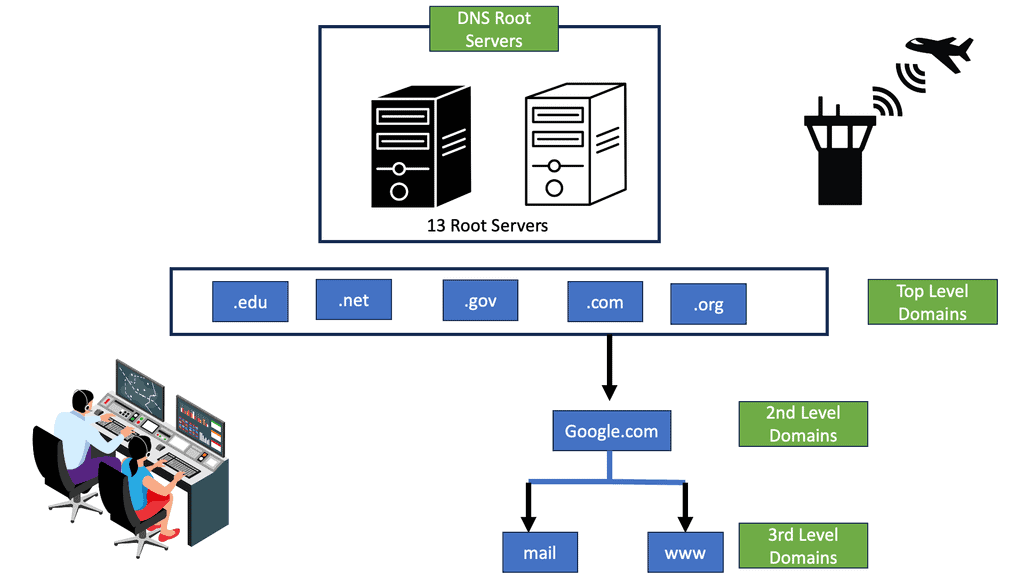
The clients send a DNS query to a local DNS server (LDNS), a Resolver. Then, the LDNS relays the request to a Root server with the required information to service the request. Root servers are a critical part of Internet architecture. They are authoritative name servers that serve the DNS root zone by directly answering requests or returning a list of authoritative nameservers for the appropriate top-level domain (TLD). Unfortunately, this chain of events is the base of DNS-based DDoS attacks such as the DNS Recursion attack.
Before you proceed, you may find the following posts useful for pre-information:
- DNS Security Solutions
- DNS Security Designs
- Cisco Umbrella CASB
- OpenShift SDN
- DDoS Attacks
- UDP Scan
- IPv6 Attacks
DNS Recursion Attack. Key DNS Reflection Attack Discussion Points: |
|
Back to Basics With DNS Reflection Attack
The Domain Namespace
So, we have domain names that index DNS’s distributed database. Each domain name is a path in a large inverted tree called the domain namespace. So, when you think about the tree’s hierarchical structure, it is similar to the design of the Unix filesystem.
The tree has a single root at the top. So, the Unix filesystem represents the root directory by a slash (/). So, we have DNS that calls and refers to it as “the root.” But it’s a similar structure that, too, has limits. The DNS’s tree can branch any number of ways at each intersection point or node. However, the depth of the tree is limited to 127 levels, which you are not likely to reach.
DNS and its use of UDP
DNS uses User Datagram Protocol (UDP) as the transport protocol. UDP is a lot faster than TCP due to its stateless operation. Stateless means no connection state is maintained between UDP peers. It has no connection information, just a query/response process.
One problem with using UDP as the transport protocol is that the size of unfragmented UDP packets has limited the number of root server addresses to 13. To alleviate this problem, root server IP addressing is based on Anycast, permitting the number of root servers to be larger than 500. Anycast permits the same IP address to be advertised from multiple locations.
Lab Guide on the DNS Process.
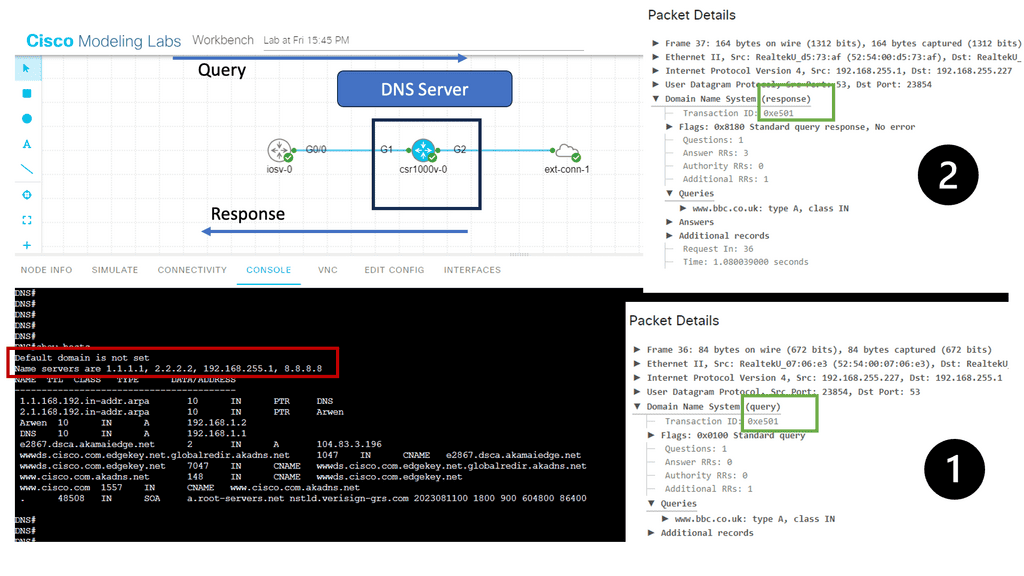
The DNS resolution process begins when a user enters a domain name in their browser. It involves several steps to translate the domain name into an IP address. In the example below, I have a CSR1000v configured as a DNS server and several name servers. I also have an external connector configured with NAT for external connectivity outside of Cisco Modelling Labs.
- Notice the DNS Query and the DNS Response from the Packet Capture. Keep in mind this is UDP and, by default, insecure.
Highlights DNS Reflection Attack
The attacker identifies vulnerable DNS resolvers that can be abused to amplify the attack. These resolvers respond to DNS queries from any source without proper source IP address validation. By sending a small DNS request with the victim’s IP address as the source, the attacker tricks the resolver into sending a much larger response to the victim’s network. This amplification effect allows attackers to generate a significant traffic volume, overwhelming the victim’s infrastructure and rendering it inaccessible.
- Impact and Consequences:
DNS Reflection Attacks can have severe consequences, both for individuals and organizations. Some of the critical impacts include:
- Disruption of Online Services:
The attack can destroy websites, online services, and other critical infrastructure by flooding the victim’s network with massive amplified traffic. This can result in financial losses, reputational damage, and significant user inconvenience.
- Collateral Damage:
In many cases, DNS Reflection Attacks can have collateral damage, affecting the intended target and other systems sharing the same network infrastructure. This can lead to a ripple effect, causing cascading failures and disrupting multiple online services simultaneously.
- Loss of Confidentiality:
During a DNS Reflection Attack, attackers exploit chaos and confusion to gain unauthorized access to sensitive data. This can include stealing user credentials, financial information, or other valuable data, further exacerbating the damage caused by the attack.
- Mitigation and Prevention:
To mitigate the risk of DNS Reflection Attacks, organizations should consider implementing the following measures:
- Source IP Address Validation:
DNS resolvers should be configured to only respond to queries from authorized sources, preventing the use of open resolvers for amplification attacks.
- Rate Limiting:
By implementing rate-limiting mechanisms, organizations can restrict the number of DNS responses sent to a particular IP address within a given time frame. This can help mitigate the impact of DNS Reflection Attacks.
- Network Monitoring and Traffic Analysis:
Organizations should regularly monitor their network traffic to identify suspicious patterns or abnormal spikes in DNS traffic. Advanced traffic analysis tools can help detect and mitigate DNS Reflection Attacks in real-time.
- DDoS Mitigation Services:
Engaging with reputable DDoS mitigation service providers can offer additional protection against DNS Reflection Attacks. These services employ sophisticated techniques to identify and filter malicious traffic, ensuring the availability and integrity of online services.
Exploiting DNS-Based DDoS Attacks
Mainly, denial of service (DoS) mechanisms disrupt activity and prevent upper-layer communication between hosts. Attacking UDP is often harder to detect than general DoS resource saturation attacks. Attacking UDP is not as complex as attacking TCP because UDP has no authentication and is connectionless.
This makes it easier to attack than some application protocols, which usually require authentication and integrity checks before accepting data. The potential threat against DNS is that it relies on UDP and is subject to UDP control plane threats. Launching an attack on a UDP session can be achieved without application awareness.
DNS query attack
One DNS-based DDoS attack method is carrying out a DNS query attack. The attacker uses a tap client and sends a query to a remote DNS server to overload it with numerous clients, sending queries to the same DNS server. The capacity of a standard DNS server is about 150,000 queries. If the remote server does not have the capacity, it will drop and ignore the legitimate request and be unable to send responses. The DNS server cannot tell which query is good or bad. A query attack is a relatively simple attack.
DNS Recursion attack
The recursive nature of DNS servers enables them to query one another to locate a DNS server with the correct IP address or to find an authoritative DNS server that holds the canonical mapping of the domain name to its IP address. The very nature of this operation opens up DNS to a DNS Recursion Attack.
A DNS Recursion Attack is also known as a DNS cache poisoning attack. DNS attacks occur when a recursive DNS server requests an IP address from another; an attacker intercepts the request and gives a fake response, often the IP address for a malicious website.
DNS reflection attack
A more advanced form of DNS-based DDoS attacks is a technique called a DNS reflection attack. The attackers take advantage of the underlying vulnerability in the DNS protocol. The return address (source IP address in the query) is tricked into being someone else. This is known as DNS Spoofing or DNS cache poisoning.
The attackers send out a DNS request and set the IP address as their target for the source IP. The natural source gets overwhelmed with return traffic, and the source IP address is known to be spoofed.
The main reason for carrying out reflection attacks is an amplification (discussed below). The advertisement of spoofed DNS name records enables the attacker to carry out many other attacks. As discussed, they can redirect flows to a destination of choice, which opens up other sophisticated attacks that facilitate eavesdropping, MiTM attacks, the injection of false data, and the distribution of Malware and Trojans.
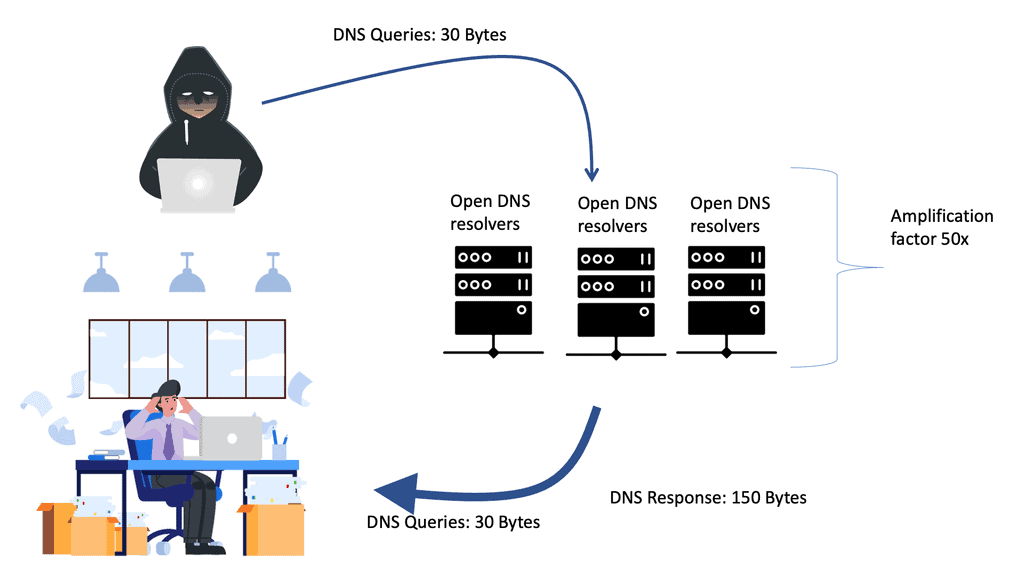
DNS and unequal sizes
The nature of the DNS system is that it has unequal sizes. The query messages are tiny, and the response is typically double the query size. However, there are certain record types that you can ask for that are much more significant. Attackers may concentrate their attack using DNS security extension (DNSSEC) cryptographic or EDNS0 extensions. If you add DNSsec, it combines a lot of keys and makes the packet much larger.
These requests can increase packet size from around 40 bytes to above the maximum Ethernet packet size of 4000. They potentially require fragmentation, further targeting network resources. This is the essence of any IPv4 and IPv6 attack amplification: a small query with a significant response. Many load balancing products have built-in DoS protection, enabling you to set limits for packets per second on specific DNS queries.
DNS Open Resolvers
The attack can be amplified even more with DNS Open Resolvers, enabling the least number of Bots with maximum damage. A Bot is a type of Malware that allows the attacker to control it. Generally, a security mechanism should be in place so resolvers only answer requests from a list of clients. These are called locked or secured DNS resolvers.
Unfortunately, many resolvers lack best-practice security mechanisms. Unfortunately, Open Resolvers amplify the amplification attack surface even further. DNS amplification is a variation of an old-school attack called an SMURF attack.
At a fundamental level, ensure you have an automated list to accept only known clients. Set up ingress filtering to ensure you don’t have an illegal address leaving your network. Ingress filtering prevents any spoofing-style attacks. This will weed it down and thin it out a bit.
Next, test your network and make sure you don’t have any Open Resolvers. NMAP (Network Mapper) is a tool with a script to test recursion. This will test whether your local DNS servers are open to recursion attacks.
GTM Load Balancer
At a more expensive level, F5 offers a product called DNS Express. It allows you to withstand DoS attacks by adding an F5 GTM Load Balancer to your DNS servers. DNS Express handles the request on behalf of the DNS server. It works from high-speed RAM and, on average, handles about 2 million requests per second.
This is about 12 times more than a regular DNS server, which should be enough to withstand a sophisticated DNS DoS attack. Later posts deal with mitigation techniques, including stateful firewalls and other devices.
Summary: DNS Reflection attack
In the vast realm of the internet, a fascinating phenomenon known as DNS reflection exists. This intriguing occurrence has captured the curiosity of tech enthusiasts and cybersecurity experts alike. In this blog post, we embarked on a journey to unravel the mysteries of DNS reflection and shed light on its inner workings.
Understanding DNS
Before diving into the intricacies of DNS reflection, it is essential to grasp the basics of DNS (Domain Name System). DNS serves as the backbone of the internet, translating human-readable domain names into IP addresses that computers can understand. It acts as a directory, facilitating seamless communication between devices across the web.
The Concept of Reflection
Reflection, in the context of DNS, refers to the bouncing back of packets between different systems. It occurs when a DNS server receives a query and responds by sending a more significant response to an unintended target. This amplification effect can lead to potentially devastating consequences if exploited by malicious actors.
Amplification Attacks
One of the most significant threats associated with DNS reflection is the potential for amplification attacks. Cybercriminals can leverage this vulnerability to launch large-scale distributed denial of service (DDoS) attacks. By spoofing the source IP address and sending a small query to multiple DNS servers, they can provoke a deluge of amplified responses to the targeted victim, overwhelming their network infrastructure.
Mitigation Strategies
Given the potential havoc that DNS reflection can wreak, it is crucial to implement robust mitigation strategies. Network administrators and cybersecurity professionals can take several proactive steps to protect their networks. These include implementing source IP verification, deploying rate-limiting measures, and utilizing specialized DDoS protection services.
Conclusion:
In conclusion, DNS reflection poses a significant challenge in cybersecurity. By understanding its intricacies and implementing appropriate mitigation strategies, we can fortify our networks against potential threats. As technology evolves, staying vigilant and proactive is paramount in safeguarding our digital ecosystems.