Cisco Firewall with IPS
In today's digital landscape, the need for robust network security has never been more critical. With the increasing prevalence of cyber threats, businesses must invest in reliable firewall solutions to safeguard their sensitive data and systems. One such solution that stands out is the Cisco Firewall. In this blog post, we will explore the key features, benefits, and best practices of Cisco Firewall to help you harness its full potential in protecting your network.
Cisco Firewall is an advanced network security device designed to monitor and control incoming and outgoing traffic based on predetermined security rules. It is a barrier between your internal network and external threats, preventing unauthorized access and potential attacks. With its stateful packet inspection capabilities, the Cisco Firewall analyzes traffic at the network, transport, and application layers, providing comprehensive protection against various threats.
Cisco Firewall with IPS functions offers a plethora of features designed to fortify network security. These include:
Signature-based detection: Cisco's extensive signature database enables the identification of known threats, allowing for proactive defense.
Anomaly-based detection: By monitoring network behavior, Cisco Firewall with IPS functions can detect anomalies and flag potential security breaches.
Real-time threat intelligence: Integration with Cisco's threat intelligence ecosystem provides up-to-date information and protection against emerging threats.
The combination of Cisco Firewall with IPS functions offers several enhanced security measures, such as:
Intrusion Prevention: Proactively identifies and blocks intrusion attempts, preventing potential network breaches.
Application Awareness: Deep packet inspection allows for granular control over application-level traffic, ensuring secure usage of critical applications.
Virtual Private Network (VPN) Protection: Cisco Firewall with IPS functions offers robust VPN capabilities, securing remote connections and data transmission.
Matt Conran
Highlights: Cisco Firewall with IPS
**Protecting The Internet Edge**
The Internet edge is the point at which the organization’s network connects to the Internet. This is the boundary between the public Internet and the private resources within an organization’s network. Worms, viruses, and botnet intrusions threaten data security, performance, and availability.
Additional problems include employee productivity loss and data leakage due to an organization’s Internet connection. A company’s network infrastructure and data resources are at risk from internet-based attackers. Worms, viruses, and targeted attacks constantly attack Internet-connected networks.
Firewalling is a fundamental aspect of network security. It is a barrier between a trusted internal network and an untrusted external network, monitoring and controlling incoming and outgoing network traffic. By implementing firewalling features, organizations can protect their sensitive data and network resources from unauthorized access and potential threats.
**Numerous Attack Vectors**
We have Malware, social engineering, supply chain attacks, advanced persistent threats, denial of service, and various man-in-the-middle attacks. And nothing inside the network should be considered safe. So, we must look beyond Layer 3 and incorporate multiple security technologies into firewalling.
We have the standard firewall that can prevent some of these attacks, but we need to add additional capabilities to its baseline. Hence, we have a better chance of detection and prevention. Some of these technologies that we layer on are provided by Cisco Snort, which enables the Cisco intrusion prevention system ( Cisco IPS ) included in the Cisco Firewall solution that we will discuss in this post.
Example Technology: Linux Firewalling
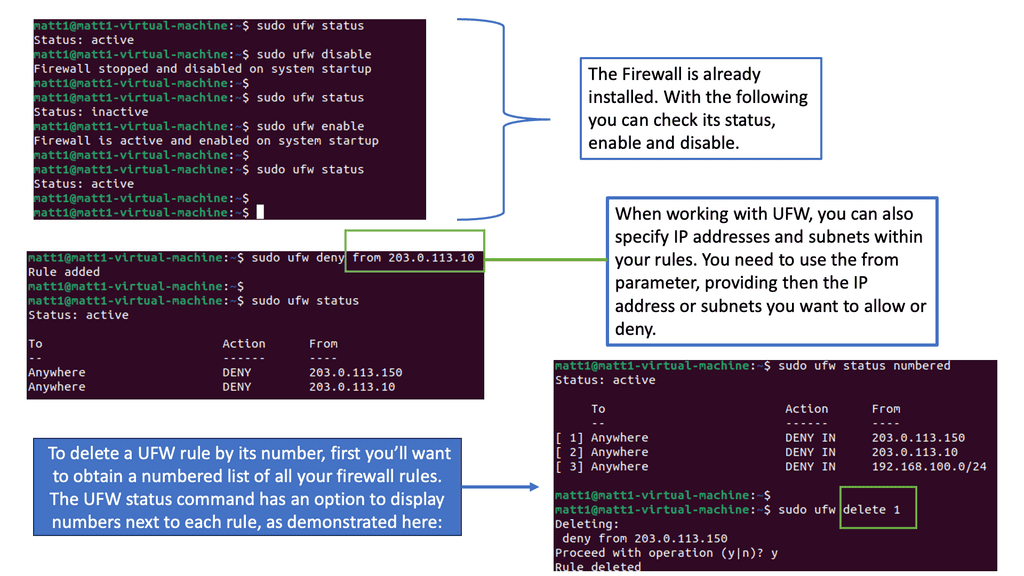
What is a UFW Firewall?
UFW, short for Uncomplicated Firewall, is a user-friendly front-end for managing firewall rules in Linux-based systems. It is built upon the robust infrastructure of iptables. Still, it provides a simplified and intuitive interface, making it accessible even to users without an in-depth understanding of networking and firewall configurations. With UFW, you can easily define and manage rules to control incoming and outgoing network traffic, safeguarding your system from unauthorized access and potential threats.
Cisco Firewall Types:
1. Cisco ASA Firewalls:
Cisco ASA (Adaptive Security Appliance) firewalls are among the most widely used firewalls in the industry. They provide advanced threat protection, application visibility and control, and integrated security services. With features such as stateful packet inspection, VPN support, and network address translation, Cisco ASA firewalls are suitable for small to large enterprises.
2. Cisco Firepower Threat Defense (FTD):
Cisco Firepower Threat Defense (FTD) is a unified software image that combines the functionality of Cisco ASA with advanced threat detection and prevention capabilities. FTD offers next-generation firewall features like intrusion prevention system (IPS), malware protection, and URL filtering. It provides enhanced visibility into network traffic and enables organizations to combat modern-day threats effectively.
3. Cisco Meraki MX Firewalls:
Cisco Meraki MX firewalls are cloud-managed security appliances designed for simplicity and ease of use. They offer robust security features, including stateful firewalling, content filtering, and advanced malware protection. Meraki MX firewalls are particularly suitable for distributed networks, remote sites, and small to medium-sized businesses.
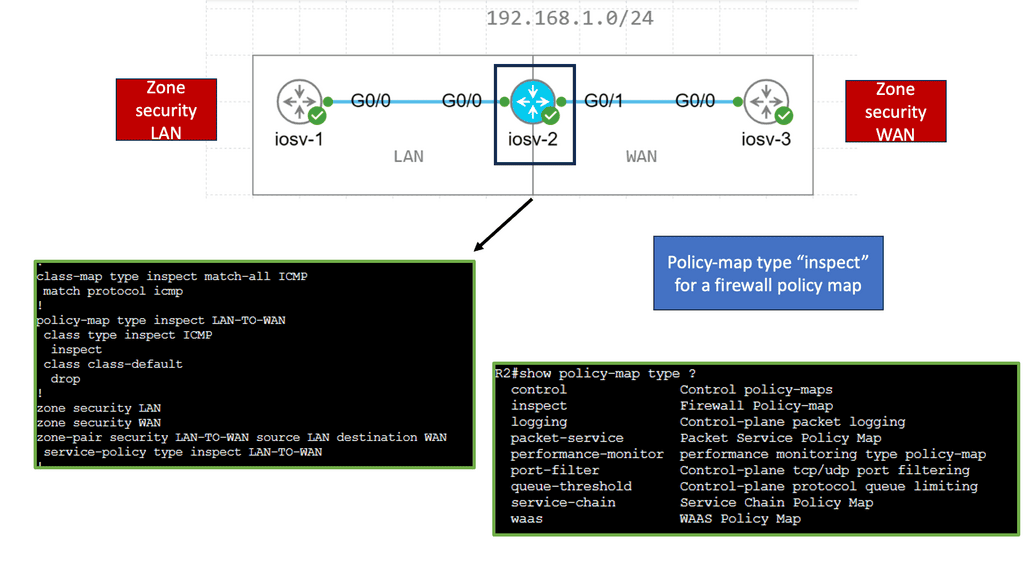
4. Cisco IOS Zone-Based Firewall:
Cisco IOS Zone-Based Firewall is a software-based firewall solution integrated into Cisco routers. It provides secure network segmentation by grouping interfaces into security zones and applying firewall policies between zones. The IOS Zone-Based Firewall is ideal for branch offices and enterprise edge deployments with its flexible configuration options and support for various protocols.
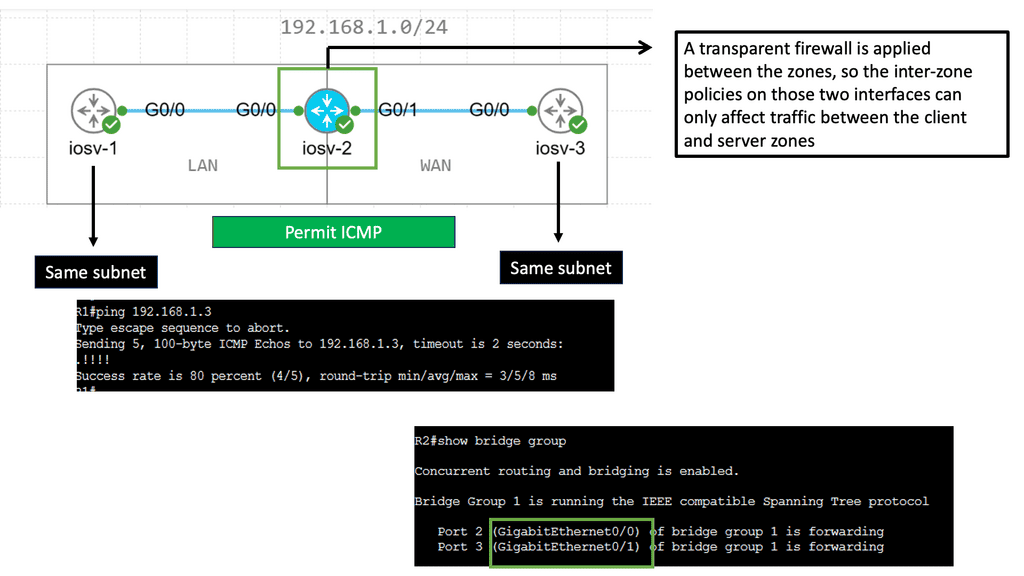
**Zone-Based Firewall in Transparent Mode**
Understanding Zone-Based Firewalls
Zone-based firewalls are a form of network security that operates based on zones rather than individual IP addresses. This approach allows for simplified policy management and enhanced security. By classifying network segments into zones, administrators can define specific security policies for each zone, controlling traffic flow between them.
One key advantage of zone-based firewalls is their ability to provide granular control over network traffic. Administrators can define policies based on the specific requirements of different zones, allowing for customized security measures. Additionally, zone-based firewalls enable simplified troubleshooting and monitoring, as traffic can be inspected and logged at the zone level.
Zone-based firewalls can integrate the existing network infrastructure seamlessly to achieve transparent network security. By placing the firewall at the perimeter of each zone, traffic can be inspected and filtered without disrupting the network’s regular operation. This transparency ensures that network performance is not compromised while maintaining robust security measures.
 Firewalling Features:
Firewalling Features:
Several types of firewalling features serve different purposes. Let’s explore a few of them:
**Packet Filtering**
1. Packet Filtering: Packet filtering firewalls examine individual data packets and decide based on predefined rules. They analyze the packet’s header information, such as source and destination IP addresses, ports, and protocol type, to determine whether to allow or block the packet. There are two main types of packet-filtering firewalls: stateless and stateful. Stateless firewalls examine individual packets without considering their context, which can be more efficient but less secure.
On the other hand, stateful firewalls maintain information about the connection state, allowing for more advanced inspection and increased security. Each type has advantages and considerations, and the choice depends on the network’s specific needs and requirements.
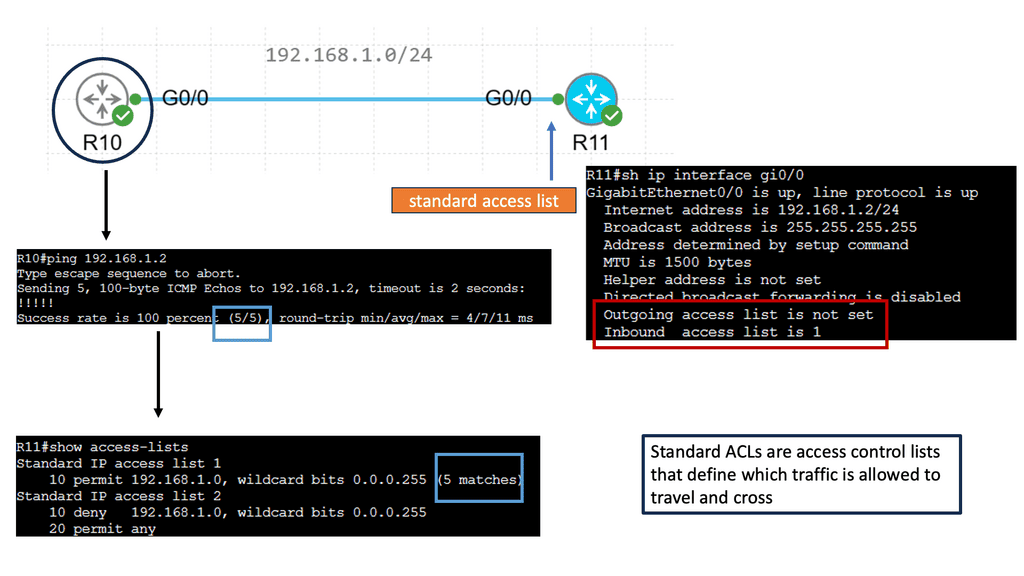
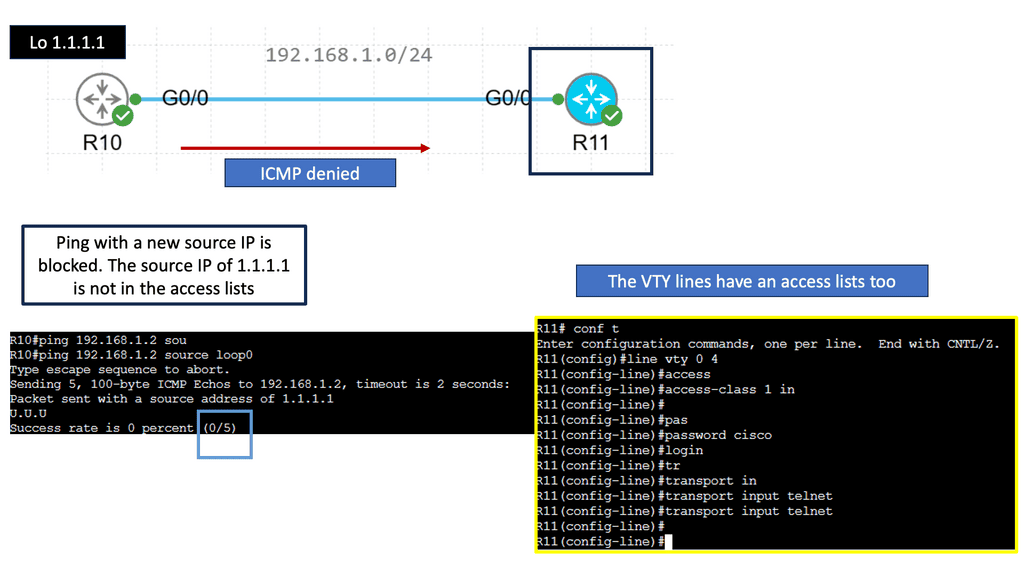
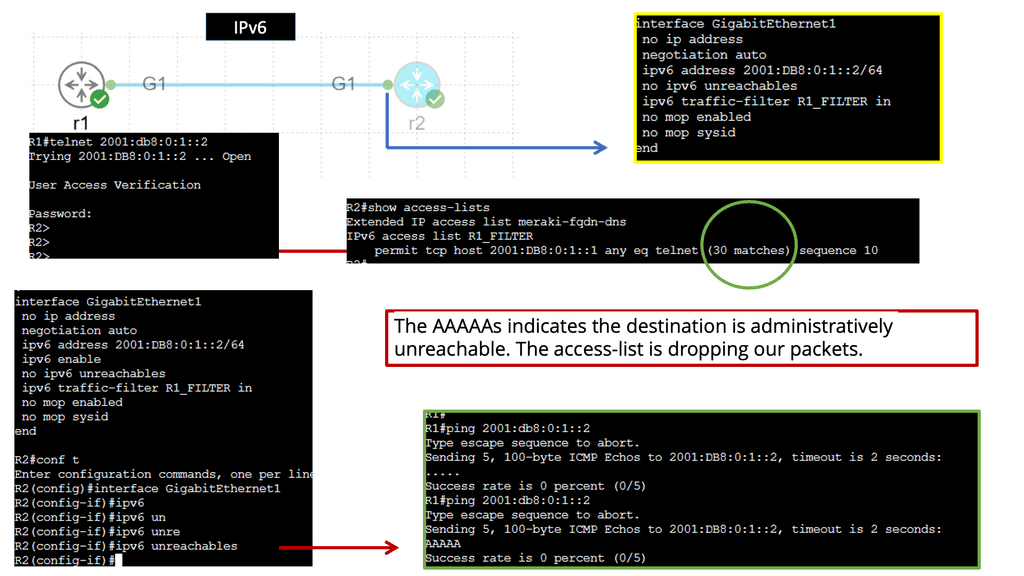
Packet Filtering – IPv4 & IPv6 Standard Access Lists
Understanding Standard Access Lists
Standard access lists, commonly known as ACLs, are an essential tool in network security. They filter IP traffic based only on source IP addresses. Network administrators can control data flow into or out of a network by specifying which source IP addresses are allowed or denied.
Specific syntax and configuration steps must be followed to create a standard access list. Typically, this involves defining the access list number, specifying the permit or deny actions, and defining the source IP addresses to be filtered. Network administrators can implement these access lists on routers or switches to regulate traffic flow effectively.
Standard access lists have applications in various network scenarios. For example, they can restrict access to specific network resources based on source IP addresses. Additionally, they can be utilized for traffic filtering, allowing or denying certain types of traffic based on predefined criteria. Practical examples will demonstrate how standard access lists can enhance network security and optimize performance.
ACL Type: IPv6 Access Lists
What are IPv6 access lists?
IPv6 access lists are firewall mechanisms that filter IPv6 traffic based on defined rules. They permit or deny packets based on various criteria, such as source and destination IP addresses, protocol types, and port numbers. Network administrators can define granular traffic policies by implementing access lists and enhancing network security and performance.
IPv6 access lists follow a specific syntax and structure. They consist of sequential lines, each containing a permit or deny statement, followed by the criteria for matching packets. The requirements can include source and destination IPv6 addresses, port numbers, and protocol types. Additionally, access lists can be configured with specific logic, such as allowing or denying packets based on a particular sequence of rules.
**Stateful Inspection**
2. Stateful Inspection: Stateful inspection firewalls go beyond packet filtering by keeping track of the state of network connections. They maintain information about the context and status of each connection, allowing them to make more informed decisions and provide better protection against sophisticated attacks.
Stateful inspection firewalls operate at Layers 3 and Layer 4 of the OSI model, examining packet headers and payload data to make intelligent decisions. They analyze packets based on protocols, source and destination IP addresses, port numbers, and the connection’s state. This comprehensive analysis empowers stateful inspection firewalls to differentiate between legitimate traffic and malicious attempts, providing robust protection.
Example: Stateful Inspection
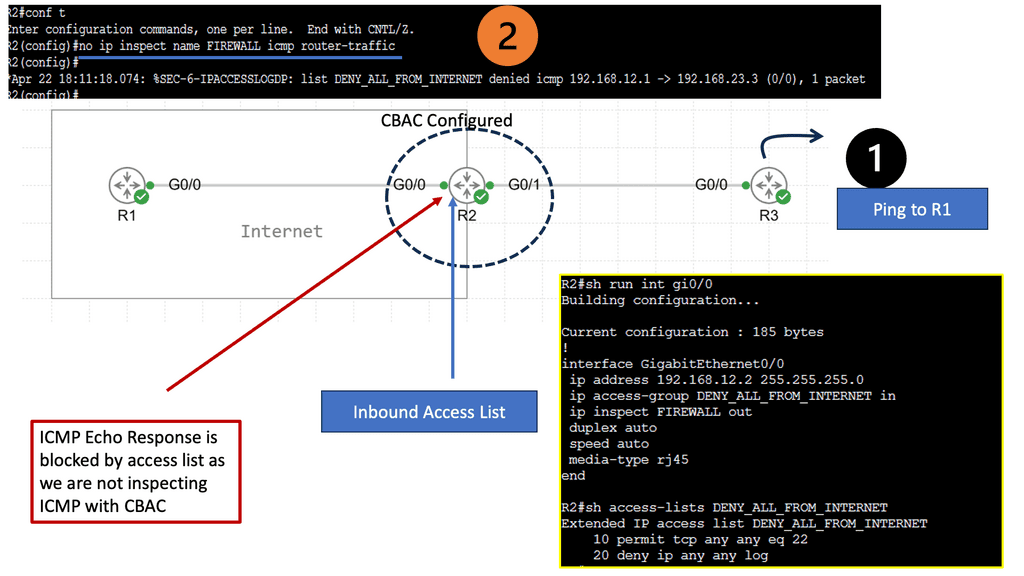
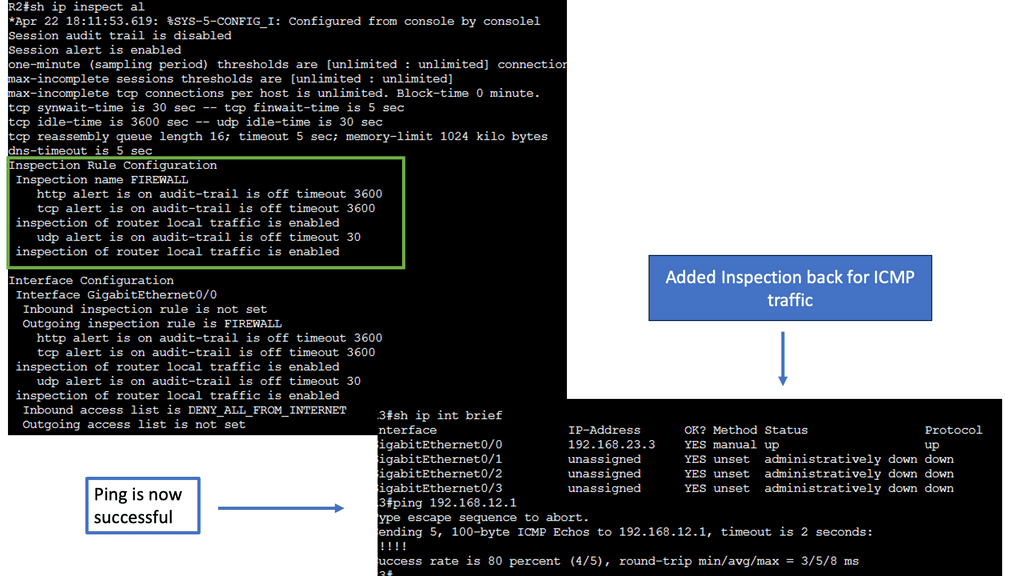
Understanding CBAC Firewall
The CBAC firewall operates by examining the state of network connections and making access control decisions accordingly. It analyzes the traffic flow in real-time, ensuring that only legitimate packets are allowed through while blocking malicious attempts. By incorporating layer 4 and layer 7 inspection, the CBAC firewall provides enhanced security measures compared to packet-filtering firewalls.
1. Stateful Packet Inspection: The CBAC firewall maintains a state table that tracks the context of network connections, allowing it to differentiate between legitimate and illegitimate traffic.
2. Application Layer Gateway: By inspecting the application layer data, the CBAC firewall can identify and control specific protocols, preventing unauthorized access and ensuring data integrity.
3. Protocol Inspection: CBAC firewall can scrutinize the protocol headers, ensuring that they comply with predefined policies and preventing protocol-level attacks.
**Application Layer Filtering**
3. Application Layer Filtering: Application layer firewalls operate at the application layer of the network stack. They can inspect the content of network traffic, including application-specific data. This allows for more granular control and protection against application-level attacks. Application-level filtering, also known as deep packet inspection (DPI), is a sophisticated security mechanism that scrutinizes data packets beyond traditional network-layer parameters.
Analyzing the packets’ content at the application layer provides granular control over network traffic based on various parameters, such as application type, protocol, and user-defined rules. We will look at DPI in just a moment.
Network Monitoring and Traffic Analysis
Understanding IDPS
IDPS, an acronym for Intrusion Detection and Prevention Systems, refers to a broad range of security solutions designed to detect and mitigate potential threats within a network infrastructure. These systems analyze network traffic, monitor suspicious activities, and alert administrators in real time. Furthermore, IDPS can take proactive measures to prevent intrusions, such as blocking malicious traffic or executing predefined security policies.
An IDPS typically consists of several interconnected components that perform its function effectively. These include:
1. Sensors: Sensors gather data from various network sources, such as network devices, servers, or individual endpoints. They continuously monitor network traffic and collect valuable information for analysis.
2. Analyzers: Analyzers are the brains behind the IDPS. They receive sensor data, analyze it using sophisticated algorithms, and determine whether suspicious or malicious activity occurs. Analyzers utilize both signature-based and anomaly-based detection techniques to identify potential threats.
3. User Interface: The user interface provides a centralized platform for administrators to manage and configure the IDPS. It allows them to customize detection rules, view alerts, and generate reports for further analysis.
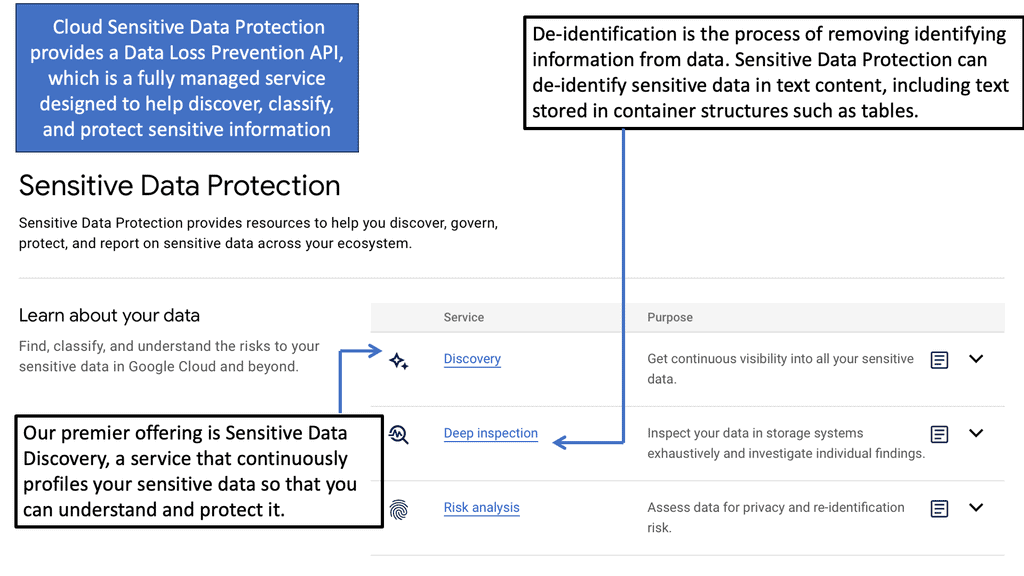
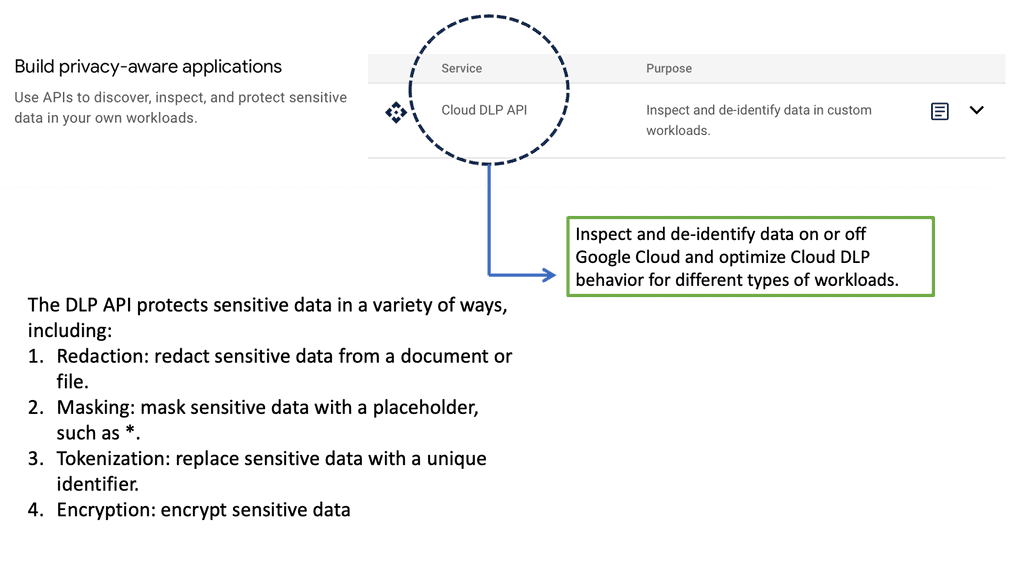
Example: Google Cloud DLP
Google Cloud & Sensitive Data Protection
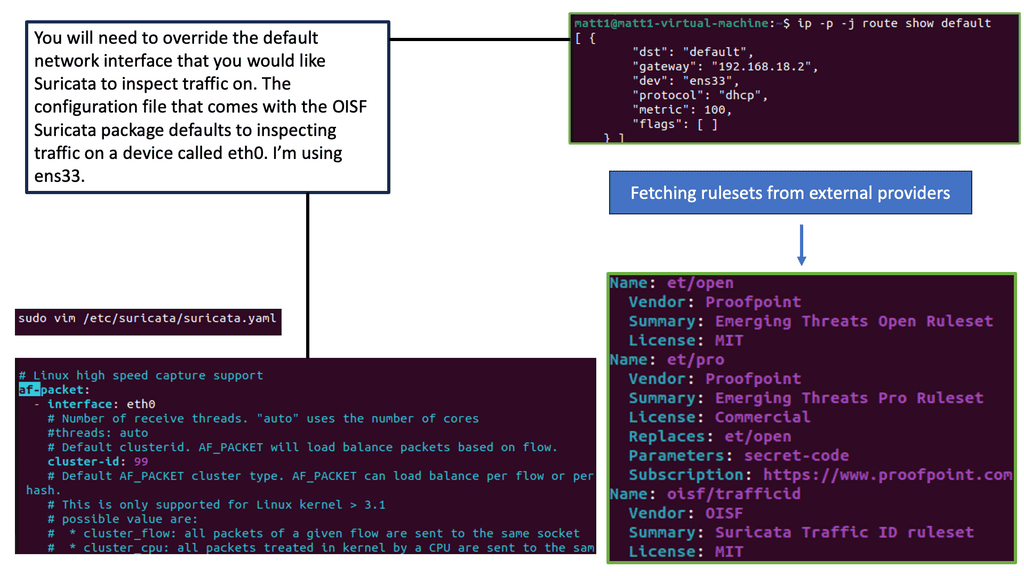
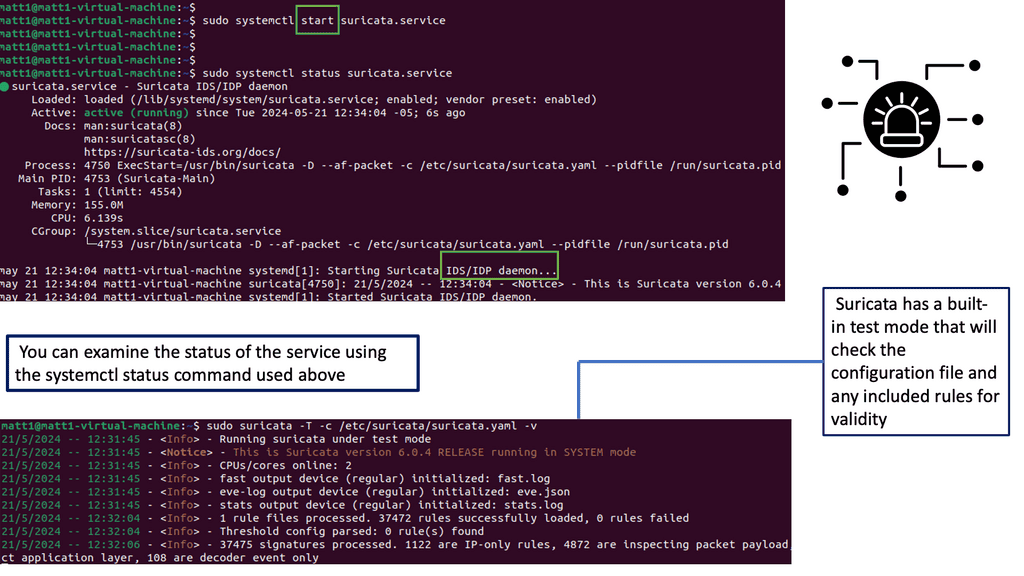
Understanding Suricata
Suricata is an open-source intrusion detection and prevention system designed to monitor network traffic and detect potential security threats. It combines the best features of signature-based and behavior-based detection, making it a versatile tool for network security professionals. Let’s delve into its core functionalities.
Suricata boasts various features that distinguish it from other IPS/IDS solutions. Its multi-threaded design efficiently utilizes system resources, ensuring optimal performance even under heavy network traffic. Suricata supports many protocols and can detect and prevent attacks, including malware infections, DDoS attacks, and suspicious network activities.
Detection Techniques
IDPS employs a variety of detection techniques to identify potential intrusions:
1. Signature-Based Detection: This technique compares network traffic patterns against a database of known attack signatures. The IDPS flags the traffic as potentially malicious if a match is found. Signature-based filters compare incoming data packets against a database of known attack signatures. When a match is found, the filter immediately acts, blocking the packet or generating an alert. This filter type effectively detects well-known attacks but may have limitations when facing new or evolving threats.
2. Anomaly-Based Detection: Anomaly-based detection identifies deviations from normal network behavior. By establishing a baseline of regular activity, the IDPS can detect and raise alerts when unusual patterns or behaviors are observed. Anomaly-Based Detection operates on the principle of identifying abnormal behavior within a network or system.
Unlike Signature-Based Detection, which relies on known patterns of attacks, Anomaly-Based Detection focuses on deviations from established norms. By building a baseline of normal behavior, this approach can effectively detect novel and sophisticated attacks that traditional methods might miss.
**Learn & Adapt to Threats**
To implement Anomaly-Based Detection, IDPS leverages techniques such as statistical analysis, machine learning, and behavior modeling. These methods enable the system to learn and adapt to evolving threats, making it an invaluable asset for cybersecurity professionals. By continuously monitoring network traffic and system behavior, Anomaly-Based Detection can identify unusual patterns and flag potential threats in real-time.
3. Heuristic Detection: Heuristic detection involves using predefined rules and algorithms to identify potential threats. These rules are based on known attack patterns and can help identify previously unseen attacks. Heuristic detection is a proactive security mechanism that goes beyond traditional signature-based approaches. It identifies potential threats and anomalies by analyzing the behavior of network traffic, files, and system activities. Unlike signature-based detection, which relies on known patterns, heuristics can detect previously unknown and emerging threats, making it a vital component of modern IDPS solutions.
**Deviations from Baseline**
Heuristic detection operates on the principles of anomaly detection and behavior analysis. It establishes a baseline of normal behavior and then identifies deviations from this baseline. By leveraging machine learning algorithms and statistical models, heuristics can identify suspicious activities that may indicate the presence of malicious intent. These algorithms continually evolve and adapt to new threats, enhancing the effectiveness of IDPS solutions.
IDPS: Prevention Mechanisms
In addition to detection, IDPS systems can also take preventive measures to mitigate threats:
1. Intrusion Prevention: IDPS can be configured to actively block or prevent suspicious or malicious traffic from entering the network. This can include blocking specific IP addresses, applying access control policies, or terminating connections.
2. Incident Response: IDPS can trigger automated incident response actions when an intrusion is detected. These actions may include isolating affected systems, initiating forensic data collection, or notifying security personnel.
Related: Before you proceed, you may find the following posts helpful for pre-information:
The Security Landscape
Firewalling & Attack Vectors
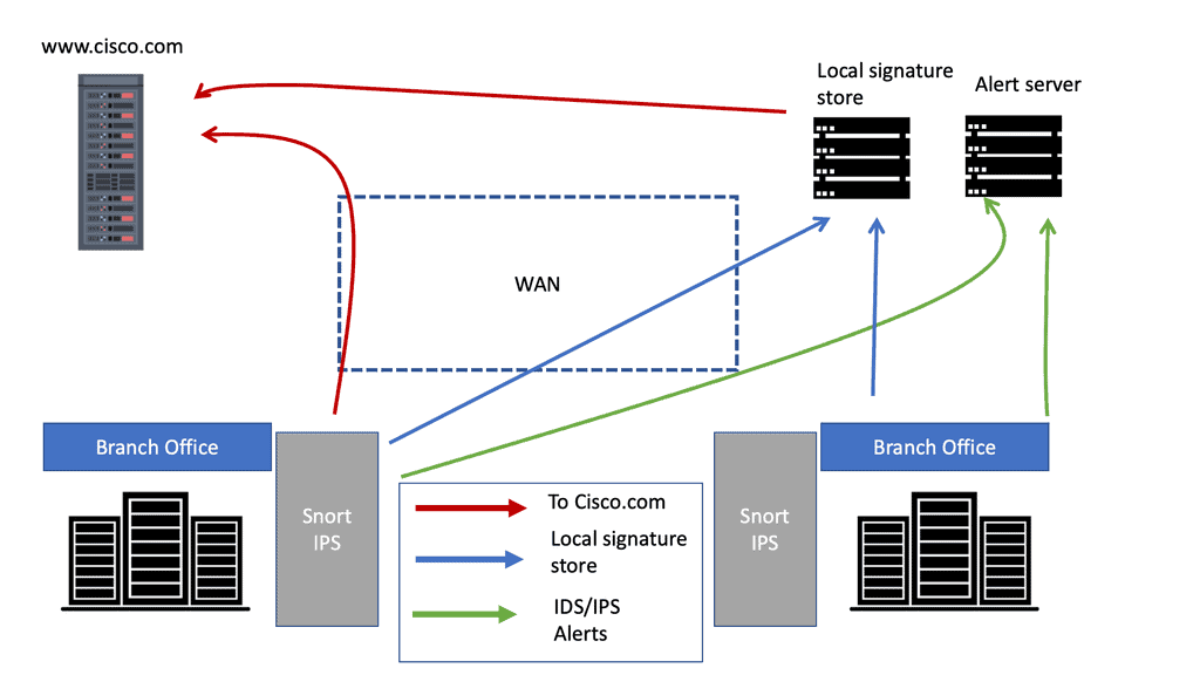
We are constantly under pressure to ensure mission-critical systems are thoroughly safe from bad actors that will try to penetrate your network and attack critical services with a range of attack vectors. So, we must create a reliable way to detect and prevent intruders. Adopting a threat-centric network security approach with the Cisco intrusion prevention system is viable. The Cisco IPS is an engine based on Cisco Snort that is an integral part of the Cisco Firewall, specifically, the Cisco Secure Firewall.
Firewalls have been around for decades and come in various sizes and flavors. The most typical idea of a firewall is a dedicated system or appliance that sits in the network and segments an “internal” network from the “external” Internet.
The traditional Layer 3 firewall has baseline capabilities that generally revolve around the inside being good and the outside being bad. However, we must move from just meeting our internal requirements to meeting the dynamic threat landscape in which the bad actors are evolving.
Firewall Security Zones
There are various firewall security zones, each serving a specific purpose and catering to different security requirements. Let’s explore some common types:
1. DMZ (Demilitarized Zone):
The DMZ is a neutral zone between the internal and untrusted external networks, usually the Internet. It acts as a buffer zone, hosting public-facing services such as web servers, email servers, or FTP servers. By placing these services in the DMZ, organizations can mitigate the risk of exposing their internal network to potential threats.
2. Internal Zone:
The internal zone is the trusted network segment where critical resources, such as workstations, servers, and databases, reside. This zone is typically protected with strict access controls and security measures to safeguard sensitive data and prevent unauthorized access.
3. External Zone:
The external zone represents the untrusted network, which is usually the Internet. It serves as the gateway through which traffic from the external network is filtered and monitored before reaching the internal network. By maintaining a secure boundary between the internal and external zones, organizations can defend against external threats and potential attacks.
Enhancing Network Security
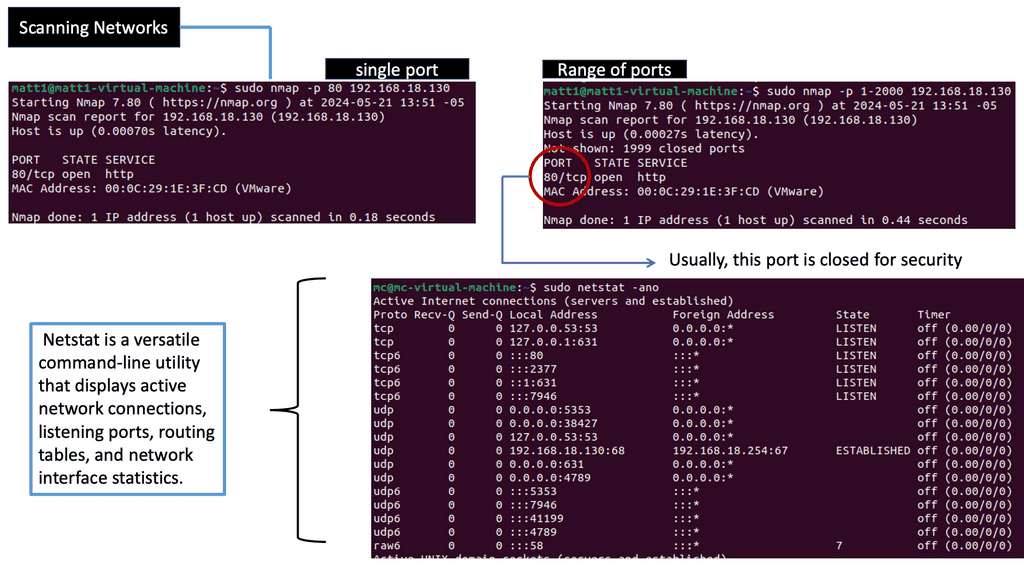
The Importance of Network Scanning
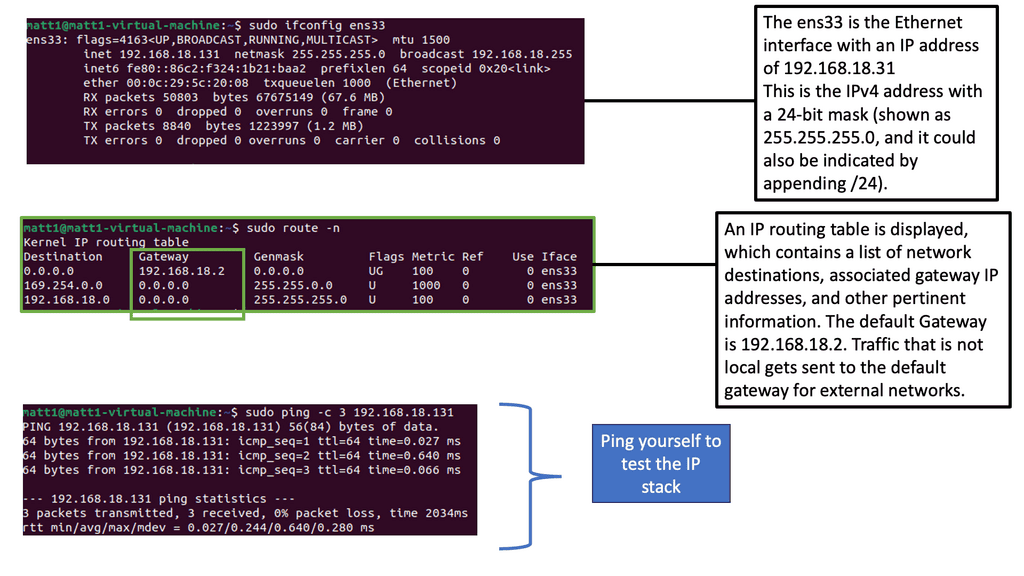
Network scanning is crucial in identifying potential security risks and vulnerabilities within a network infrastructure. Administrators can gain valuable insights into potential weak points that malicious actors may exploit by actively probing and analyzing network devices. It is a proactive approach to fortifying network defenses.
Various techniques are employed for network scanning, each with strengths and purposes. Port scanning allows administrators to identify open ports and services on network devices. Vulnerability scanning focuses on identifying known vulnerabilities in software and firmware versions. Network mapping helps create a comprehensive map of the network infrastructure, aiding in visualization and understanding of the environment.
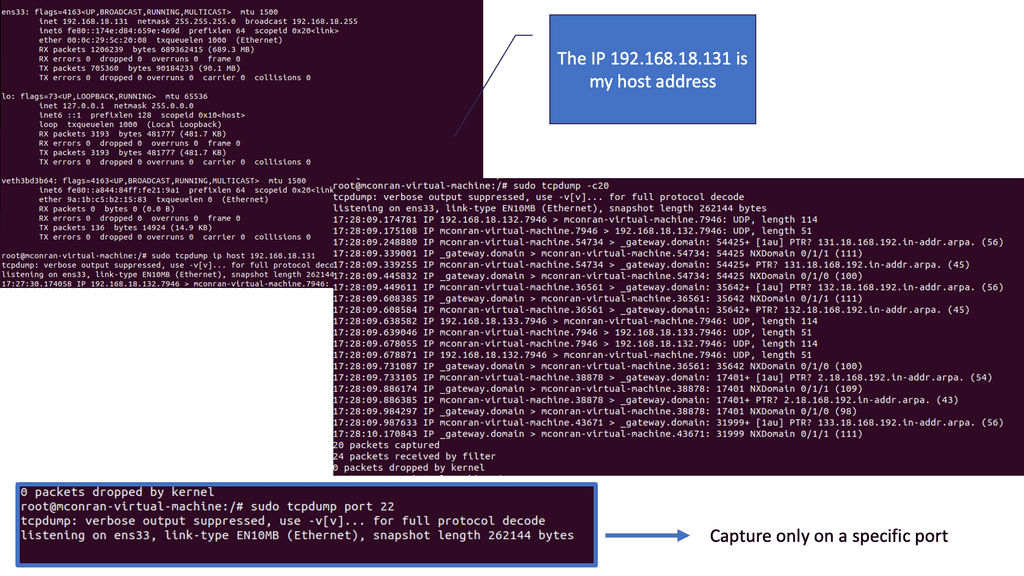
Identifying and Mapping Networks
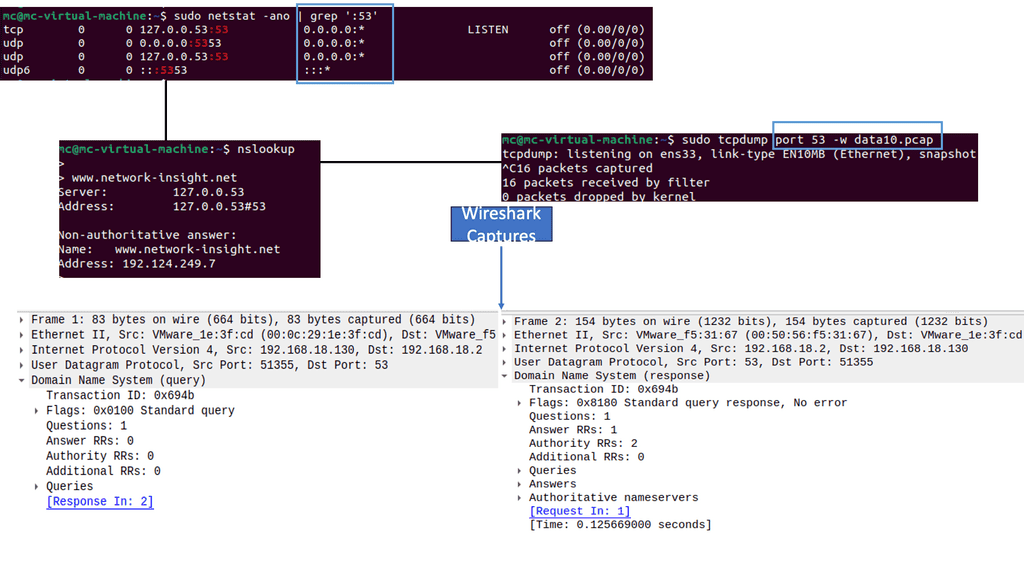
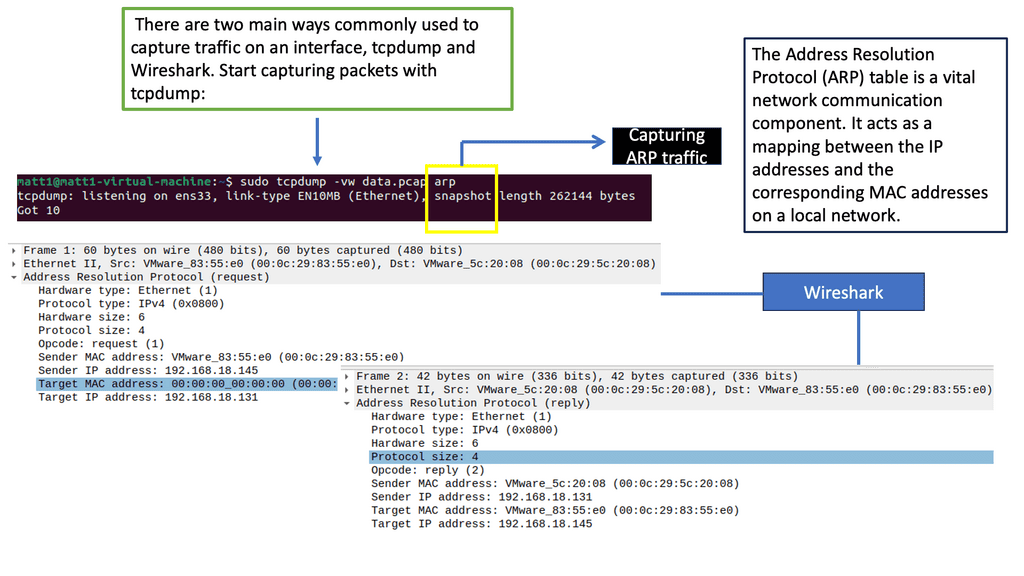
Tcpdump is a widely used tool for capturing and analyzing network packets. It captures packets, traversing a network interface and providing detailed information about each packet. With tcpdump, you can gain insights into the source and destination IP addresses, protocol types, packet size, and more.
To capture packets using tcpdump, you need to specify the network interface to monitor. Once tcpdump runs, it captures real-time packets and displays them on the terminal. You can apply filters to capture specific types of packets or focus on traffic from a particular source or destination. Tcpdump’s flexibility allows for complex filtering options, making it a powerful tool for network analysis.
Wireshark provides extensive protocol dissectors, allowing us to analyze many network protocols. From the ubiquitous HTTP and TCP/IP to more specialized protocols like SIP or DNS, Wireshark unravels the inner workings of each protocol, providing valuable insights into how data is exchanged and potential bottlenecks. We can identify anomalies, detect performance issues, and optimize network configurations by analyzing traffic patterns.
Cisco Security Technologies
A: Cisco Firewall
The Cisco Firewall is a next-generation firewall that provides several compelling threat detection and prevention technologies to the security professional’s toolbox. The Cisco Firewall solution is more than just Firewall Threat Detection (FTD). We have several components that make up the security solution. Firstly, we have the Firewall Management Center (FMC), which is the device that gives you the GUI and configures the policy and operational activities for the FTD. We also include several services.
B: Cisco Secure Endpoint
We have two critical pieces around malware. First, the Cisco Secure Endpoint cloud is a database of known bad and good files and maintains a file hash for all those entries. So, as files pass through the firewall, they can decide on known files. These hashes can be calculated at the line rate, and the Cisco firewall can do quick lookups. This allows you to hold the last packet of the file and determine whether it is good, bad, or unknown.
C: Cisco Secure Malware Analytics
So, we can make a policy by checking the hash if you like. However, you can extract the file if you have not seen it before, and it can be submitted to Cisco Secure Malware Analytics. This is a sandbox technology. The potentially bad file is placed in a VM-type world, and we can get a report with a score sent back. So this is a detection phase and not prevention, as it can take around 15 mins to get the score sent back to us.
These results can then be fed back into the Cisco Secure Endpoint cloud. Now, everyone, including other organizations that have signed up to the Cisco Secure Endpoint cloud, can block this file seen in just one place. So, no data is shared; it’s just the hash. Also, Talos Intel. This is the research organization’s secret source, with over 250 highly skilled researchers. It can provide intelligence such as Indicator of Compromise (IoC), bad domains, and signatures looking for exploits. And this feeds all security products.
D: Cisco IPS
We need several network security technologies that can work together. First, we need a Cisco IPS that provides protocol-aware deep packet inspection and detection, which Cisco Snort can offer and which we will discuss soon. You also need a list of bad IPs, Domains, and file hashes that allow you to tune your policy based on these. For example, for networks that are the source of spam, you want a different response from networks known to host the bad actors C&C.
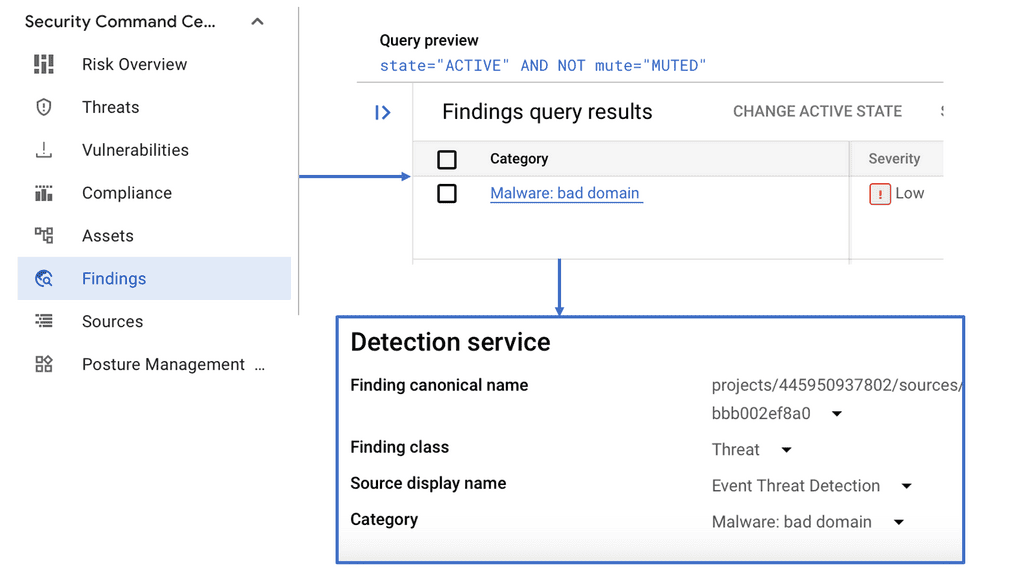
Example Security Technology: Bad Domains with Google
Also, for URL filtering, we think about content filtering in the sense that users should not access specific sites from work. However, the URL is valuable from a security and threat perspective. Often, transport is only over HTTP, DNS is constantly changing, and bad actors rely only on a URL to connect to, for example, a C&C. So this is a threat intelligence area that can’t be overlooked.
We also need to look at file hashing and run engines on the firewall that can identify Malware without sending it to the cloud for checking. Finally, it would help if you also had real-time network awareness and indicators of compromise. The Cisco Firewall can watch all traffic, and you tell us that here are the networks that this firewall protects, and these are the top talkers. Potentially to notice any abnormal behavior.
**Adopting Cisco Snort**
This is where Cisco Snort comes into play. Snort can carry out more or less all of the above with its pluggable architecture. More specifically, Snort 3. Cisco now develops and maintains Snort, known as Cisco Snort. Snort an open-source network intrusion prevention system. In its most straightforward terms, Snort monitors network traffic, examining each packet closely to detect a harmful payload or suspicious anomalies.
Required: Traffic Analysis & Packet Logging
Cisco Snort can perform real-time traffic analysis and packet logging as an open-source prevention system. So, the same engine runs in commercial products as in open-source development. The open-source core engine has over 5 million downloads and 500,000 registered users. Snort is a leader in its field.
Before the Cisco IPS team got their hands on it, Snort was released in 1998, and the program was meant to be a packet logger. You can still download the first version. It has come a long way since then. So Snort is so much more than a Cisco IPS.
Snort 3 is Pluggable
In reality, Snort is a flexible, high-performance packet processing engine. The latest version of Snort 3 is pluggable, so you can add modules to make it adaptable to cover different security aspects. Snort 2 to Snort 3 takes two years to evolve.
With the release of 7, Cisco Secure Firewall Threat Defence introduced Snort 3 on FMC-managed devices. Now, we can have a Snort 3 filter with the Cisco Firewall, rule groups, and rule recommendations. These combined will help you use the Cisco firewall better to improve your security posture.
**Highlighting Snort 2**
So we started with Snort 2, even though Snort 3 has been out for a few years. Sort 2 has 4 primaries or, let’s say, essential components:
- It starts with the decoder, which performs minor decoding once the packers are pulled off the wire. This is what you might see with TCPDump.
- Then, we have the preprocessor Snort 2’s secret sauce. It is responsible for normalization and assembly. Its primary role is to present data to the next component, the detection agent.
- The detection engine is where the Snort rules are, and this is where we process the regulations against the traffic to observe.
- Log module. Based on the rules on traffic, if something is found, we have a log module enabling you to create a unified alert.
**Snort Rule tree**
When Snort looks like a rule set, it doesn’t start at the top and run a packet through; it breaks it up into what is known as rule trees based on, for example, source port or destination port. So, when it comes to a rule to evaluate a packet, a packet only goes through a few rules. So, Cisco Snort, which provides the Cisco IPS for the Cisco Firewall, is efficient because it only needs to enable packets through the rules it might be appropriate for.
Knowledge check for Packet Sniffing
Capturing network traffic is often a task during a penetration testing engagement or while participating in a bug bounty. One of the most popular packet capture tools (sniffer) is Wireshark. If you are familiar with Linux, you know about another lightweight but powerful packet-capturing tool called tcpdump. The packet sniffing process involves a cooperative effort between software and hardware. This process can be broken down into three steps:
1. Collection: The packet sniffer collects raw binary data from the wire. Generally, this is accomplished by switching the selected network interface into promiscuous mode. In this mode, the network card can listen to all traffic on a network segment, not only the traffic addressed.
2. Conversion: The captured binary data is converted into readable form. This is as far as most developed command-line packet sniffers can go. The network data can be interpreted fundamentally at this point, leaving most of the analysis to the end user.
3. Analysis: Finally, the packet sniffer analyzes the captured and converted data. Based on the information extracted, the sniffer verifies the protocol of the captured network data and begins analyzing that protocol’s distinguishing features.
**Highlighting Snort 3**
Then, we have a new edition of Cisco IPS. Snort 3.0 is an updated version with a unique design and a superset of Snort 2. Snort 3 includes additional functionality that improves efficacy, performance, scalability, usability, and extensibility. In addition, Snort 3 aimed to address some of the limitations of Snort 2.
For example, Snort 2 is packet-based, so it’s a packet sniffer per packet. So it would help if you built in statefulness and awareness of fragments and the fact that HTTP GET’s boundaries are not packet boundaries, which can spread over multiple packets.
Snort 3 Features:
A: – HTTP Protocol Analyzer
Snort 3 has a good HTTP protocol analyzer that can detect HTTP running over any port. Many IPS providers only look at 80, 8080, and 442. However, HTTP over any port other than the Cisco IPS assumes it is TCP. However, based on Cisco Snort, Cisco IPS can detect HTTP over any port. Now that it knows HTTP, Snort can’t set up different pointers in the other parts of the packet. So when you get to the IPS rules section looking for patterns, you don’t need to do the lookup and calculation again, which is essential when you are going at a line rate.
B: – Snort is pluggable
Also, within the Cisco firewall, Cisco Snort is pluggable and does much more than protocol analysis. It can perform additional security functions and make network discovery, a type of passive detection. Along with advanced malware protection and application identification, not by ports and protocols but by deep packet inspection. Now, you can have a policy based on the application. An identity engine can also map users to IP, allowing identity-based firewalling. So, Cisco Snort does much of the heavy lifting for the Cisco Firewall.
**Snort 2 architecture: The issues**
Snort 3 has a modern architecture for handling all of the Snort 2 packet-based evasions. It also supports HTTP/2, whereas Snort 2 only supports HTTP/1. The process architecture is the most meaningful difference between Snort 2 and Snort 3. To go faster in Snort 2, you put more Snorts running on the box. Depending on the product, a connection arrives and is hashed based on a 5-tuple or a 6-tuple. I believe 5tuple is for open-source products, and 6tuple is for commercial products.
Connections on the same hash go to the same CPU. To improve Snort 2 performance, if you had a single CPU on a box, you add another Snort CPU and get double the performance with no overhead. Snort 2 works with multiple Snort processes, each affiliated with an individual CPU core, and within each Snort process, there is a separate thread for management and data handling.
But we are loading Snorts over and over again. So, we have linear scalability, which is good, but duplicated memory structure is bad. So every time we load Cisco Snort, we load the rules, and everything runs in their isolated world.
**Snort 3 architecture: Resolving the issues**
On the other hand, Snort 3 is multi-threaded, unlike Snort 2. This means we have one control thread and multiple packet threads. The packet arrives at the control thread, and we have the same connection hashing with 5-tuple or 6-tuple. Snort 3 only runs on one process, with each thread affiliated with individual CPU cores, backed by one control thread that handles data for all packet-processing threads. The connections are still pinned to the core, but they are packet threads, and each one of these packet threads is running on its CPU, but they share the control thread, and this shares the rules.
The new Snort 3 architecture eliminates the need for a control thread per process and facilitates configuration/data sharing among all threads. As a result, less overhead is required to orchestrate the collaboration among packet-processing threads. We get better memory utilization and reloads are much faster.
A) Snort 3 inspectors
Snort 3 has inspectors now. In Snort 2, we had pre-processors. We have an HTTP inspector instead of a pre-processor. Packets are processed differently in Snort 3 than in Snort 2. So, in Snort 2, the packet comes linearly in specific steps. This was done with a preprocessing stage.
What has to happen is that the packet has to go through, and every field of the packet will be decoded. And if this is HTTP, they will look at the GET, the body, and the header, for example. All of this will be decoded in case a rule needs that data. In the case of RPC, there are so many fields in an RPC packet. So, it could decode fields in the packet that a rule never needs. So, you need to save time in decoding the data.
B) Parallel resource utilization
On the other hand, Snort 3 uses what is known as parallel resource utilization. We have plugins and a publish and subscribe model in the packet inspection process. So, when it looks at a packet, there are things it can decode. When the packet gets to the rule, the rule might say that it needs the body and not any other fields. Then, the body will only be decoded. This is referred to as just in time instead of just in case. You don’t waste time if any fields in the packet must be translated.
C) Rules Group Security Levels.
With Snort 2 regarding rule sets, you have only a few options. For example, you can pick no rules active-based policy, which is not recommended. There is also a connection-based rule set ( connectivity over security). We also have balanced security and connectivity. Then, we have protection over the connectivity rules that are set. With Snort 3, you will get more than just these policy sets. We have rule groups that we can use to set the security levels individually. So, the new feature is Rule Groups, making it easier to adjust your policy.
With rule groups, we can assign security levels to each sub-group. You can adjust based on your usage, such as a more aggressive rule set for Chrome or not for Internet Explorer. The security level can be set on a per-group basis. However, Snort 2 offers this only in the base policy.
- Level 1 – Connectivity over Security
- Level 2 – Balanced Security and Connectivity
- Level 3 – Security over connectivity
- Level 4 – Maximum Detection
Now, there is no need to set individual rule states. We have levels that equate to policy. With Snort 2, you would have to change the entire base policy, but with Snort 3, we can change the groups related to the rule set. What I like about this is the trade-off so you can have rules, for example, for the browser, that are not common on your network but still exist.
Summary: Cisco Firewall and IPS
In today’s rapidly evolving digital landscape, cybersecurity is of paramount importance. With increasing cyber threats, organizations must employ robust security measures to safeguard their networks and sensitive data. One such solution that has gained immense popularity is the Cisco Firewall and IPS (Intrusion Prevention System). This blog post dived deep into Cisco Firewall and IPS, exploring their capabilities, benefits, and how they work together to fortify your network defenses.
Understanding Cisco Firewall
Cisco Firewall is a formidable defense mechanism that acts as a barrier between your internal network and external threats. It carefully inspects incoming and outgoing network traffic, enforcing security policies to prevent unauthorized access and potential attacks. By leveraging advanced technologies such as stateful packet inspection, network address translation, and application-level filtering, Cisco Firewall provides granular control over network traffic, allowing only legitimate and trusted communication.
Exploring Cisco IPS
On the other hand, Cisco IPS takes network security to the next level by actively monitoring network traffic for potential threats and malicious activities. It uses a combination of signature-based detection, anomaly detection, and behavior analysis to identify and mitigate various types of attacks, including malware, DDoS attacks, and unauthorized access attempts. Cisco IPS works in real-time, providing instant alerts and automated responses to ensure a proactive defense strategy.
The Power of Integration
While Cisco Firewall and IPS are powerful, their true potential is unleashed when they work together synchronously. Integration between the two enables seamless communication and sharing of threat intelligence. When an IPS identifies a threat, it can communicate this information to the Firewall, immediately blocking the malicious traffic at the network perimeter. This collaborative approach enhances the overall security posture of the network, reducing response time and minimizing the impact of potential attacks.
Benefits of Cisco Firewall and IPS
The combined deployment of Cisco Firewall and IPS offers numerous benefits to organizations. Firstly, it provides comprehensive visibility into network traffic, allowing security teams to identify and respond to threats effectively. Secondly, it offers advanced threat detection and prevention capabilities, reducing the risk of successful attacks. Thirdly, integrating Firewall and IPS streamlines security operations, enabling a proactive and efficient response to potential threats. Lastly, Cisco’s continuous research and updates ensure that Firewalls and IPS remain up-to-date with the latest vulnerabilities and attack vectors, maximizing network security.
Conclusion:
In conclusion, the Cisco Firewall and IPS duo are formidable forces in network security. By combining the robust defenses of a Firewall with the proactive threat detection of an IPS, organizations can fortify their networks against a wide range of cyber threats. With enhanced visibility, advanced threat prevention, and seamless integration, Cisco Firewall and IPS empower organizations to stay one step ahead in the ever-evolving cybersecurity landscape.