Blog
Network Insight.
- Premium Consultancy, Ebooks, Videos and Elearning
Data Center Failure
Data Center Failure In today’s data-driven world, the uninterrupted availability of data is crucial for businesses. Data center storage failover plays a vital role in ensuring continuous access to critical information. In this blog post, we will explore the importance of data center storage failover, its key components, implementation strategies, …
Data Center Failover
Data Center Failover In today’s digital age, data centers play a vital role in storing and managing vast amounts of critical information. However, even the most advanced data centers are not immune to failures. This is where data center failover comes into play. This blog post will explore what data …
GTM Load Balancer
GTM Load Balancer In today’s fast-paced digital world, websites and applications face the constant challenge of handling high traffic loads while maintaining optimal performance. This is where Global Traffic Manager (GTM) load balancer comes into play. In this blog post, we will explore the key benefits and functionalities of GTM …
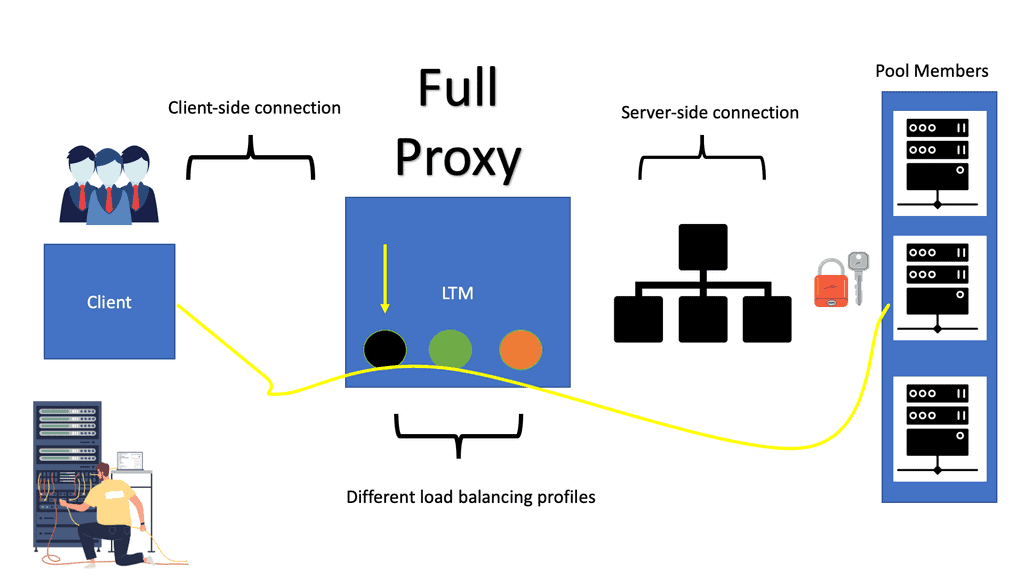
Full Proxy
Full Proxy In the vast realm of computer networks, the concept of full proxy stands tall as a powerful tool that enhances security and optimizes performance. Understanding its intricacies and potential benefits can empower network administrators and users alike. In this blog post, we will delve into the world of …
IPv6 Fragmentation
IPv6 Fragmentation In the vast landscape of networking and internet protocols, IPv6 stands as a crucial advancement. With its expanded address space and improved functionality, IPv6 brings numerous benefits. However, one aspect that requires attention is IPv6 fragmentation. In this blog post, we will dive deep into the intricacies of …
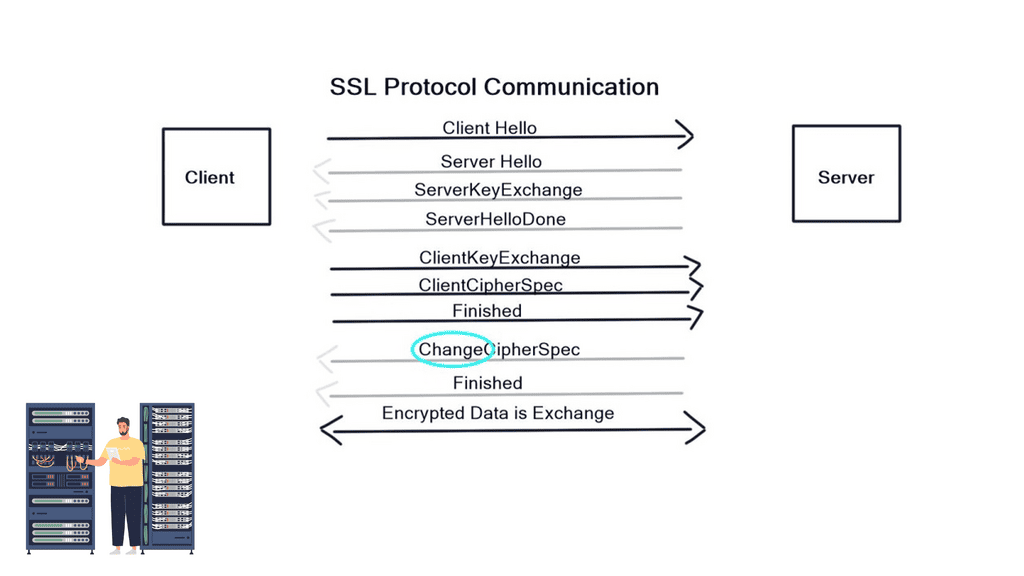
SSL Security
SSL Security In today’s digital age, ensuring online security has become paramount. One crucial aspect of protecting sensitive information is SSL (Secure Sockets Layer) encryption. In this blog post, we will explore what SSL is, how it works, and its significance in safeguarding online transactions and data. SSL, or Secure …
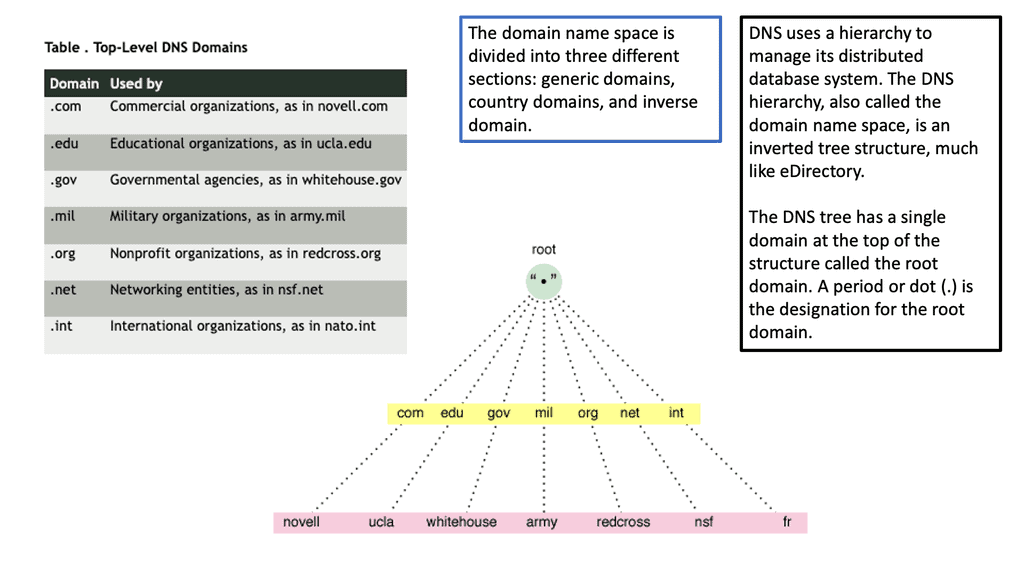
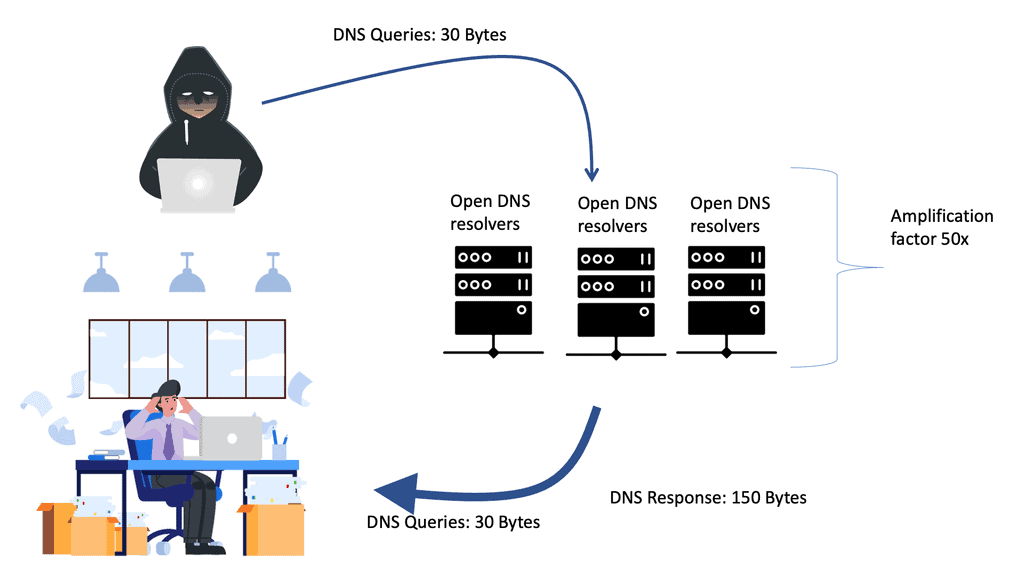
DNS Reflection Attack
DNS Reflection attack In today’s interconnected world, cyber threats continue to evolve, posing significant risks to individuals, organizations, and even nations. One such threat, the DNS Reflection Attack, has gained notoriety for its potential to disrupt online services and cause significant damage. In this blog post, we will delve into …
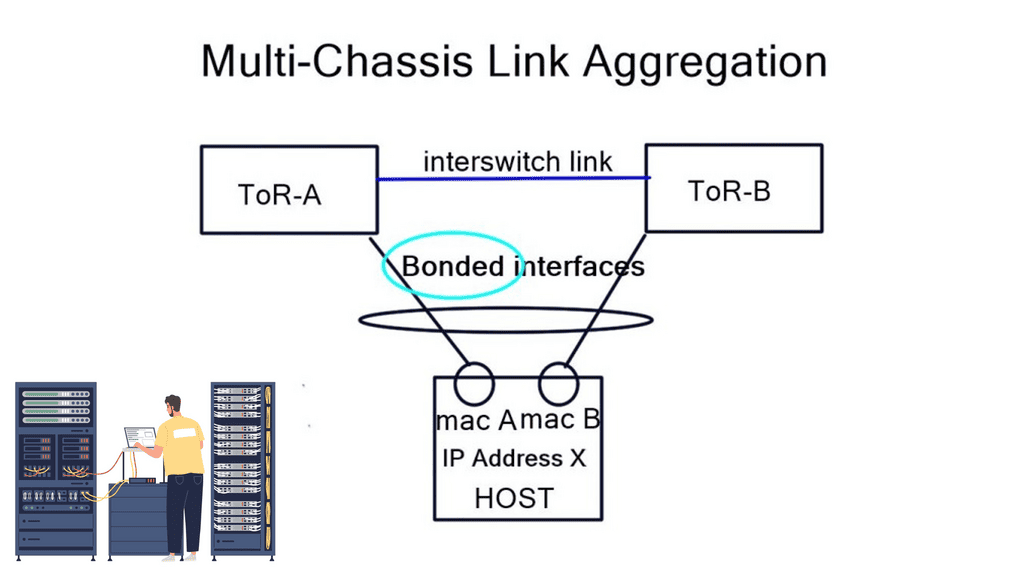
Layer-3 Data Center
Layer 3 Data Center In today’s digital age, data centers play a crucial role in powering our interconnected world. Among various types of data centers, layer 3 data centers stand out for their advanced network capabilities and efficient routing techniques. In this blog post, we will embark on a journey …
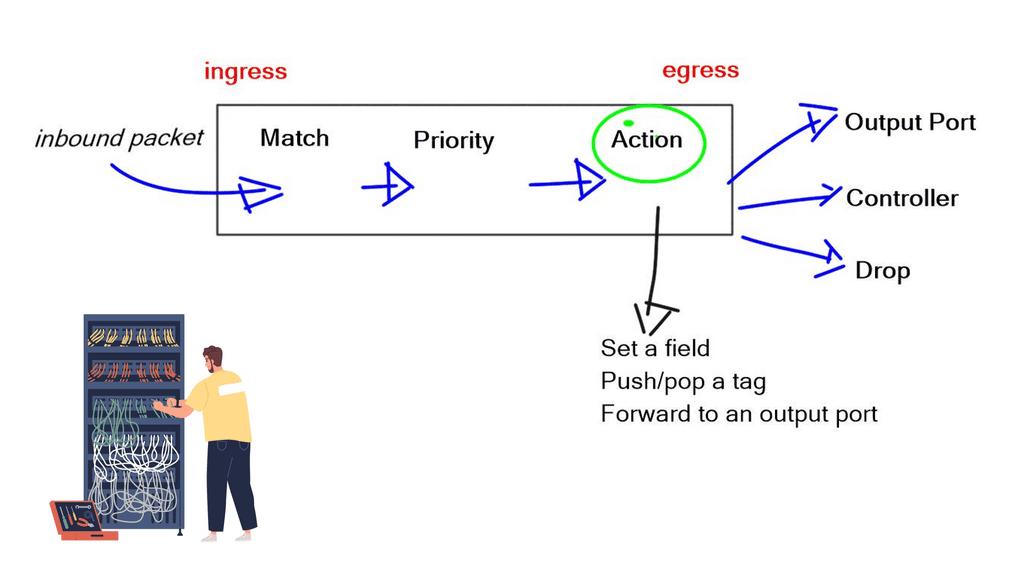
OpenFlow Protocol
OpenFlow Protocol The world of networking has witnessed remarkable advancements, and one of the key contributors to this progress is the OpenFlow protocol. In this blog post, we will dive into the depths of OpenFlow, exploring its principles, benefits, and impact on the networking landscape. OpenFlow, at its core, is …
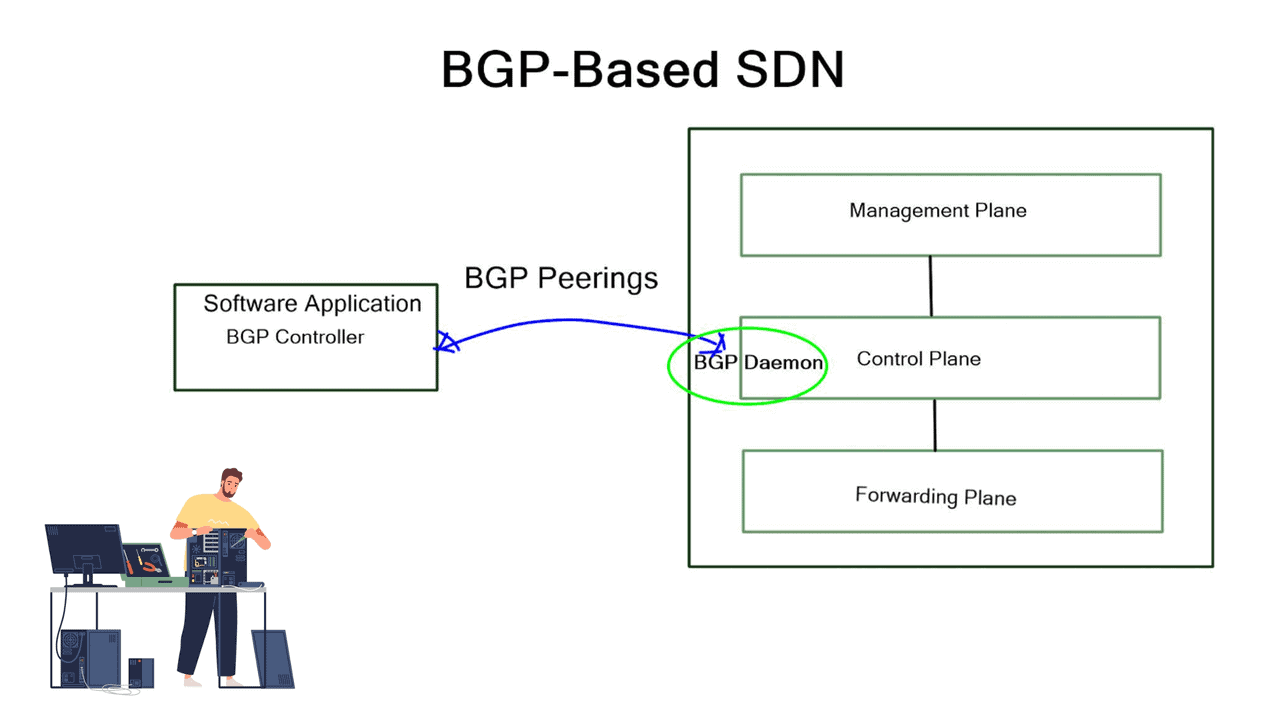
BGP has a new friend – BGP-Based SDN
BGP-Based SDN The world of networking continues to evolve rapidly, with new technologies and approaches emerging to meet the growing demands of modern communication. Two such technologies, BGP (Border Gateway Protocol) and SDN (Software-Defined Networking), have gained significant attention for their impact on network flexibility and management. In this blog …
Neutron Networks
Neutron Networks In today’s digital age, connectivity has become essential to our personal and professional lives. As the demand for seamless and reliable network connections grows, businesses seek innovative solutions to meet their networking needs. One such solution that has gained significant attention is Neutron Networks. In this blog post, …
Network Traffic Engineering
Network Traffic Engineering In today’s interconnected world, network traffic engineering plays a crucial role in optimizing the performance and efficiency of computer networks. This blog post aims to provide a comprehensive overview of network traffic engineering, its importance, and the techniques used to manage and control traffic flow. Network traffic …