DNS Security Solutions
In today's interconnected digital world, ensuring the security of your online presence is of paramount importance. One crucial aspect often overlooked is Domain Name System (DNS) security. In this blog post, we will delve into the world of DNS security solutions, exploring their significance, benefits, and implementation.
Before we dive into the realm of DNS security solutions, let's first understand what DNS is. The Domain Name System serves as the phonebook of the internet, translating domain names into IP addresses. It plays a pivotal role in facilitating online communication and accessibility.
With the increasing number of cyber threats and attacks, DNS security has become a critical concern for individuals and organizations alike. This section will shed light on the importance of safeguarding your DNS infrastructure, highlighting the potential risks and vulnerabilities associated with a compromised DNS.
DNS Filtering: DNS filtering is an effective solution that helps prevent access to malicious websites and content. By blocking requests to known malicious domains, it reduces the risk of malware infections and data breaches.
DNSSEC: DNS Security Extensions (DNSSEC) ensure the integrity and authenticity of DNS responses, mitigating the risk of DNS spoofing and cache poisoning attacks.
DDoS Protection: Distributed Denial of Service (DDoS) attacks can wreak havoc on your online presence. DNS security solutions equipped with robust DDoS protection mechanisms help mitigate the impact of such attacks, ensuring uninterrupted DNS services.
Implementing DNS security solutions requires meticulous planning and adherence to best practices. This section will provide insights into the implementation process, including considerations for choosing the right DNS security provider, configuring DNS settings, and ongoing monitoring and updates.
Investing in DNS security solutions yields numerous benefits. From enhanced online privacy and reduced downtime to improved user experience and brand reputation, this section will outline the tangible benefits and return on investment that organizations can achieve by prioritizing DNS security.
DNS security solutions are a crucial component of a comprehensive cybersecurity strategy. By safeguarding your DNS infrastructure, you can protect your online presence, mitigate potential threats, and ensure uninterrupted connectivity for your users. Stay proactive, stay secure!Matt Conran
Highlights: DNS Layer Security
Understanding DNS Layer Security
DNS, or Domain Name System, is the backbone of the internet, responsible for translating human-readable domain names into machine-readable IP addresses. DNS layer security focuses on protecting this crucial layer from cyber threats, ensuring the availability, integrity, and confidentiality of DNS infrastructure and communications.
The significance of DNS layer security cannot be overstated. Cybercriminals often exploit vulnerabilities within DNS infrastructure to launch various attacks, such as DNS hijacking, DNS amplification, and DNS tunneling. By compromising DNS, attackers can redirect users to malicious websites, intercept sensitive information, or disrupt network operations. Implementing robust DNS layer security measures is vital for organizations to safeguard their networks and maintain trust with their users.
Techniques for DNS Layer Security:
DNSSEC: Domain Name System Security Extensions (DNSSEC) is a set of cryptographic protocols that add an extra layer of security to DNS. By digitally signing DNS data, DNSSEC ensures the authenticity and integrity of DNS responses, making it difficult for attackers to manipulate DNS records.
DNS Filtering: DNS filtering involves implementing policies to block access to malicious or unauthorized domains. By utilizing threat intelligence and real-time analysis, organizations can prevent users from accessing known malicious websites, reducing the risk of malware infections and data breaches.
Traffic Monitoring and Analysis: Regularly monitoring DNS traffic can help detect anomalies and identify potential threats. Analyzing DNS query patterns and investigating suspicious activities can allow organizations to proactively respond to threats, mitigating potential attacks before they cause significant damage.
**No Security By Default**
This post will outline the domain name system: the DNS structure, the vulnerabilities and abuses of DNS security designs, and guidance on implementing DNS protection with examples of DNS security solutions with Cisco, like Cisco Umbrella DNS. Unfortunately, like many Internet protocols, the DNS system was designed without security in mind and contained several security limitations regarding privacy, integrity, and authenticity.
**Constant Security Threats**
These security constraints, combined with bad actors’ technological advances, make DNS servers vulnerable to a broad spectrum of attacking DNS vectors, including DNS Reflection attack, DNS tunneling, DoS (Denial of Service), or the interception of private personal information via means of data exfiltration via the DNS protocol. As you can presume, this causes the DNS layer to be an excellent avenue for bad actors to operate when penetrating networks and exfiltrating data.
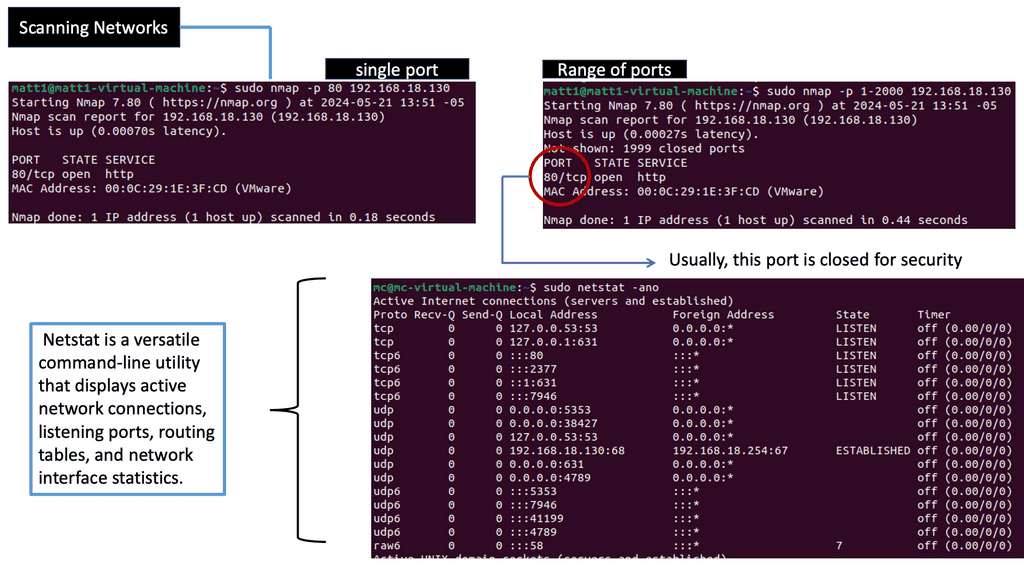
Network Scanning for DNS Threats
Network scanning is the process of identifying active hosts, open ports, and services within a network. By examining the network’s structure and mapping its assets, organizations comprehensively understand their digital environment. This knowledge serves as a foundation for effective security management and risk assessment.
There are several types of network scans, each serving a specific purpose. The most common ones include:
1. Port Scanning: This technique identifies open ports on network devices, allowing administrators to evaluate potential entry points for malicious activities.
2. Vulnerability Scanning: By actively searching for weaknesses and vulnerabilities in network systems, vulnerability scanning helps organizations identify areas that require immediate attention and patching.
3. Network Mapping: Network mapping involves visualizing the network’s structure, providing valuable insights into its topology, and facilitating efficient network management.
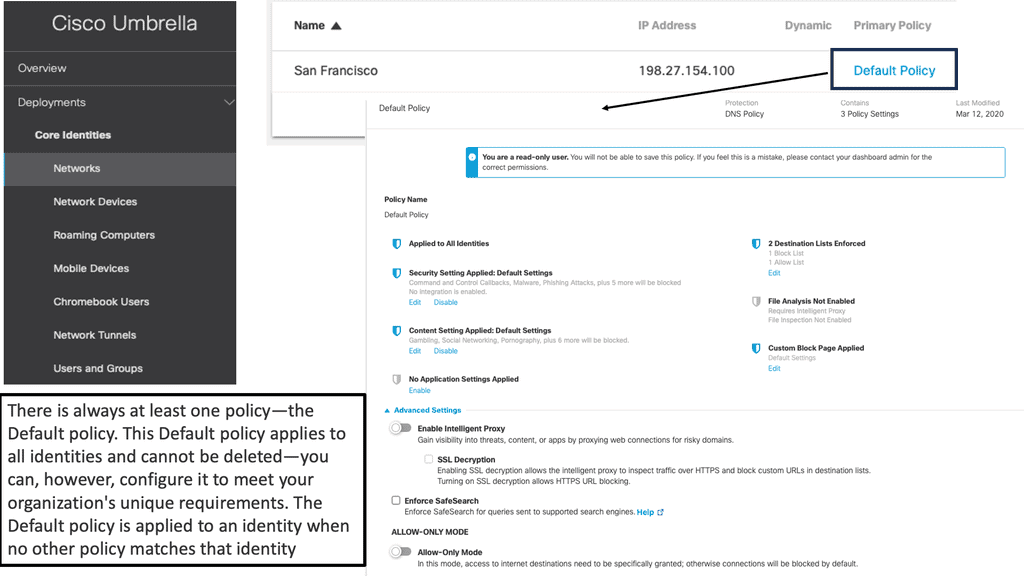
 Example Product: Cisco Umbrella
Example Product: Cisco Umbrella
DNS security involves implementing measures to protect the integrity and availability of DNS services. This includes monitoring DNS queries for suspicious activity, blocking access to known malicious domains, and ensuring that DNS responses are authentic and untampered.
### The Power of Cisco Umbrella
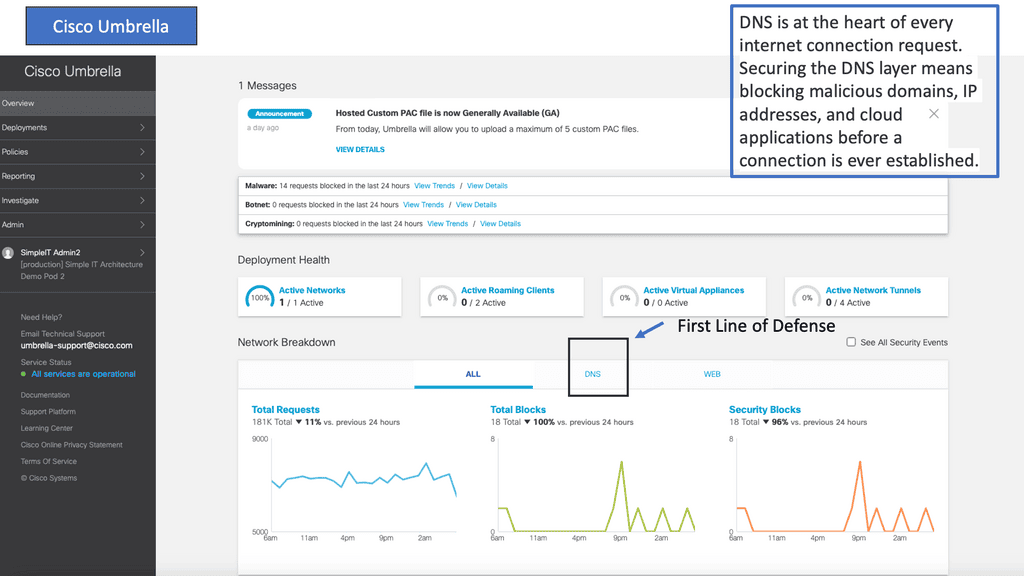
Cisco Umbrella is a cloud-delivered security platform that provides a first line of defense against threats on the internet. By leveraging the vast intelligence of Cisco’s global network, Umbrella offers comprehensive protection through advanced DNS security measures. It automatically blocks malicious domains, IP addresses, and URLs before they can reach your network or endpoints.
One of the standout features of Cisco Umbrella is its ability to provide threat intelligence and visibility across all internet activity. This ensures that you not only block current threats but also gain insights into potential vulnerabilities and attack vectors. Moreover, being cloud-based, Cisco Umbrella is both scalable and easy to deploy, making it an ideal choice for organizations of all sizes.
### Key Benefits for Organizations
Implementing Cisco Umbrella’s DNS security can yield numerous benefits for organizations:
1. **Improved Protection**: By blocking threats at the DNS layer, Cisco Umbrella stops attacks before they reach your network, reducing the risk of data breaches and system compromises.
2. **Enhanced Visibility**: Gain real-time insights into internet activity, helping you identify and respond to potential threats swiftly.
3. **Simplified Management**: As a cloud-based solution, Cisco Umbrella requires no hardware installations, making it easy to manage and scale according to organizational needs.
4. **Reduced Latency**: With multiple data centers around the world, Cisco Umbrella ensures fast and reliable DNS resolution, improving overall internet performance.
Cloud DNS Solutions
Google Cloud DNS Security Solutions
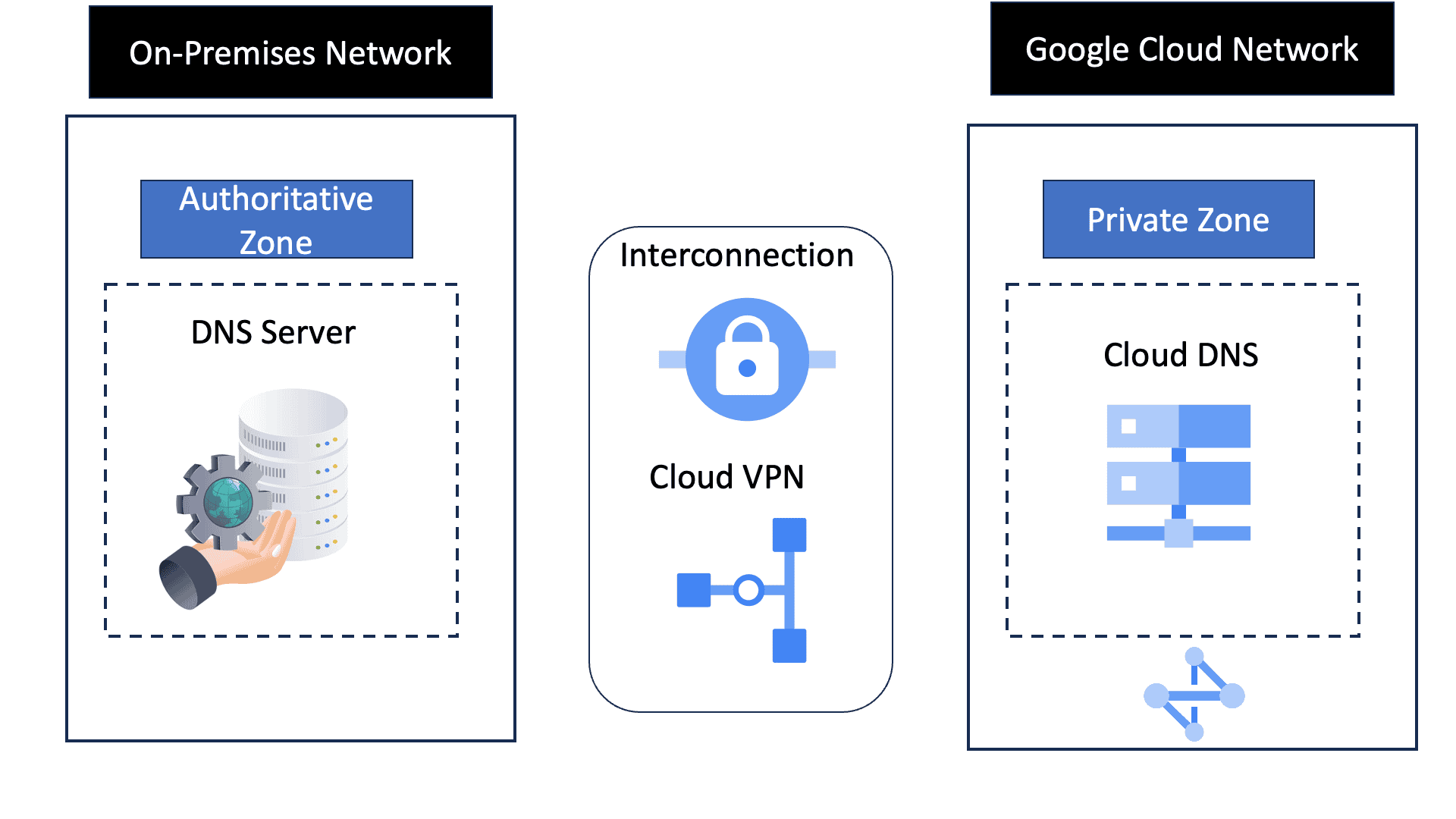
Google Cloud DNS is a scalable, reliable, and managed authoritative Domain Name System (DNS) service running on the same infrastructure as Google. It translates domain names like www.example.com into IP addresses that computers use to connect to each other. By leveraging Google Cloud DNS, businesses can ensure their websites and applications are accessible to users globally, with minimal delay and maximum uptime.
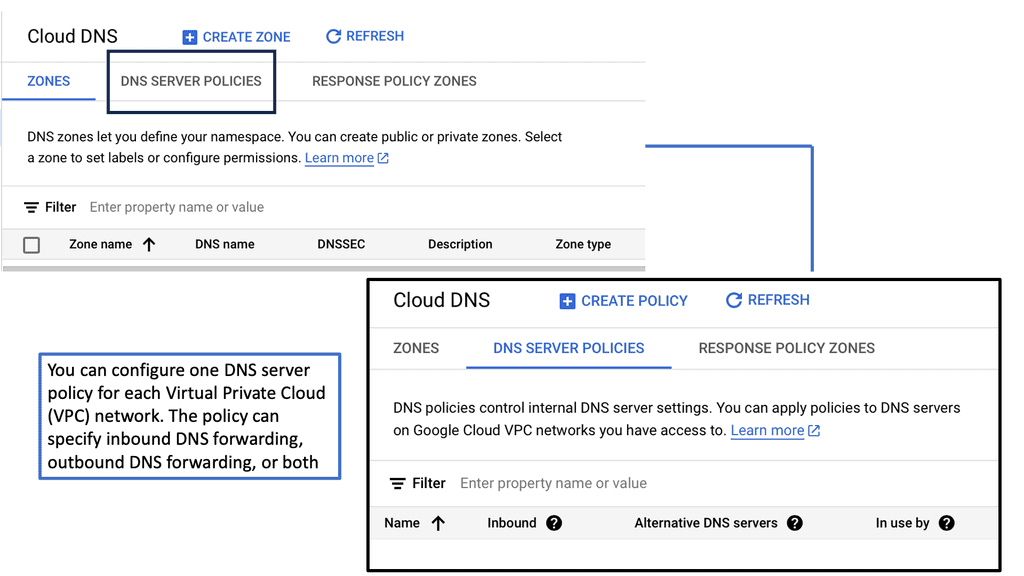
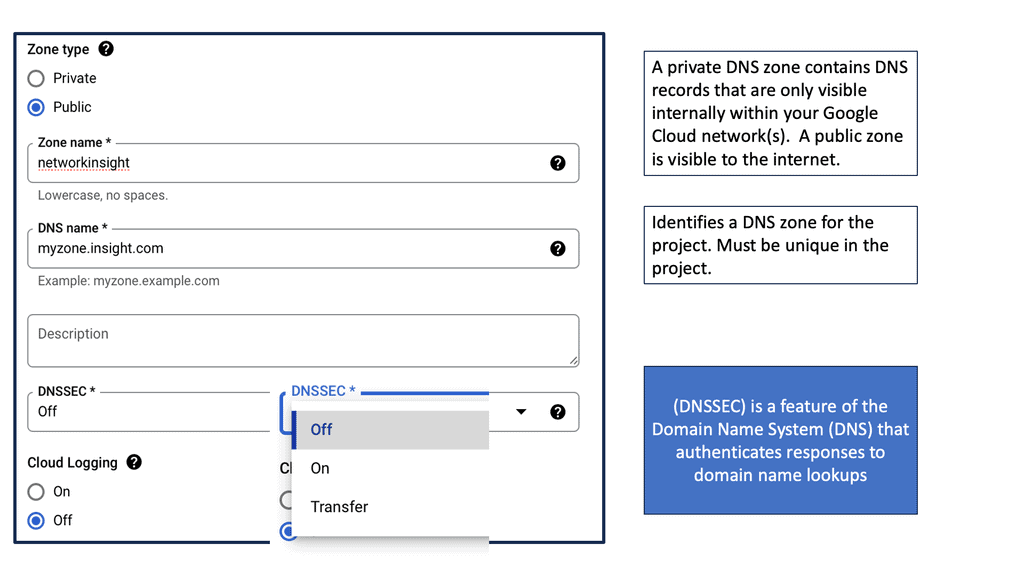
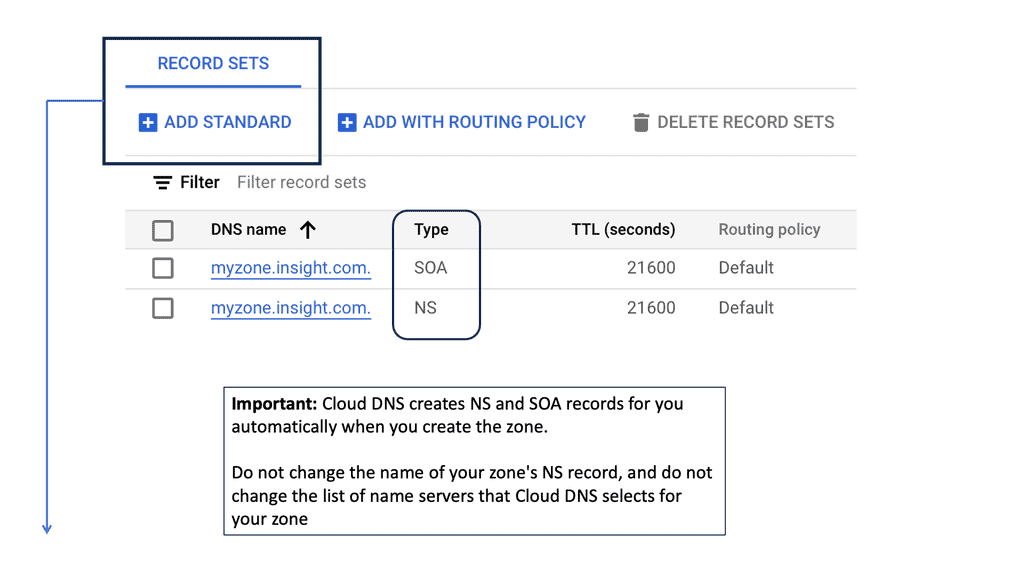
Key features of Google Cloud DNS include support for all common DNS record types, including A, AAAA, CNAME, MX, and more. It also offers features like DNSSEC for security, private DNS zones for internal networks, and logging to monitor and diagnose issues.
Google Cloud DNS offers a variety of security features to protect your DNS infrastructure:
1. **DNSSEC (Domain Name System Security Extensions):** Google Cloud DNS supports DNSSEC, which adds an additional layer of security by enabling DNS responses to be verified. This ensures that users are directed to the legitimate website without interference from malicious actors.
2. **Private DNS Zones:** By using private DNS zones, you can limit DNS resolution within your virtual private cloud (VPC) network, enhancing security by preventing external exposure of sensitive internal DNS records.
3. **Integration with Cloud IAM:** Google Cloud Identity and Access Management (IAM) allows you to manage access to your DNS resources with fine-grained, role-based controls. This ensures that only authorized individuals can make changes to DNS configurations.
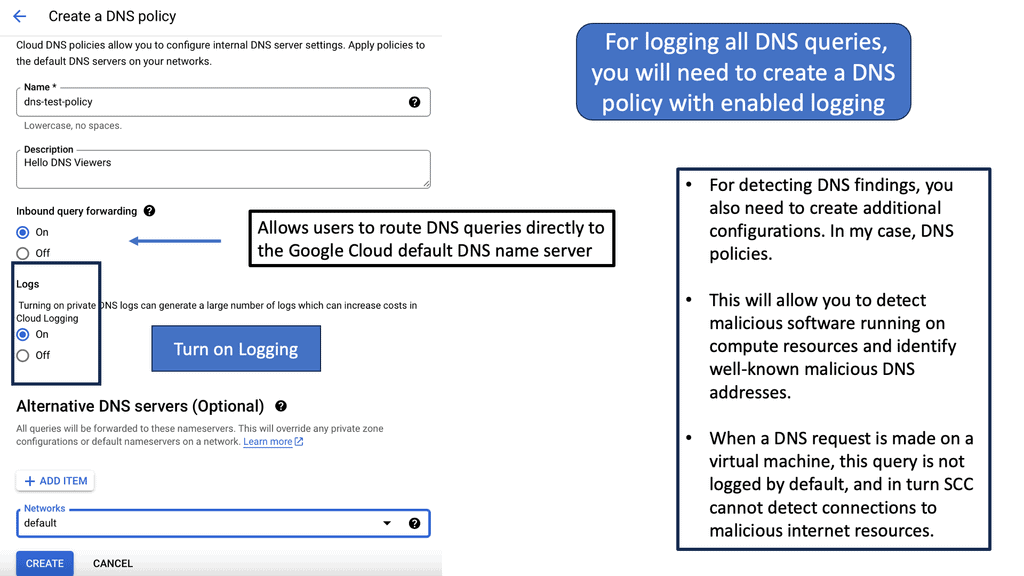
4. **Logging and Monitoring:** Google Cloud DNS integrates with Cloud Logging and Cloud Monitoring, providing real-time insights into DNS query patterns and potential security threats. This enables proactive monitoring and rapid response to suspicious activities.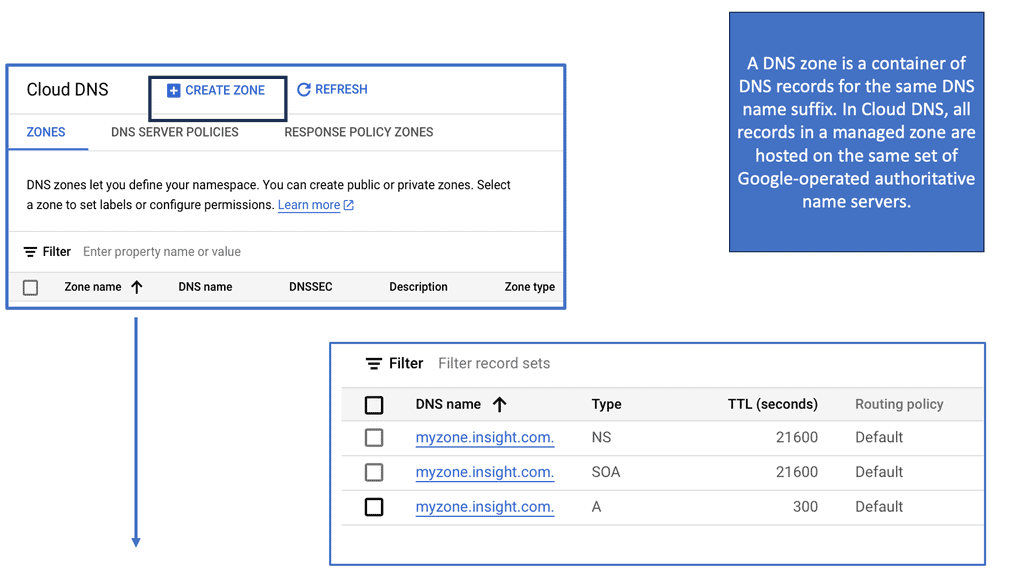
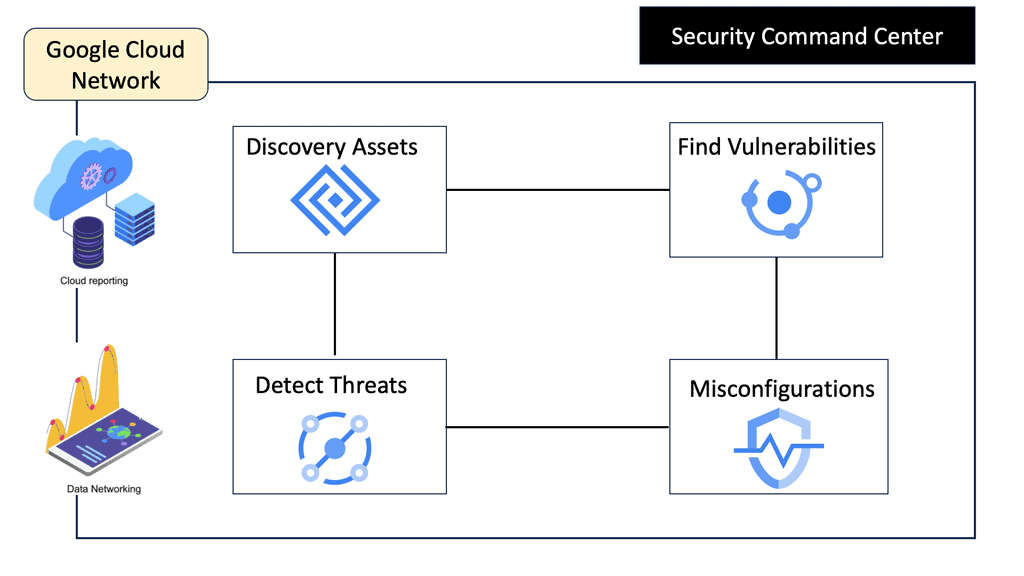
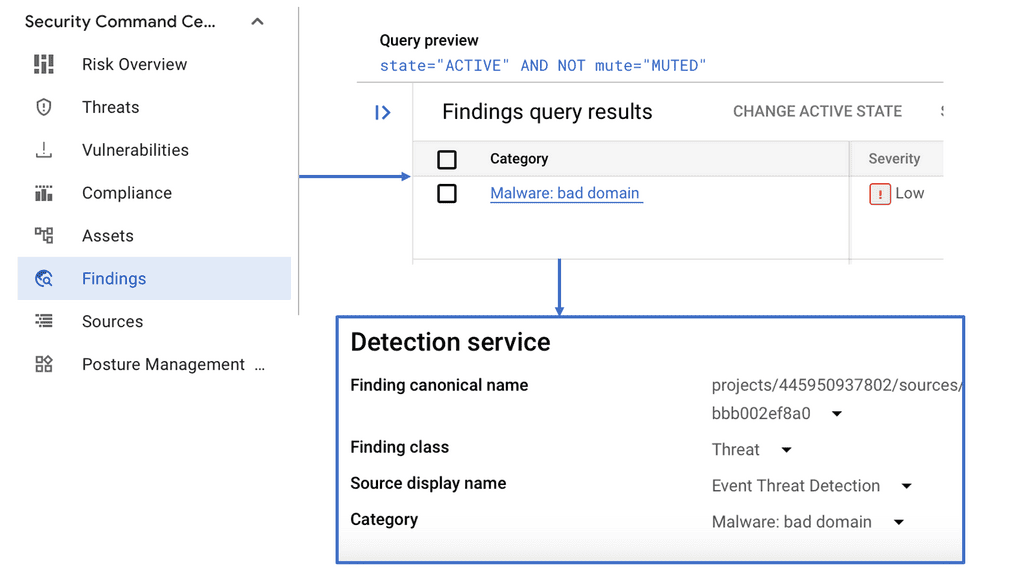
**Understanding Google Cloud’s Security Command Center**
Google Cloud’s Security Command Center (SCC) acts as a centralized dashboard, providing visibility into your cloud assets and their security posture. It integrates seamlessly with Google Cloud, offering real-time detection of vulnerabilities, misconfigurations, and threats. By leveraging Google’s extensive threat intelligence, SCC empowers organizations to proactively manage and mitigate security risks before they escalate.
**The Role of DNS Security in Threat Detection**
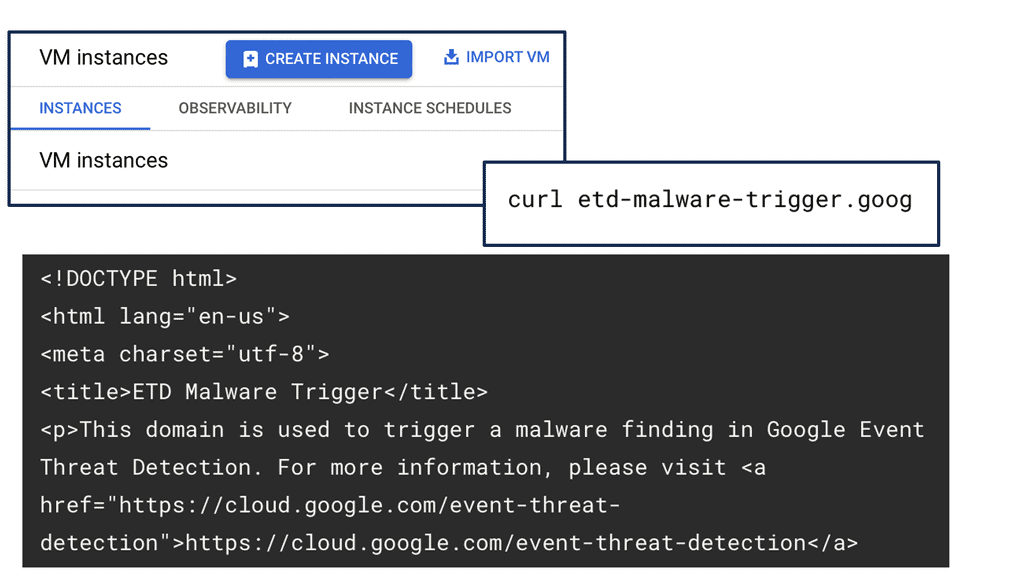
DNS Security is a crucial component of SCC, offering an additional layer of protection. By monitoring DNS traffic, SCC can identify suspicious activities indicative of potential threats, such as data exfiltration or communication with known malicious domains. This proactive approach allows organizations to swiftly respond to emerging threats, minimizing potential damage and ensuring business continuity.
**Investigative Capabilities: Unearthing Hidden Threats**
SCC’s investigative capabilities are instrumental in unearthing hidden threats within your cloud environment. With features like anomaly detection and threat hunting, security teams can delve deep into suspicious activities, tracing their origins and assessing their impact. This level of insight is invaluable for crafting effective response strategies, ensuring threats are neutralized efficiently and effectively.
**Maximizing Security with Best Practices**
To maximize the benefits of SCC, organizations should adopt best practices such as regular security assessments, continuous monitoring, and integrating SCC with other security tools. By fostering a culture of security awareness and staying informed about the latest threat trends, businesses can fortify their defenses and maintain a robust security posture.
Related: For pre-information, you will find the following posts helpful:
Decentralized but not secure
The whole resolution process may be more transparent. However, it’s usually relatively fast. One feature that speeds it up considerably is caching. A nameserver processing a recursive query may have to send out several queries to find an answer. However, it discovers a lot of information about the domain namespace as it does so.
Each time it refers to another list of nameservers, it learns that those nameservers are authoritative for some zone, and it knows the addresses of those servers. At the end of the resolution process, when it finally finds the data the original querier sought, it can also store it for future reference.
**Types of DNS Attacks**
DNS attacks come in various forms, each with modus operandi and potential damage. From DDoS attacks that flood servers to cache poisoning that redirects users to malicious websites, understanding these attack vectors is crucial for implementing adequate security strategies.
**DNS Security Solutions**
Thankfully, several DNS security solutions are available to safeguard your online presence. This section will explore some of the most effective and widely used security measures. From implementing DNSSEC (DNS Security Extensions) to deploying firewalls and intrusion detection systems, we will discuss how these solutions can help mitigate DNS-related threats.
**Best Practices for DNS Security**
While deploying DNS security solutions is essential, following best practices to enhance your security posture is equally important. This section will outline some key best practices for DNS security, including regular patching and updates, monitoring DNS traffic, and employing multi-factor authentication. By adopting these practices, you can bolster your defenses against potential threats.
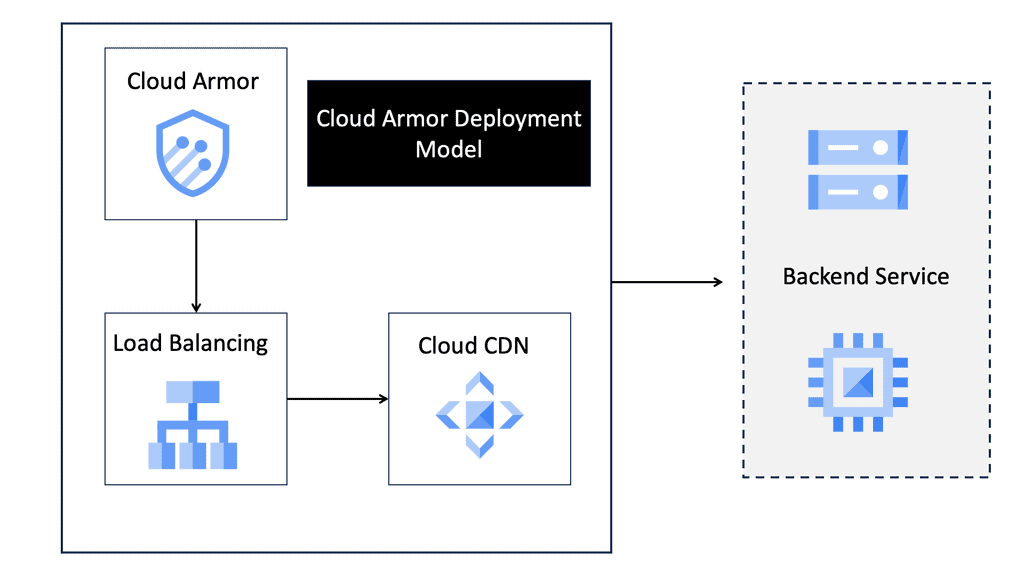
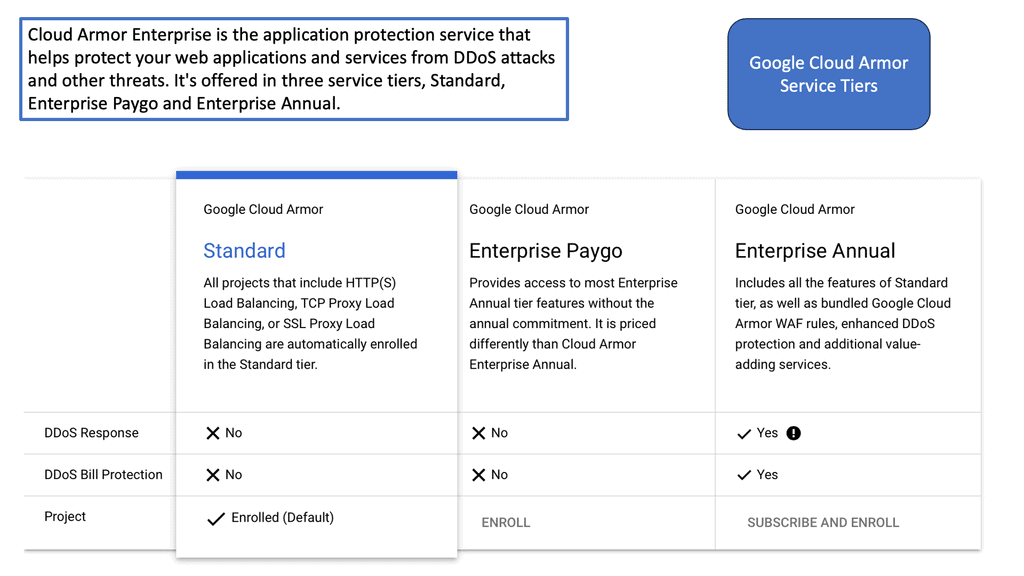
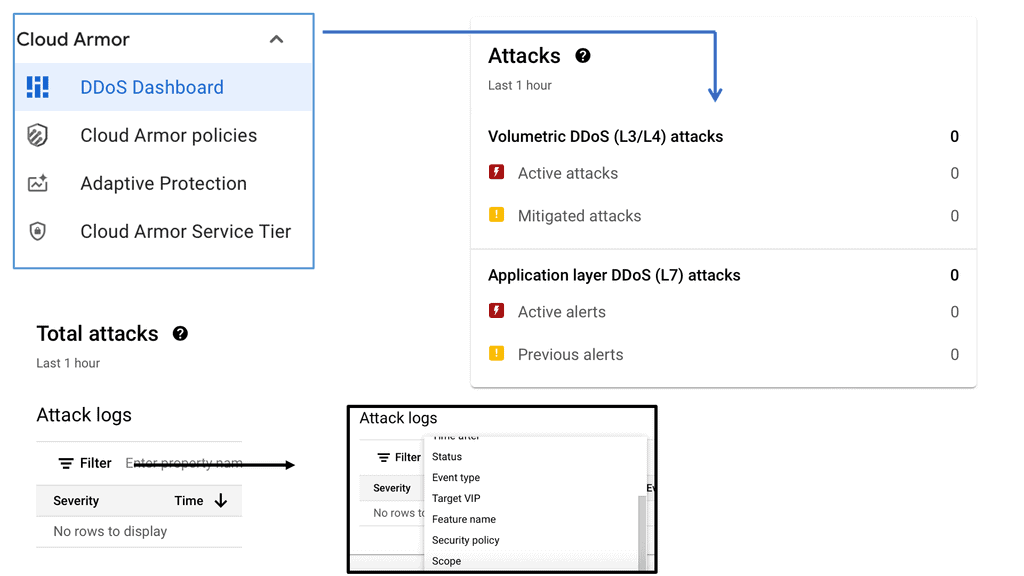
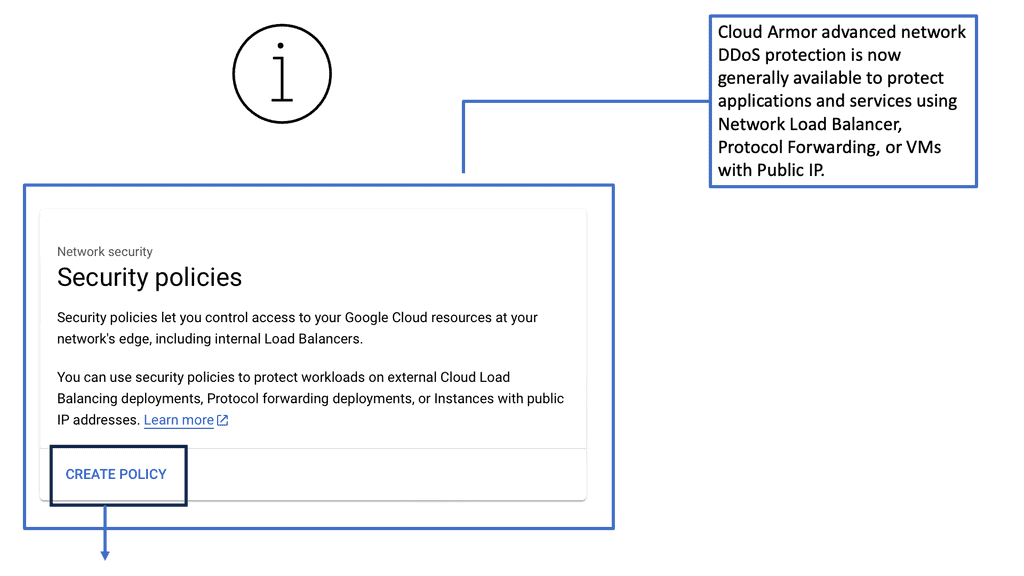
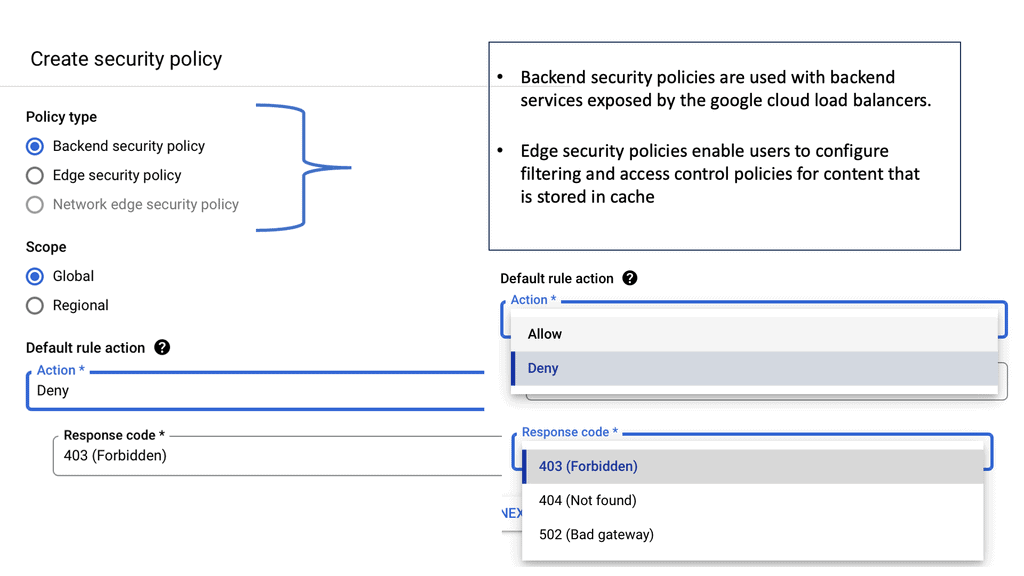
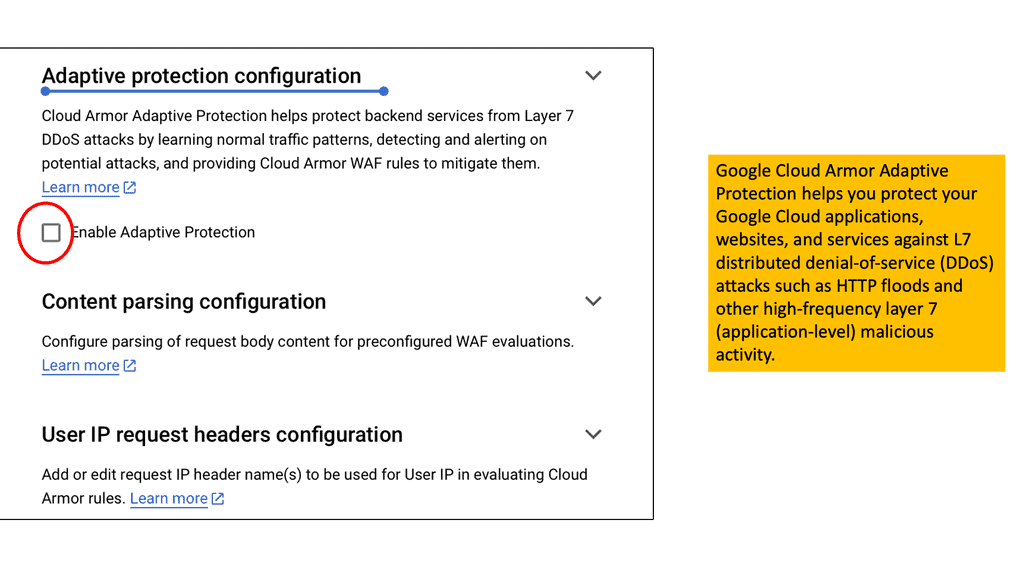
## Cloud Armor DNS Protection ##
### How Cloud Armor Works
Cloud Armor operates by leveraging a global infrastructure to detect and filter out malicious traffic before it can reach your applications. It employs advanced algorithms and machine learning techniques to differentiate between legitimate user traffic and potential threats.
By doing so, it ensures that your services remain accessible and responsive, even in the face of an ongoing attack. Furthermore, Cloud Armor integrates seamlessly with DNS security solutions, enhancing its ability to manage and redirect traffic efficiently..
### Integrating DNS Security Solutions
An integral component of Cloud Armor’s effectiveness is its seamless integration with DNS security solutions. By working in tandem, these systems provide an additional layer of security, ensuring that DNS traffic is also scrutinized and protected against potential attacks. This integration not only enhances the overall security posture but also improves the reliability and performance of your network services.
Decentralized but not secure
The DNS protocol was developed to be decentralized and hierarchical, though not secure. Almost since its inception, there have been exploits. We must protect this critical network service. Several technologies have been implemented for DNS protection. These security technologies can be implemented with secure access service edge (SASE) products such as DNS security Cisco with the Cisco Umbrella DNS product. Cisco Umbrella DNS stops threats such as Malware before the initial connection.
DNS Protection: Are DNS inquiries encrypted?
DNS queries are not encrypted. Even if users use a DNS resolver like 1.1.1.1 that does not track their activities, DNS queries travel over the Internet in plaintext. Anyone who intercepts the query can see which websites the user is visiting. This absence of privacy impacts security significantly. If DNS queries are not private, it becomes easier for governments to censor the Internet and for bad acts to lurk on users’ online behavior unknowingly.
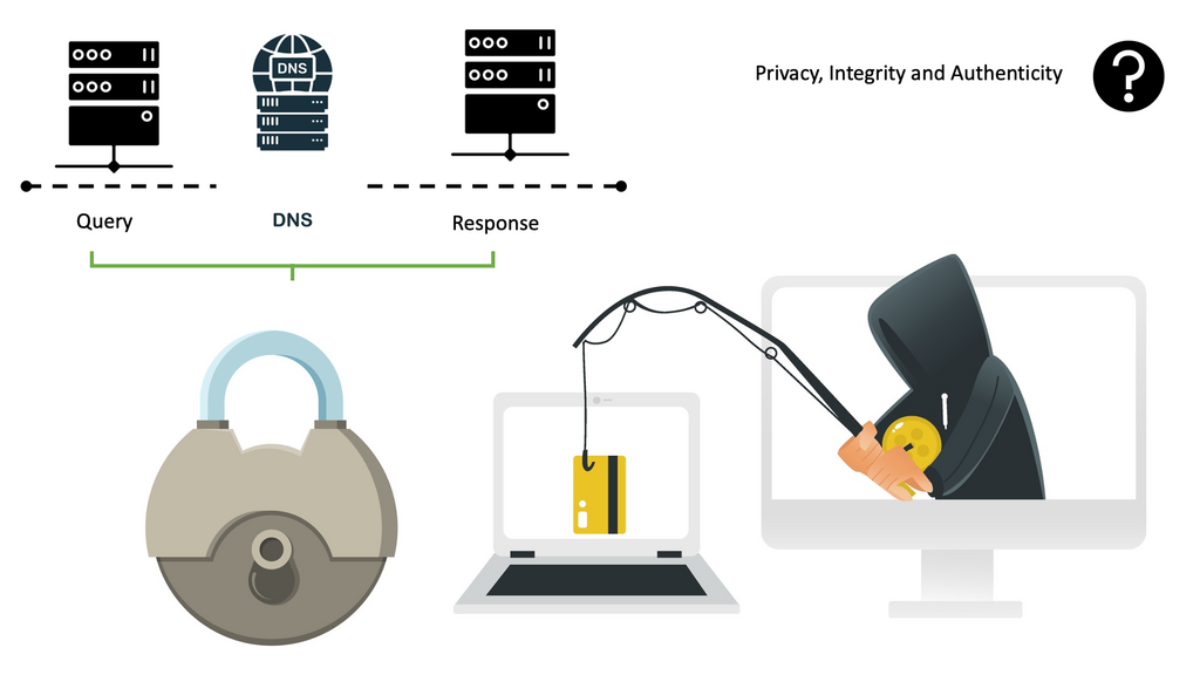
DNS Protection with Privacy, Integrity, and Authenticity
So, with DNS, the primary thing we care about with security is not there. In security, we care about privacy, integrity, and authenticity. However, with DNS left to its defaults, with privacy, you can see all the DNS queries in plain text. Then, for integrity, we want to know if someone has made changes between the query and response DNS stages. Finally, for authenticity, we have yet to learn if the DNS server that responded is the server we want to talk to, not some man-in-the-middle snooping and intercepting the DNS queries and forging responses, leading users to malicious websites.
Example: DNS over TLS (DoT) and DoH (DNS over HTTPS)
These concerns have directed us to introduce technologies for DNS protection. Some DNS protection technologies include the DNS firewall, DNS as a security tool with DNS reputation and inspection, and secure the channel with DNS over TLS (DoT) and DoH (DNS over HTTPS), as well as security protocol implementations with DNSSEC. When implemented correctly, all of this helps restore the privacy, integrity, and authenticity security issues we have with the current implementation of the DNS protocol.
DNS Protection: Lack of DNS Security Solutions
**Early days of DNS-
In the early 1980s, the network was much smaller, with fewer relatively well-known and trusted participants. However, as the network scaled, DNS remained an insecure and unauthenticated protocol, even though the networks grew to have many relatively unknown and untrusted participants.
Since 1980, we have been stuck with this protocol. At that time, around a hundred hosts around the USA communicated with each other. Some of these communication protocols include FTP and SMNP. You still needed to find the IP back then, so you had to look it up in a host file. Then, if you wanted to be put into this host file, you would have to call Stanford and request it literally, and they wrote it manually for you.
**Challenge: Scaling-
Before you can scale, we need to create something to replace the host file. This was when the Domain Name System was designed. So, we have delegation with hierarchy instead of a host file that must be manually edited for new hosts.
With the Domain Name System, we have the concept of hierarchy. There is a Root at the very top, which is responsible for the IPs of the servers for the TLDs, which are .com and .org; there are thousands of them now, and they are responsible for the domains that are in them and not any other domains that are not part of that TLD.
**DNS protection: DNS creates blind spots-
Organizations widely trust DNS. The concept of trust in public and private IP addresses boils down to binary numbers and has nothing to do with one being more trustworthy, except for the excessive trust placed on private IP ranges.
DNS traffic is typically permitted to pass freely through network firewalls and other security infrastructure. However, bad actors with malicious intent attack and abuse it. Because of this, DNS traffic can be manipulated through techniques such as DNS tunneling and DNS poisoning, all of which create blind spots in your security posture.
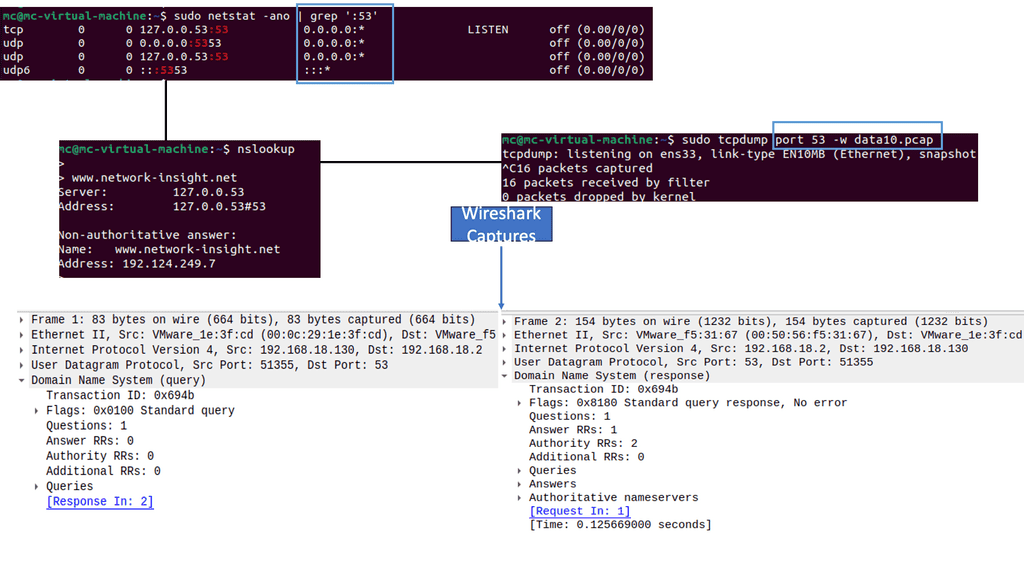
**The issue with UDP-
Let us start with the basics. Clients can ask for DNS if they want to connect to an address such as ‘www.network-insight.com’ and need to know which IP address corresponds to it. Typically, all DNS messages are sent over UDP, where the problems start.
The first issue is that UDP is a stateless protocol and that source IP addresses are blindly trusted, similar to how everyone would trust a private IP address over a public one. Therefore, each request and response described here is a single UDP request containing to and from IP addresses.
Any host can forge the source address on a UDP message, making it look like it came from the expected source. Therefore, a bad actor sitting on a network that does not filter outbound packets can construct a UDP message that says it’s from the authoritative server and send it to the recursive resolver.
DNS Security Cisco with DNS Security Solutions:
a) Neglected attack surface
Today’s bad actors use DNS’s often neglected attack surface – to steal data, spread malware, perform data exfiltration, command, and control network surveillance, along with the capabilities to perform social engineering. DNS is a bidirectional, Internet-facing protocol that carries a tremendous amount of data, making it an adversary’s most excellent tool for carrying out attacks and causing damage.
In addition, the combination of security teams failing to secure their DNS traffic and DNS’s ubiquity makes it a bad actor’s most potent yet unforgotten tool.
b) Example: Secure Web Gateway
While they have solutions that inspect and secure areas like their network with a stateful firewall, web traffic with Secure Web Gateways (SWG), and even some of the newer zero-trust technologies, these solutions cannot perform a deep inspection of their DNS traffic, leaving them vulnerable to the many threats today that abuse DNS. This is because they are not designed to inspect DNS traffic. As a result, techniques such as DNS tunneling should be noticed.
In most instances, DNS packets – typically including IP address information – enter networks via unblocked ports without first being inspected by security systems. So, again, DNS activity in a network is rarely monitored. This makes the DNS layer the perfect blind spot for bad actors to manipulate.
c) Issues with phishing
Many of today’s sophisticated attacks depend on DNS activity. In addition, there has been a rise in malware; ransomware binaries, once executed, are quick to encrypt, and you can’t trust that your employee won’t click on a phishing email. As a result, there needs to be more trust and high complexity.
Bad actors use this and manipulate DNS to stage the internet infrastructure to support each attack stage and fully execute their kill chain. In many of today’s more sophisticated ransomware attacks, for example, bad actors will use DNS packets to upload Malware to a device.
DNS Protection
The vulnerability and abuses of this protocol are comprehensive, and several methods of attacking DNS exist. For example, DNS poisoning, denial of service, spoofing/hijacking, and DNS tunneling exist.
DNS Tunneling:
Unless you have DNS-layer security, the DNS packets typically used to communicate IP addresses will only be inspected as they move through your network. Additionally, most security solutions don’t even register anomalous DNS activity – like DNS tunneling- a sure sign of an in-progress attack. DNS tunneling uses the DNS protocol to communicate non-DNS traffic over port 53. It sends HTTP(s) and additional protocol traffic over DNS.
DNS tunneling establishes DNS tunnels between their servers and victims’ machines. This connection between attacker and victim allows for the exfiltration of sensitive data and the execution of command and control operations.
DNS Poisoning:
DNS Poisoning, or DNS cache poisoning, is where forged DNS data is submitted into a DNS resolver’s cache. This results in the resolver returning an incorrect IP address for a domain. Therefore, rather than going to the indented website unknown to the user, their traffic can be redirected to a malicious machine. More often, this will be a replica of the original site used for malicious purposes, such as distributing Malware or collecting login information.
DNS poisoning was first uncovered in 1998. In this case, a recursive server sends a query out to the Root. As we are using UDP, there is no connection, and the only thing back then to identify the query as it came back as a response was simply a Query ID. That was a little short. Now, there was the possibility of tricking a DNS recursive resolver into storing incorrect DNS records. Once the nameserver has stored the wrong response, it will return it to anyone who asks.
**Issue: Redirect Web Browsers**
This “DNS poisoning” attack could allow random attackers to deceive DNS and redirect web browsers to false servers, hijacking traffic. Furthermore, the incorrect stored entry will remain until the cache entry expires, down to the TTL, which could lead to weeks of compromise.
So, if you attacked the server with forged responses for a domain and tried to brute-force the Query ID not very long ago, you could eventually guess it and insert your response into that recursive server cache.
If you set the TTL for a low time, such as a week, then everyone who queries that recursive server will get your chosen IP address for this domain name. Today, there have been changes to mitigate DNS poisoning. They have made the Query string very long and hard to guess, so it is hard to do, but it can still happen.
DNS Spoofing:
Then we have DNS Spoofing, or hijacking is very easy to do and difficult to detect. For example, let’s say you type the incurred domain name. So you try to go somewhere that does not exist and are returned to a search page with many ads. This is the ISP that is hijacking NX domain responses. So when you try to query for a name that does not exist, your ISP sees this, crafts its response, and sends you to a search page to sell you ads. This commonly happens on public Wi-Fi networks.
We have similar DNS spoofing and poisoning attacks, but they have distinguishable characteristics. Both attacks attempt to trick users into revealing sensitive data, which could result in a targeted user installing malicious software that can be used later in the kill chain. Poisoning DNS cache changes entries on DNS resolvers or servers where IP addresses are stored.
DNS Amplification Attack (DNS Flood):
Then, we have the DNS amplification style of attack, also known as DNS floods. A bad actor exploits vulnerabilities to initially turn small queries into much larger payloads, which are used to bring down the victim’s hosts.
So, we know that DNS uses UDP for transport, meaning a bad actor can spoof the source address of a DNS request and send the response to any IP address of their choosing. In this case, they can amplify DDoS attacks using DNS responses larger than the initial query packet. For example, fake DNS lookups to open recursive servers can achieve a 25x to 40x amplification factor. This is because the source IP of the bogus lookups is the victim’s website, which becomes overwhelming.
DNS Flood Attack:
DNS flood targets one or more DNS servers belonging to a given zone, attempting to impede the resolution of resource records of that zone and its sub-zones. This attack overwhelms the network capacity that connects authoritative servers to the Internet.
Once the bandwidth is depleted with malicious traffic, legitimate traffic carrying DNS queries from legitimate sources cannot contact the authoritative servers. DNS flood attacks differ from DNS amplification attacks. Unlike DNS floods, DNS amplification attacks reflect and amplify traffic off unsecured DNS servers to hide the attack’s origin and increase its effectiveness.
Random Subdomain Attack:
Random Subdomain DDoS attacks, such as the Mirai attack on Dyn, have become popular recently. In these DNS attacks, many queries are sent for a single or a few target domains, yet they include highly varying nonexistent subdomains generated randomly.
This denial-of-service attack hits a domain’s authoritative name servers with multiple requests for random, nonexistent subdomains. The name servers become bogged down when replying to these phony requests and need help responding to legitimate queries. These attacks are also called NXDomain attacks; they can result in denial of service at the recursive resolver level.
DNS Tunneling:
Then, we have DNS tunneling, which we briefly mentioned. DNS tunneling is frequently used to deliver payloads encoded in DNS queries and responses, exfiltrate data, and execute command and control attacks as the attackers use SSH, TCP, or HTTP to pass, for example, Malware or stolen information into DNS queries undetected.
This allows the bad actor to exfiltrate sensitive data in small chunks within DNS requests to bypass security. With the amount of DNS traffic and requests a network typically sees, attackers can easily hide data theft.
The bad actor can use standard protocols like TCP or SSH, encoded within DNS protocol requests. At the same time, it is not an attack on DNS. This form of malicious activity can use DNS to exfiltrate data.
**DNS Security Cisco**
There are several ways these attacks can be prevented. Firstly, the DNS firewall enables DNS layer security. DNS-layer security effectively prevents malicious activity at the earliest possible point and, in the case of Malware, contains callbacks to attackers. DNS security solutions can be accomplished with products such as Cisco Umbrella DNS.
DNS Security Cisco with DNS-layer security
Cisco Umbrella DNS uses DNS-layer security encompassing the Internet’s infrastructure to block malicious and unwanted domains before a connection is established as part of recursive DNS resolution. In addition, it utilizes a technology known as selective cloud provide that redirects specific requests noted as risky for a deeper and more thorough inspection.
Cisco Umbrella DNS accomplishes this process transparently through the DNS response without adding latency or degrading performance. Just as a standard firewall watches incoming and outgoing web traffic and blocks unsafe connections, a DNS firewall works the same way. The distinction is that DNS firewalls analyze and filter queries based on threat feeds and threat intelligence. There are two kinds of DNS Firewalls: those for recursive servers and those for authoritative servers.
No Performance Hits
A DNS firewall provides several security services for DNS servers. It sits between a user’s recursive resolver and the authoritative nameserver of the website or service they are trying to reach. This can help with reputation filtering and domain reputation.
Cisco Umbrella DNS: Secure the channel
We have DNS over TLS and DNS over HTTPS, two standards for encrypting DNS queries to prevent external parties from being able to read them. DNS over TLS (DoT) and DoH (DNS over HTTPS) add a secure layer to an insecure protocol. By using DoH and DoT, users can ensure the privacy of DNS responses and block eavesdropping on their DNS requests (which reveals the sites they are visiting).
Cisco Umbrella DNS: Secure the protocol
Application layers use security protocols such as HTTPS, DMARC, etc., so the DNS protocol should be no exception. DNS Security Extensions (DNSSEC) defends against attacks by digitally signing data to help guarantee its validity. The signing must happen at every level in the DNS lookup process, which can make it a complicated setup.
DNSSEC was one of the first things we started implementing, and it is much older than many assume. The first talks about DNSEEC were in the early 1990s. It is a way to ensure that you know that a record you get back has not been tampered with and that the server you are talking to is the server you intend to talk to. All of this is done with PKI.
Public Key Infrastructure (PKI)
The server has a public and private key pair. So we have the public key, and they can sign the record. However, as we maintain a distributed hierarchy in DNS, we must guarantee that these are signed up to the Root. DNSSEC implements a hierarchical digital signing policy across all layers of DNS.
For example, in the case of a ‘google.com’ lookup, a root DNS server would sign a key for the.COM nameserver, and the.COM nameserver would then sign a key for google.com’s authoritative nameserver. DNSSEC not only allows a DNS server to verify the authenticity of the records it returns, but It also enables the assertion of the “non-existence of records.”
DNS resolvers can also be configured to provide security solutions. For example, some DNS resolvers provide content filtering, which can stop sites known to distribute Malware and spam, and botnet protection, which blocks communication with known botnets. Many of these secure DNS resolvers are free to use
Summary: DNS Security Solutions
This blog post delved into DNS security solutions, exploring the key concepts, benefits, and best practices for safeguarding one’s online activities.
Understanding DNS Security
The DNS, often called the internet’s phonebook, translates domain names into IP addresses, allowing us to access websites by typing in familiar URLs. However, this critical system is susceptible to various security risks, such as DNS spoofing, cache poisoning, and DDoS attacks. Understanding these threats is crucial in comprehending the importance of DNS security solutions.
DNS Security Solutions Explained
Several effective DNS security solutions are available to mitigate risks and fortify your online presence. Let’s explore a few key options:
- DNS Filtering: This solution involves implementing content filtering policies to block access to malicious websites, reducing the likelihood of falling victim to phishing attempts and malware infections.
- DNSSEC: Domain Name System Security Extensions (DNSSEC) provide cryptographic authentication and integrity verification of DNS data, preventing DNS spoofing and ensuring the authenticity of domain name resolutions.
- Threat Intelligence Feeds: By subscribing to threat intelligence feeds, organizations can stay updated on emerging threats and proactively block access to malicious domains, bolstering their overall security posture.
Benefits of DNS Security Solutions
Implementing robust DNS security solutions offers numerous benefits to individuals and organizations alike. Some notable advantages include:
– Enhanced Data Privacy: DNS security solutions protect sensitive user information, preventing unauthorized access or data breaches.
– Improved Network Performance: By filtering out malicious requests and blocking access to suspicious domains, DNS security solutions help optimize network performance and reduce potential downtime caused by cyberattacks.
– Mitigated Business Risks: By safeguarding your online infrastructure, DNS security solutions minimize the risk of reputational damage, financial loss, and legal repercussions due to cyber incidents.
Best Practices for DNS Security
While investing in DNS security solutions is crucial, adopting best practices is equally important to maximize their effectiveness. Here are a few recommendations:
– Regularly update DNS software and firmware to ensure you benefit from the latest security patches and enhancements.
– Implement strong access controls and authentication mechanisms to prevent unauthorized access to DNS servers.
– Monitor DNS traffic for anomalies or suspicious activities, enabling prompt detection and response to potential security breaches.
Conclusion:
In an era where online threats continue to evolve, prioritizing DNS security is vital for individuals and organizations. By understanding the risks, exploring effective solutions, and implementing best practices, you can fortify your online security, safeguard your data, and confidently navigate the digital landscape.
- DMVPN - May 20, 2023
- Computer Networking: Building a Strong Foundation for Success - April 7, 2023
- eBOOK – SASE Capabilities - April 6, 2023