BGP FlowSpec
Network operators face various challenges in managing and securing their networks in today's interconnected world. BGP FlowSpec, a powerful extension to the Border Gateway Protocol (BGP), has emerged as a valuable tool for mitigating network threats and improving traffic management. This blog post aims to provide a comprehensive overview of BGP FlowSpec, its benefits, and its role in enhancing network security and traffic management.
BGP FlowSpec, short for BGP Flow Specification, is an extension of the BGP protocol that allows network operators to define and distribute traffic filtering rules across their networks. Unlike traditional BGP routing, which focuses on forwarding packets based on destination IP addresses, BGP FlowSpec enables operators to control traffic based on various attributes, including source IP addresses, destination ports, protocols, and more.
BGP FlowSpec is an extension to the traditional BGP protocol that allows for fine-grained control of network traffic. It enables network operators to define traffic filtering rules based on various criteria such as source and destination IP addresses, port numbers, packet attributes, and more. These rules are then distributed across the network, ensuring consistent traffic control and management.
Traffic Filtering: BGP FlowSpec enables administrators to define specific traffic filtering rules, allowing them to drop, redirect, or rate-limit traffic based on various criteria.
DDoS Mitigation: By leveraging BGP FlowSpec, network operators can swiftly respond to DDoS attacks by deploying traffic filtering rules in real-time, mitigating the impact and ensuring the stability of their network.
Service Differentiation: BGP FlowSpec enables the creation of differentiated services by allowing administrators to prioritize, shape, or redirect traffic based on specific requirements or customer agreements.
Increased Network Security: BGP FlowSpec allows for rapid response to security threats by deploying traffic filtering rules, providing enhanced protection against malicious traffic and reducing the attack surface.
Improved Network Performance: With the ability to fine-tune traffic management, BGP FlowSpec enables better utilization of network resources, optimizing performance and ensuring efficient traffic flow.
Flexibility and Scalability: BGP FlowSpec is highly flexible, allowing administrators to easily adapt traffic filtering rules as per evolving network requirements. Additionally, it scales seamlessly to accommodate growing network demands.
Data Centers: BGP FlowSpec is utilized in data centers to enforce traffic engineering policies, prioritize critical applications, and protect against DDoS attacks.
Internet Service Providers (ISPs): ISPs leverage BGP FlowSpec to enhance network security, offer differentiated services, and efficiently manage traffic across their infrastructure.
Cloud Service Providers: BGP FlowSpec enables cloud service providers to dynamically manage and prioritize traffic flows, ensuring optimal performance and meeting service level agreements (SLAs).
BGP FlowSpec is a game-changer in the realm of network control. Its powerful features, combined with the ability to fine-tune traffic management, provide network operators with unprecedented control and flexibility. By adopting BGP FlowSpec, organizations can enhance security, optimize performance, and unleash the true potential of their networks.
Matt Conran
Highlights: BGP FlowSpec
### Understanding the Basics
At its core, BGP FlowSpec is an extension of BGP, the protocol that governs the exchange of routing information across the internet. Unlike standard BGP, which primarily focuses on IP address prefixes, FlowSpec allows for the creation and dissemination of rules that define specific traffic flows. These rules enable network operators to specify actions for particular types of traffic, such as redirecting, rate-limiting, or even discarding packets based on certain criteria like source and destination IP addresses, ports, and protocols.
### Key Features of BGP FlowSpec
One of the standout features of BGP FlowSpec is its ability to define traffic filters using a variety of match conditions. These conditions can include IP prefixes, source and destination ports, protocols, and even packet length. This level of specificity enables network administrators to craft precise rules that can mitigate security threats such as DDoS attacks or optimize traffic flows for better performance. Additionally, FlowSpec rules are propagated through BGP, ensuring that all routers in the network can enforce the same policies consistently.
Traffic Filtering Policies
BGP (Border Gateway Protocol) Flow Spec is an extension of BGP that enables the distribution and enforcement of traffic filtering policies throughout a network. It provides granular control over network traffic by allowing operators to define and propagate specific traffic flow characteristics.
Within the realm of BGP Flow Spec, several important components work together to achieve effective traffic filtering. These include Match Fields, Actions, and Communities. Match Fields define the criteria for traffic identification, Actions determine how the matched traffic should be treated, and Communities facilitate the distribution of Flow Spec rules.
BGP Flow Spec offers a wide range of use cases in network security. One such application is DDoS mitigation, where Flow Spec rules can be deployed at the edge of a network to quickly identify and drop malicious traffic. Additionally, BGP Flow Spec can be used for implementing fine-grained traffic engineering policies, enabling network operators to optimize network resources and ensure optimal traffic flow.
While BGP Flow Spec presents numerous benefits, it also comes with its fair share of challenges. Interoperability among different vendors’ implementations can be a concern, as not all vendors support the same set of match fields and actions. Furthermore, the potential for misconfigurations and unintended consequences should be carefully addressed to prevent disruptions in network operations.
What is BGP FlowSpec?
BGP FlowSpec is an extension to BGP that allows for the distribution of traffic filtering rules across network devices. It enables network administrators to define fine-grained traffic policies based on various criteria, such as source/destination IP addresses, port numbers, protocols, etc. By leveraging BGP FlowSpec, network operators can quickly disseminate and enforce traffic filtering rules throughout their networks.
1. DDoS Mitigation:
One key application of BGP FlowSpec is mitigating Distributed Denial of Service (DDoS) attacks. By utilizing BGP FlowSpec, network operators can dynamically distribute traffic filtering rules to divert and reduce malicious traffic at the edge of their networks, preventing them from reaching the targeted resources.
2. Traffic Engineering:
BGP FlowSpec also enables advanced traffic engineering capabilities. By manipulating traffic flows based on specific criteria, network administrators can optimize network performance, allocate resources efficiently, and ensure a smooth user experience.
3. Firewalling and Access Control:
With BGP FlowSpec, network operators can implement granular firewalling and access control policies. By defining filtering rules at the edge routers, they can selectively allow or deny traffic based on specific attributes, enhancing network security and protecting critical assets.
4. Enhanced Network Security:
BGP FlowSpec enables the rapid deployment of traffic filtering rules to mitigate Distributed Denial of Service (DDoS) attacks, preventing malicious traffic from reaching critical network infrastructure. Its ability to filter traffic based on source and destination addresses, protocols, and port numbers provides a powerful first line of defense against various attack vectors.
5. Improved Network Flexibility:
With BGP FlowSpec, network administrators can dynamically manipulate traffic flows within their networks. This flexibility allows for implementing traffic engineering strategies, such as diverting traffic to optimize performance, balancing loads across multiple paths, or redirecting traffic during maintenance operations. BGP FlowSpec enables network operators to adapt quickly to changing network conditions and optimize resource utilization.
**Flowspec**
With Flowspec (Flow Specification), you can filter and limit traffic based on specific flow characteristics, such as source and destination IPv4 and IPv6 addresses, IP protocol, and source and destination ports. By distributing traffic filtering and rate-limiting rules across their networks using BGP, flowspec can help mitigate the impact of DDoS attacks and other unwanted traffic patterns.
For Flowspec to work, the router receives specially formatted BGP Network Layer Reachability Information (NLRI) messages that contain the flow characteristics and the desired actions to be applied to the matching traffic. Using this information, the router dynamically creates and applies traffic filtering and rate-limiting policies.
Flowspec & Cisco IOS
1) – Flowspec can be configured on Cisco IOS routers by enabling BGP, configuring a BGP session with a neighbor, and configuring BGP policy templates with the desired traffic filtering and rate-limiting actions. In addition, you may need to enable Flowspec client functionality and configure the router to accept and install Flowspec routes.
2) – In addition to forwarding traffic based on IP prefixes, modern IP routers can classify, shape, rate limit, filter, or redirect packets based on administratively defined policies. These traffic policy mechanisms allow routers to define match rules based on multiple fields of packet headers. Actions such as those described above can be associated with each rule.
3) – The n-tuple containing the matching criteria defines an aggregate traffic flow specification.IP protocols, transport protocol port numbers, and source and destination address prefixes can also be used as matching criteria. An aggregated traffic flow’s flow specification rules are encoded using the BGP [RFC4271] NLRIs.
4) – Flow specifications are more specific entries in unicast prefixes and depend on existing unicast data. Before flow specifications can be accepted from external autonomous systems, they must be validated against unicast routing. When the aggregate traffic flow defined by the unicast destination prefix is forwarded to a BGP peer, the local system can safely install more specific flow rules.
Dealing with FlowSpec
BGP Flowspec
In RFC 5575, Dissemination of Flow Specification Rules, the BGP Flow Specification (Flowspec) describes a mechanism for distributing network layer reachability information (NLRI) for aggregated traffic flows. According to the RFC, a flow specification is an n-tuple with several matching criteria. An IP packet matches a defined flow if all the requirements are met. Flowspecs are n-tuples because they can define multiple match criteria, which must all be met. Traffic does not match the flowspec entry if all the tuples are not matched.
Network operators use BGP flowspec primarily to distribute traffic filtering actions to mitigate DDoS attacks.
The focus should first be on detecting DDOS attacks, such as invalid or malicious incoming requests, and then on mitigation. To mitigate DDOS attacks, two steps must be taken:
Step 1. Diversion: Route traffic to a specialized device that removes invalid or malicious packets from the traffic stream while retaining legitimate packets.
Step 2. Return: Redirect the clean and legitimate traffic back to the server.
**Dealing with DDoS Attacks**
To deal with DDoS attacks, as standard IP routing is destination-based, we can use routing to route the packets toward a null destination. If BGP is involved, we can use a remote-triggered blackhole (RTBH) to remotely signal our upstream router to route the particular destination into a NULL route.
This is quite a simplistic way to mitigate a DDoS attack. On the other hand, BGP FlowSpec can be used as a BGP SDN DDoS solution. And can influence behavior based on a much broader set of criteria with the DDoS BGP redirect criteria?
**FlowSpec DDoS**
For example, with FlowSpec DDoS, we can match up more fields supported by BGP Flowspec (source and destination, IP protocol, source and destination port, ICMP code, and TCP Flags) and more dynamic actions such as dropped packet test or rate limit.
For pre-information, you may find the following helpful post before you proceed:
BGP FlowSpec
BGP Security
BGP is one protocol that makes the Internet work. Unfortunately, because of its criticality, BGP has been the target protocol. The main focus of any attacker is to find a vulnerability in a system, in this case, BGP, and then exploit it. RFC 4272, BGP Security Vulnerabilities Analysis, presents various weak areas in BGP that every enterprise or service provider should consider when implementing BGP.
Like most protocols were designed in the past, BGP provides no confidentiality and only limited integrity and authentication services. Furthermore, BGP messages can be replayed; if a bad actor intercepts a BGP UPDATE message that adds a route, the hacker can resend that message after the route has been withdrawn, causing an inconsistent and invalid route to be present in the routing information base (RIB).
Enhancing Network Security:
One of BGP FlowSpec’s critical benefits is its ability to enhance network security. By leveraging FlowSpec, network operators can quickly respond to security threats and implement granular traffic filtering policies. For example, in the event of a distributed denial-of-service (DDoS) attack, operators can use BGP FlowSpec to instantly distribute traffic filters across their network, effectively mitigating the attack at its source. This real-time mitigation capability significantly reduces the impact of security incidents and improves network resilience.
Traffic Engineering and Quality of Service:
BGP FlowSpec also plays a crucial role in traffic engineering and quality of service (QoS) management. Network operators can use FlowSpec to shape and redirect traffic based on specific criteria. For instance, by employing BGP FlowSpec, operators can prioritize certain traffic types, such as video or voice traffic, over others, ensuring better QoS for critical applications. Furthermore, FlowSpec enables operators to dynamically reroute traffic in response to network congestion or link failures, optimizing network performance and user experience.
Implementing BGP FlowSpec:
Implementing BGP FlowSpec requires compatible routers and appropriate configuration. Network operators must ensure that their routers support the BGP FlowSpec extension and have the necessary software updates. Additionally, operators must carefully define traffic filtering rules using the BGP FlowSpec syntax, specifying each rule’s desired attributes and actions. It is crucial to thoroughly test and validate the FlowSpec configurations to avoid unintended consequences and ensure the desired outcomes.
Challenges and Considerations:
While BGP FlowSpec offers significant advantages, some challenges and considerations must be considered. FlowSpec configurations can be complex, requiring a deep understanding of network protocols and traffic patterns. Additionally, incorrect or overly aggressive FlowSpec rules can unintentionally disrupt legitimate traffic. Therefore, operators must balance security and network accessibility while regularly reviewing and fine-tuning their FlowSpec policies.
BGP FlowSpec Flow-based Policies
BGP FlowSpec is a BGP SDN mechanism that distributes flow-based policies to other BGP speakers. It enables the dynamic distribution of security profiles and corrective actions using a signaling mechanism based on BGP. No other protocols (OpenFlow, NETCONF, etc.) are used to disseminate the policies. The solution is based entirely on BGP and consists of a new Border Gateway Protocol Network Layer Reachability Information (BGP NLRI—AFI=1, SAFI=133) encoding format.
It reuses BGP protocol algorithms and inherits all the operational experience from existing BGP designs. It’s simple to extend by adding a new NLRI – MP_REACH_NLRI / MP_UNREACH_NLRI. It’s also a well-known protocol for many other technologies, including IPv6, VPN, labels, and multicast.
All existing BGP high availability and scalability features can be used with BGP FlowSpec; for example, route reflection is possible for point-to-multipoint connections. In addition, BGP provides the following:
- Inter-domain support.
- Meaning you are not tied down to one AS.
- You are enabling your BGP FlowSpec domain to span multiple administrative domains.
BGP FlowSpec Operations
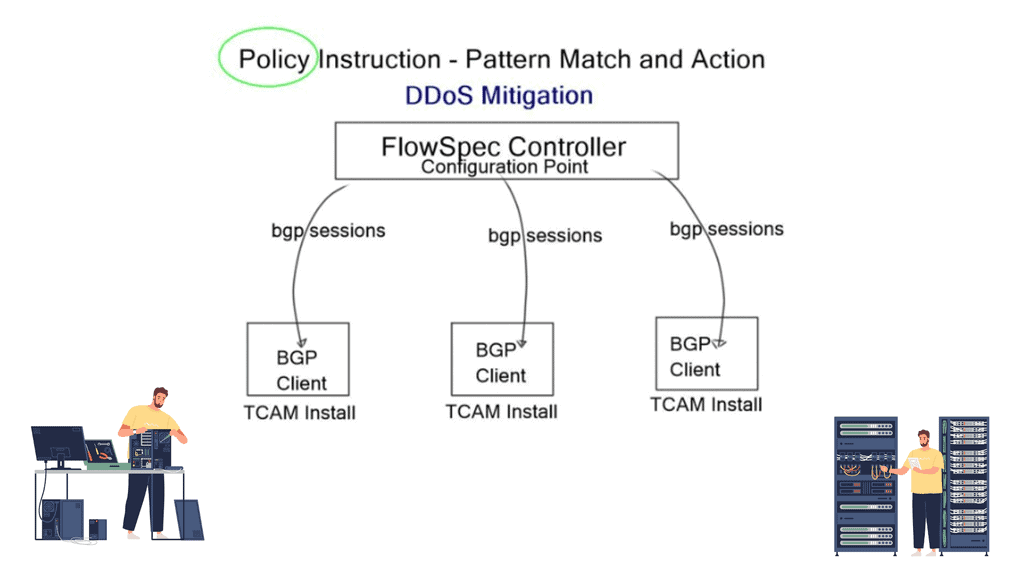
BGP FlowSpec separates BGP networks’ control and data plane and distributes traffic flow specifications. Within the infrastructure, we have a Flowspec controller, the server, one or more Flowspec clients, and optionally a route-reflector for scalability. Rules that contain matching criteria and actions are created on the server and redistributed to clients via MP-BGP.
The central controller programs forward decisions and inject rules remotely into BGP clients. Cisco, Juniper, and Alcatel-Lucent support BGP FS controllers. It may also run on an x86 server with ExaBGP or Arbor PeakFlow SP Collector Platform.
The client receives the rules from the controller and programs, including rules for a) traffic descriptions and b) actions to apply to traffic. Then, the client, a BGP speaker, makes the necessary changes to TCAM. An additional optional route reflector component can receive rules from the controller and distribute them to clients.
Traffic classification
It classes traffic with Layer 3 and 4 information and offers similar granularity to ACLs. Still, one significant added benefit is that it is distributed, and a central controller controls flow entries. It can match the destination IP, source IP, IP protocol, port, destination port, source port, ICMP type and code, TCP flags, packet length, DCSP, and fragments. Once traffic is identified, it is matched, and specific actions are applied. In some cases, multiple actions are applied.
For example, FlowSpec can remotely program QoS – policers and markers, PBR – leak traffic to a Virtual Routing and Forwarding (VRF) or a new next hop, and replicate the traffic to, for example, a sniffer – all the configuration is carried out on the controller.
A key point: Scalability restrictions.
However, scalability restrictions exist as BGP FlowSpec entries share the TCAM with ACL and QoS. Complex rules using multi-value ranges consume more TCAM than simple matching rules. Cisco provides general guidance of 3000 simple rules per line card.
BGP DDoS and DDoS Mitigation
FlowSpec was initially proposed with RFC 5575 as a DDoS mitigation tool, but its use cases expand to other areas, such as BGP unequal cost load balancing. It’s tough to balance unequally based on your destination. With FlowSpec, it’s possible to identify groups of users based on the source address and then use FlowSpec to traffic engineer on ALL core nodes, not just at network edges.
DDoS mitigation operations
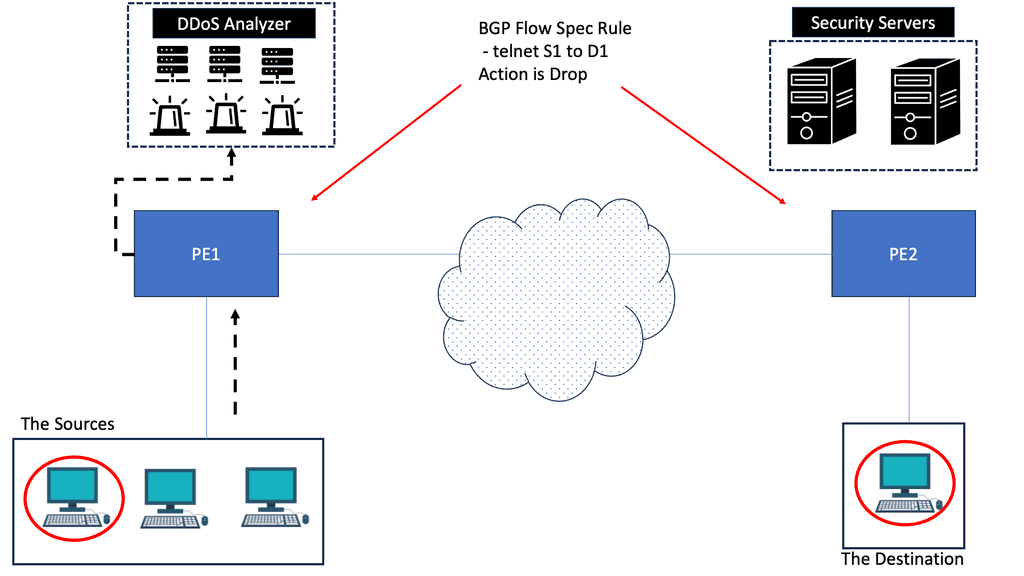
BGP Flowspec resembles access lists created with class maps and policy maps that provide matching criteria and traffic filtering actions. They are injected into BGP and propagated to BGP peers. As a result, there are many more criteria to use that destination IP address that can be used to mitigate the DDoS attack.
For example, with the DDoS BGP redirect, we can use criteria such as the source, destination, and L4 parameters and packet specifics such as length.
These are sent in a BGP UPDATE message to BGP border routers within FLOW_SPEC_NLRI along with the action criteria. Once received, several actions can be carried out, and these actions are carried in the extended communities’ Path attributes. So you can drop the policy or redirect it to another VRF.
DDoS BGP redirects The volumetric attack.
The primary type of DDoS attack FlowSpec protects against is a volumetric attack – long-lived large flows along with the DNS reflection attack. Volumetric attacks are best mitigated as close as possible to the Internet border. The closer you drop the packet to the source, the better. You don’t want the traffic to arrive at its destination or to have the firewall process and drop it.
For example, a TCP SYN attack could be 1000 million packets per second; not many firewall states can address that. It is much better to drop volumetric-type attacks at network borders as they cannot be mitigated within the data center; it’s simply too late.
FlowSpec is also suitable for dropping amplification-type attacks. These attacks do not need to be sent to scrubbing systems and can be handled by FlowSpec by matching the traffic pattern and filtering at the edge.
With BGP Flowspec for DDoS BGP redirects, we have a more granular approach to mitigating DDoS attacks than old-school methods. This is accomplished by a specific definition of flows based on Layer 3 and 4 matching criteria and actions configured on the FlowSpec server. The rules are automatically redistributed to FlowSpec clients using MP-BGP (SAFI 133) so the clients can take action defined in the flow rules.
Closing Points on BGP FlowSpec
BGP FlowSpec is an extension to BGP, designed to provide a scalable and automated method for distributing traffic flow specifications. By leveraging BGP’s existing infrastructure, FlowSpec allows for the dynamic configuration of firewall policies across a network. This functionality enables network operators to quickly respond to network threats and anomalies by propagating filter rules in a highly scalable manner.
At its core, BGP FlowSpec uses a combination of match conditions and actions. Match conditions define the type of traffic to be filtered, such as source/destination IP address, port numbers, or even specific protocols. Once a flow is matched, actions such as rate limiting or redirection can be applied. These flow specifications are distributed across the network using BGP, ensuring that all routers in the network enforce the same security policies.
Implementing BGP FlowSpec offers multiple advantages. First, it provides a centralized mechanism for managing network security policies, reducing the complexity associated with configuring individual devices. Second, its dynamic nature allows for rapid response to network threats, minimizing downtime and potential damage. Lastly, BGP FlowSpec’s scalability makes it suitable for both small enterprises and large-scale service providers.
Despite its advantages, BGP FlowSpec is not without challenges. One major consideration is ensuring compatibility with existing network devices, as not all routers support FlowSpec. Additionally, careful planning is required to avoid misconfigurations that could lead to unintended traffic blocking. Network administrators must also consider the potential impact on routing performance, particularly in large networks with complex policies.
Summary: BGP FlowSpec
The demand for highly flexible and secure networks continues to grow in today’s interconnected world. Among the many protocols that enable this, BGP Flowspec stands out as a powerful tool for network administrators. In this blog post, we will explore its key features, use cases, and benefits.
What is BGP Flowspec?
BGP Flowspec, or Border Gateway Protocol Flowspec, is an extension of BGP that enables network operators to define traffic filtering rules at the edge of their networks. Unlike traditional BGP routing, which focuses on forwarding packets based on destination IP addresses, BGP Flowspec allows for more granular control by filtering traffic based on various packet fields, including source and destination IP addresses, protocols, port numbers, and more.
Use Cases of BGP Flowspec
1. DDoS Mitigation: BGP Flowspec provides a powerful mechanism to detect and mitigate Distributed Denial of Service (DDoS) attacks in real time. Network administrators can swiftly drop or redirect malicious traffic by dynamically updating routers’ access control lists (ACLs), ensuring that critical resources remain available.
2. Traffic Engineering: BGP Flowspec enables network operators to shape and optimize network traffic flows. Administrators can achieve efficient resource utilization and improve overall network performance by manipulating traffic based on specific criteria, such as particular application types or geographic regions.
3. Policy Enforcement: BGP Flowspec allows network administrators to enforce specific policies at the edge of their networks. This could include blocking or redirecting traffic that violates particular security policies or regulatory requirements, ensuring compliance, and protecting sensitive data.
Benefits of BGP Flowspec
1. Flexibility: BGP Flowspec provides fine-grained control over traffic, allowing network operators to adapt quickly to evolving network requirements. This flexibility empowers administrators to respond to security threats, optimize network performance, and enforce policies with minimal disruption.
2. Real-time Response: With BGP Flowspec, network operators can quickly respond to security incidents and traffic anomalies. Administrators can effectively mitigate threats and protect network resources without manual intervention by dynamically updating filtering rules across routers.
3. Scalability: BGP Flowspec leverages the existing BGP infrastructure, making it highly scalable and suitable for large-scale networks. As networks grow and evolve, BGP Flowspec can seamlessly adapt to accommodate increased traffic and changing filtering requirements.
Conclusion:
In conclusion, BGP Flowspec is a powerful addition to the network administrator’s toolkit, offering enhanced flexibility, real-time response capabilities, and scalable traffic filtering. By leveraging BGP Flowspec’s capabilities, network operators can better address security threats, optimize network performance, and enforce policies tailored to their needs. As the demand for secure and highly adaptable networks continues to rise, understanding and harnessing the power of BGP Flowspec becomes increasingly essential.
- DMVPN - May 20, 2023
- Computer Networking: Building a Strong Foundation for Success - April 7, 2023
- eBOOK – SASE Capabilities - April 6, 2023


[…] are other potential design alternatives to SDX, for example, BGP FlowSpec. But in this case, BGP FlowSpec would have to be supported by all participating member AS edge […]