IPv6 Host Exposure
The Internet Protocol version 6 (IPv6) has emerged as the next-generation addressing protocol in today's interconnected world. With the depletion of IPv4 addresses, IPv6 offers a larger address space and improved security features. However, the widespread adoption of IPv6 has also introduced new challenges, particularly regarding host exposure. In this blog post, we will explore the concept of IPv6 host exposure, its implications, and effective mitigation strategies.
IPv6 host exposure refers to the visibility or accessibility of a particular host or device connected to the IPv6 network. Unlike IPv4, where Network Address Translation (NAT) provides security by hiding internal IP addresses, IPv6 assigns globally unique addresses to each device. This means that every device connected to the IPv6 network is directly reachable from the Internet, making it more susceptible to potential risks.
IPv6 host exposure offers numerous benefits, including enhanced end-to-end connectivity, simplified network architectures, and improved efficiency in peer-to-peer communications. It enables seamless device-to-device communication without relying on intermediaries. However, this increased connectivity also brings forth potential security and privacy concerns that need to be addressed proactively.
While IPv6 host exposure opens up new possibilities, it also introduces certain risks. Without proper configuration and security measures, exposed devices may become vulnerable to unauthorized access, network scanning, and potential exploitation. Additionally, the increased address space in IPv6 makes it challenging for network administrators to effectively monitor and manage their network infrastructure.
To mitigate risks associated with IPv6 host exposure, implementing best practices is crucial. These include:
Network Segmentation: Dividing the network into different segments helps isolate critical systems and prevents unauthorized access.
Firewall Configuration: Configuring firewalls to filter and monitor incoming and outgoing traffic plays a vital role in securing IPv6 networks.
Regular Updates and Patching: Keeping devices and network infrastructure up to date with the latest security patches ensures vulnerabilities are addressed promptly.
Intrusion Detection and Prevention Systems (IDPS): Deploying IDPS solutions provides real-time monitoring and alerts for potential threats.
While implementing technical measures is essential, educating end-users about the risks and best practices associated with IPv6 host exposure is equally important. Promoting strong password management, encouraging regular software updates, and raising awareness about the potential risks of exposing sensitive information online can significantly enhance overall security.
Understanding and properly managing IPv6 host exposure is crucial in today's digital landscape. By implementing best practices, staying vigilant, and prioritizing user education, organizations and individuals can navigate the world of IPv6 host exposure securely and confidently. Embracing the benefits of IPv6 while mitigating potential risks will ensure a safer and more connected future.
Matt Conran
Highlights: IPv6 Host Exposure
### Understanding the Basics of IPv6
IPv6, or Internet Protocol version 6, is designed to replace IPv4, the original protocol that has been in use since the early 1980s. While IPv4 uses a 32-bit address scheme, which allows for about 4.3 billion unique addresses, IPv6 uses a 128-bit scheme, providing an almost inconceivable number of addresses. This expansion is necessary to accommodate the ever-growing number of devices connected to the internet. But IPv6 is more than just a solution to address exhaustion; it also introduces improvements in routing, configuration, and security.
### The Security Advantages of IPv6
One of the key benefits of IPv6 is its built-in security features. Unlike IPv4, IPv6 was designed with security in mind from the outset. It includes IPsec, a suite of protocols that provide confidentiality, integrity, and authentication at the packet level. This means that data sent over an IPv6 network can be encrypted and verified, offering enhanced protection against eavesdropping and man-in-the-middle attacks. Additionally, IPv6 simplifies the process of implementing secure communications, which can encourage wider adoption of encryption across the internet.
### Challenges in IPv6 Security
Despite its advantages, IPv6 also presents new security challenges. The sheer size of the IPv6 address space can make it difficult for traditional security tools, like firewalls and intrusion detection systems, to effectively monitor and filter traffic. Moreover, many organizations are still learning how to properly configure and secure IPv6 networks, which can lead to vulnerabilities. Transition mechanisms designed to facilitate the coexistence of IPv4 and IPv6 can also introduce security gaps if not implemented correctly.
### Best Practices for Ensuring IPv6 Security
To fully leverage the benefits of IPv6 while mitigating potential risks, organizations should adopt a set of best practices. These include conducting comprehensive training for IT staff on IPv6 concepts, configuring IPsec for all IPv6 traffic, and updating security policies to address the unique aspects of IPv6. Regular network audits and penetration testing should be conducted to identify and resolve security weaknesses. Additionally, organizations should stay informed about the latest developments in IPv6 security to proactively address emerging threats.
IPv6 Security
Starting with IPv6 Host Exposure
– IPv6 host exposure refers to connecting IPv6-enabled devices to the internet, allowing them to communicate and interact with other devices and services. Unlike IPv4, which uses a 32-bit address format, IPv6 utilizes a 128-bit address format. This vast address space enables a significant increase in the number of available IP addresses, catering to the growing needs of our interconnected world.
– With the exponential growth of internet-connected devices, IPv6 offers a virtually limitless supply of IP addresses. This alleviates the issue of address exhaustion that plagues IPv4 and ensures every device can have a unique, globally routable IP address. The abundance of addresses also simplifies network management and eliminates the need for complex workarounds, such as network address translation (NAT).
– IPv6 incorporates several security enhancements compared to its predecessor. Built-in IPsec support provides end-to-end encryption, ensuring data confidentiality and integrity. Additionally, IPv6 simplifies network configuration by eliminating the need for specific protocols like DHCP, reducing potential attack vectors.
– The Internet of Things (IoT) has grown remarkably in recent years. IPv6 host exposure plays a crucial role in supporting the proliferation of IoT devices by offering a virtually limitless address pool. Moreover, as emerging technologies like 5G and augmented reality continue to evolve, IPv6 provides the necessary foundation for seamless connectivity and innovation.
**The Benefits of IPv6 Host Exposure**
Embracing IPv6 host exposure brings several advantages. Firstly, it allows for enhanced end-to-end connectivity, enabling direct communication between devices without the need for complex network address translation (NAT) mechanisms. Additionally, IPv6 enables efficient peer-to-peer communication, facilitating faster data transfer and reducing latency. With a larger address space, IPv6 also supports the growth of Internet of Things (IoT) devices, paving the way for a more connected and automated world.
**Potential Risks and Vulnerabilities**
While the adoption of IPv6 host exposure offers numerous benefits, it also introduces potential risks. One such concern is the increased exposure of devices to the external network, making them more susceptible to unauthorized access and potential security breaches. The larger address space of IPv6 can make it challenging to manage and secure all connected devices effectively. Furthermore, the coexistence of IPv6 and IPv4 protocols poses compatibility issues that could be exploited by malicious actors.
**Best Practices for Secure IPv6 Host Exposure**
To mitigate the risks associated with IPv6 host exposure, implementing robust security measures is crucial. Here are some best practices to consider:
1. Firewall Configuration: Configure firewalls to allow only necessary traffic and filter out unauthorized access attempts.
2. Network Segmentation: Implement proper network segmentation to isolate critical devices and services from potential threats.
3. Regular Monitoring and Updates: Continuously monitor network traffic, detect anomalies, and apply necessary updates to devices and firmware.
4. Access Control Policies: Enforce strict access control policies, utilizing strong authentication mechanisms and encryption protocols.
5. IPv6 Security Assessments: Conduct periodic security assessments to identify vulnerabilities and address them promptly.
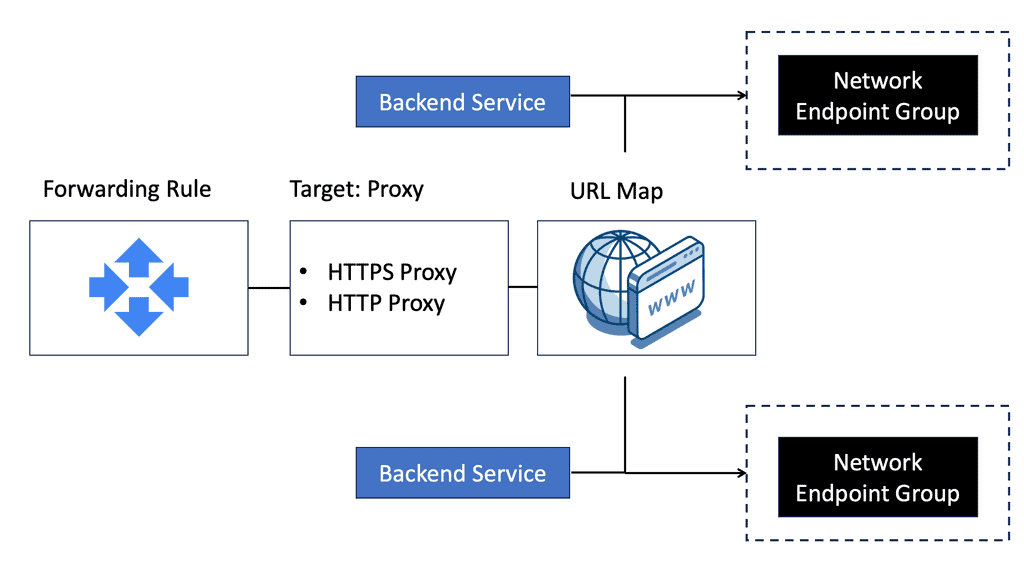
Example Segmentation Technology: NEGs
### Introduction to Network Endpoint Groups
In the ever-evolving landscape of cloud computing, efficient network management is crucial. Network Endpoint Groups (NEGs) on Google Cloud offer a robust solution for managing backend services with precision and flexibility. By segmenting network traffic, NEGs allow for more granular control, paving the way for optimized performance and scalability. In this blog post, we’ll explore the ins and outs of NEGs, their benefits, and how you can leverage them to enhance your cloud infrastructure.
### Understanding Network Endpoint Groups
Network Endpoint Groups are a Google Cloud feature that organizes endpoints—such as VM instances, internet-facing endpoints, or serverless services—into groups based on specific criteria. This segmentation allows for targeted traffic management and routing, ensuring that each endpoint can be addressed according to its role within the cloud ecosystem. NEGs are particularly useful in scenarios where services are distributed across multiple regions or when leveraging hybrid cloud strategies.
### The Benefits of Using NEGs
One of the primary advantages of using Network Endpoint Groups is the ability to improve load balancing. By grouping endpoints, you can direct traffic more efficiently, reducing latency and improving response times. Additionally, NEGs offer enhanced flexibility by allowing you to manage endpoints within a single, consistent framework, regardless of their nature or location. This is particularly beneficial for applications that require high availability and fault tolerance.
Example: IPv6 Connectivity
Understanding IPv6 Basics
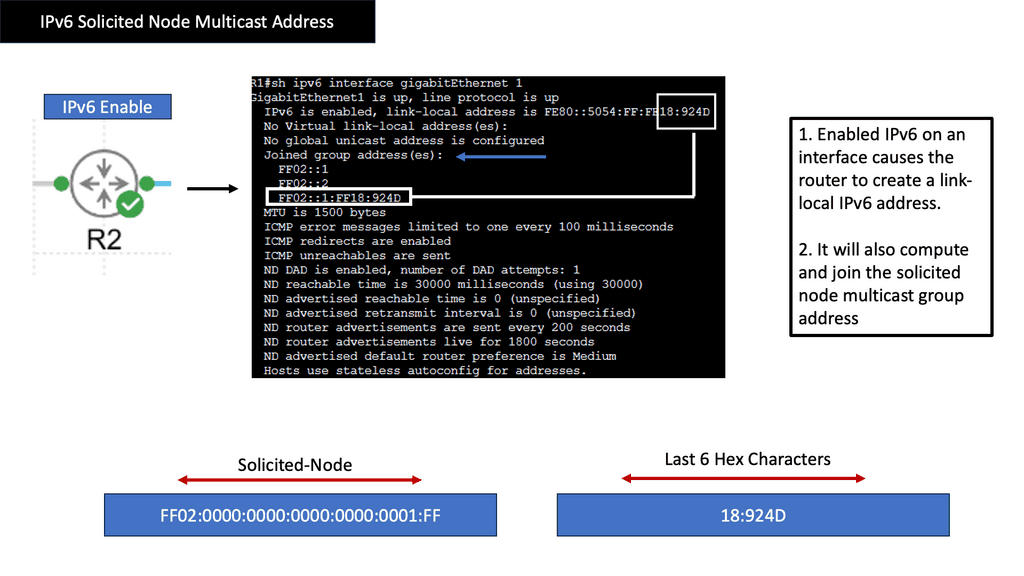
Before we delve into Solicited Node Multicast Address, let’s briefly revisit the fundamentals of IPv6. IPv6, the successor to IPv4, offers a much larger address space, improved security features, and enhanced support for mobile devices. With its 128-bit address format, IPv6 provides a staggering number of unique addresses, allowing for the growth and scalability of the modern Internet.
Solicited Node Multicast Address is a unique feature of IPv6 that plays a vital role in efficient communication within a network. When a node joins the network, it sends a Neighbor Solicitation message to discover the link-layer address of another node. The Solicited Node Multicast Address enables this process by allowing multiple nodes to simultaneously receive the Neighbor Solicitation message.
Formation and Structure
To create a Solicited Node Multicast Address, the last 24 bits of the corresponding unicast address are replaced with a well-defined prefix. This prefix, “ff02::1:ff00:0/104”, ensures uniqueness and easy identification within the IPv6 network. By utilizing this specific multicast address, nodes can efficiently resolve link-layer addresses and establish communication.
The utilization of Solicited Node Multicast Address brings several advantages to IPv6 networks. First, it reduces network traffic by enabling multiple nodes to receive Neighbor Solicitation messages simultaneously, enhancing network efficiency and reducing unnecessary bandwidth consumption. Second, the use of Solicited Node Multicast Address simplifies address resolution processes, leading to faster and more reliable communication within local networks.
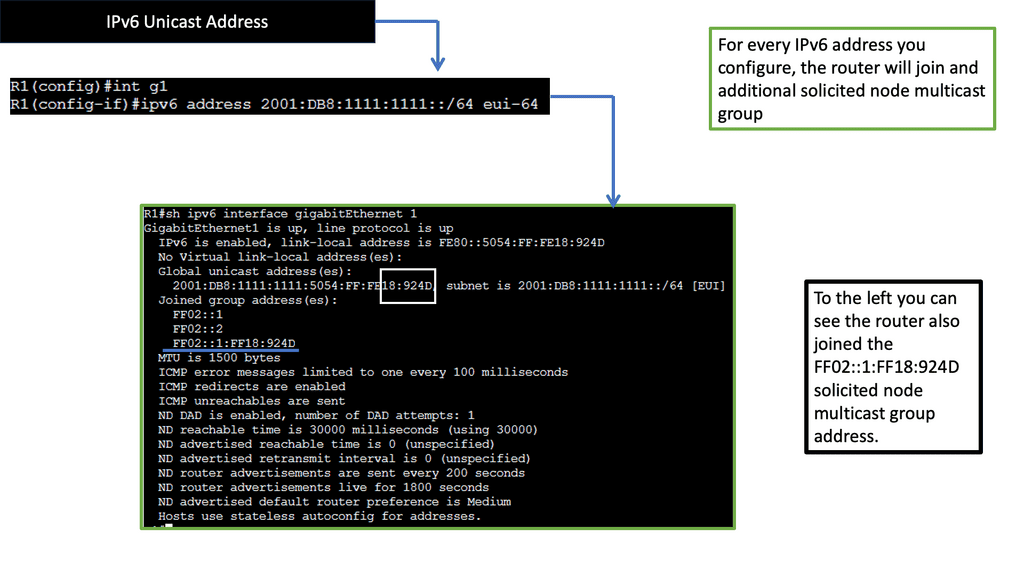 Example: IPv6 NDP. Understanding the Basics
Example: IPv6 NDP. Understanding the Basics
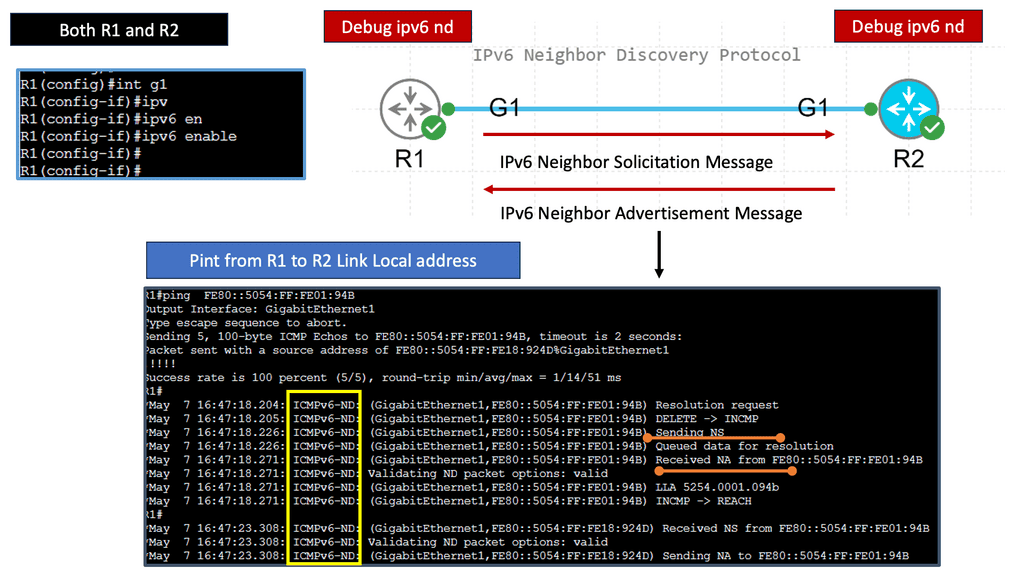
The IPv6 Neighbor Discovery Protocol, or NDP, is an essential component of IPv6 networks. It replaces the Address Resolution Protocol (ARP) used in IPv4 networks. NDP enables nodes on the network to discover and communicate with other nodes in the same network segment.
To fully comprehend the functioning of NDP, it is crucial to explore its key components. One such component is Neighbor Solicitation, which allows a node to determine the link-layer address of another node. Another component is Neighbor Advertisement, which provides the necessary information for nodes to update their neighbor caches.
IPv6 Neighbor Discovery:
The IPv6 Neighbor Discovery Protocol benefits network administrators and end-users alike. Firstly, it simplifies network configuration by eliminating the need for manual configuration of IPv6 addresses. Additionally, it enables efficient address resolution and facilitates the automatic configuration of routers. Moreover, NDP enhances network security by supporting features such as Secure Neighbor Discovery (SEND) and Cryptographically Generated Addresses (CGA).
The versatility of the IPv6 Neighbor Discovery Protocol allows for its application in various use cases. One prominent use case is in large-scale networks, where NDP helps streamline address assignment and management.
Furthermore, NDP plays a crucial role in mobile networks, enabling seamless handover and efficient neighbor detection. Additionally, it is employed in Internet of Things (IoT) deployments, facilitating device discovery and communication.
Considerations: Implementing IPv6 Host Exposure
Before embracing IPv6 host exposure, organizations must assess their network infrastructure’s readiness. This includes evaluating the compatibility of existing hardware, software, and network devices. Upgrading or replacing incompatible components may be necessary to ensure smooth implementation.
With IPv6’s vast address space, proper address planning and management become critical. Organizations must design an addressing scheme that aligns with their requirements and growth projections. Implementing robust address management practices, such as hierarchical addressing and efficient allocation, can streamline network operations.
During the transition from IPv4 to IPv6, coexistence between the two protocols becomes essential. Various transition mechanisms, such as dual-stack, tunneling, and translation, enable interoperability between IPv4 and IPv6 networks. Understanding these mechanisms and selecting the most suitable approach for a smooth transition is vital.
Understanding IPv6 Security
IPv6 presents a multitude of security considerations that differ from its predecessor, IPv4. From the expanded address space to autoconfiguration mechanisms, this section explores IPv6’s unique features and how they impact security. We delve into the potential vulnerabilities and threats organizations must know when implementing IPv6 networks.
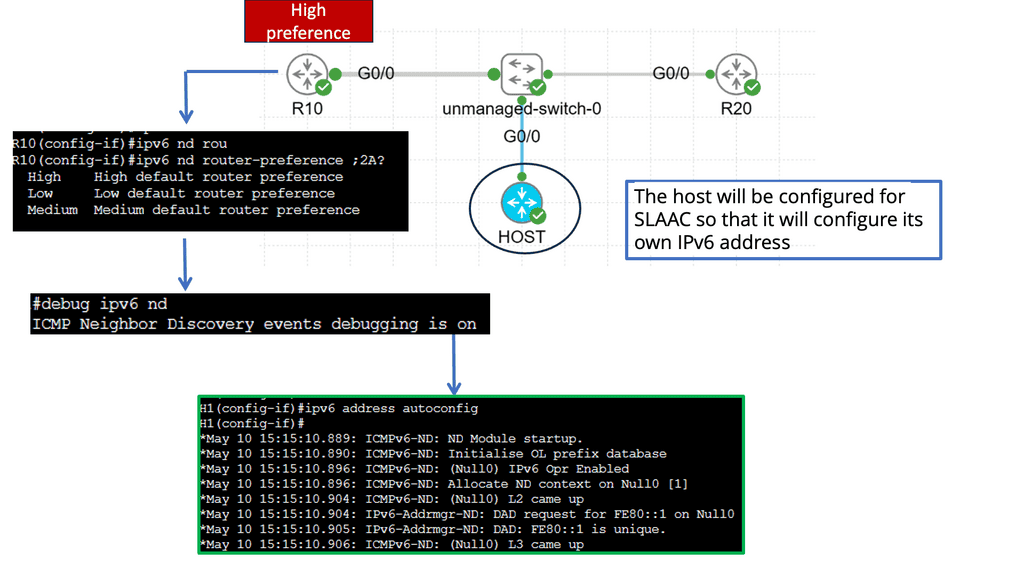
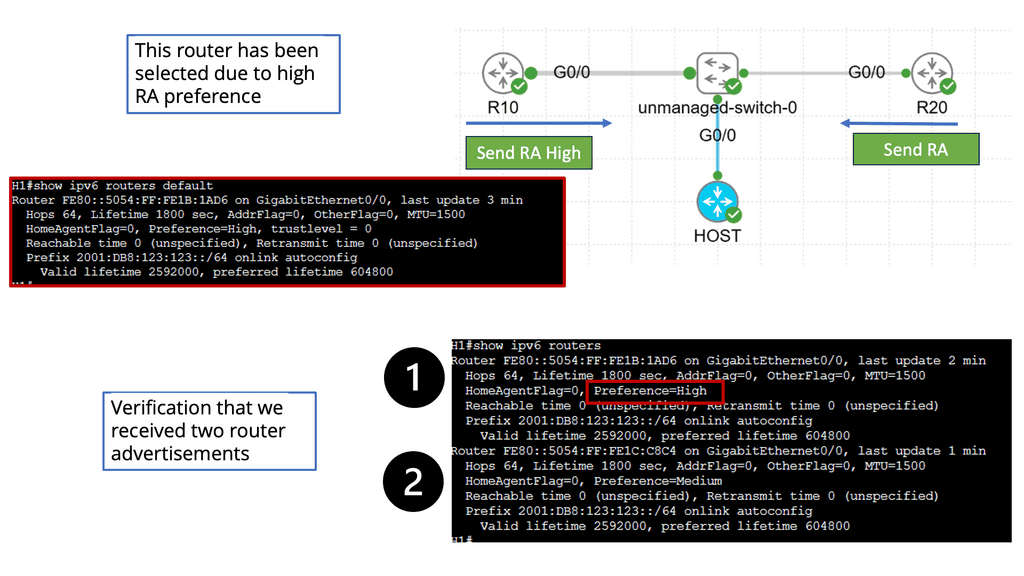
Understanding Router Advertisement Preference
1 – Router advertisement preference is a fundamental aspect of IPv6 that determines the selection of default gateways by hosts on a network. It involves using Router Advertisement (RA) messages periodically sent by routers to announce their presence and share configuration information with hosts.
2 – RA messages contain essential information such as the router’s IP address, prefix, and configuration options. The router preference field within the RA message plays a vital role in indicating routers’ priorities. Hosts utilize this information to select the most suitable default gateway for their traffic.
3 – Several factors contribute to the determination of router preference. These include the router’s reliability, the advertised prefix length, and the presence of additional configuration options. Understanding these factors allows network administrators to fine-tune their network configurations and ensure optimal routing.
Best Practices for Securing IPv6 Networks
To mitigate the risks associated with IPv6, organizations should adhere to best practices for securing their networks. This section outlines essential steps that can be taken, including network segmentation, robust firewall configurations, and secure neighbor discovery protocols. Additionally, we discuss the importance of monitoring and auditing IPv6 traffic to detect and respond to potential threats effectively.
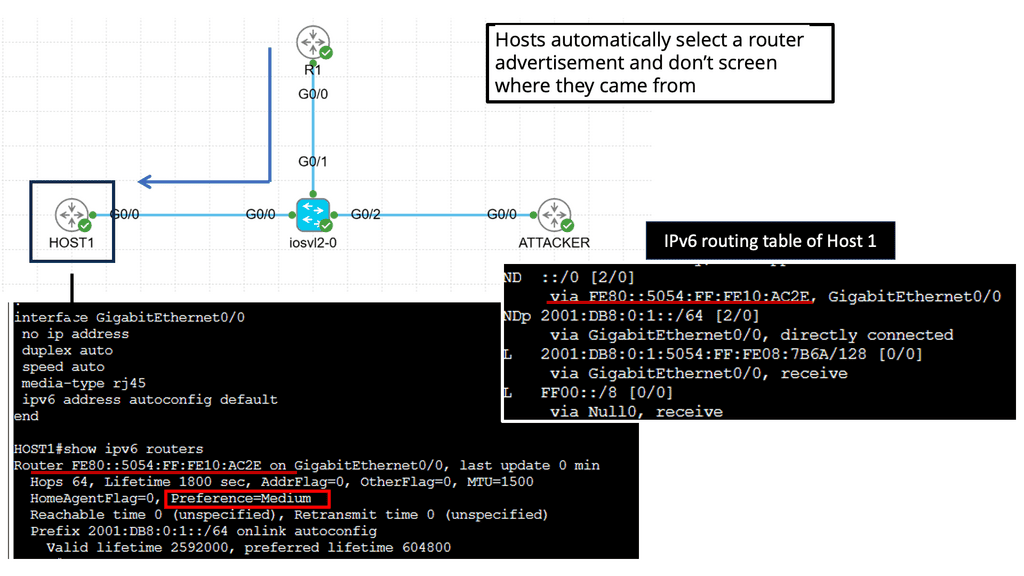
Understanding Router Advertisements
Router Advertisements are an essential part of IPv6 network configuration. They allow routers to announce their presence and provide network-related information to hosts. However, if not properly managed, these advertisements can also become a gateway for potential security breaches.
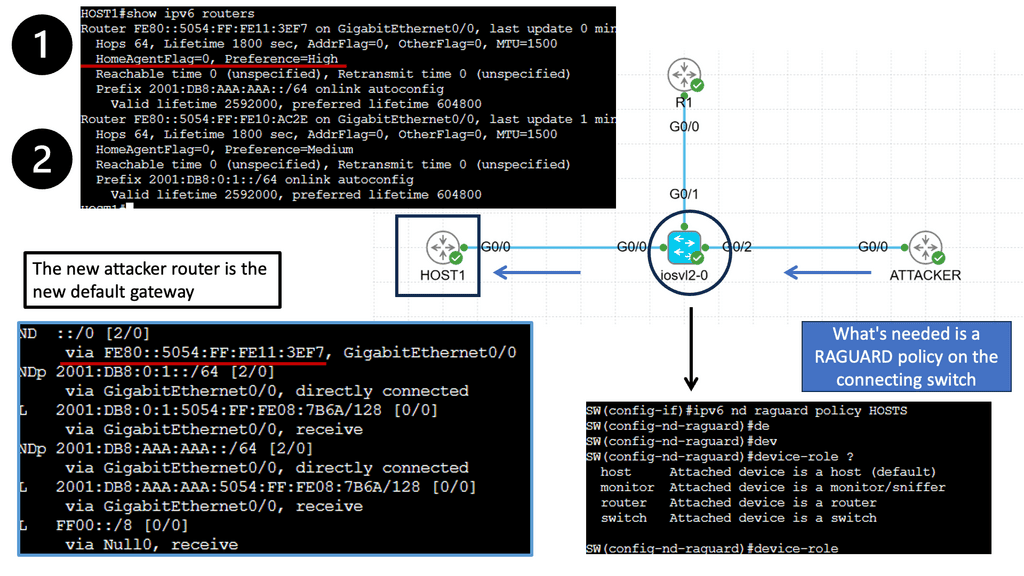
IPv6 RA Guard is a security feature designed to mitigate the risks of rogue router advertisements. Its primary purpose is to prevent unauthorized or malicious RA messages from compromising the network infrastructure. Network administrators can ensure that only legitimate routers can advertise network parameters by implementing RA Guard.
Inspecting RA Messages
IPv6 RA Guard operates by inspecting the RA messages received on network interfaces. It verifies the legitimacy of these messages by checking various attributes such as source IP address, hop limit, and ICMPv6 Router Advertisement flags. The RA Guard can drop or log the suspicious packets if a potential threat is detected.
Configuring IPv6 RA Guard depends on the specific network infrastructure and devices. Generally, it involves enabling RA Guard to use appropriate network interfaces and defining policies for handling suspicious RA messages. Network administrators should carefully plan and test their configuration to ensure a seamless implementation.
**No NAT in IPv6**
IPv6, or Internet Protocol version 6, is the latest version of the Internet Protocol, designed to replace the older IPv4. IPv6 provides a larger address space, improved security, and better support for mobile devices and multimedia applications. However, as with any new technology, IPv6 introduces new security challenges, including IPv6 host exposure.
Host exposure refers to a host being directly accessible from the Internet without any network address translation (NAT) or firewall protection. In IPv4, host exposure is typically prevented by using NAT, which maps private IP addresses to public IP addresses and hides the internal network from the outside world. However, in IPv6, there is no need for NAT, as each device can have a unique public address.
This means IPv6 hosts are more exposed to the Internet than their IPv4 counterparts. Attackers can scan for and exploit vulnerabilities in IPv6 hosts directly without penetrating any firewalls or NAT devices. Therefore, taking appropriate measures to protect IPv6 hosts from exposure is essential.
**The Role of Firewalls and IPsec**
One way to protect IPv6 hosts is to use firewalls that support IPv6. These firewalls can filter incoming and outgoing traffic based on predefined rules, providing protection similar to NAT in IPv4. It is also important to regularly apply security patches and updates to IPv6 hosts to prevent known vulnerabilities from being exploited.
Another way to protect IPv6 hosts is to use IPv6 security protocols, such as IPsec. IPsec provides authentication and encryption for IPv6 packets, ensuring they are not tampered with or intercepted by attackers. IPsec can secure communication between hosts or between hosts and routers.
Related: Before you proceed, you may find the following post helpful:
IPv6 Host Exposure
IPv6 Security
IPv6 security is an essential component of modern network architecture. By utilizing the latest security technology, organizations can ensure their networks are secure from malicious actors and threats. IPv6 is an upgrade from the IPv4 protocol and has many advantages. It is faster, has a larger address space, and has more efficient routing protocols. It also provides better options for network segmentation, making it easier to create secure networks.
So, what is IPv6 Host Exposure? Firstly, IPv6 as a protocol suite isn’t inherently more or less secure than its predecessor. However, as with IPv4, most IPv6 attacks and security incidents arise from design and implementation issues rather than weaknesses in the underlying technology. Therefore, we need to consider critical areas of IPv6 security, such as IPv6 host exposure and the numerous IPv6 security vulnerabilities that IPv6 stacks are susceptible to.
Many organizations already have IPv6 running on their networks and must realize it. In addition, many computer operating systems now default to running both IPv4 and IPv6. This is known as dual-stack mode, which could cause security vulnerabilities if one is less secure than the other. IPv6 security vulnerabilities currently exist, and as the popularity of the IPv6 protocol increases, so does the number of IPv6 security vulnerabilities and threats.
IPv6 FHS (First Hop Security) protects IPv6 on L2 links.
Initially, you might think the first hop is the first router, but that is false. These are all features of switches, specifically those that sit between your end devices and your first router.
First Hop Security features are listed below.
RA Guard: With RA Guard, hosts don’t care where router advertisements come from; any device on the network can transmit them. Any offer will be gladly accepted. You can filter router advertisements with RA Guard. If you inspect RAs and permit them only when they meet specific criteria, you can create a simple policy that only accepts RAs on specific interfaces.
IPv6 DHCP Guard: similar to IPv4 DHCP snooping. Only trusted interfaces are allowed to transmit DHCP packets. Additionally, you can create policies that only allow specific prefixes and preferences to receive DHCP packets.
Inspection of NS (Neighbor Solicitation) and NA (Neighbor Advertisement) messages: the switch inspects and stores NS and NA messages in the IPv6 binding table. If any NS/NA messages are spoofed, the switch can drop them.
Source Gaurd: When a packet’s source address does not appear in the IPv6 binding table, the switch filters it, preventing spoofing attacks.
Guide: IPv6 security with access lists
Access lists in IPv6 are used more and less like they are in IPv4. Access lists are used to filter and select traffic. If you recall, IPv6 access lists have three invisible statements at the bottom:
- permit icmp any any nd-na
- permit icmp any any nd-ns
- deny ipv6 any any
In the following screenshot, I have IPv6 access set inbound on R1 to explicitly permit telnet traffic from R2. The access list, known as an access filter, will block any other type of traffic, such as ping. As a security best practice, I recommend you also turn on “no IPv6 unreachables” on the interface. This will stop the AAAA from appearing, which is a security threat.
You don’t want a bad actor to know that an access filter is dropping their packets, as they will try to circumvent it. With the following command enabled under the interface, packets are dropped silently.
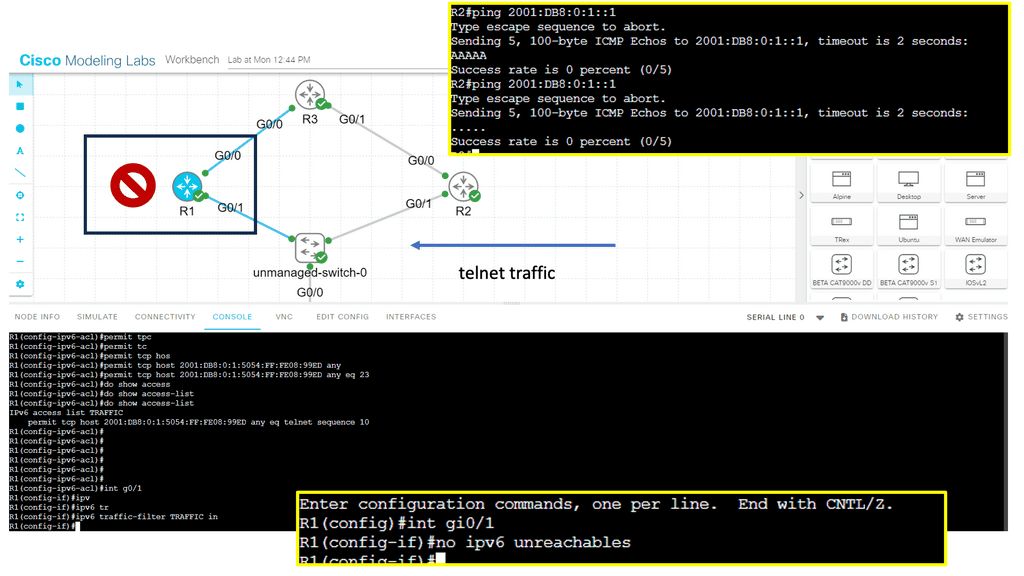
**Implications of IPv6 Host Exposure**
1. Increased attack surface: IPv6’s larger address space makes it easier for attackers to scan and identify vulnerable devices. With direct access to each device, attackers can exploit security vulnerabilities, potentially leading to unauthorized access, data breaches, or service disruptions.
2. Lack of visibility: Traditional security tools and monitoring systems primarily designed for IPv4 networks may struggle to detect and defend against threats in an IPv6 environment effectively. This lack of visibility can leave organizations unaware of potential security breaches or ongoing attacks.
3. Misconfiguration risks: IPv6 addressing and configuration complexity can result in misconfigurations, inadvertently exposing hosts to the Internet. These misconfigurations can open up opportunities for attackers to exploit and compromise devices or networks.
4. Privacy concerns: IPv6 addresses can contain unique identifiers, potentially compromising users’ privacy. This can enable tracking and profiling of individuals, raising privacy concerns for individuals and organizations.
**Challenges with IPv4 designs**
In IPv4’s initial design, network security was a minor concern. However, as IPv4 was developed and the Internet explosion occurred in the 1990s, Internet threats became prolific, and we were essentially wide open to attack. If the current circumstances of Internet threats could have been predicted when IPv4 was being developed, the protocol would have had more security measures incorporated.
IP Next Generation (IPng) was created, becoming IPv6 (RFC 1883). IPv6 is the second network layer standard protocol that follows IPv4, offers several compelling functions, and is the next step in the evolution of the Internet Protocol.
IPv6 provides several improvements over its predecessor. The following list summarizes the characteristics of IPv6 and the improvements it can deliver:
- Larger address space: Increased address size from 32 bits to 128 bits
- Streamlined protocol header: Improves packet-forwarding efficiency
- Stateless autoconfiguration: The ability for nodes to determine their address
- Multicast: Increased use of efficient one-to-many communications
- Jumbograms: The ability to have huge packet payloads for greater efficiency
- Network layer security: Encryption and authentication of communications
- Quality of service (QoS) capabilities: QoS markings of packets and flow labels that help identify priority traffic,
Nothing changes above the Layer 3 “Network” layer.
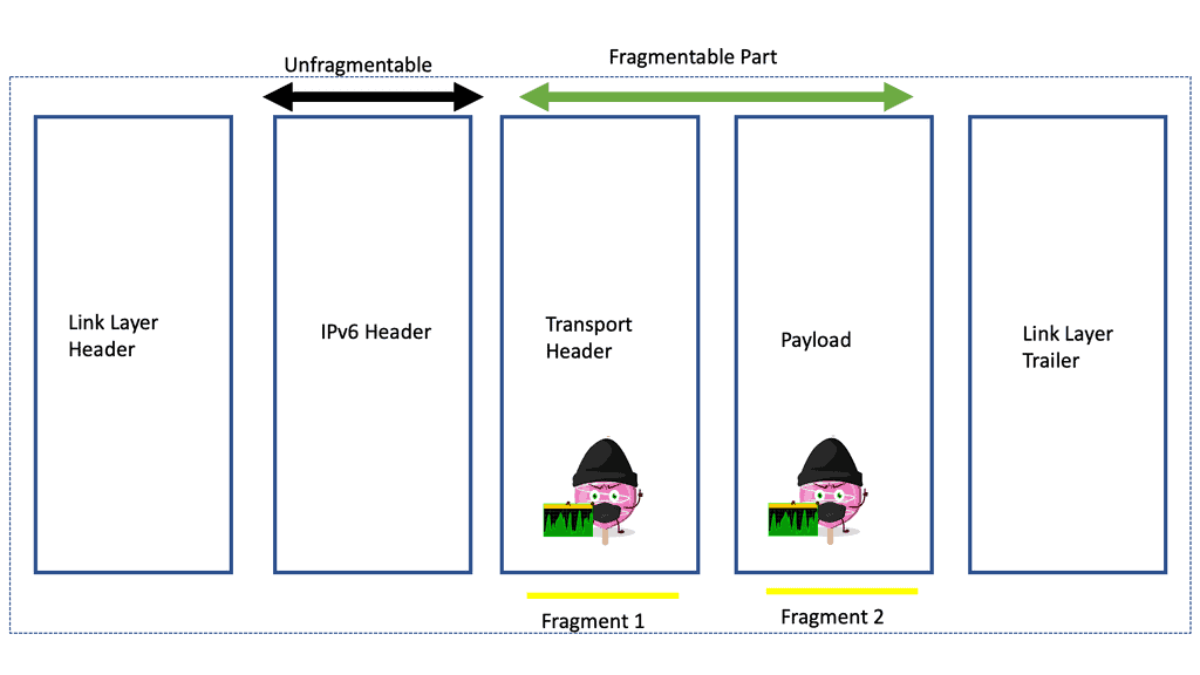
Deploying IPv6 changes nothing above the Layer 3 “Network” layer. IPv4 and IPv6 are network layer protocols, and protocols above and below remain the same for either IP version. Problems such as a lack of a session layer with Transmission Control Protocol ( TCP ) continue to exist in IPv6, along with new security issues of IPv6 fragmentation. In addition, the limitations of multihoming and the exponential growth of the Default Free Zone ( DFZ ) table size are not solved by deploying IPv6. Attacks against any IPv6 network fall within the following areas and are similar to those related to IPv4 attacks,
Securty Attack | Security Attack Area |
Attack Type 1 | Internet ( DMZ, fragmentation, web pages ) |
Attack Type 2 | IP Spoofing, protocol fuzzing, header manipulation, sessions hijacking |
Attack Type 3 | Buffer overflows, SQL Injection, cross-site scripting |
Attack Type 4 | Email ( attachements, phishing ) |
Attack Type 5 | Worms, viruses, DDoS |
Attack Type 6 | Chat, peer to peer |
We have similar security problems but with different countermeasures. For example, instead of IPv4 ARP spoofing, we have IPv6 ND spoofing. Existing network attacks such as Flooding / DDoS, eavesdropping, session hijacking, DNS attacks, man-in-the-middle attacks, and routing security problems are still present with IPv6.
Application-level attacks
The majority of vulnerabilities are at the application layer. Application layer attacks in IPv4 and IPv6 are identical, and security concerns with SQL injections still occur at layers operating over IPv6. However, new IPv6 security considerations such as Dual-Stack-exposures and Tunneling exposures not concerned with IPv4 must be addressed as some of the principal IPv6 security vulnerabilities.
IPv6 Security Vulnerabilities
Running both IPv4 and IPv6 at the same time is called Dual-Stack. A router can support two or more different routed protocols and forward for each type of traffic. The IPv4 and IPv6 protocols can share the same physical node but act independently. Dual stacking refers to the concept known as “ships-in-the-night-routing”; packets from each protocol can pass without affecting one another.
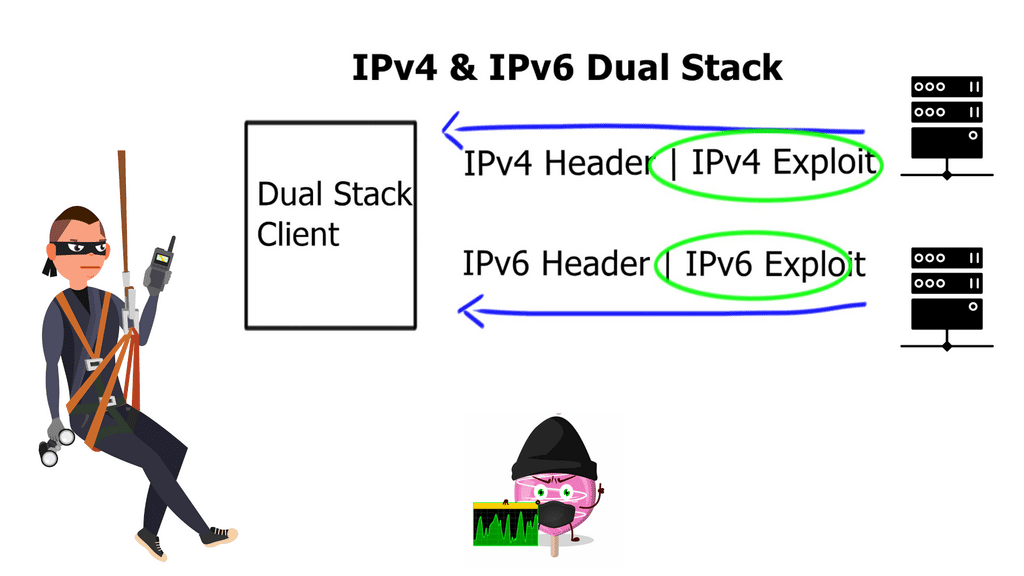
**Avoid Dual Stack when possible**
It is recommended to avoid Dual Stack as the Multi-Protocol world is tricky. The problem may arise if someone configures IPv6 without prior knowledge. All servers and hosts would then expose themselves to IPv6 threats. For example, imagine you have a protected server segment-running IP tables, NIC-level firewalls, and stateful aggregation layer firewalls on the servers.
Best practices are followed, resulting in a protected segment. What you do not control is whether servers have IPv6 enabled. When a router sends IPv6 Router Advertisement ( RA ) messages, these servers will auto-configure themselves and become reachable over IPv6 transport. This may not be a problem with Windows servers. Windows firewall works for both IPv4 and IPv6. Unfortunately, Linux servers have different IP tables for IPv4 and IPv6; Iptable for IPv4 and IP6tables for IPv6.
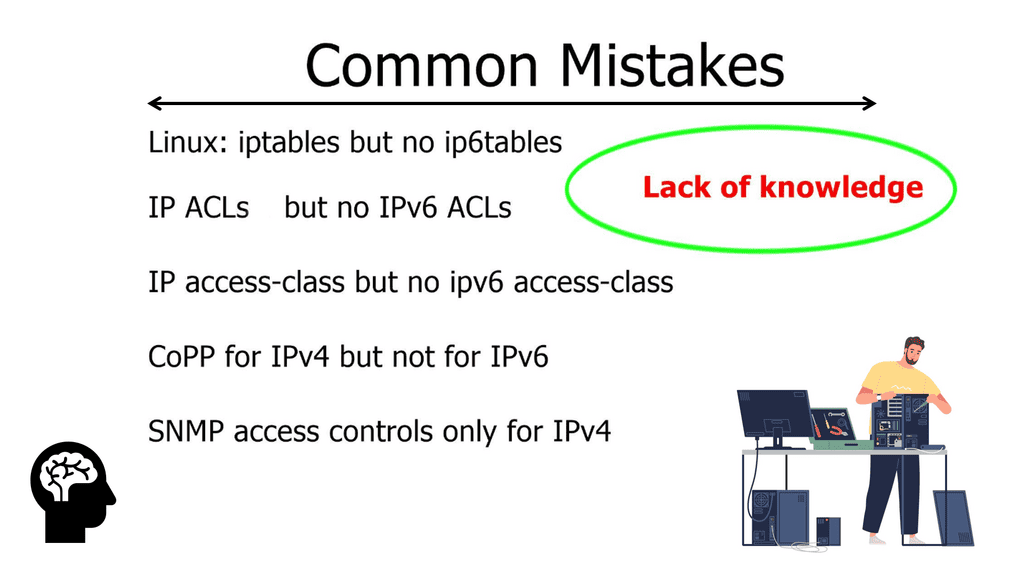
Linux hosts receive IPv6 RA messages, and some dual-stack Linux hosts with link-local addresses establish outbound IPv6 sessions. The link-local is local to the link, and the first-hop router sends an ICMP reply saying “out of scope.” Most Linux OSs will terminate IPv6 sessions so you can fall back to IPv4.
However, other versions of Linux do not fall back immediately and wait for TCP to time out, causing significant application outages. As a temporary measure, people started to build IPv6 tunnels. As a result, tunnel-related exposure exists. Teredo is the most notorious attack on IPv6. Therefore, all IPv6 tunnels should be blocked by the firewall.
**Pay Close Attention To Tunnels**
IPv4 and IPv6 are not natively compatible with handling mixed networks. However, IPv6 traffic can be carried over IPv4 native networks using tunnels. Tunnels may have security drawbacks, such as reducing visibility into traffic, traversing them, and bypassing firewalls. In addition, an attacker can manipulate the traffic flow by abusing auto-tunneling mechanisms.
Tunnels should be treated with caution. Generally, static tunnels are preferred over dynamic tunnels, and they should only be enabled when explicitly needed. Filtering can also control which hosts can act as tunnel endpoints at the firewall level.
Guide with IPv6 RA
In the following, we address IPv6 RA. IPv6 Router Advertisement (RA) is a key mechanism in IPv6 networks that allows routers to inform neighboring hosts and networks about their presence and provide essential network configuration information. Routers periodically send RA messages, enabling hosts to autoconfigure their network settings, such as IPv6 addresses, default gateways, and other parameters.
The command ipv6 address autoconfig default creates a static route on R2, potentially creating a security flaw in certain use cases.
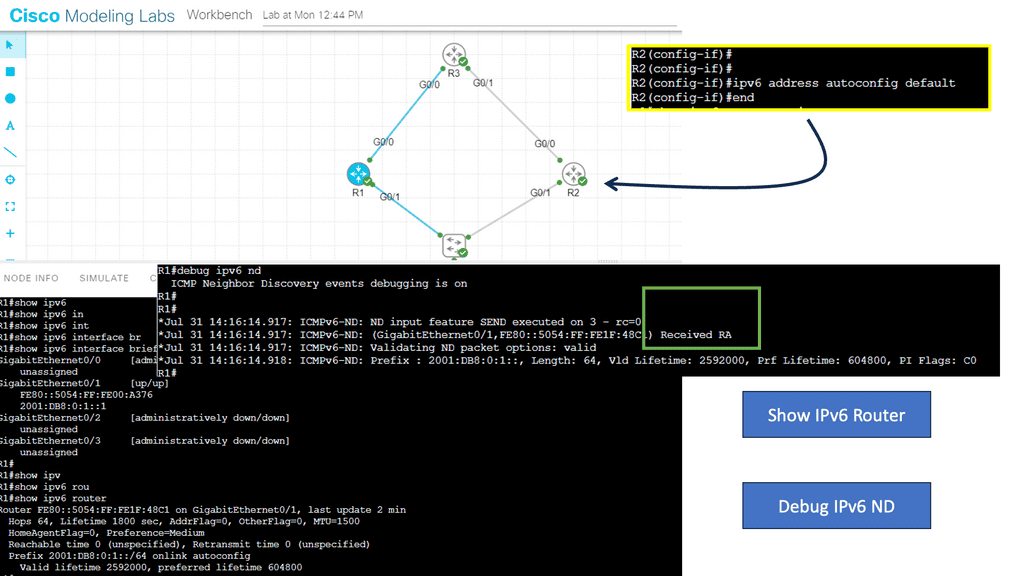
Use a random addressing scheme instead of a predictable one
The predictability of IPv6 addresses has contributed significantly to the success of reconnaissance attacks against IPv6 subnets. Even though this can be helpful for network administration, it dramatically hinders IPv6 security. In many cases, these attacks can be mitigated by using random addresses, especially for static assignments.
Autoconfiguration once resulted in Layer 3 IPv6 addresses being derived partly from Layer 2 MAC addresses where autoconfiguration is used. As a result, attackers may find it easier to discover hosts. Now, most operating systems can generate random or pseudo-random addresses, so check if this feature is enabled on your endpoints when autoconfiguration is allowed.
IPv6 First Hop Vulnerabilities
- Fake router advertisement ( RA ) messages
IPv6 routers advertise themselves via router advertisement ( RA ) messages. Hosts listen to these messages and can figure out what the first hop/gateway router is. If a host needs to send traffic off its local LAN ( off-net traffic ), it sends it to the first-hop router with the best RA message. In addition, RA messages contain priority fields that can be used for backup routing.
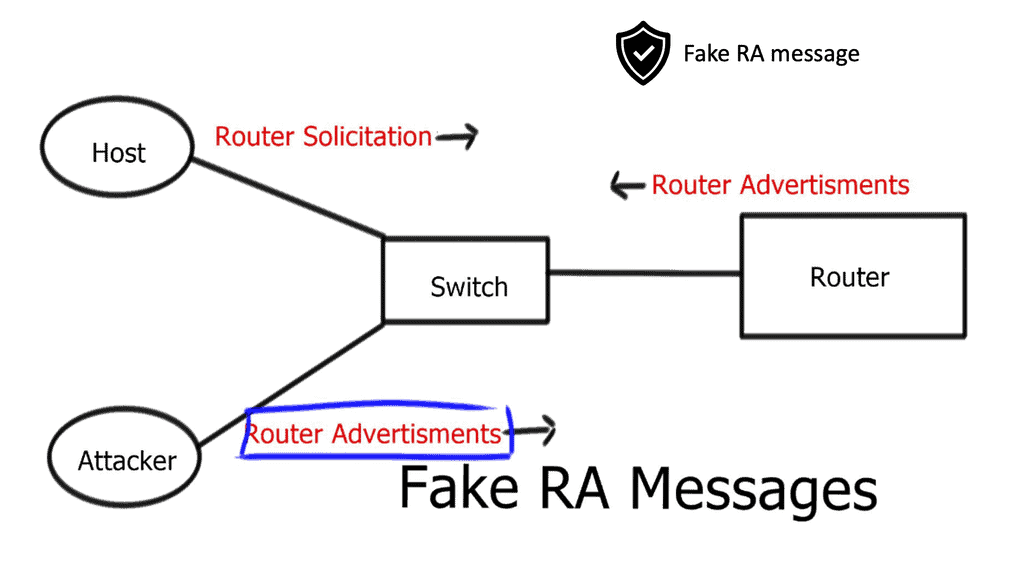
- IPv6 first-hop routers
Intruders can advertise themselves as IPv6 first-hop routers, and any host that believes it will send the intruder its off-net traffic. Once intercepted, attackers have numerous attacking options. It can respond to hosts’ Domain Name System ( DNS ) requests instead of sending them to a legitimate DNS server. Potential DoS attacking hosts. RFC 6101 introduced mitigation techniques in Port ACL, RA-guard lite, and RA-guard.
- IPv6 DHCPv6 attacks
An intruder could pretend to be a DHCPv6 server. If hosts use Stateless Address Autoconfiguration ( SLAAC ) for address configuration, they still require the address of the IPv6 DNS server. Hosts obtain their IPv6 address automatically; it sends out DHCP information requests asking for the IPv6 address of the DNS server. Intruders can intercept and send in Bogus IPv6 for the hostnames that the client is querying for.
- Fake neighbor advertisement messages
When a device receives a neighbor solicitation, it looks into the source address of the message and stores the result in the cache. Excessive neighbor solicitation from an intruder can fill up this cache-causing router ND cache overflow and increased CPU load on the router, overloading the control plane.
Well-known problems Well-known countermeasures Large scale flooding Traffic scrubbing Source address spoofing RPF checks TCP SYN attacks TCP SYN cookies TCP slowdown attacks Load balancers and Proxies Application-level attacks Web Application Firewalls ( WAFs ) IP Fragmentation attacks ACL’s and stateless filters
Remote neighbor discovery attacks
Remote neighbor discovery occurs when an intruder scans IPv6 subnets with “valid” IPv6 packets, either “valid” TCP SYN packets or PINGs. Unknown directly connected destination IPv6 addresses trigger Router Solicitation neighbor discovery mechanism, causing ND cache and CPU overload. The critical point is an attacker can trigger the attack remotely.
This may not have been a problem with IPv4, as subnets are small. However, in IPv6, you have large subnets; you can try to scan them and generate neighbor cache problems on the last layer 3 switches.
Input ACL that allows known IPv6 subnets. However, some devices do the ND process before checking the inbound ACL. Check the order of operation in the forwarding path. Control plane policing. Cache limits. Prefix longer than /64. People are using /128 on server subnets. Use with care. It is better to use Inbound ACL and not with longer prefixes.
Duplicate address detection ( DAD ) attacks
Autoconfiguration works when hosts create their IPv6 address and send a packet asking if anyone else uses it. An intruder can then reply and say yes, I do, which disables auto-configuration on that LAN.
IPv6 host exposure and IPv6 fragmented DOS attacks
IPv6 has multiple extension headers, offering attackers tremendous options for attack. Potentially, there are too many extension headers attempting to generate fragments. Generating fragments hides the real TCP and UDP port numbers into fragments where firewalls can’t immediately see them. Firewalls should be configured to drop fragmented headers.
- The hop-by-hop Header tells each switch to inspect and act on this header, which can lead to a great DoS tool.
- The routing header is the same as the IP source route in IPv4. It should drop by default.
- A key point: Filter on the IPv6 extension headers
Firewalls and ACLs should be able to filter extension headers. However, performing Deep Packet Inspection (DPI) on an IPv6 packet that contains many extension headers is resource-intensive, so firewalls should limit the number of extension headers.
**Mitigation Strategies:**
1. Network segmentation: By properly segmenting the network and implementing firewalls, organizations can limit the exposure of IPv6 hosts. This approach helps isolate critical assets from threats and reduces the attack surface.
2. Continuous monitoring: Organizations should use network monitoring tools to detect and analyze IPv6 traffic. This ensures the timely detection of potential security incidents and allows for effective response and mitigation.
3. Regular security assessments: Conducting periodic security and penetration testing can help identify vulnerabilities and weaknesses in IPv6 deployments. Addressing these issues promptly can prevent potential host exposure and minimize risks.
4. Proper configuration and patch management: Organizations should ensure that IPv6 devices are appropriately configured and regularly updated with the latest security patches. This reduces the likelihood of misconfigurations and minimizes the risk of known vulnerabilities being exploited.
5. Education and awareness: Organizations should prioritize educating their employees about the risks associated with IPv6 host exposure and provide guidelines for secure IPv6 deployment. This empowers individuals to make informed decisions and helps create a security-conscious culture.
Final Points: IPv6 Host Exposure
IPv6, or Internet Protocol Version 6, is crucial for the continued growth and sustainability of the internet. Unlike its predecessor, IPv4, which uses a 32-bit address space, IPv6 employs a 128-bit address space, allowing for approximately 340 undecillion unique addresses. This expansive address space is essential for accommodating the burgeoning number of internet-connected devices, from smartphones and laptops to smart appliances and IoT gadgets.
One of the key features of IPv6 is its ability to assign a unique public IP address to every device, potentially making them directly reachable from anywhere in the world. While this eliminates the need for NAT (Network Address Translation) and simplifies routing, it also increases the risk of host exposure. Host exposure refers to the vulnerability of devices to unauthorized access or cyber-attacks, as they are more visible on the global internet.
The increased visibility of devices under IPv6 necessitates a reevaluation of network security strategies. Traditional security measures like firewalls and intrusion detection systems must be adapted to account for the unique characteristics of IPv6. Organizations must ensure that their security policies are robust enough to protect against the threats posed by exposed hosts. This includes implementing effective access controls, monitoring network traffic, and keeping all devices and systems up-to-date with the latest security patches.
To mitigate the risks associated with IPv6 host exposure, network administrators should adopt a proactive approach. This includes:
1. **Implementing IPv6 Firewalls:** Ensure that IPv6-specific firewalls are in place to filter traffic and prevent unauthorized access.
2. **Addressing Configuration Management:** Regularly review and update device configurations to ensure they adhere to security best practices.
3. **Conducting Security Audits:** Periodically assess the network infrastructure to identify and address potential vulnerabilities.
4. **Educating Users:** Raise awareness among users about the importance of cybersecurity and the role they play in protecting network assets.
Summary: IPv6 Host Exposure
In today’s interconnected world, where technology evolves rapidly, the transition from IPv4 to IPv6 has become necessary. With the depletion of IPv4 addresses, adopting IPv6 is crucial to ensure the continued growth of the internet. This blog post delved into the concept of IPv6 host exposure, its benefits, challenges, and the steps towards embracing this new standard.
Understanding IPv6 Host Exposure
IPv6 host exposure refers to making a device or network accessible through IPv6 addresses. Unlike IPv4, which uses a limited number of addresses, IPv6 offers an almost limitless pool of unique addresses. This enables enhanced connectivity, improved security, and the ability to support the growing number of internet-enabled devices.
Benefits of IPv6 Host Exposure
Enhanced Connectivity: With IPv6, devices can directly communicate with each other without the need for complex network address translation (NAT) mechanisms. This results in faster and more efficient communication, reducing latency and enhancing the overall user experience.
Improved Security: IPv6 incorporates built-in security features, such as IPsec, which provides secure communication and protects against network threats. By adopting IPv6 host exposure, organizations can strengthen their network security and mitigate potential risks.
Future-Proofing: As the world moves towards an increasingly connected future, embracing IPv6 host exposure ensures compatibility and scalability. By preparing for IPv6, organizations can avoid the need for costly network infrastructure upgrades down the line.
Challenges and Considerations
Network Configuration: Implementing IPv6 host exposure requires careful planning and configuration adjustments. Network administrators must ensure proper routing, address assignment, and compatibility with existing IPv4 infrastructure.
Application Compatibility: Some legacy applications and systems may not be fully compatible with IPv6. Organizations must assess their software ecosystem and address compatibility issues before enabling IPv6 host exposure.
Skillset and Training: Transitioning to IPv6 may require additional training and upskilling for network administrators and IT professionals. Acquiring the necessary expertise ensures a smooth transition and effective management of IPv6-enabled networks.
Conclusion:
In conclusion, embracing IPv6 host exposure is not just an option but a necessity in today’s digital landscape. The benefits of enhanced connectivity, improved security, and future-proofing make it imperative for organizations to adapt to this new standard. While challenges and considerations exist, proper planning, configuration, and training can overcome these hurdles. By embracing IPv6 host exposure, organizations can unlock the internet’s full potential and pave the way for a seamless and connected future.
- DMVPN - May 20, 2023
- Computer Networking: Building a Strong Foundation for Success - April 7, 2023
- eBOOK – SASE Capabilities - April 6, 2023