Internet Locator
In today's digitally connected world, the ability to locate and navigate through various online platforms has become an essential skill. With the advent of Internet Locator, individuals and businesses can now effortlessly explore the vast online landscape. In this blog post, we will delve into the concept of Internet Locator, its significance, and how it has revolutionized how we navigate the digital realm.
Routing table growth: There has been exponential growth in Internet usage, and the scalability of today's Internet routing system is now a concern. With more people surfing the web than ever, the underlying technology must be able to cope with demand.
Whereas in the past, getting an internet connection via some internet locator service could sometimes be expensive, nowadays, thanks to bundles that include telephone connections and streaming services, connecting to the web has never been more affordable. It is also important to note that routing table growth has a significant drive driving a need to reexamine internet connectivity.
Limitation in technologies: This has been met with the limitations and constraints of router technology and current Internet addressing architectures. If we look at the core Internet protocols that comprise the Internet, we have not experienced any significant change in over a decade.
The physical-layer mechanisms that underlie the Internet have radical changed, but only a small number of tweaks have been made to BGP and its transport protocol, TCP. Mechanisms such as MPLS were introduced to provide a workaround to IP limitations within the ISP. Still, Layer 3 or 4 has had no substantial change for over a decade.
Matt Conran
Highlights: Internet Locator
Understanding the Basics of Routing
– At its core, routing refers to the process of selecting paths in a network along which to send data packets. Imagine it as the GPS for the internet, making split-second decisions to ensure that your data takes the most efficient and reliable route.
– Routers, the devices responsible for this task, constantly analyze the network’s topology, updating their routing tables to reflect the best paths available. This dynamic process allows the internet to function smoothly, even as network conditions change.
– Path selection is the heart of routing, involving complex algorithms that determine the best possible path for data to travel. Factors such as path length, bandwidth, congestion, and network policies all influence the decision-making process.
– Protocols like OSPF (Open Shortest Path First) and BGP (Border Gateway Protocol) are employed to ensure that data flows through the most optimal routes, minimizing delays and maximizing efficiency. Understanding these protocols is essential for networking professionals aiming to optimize network performance and reliability.
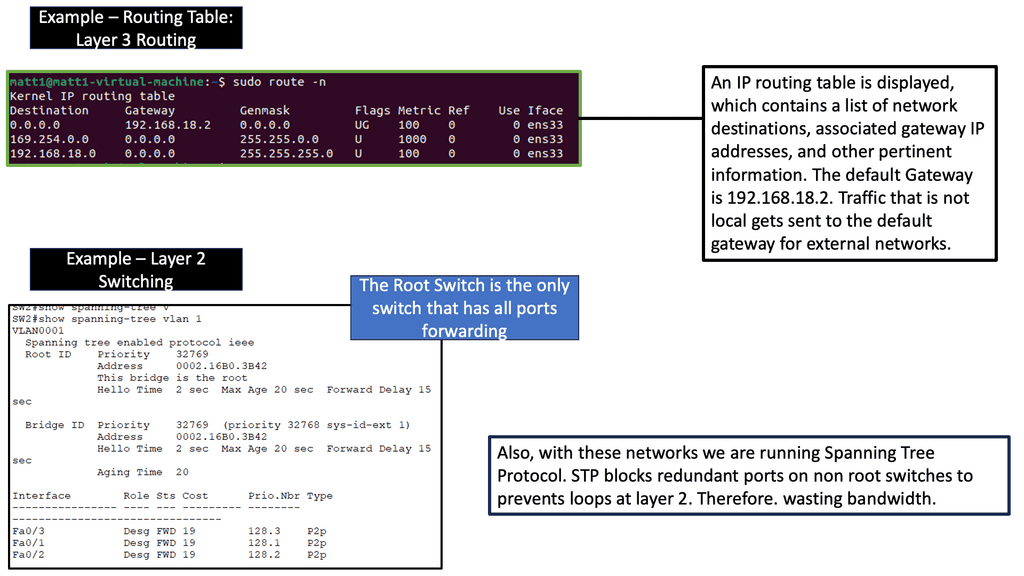
Note – Routing Tables
### What Are Routing Tables?
Routing tables are essentially databases stored on routers that contain information about the paths to various network destinations. Each entry in a routing table details a specific route and consists of several components, including the destination IP address, the subnet mask, the next hop, and the metric. These components work together to determine the best path for data to travel across the network. By constantly updating and maintaining these tables, routers ensure that data packets reach their endpoints efficiently.
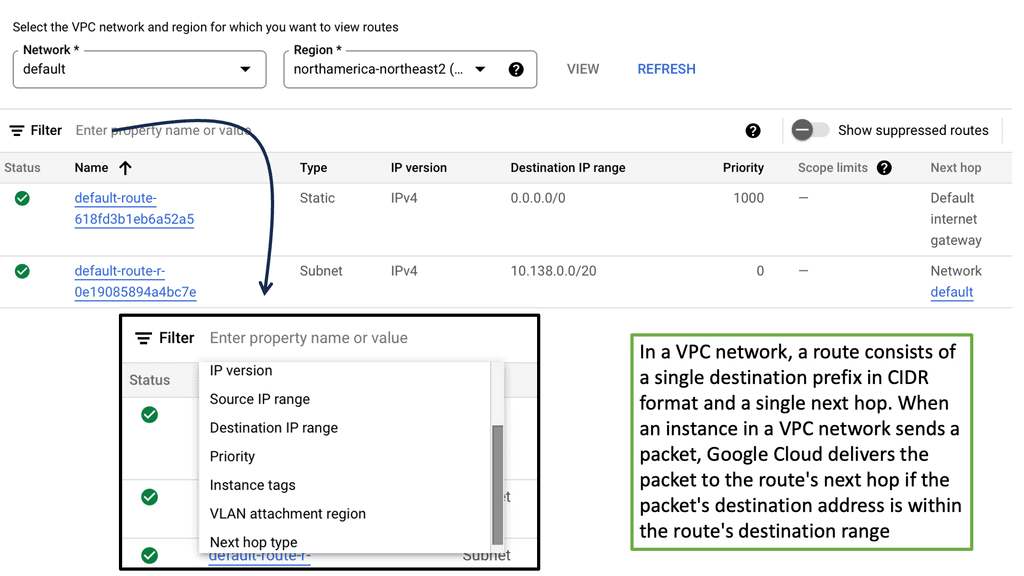
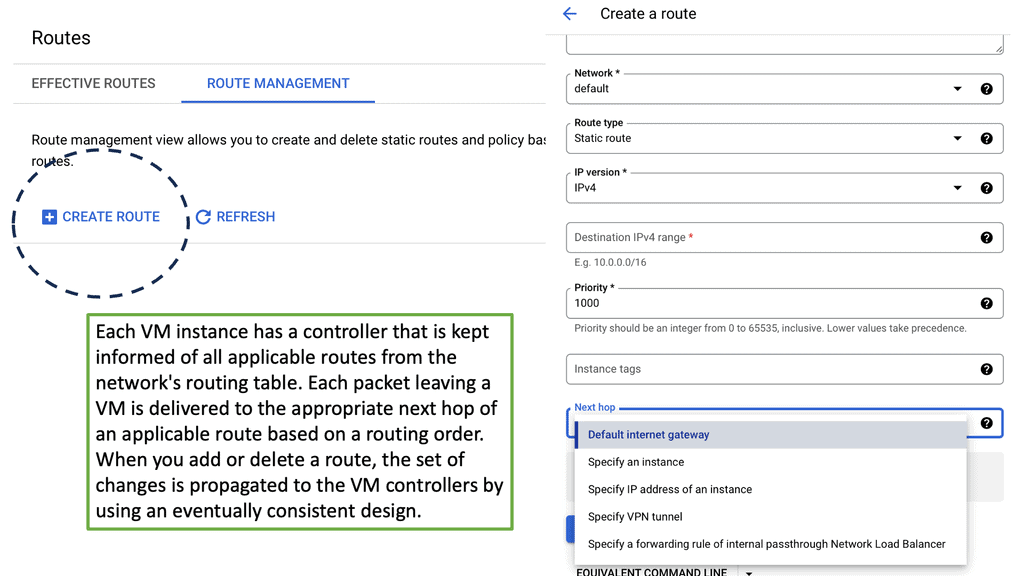
Example of VPC Networking & Routes:
### The Process of Path Selection
Path selection is a critical function of routing tables. It involves determining the most optimal route for data packets to travel from their source to their destination. This decision-making process is influenced by various factors, such as network topology, link costs, and congestion levels. Routers evaluate these factors using algorithms like Distance Vector, Link State, and Path Vector to select the best available path. By doing so, they help maintain high network performance and reliability.
### Dynamic vs. Static Routing
Routing tables can be classified into two types: dynamic and static. Static routing involves manually configuring routers with fixed paths, which can be inefficient in complex or changing network environments. On the other hand, dynamic routing uses protocols such as OSPF, EIGRP, and BGP to automatically update routing tables based on real-time network conditions. Dynamic routing offers greater flexibility and adaptability, making it suitable for larger and more complex networks.
### Challenges and Considerations
While routing tables and path selection are essential for network efficiency, they also present certain challenges. Network administrators must consider factors such as scalability, security, and redundancy when configuring routing tables. Additionally, the risk of routing loops, incorrect configurations, and outdated tables can impact network performance. To mitigate these risks, regular monitoring and maintenance of routing tables are necessary.
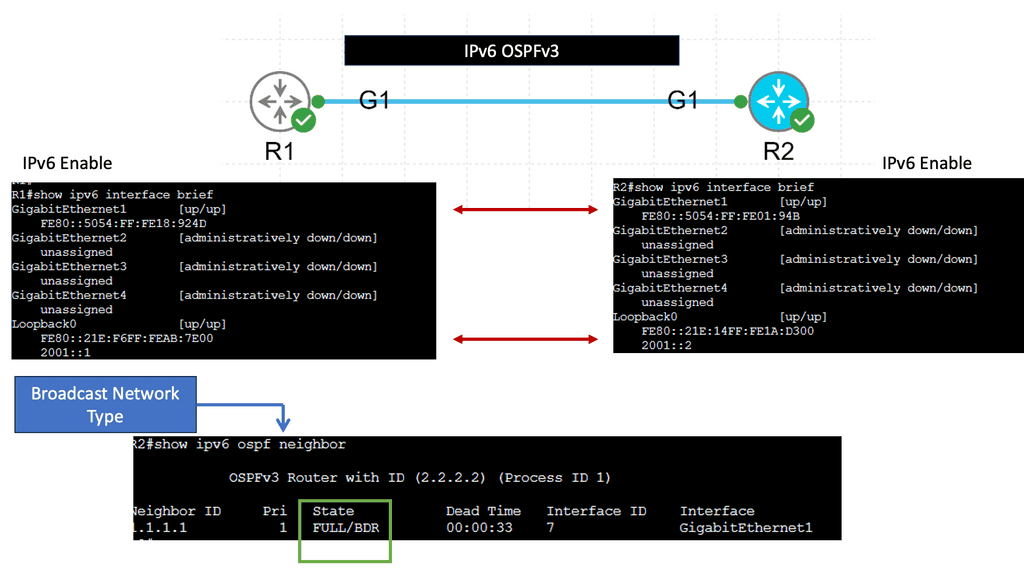
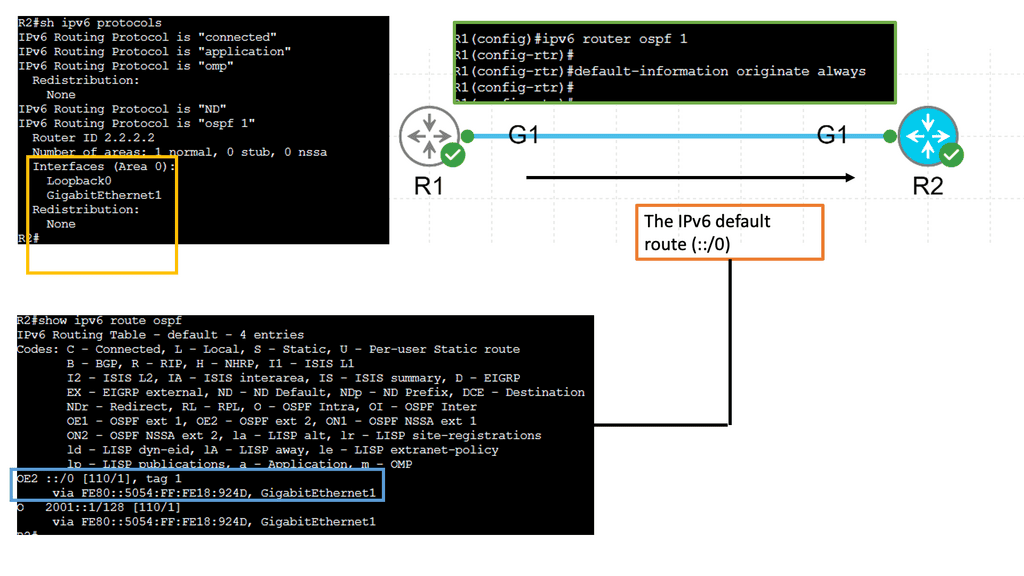
Example Routing with IPv6 OSPFv3
Path Selection
In the Forwarding Information Base (FIB), prefix length determines the path a packet should take. Routing information bases (RIBs), or routing tables, program the FIB. Routing protocol processes present routes to the RIB. Three components are involved in path selection:
- In the subnet mask, the prefix length represents the number of leading binary bits in the on position.
- An administrative distance rating (AD) indicates how trustworthy a routing information source is. If a router learns about a route to a destination from multiple routing protocols, it compares the AD.
- Routing protocols use metrics to calculate the best paths. Metrics vary from routing protocol to routing protocol.
Prefix Length
Here’s an example of how a router selects a route when the packet destination falls within the range of multiple routes. Consider a router with the following routes, each with a different prefix length:
- 10.0.3.0/28
- 10.0.3.0/26
- 10.0.3.0/24
There are various prefix lengths (subnet masks) for these routes, also known as prefix routes. RIBs, also known as routing tables, contain all of the routes that are considered different destinations. Unless the prefix is connected to a network, the routing table includes the outgoing interface and the next-hop IP address.
Related: Before you proceed, you may find the following posts helpful:
- Container Based Virtualization
- Observability vs Monitoring
- Data Center Design Guide
- LISP Protocol
- What Is BGP Protocol In Networking
Internet Locator
The Internet is often represented as a cloud. However, this needs to be clarified as there are few direct connections over the Internet. The Internet is also a partially distributed network. It is decentralized, with many centers or nodes and direct or indirect links. There are also different types of networks on the Internet. For example, we have a centralized, decentralized, and distributed network.
The Internet is a conglomeration of independent systems representing organizations’ administrative authority and routing policies. Autonomous systems are made up of Layer 3 routers that run Interior Gateway Protocols (IGPs) such as Open Shortest Path First (OSPF) and Intermediate System-to-Intermediate System (IS-IS) within their borders and interconnect via an Exterior Gateway Protocol (EGP). The current Internet de facto standard EGP is the Border Gateway Protocol Version 4 (BGP-4), defined in RFC 1771.
Guide on BGP Connectivity
In the following, we see a simple BGP design. BGP operated over TCP, more specifically, TCP port 179. BGP peers are created and can be iBGP or EBGP. In the screenshots below, we have an iBGP design. Remember that BGP is a Path Vector Protocol and utilizes a path vector protocol, which considers various factors while making routing decisions. These factors include the number of network hops, network policies, and path attributes such as AS path, next-hop, and origin.
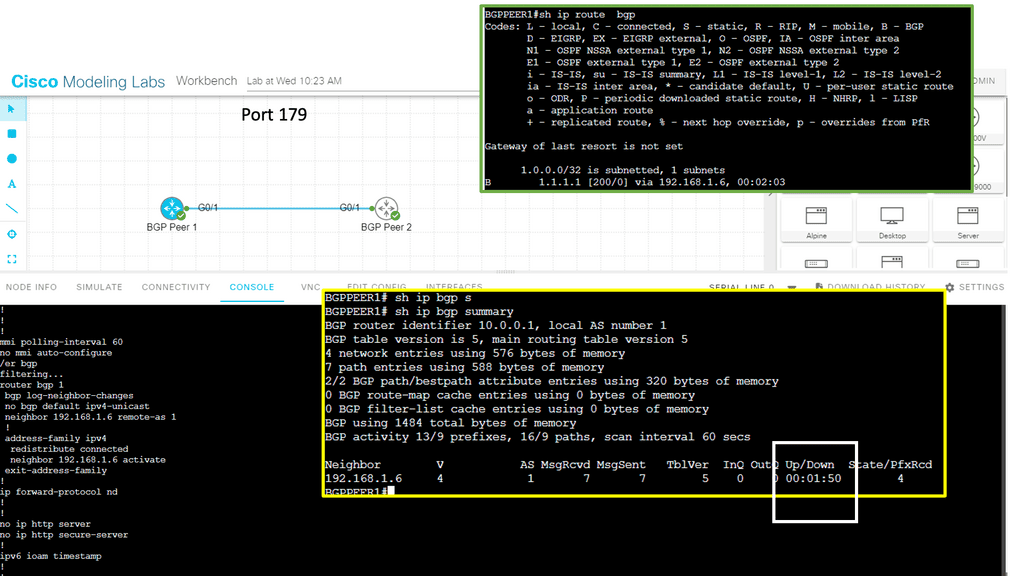
1. Path Vector Protocol: BGP utilizes a path vector protocol, which considers various factors while making routing decisions. These factors include the number of network hops, network policies, and path attributes such as AS path, next-hop, and origin.
Internet Locator: Default Free Zone ( DFZ )
The first large-scale packet-switching network was ARPAnet- the modern Internet’s predecessor. It used a simplex protocol called Network Control Program ( NCP ). NCP combined addressing and transport into a single protocol. Many applications were built on top of NCP, which was very successful. However, it lacked flexibility. As a result, reliability was separated from addressing and packet transfer in the design of the Internet Protocol Suite, with IP being separated from TCP.
On the 1st of January 1983, ARPAnet officially rendered NCP and moved to a more flexible and powerful protocol suite – TCP/IP. The transition from NCP to TCP/IP was known as “flag day,” It was quickly done with only 400 nodes to recompute.
Today, a similar flag day is impossible due to the sheer size and scale of the Internet backbone. The requirement to change anything on the Internet is driven by necessity, and it’s usually slow to change such a vast network. For example, inserting an additional header into the protocol would impact IP fragmentation processing and congestion mechanism. Changing the semantics of IP addressing is problematic as the IP address has been used as an identifier to higher-level protocols and encoded in the application.
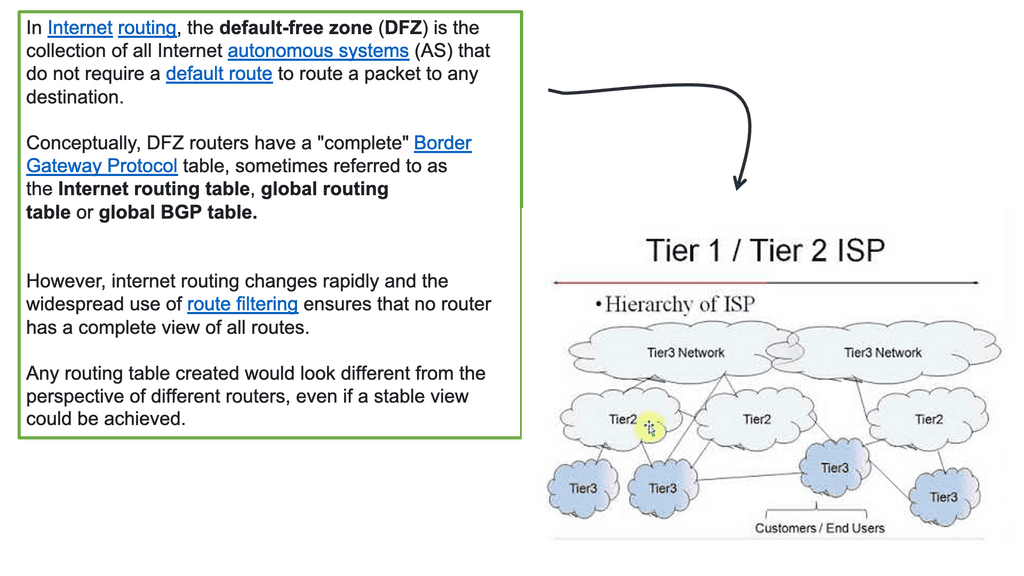
**Understanding Default-Free Zones**
In the rapidly evolving landscape of network architecture, the concept of a Default-Free Zone (DFZ) stands out as a crucial element for ensuring seamless connectivity and resilience. A DFZ is essentially a segment of the Internet routing infrastructure where routers operate without a default route. This means that every packet of data must have a specific path, enhancing the precision and efficiency of data transmission. Understanding DFZs is vital for network engineers and IT professionals who strive to maintain robust and efficient networks.
**The Role of DFZ in Modern Networks**
Default-Free Zones play a pivotal role in modern networks by eliminating the dependency on a default router. This leads to a more streamlined routing process, reducing the risk of data bottlenecks and enhancing overall network performance. In a DFZ, routers must rely on complete and accurate routing information, which makes it essential for organizations to maintain up-to-date routing tables and configurations. This meticulous approach not only improves network reliability but also makes troubleshooting more straightforward, as each route is explicitly defined.
**The driving forces of the DFZ**
Many factors are driving the growth of the Default Free Zone ( DFZ ). These mainly include multi-homing, traffic engineering, and policy routing. The Internet Architecture Board ( IAB ) met on October 18-19th, 2006, and their key finding was that they needed to devise a scalable routing and addressing system. Such an addressing system must meet the current challenges of multi-homing and traffic engineering requirements.
**Challenges and Considerations**
While the benefits of adopting a DFZ are manifold, there are challenges that organizations must address. Maintaining a DFZ requires a high level of expertise and constant monitoring to ensure that routing tables are comprehensive and accurate. The lack of a default route means that any missing information could lead to data transmission failures. As such, organizations must invest in skilled personnel and advanced routing technologies to manage their DFZ effectively. Additionally, the complexity of setting up and maintaining a DFZ can be prohibitive for smaller organizations with limited resources.
**The Future of Networking with DFZ**
As network demands continue to grow, the importance of Default-Free Zones is expected to increase. The rise of cloud computing, IoT devices, and the ever-expanding Internet of Things (IoT) ecosystem necessitates a more resilient and efficient network infrastructure. DFZs are poised to play a critical role in meeting these demands by providing a more reliable and efficient routing framework. Organizations that adopt DFZs are likely to be better equipped to handle future network challenges and innovations.
Internet Locator: Locator/ID Separation Protocol ( LISP )
There has been some progress with the Locator/ID separation protocol ( LISP ) development. LISP is a routing architecture that redesigns the current addressing architecture. Traditional addressing architecture uses a single name, the IP address, to express two functions of a device.
The first function is its identity, i.e., who, and the second function is its location, i.e., where. LISP separates IP addresses into two namespaces: Endpoint Identifiers ( EIDs ), non-routable addresses assigned to hosts, and Routing Locators ( RLOCs), routable addresses assigned to routers that make up the global routing system.
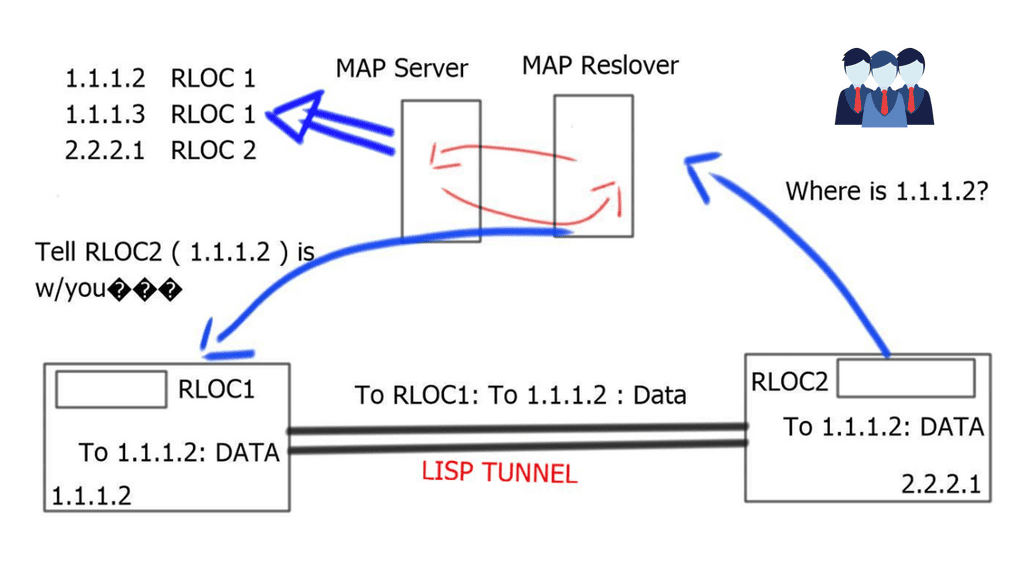
Separating these functions offers numerous benefits within a single protocol, one of which attempts to address the scalability of the Default Free Zone. In addition, LISP is a network-based implementation with most of the deployment at the network edges. As a result, LISP integrates well into the current network infrastructure and requires no changes to the end host stack.
Recap on LISP Protocol and Path Selection
Path selection in LISP is a crucial component that determines how data packets traverse the network. Unlike traditional routing protocols that rely solely on path metrics or shortest path algorithms, LISP introduces a more dynamic and intelligent approach. It leverages a mapping system to decide the best route for data transmission, considering factors such as bandwidth, latency, and network policies. This innovative method ensures that data flows are optimized for efficiency and reliability, even in complex network environments.
### How LISP Enhances Network Scalability
One of the standout features of the LISP protocol is its ability to address the growing demands of network scalability. By decoupling identity from location, LISP minimizes the size of routing tables, thereby reducing memory and processing requirements on routers. This is particularly advantageous in large-scale networks, where maintaining a table of all possible routes can be cumbersome and inefficient. LISP’s path selection mechanism dynamically adapts to changes in the network, ensuring scalability without compromising performance.
Guide on LISP.
In the following guide, we will look at a LISP network. These LISP protocol components include the following:
- Map Registration and Map Notify.
- Map Request and Map-Reply.
- LISP Protocol Data Path.
- Proxy ETR.
- Proxy ITR.
LISP implements the use of two namespaces instead of a single IP address:
- Endpoint identifiers (EIDs)—assigned to end hosts.
- Routing locators (RLOCs) are assigned to devices (primarily routers) that comprise the global routing system.
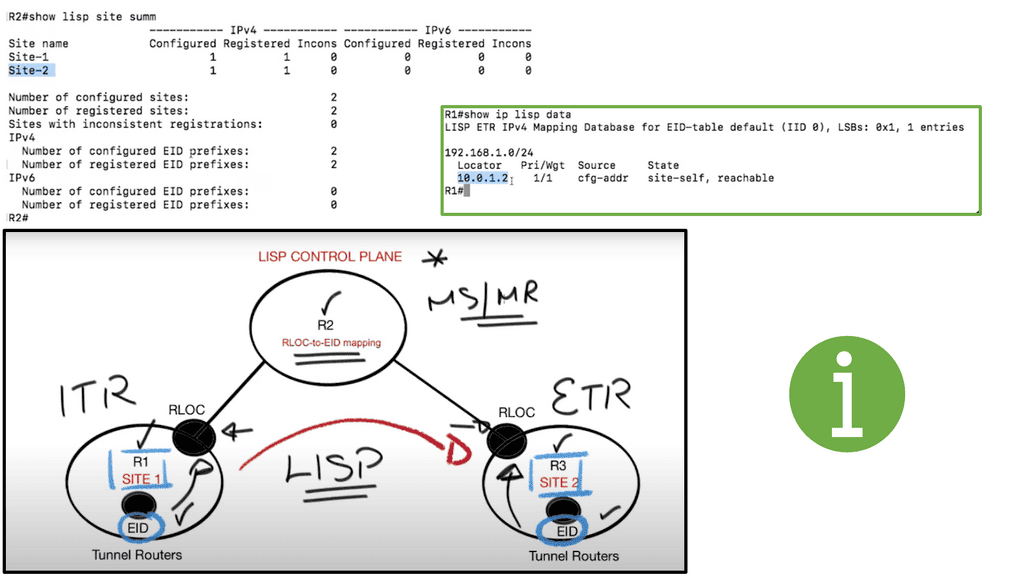
Splitting EID and RLOC functions yields several advantages, including improved routing system scalability, multihoming efficiency, and ingress traffic engineering. With the command: show lisp site summary, site 1 consists of R1, and site 2 consists of R2. Each of these sites advertises its own EID prefix. On R1, the tunnel router, we see the routing locator address 10.0.1.2. The RLOCs ( routing locators ) are interfaces on the tunnel routers.
Border Gateway Protocol (BGP) role in the DFZ
Border Gateway Protocol, or BGP, is an exterior gateway protocol that allows different autonomous systems (AS) to exchange routing information. It is designed to enable efficient communication between different networks and facilitate data exchange and traffic across the Internet.
Exchanging NLRI
BGP is the protocol used to exchange NLRI between devices on the Internet and is the most critical piece of Internet architecture. It is used to interconnect Autonomous systems on the Internet, and it holds the entire network together. Routes are exchanged between BGP speakers with UPDATE messages. The BGP routing table ( RIB ) now stands at over 520,000 routes.
Although some of this growth is organic, a large proportion is driven by prefix de-aggregation. Prefix de-aggregation leads to increased BGP UPDATE messages injected into the DFZ. UPDATE messages require protocol activity between routing nodes, which requires additional processing to maintain the state for the longer prefixes.
Excess churn exposes the network’s core to the edges’ dynamic nature. This detrimental impacts routing convergence since UPDATES need to be recomputed and downloaded from the RIB to the FIB. As a result, it is commonly viewed that the Internet is never fully converged.
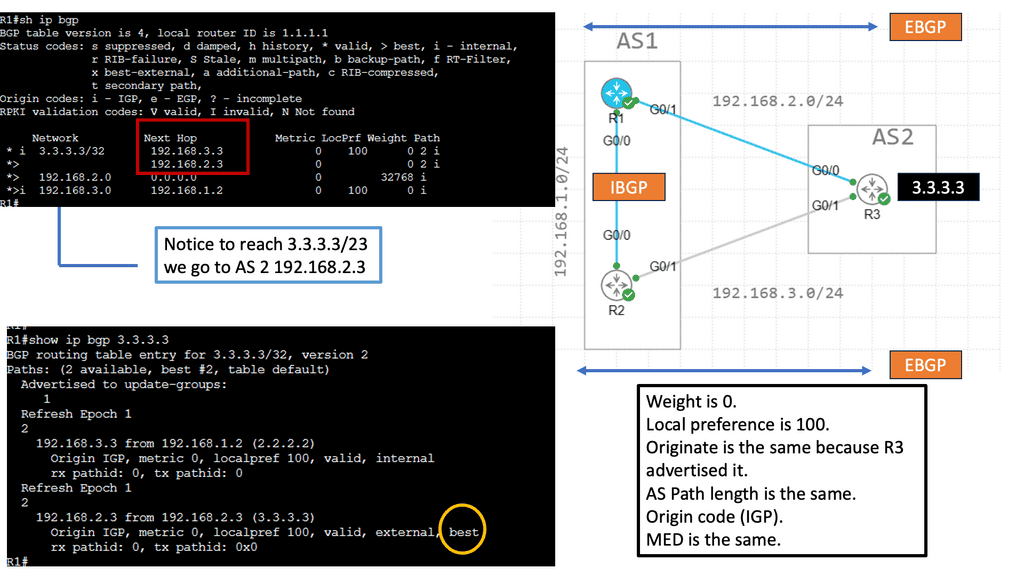
Example BGP Technology: Prefer EBGP over iBGP
**Section 1: EBGP vs. iBGP – The Core Differences**
EBGP operates between different autonomous systems (AS), facilitating communication across diverse networks. In contrast, iBGP works within a single AS, managing internal routing. This fundamental difference is pivotal. EBGP’s capability to interact with different AS is crucial for network scalability and maintaining global connectivity, while iBGP focuses on internal efficiency and stability.
**Section 2: The Role of EBGP in Network Scalability**
One of EBGP’s standout features is its ability to support network scalability. It simplifies routing policies between AS and enables organizations to connect with multiple external networks seamlessly. By using EBGP, networks can efficiently manage route advertisements and prevent routing loops, ensuring stable data flows across vast geographical areas. This scalability is less achievable with iBGP, which is limited to internal network boundaries.
**Section 3: EBGP’s Influence on Network Security**
Security is paramount in network management, and EBGP offers robust solutions. By operating between distinct AS, EBGP provides clear demarcations that help isolate and manage security threats. Network administrators can implement stringent policies and filters, ensuring only legitimate routes are advertised. This level of security management is more challenging with iBGP, where internal threats can propagate more easily across the network.
Security in the DFZ
Security is probably the most significant Internet problem; no magic bullet exists. Instead, an arms race is underway as techniques used by attackers and defenders co-evolve. This is because the Internet was designed to move packets from A to B as fast as possible, irrespective of whether B wants any of those packets.
In 1997, a misconfigured AS7007 router flooded the entire Internet with /24 BGP routes. As a result, routing was globally disrupted for more than 1 hour as the more specific prefixes took precedence over the aggregated routes. In addition, more specific routes advertised from AS7007 to AS1239 attracted traffic from all over the Internet into AS1239, saturating its links and causing router crashes.
There are automatic measures to combat prefix hijacking, but they are not widely used or compulsory. The essence of BGP design allows you to advertise whatever NLRI you want, and it’s up to the connecting service provider to have the appropriate filtering in place.
Drawbacks to BGP
BGP’s main drawback concerning security is that it does not hide policy information, and by default, it doesn’t validate the source. However, as BGPv4 runs over TCP, it is not as insecure as many think. A remote intrusion into BGP would require guessing the correct TCP numbers to insert data, and most TCP/IP stacks have hard-to-predict TCP sequence numbers. To compromise BGP routing, a standard method is to insert a rogue router that must be explicitly configured in the target’s BGP configuration as a neighbor statement.
### Complexity in Configuration
One of the primary drawbacks of EBGP is its complexity in configuration. Unlike its internal counterpart, IBGP, EBGP requires careful planning and meticulous setup. Network administrators must configure policies, route maps, and filters to ensure optimal routing paths and prevent routing loops. This complexity can lead to misconfigurations, resulting in network inefficiencies or even outages.
### Limited Scalability
EBGP can also present scalability issues. As networks grow and the number of autonomous systems increases, maintaining numerous EBGP sessions becomes challenging. Each EBGP session consumes memory and processing power, potentially overwhelming routers if not managed properly. This limitation necessitates careful network design and the use of route reflectors or confederations to maintain scalability.
### Security Concerns
Security is another significant concern with EBGP. The protocol itself does not include built-in security features, making it vulnerable to various attacks, such as route hijacking and prefix spoofing. Network operators must implement additional security measures like prefix filtering, route validation, and the use of Resource Public Key Infrastructure (RPKI) to safeguard their networks against such threats.
Significance of BGP:
1. Inter-Domain Routing: BGP is primarily used for inter-domain routing, enabling different networks to communicate and exchange traffic across the internet. It ensures that data packets reach their intended destinations efficiently, regardless of the AS they belong to.
2. Internet Service Provider (ISP) Connectivity: BGP is crucial for ISPs as it allows them to connect their networks with other ISPs. This connectivity enables end-users to access various online services, websites, and content hosted on different networks, regardless of geographical location.
3. Redundancy and Load Balancing: BGP’s dynamic routing capabilities enable network administrators to create redundant paths and distribute traffic across multiple links. This redundancy enhances network resilience and ensures uninterrupted connectivity even during link failures.
4. Internet Traffic Engineering: BGP plays a vital role in Internet traffic engineering, allowing organizations to optimize network traffic flow. By manipulating BGP attributes and policies, network administrators can influence the path selection process and direct traffic through preferred routes.
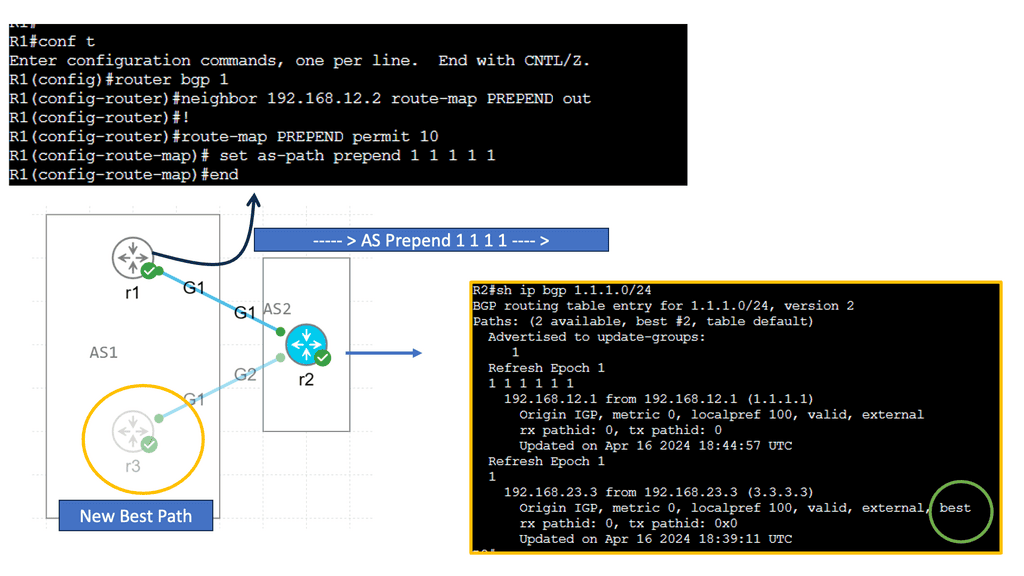
Example BGP Traffic Engineering – AS Prepend
### Understanding BGP AS Prepend
BGP AS Prepend is a method by which an autonomous system (AS) can influence the path selection of outgoing traffic by artificially inflating the AS path length. This is done by adding (or “prepending”) multiple instances of its own AS number to the AS path attribute of BGP routes. This makes the path appear longer than it actually is, persuading other networks to prefer alternative, shorter paths.
### Why Use BGP AS Prepend?
The primary reason for using AS Prepend is to control the routing of incoming traffic for multi-homed networks—those connected to two or more ISPs. By prepending AS numbers, network administrators can manipulate the perceived path cost across different routes, directing traffic through more preferred paths. This can enhance load balancing, improve latency, and avoid congestion on certain links.