DNS Security Designs
In today's digital age, where data breaches and cyber attacks are becoming increasingly common, ensuring the security of our online activities is of utmost importance. One crucial aspect of online security is the Domain Name System (DNS) – the backbone of the internet that translates domain names into IP addresses. This blog post will explore various DNS security designs organizations can implement to protect their networks and data from malicious activities.
Before diving into the design aspects, it's important to understand the basics of DNS security. DNS is responsible for translating domain names into IP addresses, allowing us to access websites by typing in easy-to-remember names instead of complicated numeric addresses. However, this system can be vulnerable to attacks, such as DNS spoofing or cache poisoning, which can redirect users to malicious websites. Implementing robust DNS security designs is crucial to mitigate these risks.
DNS security is integral to safeguarding against cyber threats and maintaining the integrity of online communications. There are a number of potential risks associated with insecure DNS systems, including DNS cache poisoning, DDoS attacks, and DNS hijacking. By understanding these risks, we can better appreciate the need for robust security measures.
Now that we recognize the significance of DNS security, let's explore various design strategies employed to fortify DNS systems. We will discuss the role of DNSSEC (Domain Name System Security Extensions) in providing authentication and data integrity, as well as DNS filtering techniques to mitigate malicious activities.
One effective approach to enhancing DNS security is through the implementation of DNS firewalls. This section will delve into the functionality and benefits of DNS firewalls, which act as protective barriers against unauthorized access, malware, and phishing attempts.
For organizations seeking to bolster their DNS security, adhering to best practices is crucial. This section will outline key recommendations, such as regular software updates, strong access controls, monitoring DNS logs, and implementing robust encryption protocols.
Securing the Domain Name System is an ongoing endeavor, considering the ever-evolving landscape of cyber threats. By comprehending the significance of DNS security and exploring various design strategies, organizations can take proactive steps to safeguard their digital infrastructure. Remember, protecting the DNS not only ensures the reliability of online services but also upholds the privacy and trust of users in the digital realm.Matt Conran
Highlights: DNS Security Designs
Understanding DNS Security
DNS security is critical to protecting networks and data from cyber threats. By implementing various DNS security designs such as DNSSEC, filtering and whitelisting, DNS firewalls, anomaly detection, and DANE, organizations can strengthen their overall security posture. Businesses must stay proactive and adopt these security measures to mitigate the risks associated with DNS vulnerabilities. By doing so, they can ensure a safer online environment for their users and protect valuable data from falling into the wrong hands.
**The Anatomy of DNS Attacks**
To effectively protect DNS, one must first understand the threats it faces. Common DNS attacks include DNS spoofing, where attackers redirect traffic to malicious sites, and DNS amplification attacks, which overload servers with traffic. By exploiting these vulnerabilities, cybercriminals can intercept sensitive data or disrupt services. Recognizing these threats is the first step towards building a robust security strategy.
**Building a Resilient DNS Security Architecture**
A multi-layered approach is essential for DNS security. This includes implementing DNSSEC (Domain Name System Security Extensions) to authenticate DNS data and prevent tampering. Additionally, using redundant DNS servers and anycast routing can enhance resilience and availability. Organizations should also consider leveraging threat intelligence feeds to detect and mitigate real-time threats. By integrating these elements, businesses can create a fortified DNS infrastructure.
**The Role of DNS Monitoring and Response**
Constant vigilance is crucial in DNS security. Implementing monitoring tools that provide real-time alerts for anomalies and suspicious activities can help in early detection of potential threats. Automated response systems can mitigate attacks before they escalate, reducing downtime and data breaches. Regular audits and updates to DNS configurations and security policies further strengthen this defense mechanism.
**Adopting Best Practices for DNS Security**
Beyond technical measures, adopting best practices is paramount. This includes enforcing strong access controls, ensuring DNS software is up-to-date, and conducting regular security assessments. Training employees about DNS threats and establishing incident response protocols are equally important. By fostering a security-conscious culture, organizations can effectively mitigate risks associated with DNS vulnerabilities.
DNS Security Key Considerations:
– The DNS is the backbone of internet communication, translating domain names into IP addresses. However, it is susceptible to various vulnerabilities, including cache poisoning, DDoS attacks, and data exfiltration. Understanding these risks is crucial to implementing effective security designs.
– DNS Security Extensions (DNSSEC) is a widely adopted security protocol that adds a layer of protection to the DNS. By digitally signing DNS records, DNSSEC ensures the integrity and authenticity of DNS data. We will explore the implementation process, key benefits, and challenges of DNSSEC.
– Distributed Denial of Service (DDoS) attacks can cripple DNS infrastructure, leading to service disruptions and potential data breaches. Mitigating such attacks requires a comprehensive strategy involving traffic monitoring, rate limiting, and intelligent DDoS mitigation systems. We will discuss these techniques and their role in safeguarding DNS availability.
– DNS firewalls play a vital role in protecting against malicious activities by filtering and blocking access to suspicious domains. By leveraging threat intelligence feeds and employing machine learning algorithms, DNS firewalls can identify and block connections to known malicious domains, enhancing overall security posture.
**Fundamental Components: DNS Security**
A key component of DNS security is protecting DNS infrastructure from cyber attacks. Several overlapping defenses must be implemented to ensure DNS security, including redundant DNS servers, security protocols like DNSSEC, and robust DNS logging.
The DNS system has several design limitations, as it was not designed with security in mind like many Internet protocols. Due to these limitations and technological advances, DNS servers are susceptible to various attacks, such as spoofing, amplification, DoS (Denial of Service), and interception of private information. Because DNS is an integral part of most Internet requests, it can be a prime target for cyber attacks.
DNS attacks are often deployed. Organizations must mitigate DNS attacks quickly so they are not too busy to handle simultaneous attacks from other vectors.
Google Cloud DNS
### Key Features of Google Cloud DNS
Google Cloud DNS provides several features that set it apart from traditional DNS services. These include global load balancing, DNS forwarding, and private DNS zones. It integrates seamlessly with other Google Cloud services, ensuring that your DNS infrastructure is both powerful and flexible. By leveraging these features, businesses can achieve faster query responses and improved reliability, crucial for maintaining customer trust and satisfaction.
### Designing a Secure DNS Architecture
When it comes to DNS security design, there are several best practices to consider. Start by implementing DNSSEC (Domain Name System Security Extensions) to protect against data corruption and spoofing attacks. Regularly auditing your DNS records for accuracy and consistency is also essential. Additionally, restrict access to your DNS management console to authorized personnel only, and monitor for suspicious activities to prevent unauthorized access.
### The Role of Automation in DNS Management
Automation can significantly enhance the efficiency and security of your DNS management. Google Cloud DNS supports Infrastructure as Code (IaC) tools like Terraform, enabling you to automate DNS record creation and updates. This reduces the risk of human error and accelerates deployment times. By automating routine tasks, you free up valuable resources to focus on more strategic initiatives.
### Understanding the Core Features
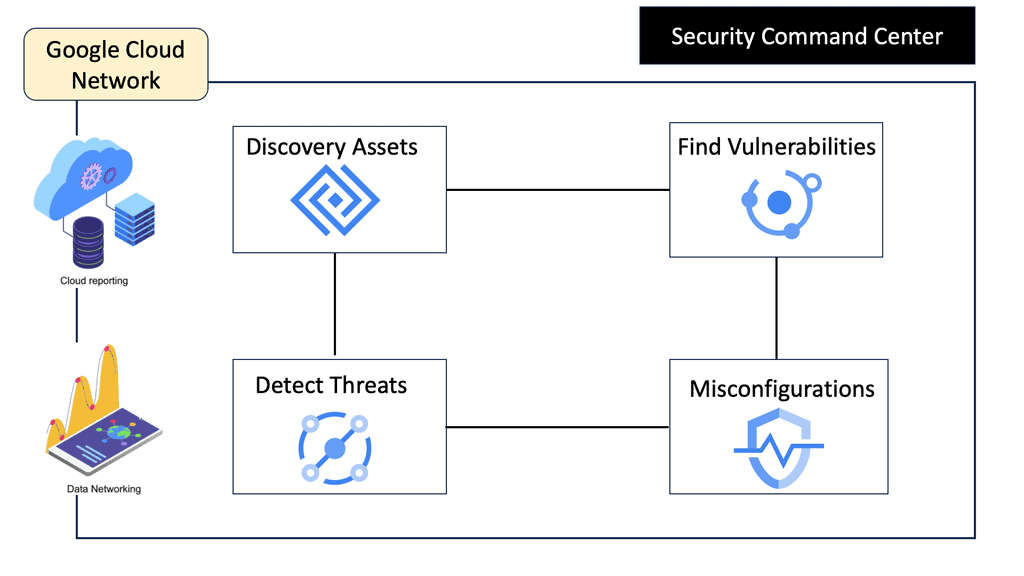
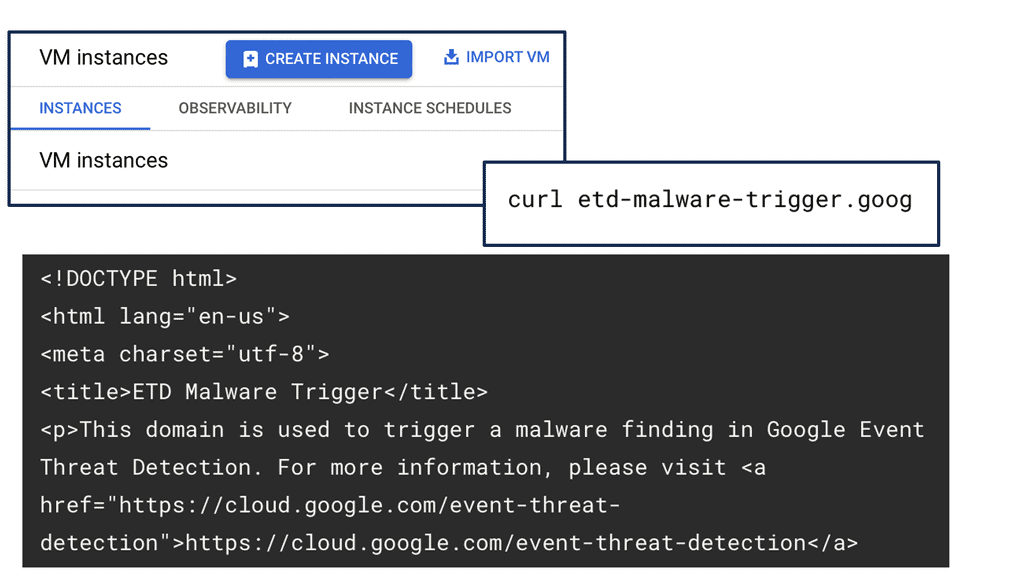
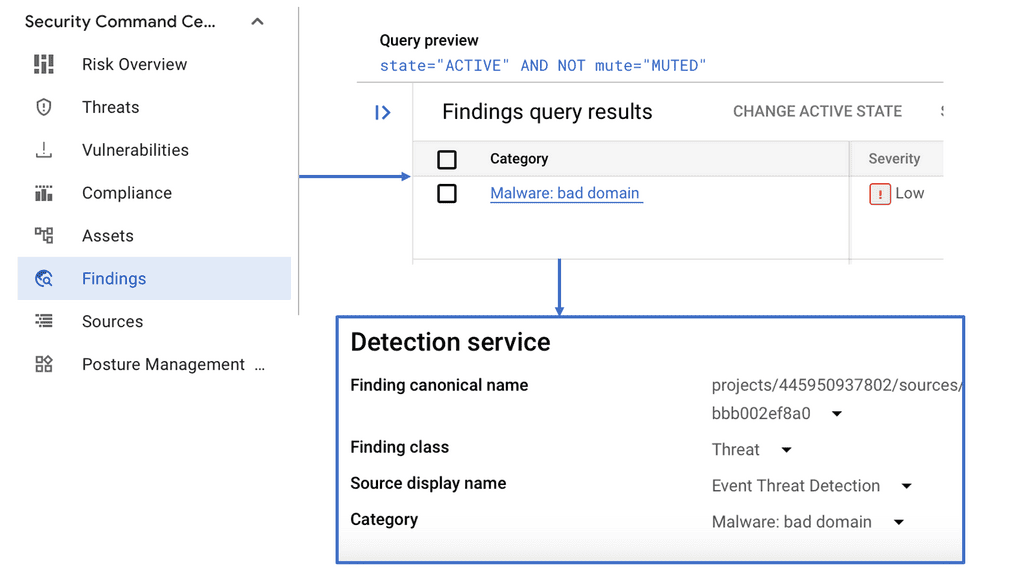
At the heart of SCC is its ability to provide visibility into your cloud assets and potential vulnerabilities. The platform equips security teams with tools for asset discovery, allowing them to inventory and classify resources in real time. SCC’s continuous scanning feature ensures that any new vulnerabilities or misconfigurations are promptly identified, enabling swift remediation. Furthermore, the integration of threat intelligence directly from Google helps in recognizing and prioritizing risks based on their severity.
### Leveraging DNS Security
One of the standout features of SCC is its DNS Security capabilities. By monitoring DNS logs and analyzing patterns, SCC can detect anomalies indicative of malicious activities, such as DDoS attacks or data exfiltration attempts. This proactive approach ensures that potential threats are identified before they can cause significant harm. The use of machine learning algorithms enhances the accuracy of threat detection, providing a robust defensive mechanism against evolving cyber threats.
### Investigating Threats with SCC
When a threat is detected, Security Command Center offers a streamlined process for investigation. The platform’s intuitive dashboard provides detailed insights into the nature and source of the threat, allowing security professionals to quickly assess the situation. SCC’s integration with other Google Cloud services facilitates a comprehensive analysis, enabling teams to trace the threat’s trajectory and implement effective countermeasures.
### Optimizing Security Strategies
Beyond threat detection and investigation, SCC plays a pivotal role in refining overall security strategies. By analyzing security findings and patterns over time, organizations can identify recurring vulnerabilities and adjust their policies accordingly. SCC also supports compliance efforts by aligning with industry standards, such as PCI-DSS and GDPR, ensuring that your security measures are up to par with global requirements.
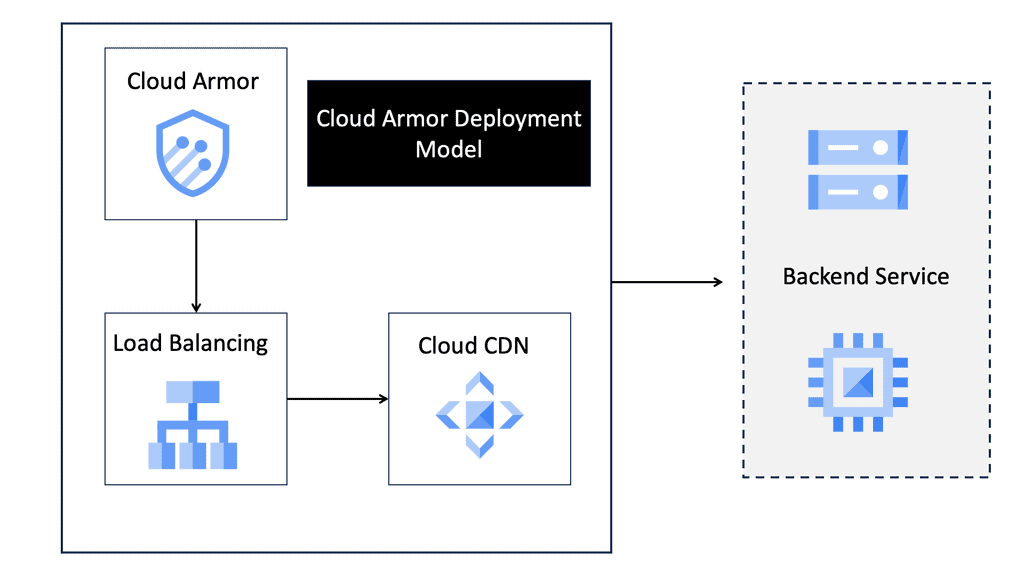
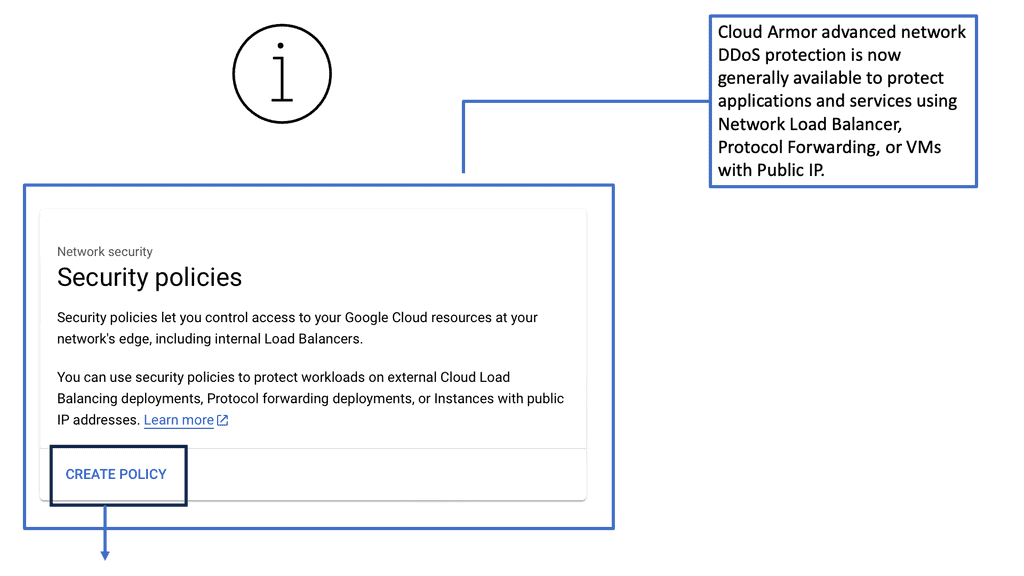
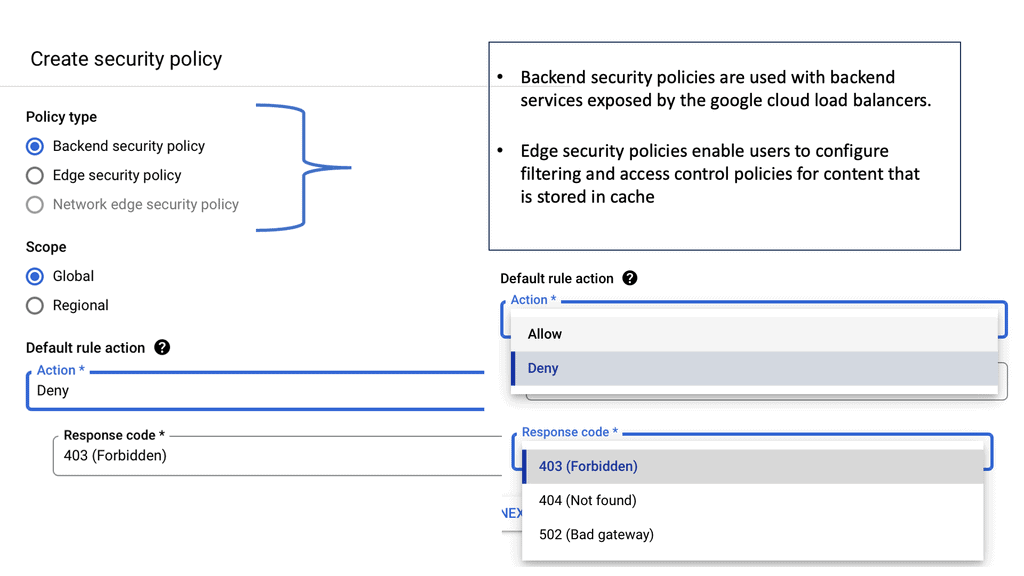
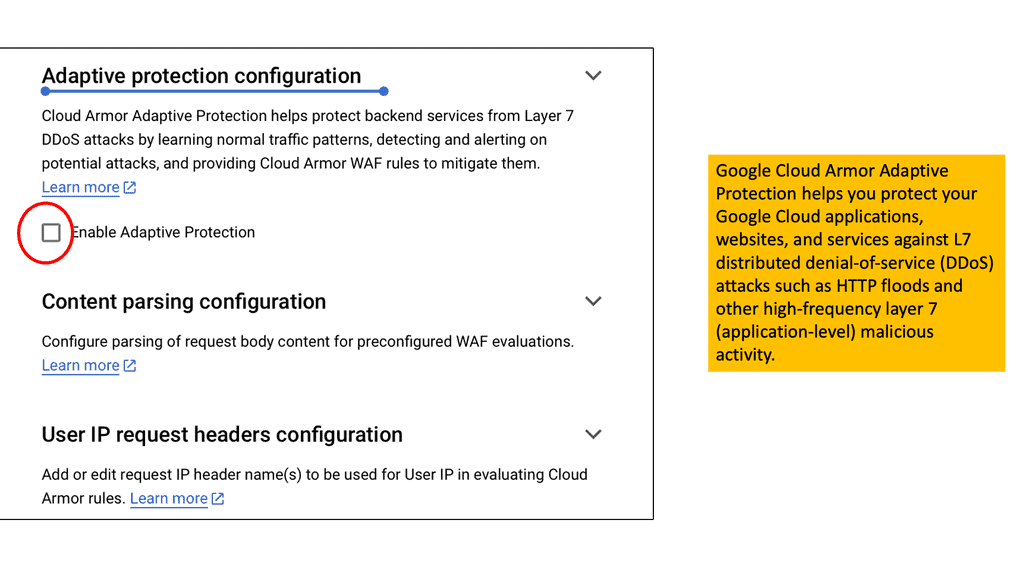
Cloud Armor DDoS Protection
What is Cloud Armor DDoS Protection?
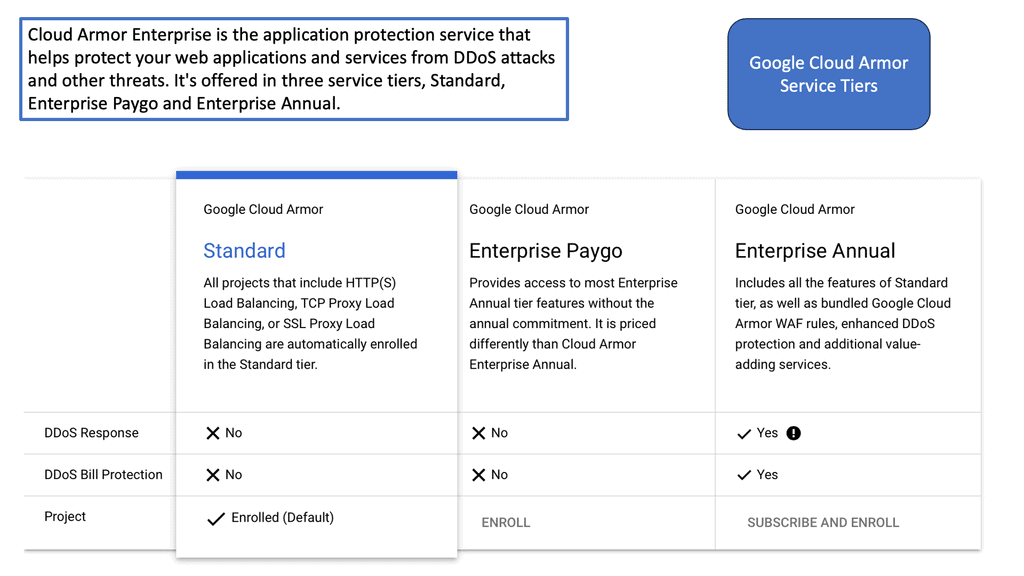
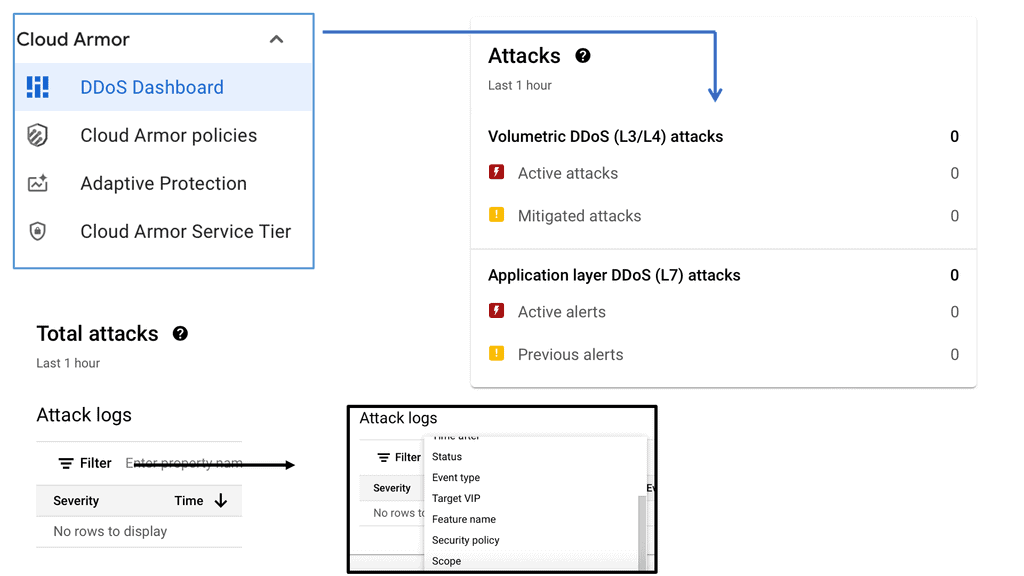
Cloud Armor is a security service designed to protect applications and websites from DDoS attacks. It leverages Google’s global infrastructure to provide scalable and reliable protection. By automatically detecting and mitigating attacks, Cloud Armor ensures that businesses maintain uptime and performance, even in the face of potential threats. The service is capable of handling massive volumes of traffic, thereby shielding applications from both volumetric and application-layer DDoS attacks.
### The Role of DNS Security Solutions
DNS security solutions play a pivotal role in the broader spectrum of DDoS protection. By securing the Domain Name System (DNS), these solutions prevent attackers from exploiting DNS vulnerabilities to disrupt services. Cloud Armor integrates seamlessly with DNS security measures, providing a comprehensive shield against potential threats. This dual-layer protection is crucial in maintaining the integrity and availability of online services, ensuring that users can access applications without interruption.
### Key Features of Cloud Armor
Cloud Armor offers a range of features designed to enhance security and performance. Some of the standout features include:
– **Scalability**: As traffic increases, Cloud Armor scales dynamically to handle the load, ensuring consistent protection.
– **Custom Rules**: Users can create custom security policies tailored to their specific needs, allowing for flexible threat management.
– **Real-time Monitoring**: Continuous monitoring and reporting enable businesses to stay informed about potential threats and system performance.
– **Integration Capabilities**: Cloud Armor works seamlessly with other Google Cloud services, providing a unified security approach.
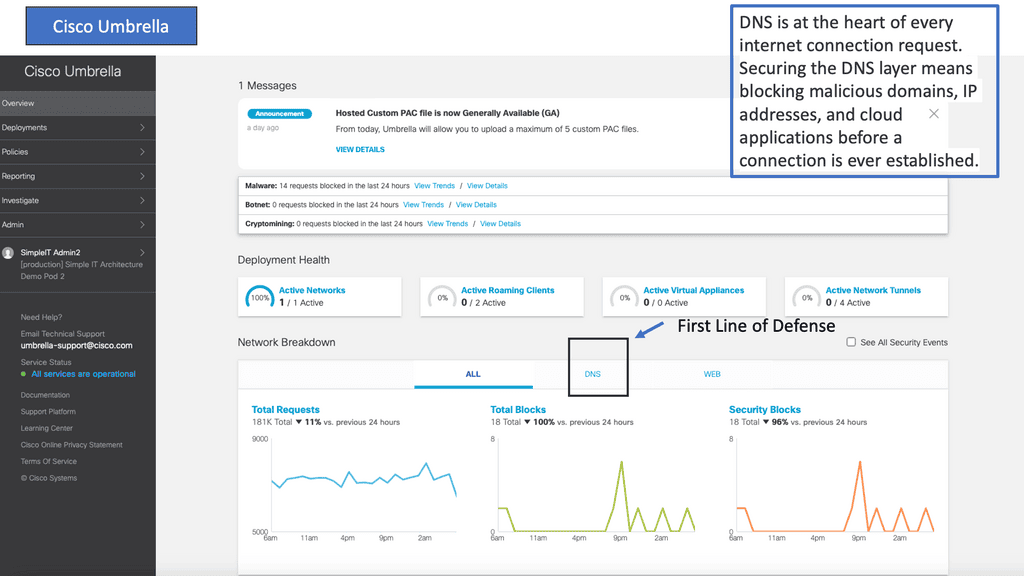
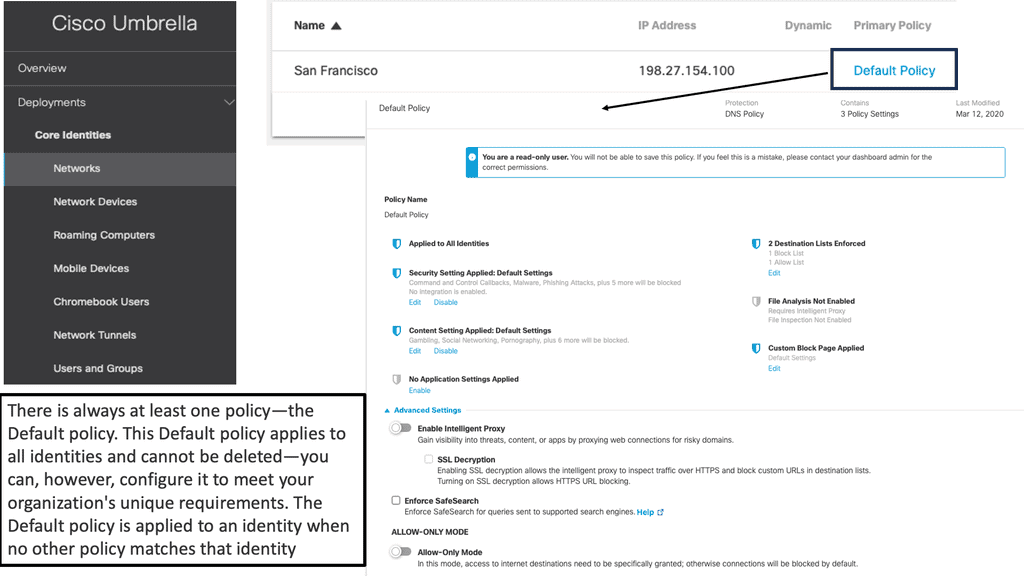
Example Product: DNS Security with Cisco Umbrella
### What is Cisco Umbrella?
Cisco Umbrella is a cloud-based security platform that provides a first line of defense against threats on the internet. By leveraging DNS layer security, it acts as a protective barrier between your network and potential cyber threats. Cisco Umbrella not only blocks malicious domains but also provides visibility into internet activity across all devices, whether on or off the corporate network.
### The Importance of DNS Security
Domain Name System (DNS) is the backbone of the internet, translating human-friendly domain names into IP addresses that computers use to identify each other. However, this crucial function can be exploited by cybercriminals to redirect users to malicious sites. DNS security, therefore, is essential to prevent such attacks and ensure a secure browsing experience. Cisco Umbrella fortifies DNS security by preemptively blocking access to harmful sites before they can cause any damage.
### Key Features of Cisco Umbrella
Cisco Umbrella comes packed with several features designed to enhance DNS security:
1. **Threat Intelligence:** Cisco Umbrella uses data from Cisco Talos and other threat intelligence sources to identify and block malicious domains and IPs.
2. **DNS Layer Security:** It stops threats over any port or protocol, preventing phishing, malware, and ransomware attacks.
3. **Cloud-Based:** Being a cloud-delivered service, it’s easy to deploy and manage with no hardware or software to install.
4. **Comprehensive Reporting:** Gain full visibility into internet activity and detailed reports on threats and policy enforcement.
### Benefits for Organizations
Implementing Cisco Umbrella can offer numerous benefits for organizations:
– **Enhanced Security:** Robust protection against a wide array of cyber threats.
– **Reduced Latency:** Faster internet performance due to efficient DNS resolution.
– **Ease of Management:** Simplified security management with a cloud-based solution.
– **Scalability:** Easily scalable to meet the needs of growing organizations.
DNS Security Design Options
DNSSEC (Domain Name System Security Extensions). DNSSEC is a widely adopted security protocol that adds an extra layer of protection to the DNS infrastructure. By digitally signing DNS records, it ensures the authenticity and integrity of the data exchanged between servers, thwarting various DNS-based attacks such as cache poisoning or DNS spoofing.
DNS Filtering and Blacklisting: Implementing DNS filtering and blacklisting mechanisms allows organizations to block access to malicious or suspicious websites. By leveraging threat intelligence sources and maintaining updated lists of known malicious domains, this design helps prevent users from inadvertently accessing harmful content or falling victim to phishing attempts.
Anycast DNS: Anycast DNS is a distributed DNS infrastructure design that improves both performance and security. By deploying multiple geographically dispersed DNS servers, it minimizes network latency and mitigates the impact of DDoS (Distributed Denial of Service) attacks by spreading the incoming traffic across multiple locations.
DNS Monitoring and Logging: Effective DNS security design also involves continuous monitoring and logging of DNS activities. By closely monitoring DNS queries and responses, organizations can detect anomalies, identify potential attacks, and respond proactively to security incidents. Robust logging mechanisms also aid in forensic investigations and post-incident analysis.
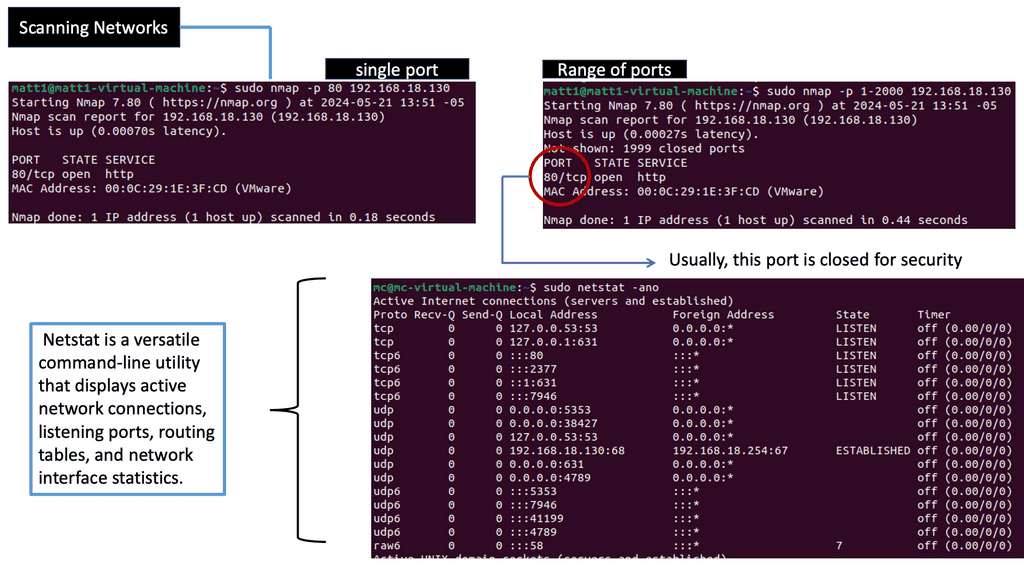
Core DNS Security: What is Network Scanning?
Network scanning systematically probes a network to identify its active hosts, open ports, and services running on those ports. It involves sending crafted packets, known as probes, to target systems and analyzing their responses. By doing so, network scanning allows us to map the network topology, discover vulnerabilities, and gain insights into the structure and security of a network.
Several techniques are used in network scanning, each tailored for different purposes. One common technique is Ping Scanning, which uses ICMP echo requests to check if a host is reachable. On the other hand, Port Scanning focuses on scanning open ports on target systems, revealing potential entry points for attackers. Service Scanning involves identifying the services running on open ports and providing valuable information about the network’s infrastructure. Finally, Vulnerability Scanning aims to detect vulnerabilities in network devices and software, assessing potential risks.
Domain Name System Attacks
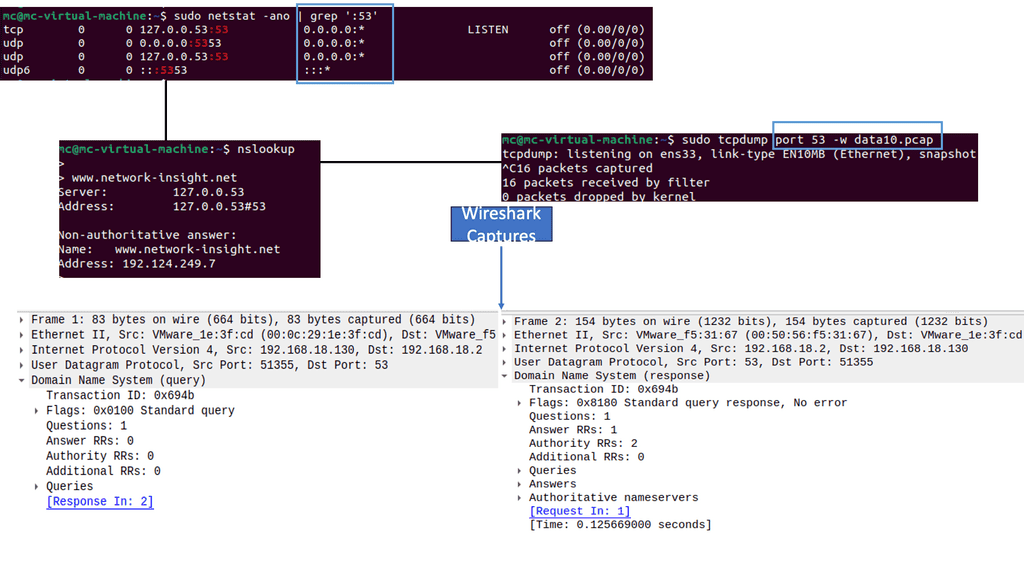
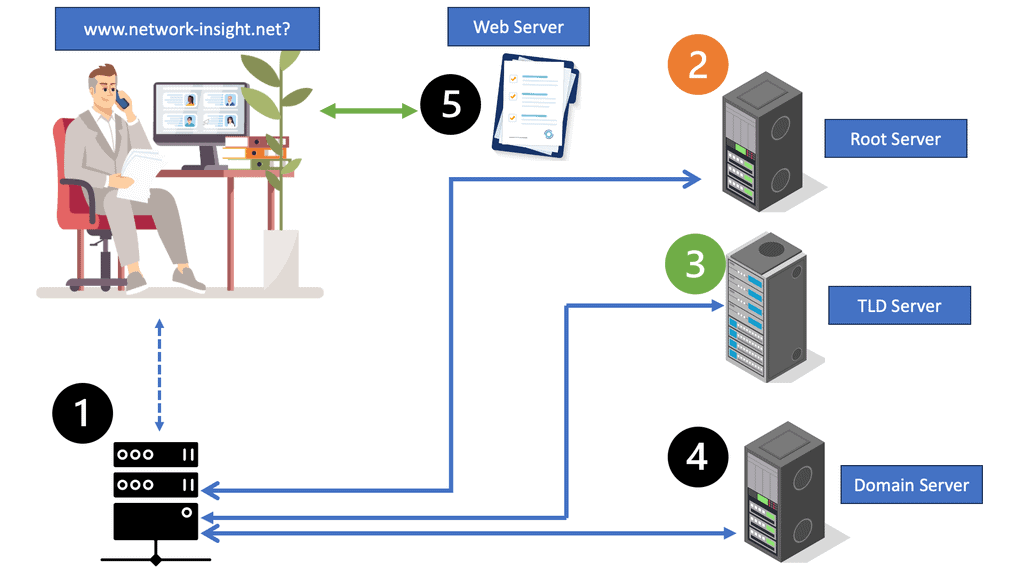
Hostnames and domain names, like www.network-insight.net, are translated into their numerical IP addresses by DNS, the backbone of the internet. Users can seamlessly access their intended online destinations through it. Even so, it is possible to exploit the integral system. Web browsers use DNS resolution to determine the IP address of a website when a user types its URL. Attackers can, however, compromise DNS resolution. To attack the DNS system, we need to understand the following concepts:
By using DNS name resolution, the DNS server converts the URL hostname of www.network-insight.net into its IP address when a user types the URL of a website, such as www.network-insight.net. The following steps are taken to resolve a name:
- First, the system checks the DNS cache, which is stored locally. The cache can be viewed by typing ipconfig /displaydns. Since the DNS cache is the first place where DNS resolution is performed, it is a prime target for attackers.
- If the URL is not in the DNS cache, the HOSTS file is checked. You can find the file on your local computer. A Windows computer’s driver can be found at C:/Windows/System32/drivers/etc.
- The system consults the root hints when the URL is not in the cache or the HOSTS file.
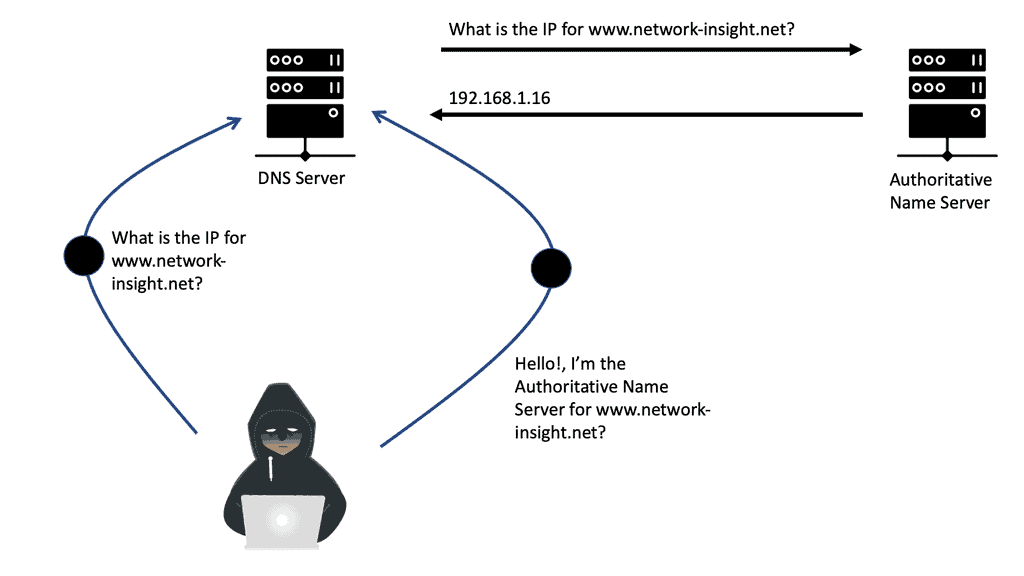
Attackers cannot launch attacks against known malicious domains because DNS sinkholes provide false information. If the sinkhole redirects malicious actors to a honeypot instead of the sinkhole, they might be redirected to the honeypot.
Using DNS cache poisoning, an attacker redirects users to malicious websites by manipulating DNS records. When attackers poison DNS caches with fake information, users are exposed to fraudulent activity. The attacker poisons the DNS cache with fake entries to redirect the victim to a fake website that looks legitimate. Attackers can also manipulate HOSTS files, which are searched twice during DNS resolution.
Network security and information gathering depend heavily on DNS tools and protocols. Kali Linux’s DNSenum tool collects comprehensive DNS information. DNSSEC employs digital signatures to enhance DNS security and thwart DNS cache poisoning attacks.
DON’T FORGET
The victim is redirected from a legitimate website to a fraudulent one by DNS cache poisoning. DNS spoofing is another term for it.
**Example Technology: DNS Firewall**
A : – DNS firewalls can provide several security and performance benefits. They sit between recursive resolvers and the authoritative nameservers of websites and services. The firewall can limit the rate at which attackers can access the server to prevent it from being overwhelmed.
B : – the event of an attack or any other reason the server goes down, a DNS firewall can serve DNS responses from the cache. Additionally, to security features, DNS firewalls provide performance solutions, such as faster DNS lookups and reduced bandwidth costs for DNS operators.
C: – DNS firewalls operate by intercepting DNS requests made by devices on your network. These requests are then compared against a database of known malicious domains or filtered based on your custom-defined rules. If a domain is flagged as malicious or unwanted, the DNS firewall prevents the device from accessing it, effectively blocking potential threats.
D : – DNS firewall can be implemented at the network level or on individual devices. Network-level DNS firewalls provide comprehensive protection for all devices connected to the network, while device-level firewalls offer more granular control. Choosing the right approach depends on your specific needs and network infrastructure.
**Example Technology: DNSSEC**
DNSSEC protects against attacks by digitally signing data. Secure DNS lookup requires signatures at every level. An expert can verify the signature by looking at it, much like when someone signs a legal document with a pen; the signature is unique and cannot be faked. Digital signatures prevent tampering with data.
The primary purpose of DNSSEC is to prevent DNS spoofing and cache poisoning attacks, which can lead to unauthorized redirection of web traffic and potential data breaches. By implementing DNSSEC, organizations and users can be more confident that the websites they are accessing are legitimate and haven’t been tampered with.
DNSSEC uses a hierarchical chain of trust to verify the authenticity of DNS records. It involves using public and private key pairs to sign and verify DNS data. When a user requests a DNS record, the response is validated by tracing the digital signatures up the chain of trust until it reaches the root zone. This ensures the response is authentic and hasn’t been altered in transit.
The Challenging Landscape:
Cyber threats are evolving and becoming more costly. They’re not just about stealing information anymore; they’re about disrupting service and causing downtime. Internet-facing networks and services are easy targets. Powerful botnets are readily available to lease and have the capacity to bring networks to a halt. A botnet-for-hire service costs around $38 per month.
A nominal fee compared to the negative effect on company services. Incapsula states that a DDoS could cost a business $40,000 per hour in loss of opportunity, property loss, and customer trust. Individuals who lease botnets do not need special skills and can execute assaults using previously packaged scripts. Nowadays, launching a DDoS attack is easy, getting a lot for minimal effort.
Lock Down Master Databases:
They are making DNS security designs a key component. One of the most valuable network services is the Domain Name System (DNS). The DNS structure is an address book of names to I.P. mappings. When DNS is down, users can’t resolve correctly, or requests get redirected to imposter locations when databases are compromised.
Therefore, administrators must ensure their master databases are appropriately locked and secured. If the master database becomes compromised, SSL security and passwords no longer mean squat. It’s game over. The attack surface for DNS-based DoS attacks is so vast, with various DNS amplification, DNS reflection attack, and other DNS exploits available. There are DNS security solutions, such as Domain Name System Security Extensions (DNSSEC), but they are not widely implemented.
For additional pre-information, you may find the following posts helpful:
Highlights: DNS Security Designs
DNS plays a role in all things internet; remember, absolutely nothing happens without it. The DNS system provides a compelling attack vector to those bad actors. If you remove somebody’s authoritative nameservers, you take that person off the internet. So, there is a lot of collateral damage. So, the first order of business if you’re hosting the direct target of a DDoS attack is to identify who that target is.
Utilities, such as dnstop, can show the inbound queries broken down by domain, RRtype, and originating resolver, among other criteria. We also use Packet analyzers, with Wireshark being the most popular. Wireshark can help you discern patterns in the attack traffic used to create firewall rules or filters to discard malicious traffic.
DNS Security Extensions (DNSSEC)
DNSSEC is a set of security extensions to DNS that helps verify the authenticity and integrity of DNS responses. Using digital signatures, DNSSEC ensures that the responses received from DNS servers are not tampered with during transit. It also helps prevent DNS cache poisoning attacks, where attackers redirect users to malicious websites by corrupting DNS cache data. Implementing DNSSEC provides a layer of trust and authenticity to DNS queries and responses.
DNS Filtering and Whitelisting
DNS filtering and whitelisting are essential to protecting networks from accessing malicious websites and content. Organizations can block access to known malicious domains by filtering DNS requests, preventing users from inadvertently accessing harmful websites. Whitelisting, on the other hand, allows organizations to explicitly allow access to specific domains, reducing the risk of accidental exposure to malicious content.
DNS Firewall
A DNS firewall acts as a protective barrier between the internal network and the internet. It monitors and filters DNS traffic, blocking access to known malicious domains or IP addresses. DNS firewalls can also detect and block DNS tunneling attempts, where attackers use DNS requests and responses to bypass traditional security controls and exfiltrate data. Organizations can add an extra layer of defense to their network infrastructure by implementing a DNS firewall.
DNS Anomaly Detection
DNS anomaly detection systems analyze DNS traffic patterns to identify any abnormal behavior that may indicate a security threat. By continuously monitoring DNS queries and responses, these systems can detect patterns such as large volumes of queries from a single IP address, unusual query types, or sudden spikes in DNS traffic. DNS anomaly detection helps organizations proactively prevent security incidents by promptly detecting and alerting administrators about potential threats.
DNS-based Authentication of Named Entities (DANE)
DANE is a protocol that allows the association of digital certificates with domain names using DNS records. By leveraging DNS as a repository for certificate authority (CA) information, DANE provides an additional layer of security to SSL/TLS certificates. It helps prevent man-in-the-middle attacks by ensuring that the certificate presented by a server matches the one stored in DNS records. Implementing DANE can help organizations enhance the security of their encrypted communications.
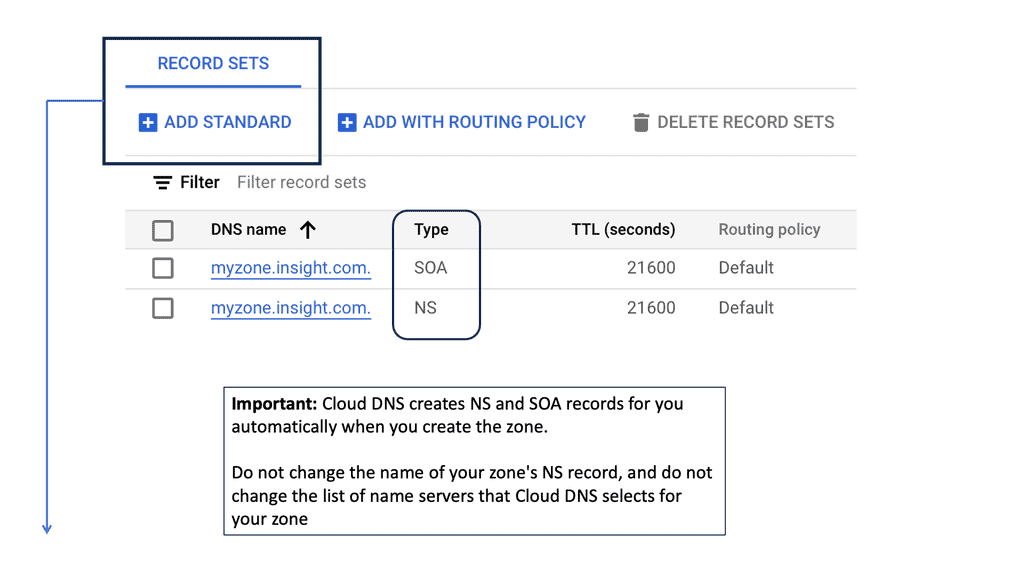
DNS designs usually operate in a master / secondary mode, a simple delegation design. The master database is a read-write database protected on the LAN behind a firewall. The secondary database is a slave to the master and accepts client requests. It cannot be modified and usually sits in the demilitarized zone (DMZ) for internet-facing requests. Additions and modification records are processed on the master, with only the administrator having access.
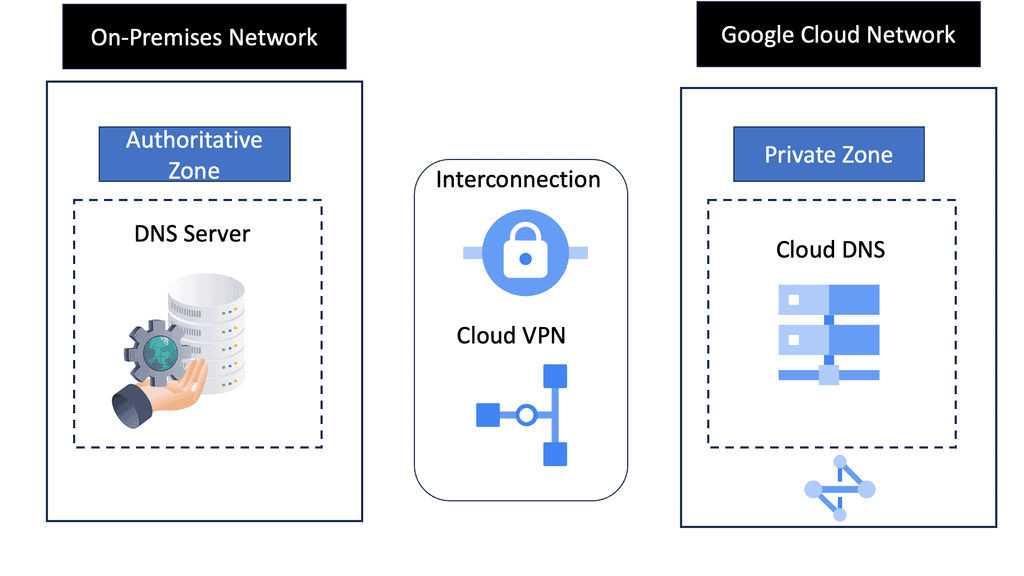
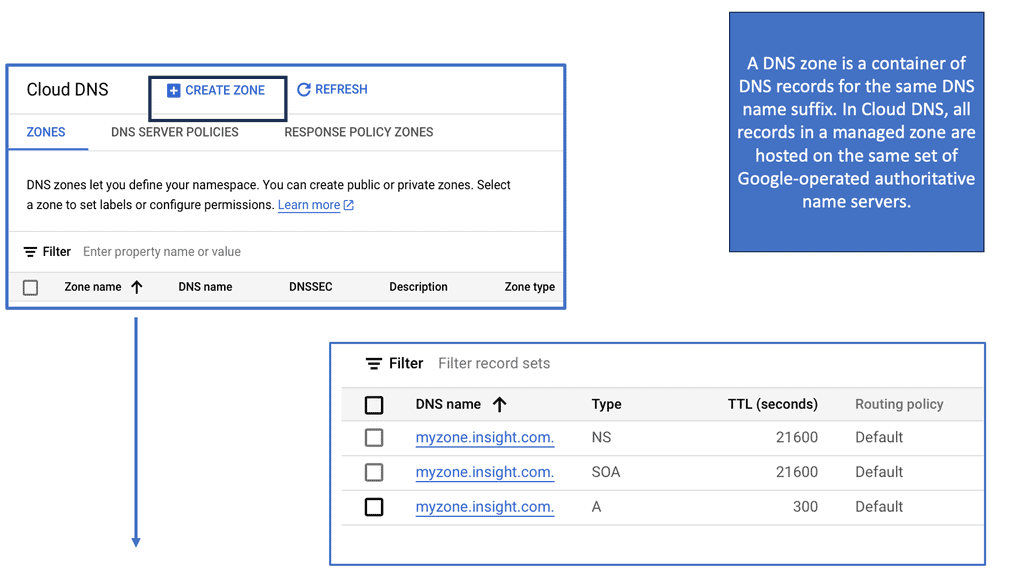
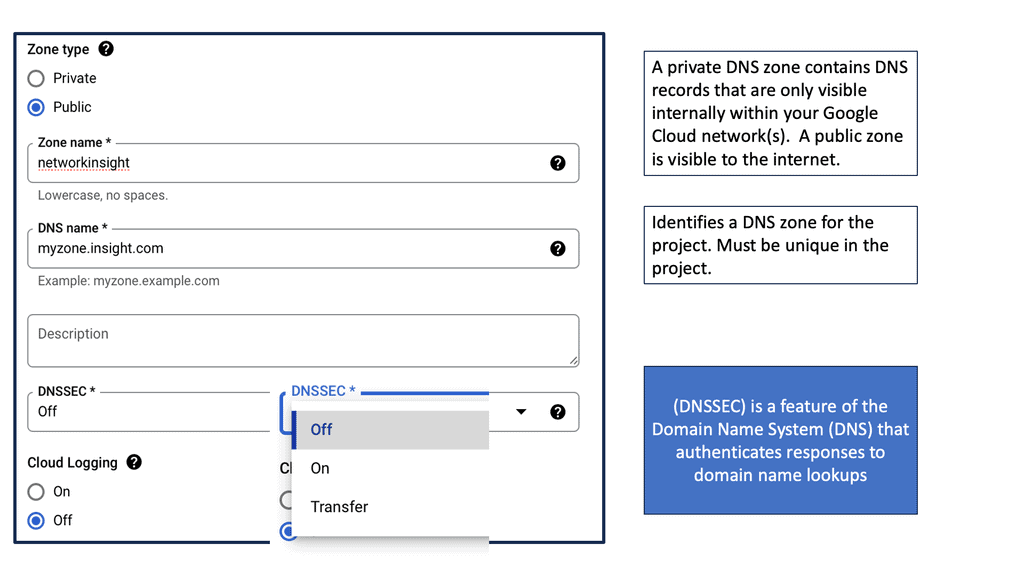
Cloud DNS
Everything is moving to the cloud, a shared resource multiple people use. The cloud is cheaper, and resources are fully utilized. It supports long- and short-lived environments, making it a popular resource for I.T. environments. However, the cloud presents challenges because resources may move from intra and inter-data center locations.
We usually keep the same I.P. within the data center, but the I.P. address may change if it’s an inter-data center move. You may use stretched VLANs or IPv6 host-based routing, but this creates routing protocol churn, and stretched VLANs bring apparent drawbacks. DNS must be accurate and flexible to fully support private, public, and hybrid cloud environments.
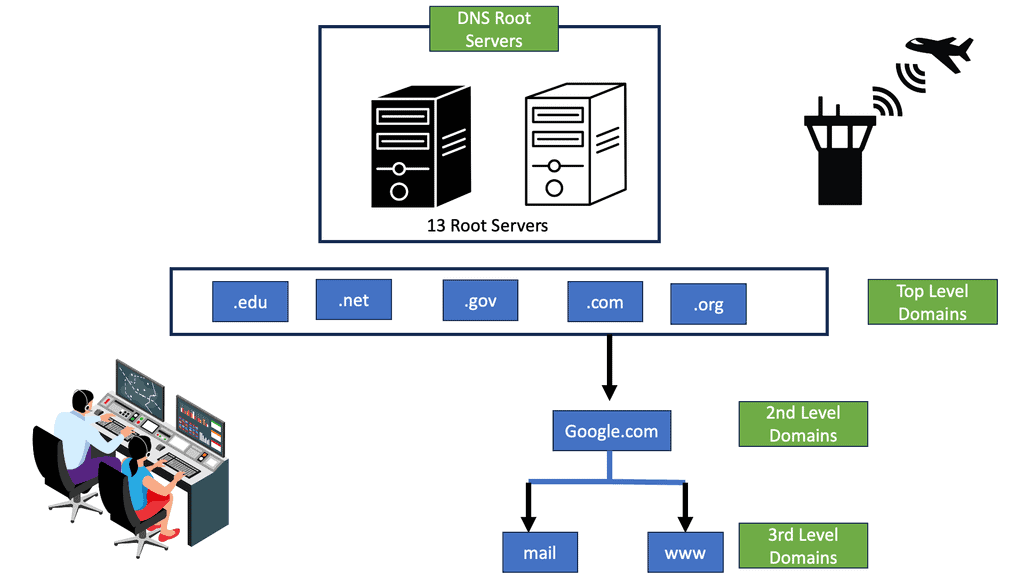
DNS Root Servers
DNS is a fully distributed hierarchical database that relies on root servers. Requests start walking the root zone down to top-level domains, subdomains, and hosts. There is no limit on how deep you go. The concept of zones exists, referring to an administrative boundary. It is up to the administrator to ensure their zones are correctly secure.
Everything relies on root servers; nothing is resolvable if the DNS root servers go down. An attack in December 2015 effectively knocked three of the 13 root servers out for several hours. All lower-down layers still operate as usual—ping, traceroute, and MPLS still work, except for simple name resolution.
We have 13 root servers labeled A to M. It would be impossible to serve all client’s requests with just 13 servers, so they are replicated with anycast I.P. addressing. Their purpose is to route requests to the closest name server. Close does not mean distance in kilometers. It refers to hop count or latency. Latency is more challenging to measure.
DNS Security: The Extensions
The reconnaissance phase of a broader attack might start by querying DNS. Anyone from any computer connected to the Internet can initiate a Whois command to determine who manages the DNS servers. Some servers return the actual individual’s name as the contact for the queried administrative domain. This contact account is authorized to make any changes.
If the account is compromised, the attacker obtains complete control and may redirect the entire domain. The best practice is to label the contact as the “domain manager, ” not individual names. For further investigation, one can enter the command-line lookup for whois called nslookup. Nslookup allows you to look at different individual records. For example, set q=mx examines individual mail records.
DNS tools
There are tools available to secure DNS. DNS security extensions are enhancements to the original DNS name system invented 25 years ago. They add digital signatures to DNS and can sign DNS zone data cryptographically. This allows DNS servers to validate data and ensure it hasn’t changed. DNSSEC is available, but most don’t use it. It is a trust relationship relying on Public and Private keys. The entire chain must be trusted. Anyone can assess the public key, but no one sees the private key.
The private sector does the encryption while the public sector decrypts. It can work the other way around, but you can only decrypt it with the private key. DNSSEC encrypts the actual checksum. The public key decrypts the assigned digest and then compares the two. If they are the same, everything works. The initial question with DNSSEC is, how do you get all the public keys to the database? They publish the public key in DNS as a record type to get around this.
DNS sinkholing
Palo Alto and other vendors offer what is known as DNS sinkholing. Sinkholing allows you to direct suspicious DNS traffic to a sinkhole IP address. The sinkhole IP is not an actual host but simply a logical address. The malicious domain name can be resolved with the specified IP address. For example, F5 has a DNS Express product that puts a GTM load balancer before the DNS servers. F5 GTM can handle over 2 million requests per second – more than enough to handle most DDoS attacks.
Closing Points on DNS Security Designs
DNS, by its nature, is vulnerable to several types of attacks. Among the most prevalent are DNS spoofing and cache poisoning, where attackers corrupt the DNS data to redirect users to fraudulent sites. Denial of Service (DoS) attacks, where DNS servers are overwhelmed with traffic, can also cripple network services. Understanding these threats is the first step in designing robust security measures to protect DNS infrastructure.
Effective DNS security design involves multiple layers of defense. One of the primary strategies is implementing DNS Security Extensions (DNSSEC), which adds a layer of authentication to ensure the integrity and authenticity of DNS data. Furthermore, employing secure configurations, such as disabling unnecessary services and regularly updating software, can significantly reduce vulnerabilities. Another vital aspect is the use of redundant DNS servers to ensure network resilience against attacks.
Implementing security measures is only part of the solution; ongoing management is crucial. Regular monitoring and auditing of DNS traffic can help detect anomalies and potential threats. Employing automated tools for threat detection and response can enhance security posture. Additionally, educating staff on DNS-related security risks and practices ensures that human error does not compromise security efforts.
Summary: DNS Security Designs
With the ever-increasing importance of online security, it is crucial to understand the significance of DNS security designs. This blog post delved into DNS security and explored various design approaches to safeguard your online presence. From encryption to DNS filtering, we will cover essential aspects to help you make informed decisions for your digital security strategy.
Understanding DNS Security
DNS (Domain Name System) security is all about protecting the integrity, availability, and confidentiality of the DNS infrastructure. It is pivotal in securely ensuring that website visitors are directed to the correct IP address. Without proper DNS security, cyber threats like DNS spoofing and cache poisoning can lead to unauthorized access, data breaches, and other detrimental consequences.
Encryption for DNS Security
Encryption is a fundamental aspect of DNS security designs. Implementing protocols like DNS over HTTPS (DoH) or DNS over TLS (DoT) can provide additional protection against eavesdropping and tampering. Encrypting DNS traffic protects sensitive information, such as domain queries and IP addresses, from prying eyes, bolstering the overall security posture.
DNS Filtering for Enhanced Security
DNS filtering is a practical approach to fortifying DNS security designs. By leveraging filtering techniques, organizations can block access to malicious websites, phishing attempts, and malware distribution networks. Implementing robust DNS filtering policies helps promote safer browsing experiences for users and prevent potential security breaches.
Implementing DNSSEC for Data Integrity
DNS Security Extensions (DNSSEC) is a crucial technology that ensures the integrity and authenticity of DNS responses. DNSSEC mitigates the risks of DNS cache poisoning and domain hijacking by digitally signing DNS records. Implementing DNSSEC provides a verifiable chain of trust, reducing the chances of falling victim to DNS-related attacks.
Conclusion
In this blog post, we have explored various DNS security designs to help safeguard your online presence. Understanding the significance of DNS security and implementing measures like encryption, DNS filtering, and DNSSEC can significantly enhance your digital security posture. By staying proactive and adopting these security practices, you are taking crucial steps toward protecting your online assets and ensuring a safer digital experience.