Blog
Network Insight.
- Premium Consultancy, Ebooks, Videos and Elearning
BGP SDN – Centralized Forwarding
BGP SDN The networking landscape has significantly shifted towards Software-Defined Networking (SDN) in recent years. With its ability to centralize network management and streamline operations, SDN has emerged as a game-changing technology. One of the critical components of SDN is Border Gateway Protocol (BGP), a routing protocol that plays a …
Smarter Networks: Nuage Networks & SD-WAN Part 2
Nuage Networks: SD-WAN Traditional WANs hinder business operations and don’t meet the demands of today’s applications. A new emerging WAN architecture called SD-WAN replaces existing WANs with a business-aware approach to networking. This approach is now thoroughly adopted by Nuage Networks, and their SD-WAN solution solves the limitations of …
Load Balancing
Load Balancing In today’s digital age, where websites and applications are expected to be fast, efficient, and reliable, load balancing has emerged as a critical component of modern computing infrastructure. Load balancing significantly ensures that server resources are utilized optimally, maximizing performance and preventing system failures. This blog post will …
OVS Bridge and Open vSwitch (OVS) Basics
Open vSwitch: What is OVS Bridge? Open vSwitch (OVS) is an open-source multilayer virtual switch that provides a flexible and robust solution for network virtualization and software-defined networking (SDN) environments. It’s versatility and extensive feature set make it an invaluable tool for network administrators and developers. In this …
SD WAN Tutorial: Nuage Networks
Nuage Networks The following post details Nuage Netowrk and its response to SD-WAN. Part 2 can be found here with Nuage Network and SD-WAN. It’s a 24/7 connected world, and traffic diversity puts the Wide Area Network (WAN) edge to the test. Today’s applications should not be hindered …
Data Center Failure
Data Center Failure In today’s data-driven world, the uninterrupted availability of data is crucial for businesses. Data center storage failover plays a vital role in ensuring continuous access to critical information. In this blog post, we will explore the importance of data center storage failover, its key components, implementation strategies, …
Data Center Failover
Data Center Failover In today’s digital age, data centers play a vital role in storing and managing vast amounts of critical information. However, even the most advanced data centers are not immune to failures. This is where data center failover comes into play. This blog post will explore what data …
GTM Load Balancer
GTM Load Balancer In today’s fast-paced digital world, websites and applications face the constant challenge of handling high traffic loads while maintaining optimal performance. This is where Global Traffic Manager (GTM) load balancer comes into play. In this blog post, we will explore the key benefits and functionalities of GTM …
Full Proxy
Full Proxy In the vast realm of computer networks, the concept of full proxy stands tall as a powerful tool that enhances security and optimizes performance. Understanding its intricacies and potential benefits can empower network administrators and users alike. In this blog post, we will delve into the world of …
IPv6 Fragmentation
IPv6 Fragmentation In the vast landscape of networking and internet protocols, IPv6 stands as a crucial advancement. With its expanded address space and improved functionality, IPv6 brings numerous benefits. However, one aspect that requires attention is IPv6 fragmentation. In this blog post, we will dive deep into the intricacies of …
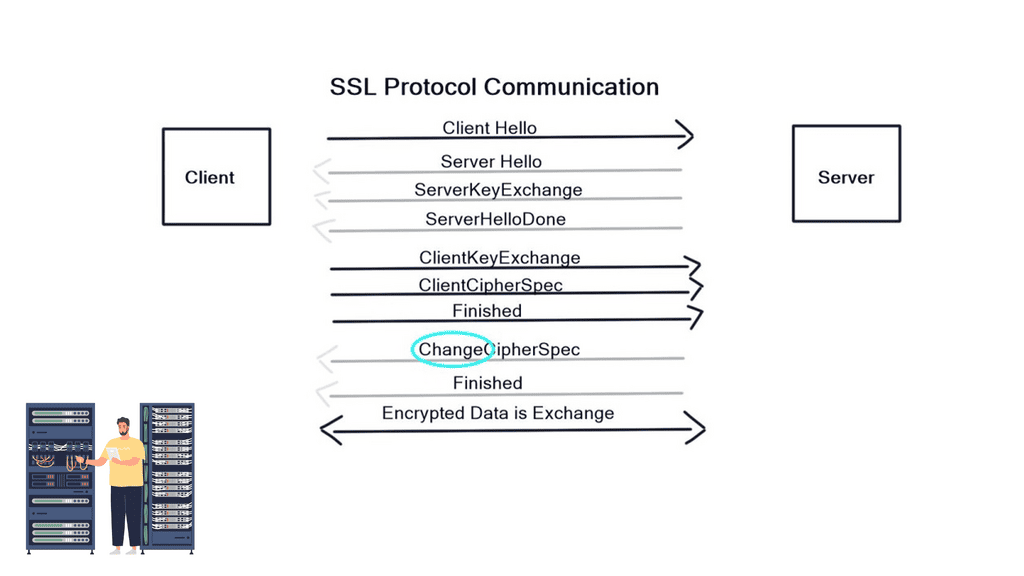
SSL Security
SSL Security In today’s digital age, ensuring online security has become paramount. One crucial aspect of protecting sensitive information is SSL (Secure Sockets Layer) encryption. In this blog post, we will explore what SSL is, how it works, and its significance in safeguarding online transactions and data. SSL, or Secure …
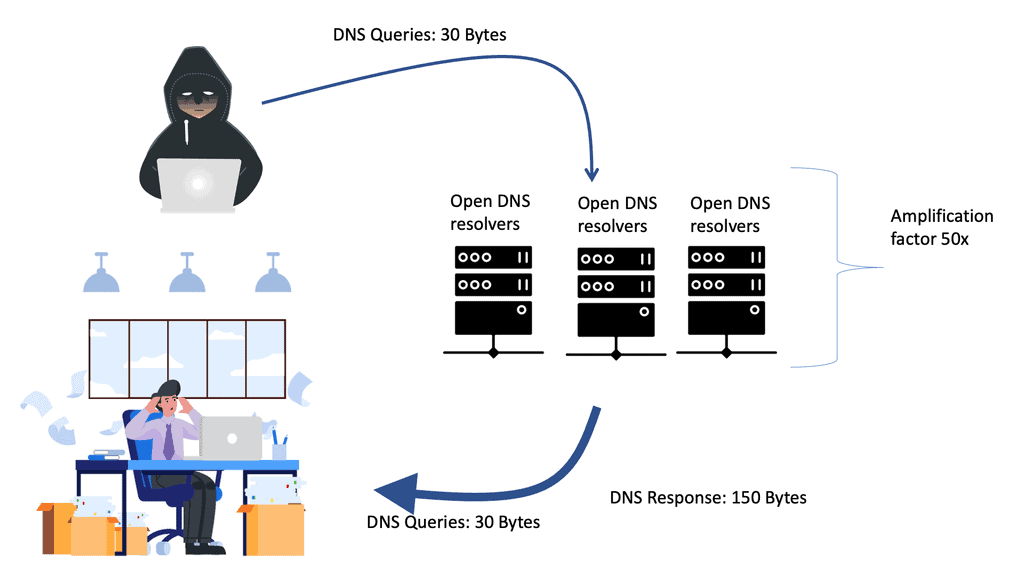
DNS Reflection Attack
DNS Reflection attack In today’s interconnected world, cyber threats continue to evolve, posing significant risks to individuals, organizations, and even nations. One such threat, the DNS Reflection Attack, has gained notoriety for its potential to disrupt online services and cause significant damage. In this blog post, we will delve into …