Distributed Firewalls
In today's interconnected world, where data breaches and network attacks are becoming increasingly common, protecting sensitive information has become paramount. As organizations expand their networks and adopt cloud-based solutions, the need for robust and scalable security measures has grown exponentially. This is where distributed firewalls come into play. In this blog post, we will delve into the concept of distributed firewalls and explore how they can help secure networks at scale.
Traditionally, firewalls have been deployed as centralized devices that simultaneously monitor and filter network traffic. While effective in small networks, this approach becomes inadequate as networks grow in size and complexity. Distributed firewalls, on the other hand, take a different approach by decentralizing the security infrastructure.
Distributed firewalls disperse security capabilities across multiple network nodes, enabling organizations to achieve better performance, scalability, and protection against various threats. By distributing security functions closer to the source of network traffic, organizations can reduce latency and increase overall network efficiency.
Distributed firewalls, also known as distributed network security, are a network security architecture that involves the deployment of multiple firewall instances across various network segments. Unlike traditional firewalls that rely on a single point of entry, distributed firewalls provide a distributed approach to network security, effectively mitigating risks and minimizing the impact of potential breaches.
Enhanced Network Segmentation: One of the key advantages of distributed firewalls is the ability to create granular network segmentation. By implementing firewalls at different points within the network, organizations can divide their network into smaller, isolated segments. This segmentation ensures that even if one segment is compromised, the impact will be contained, preventing lateral movement of threats.
Scalability and Performance: Distributed firewalls offer scalability and improved network performance. By distributing the firewall functionality across multiple instances, the workload is distributed as well, reducing the chance of bottlenecks. This allows for seamless expansion and accommodates the growing demands of modern networks without sacrificing security.
Intelligent Traffic Inspection and Filtering: Distributed firewalls enable intelligent traffic inspection and filtering at multiple points within the network. Each distributed firewall instance can analyze and filter traffic specific to its segment, allowing for more targeted and effective security measures. This approach enhances threat detection and response capabilities, reducing the risk of malicious activities going unnoticed.
Centralized Management and Control: Despite the distributed nature of these firewalls, they can be managed centrally. A centralized management platform provides a unified view of the entire network, allowing administrators to configure policies, monitor traffic, and apply updates consistently across all distributed firewall instances. This centralized control simplifies network management and ensures consistent security measures throughout the network infrastructure.
Distributed firewalls are a powerful tool in defending your network against evolving cyber threats. By distributing firewall instances strategically across your network, you can enhance network segmentation, improve scalability and performance, enable intelligent traffic inspection, and benefit from centralized management and control. Embracing distributed firewalls empowers organizations to bolster their security posture and safeguard their valuable assets in today's interconnected world.
Matt Conran
Highlights: Distributed Firewalls
At its core, a firewall is a network security device that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Acting as a barrier between a trusted internal network and untrusted external networks, such as the internet, firewalls help prevent unauthorized access while allowing legitimate communication to pass through.
Firewalls come in various forms, each tailored to specific needs and environments. The most common types include:
1. **Packet-Filtering Firewalls:** These are the most basic type of firewalls, examining packets and blocking them based on source and destination IP addresses, protocols, and ports. They are fast but don’t inspect the payload of packets, making them less effective against more sophisticated threats.
2. **Stateful Inspection Firewalls:** These firewalls monitor the state of active connections and make decisions based on the context of the traffic. They offer more robust protection than packet-filtering firewalls by keeping track of the state of network connections.
3. **Proxy Firewalls:** Acting as an intermediary between users and the internet, proxy firewalls filter messages at the application layer, providing a higher level of security by inspecting the content of the messages.
4. **Next-Generation Firewalls (NGFW):** Combining traditional firewall technology with additional functionalities like intrusion prevention systems (IPS), application awareness, and identity-based access control, NGFWs offer a comprehensive security solution for modern networks.
**How Firewalls Work: The Inner Mechanics**
Firewalls operate by enforcing a set of rules that determine whether to allow or block network traffic. These rules are based on:
– **IP Addresses:** Allowing or blocking traffic from specific IP addresses.
– **Protocols:** Controlling traffic based on the type of protocol, such as HTTP, FTP, or SMTP.
– **Ports:** Specifying which ports can be used for data transfer.
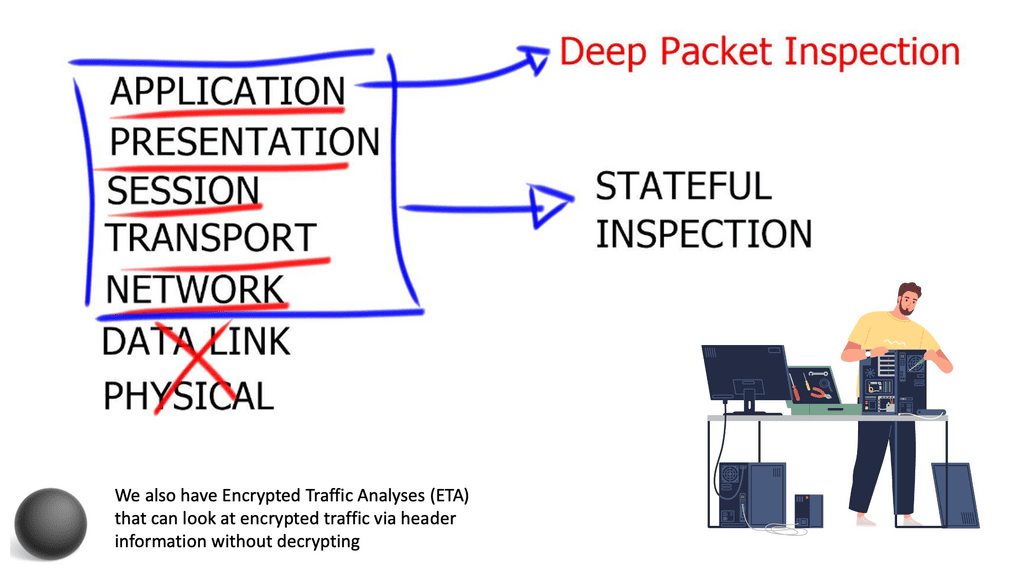
Advanced firewalls also incorporate deep packet inspection, analyzing the data contained within the packets to detect and block malicious content.
**The Role of Firewalls in Cybersecurity**
Firewalls are a fundamental component of any cybersecurity strategy. They provide a first line of defense against external threats, preventing unauthorized access to sensitive data and systems. By filtering traffic and blocking suspicious activity, firewalls help protect against various cyber threats, such as malware, ransomware, and denial-of-service attacks.
Furthermore, firewalls can be configured to enforce organizational security policies, ensuring compliance with industry standards and regulations.
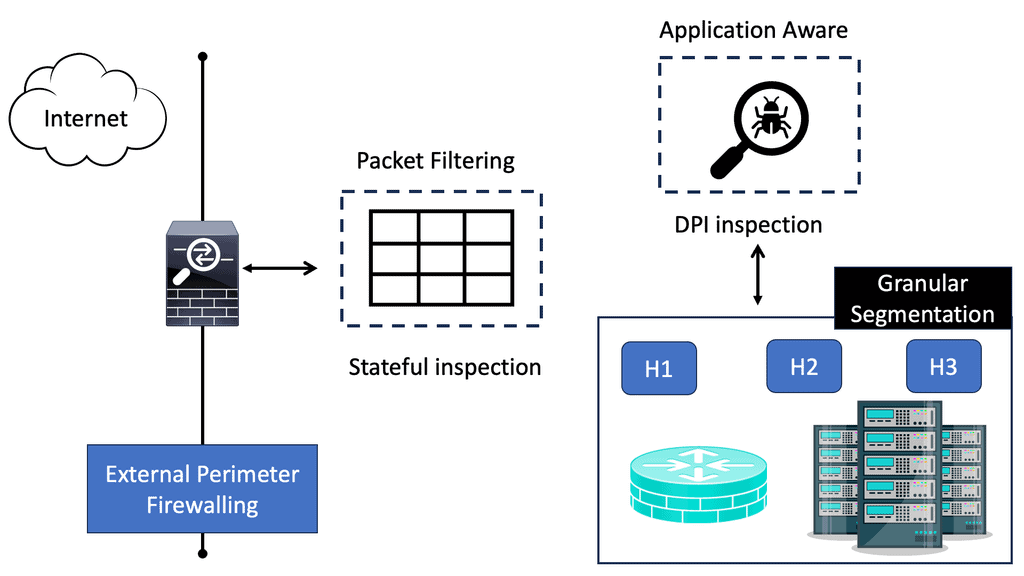
Distributed Firewalling
– Distributed firewalls protect an enterprise’s networks’ servers and user machines against unwanted intrusions by running on host machines. Firewalls are systems (routers, proxies, or gateways) that enforce access control between two networks, protecting the “inside” network from the “outside.” In other words, they filter all traffic, regardless of origin – the Internet or the internal network.
– As a second layer of defense, they are usually deployed behind the traditional firewall. For large organizations, distributed firewalls offer the advantage of defining and pushing enterprise-wide security rules (policies).
– In operating systems, distributed firewalls are usually kernel-mode applications at the bottom of the OSI stack. They filter traffic regardless of where it originates—the Internet or an internal network. They are not considered friendly to either the Internet or the internal network. The perimeter firewall protects the entire network, just as the local firewall protects an individual machine.
– One of the primary advantages of distributed firewalls is their ability to provide enhanced security and protection. Distributing security functions mitigates the impact of a single point of failure, making it harder for malicious actors to breach the network. Additionally, distributed firewalls can handle high-traffic loads more efficiently, reducing latency and improving overall network performance.
Key Considerations:
1 Enhanced Scalability: By distributing firewalling capabilities, organizations can easily scale their security infrastructure to accommodate growing network demands. Additional firewalls can be deployed as needed without relying on a single point of failure.
2. Improved Performance: With distributed firewalling, network traffic can be processed locally, closer to its source. This reduces latency and improves overall network performance, ensuring a seamless user experience.
3. Increased Resilience: Since distributed firewalling is not reliant on a single firewall, the network becomes more resilient to failures. In the event of a firewall malfunction, the remaining firewalls continue to protect the network, minimizing downtime and potential security breaches.
4. Network Segmentation: To effectively implement distributed firewalling, organizations should consider dividing their network into logical segments. Each segment can then be protected by a dedicated firewall, providing granular security control.
5. Centralized Management: While distributed firewalling involves multiple firewalls, it is crucial to have a centralized management system. This allows for unified policy enforcement, simplified configuration management, and comprehensive monitoring across all distributed firewalls.
6. Traffic Visibility: Organizations must ensure that they have the necessary visibility into network traffic to effectively enforce security policies. Solutions such as network monitoring tools and intrusion detection systems can provide valuable insights into the traffic flow and aid in identifying potential threats.
**Implementation Considerations**
Implementing a distributed firewall requires careful planning and consideration. Organizations need to assess their network infrastructure, identify critical nodes for firewall deployment, and define security policies that align with their specific requirements. Furthermore, ensuring seamless communication and coordination between distributed firewall nodes is crucial to maintaining consistent security across the network.
Distributed firewalls have a profound impact on network security. Distributing security policies and enforcement mechanisms creates a more resilient and adaptive architecture. This allows for better protection against advanced threats, as distributed firewalls can detect and respond to attacks in real time, reducing the risk of data breaches and unauthorized access.
 VPC Service Controls
VPC Service Controls
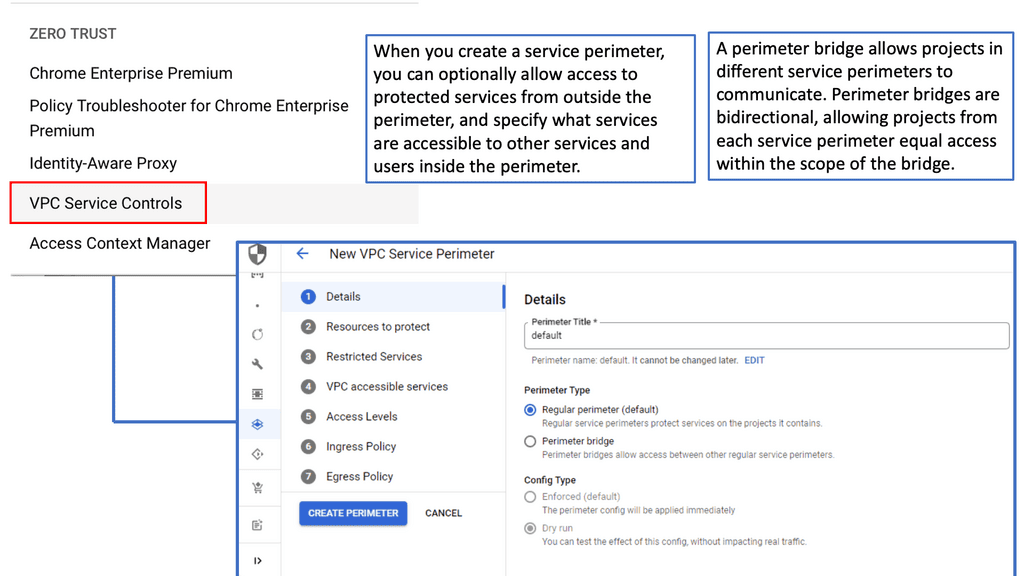
**What Are VPC Service Controls?**
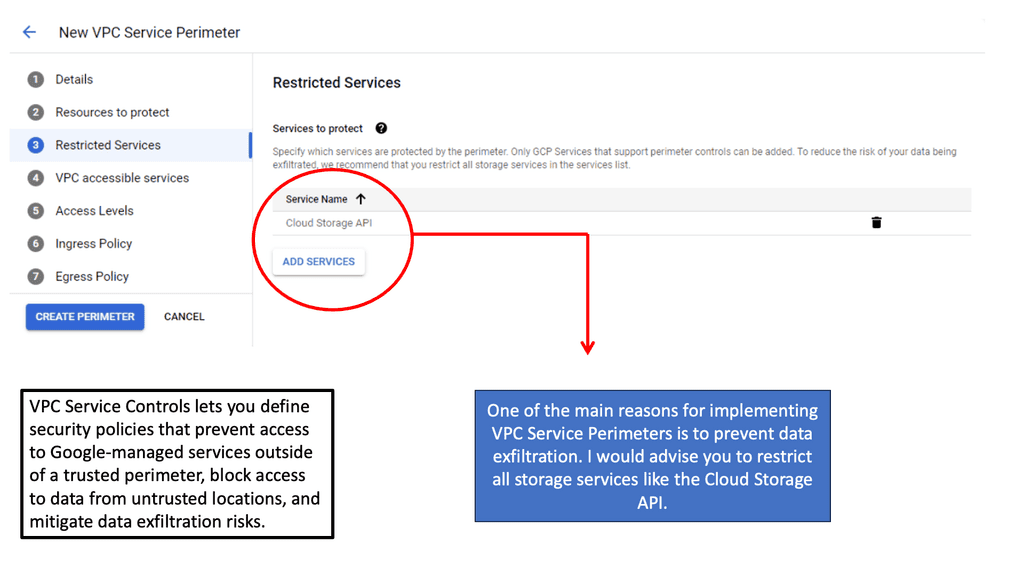
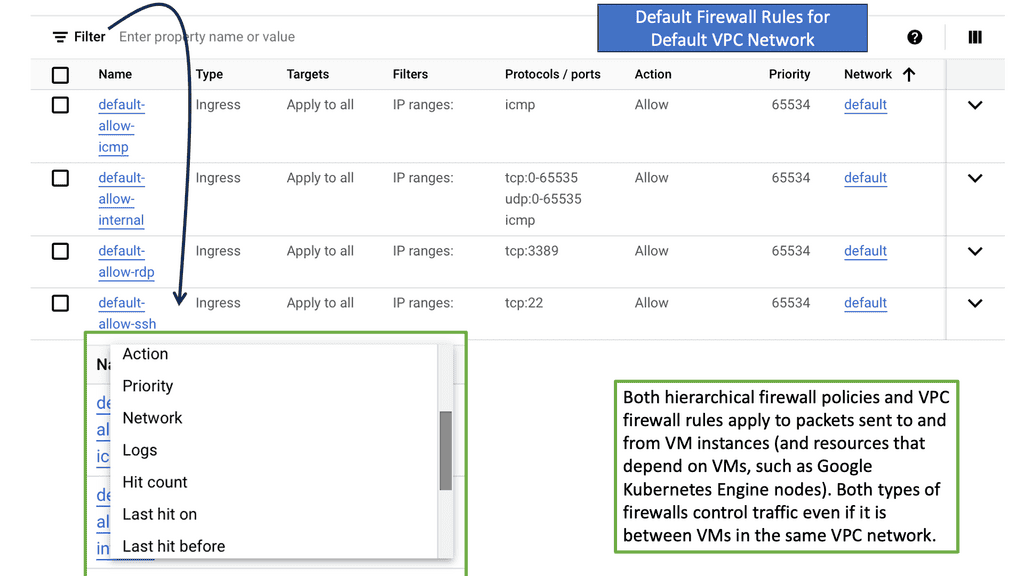
VPC Service Controls are a security feature within Google Cloud that allows organizations to define a security perimeter around Google Cloud resources. This perimeter ensures that sensitive data can only be accessed by authorized services and users, significantly reducing the risk of data exfiltration. By restricting the communication between resources, VPC Service Controls provide a safeguard against unauthorized access and data leaks, making it an invaluable tool for businesses dealing with sensitive information.
**Implementing VPC Service Controls**
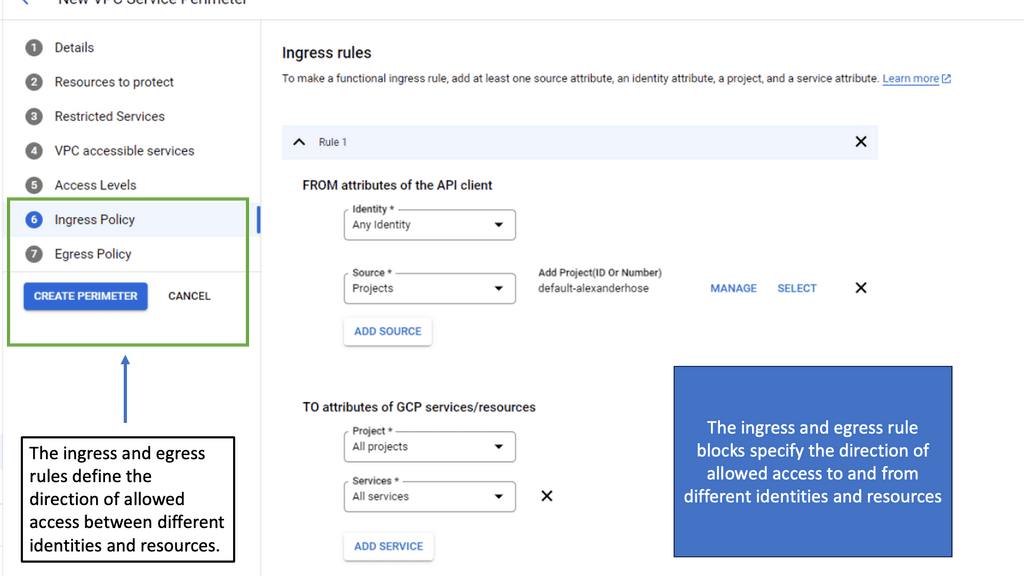
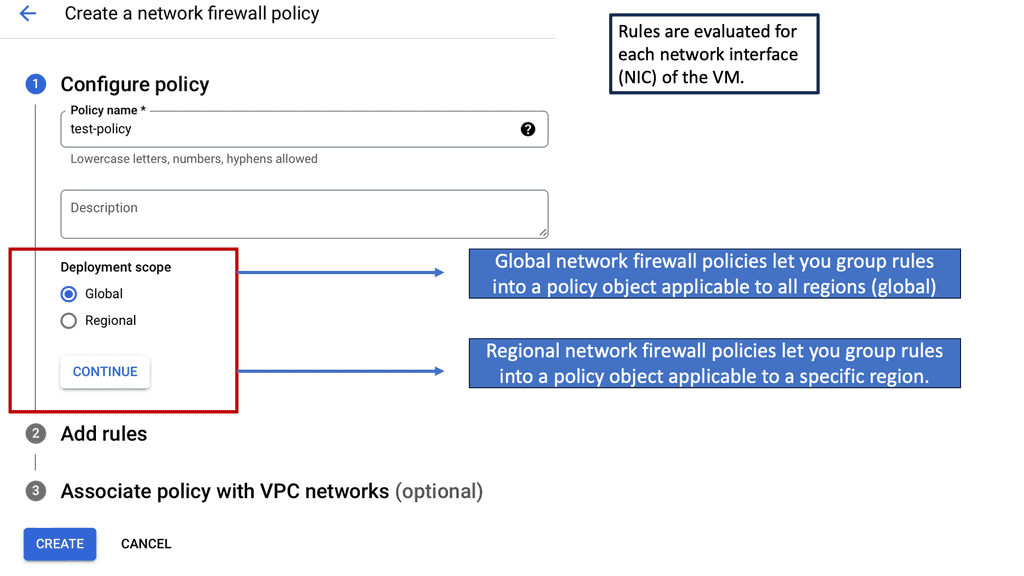
Setting up VPC Service Controls is a straightforward process, but it requires a thoughtful approach to ensure optimal results. To begin with, you’ll need to define your service perimeter, specifying which Google Cloud services and resources are included. Once this is established, you can implement access levels to control who can access the data within this perimeter. This involves setting up user and service account permissions, which are critical in maintaining a secure environment. Google Cloud’s Identity and Access Management (IAM) plays a crucial role in this process, enabling you to manage access easily and effectively.
**Benefits of Using VPC Service Controls**
The primary advantage of using VPC Service Controls is the enhanced security it provides. By controlling the flow of data within your Google Cloud environment, you can prevent unauthorized access and ensure compliance with regulatory requirements. Another significant benefit is the ability to isolate data and services, which minimizes the risk of data breaches. Furthermore, VPC Service Controls offer a flexible and scalable solution that can adapt to the growing needs of your organization, making it an ideal choice for businesses of all sizes.
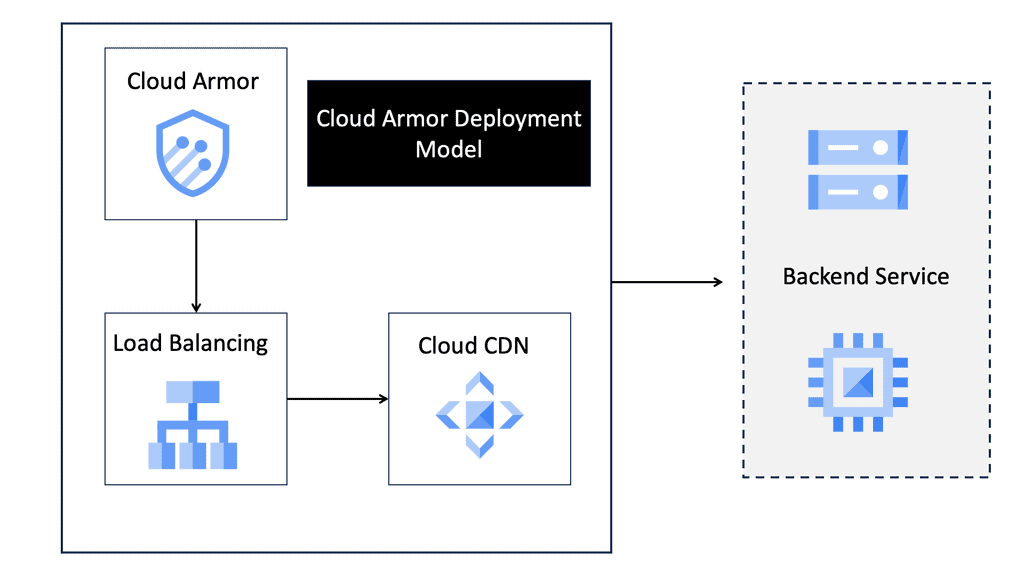
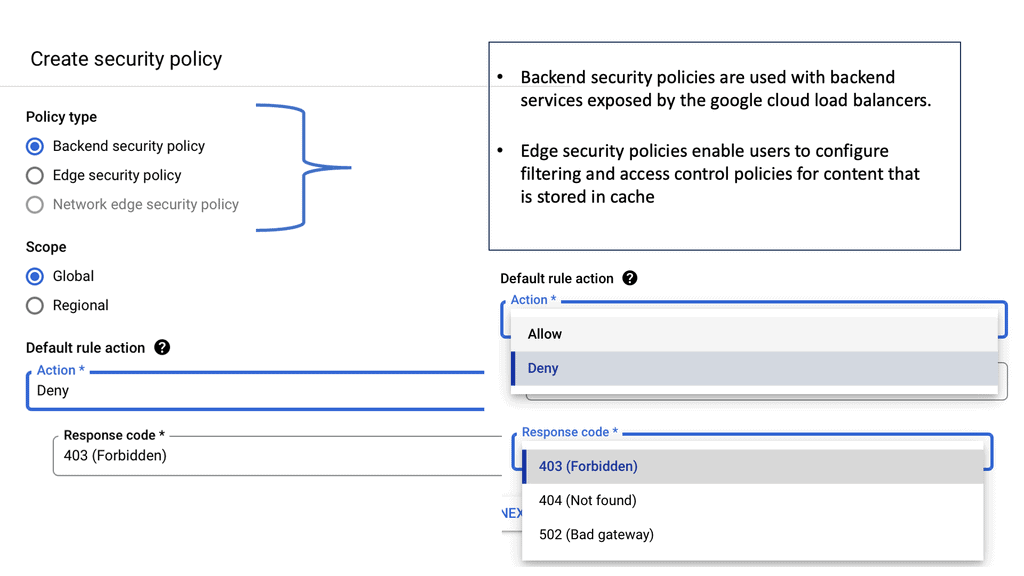
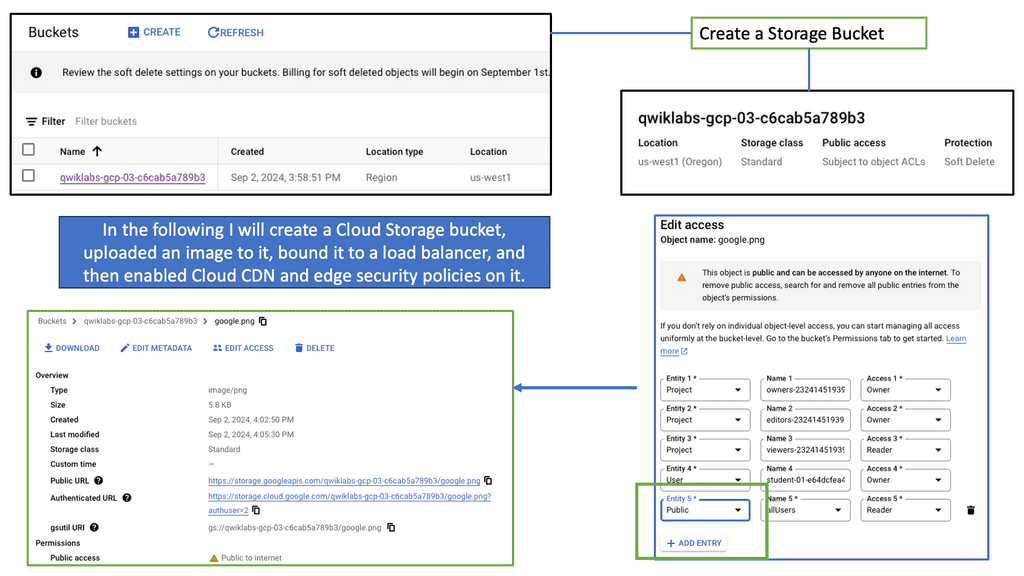
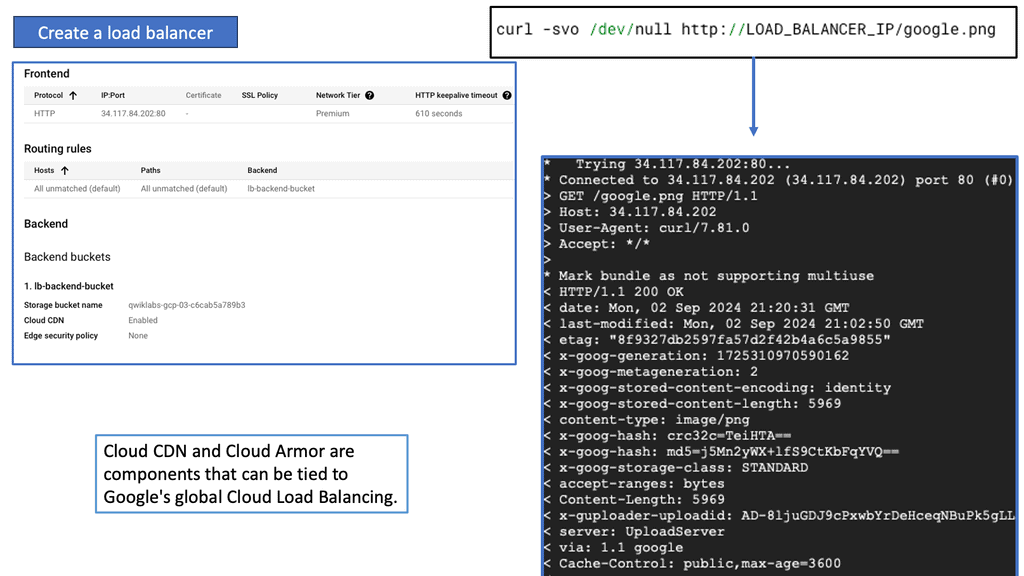
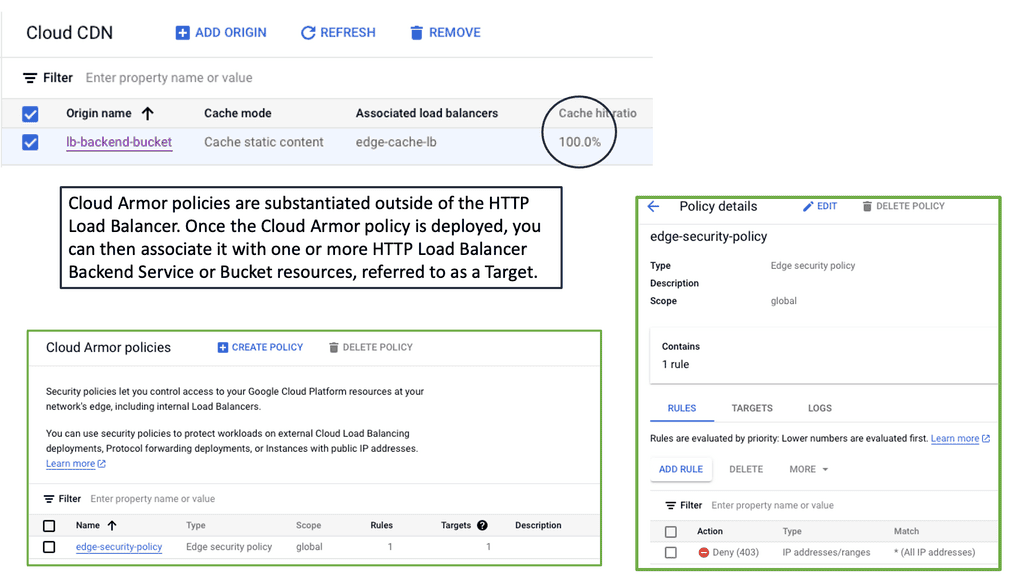
Cloud Armor Distributed Architecture
### What is Cloud Armor?
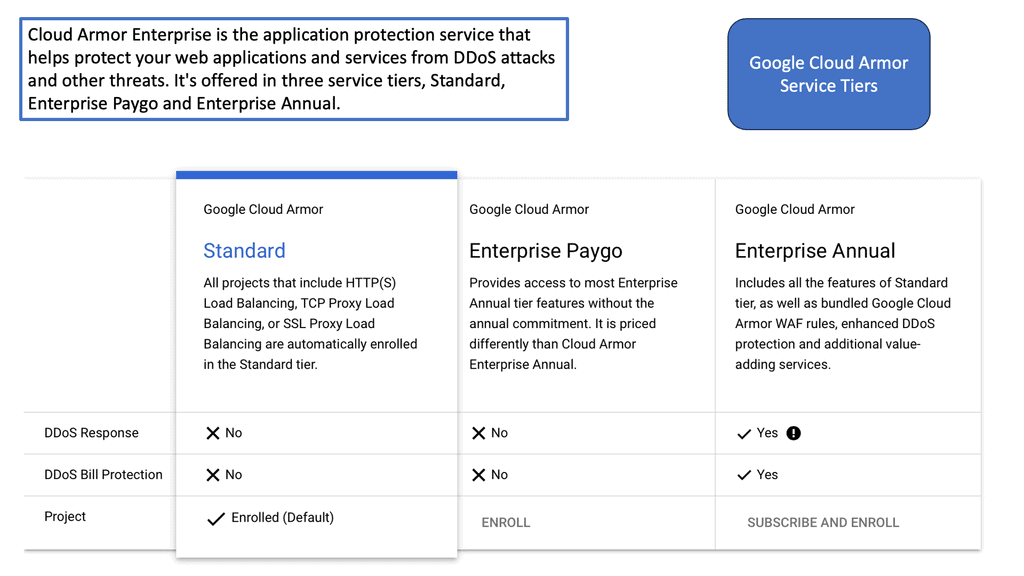
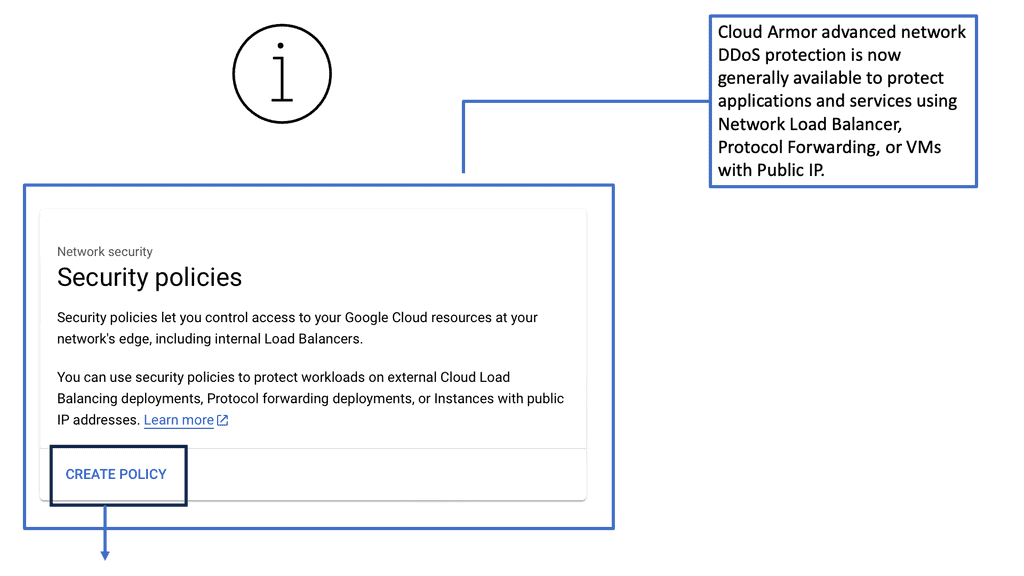
Cloud Armor is a security service that helps protect your applications and websites from a variety of threats such as DDoS attacks, SQL injections, and cross-site scripting. By leveraging Google’s global infrastructure and advanced security technologies, Cloud Armor provides scalable and adaptive protection, ensuring that your digital assets remain secure even under the most demanding conditions.
**Advantages of Cloud Armor’s Distributed Firewall**
One of the standout features of Cloud Armor is its distributed firewall architecture. Unlike traditional firewalls that guard a specific network perimeter, a distributed firewall extends its protection across multiple locations. This feature is critical in the cloud era, where applications and data are often spread across different geographies. Cloud Armor’s distributed approach ensures consistent security policies and threat mitigation strategies regardless of where your assets reside. This not only enhances security but also simplifies management and compliance with regulatory standards.
**Implementing Cloud Armor for Maximum Protection**
Implementing Cloud Armor involves a strategic approach to maximize its protective capabilities. The first step is to integrate Cloud Armor with your existing cloud infrastructure, ensuring seamless communication between your applications and the security layer. Next, configuring security policies tailored to your specific needs will help in filtering out unwanted traffic while allowing legitimate requests. Regular monitoring and updating of these policies are essential to adapt to evolving threats and maintain optimal protection.
### Key Features of Cloud Armor
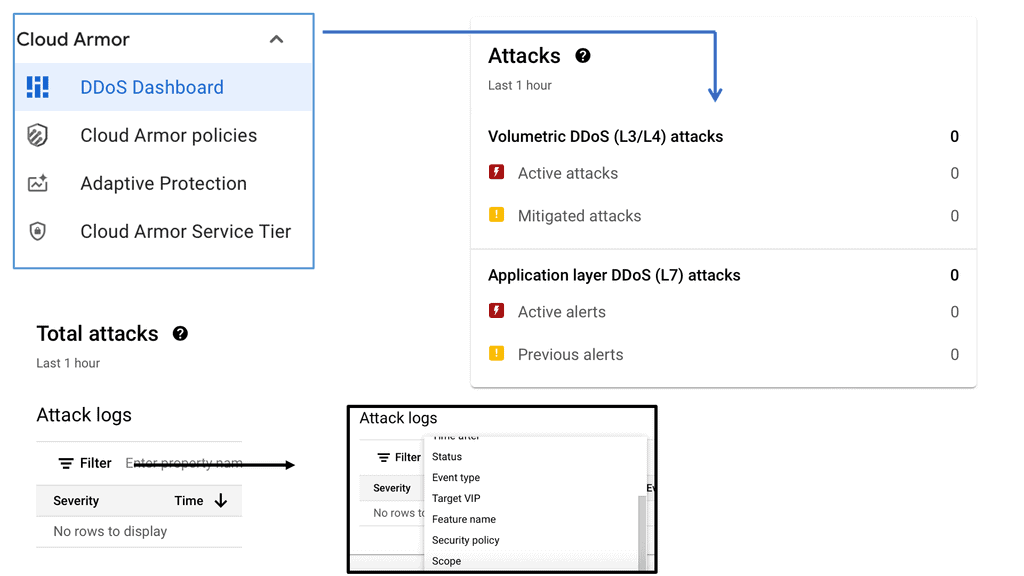
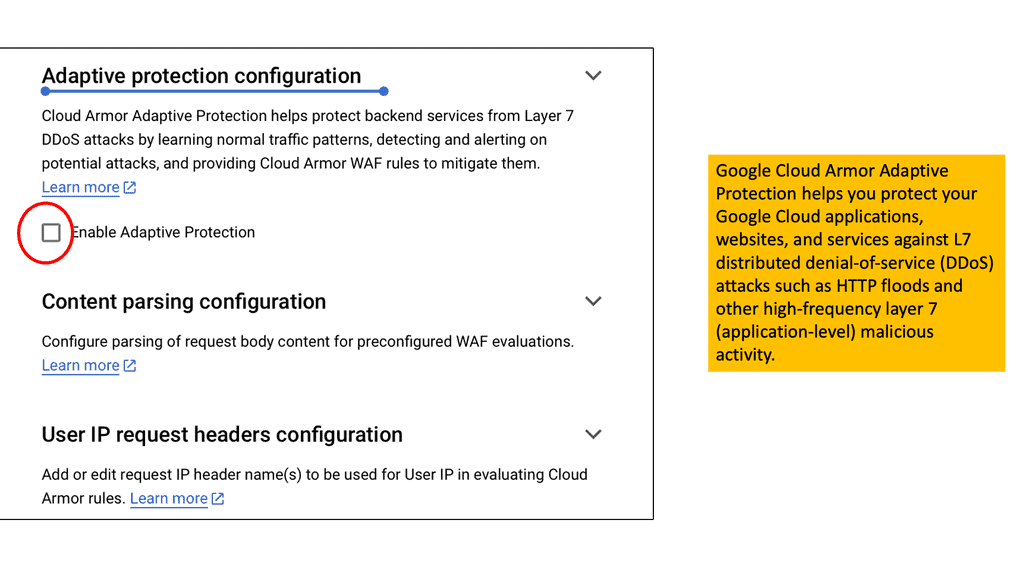
#### Adaptive Threat Detection
One of the standout features of Cloud Armor is its adaptive threat detection capability. This feature uses machine learning to identify and mitigate threats in real-time, adapting to new and evolving attack vectors. It ensures that your security measures are always one step ahead of potential threats.
#### Customizable Security Policies
Cloud Armor allows you to create and enforce custom security policies tailored to your specific needs. Whether you need to block certain IP addresses, enforce rate limiting, or apply more complex rules, Cloud Armor provides the flexibility to design a security framework that aligns with your organizational requirements.
#### Integration with Google Cloud Platform
Seamlessly integrated with the Google Cloud Platform (GCP), Cloud Armor offers a unified approach to security management. This integration allows for easy deployment and management of security policies across your cloud infrastructure, providing a cohesive and streamlined security strategy.
### Enhancing Edge Security Policies with Cloud Armor
Edge security policies are crucial for protecting the periphery of your network where data enters and exits. Cloud Armor enhances these policies by providing robust protection at the edge, ensuring that threats are neutralized before they can penetrate deeper into your network. By deploying Cloud Armor, you can ensure that your edge security policies are enforced with precision, minimizing the risk of data breaches and other cyber threats.
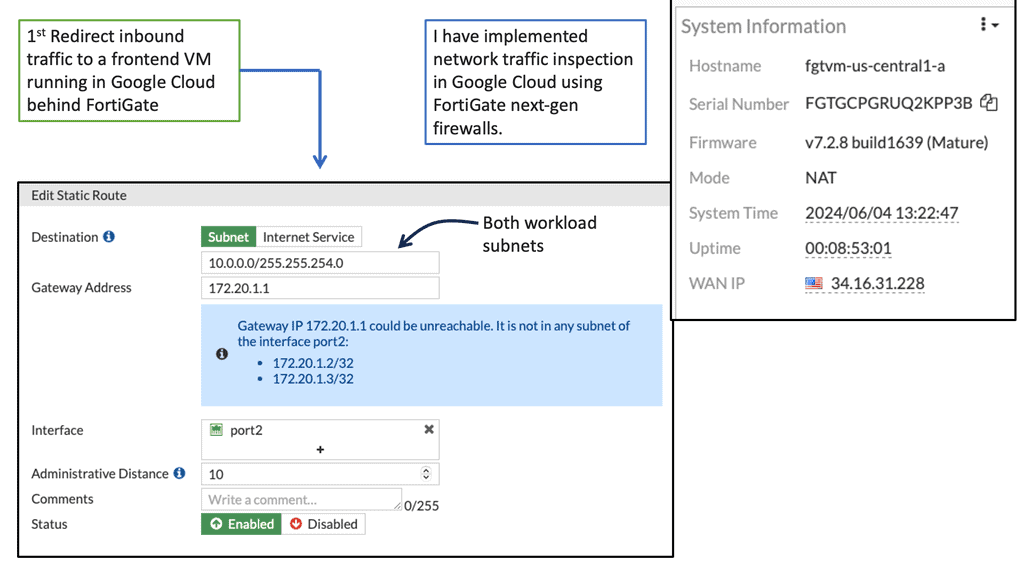
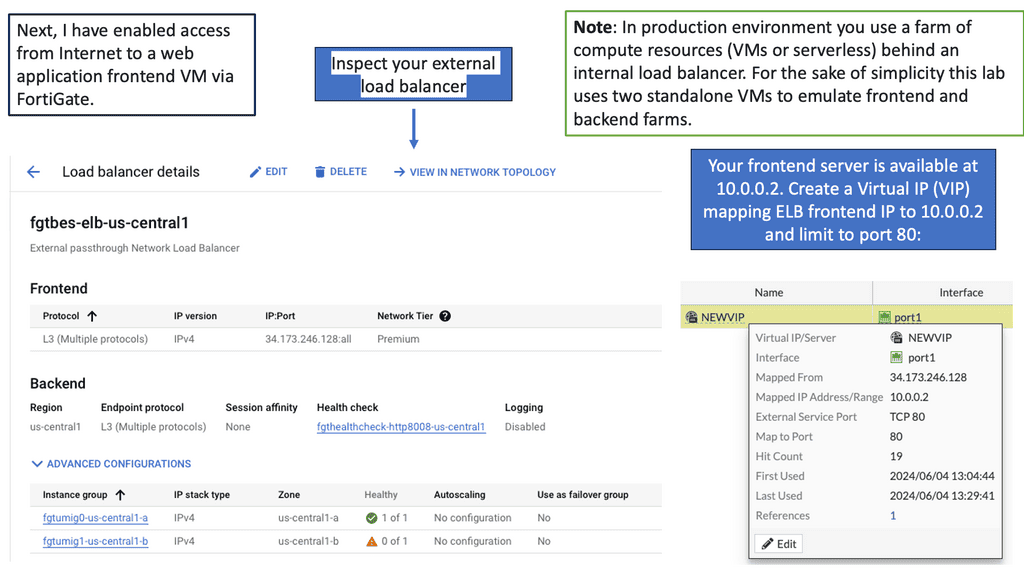
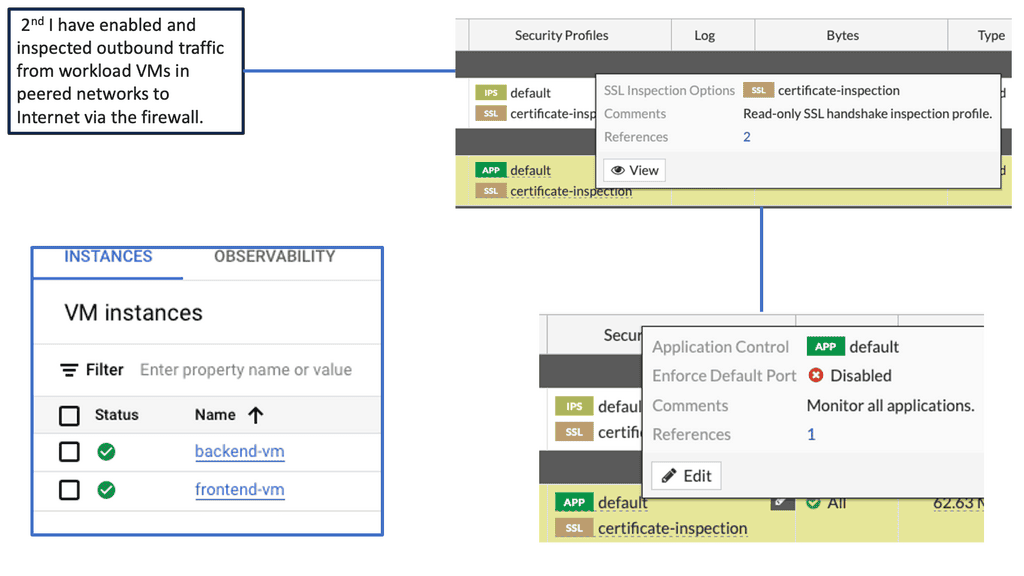
Fortiget Distributed Firewall
The Fortiget distributed firewall is a cutting-edge security solution designed to protect cloud-based infrastructures, including those deployed on Google Cloud. Built upon a distributed architecture, it offers advanced threat intelligence, high-performance traffic inspection, and granular control over network traffic. Its scalable design allows seamless integration with Google Cloud, ensuring comprehensive security across various cloud-based workloads.
Advanced Threat Intelligence: The Fortiget distributed firewall leverages sophisticated threat intelligence capabilities to identify and mitigate potential security risks. It utilizes machine learning algorithms and real-time threat feeds to detect and block malicious activities, providing proactive defense against emerging threats.
High-Performance Traffic Inspection: With its advanced hardware and software components, the Fortiget firewall delivers high-performance traffic inspection, ensuring optimal network performance without compromising security. It efficiently analyzes incoming and outgoing traffic, applying security policies and protocols to mitigate vulnerabilities and unauthorized access attempts.
Granular Control and Policy Enforcement: One of the standout features of the Fortiget distributed firewall is its ability to enforce granular control over network traffic. Administrators can define and enforce policies based on user roles, application types, or specific criteria. This level of control enables organizations to implement strict security measures while maintaining the flexibility required for efficient operations.
Critical Benefits of Distributed Firewalls:
1. Scalability: One of the primary benefits of distributed firewalls is their ability to scale seamlessly with network growth. As new devices and users are added to the network, distributed firewalls can adapt and expand their security capabilities without causing bottlenecks or compromising performance.
2. Enhanced Performance: By distributing security functions across multiple points in the network, distributed firewalls can offload the processing burden from central devices. This improves overall network performance and reduces the risk of latency issues, ensuring a smooth user experience.
3. Improved Resilience: Distributed firewalls offer improved resilience by eliminating single points of failure. In a distributed architecture, even if one firewall node fails, others can continue to provide security services, ensuring uninterrupted protection for the network.
4. Granular Control: Unlike traditional firewalls that rely on a single control point, distributed firewalls allow for more granular control and policy enforcement. Organizations can implement fine-grained access controls by distributing security policies and decision-making across multiple nodes and adapting to rapidly changing network environments.
Use Cases for Distributed Firewalls:
1. Cloud Environments: As organizations increasingly adopt cloud-based infrastructures, distributed firewalls can provide security controls to protect cloud resources. Organizations can secure their cloud workloads by deploying firewall instances close to cloud instances.
2. Distributed Networks: Firewalls are particularly useful in large, geographically dispersed networks. Organizations can effectively ensure consistent security policies and protect their network assets by distributing security capabilities across different branches, data centers, or remote locations.
3. IoT and Edge Computing: With the proliferation of the Internet of Things (IoT) devices and edge computing, the need for security at the network edge has become critical. Distributed firewalls can help secure these distributed environments by providing localized security services and protecting against potential threats.
Example: Linux Firewalling
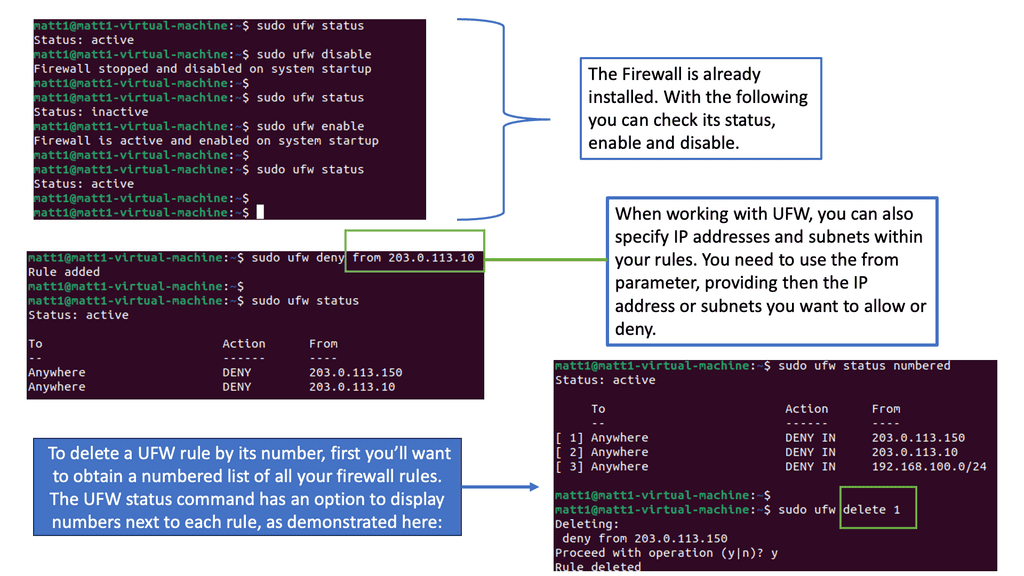
Understanding UFW Firewall
The UFW firewall, designed for ease of use, is a frontend to the iptables firewall that comes pre-installed with most Linux distributions. It provides a user-friendly command-line interface to manage and control incoming and outgoing network traffic. With its intuitive syntax and simplified rule management, even those new to firewalls can grasp its power swiftly.
Effectively configuring the UFW firewall is crucial to unleashing its full potential. This section will delve into the critical aspects of UFW configuration, including allowing and denying specific ports, managing application profiles, and setting up default policies. You can create a robust defense system tailored to your needs by fine-tuning these settings.
Types of Distributed Firewalling
– Network-Based Distributed Firewalling: Network-based distributed firewalling involves placing firewalls at different network entry and exit points. This type of firewalling ensures that all incoming and outgoing traffic undergoes rigorous inspection, preventing unauthorized access and potential threats from entering or leaving the network.
– Host-Based Distributed Firewalling: Host-based distributed firewalling protects individual hosts or endpoints within a network. Each host has a firewall that monitors and filters traffic at the host level. This approach provides granular control and allows for tailored security policies based on each host’s specific requirements.
– Cloud-Based Distributed Firewalling: With the rise of cloud computing, cloud-based distributed firewalling has become increasingly popular. This approach involves deploying firewalls within cloud environments, securing both on-premises and cloud-based resources. Cloud-based distributed firewalling offers scalability, flexibility, and centralized management, making it an ideal choice for organizations with hybrid or multi-cloud infrastructures.
To better comprehend distributed firewalling, we must familiarize ourselves with its key components. These components include:
1. Distributed Firewall Controllers: These centralized entities manage and orchestrate the entire firewalling infrastructure. They handle policy enforcement, traffic monitoring, and threat detection across the network.
2. Firewall Agents are lightweight software modules installed on individual network devices such as switches, routers, and endpoints. They function as the first line of defense within their respective network segments, enforcing security policies and filtering traffic.
3. Centralized Management Interface: This user-friendly interface allows administrators to configure and manage the distributed firewalling components efficiently. It provides a centralized network view, enabling seamless policy enforcement and threat mitigation.
**Zero Trust and Firewalling**
Network security is traditionally divided into zones contained by one or more firewalls. A trust level is assigned to each zone, determining what network resources it can access. This model provides a very strong, in-depth defense. An exclusion zone (often called a “DMZ”) is set up where traffic can be tightly monitored and controlled for resources considered to be more vulnerable, such as web servers that expose themselves to the public Internet.
Generally, firewalls are configured to control traffic on a deny-by-default/allow-by-exception basis. The firewall does not allow anything to pass simply because it is on the network (or is attempting to reach the network). The firewall requires all traffic to meet a set of requirements to proceed.
Recap: Basics of Firewalls
Firewalls are differentiated in different ways, from the network size they are designed to work to how they protect critical assets. They can range from simple packet filters to stateful packet filters to application proxies. The most typical firewall concept is a dedicated system or appliance that sits in the network and segments an “internal” network from the “external” Internet.
However, the Internet and external perimeters are not as distinguishable as they were in the past. Most home or SOHO networks use an appliance-based broadband connectivity device with a built-in firewall.
- Controlling Traffic
You control which traffic passes through firewalls and which traffic is blocked as a network administrator or information security officer. In addition to ingress and egress filtering, you can determine whether filtering occurs on inbound or outbound traffic. It is usual for an organization to filter inbound traffic, as many threats are outside the network. It is also essential to filter outbound traffic, as sensitive data and company secrets may be sent outside the network.
- The Role of Abstraction
When considering distributed firewalls, let’s start with the basics. Virtual computing changes the compute operational landscape by introducing a software abstraction layer. All physical compute components (NICs, CPU, etc.) are bundled into software and managed as software objects, not as individual physical components.
Virtualization offers many benefits in agility and automation, but static provisioning of network functions hinders its full capabilities. Server virtualization allows administrators to spin up a VM in seconds (Containers—250ms), yet it potentially takes weeks to provision the physical network to support the new VM. The compute and network worlds lack any symmetry.
- Network Virtualization
However, their combined service integration is vital to supporting the application stack. Network virtualization creates a similar abstraction layer to what we see in the computing world. It keeps the network in line with computing regarding agility and automation. Network services, including Layer 2 switching, Layer 3 routing, load balancing, and firewalling, are now available in software, enabling distributed firewalls. Moving physical to software changes the operational landscape of networking to match that of computing.
Both compute and network are now decoupled from the physical hardware, meaning they can be provisioned simultaneously. These architectural changes form the basis for the zero-trust networking design.
For additional pre-information, you may find the following helpful:
Distributed Firewalls
Initially, we abstracted network services with the vSwitch installed on the hypervisor. It was fundamental, and it could only provide simple network services. There was no load balancing or firewalling. With recent network virtualization techniques, we introduce many more network services into the software. One essential service enabled by network virtualization is distributed firewalls.
The distributed model offers a distributed data plane with central programmability. Rules get applied via a central entity, so there is no need to configure the vNIC individually. The vNIC may have specific rule sets, but all the programming is done centrally.
VM mobility is minimal if you can’t move the network state with it. Distributing the firewalling function allows the firewall state and stateful inspection firewall ( connections, rule tables, etc.) to move with the VM. Firewalls are now equally mobile. Something 10 years ago I thought I would never see. As a side note, docker containers do not move as VMs do. They usually get restarted very quickly with a new IP address. What is a feature of distributed firewalls?
Distributed firewalls – Spreading across the hypervisor
1- ) When considering a feature of distributed firewalls, let’s first discuss that traditional security paradigms are based on a centrally focused design. A centrally positioned firewall device, usually placed on a DMZ, intercepts traffic. It consists of a firewall physically connected to the core, and traffic gets routed from access to the core with manual configuration.
2 – ) There is no agility. We had many firewalls deployed per application, but nothing targeted east-to-west traffic. As you are probably aware, the advent of server virtualization meant there was more east-to-west traffic than north-to-south traffic. Traffic stays in the data center, so we need an optimal design to inspect it thoroughly.
3 – ) Protecting the application is critical, but the solution should also support automation and agility. Physical firewalls lack any agility. They can’t be moved. If a VM moves from one location to another, the state in the original firewall does not move with the VM. They were resulting in traffic tromboning for egress traffic.
4 – ) exist to circumvent this, but they complicate network operations. Stretched HA firewall designs across two data centers are not recommended, as a DCI failure will break both data centers. Proper application architecture and DNS-based load balancing should fix efficient ingress traffic.
A world of multi-tenancy
We are in multi-tenancy, and physical devices are not ideal for multi-tenant environments. Most physical firewalls offer multiple contexts, but the code is still shared. To properly support multi-tenant cloud environments, we need devices built initially in mind to support multi-tenant environments. Physical devices were never built to support cloud environments. They evolved to do this with VRFs and contexts.
We then moved on to firewall appliances in VM format, known as virtual firewalls. They offer slightly better agility but still suffer traffic tromboning and a potential network chokepoint. Examples of VM-based firewalls include vShield App, vASA, and vSRX Gateway. There is only so much you can push into software.
Generally, you can get up to 5 Gbps with a reduced feature set. I believe Paolo Alto can push up to 10 Gbps. Check the feature parity between the VM and the corresponding physical device.
Network Security Components
a ) Network Evolution now offers distributed network services among hypervisors. The firewalling function takes a different construct and is a service embedded in the hypervisor kernel network stack. All hypervisors become one big firewall in software. There is no more extended single device to manage, and we have a new firewall-as-a-service landscape.
b ) Distributing firewalling offers a very scalable model. Firewall capacity is expanded, and different hypervisors are added to provide a scale-out distributed kernel data plane.
c ) So, what is a feature of distributed firewalls? Well, scale comes to mind. They are distributed firewalls, and their performance scales horizontally as more hosts are added. Distributed firewalling is similar to connecting every VM directly to a separate firewall port, which is an ideal situation but impossible in the physical world.
d ) Now that the VM has a direct firewall port, there is no traffic tromboning or network choke points. All VM ingress and egress traffic is inspected statefully at the source and destination, not at a central point in the network. This has many benefits, especially with the security classification.
Distributed Firewalls: Decoupled from IP addressing
In the traditional world, security classification was based on IP address and port number. For example, we would create a rule that source IP address X can speak to destination IP address Y on port 80. We used IP as a security mechanism because the host did not have a direct port mapping to the firewall. The firewall used an IP address as the identifier to depict where traffic is sourced and destined.
This is no longer the case with distributed firewalls. Security rules are entirely decoupled from IP addresses. A direct port mapping from the VM to the kernel-based firewall permits the classification of traffic based on any arbitrary type of metadata: objects, tagging, OS type, or even detection of a specific type of virus/malware.
Many companies offer distributed firewalling; VMware with NSX is one of them, and it has released a VMware NSX trial allowing you to test for yourself. NSX offers Layer 2 to Layer 4 stateful services using a distributed firewall running in the ESXi hypervisor kernel.
First, the distributed firewall is installed in the kernel by deploying the kernel VIB – VMware Internetwork Service. Then, NSX Manager installs the package via ESX Agency Manager (EAM).
Then, the VIB is initiated, and the vsfwd daemon is automatically started in the hypervisor’s user space.
Each vNIC is associated with the distributed firewall. As mentioned, we have a one-to-one port mapping between vNICs and firewalls. Rules are applied to the VM; the enforcement point is the VM virtual NIC—vNIC. The NSX manager sends rules to the vsfwd user world process over the Advanced Message Queuing Protocol message bus.
Closing Points on Distributed Firewalling
A distributed firewall is a security mechanism that decentralizes the traditional firewall’s functionality by distributing its policies and enforcement points across various locations within the network. Unlike conventional firewalls, which operate at the network’s perimeter, distributed firewalls provide security at multiple points, including endpoints, servers, and cloud environments. This approach ensures a more comprehensive and adaptable security framework, capable of handling the dynamic nature of contemporary networks.
One of the primary benefits of distributed firewalls is their ability to offer granular control over network traffic. By implementing security policies closer to the data source, they can effectively manage and filter traffic based on specific needs and contexts. Additionally, distributed firewalls enhance network performance by reducing bottlenecks often associated with centralized firewalls. This scalability is particularly beneficial for organizations with complex, multi-cloud, or hybrid environments, as it allows for seamless integration across different platforms.
When adopting distributed firewalling, organizations must consider several factors to ensure successful implementation. First, it’s crucial to have a comprehensive understanding of the network architecture and the specific security requirements of each segment. This knowledge will help in designing appropriate policies and enforcement strategies. Additionally, organizations should invest in robust management tools that provide visibility and control over the distributed firewall infrastructure, enabling them to monitor and respond to threats in real time.
While distributed firewalls offer numerous advantages, they also present certain challenges. Managing multiple enforcement points can be complex, requiring sophisticated coordination and policy management. To address these challenges, organizations can leverage automation and machine learning technologies to streamline policy updates and threat detection processes. Furthermore, ongoing training and awareness programs are essential to ensure that IT teams are equipped to manage and optimize distributed firewall systems effectively.
Summary: Distributed Firewalls
In today’s interconnected world, network security is of utmost importance. With increasing cyber threats, organizations are constantly seeking innovative solutions to protect their networks. One such solution that has gained significant attention is distributed firewalling. In this blog post, we explored the concept of distributed firewalling and its benefits in enhancing network security.
Understanding Distributed Firewalling
Distributed firewalling is a network security approach that involves the deployment of multiple firewalls throughout a network infrastructure. Unlike traditional centralized firewalls, distributed firewalls are strategically placed at different points within the network, providing enhanced protection against threats and malicious activities. Organizations can achieve improved security, performance, and scalability by distributing the firewall functionality.
Benefits of Distributed Firewalling
a) Enhanced Threat Detection and Prevention:
Distributed firewalls offer increased visibility into network traffic, enabling early detection and prevention of threats. By deploying firewalls closer to the source and destination of traffic, suspicious activities can be identified and blocked in real time, reducing the risk of successful cyber attacks.
b) Reduced Network Congestion:
Traditional centralized firewalls can bottleneck in high-traffic environments, leading to network congestion and performance issues. With distributed firewalling, the load is distributed across multiple firewalls, ensuring efficient traffic flow and minimizing network latency.
c) Scalability and Flexibility:
As organizations grow, their network infrastructure needs to scale accordingly. Distributed firewalling provides the flexibility to add or remove firewalls per evolving network requirements. This scalability ensures that network security remains robust and adaptable to changing business needs.
Implementation Considerations
Before implementing distributed firewalling, organizations should consider the following factors:
a) Network Architecture: Analyzing the existing network architecture is crucial to determining the optimal placement of distributed firewalls. Identifying critical network segments and data flows will help design an effective distributed firewalling strategy.
b) Firewall Management: Managing multiple firewalls can be challenging. Organizations must invest in centralized management solutions that provide a unified view of distributed firewalls, simplifying configuration, monitoring, and policy enforcement.
c) Security Policy Design: A comprehensive security policy ensures consistent protection across all distributed firewalls. The policy should align with organizational security requirements and industry best practices.
Conclusion:
Distributed firewalling is a powerful approach to network security, offering enhanced threat detection, reduced network congestion, and scalability. By strategically distributing firewalls throughout the network infrastructure, organizations can bolster their defenses against cyber threats. As the digital landscape continues to evolve, investing in distributed firewalling is a proactive step towards safeguarding valuable data and maintaining a secure network environment.
- DMVPN - May 20, 2023
- Computer Networking: Building a Strong Foundation for Success - April 7, 2023
- eBOOK – SASE Capabilities - April 6, 2023