DDoS Attacks
In today's digital age, cyber threats have become increasingly sophisticated, posing a significant challenge to individuals and organizations. One such malevolent force that has gained notoriety is Distributed Denial of Service (DDoS) attacks. In this blog post, we will delve into the world of DDoS attacks, uncovering their inner workings, motives, and the devastating impact they can have on their victims.
DDoS attacks are orchestrated attempts to overwhelm a target system or network with a flood of traffic, rendering it inaccessible to legitimate users. These attacks involve multiple compromised devices, forming a botnet army, which is controlled by a malicious entity. By harnessing the combined bandwidth of these devices, the attacker can launch a massive assault that cripples the target's online presence.
DDoS attacks can be motivated by various factors. Hacktivism, where attackers aim to make a political or social statement, is one such motive. Cybercriminals may also carry out DDoS attacks as a smokescreen to divert attention from other malicious activities, such as data breaches or theft. Additionally, in some instances, competitors or disgruntled individuals may resort to DDoS attacks to gain a competitive advantage or exact revenge.
DDoS attacks utilize a range of techniques to overwhelm targeted systems. One commonly employed method is the "volumetric attack," which floods the target with an enormous volume of traffic, exceeding its capacity to handle requests. Another technique is the "application layer attack," where the attacker targets specific vulnerabilities in the application layer, exhausting server resources and causing service disruptions. Furthermore, "amplification attacks" exploit the vulnerabilities of certain protocols or services to amplify the volume of traffic directed at the target.
Given the severity of DDoS attacks, it is crucial for individuals and organizations to implement robust mitigation strategies. Proactive measures involve employing traffic filtering mechanisms, such as firewalls or intrusion prevention systems, to identify and block malicious traffic. Content Delivery Networks (CDNs) can also help mitigate attacks by distributing traffic across multiple servers, reducing the impact of an attack on any single server.
As technology evolves, so do the methods employed by attackers. The future of DDoS attacks holds the potential for more sophisticated techniques, including the utilization of artificial intelligence and the Internet of Things (IoT) devices as botnet components. This calls for enhanced security measures, industry collaboration, and continuous research to stay one step ahead of the attackers.
DDoS attacks present a significant threat to the digital landscape, capable of disrupting businesses, causing financial losses, and compromising user trust. Understanding the inner workings of these attacks, their motives, and implementing effective mitigation strategies are vital in safeguarding against this insidious menace. By staying informed and proactive, we can collectively build a safer and more resilient online ecosystem.
Matt Conran
Highlights: DDoS Attacks
Understanding DDoS Attacks
DDoS attacks are orchestrated attempts to overwhelm a target system, network, or website with an overwhelming amount of traffic. By flooding the target with an unmanageable influx of requests, DDoS attacks render the system inaccessible to legitimate users. The motives behind these attacks can vary, ranging from hacktivism and revenge to financial gain or even political sabotage.
To execute a DDoS attack, perpetrators typically harness a botnet—an army of compromised computers or devices under their control. These compromised machines, often referred to as “zombies,” are used to generate a massive volume of traffic towards the target. The attack may exploit vulnerabilities in network protocols, application layers, or even the target’s bandwidth capacity. With the combined firepower of the botnet, the target’s resources are overwhelmed, resulting in service disruption.
The Ramifications of DDoS Attacks
1: The implications of a successful DDoS attack can be severe. Businesses may experience significant financial losses due to prolonged service downtime, tarnished reputation, and potential legal consequences. Moreover, the psychological impact on users who rely on the targeted services can lead to a loss of trust and confidence in the affected organization. The fallout from DDoS attacks extends beyond immediate damages, making it crucial to be prepared and proactive in safeguarding against such threats.
2: Mitigating the risks associated with DDoS attacks requires a multi-layered approach. Implementing robust network security measures, such as firewalls and intrusion detection systems, can help identify and filter out suspicious traffic.
3: Employing content delivery networks (CDNs) can distribute the load and provide additional protection. Utilizing traffic monitoring and anomaly detection tools can aid in early detection and response to potential attacks. Additionally, collaborating with internet service providers (ISPs) and implementing rate limiting measures can help mitigate the impact of an attack.
**DDoS Attacks**
The underlying mechanism of software or infrastructure does not need to be understood to carry out a successful DDoS attack. Some of the more successful attacks have been carried out by industry outsiders who understand the architecture.
The attacker must control many administrated sources for the attack to be complex. With everyone carrying a smartphone in their pocket, living in a home with embedded computers, and traveling in self-driving cars with supercomputers for brains, it is not hard to imagine such hosts.
What is a DDoS Attack?
At its core, a DDoS attack aims to overwhelm a target server or network with an enormous volume of traffic, rendering it unable to handle legitimate requests. Attackers achieve this by harnessing a compromised computer network, forming a botnet, and directing it towards the target. The motive behind such attacks can vary, including extortion, revenge, or malicious intent.
There are several types of DDoS attacks, each with its unique characteristics. Some common variations include:
1. Volume-Based Attacks: These attacks flood the target with massive traffic, consuming all available bandwidth and resources.
2. Protocol Attacks: Instead of targeting the target’s bandwidth, protocol attacks exploit vulnerabilities in network protocols (e.g., TCP/IP) to exhaust server resources or disrupt communication.
3. Application Layer Attacks: These attacks target web applications or services, overwhelming them with requests until they become unresponsive.
Key Considerations on DDoS Attacks:
In DoS attacks, the attacker disrupts the services of a host connected to a network to make the host or resource unavailable to its intended users. To achieve denial of service, extra requests are flooded onto a targeted machine or resource to overload it and prevent some or all legitimate requests from being fulfilled. Various attacks can slow down a server, including flooding it with millions of requests, overloading it with invalid data, and sending requests from an illegitimate IP address.
Distributed denial-of-service attacks (DDoS attacks) flood the victim with traffic from many sources. Managing this type of attack requires more sophisticated strategies, as blocking one source is insufficient. The effects of a DDoS attack are similar to crowding the entrance of a business, disrupting trade, and causing the company to lose money. DoS attacks are often perpetrated against high-profile web servers, including banks and payment gateways. Motives for these attacks include revenge, blackmail, or hacktivism.
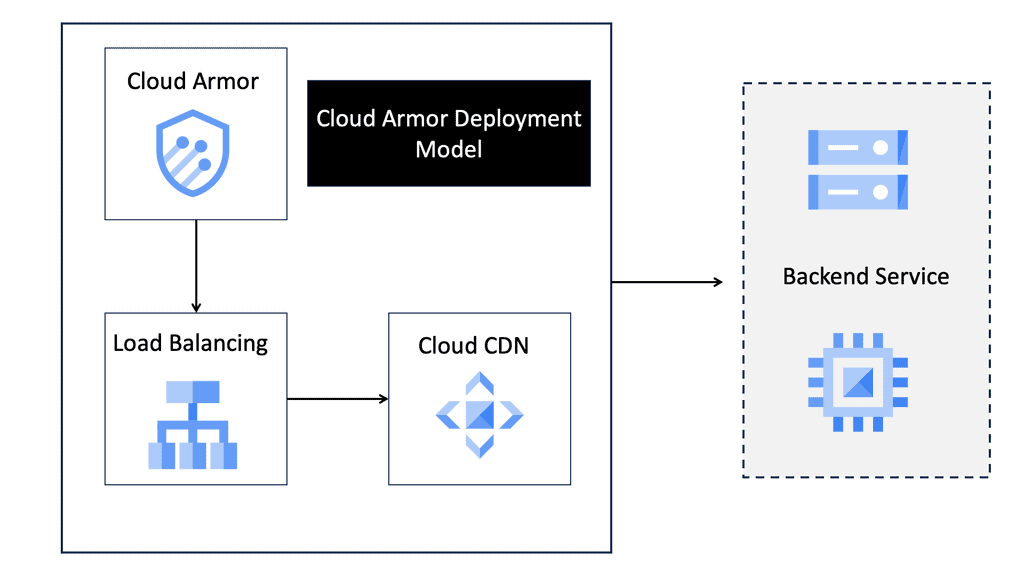
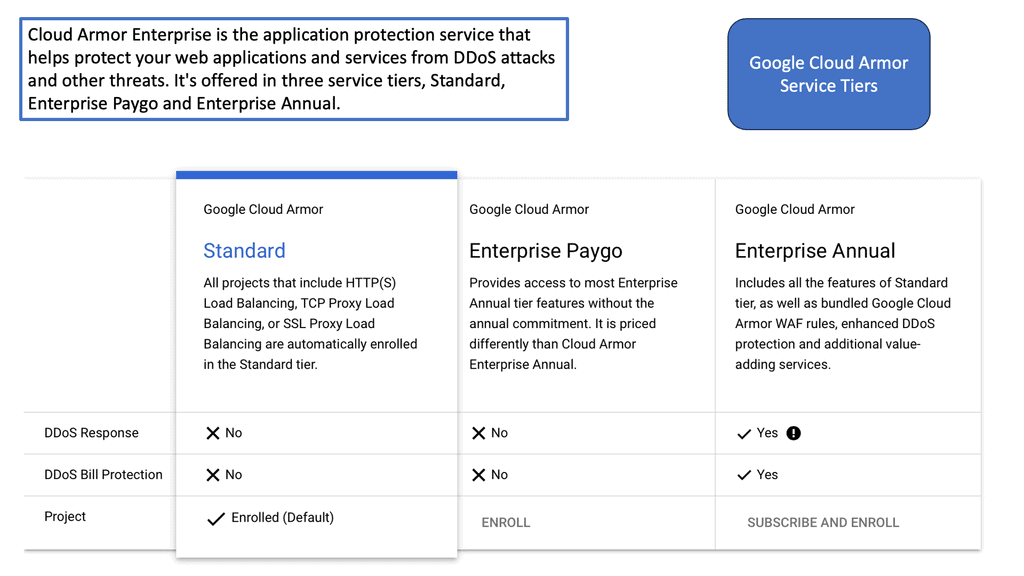
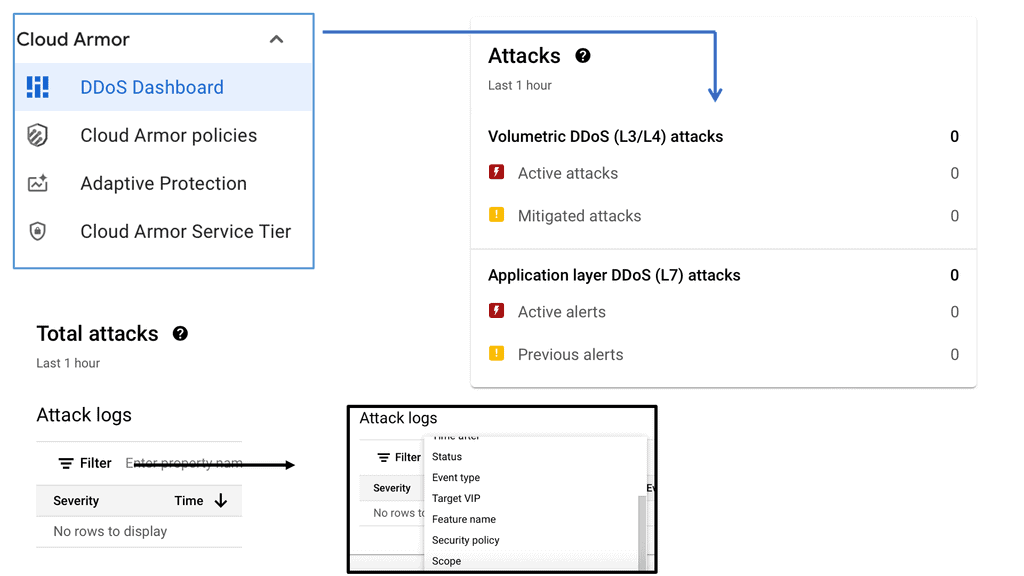
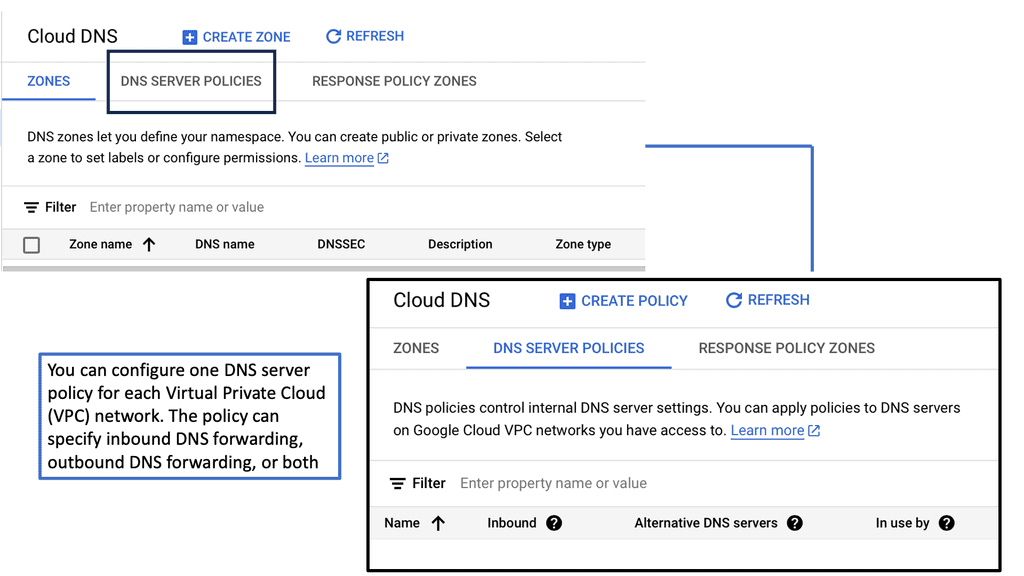
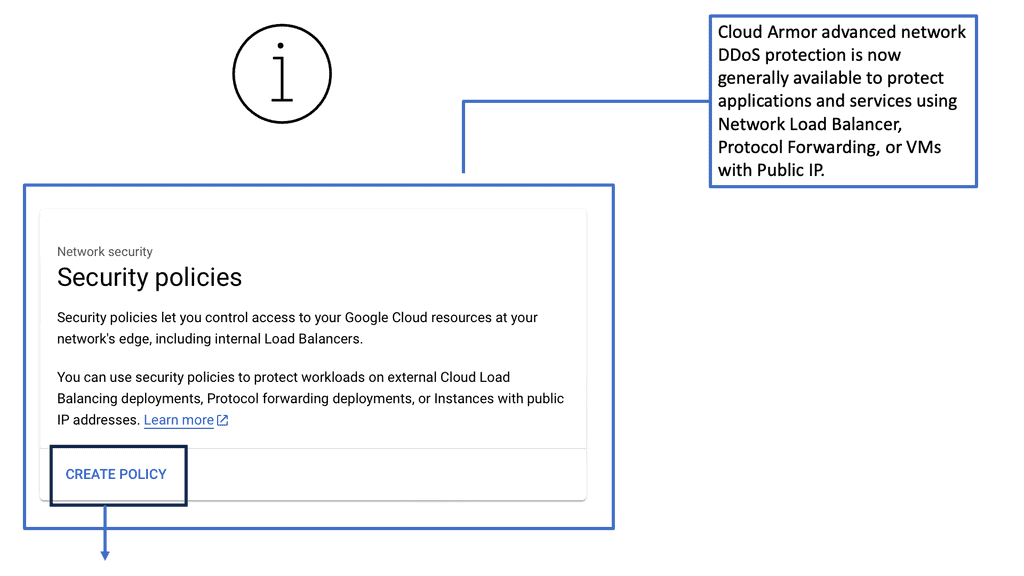
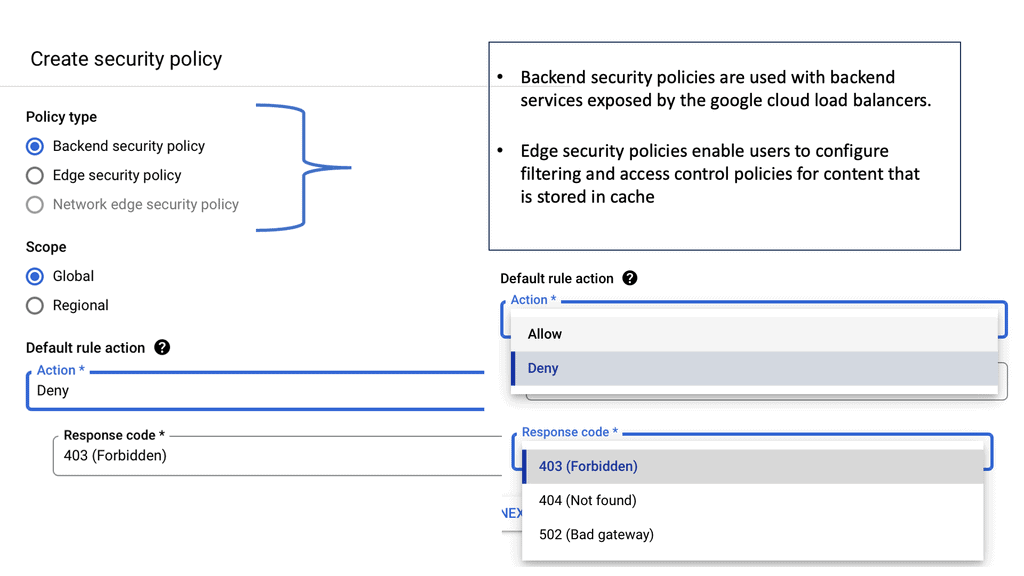
Cloud Armor DoS Protection
### What is Cloud Armor?
Cloud Armor is a security service designed to protect applications and websites from harmful internet traffic. Leveraging the power of global cloud infrastructure, Cloud Armor provides scalable and reliable defense mechanisms against DDoS attacks. It acts as a shield, filtering out malicious traffic while allowing legitimate users to access the services they need. With its ability to scale according to the size and scope of an attack, Cloud Armor ensures that your digital assets remain safe and operational.
### Key Features of Cloud Armor
Cloud Armor boasts several features that make it an essential tool for DDoS protection. Firstly, its global reach allows it to detect and mitigate threats from any part of the world, offering comprehensive protection. Additionally, Cloud Armor’s intelligent algorithms can differentiate between normal and malicious traffic, ensuring that genuine users experience no disruption. Another significant feature is its real-time monitoring and reporting capabilities, which provide insights into attack patterns and help in fine-tuning security strategies.
### How Cloud Armor Enhances Security
Beyond its primary role in DDoS mitigation, Cloud Armor also enhances overall security through its integration with other security services. By working in tandem with firewalls and intrusion detection systems, Cloud Armor creates a multi-layered defense strategy that is harder for attackers to penetrate. This holistic approach not only safeguards against DDoS attacks but also protects against other types of cyber threats, ensuring a robust security posture.
### Implementing Cloud Armor in Your Organization
Integrating Cloud Armor into your organization’s security framework is a strategic move towards ensuring digital resilience. The process begins with an assessment of your current infrastructure to identify vulnerabilities and determine the level of protection needed. Once implemented, Cloud Armor’s customizable rules and policies allow you to tailor its functionalities to suit your specific needs. Regular updates and security audits will help in maintaining optimal performance and protection levels.
 Example Yo-yo attack
Example Yo-yo attack
A yo-yo attack is a DoS/DDoS targeting cloud-hosted applications using autoscaling. An attacker generates a flood of traffic until a cloud-hosted service can handle the increase in traffic, then stops the attack, leaving the victim with overprovisioned resources. The attack resumes when the victim scales down again, causing resources to be rescaled. As a result, the quality of service may be reduced during scaling up and down, and over-provisioning can drain resources. However, an attacker will pay a lower cost than a typical DDoS attack since it only needs to generate traffic for a portion of the attack period.
Popular DDOS Attacking Tools
1. LOIC (Low Orbit Ion Cannon): LOIC is a widely known DDOS attacking tool that enables users to flood a target with traffic, often rendering it inaccessible. Its simplicity and accessibility have made it a popular choice among inexperienced attackers.
2. HOIC (High Orbit Ion Cannon): HOIC is an upgraded LOIC version capable of launching more powerful attacks. It utilizes a decentralized approach, making it harder to trace the source of the attack.
3. Slowloris: Unlike traditional flood attacks, Slowloris takes a stealthy approach. It sends partial HTTP requests to the target server, gradually consuming its resources until it becomes overwhelmed and unresponsive.
#### Botnets – The Army of Attackers
Botnets represent a more sophisticated and dangerous form of DDoS attack. By hijacking thousands of vulnerable devices, attackers create a network capable of executing massive DDoS campaigns. Tools like Mirai have demonstrated the destructive power of botnets, bringing down major websites and services. Defending against botnets requires robust security measures and constant vigilance.
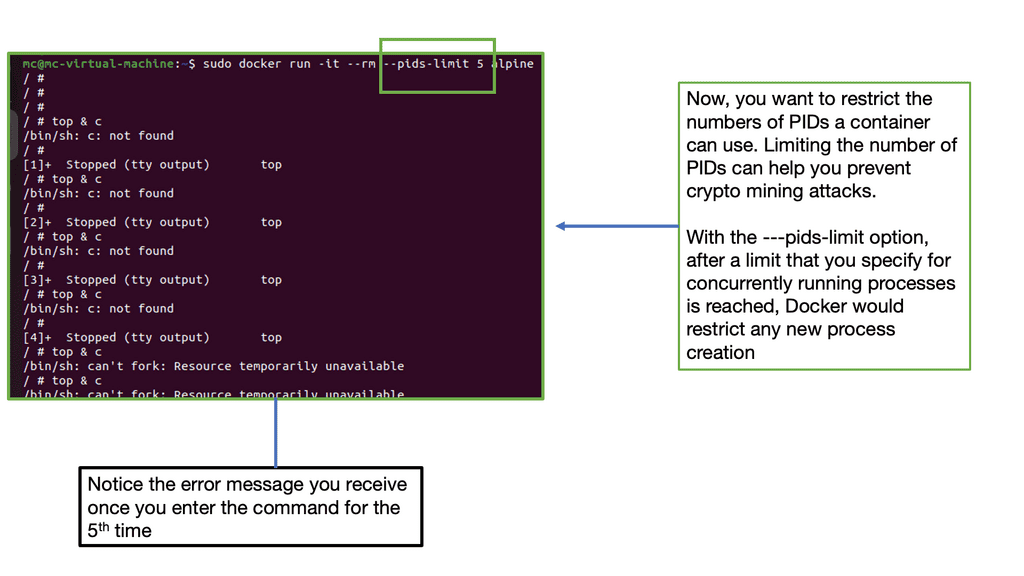
Protecting Docker Containers
Understanding Docker Images
Docker Images are the building blocks of Docker containers. They contain everything needed to run software, including the code, runtime, system tools, libraries, etc. Using Docker Images, developers can ensure consistency, portability, and efficiency across different environments.
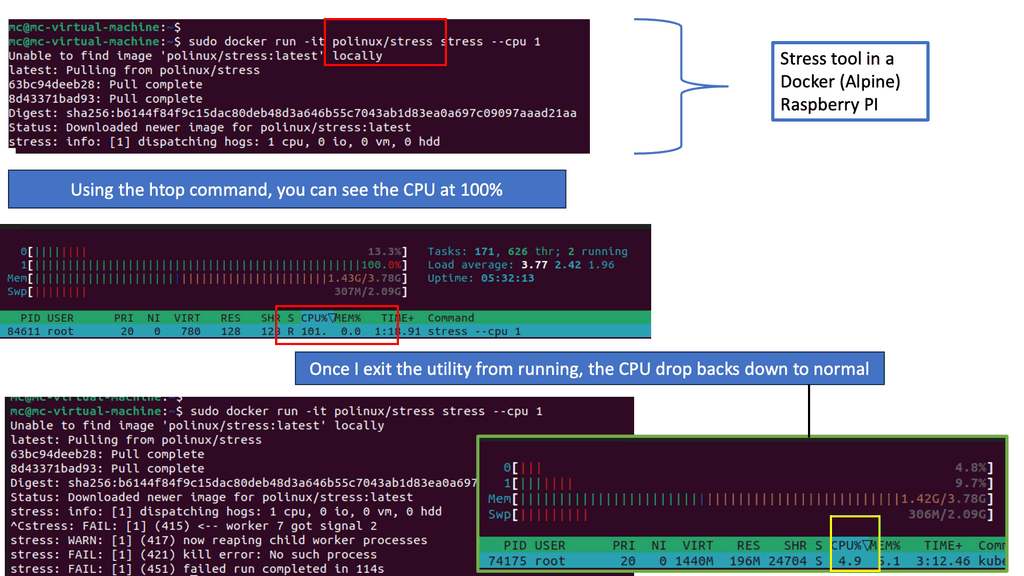
The Stress tool is a powerful utility that allows developers to simulate high-stress scenarios and measure the performance and reliability of their systems. It can generate high CPU, memory, I/O, or network loads, helping identify potential bottlenecks and areas for improvement. By combining Docker Images with the Stress tool, developers can create controlled testing environments that resemble real-world usage scenarios.
DDoS Mitigation
It is already well known that a DDoS attack can have catastrophic effects on your service, business, and infrastructure.
Even though macro and micro behavior can detect an attack, we need to get down to the nitty-gritty of the attack to devise a mitigation strategy. Mitigation strategies must be tailored to the attack you are experiencing, just as doctors prescribe precise medication based on symptoms. For example, a payload filter that stops HTTP GET floods cannot stop TCP SYN floods.
As a general rule, DDoS attacks rely on the same type of exploit repeated several times. An example of a TCP SYN Flood attack is when a packet, TCP SYN, is repeated from different sources repeatedly and reaches your network. The volumetric and differentiation aspects of the attack present the biggest challenge to mitigating it. Using a very high traffic rate, the mitigation distinguishes the legitimate request (in this instance, TCP SYN) from the malicious request.
**Identifying the Warning Signs**
One of the most crucial steps in DDoS mitigation is early detection. Recognizing the warning signs can make a significant difference in your response strategy. Common indicators include unusual slow network performance, unavailability of a particular website, or an increase in spam emails. By setting up alerts for unusual traffic patterns and regularly monitoring network activity, businesses can identify potential DDoS threats before they escalate.
**Implementing Robust Defense Mechanisms**
Once a potential threat has been identified, implementing a robust defense mechanism is essential. A multi-layered approach is often the most effective strategy. This includes deploying firewalls, intrusion detection systems, and anti-DDoS hardware and software solutions. Additionally, working with a DDoS mitigation service provider can offer specialized expertise and resources that are tailored to your specific needs. These providers use advanced technologies and methodologies to filter out malicious traffic and ensure legitimate traffic can reach its destination.
**Developing a Response Plan**
Having an established response plan is a critical component of any DDoS mitigation strategy. This plan should outline the steps to be taken in the event of an attack, including communication protocols, roles and responsibilities, and escalation procedures. Regularly updating and testing this plan ensures that all team members are prepared and can respond quickly and efficiently. A well-developed response plan can minimize downtime and help maintain customer trust and business continuity.
**A mechanism for distraction**
DDoS attacks are deliberate attempts to make resources unavailable for their intended use. They are like lightning and are very common in today’s internet landscape, having a wide range of adverse effects on public, private, and small businesses. A DDoS goal is to draw systems, bandwidth, or human resources and block service from legitimate connections. They are commonly not isolated events and are often implemented to facilitate a more significant sophisticated attack. In addition, they can be used as a mechanism for distraction.
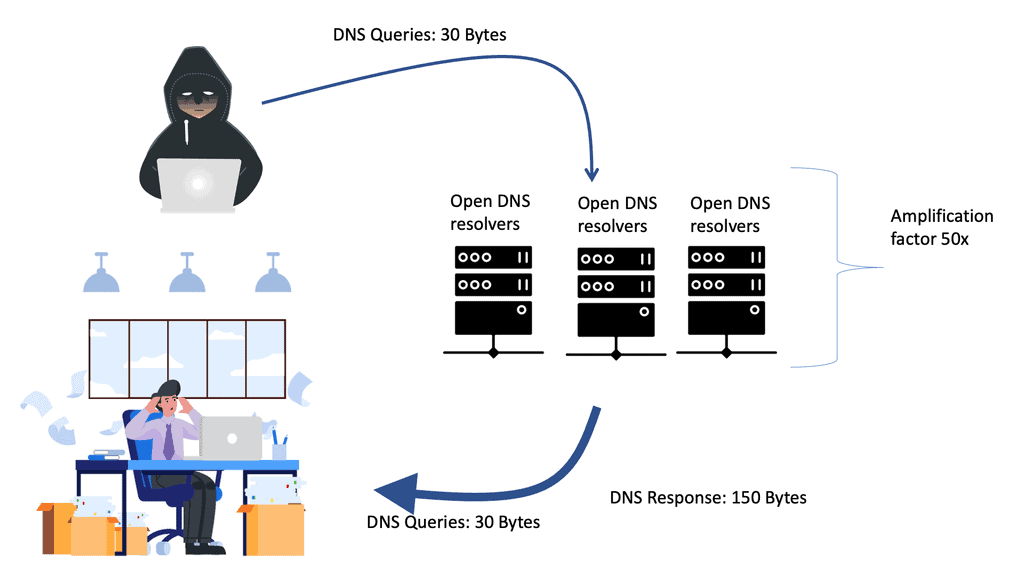
Example: NTP Reflection Attack
For example, a large UDP flood combined with a slow HTTP GET flood. Internet history’s most significant denial of service event was an NTP reflection DDoS attack that peaked at 400Gbps. Now, we have a range of new IPv6 DDoS attacks to circumvent. Opening up a range of IPv6 attacks, some targeting IPv6 host exposure.
For additional information, you may find the following posts helpful:
DDoS Attacks
DNS Security
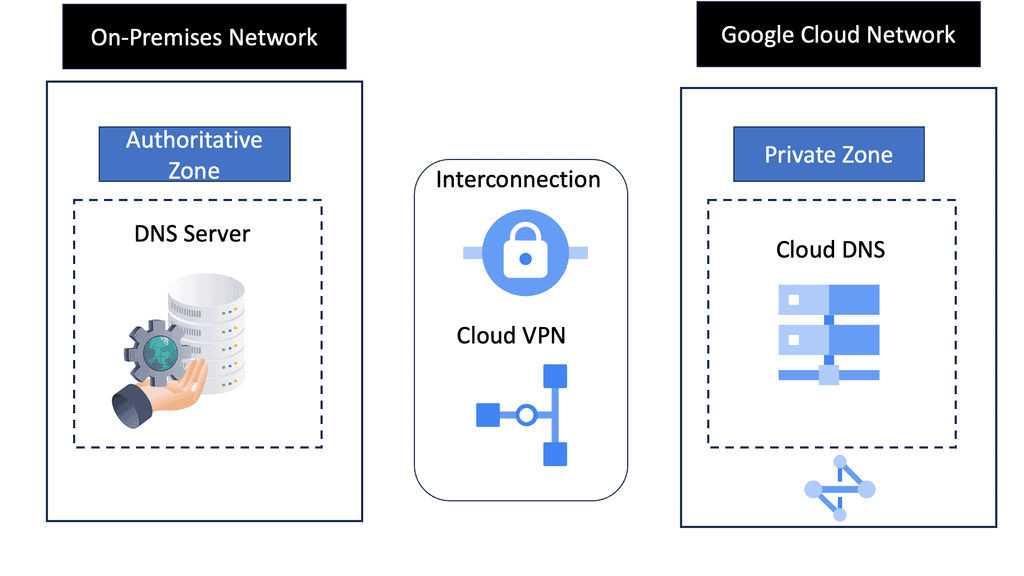
### The Role of DNS Security
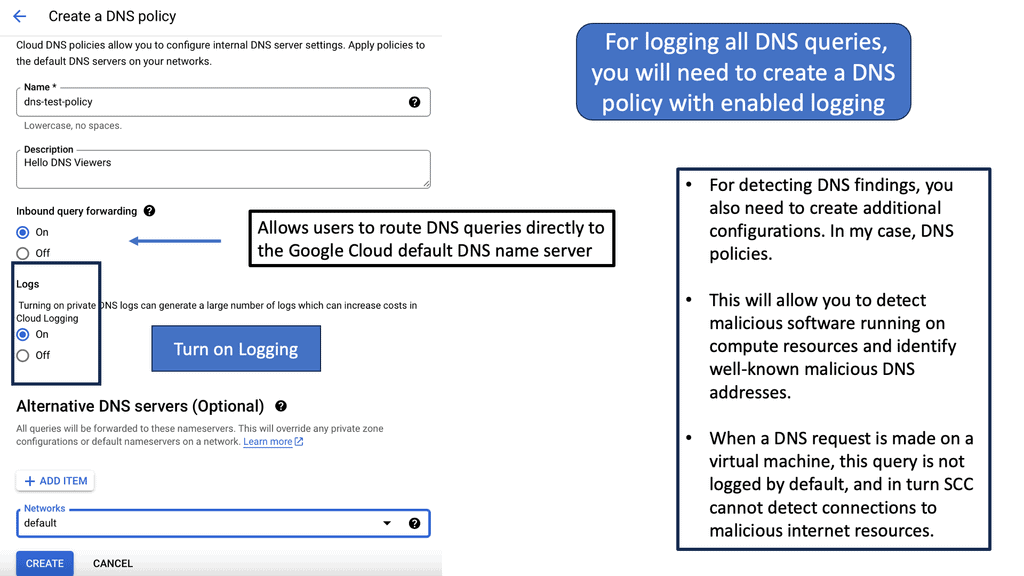
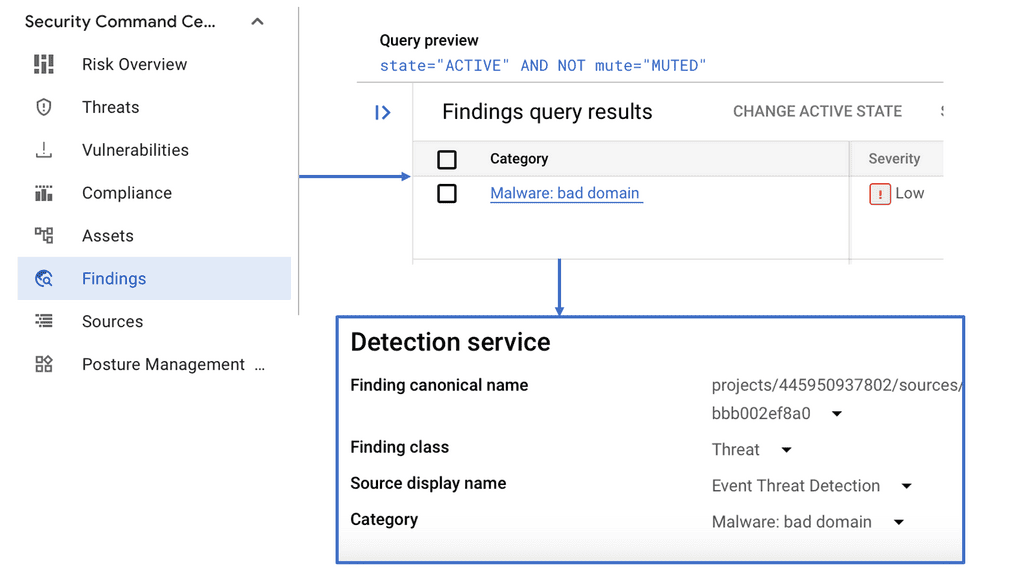
DNS Security forms a cornerstone of the Security Command Center’s offerings. As one of the primary protocols that keep the internet functioning seamlessly, the Domain Name System (DNS) is a frequent target for cybercriminals. From cache poisoning to DNS tunneling, the threats are diverse and evolving. The SCC employs advanced DNS security measures to detect and neutralize these threats, ensuring your domain’s integrity and availability remain uncompromised. By leveraging these capabilities, businesses can protect sensitive data and maintain the trust of their users.
### Leveraging Google Cloud for Enhanced Protection
Google Cloud’s integration with the Security Command Center enhances its utility manifold. This synergy offers unparalleled insights and control over cloud resources, ensuring that security is not just an afterthought but an integral part of the cloud strategy. With Google Cloud’s advanced analytics and threat intelligence, the SCC can identify vulnerabilities across various layers of infrastructure. This integration also facilitates automated responses to incidents, minimizing downtime and potential damage.
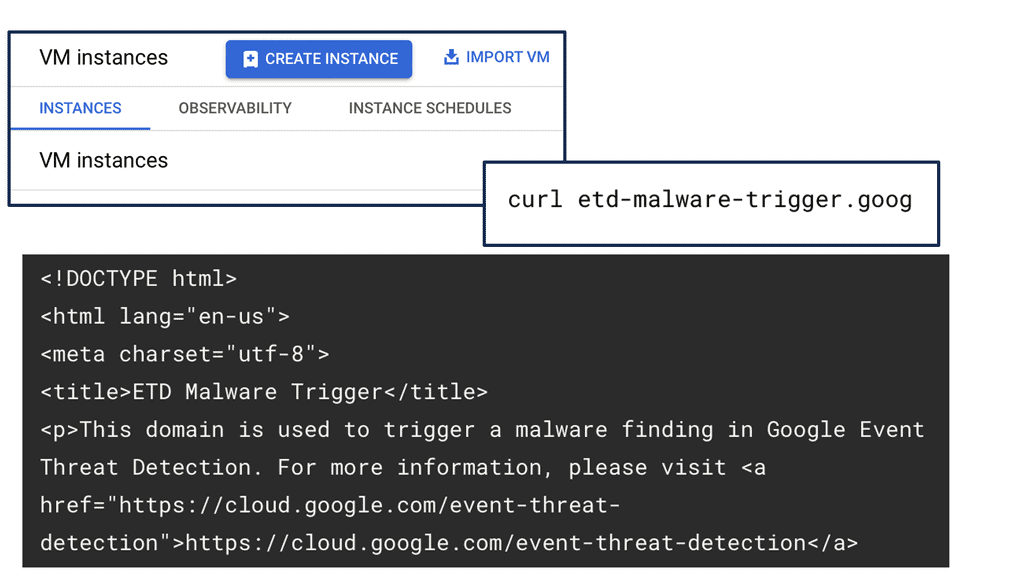
### Defending Against DDoS Attacks
DDoS (Distributed Denial of Service) attacks remain a persistent threat to online services. These attacks can cripple a network by overwhelming it with traffic, leading to significant downtime and financial losses. The Security Command Center provides robust defenses against such threats by monitoring traffic patterns and deploying countermeasures in real-time. By utilizing machine learning algorithms, the SCC can differentiate between legitimate traffic and potential DDoS attempts, ensuring continuous availability of services.
DDoS attacks have existed for almost as long as the web has existed. Unfortunately, they remain one of the most effective ways to disrupt online services. The most common DDoS attack is to congest your network, which can be performed in several ways. This congestion can happen at your internet egress or another network bottleneck.
The pre-mitigation step against these flooding scenarios demands that you understand your current capacities. These can be your bandwidth capacity and packets-per-second capabilities. This information will be matched to the flood level you are observing; at this point, you need to initiate the different mitigation tools you have at your disposal.
Types of DDOS Attacks:
1. Volume-based attacks aim to saturate the target’s network or server capacity by flooding it with massive traffic. Standard techniques used in volume-based attacks include ICMP floods, UDP floods, and amplification attacks.
2. Application-layer attacks exploit vulnerabilities in the target’s web applications or services. By sending many seemingly legitimate requests, the attacker aims to exhaust the target’s resources, rendering it unable to serve genuine users. Examples of application-layer attacks include HTTP floods and Slowloris attacks.
3. Protocol attacks: These attacks exploit vulnerabilities in network protocols to overwhelm the target’s resources. For instance, SYN floods flood the target with high SYN requests, depleting its capacity to respond to legitimate traffic.
Impact of DDOS Attacks:
DDOS attacks can have severe consequences for both individuals and organizations. Some of the notable impacts include:
1. Financial losses: A successful DDOS attack can result in significant financial losses for businesses, as their online services become unavailable, leading to decreased productivity, lost sales, and potential reputational damage.
2. Reputation damage: Organizations that fall victim to DDOS attacks may suffer reputational damage, as customers and clients lose trust in their ability to provide reliable services. This can further impact their long-term growth and success.
3. Disruption of critical services: DDOS attacks can disrupt critical services, such as banking, healthcare, or government systems, leading to potential chaos and loss of essential services for individuals and communities.
Mitigating DDOS Attacks:
While it is impossible to eliminate the risk of DDOS attacks completely, there are several measures individuals and organizations can take to mitigate the impact:
1. Implementing robust network infrastructure: Organizations should invest in scalable and resilient network infrastructure that can withstand high traffic volumes. This includes load balancing, traffic filtering, and redundant systems.
2. Utilizing DDOS mitigation services: Professional DDOS mitigation services can help organizations identify, mitigate, and respond to attacks effectively. These services employ advanced techniques like traffic analysis, rate limiting, and behavior-based anomaly detection.
3. Regular security audits: Regular security audits can help identify vulnerabilities that could be exploited in a DDOS attack. By addressing these vulnerabilities promptly, organizations can reduce their risk exposure.
DDoS: An Expensive Type of Attack
A port on a firewall or an IPS device is expensive. Third-party infrastructure-as-a-service options are available on a demand basis. In this case, you don’t need to overprovision bandwidth or purchase specialist hardware, as third-party DDoS companies already have the capacity and capability to deal with such attacks.
Content distribution networks help by absorbing DDoS traffic. There are also cloud-based firms specializing in DDoS mitigation. If you are under an attack, you can redirect your traffic to their network, which is scrubbed and sent back. They put a shield in front of your services.
Cloud Flare offered a content delivery network and distributed domain name server service. They are known to have protected the LulzSec website from several high-profile attacks. They use reverse proxy technology and an anycast network, enabling them to take high-volume DDoS attacks and spread them over a large surface area.
Cloudflare recently experienced an attack using Google IP addresses as a reflector; they called this the Google ACK reflection attack. Cloud Flare has special rules, so they never block Google’s legitimate crawler traffic. With a Google ACK reflection, the attacker sends a TCP SYN with a fake header pointing back at an IP address to Google, causing Google to respond with an ACK. It was resolved by blocking the ACK that didn’t have an SYN attached.
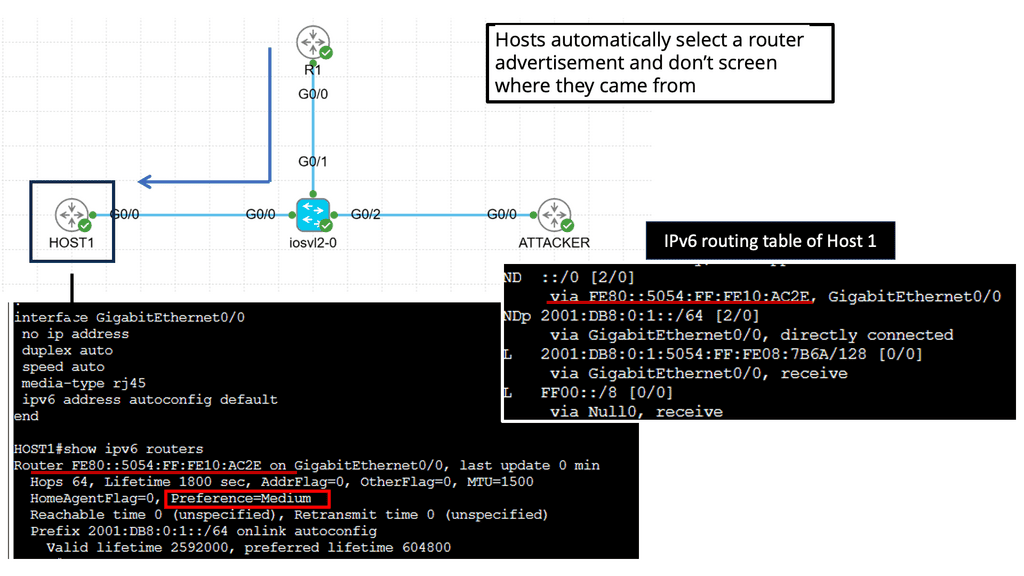
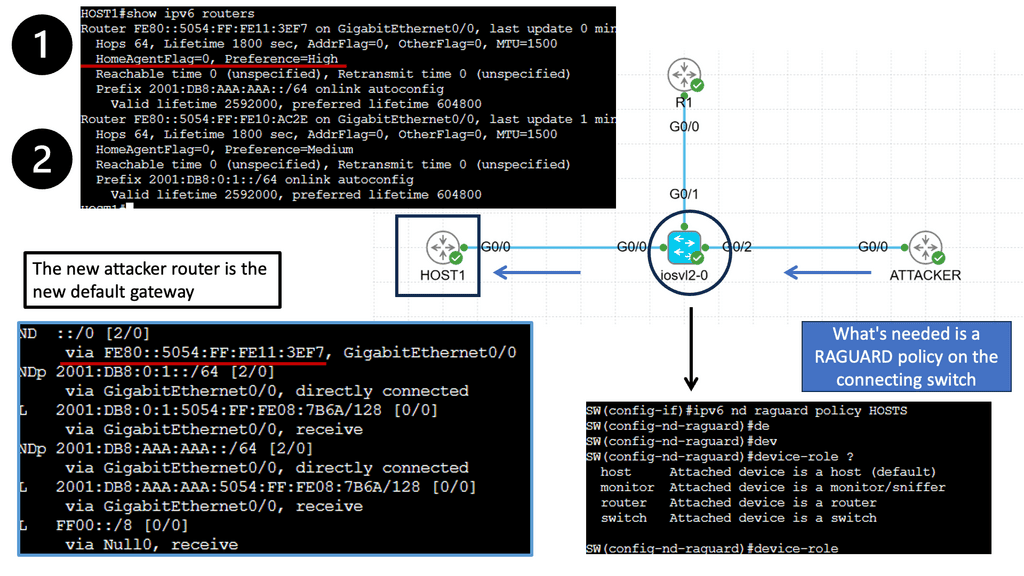
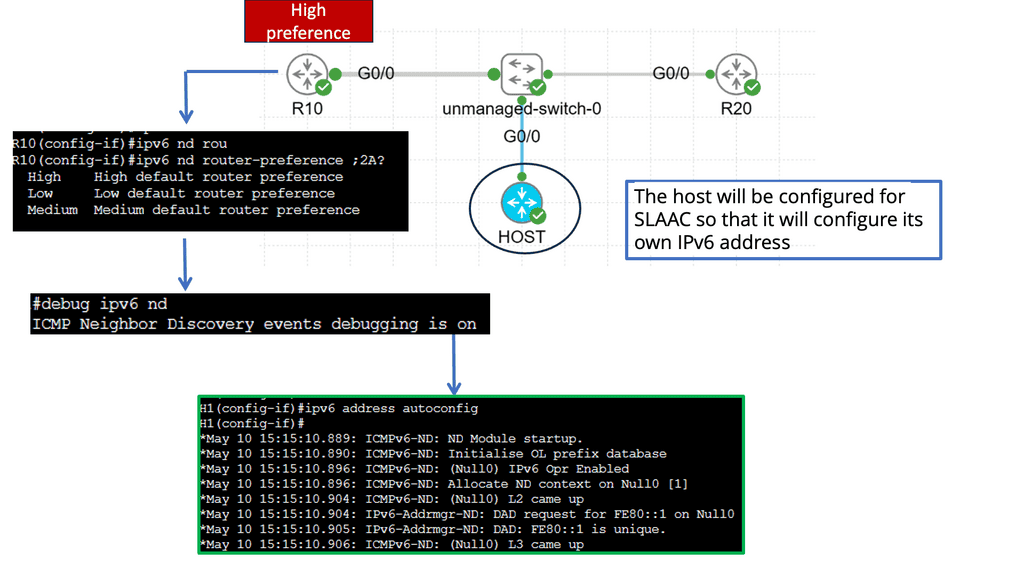
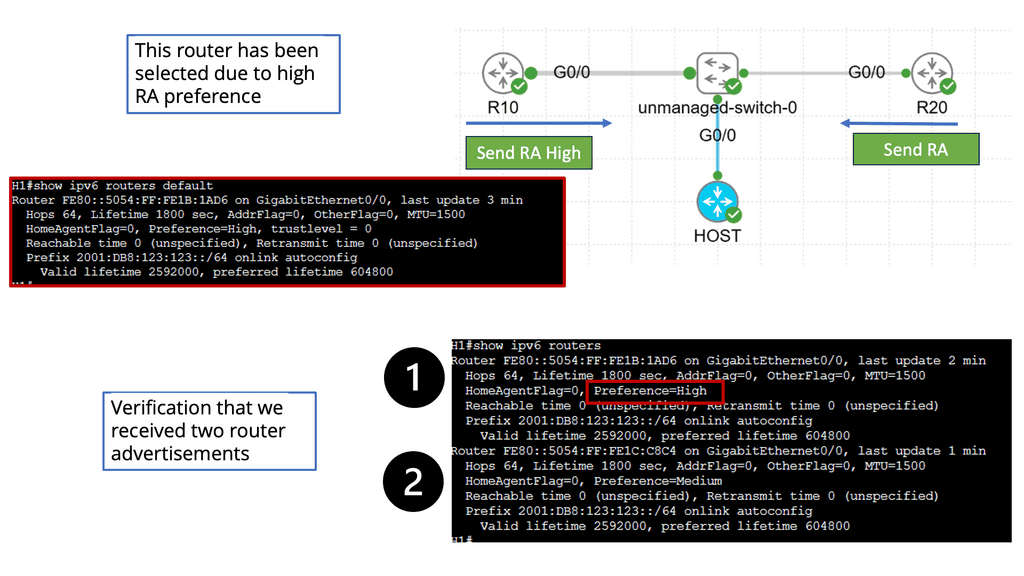
IPv6 Link-Local DoS
IPv6 Link-Local DoS attack is an IPv6 RA ( Router Advertisement ) attack. With this IPv6 attack, one attacker can bring down a whole network. It only needs a few packets/sec. With IPv4 DHCP, the host looks up and retrieves an IPv4 address, a PULL process. IPv6 is not done this way. IPv6 addresses are provided by IPv6 router advertising, a PUSH process.
The IPv6 router advertises itself to everyone to join its networks. It uses multicast to all node addresses, similar to broadcast, which uses one packet to every node. The problem is that you can send many RA messages, which causes the target to join ALL networks.
DDoS is a growing problem that gets more sophisticated every year. ISP and user collaboration are essential, but we are not winning the game. Who owns the problem? The end-user doesn’t know they are compromised, and the ISP is just transiting network traffic.
Traffic can quickly go through multiple ISPs, so how do the ISPs trace back and channel to each other? Who do you hold responsible, and in what way are they accountable? Is it fair to personalize an end-user if they don’t know about it? There need to be terms of service for abuse policies. Users should control their computers more and understand that Anti-Virus software is not a complete solution.
DDOS attacks continue to be a persistent threat in the digital world, with potentially devastating consequences for individuals and organizations. By understanding the nature of these attacks and implementing appropriate security measures, we can better protect ourselves and ensure a more secure online environment.
DDoS attacks: Types
There are three main types of DOS attacks: a) Network-centric Layer 4, b) Application-centric Layer 7, and c) IPv6 DDoS Link-Local DoS attacks. The DDoS umbrella holds lots of variations: SYN packets usually fill up connection tables, while ICMP and UDP attacks consume bandwidth.
Layer 4 attacks
Layer 4 is the simplest type of attack and has been used to take down companies such as MasterCard and Visa. These attacks use thousands of machines to bring down one. They’re primitive-style attacks in which multiple machines send simple packets to a target, attempting to deplete computing resources like CPU, memory, and network bandwidth.
The connections are standard; they establish fully and terminate as regular connections do, unlike Layer 7 attacks (discussed below). The connection only takes a few seconds, so thousands of hosts must overload a single target. For example, the tools for Layer 4 attacks are readily available – low orbit ion cannon (LOIC). LOIC is an open-source denial-of-service attack application written in C#. Layer 4 DDoS attacks are easily tracked back and blocked.
Layer 7 attacks
Layer 7 attacks are more sophisticated and usually require one to bring down many. For example, Wikileaks’s whistle-blowing website went down for one day with only one attacker penetrating a Layer 7 attack. A SlowLoris attack is an elegant Layer 7 attack associated with several high-profile attacks. It opens multiple connections to the targeted web server and keeps them open.
It uses up all the lines and blocks legitimate traffic, designed to keep all the tables full. Layer 4 attacks cannot be run through anonymity networks (ToR networks), but Layer 7 attacks can, due to their small packets/second rate. Layer 7 attacks are like guided missiles. The pending requests take up to 400 seconds, so you don’t need to send many.
Common types of attacks
The most common type of attacks right now are carried out with HTTP. About 80% of the attack surface is coming through HTTP. A Layer 7 HTTP GET attack requests to send only part of the HTTP GET. As a result, the server assumes you are on an unreliable network and have fragmented packets. It waits for the other half, which ties up resources, freezing all available lines.
All you need is about one packet per second. The R-U-Dead-Yet attack is similar to the HTTP GET attack but uses HTTP POSTS instead of HTTP GETs. It works by sending incomplete HTTP POSTs, which affects IIS servers. IIS is not affected by the SlowLoris attack that sends incomplete HTTP GET. There are other variations called HTTP Keep-Alive DoS. HTTP Keepalives allows 100 requests in a single connection.
Closing Points on DDoS Attacks
Essentially, a DDoS attack is an attempt to crash a server, a service, or a network by overwhelming it with a flood of internet traffic. Imagine hundreds of people trying to squeeze through a single door at once; the result is chaos and congestion, preventing legitimate users from entering. This is precisely what happens during a DDoS attack, where multiple compromised systems are used to target a single system, causing a denial of service for users of the targeted resource.
Understanding the mechanics of a DDoS attack can help in developing strategies to mitigate its impact. These attacks harness the power of botnets—networks of infected computers controlled by attackers—to flood targets with traffic. The targeted system is inundated with requests, rendering it slow or completely inoperative. There are several types of DDoS attacks, including volumetric attacks, which saturate the bandwidth of the victim, and application-layer attacks, which target web applications to exhaust resources.
The implications of a successful DDoS attack can be devastating. Beyond the immediate disruption of services, there are financial repercussions, including lost revenue, the cost of mitigation, and potential regulatory fines. Moreover, the reputational damage can be long-lasting, as customers lose trust in the reliability of a company’s digital services. For businesses, especially those that rely heavily on their online presence, a DDoS attack can be catastrophic.
Given the potential damage, it’s crucial to implement robust defense strategies against DDoS attacks. Organizations can invest in DDoS protection services that detect and mitigate attacks in real-time. Additionally, creating a response plan that includes identifying vulnerabilities, developing incident response teams, and conducting regular security audits can help in preparing for potential threats. Leveraging cloud-based solutions, which can absorb and disperse attack traffic, is another effective strategy to protect against these attacks.
DDoS Attacks
Summary: DDoS Attacks
Cybersecurity remains a paramount concern in today’s interconnected world, where the digital realm is an integral part of our lives. Distributed Denial of Service (DDoS) attacks have emerged as a significant challenge among the various threats lurking in cyberspace. In this blog post, we will delve into the intricacies of DDoS attacks, understand their mechanisms, explore their impact, and discuss preventive measures.
Understanding DDoS Attacks
DDoS attacks, short for Distributed Denial of Service attacks, involve overwhelming a targeted server or network with excessive traffic. These attacks are orchestrated by malicious actors who exploit vulnerabilities in the system to flood it with requests, rendering it unable to respond to legitimate users. The diversity and complexity of DDoS attack techniques make them a formidable threat to online platforms, businesses, and critical infrastructure.
Types of DDoS Attacks
There are various types of DDoS attacks, each with its distinctive characteristics. Some common attack types include:
1. Volumetric Attacks: These attacks aim to saturate the target’s bandwidth, consuming all available network resources and rendering the system unresponsive.
2. TCP State-Exhaustion Attacks: By depleting the target’s connection state table, these attacks disrupt the TCP three-way handshake process, causing service disruptions.
3. Application Layer Attacks: These attacks exploit vulnerabilities in the application layer, overwhelming the target with malicious requests that often mimic legitimate traffic.
Impacts and Consequences
The consequences of DDoS attacks can be severe and wide-ranging. For businesses, an attack can result in financial losses, reputational damage, and erosion of customer trust. Online services may experience prolonged downtime, leading to dissatisfied users and potential revenue decline. Additionally, critical infrastructure sectors, such as healthcare and banking, face the risk of disrupted services, potentially impacting public safety and economic stability.
Preventive Measures
Mitigating the risk of DDoS attacks requires a multi-layered approach. Here are some preventive measures that organizations can adopt:
1. Network Monitoring and Traffic Analysis: Implement robust monitoring systems to detect abnormal traffic patterns and behavior, enabling proactive responses to potential attacks.
2. Scalable Infrastructure: Build a resilient and scalable infrastructure that can handle sudden surges in traffic, reducing the impact of volumetric attacks.
3. Web Application Firewalls (WAF): Employ WAF solutions that can filter and block malicious traffic, preventing application layer attacks from reaching the targeted systems.
4. Content Delivery Network (CDN): Utilize CDN services to distribute traffic across multiple servers, improving availability and mitigating the impact of DDoS attacks.
In conclusion, DDoS attacks significantly threaten the stability and security of online platforms, businesses, and critical infrastructure. Understanding the various attack types and their impacts and implementing preventive measures are crucial steps towards safeguarding against these threats. By staying vigilant, investing in robust cybersecurity measures, and fostering collaboration among stakeholders, we can combat the menace of DDoS attacks and ensure a safer digital environment for all.