IPv6 Attacks
In today's digital age, the internet has become an integral part of our lives. The transition from IPv4 to IPv6 was necessary to accommodate the growing number of devices connected to the internet. However, with this transition, new security challenges have emerged. This blog post will delve into IPv6 attacks, exploring their potential risks and how organizations can protect themselves.
Before discussing potential attacks targeting IPv6, it is essential to understand why the transition from IPv4 to IPv6 was necessary. IPv4, with its limited address space, could no longer sustain the increasing number of internet-connected devices. IPv6, on the other hand, provides an enormous number of unique addresses, ensuring the growth of the internet for years to come.
Common IPv6 Attack Vectors: In this section, we will explore the various attack vectors that exist within the IPv6 landscape. From address scanning and spoofing to router vulnerabilities and neighbor discovery manipulation, attackers have ample opportunities to exploit weaknesses in the protocol.
Implications of IPv6 Attacks: The consequences of successful IPv6 attacks can be severe. With the potential to disrupt communication networks, compromise sensitive data, and even launch large-scale DDoS attacks, it is crucial to understand the implications of such security breaches.
Mitigating IPv6 Attacks: Thankfully, there are several measures that can be taken to mitigate the risks associated with IPv6 attacks. This section will discuss best practices for securing IPv6 networks, including implementing strong firewall rules, monitoring network traffic, and keeping network devices up to date with the latest security patches.
The Role of Network Administrators: Network administrators play a crucial role in maintaining the security and integrity of IPv6 networks. This section will highlight the responsibilities and proactive steps that administrators should take to safeguard their networks against potential threats.Matt Conran
Highlights: IPv6 Attacks
Change in perception and landscape
In the early days of the Internet, interconnected systems comprised research organizations and universities. There wasn’t a sinister dark side, and the Internet was used for trusted sharing, designed without security. However, things rapidly changed, and now the Internet consists of interconnected commercial groups of systems running IPv4 and IPv6. Now, Internet-facing components are challenged with large-scale Internet threats, such as malware, worms, and various service exhaustion DoS attacks.
New types of IPv6 attacks
Along with the birth of new IPv6 attacks based on, for example, IPv6 broadcast that requires new mitigation techniques such as IPv6 filtering and the ability to manage against security issues from IPv6 fragmentation. IP networks carry data and control packets in a common “pipe.” The common “pipe” and its payload require secured infrastructure. Legacy is the same for both versions of the IP protocol. IPv4 and IPv6 systems need security to protect the “pipe” from outside intrusion.
Related: Before you proceed, you may find the following useful:
- IPv6 RA
- IPv6 Host Exposure.
- Technology Insight for Microsegmentation
- Virtual Firewalls
- Data Center Network Design
- WAN SDN
IPv6 Attacks Key IPv6 Attacks Discussion Points: |
|
Back to basics with IPv6 Security
IPv6 Security
In those early days of IPv4-connected hosts, the Internet consisted of a few trusted networks of well-known researchers. If security was needed, it was usually just the fundamentals of authentication/authorization, which could have been included in the application code. Numerous years later, IPsec was introduced when IPv4 had already been widely deployed.
However, it was cumbersome to deploy into existing networks. As a result, IPsec could be more commonly deployed in many IPv4 scenarios. This is in contrast to IPv6, which initially had the notion that fundamental security functionality had to be included in the base protocol to be used on any Internet platform.
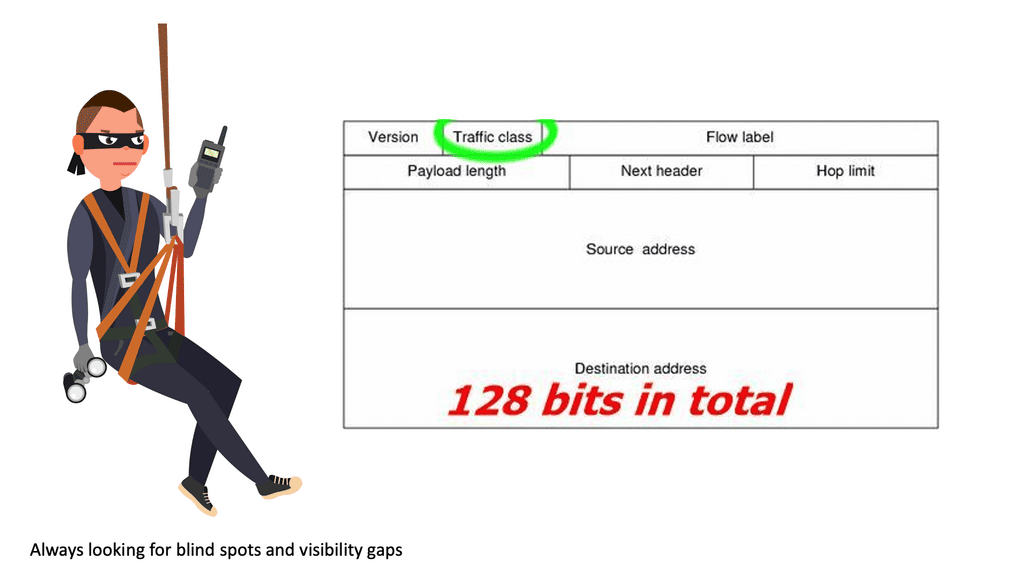
The main difference between IPv6 and IPv4 is the size of addresses: 128 bits for IPv6 versus 32 bits for IPv4—the increase in address size results in a larger IPv6 header. The minimum size of the IPv6 header is twice the size of the IPv4 minimum header. The Internet has evolved to use IPv6 and its new structures. Threats have also evolved to cope with the size and hierarchical nature of IPv6.
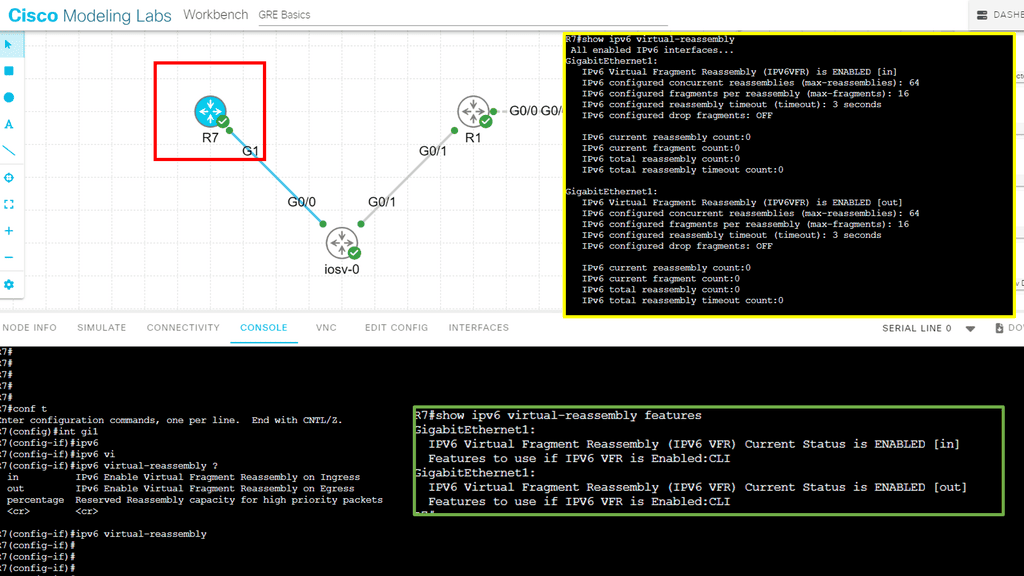
1st Lab Guide: Using IPv6 Filters
In the following, we have an IPv6 filter configured on R1. An IPv6 filter is similar to that of IPv4 access lists. However, it would be best if you kept in mind the following:
- IPv4 access-lists can be standard or extended, numbered or named. IPv6 only has named extended access-lists.
- IPv4 access-lists have an invisible implicit deny any at the bottom of every access-list. IPv6 access-lists have three invisible statements at the bottom:
- permit icmp any any nd-na
- permit icmp any any nd-ns
- deny ipv6 any any
As a security best practice, I would also have the command: no ipv6 unreachables on the interface.
Highlighting the types of IPv6 Attacks:
Neighbor Discovery Protocol (NDP) Attacks:
The Neighbor Discovery Protocol (NDP) is a fundamental component of IPv6 networks. Attackers can exploit vulnerabilities in NDP to launch various attacks, such as Neighbor Advertisement Spoofing, Router Advertisement Spoofing, and Neighbor Unreachability Detection (NUD) attacks. These attacks can result in traffic interception, denial of service, or even network infiltration.
Flood Attacks:
IPv6 flood attacks, similar to their IPv4 counterparts, aim to overwhelm a target device or network with excessive traffic. These attacks can lead to network congestion, service disruption, and resource exhaustion. Flood attacks targeting IPv6, such as ICMPv6, NDP, or UDP floods, can exploit vulnerabilities in network infrastructure or exhaust network resources like bandwidth or CPU.
Fragmentation Attacks:
IPv6 fragmentation allows large packets to be divided into smaller fragments, which are reassembled at the receiving end. Attackers can exploit fragmentation vulnerabilities to bypass security measures, evade detection, or launch Denial of Service (DoS) attacks. Fragmentation attacks can overload network resources or cause packet loss, disrupting communication.
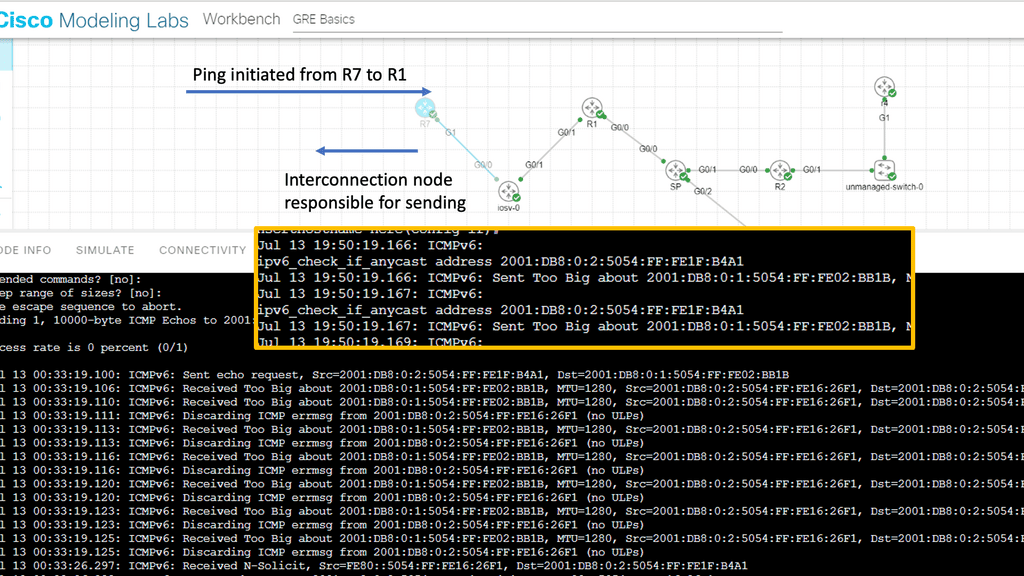
2nd Lab guide on IPv6 fragmentation attacks
You can set IPv6 virtual reassembly on the interface to prevent fragmentation attacks.IPv6 virtual reassembly is a process that reconstructs fragmented packets at the receiving end of a network transmission. When transmitted across the Internet, packets are divided into smaller units. Due to various factors, such as network congestion, these packets may arrive out of order or get fragmented.
Virtual reassembly ensures these packets are correctly reassembled and delivered to the intended recipient. This mechanism is crucial for maintaining data integrity, reducing latency, and optimizing network performance.
Detailing IPv6 Attacks
One of the most basic forms of IPv6 security is ingress and egress filtering at Internet Edge. However, attackers can forge an IPv6 packet with specially crafted packets and spoofed IPv6 addresses, so filtering based on IP addresses is required. Spoofing modifies source IP addresses or ports to appear if packets are initiated from another location.
IPv4 networks are susceptible to “Smurf” broadcast amplification attacks where a packet from a forged unknowing victim’s address is sent to the subnet broadcast of an IPv4 segment. The attack type employs the Spoofing technique, in which the victim’s IP address is used as the source of the attack. The broadcast subnet is the all-one host address of each subnet (example 192.168.1.255 255.255.255.0).
As we send to the broadcast address, all hosts on the subnet receive a packet consisting of an ICMP-ECHO with a payload. Hosts automatically send back an ECHO-REPLY to the victim’s spoofed address. As a result, the victim gets bombarded with packets (ECHO-REPLIES), forcing CPU interrupts, eventually resulting in a Denial of Service (DoS) attack. Cisco IOS has the command “no IP directed-broadcast” on by default, but some poorly designed networks use directed broadcast for next-hop processing.
So we don’t have to worry about this in IPv6? IPv6 uses multicasts and is not broadcast for communication.
Multicast amplification attacks
IPv6 does not use a type of IPv6 broadcast as its communication, but it uses various multicast addresses. You are essentially doing the same thing but differently. Multicast is the method for one-to-many communications. For this reason-IPv6, multicast addresses can be used for traffic amplification.
The Smurf6 tools are a type of Smurf attack run with Kali Linux. It generates lots of local ICMPv6 traffic used to DoS attack-local systems. Smurf6 sends locally generated ICMPv6 ECHO REQUEST packets toward the “all routers” multicast address of FF02::2.
As this multicast address represents all routers on the segment, they all respond with ICMPv6 ECHO RESPONSE to the victims’ source address. The multicast address can be used for DoS attacks. It is essential to control who can send to these multicast addresses and who can respond to a multicast packet.
IPv6 security and important IPv6 RFCs
RFC 2463 “Internet Control Message Protocol (ICMPv6) for the Internet Protocol Version 6 Specification” states that no ICMP message can be generated in response to an IPv6 packet destined for multicast groups. This protects your host’s IPv6 stack and is designed with RFC 2463 specifications. Smurf attacks should not be a threat if all hosts comply with RFC 2463. However, there are two exemptions to this rule. “The “packet too big” and “parameter problem ICMP” are generated in response to packets destined for a multicast group.
Prevent uncontrolled forwarding of these ICMPv6 message types, and filter based on the ICMPv6 type. To prevent packet amplification attacks for “packet too big” and “parameter problem ICMP” filter based on ICMPv6 Type 2: “Packet too big” and ICMPv6 Type 4: “Parameter problem.” You can also rate-limit these message types with the ipv6 ICMP rate-limit command.
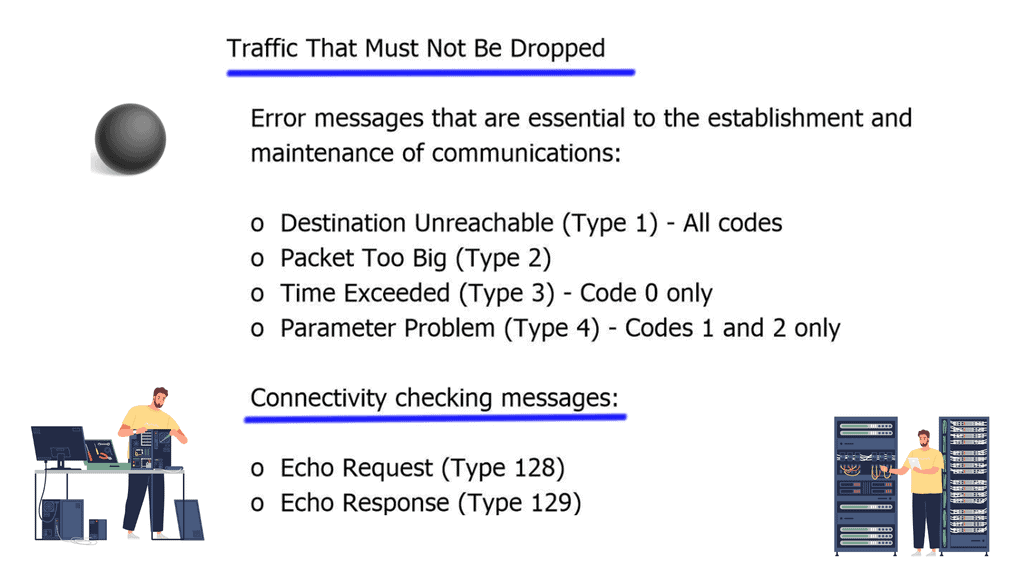
RFC 4890 outlines guidelines for filtering ICMPv6 messages in firewalls. Filter these options or only allow trusted sources and deny everything else. If you are unsure hosts comply with these RFCs, perform ingress filtering of packets with IPv6 multicast source addresses. As a recommendation, purchase firewalls that support stateful filtering of IPv6 packets and ICMPv6 messages. It’s always better to prevent an attack than react to one.
Mitigating IPv6 Attacks:
a) Network Segmentation:
Segmenting networks into smaller subnets can limit the impact of potential attacks by containing them within specific network segments. By implementing strict access controls, organizations can minimize the lateral movement of attackers within their network infrastructure.
b. Intrusion Detection and Prevention Systems (IDPS):
Deploying IDPS solutions can help organizations detect and prevent IPv6 attacks. IDPS solutions monitor network traffic, identify suspicious patterns, and take appropriate actions to mitigate the attacks in real-time.
c. Regular Security Audits:
Regular security audits of network infrastructure, systems, and applications can help identify and address vulnerabilities before attackers exploit them. Organizations should also keep their network equipment and software patched and up to date.
As the world becomes more connected, robust security measures to protect against IPv6 attacks are paramount. Understanding the risks associated with IPv6 and implementing appropriate security measures can help organizations safeguard their networks and data. By staying vigilant and proactive, we can ensure a secure and reliable internet experience for all users in the IPv6 era.
Summary: IPv6 Attacks
In today’s interconnected digital landscape, Internet Protocol version 6 (IPv6) has emerged as a critical infrastructure for enabling seamless communication and accommodating the ever-growing number of devices. However, with the rise of IPv6, new vulnerabilities and attack vectors have also surfaced. In this blog post, we explored the world of IPv6 attacks, shedding light on their mechanisms, potential risks, and mitigation strategies.
Section 1: Understanding IPv6 Attacks
IPv6 attacks encompass a wide range of malicious activities targeting the protocol’s vulnerabilities. From address scanning and spoofing to router vulnerabilities and neighbor discovery exploits, attackers have found various ways to exploit IPv6’s weaknesses. Understanding these attack vectors is crucial for effective protection.
Common Types of IPv6 Attacks
1. Address Resolution Protocol (ARP) Spoofing: This attack involves manipulating the ARP cache to redirect traffic, intercept sensitive information, or launch further attacks.
2. Router Advertisement (RA) Spoofing: By sending forged RAs, attackers can misconfigure routing tables, leading to traffic hijacking or DoS attacks.
3. Neighbor Discovery Protocol (NDP) Attacks: Attackers can exploit vulnerabilities in the NDP to perform address spoofing, router redirection, or even denial of service attacks.
4. Fragmentation Attacks: Fragmentation header manipulation can cause packet reassembly issues, leading to resource exhaustion or bypassing security measures.
Implications and Risks
IPv6 attacks pose significant risks to organizations and individuals alike. These risks include unauthorized network access, data exfiltration, service disruption, compromised confidentiality, integrity, and availability of network resources. With the expanding adoption of IPv6, the impact of these attacks can be far-reaching.
Mitigation Strategies
1. Network Monitoring and Intrusion Detection Systems: Implementing robust monitoring solutions can help detect and respond to suspicious activities promptly.
2. Access Control Lists and Firewalls: Configuring ACLs and firewalls to filter and restrict IPv6 traffic can mitigate potential attack vectors.
3. Secure Network Architecture: Secure network design principles, such as proper segmentation and VLAN configuration, can limit the attack surface.
4. Regular Patching and Firmware Updates: It is crucial to keep network devices up to date with the latest security patches and firmware versions to address known vulnerabilities.
Conclusion:
As the world becomes increasingly reliant on IPv6, understanding the threats it faces is paramount. Organizations can better protect their networks and data from potential harm by being aware of the different types of attacks and their implications and implementing robust mitigation strategies. Stay vigilant, stay informed, and stay secure in the ever-evolving landscape of IPv6.
- DMVPN - May 20, 2023
- Computer Networking: Building a Strong Foundation for Success - April 7, 2023
- eBOOK – SASE Capabilities - April 6, 2023