Cloud Native Meaning
In recent years, the term “cloud native” has gained immense popularity in technology. Organizations across industries embrace cloud-native architectures to enhance their digital transformation efforts. But what exactly does “cloud native” mean? In this blog post, we will delve into the concept of cloud-native, exploring its meaning, characteristics, and the benefits it offers to businesses.
At its core, cloud-native refers to building and running applications that takes full advantage of cloud computing capabilities. It entails designing applications specifically for deployment on cloud platforms, utilizing the native features and services offered by the cloud provider. Cloud-native applications are typically developed using microservices architecture, enabling them to be highly scalable, resilient, and easily manageable.
Highlights: Cloud Native Meaning
- The Journey To Cloud Native
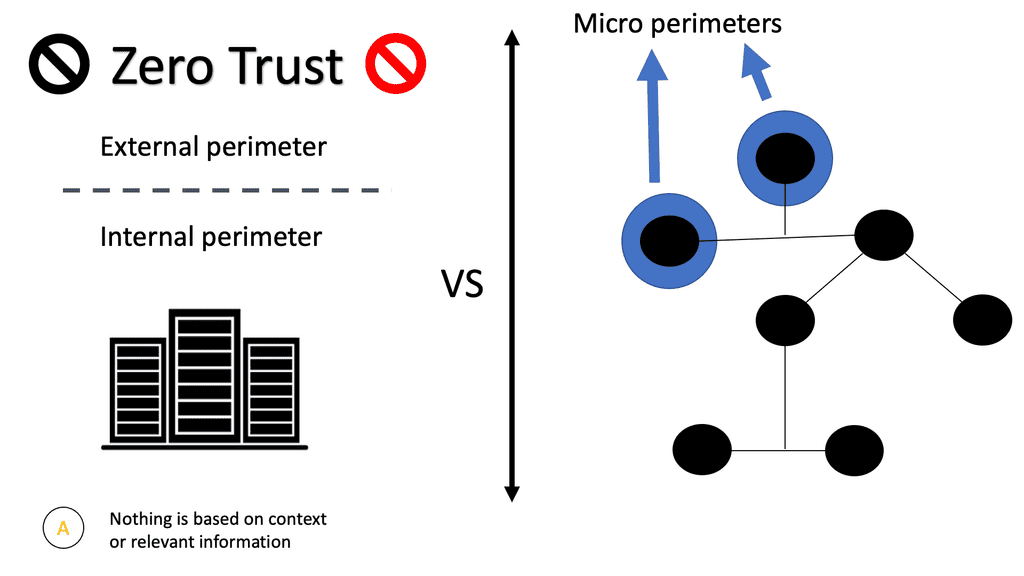
We must find ways to efficiently secure cloud-native microservice environments and embrace a Zero Trust Network Design. To assert who we say we are, we need to provide every type of running process in an internal I.T. infrastructure with an intrinsic identity. So, in our journey for cloud native meaning, how do you prove who you are flexibly, regardless of what platform?
- Everything is an API Call
First, you need to give someone enough confidence to trust your words. I.P. addresses are like home addresses, creating a physical identity for the house but not telling you who the occupants are. The more you know about the people living in the house, the richer the identity you can give them. The richer the identity, the more secure the connection.
Larger companies have evolved their authentication and network security components to support internal service-to-service, server-to-server, and server-to-service communications. Everything is an API call. There may only be a few public-facing API calls, but there will be many internal API calls, such as user and route lookups. In this situation, CASB tools will help your security posture. However, this will result in a scale we have not seen before. Companies like Google and Netflix have realized there is a need to move beyond what most organizations do today.
Before you proceed, you may find the following post helpful:
- Microservices Observability
- What is OpenFlow
- SASE Definition
- Identity Security
- Security Automation
- Load Balancing
- SASE Model
Cloud Native Meaning. |
|
- A key point: Video on Cloud operating models
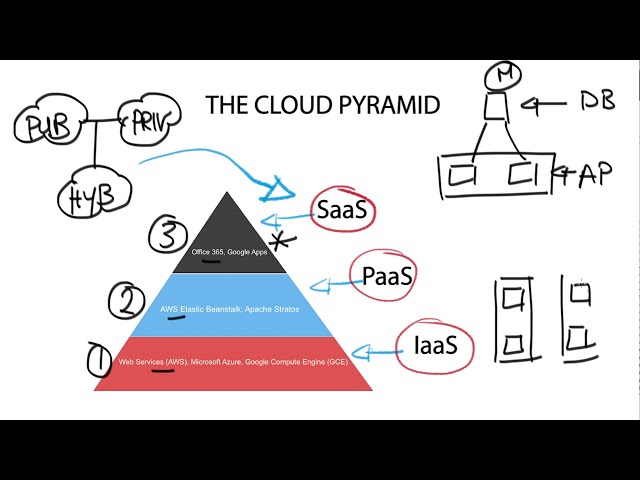
In the following video, we will discuss the cloud operating models. Clouds operate under different service models – Infrastructure of a service IaaS, Platform of a service PaaS, and Software of a Service SaaS service models. These service models provide different abstraction layers to the consumer and offer different security requirements to the consumer. Public Cloud Providers are not a single type, and A generic evaluation of security cannot be generalized amongst all of them.
Back to basics Cloud Native Meaning
The Role of cloud computing
Cloud computing is feasible only because of the technologies that enable resource virtualization. If you’re going to have multiple virtual endpoints share a physical network. Still, different virtual endpoints belong to different customers, and the communication between these virtual endpoints also needs to be isolated. In other words, the network is a resource, too, and network virtualization is the technology that enables sharing of a standard physical network infrastructure.
Essential Characteristics of Cloud Native Applications:
Cloud-native applications exhibit several key characteristics that set them apart from traditional applications. These characteristics include:
1. Scalability: Cloud-native applications are designed to scale effortlessly, allowing organizations to handle increasing workloads without compromising performance. By leveraging cloud resources, applications can dynamically adjust their resource usage based on demand.
2. Resilience: Cloud native applications are built with resilience in mind. They are designed to handle failures gracefully, automatically recovering from disruptions and minimizing downtime. This resilience is achieved through fault tolerance, self-healing, and distributed architectures.
3. Agility: Cloud-native applications enable organizations to rapidly develop, deploy, and update software. Developers can easily package, deploy, and manage applications across different environments by utilizing containerization technologies like Docker and orchestration tools like Kubernetes.
4. DevOps Culture: Cloud native development fosters a DevOps culture by promoting collaboration between development and operations teams. Continuous integration and continuous deployment (CI/CD) practices are integral parts of cloud-native development, allowing organizations to deliver new features and updates faster.
Benefits of Cloud Native Adoption:
Embracing a cloud-native approach offers numerous benefits for organizations:
1. Cost Optimization: Cloud-native applications can leverage cloud resources more efficiently, resulting in cost savings by only utilizing the resources needed at any time. Additionally, organizations no longer need to invest in physical infrastructure or worry about maintenance costs.
2. Scalability and Elasticity: Cloud-native applications can dynamically scale up or down based on demand, ensuring optimal performance during peak periods while reducing costs during periods of low usage.
3. Faster Time to Market: The agility provided by cloud-native development allows organizations to bring new products and features to market faster. By automating the deployment process and utilizing scalable infrastructure, development teams can focus on delivering value rather than managing infrastructure.
4. Improved Reliability and Resilience: Cloud-native applications are inherently designed to be more reliable and resilient. By utilizing containerization and distributed architectures, organizations can achieve higher levels of availability and minimize the impact of failures.
Cloud Native Meaning: Network Segmentation
Firstly, they rely on traditional network constructs such as firewalls and routers to enforce authentication. If traffic wants to get from one I.P. segment to another I.P. segment, it passes through a layer 4 to layer 7 rule set filter; then, those endpoints should be allowed to talk to each other.
However, network segmentation is a bit too coarse-grained versus what is happening at the application layer. The application layer is going through significant transformational changes. The changes to network security represent the application less than the application should be represented. API gateways, web application firewalls (WAFs), and next-gen firewalls are all secondary to protecting microservices. They are just the first layer of defense. Every API call is HTTP/HTTPS, so what good is a firewall anyway?
Traditional Security Mechanism
We have new technologies being protected by traditional means. The traditional security mechanism based on I.P. and 5-tuple can’t work in a cloud-native microservice architecture, especially when there are lateral movements. Layer 4 is coupled with the network topology and lacks the flexibility to support agile applications.
These traditional devices must follow the microservice workload, source/destination I.P. address, and source/destination port number around the cloud, or else things will be practical. This is a design phase that will not happen. You need to bring security to the microservice, not vice versa.
Traditional security mechanisms are evaporating. The perimeter has changed and is now at the API layer. Every API presents a new attack surface which results in a gap. A gap must be filled, and only a few companies do this. There are too few, and we need more.
Outdated: Tokens and Keys
The other thing is the continued use of Tokens and Keys. They are hard-coded strings that serve as a proxy for who you are. The problem is that the management of these items is complex. For example, rotating and revoking them is challenging. This is compounded by the fact that we must presume that the I.T. organization infrastructure will become more horizontally scaled and dynamic.
We can all agree that we will arbitrarily see these things spin up and down with the introduction of technologies such as containers and serverless because it’s more cost-effective than building and supporting tightly coupled monolithic applications. So the design pattern of enterprise I.T. is moving forward, making the authentication problem more difficult. So we need to bring life a new initiative. We need a core and identity construct that supports the design pattern when building for the future.
Cloud-native meaning with a new identity-based mechanism
We need companies to recognize that a new identity-based mechanism is required. We have had the identity for human-centric authentication for decades. There are hundreds of companies built to do this. However, the scale of identity management of internal infrastructure is an order of magnitude more significant than it was with humans.
That means existing technology constructs and technologies such as Active Directory need to be more scalable and built for this scale. This is where the opportunity arises – building architectures that match this scale.
Another thing that comes to mind when you look at these authentication frameworks when you think about identity and cryptography, it’s a bit of a black box, especially for the newer organizations that don’t have the capacity and DNA to think about infrastructure at that layer.
For the organization, there is interest in a product that allows them to translate internal policies that are no longer in the internal data center but in the cloud. We need a way to carry out the mappings to the middleware public cloud using identity as the core service. When everything has an atomic identity, it can also be used for other purposes. For example, you can use it to chain identities together and better debug and trace, to name a few.
Conclusion:
In today’s rapidly evolving digital landscape, embracing cloud-native architectures has become imperative for organizations seeking to stay competitive. By understanding the meaning and characteristics of cloud-native, businesses can leverage its benefits to drive innovation, improve efficiency, and deliver exceptional user experiences. Organizations must adapt and embrace this transformative approach to ensure long-term success in the digital era as the cloud-native ecosystem continues to evolve.
- DMVPN - May 20, 2023
- Computer Networking: Building a Strong Foundation for Success - April 7, 2023
- eBOOK – SASE Capabilities - April 6, 2023