Triangular Routing
LISP, which stands for Locator/ID Separation Protocol, is a groundbreaking networking protocol that has gained significant attention in recent years. In traditional networking, the IP address plays a dual role as both a locator and an identifier. However, LISP introduces a new approach by separating the two, allowing for more efficient and scalable routing. In this blog post, we will delve into the world of LISP and specifically explore the concept of triangular routing.
Triangular routing is a network routing technique that involves sending data packets through a triangular path instead of the traditional direct route. It aims to optimize network performance by avoiding congestion and improving redundancy. By introducing additional paths, triangular routing enhances fault tolerance and load balancing within the network.
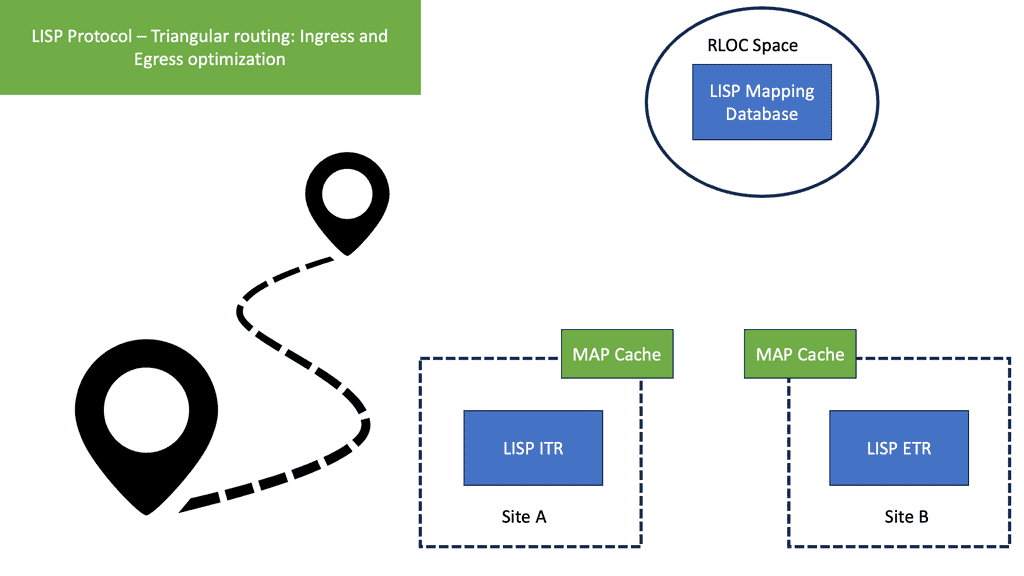
Triangular routing is a fundamental concept within LISP that plays a crucial role in its operation. In traditional routing, packets travel from the source to the destination in a direct path. However, LISP introduces a different approach by employing a triangular routing scheme. In this scheme, packets take a detour through a mapping system known as the Mapping System (MS).
The MS acts as an intermediary, allowing the encapsulation and decapsulation of packets as they traverse the LISP-enabled network. This triangular path not only provides flexibility but also enables various LISP functionalities, such as mobility and traffic engineering.
- Enhanced Network Security: By diverting traffic through an intermediate point, triangular routing provides an additional layer of security. It can help prevent direct attacks on network devices and detect potential threats more effectively.
- Load Balancing: Triangular routing allows for better load distribution across different network paths. By intelligently distributing traffic, it helps prevent congestion and ensures a more balanced utilization of network resources.
- Improved Network Performance: Although triangular routing may introduce additional latency due to the longer path, it can actually enhance network performance in certain scenarios. By avoiding congested or unreliable links, it helps maintain a more consistent and reliable connection.Matt Conran
Highlights: Triangular Routing
LISP Overlay
It creates an overlay network in which the core routers forward packets to RLOCs and EIDs. LISP provides a level of indirection for routing and addressing. A natural mobility feature is created as long as the EID assigned to an endpoint remains constant and the RLOCs change. LISP provides essential support for moving EIDs around, one of its many uses. All devices, whether smartphones, virtual machines, provider-to-provider roaming (physical or in the cloud), or IoT devices, are assigned EIDs with changing RLOCs.
Original use cases
- Reducing the size of the routing table in the core router
- Making multihoming easier to manage while preventing multiconnected sites (multihoming) from adding more routes to the core routing system
- Site addresses can be kept connections can be easily moved from one service provider to another and provider-independent addresses are encouraged
Ingress Site Selection
Supporting distributed applications is an essential requirement for business continuity. Different types of applications, be they legacy or nonlegacy, will provide particular challenges for ingress site selection. One of the main challenges designers face is workload virtualization between different geographic locations. Workload virtualization requires location independence for server resources and the ability to move these resources from one geographic area to another. This is where triangular routing comes into play.
The LISP protocol
What is triangular routing? Triangular routing is a method for transmitting packets of data in communications networks. It uses a form of routing that sends a packet to a proxy system before transmission to the intended destination. The LISP Protocol used as an Internet locator can be used as a proxy.
Introducing LISP
LISP, short for Locator/Identifier Separation Protocol, is a protocol designed to separate IP addresses’ location and identification functions. It provides a scalable and flexible solution to handle IP mobility, multi-homing, and traffic engineering. LISP achieves this by introducing two new address types: Endpoint Identifiers (EIDs) and Routing Locators (RLOCs).
Implementing Triangular Routing with LISP
Now, let’s explore how LISP enables the implementation of triangular routing. By leveraging its capabilities, LISP allows for the creation of multiple paths between the source and destination. This is achieved through LISP mapping systems, which provide the necessary mapping information to enable triangular routing decisions.
Benefits of Triangular Routing with LISP
Triangular routing with LISP offers several advantages in modern network architectures. First, it enhances network resilience by providing alternate paths for data transmission. This improves fault tolerance and reduces the chances of single points of failure. Second, it allows for efficient load balancing, as traffic can be intelligently distributed across multiple paths.
Considerations and Challenges
While triangular routing with LISP brings numerous benefits, certain factors must be considered. One key consideration is the increased complexity of network configuration and management. Proper planning and expertise are required to ensure a smooth implementation. Potential issues such as suboptimal routing and increased latency should also be carefully evaluated.
Related: Before you proceed, you may find the following posts helpful for pre-information:
- Network Security Components
- LISP Hybrid Cloud
- Remote Browser Isolation
- Dynamic Workload Scaling
- Active Active Data Center Design
- Identity Security
Triangular Routing Key Triangular Routing Discussion Points: |
|
Virtualized Workload Mobility
Virtualized Workload Mobility allows live migration between “Twin” data centers and presents several challenges. Firstly, it brings the challenge of route optimization once the workload has moved to the new location. When virtual machines are migrated between data centers, the traffic flow for client-server may become suboptimal, leading to application performance degradation.
How do existing and new connections get directed to the new location? Traditional methods, such as Route Health Injection ( RHI ) and DNS, are available but don’t suit all requirements. They can place unnecessary workloads over the data center interconnect link ( DCI ), creating a triangular routing effect discussed below.
Back to Basics: Triangular Routing
With traditional IP routing, an IP address has two functions:
- Identity: To identify the device.
- Location: We use the device’s location in the network for routing.
LISP separates these two functions of an IP address into two separate tasks:
- Endpoint Identifier (EID): Assigned to hosts like computers, laptops, printers, etc.
- Routing Locators (RLOC): Assigned to routers. We use the RLOC address to reach EIDs.
Cisco created LISP. Originally, it was designed for the Internet, but nowadays, it is also used in other environments, such as data centers, IoT, WAN, and the campus (Cisco SD-Access).
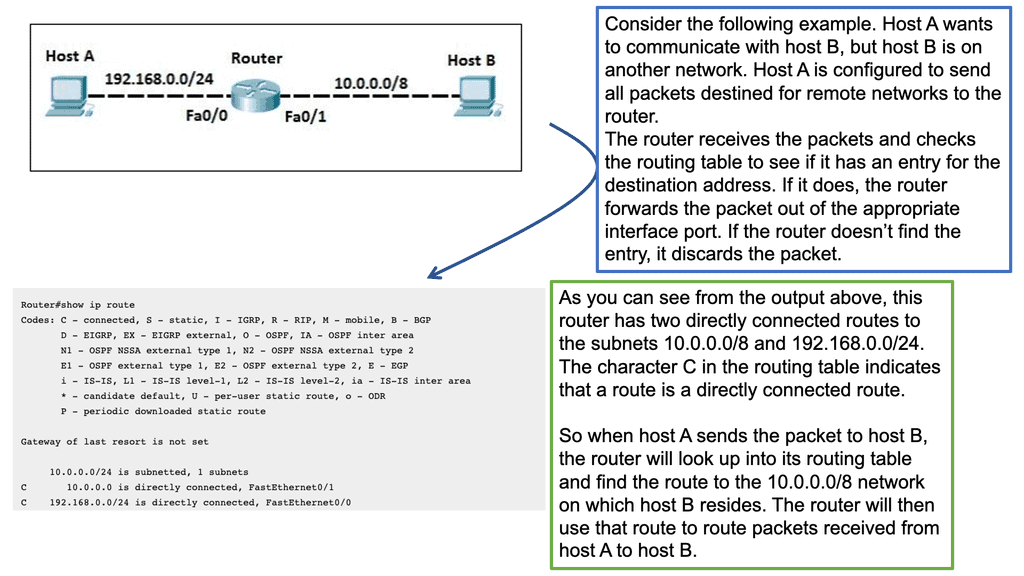
IP Routing.
A router’s primary function is to move an IP packet from one network to a different network. Routers try to select the best loop-free path in a network that forwards a packet to its destination IP address. A router understands nonattached networks through static configuration or dynamic IP routing protocols. So, we have two routing protocols, static and dynamic.
Dynamic IP routing protocols distribute network topology information between routers and provide updates without intervention when a topology change occurs. On the other hand, IP routing with static routes only accommodates topology changes well and can burden network engineers depending on the network size.
A network routing technique
So, what is triangular routing? Triangular routing is a network routing technique that involves sending traffic through three or more points on the network. It is often used to increase the network’s reliability, security, or performance by reducing the load on any single point. In triangular routing, the data is sent from the source node to a middle node and then to the destination node. Depending on the network configuration, the central node may be a router, switch, or hub.
LISP is a map and encapsulation protocol. There are three essential environments in a LISP environment:
- LISP sites: This is the EID namespace where EIDs are.
- Non-LISP sites: This is the RLOC namespace where we find RLOCs. For example, the Internet.
- LISP mapping service: This infrastructure takes care of EID-to-RLOC mappings.
Avoid congestion
Triangular routing is a common technique on the Internet. It is used to avoid congestion and increase reliability. When a connection is established between two nodes, the traffic is sent from the source to the middle node via a shorter route. If the connection between the central node and the destination node is interrupted, the data can be re-routed through another node. This ensures the data is delivered to the destination without interruption.
Triangular routing is also used in private networks, such as corporate networks. It reduces the load on a single point, reduces latency, and increases the network’s security. In addition, each node in the triangular routing is configured with different routing protocols, making it difficult for intruders to penetrate the network.
Triangular routing is a reliable and secure technique for improving network performance. Routing data through multiple points on the network can avoid congestion and increase reliability. The following figure shows an example of triangular routing.
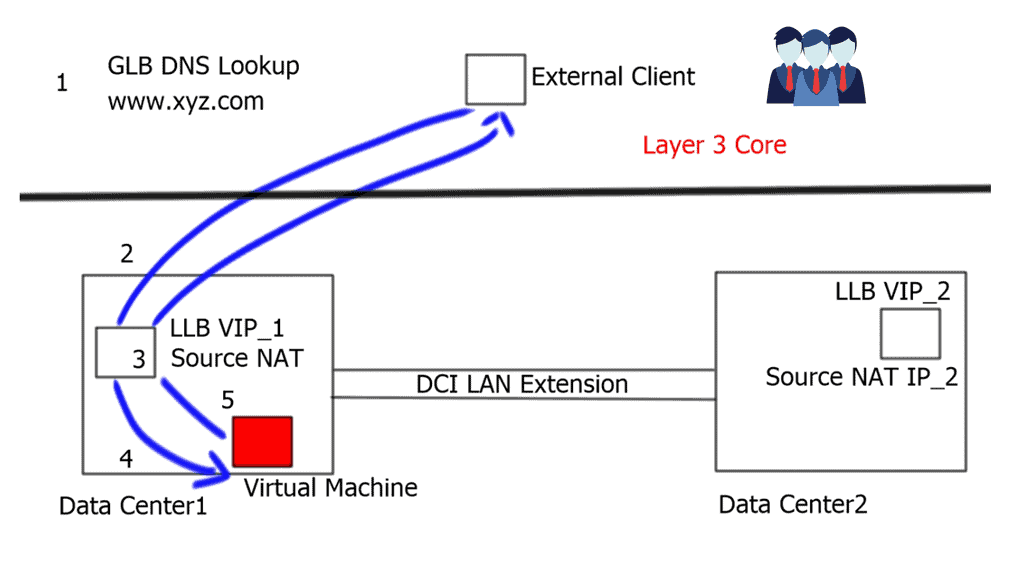
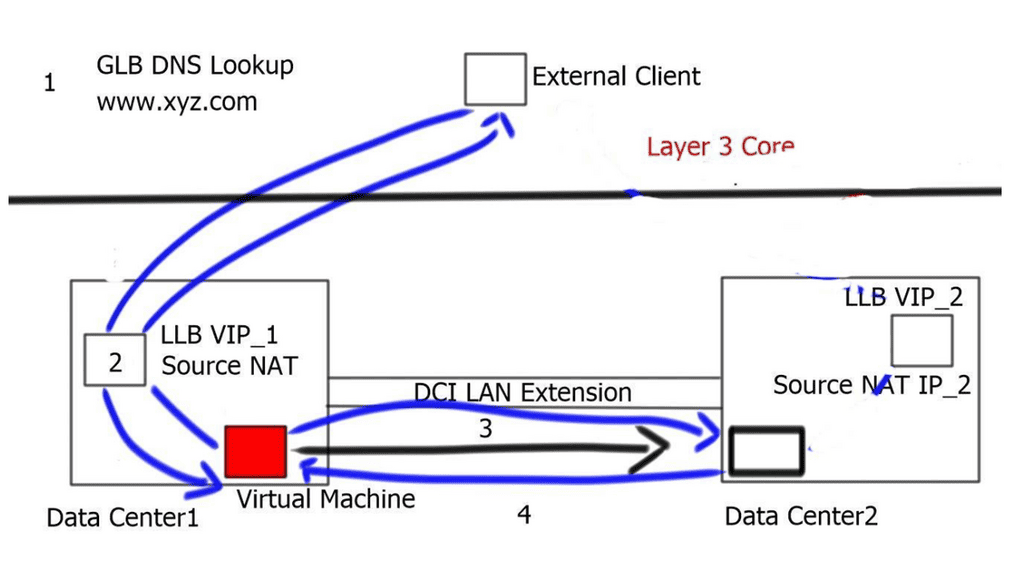
Hair-pinning & Triangular routing – Ingress and Egress traffic flows.
- The external client queries its configured DNS server. The Global Load Balancing ( GLB ) device receives the request, which is authoritative for the queried domain. The GLB responds with the VIP_1 address of the local Load Balancer ( LLB ) in DC1. The VIP_1 represents the application in DC1.
- Traffic gets directed toward the active LLB in DC1.
- The LLB performs a source-NAT translation. Source-NAT changes the source IP address to the LLB’s internal IP address. This enables return traffic to be routed through the correct Load balancer, which is necessary to retain existing established sessions.
- The Virtual Machine ( VM ) receives the packet and replies with the destination address of the Local Load Balancer ( due to Source-NAT ).
- The LLB performs reverse translation and returns the packet to the external client.
Let’s assume that DC1 is overutilized and the network administrator wants to move the VM from DC1 to DC2. This move will be a hot move, a “live migration,” so all established sessions must remain intact. This is mainly because of the presence of stateful devices and the fact that we are not stretching the state of these stateful devices between the two data centers.
There is also a requirement for a LAN extension, such as OTV or vPC, between the two data centers. The LAN extension stretches VLANs and the layer 2 traffic between the two data centers.
- The client-server flows are still directed to VIP_1 from the global load balancers, as there have been no changes to site selection for existing connections. We are traversing the same stateful device as in the earlier example.
- The local load balancer performs Source-NAT and changes the source IP address to its inside address.
- The packet can reach the moved VM by leveraging the L2 LAN extension between both DCs.
- Any existing or new sessions using DC1’s VIP_1 will follow the suboptimal path through DC1 to reach DC2.
You hope there will be immediate changes to DNS and any new sessions ingress to DC2. This would follow the optimum path to the VIP_2, and egress traffic would follow the local gateway in DC2.
Triangular routing: The challenge
The main problem with this approach is that it works for only name-based connections, and previously established connections are hairpinned. The hair-pinning effect implies that there have been active connections to the VIP_1 ( old address ) and some new connections to the VIP_2 in the second data center for some time. Hair-pinning can put an additional load on the DCI and create a triangular routing effect.
The Solution? Locator Identity Separation Protocol ( LISP )
A new routing architecture called the Locator Identity Separation Protocol ( LISP ) was developed to overcome the challenges of workload mobility and triangular routing that were previously discussed. LISP overcomes the problems faced with route optimization when workloads migrate. It creates a new paradigm by splitting the device identity, an Endpoint Identifier ( EID ), and its location, known as its Routing Locator ( RLOC ), into two different numbering spaces.
This means we have a separate protocol representing where and who you are. The existing number scheme based on IP does not offer this flexibility, and both roles ( who and where ) are represented by one address.
Additional information on the LISP protocol
RFC 6830 describes LISP as an Internet Protocol routing and addressing architecture. The LISP routing architecture addresses scalability, multihoming, inter-site traffic engineering, and mobility.
Internet addresses today combine location (how a device is connected to the network) and identity semantics into a single 32-bit or 128-bit number. In LISP, the location is separated from the identity. LISP allows you to change your location in a network (your network layer locator), but your identity remains the same (your network layer identifier).
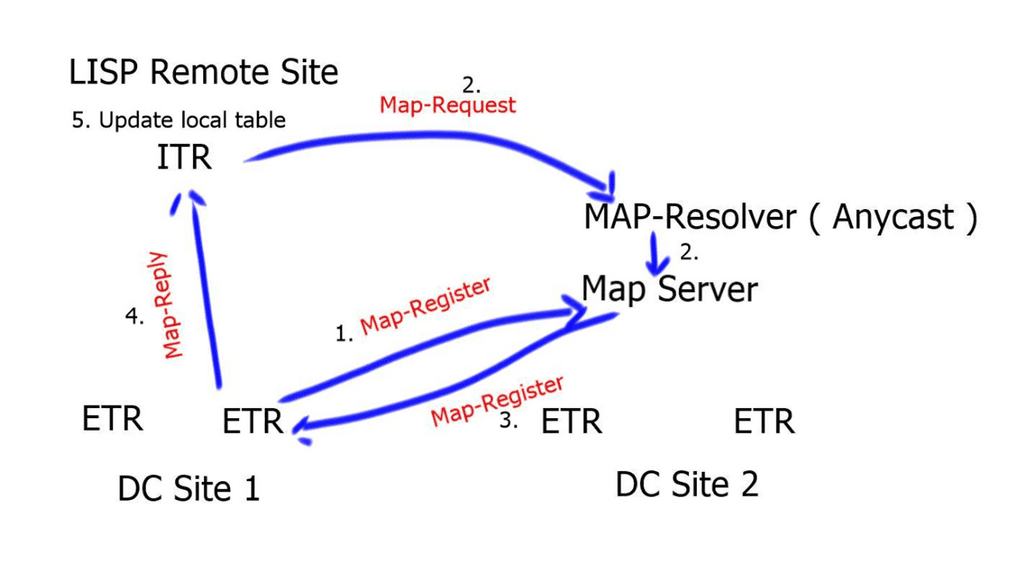
A LISP separates the identifiers of end users from the routing locators used to reach them. The LISP routing architecture design separates device identity – endpoint identification (EID) – from its location – routing locator (RLOC). To further understand how LISP does the locator/ID separation, it is essential to first learn about the architectural components of LISP. The following are some of the functions or features that form the LISP architecture:

LISP Host Mobility
LISP Host Mobility provides an automated solution that enables IP endpoints, such as Virtual Machines ( VM ), to change location while keeping their assigned IP address. As a result, the LISP detection and mapping system guarantees optimal routing between clients and the IP endpoints that moved. The critical point to note is that it’s an automated system.
Once the VM moves to the new location, there is no need to change DNS. The LISP control plane does not make any changes to DNS and does not require agents to be installed on the clients. It’s completely transparent.
LISP VM-mobility provides a transparent solution to end hosts and guarantees optimal path routing to the moving endpoints. It decouples the identity from the topology but creates two separate namespaces, RLOC and EID. The RLOCs remain associated with the topology and are reachable via traditional routing methods. The EID, which describes the end host, can dynamically change location and associate with different RLOCs. This allows the End-point Identifier space to be mobile without impacting the routing interconnecting the locator’s IP space.
LISP VM-Mobility solution:
- VM migrations are automatically detected by the LISP Tunnel Router ( xTR ). This is accomplished by comparing the source in the IP header of traffic received from the hosts against a range of configured prefixes allowed to roam.
- No changes are required to DNS or to install any agents. Transparent to end-users.
- Once the move is detected, the mappings between EIDs and RLOCs are updated by the new xTR.
- Updating the RLOC-to-EID mappings allows traffic to be redirected to the new locations without causing any updates or churn in the underlying routing. It is transparent to the core.
Additional information
Load Balancing:
By distributing data packets across multiple paths, triangular routing helps balance the network load. This ensures that no single path becomes overwhelmed with traffic, preventing congestion and optimizing network performance. Load balancing improves network efficiency and minimizes latency, resulting in faster data transmission.
Fault Tolerance:
One critical advantage of triangular routing is its fault tolerance capabilities. In the event of a link failure or network congestion on one path, the other two paths can still carry the data packets to their destination. This redundancy ensures that the network remains operational despite adverse conditions, reducing the risk of data loss and maintaining uninterrupted connectivity.
Benefits of Triangular Routing:
1. Improved Network Performance: Triangular routing enhances network performance by distributing traffic across multiple paths, reducing congestion, and minimizing latency.
2. Enhanced Reliability: With fault tolerance capabilities, triangular routing ensures uninterrupted connectivity, even in the face of link failures or network congestion.
3. Scalability: Triangular routing provides a scalable solution for network optimization. As the network expands, additional paths can be added to accommodate the increased traffic, ensuring efficient data transmission.
4. Cost-Efficiency: By optimizing network performance, triangular routing helps reduce operational costs associated with network maintenance and upgrades.
Summary: Triangular Routing
The LISP (Locator/ID Separation Protocol) has revolutionized network architecture, providing efficient solutions for routing and scalability. One intriguing aspect of LISP is triangular routing, a crucial mechanism in optimizing traffic flow. In this blog post, we explored the intricacies of triangular routing within the LISP protocol, exploring its significance and functionality.
Section 1: Understanding LISP Protocol
Before diving into triangular routing, it is essential to grasp the fundamentals of the LISP protocol. LISP is designed to separate the identifier (ID) and the locator (LOC) within IP addresses. By doing so, it enables efficient routing and mobility management. This separation allows for enhanced scalability and flexibility in handling network traffic.
Section 2: Unveiling the Concept of Triangular Routing
Triangular routing is a crucial mechanism employed by LISP to optimize traffic flows. It involves the establishment of a direct tunnel between the source and destination devices, bypassing traditional routing paths. This tunnel ensures that packets take the shortest path possible, improving performance and reducing latency.
Section 3: The Benefits of Triangular Routing
Triangular routing offers several advantages within the LISP protocol. Firstly, it eliminates unnecessary detours by establishing a direct tunnel, thus reducing packet travel time. Secondly, it enhances network security by obscuring the devices’ location, making it challenging for potential attackers to pinpoint them. Lastly, triangular routing promotes load balancing by dynamically selecting the most efficient path for traffic flow.
Section 4: Challenges and Considerations
While triangular routing brings notable benefits, it also presents challenges that must be addressed. One key consideration is the potential for suboptimal routing in specific scenarios. Careful planning and configuration are required to ensure that triangular routing is properly implemented and does not interfere with network performance. Additionally, network administrators must be aware of the potential impact on troubleshooting and monitoring tools, as triangular routing may introduce complexities in these areas.
Conclusion:
Triangular routing plays a significant role within the LISP protocol, offering enhanced performance, security, and load-balancing capabilities. Establishing direct tunnels between devices enables efficient traffic flow and minimizes latency. However, it is essential to consider the challenges and potential trade-offs associated with triangular routing. With careful planning and configuration, network administrators can harness its benefits and optimize network performance within the LISP protocol.